Давайте углубимся в различие между ключом продукта и кодом активации:
ключ продукта
-
Ключ продукта — это уникальный буквенно-цифровой код, предоставленный во время установки программного обеспечения Майкрософт (например, Windows или Office).
-
Он служит лицензионным ключом, который проверяет вашу собственность на программное обеспечение.
-
Ключи продукта обычно имеют длину 25 символов и используются в процессе установки.
-
При вводе допустимого ключа продукта он открывает все функциональные возможности программного обеспечения.
-
Думайте о нем как о «ключе», который предоставляет доступ к программному обеспечению.
Код активации
-
Код активации (также известный как ключ активации) используется для активации программного обеспечения после установки.
-
Активация гарантирует, что программное обеспечение является подлинным и лицензированным по закону.
-
В отличие от ключа продукта, который вводится во время установки, код активации применяется после установки.
-
Коды активации часто связаны с определенной конфигурацией оборудования или учетной записью пользователя.
-
Они проверяют, что у вас есть действительная лицензия на использование программного обеспечения.
Таким образом, ключ продукта используется во время установки, а код активации используется для последующей активации программного обеспечения. Оба они имеют важное значение для обеспечения законного и функционального взаимодействия с программным обеспечением.
Совет: Для Windows 10/11, если вы столкнулись с ситуацией, когда ключ продукта короче (20 символов), не волнуйтесь, вы можете переустановить Windows 10/11 без необходимости ключа продукта. После подключения компьютера к Интернету Windows 10 самостоятельно активируется на основе ваших цифровых прав, хранящихся на серверах активации Майкрософт.
Подробнее
Активация ключа продукта или активация Office
Использование ключей продуктов с Office
Как найти ключ продукта Windows
Активация Windows
Активировать Office
Нужна дополнительная помощь?
Нужны дополнительные параметры?
Изучите преимущества подписки, просмотрите учебные курсы, узнайте, как защитить свое устройство и т. д.
With its widespread use across personal computers and servers worldwide, Windows has become an indispensable operating system from Microsoft. Yet, its less visible elements, such as Product IDs and Product Keys, play a critical role in the Windows ecosystem.
If you also think of these two elements as the same thing, you are wrong. Though these strings of characters serve as digital fingerprints, uniquely identifying and verifying a specific instance of the software, product ID and product key are two different things.
While seemingly small, these hold immense significance not just for Microsoft but also for the millions of users relying on Windows to carry out daily tasks.
Let’s take a closer look at Product IDs and Product Keys and understand why they are important in the world of Windows.
Table of Contents
What is Windows Product ID
Imagine you have just bought a brand new laptop with the latest version of Windows installed on it. Everything seems to be running smoothly until one day when you try to activate your operating system, you are prompted to enter a mysterious sequence of characters known as a “Product ID.”
So, what exactly is a Product ID, and why is it important?
Simply put, it is a unique identifier that is used to distinguish one installation of Windows from another. It is typically a combination of numbers and letters specific to the version of Windows installed on your computer, as well as the channel through which it was acquired.
In simpler words, a Windows product ID is the equivalent of a chassis number for a car – there is only one item in the entire world with the associated ID.
It is essential for maintaining the security and stability of your computer and ensuring that you have access to all of the features and benefits of a valid license. Microsoft uses this information to track its software usage and support users who have purchased a license.
The importance of having a valid Product ID cannot be overstated. Without it, your operating system will be unable to receive important security updates and other critical patches that are necessary for keeping your computer safe and secure.
In addition, if you ever need to contact Microsoft support for assistance with your software, they will likely ask you to provide your Product ID in order to verify that you are running a genuine version of Windows.
How to Find Windows Product ID
There are several ways for you to find the product ID on a Windows client PC (Windows 10/11, etc.) or a Windows Server.
Get Product ID on Windows 11, 10, Server 2019
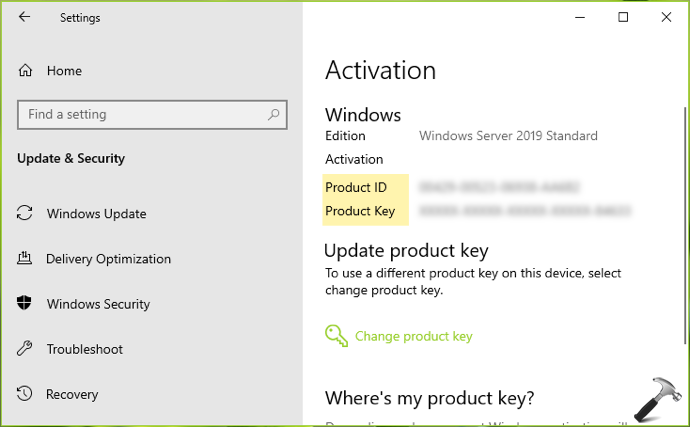
On the modern Windows operating systems, you can view the product ID in the Settings app or from the Command Prompt. Follow these steps to view the product ID from the Settings app:
-
Navigate to the following:
-
In Windows 11:
Settings app >> System >> Activation
-
In Windows 10, Server 2019 and later:
Settings app >> Update & Security >> Activation
-
-
You will find the Product ID in this format “XXXXX-XXX-XXXXXXX-XXXXX.”
To get the product ID for a Windows OS, use these steps instead:
-
Open an elevated Command Prompt.
-
Run the following cmdlet:
slmgr/dli -
A pop-up will now appear with your product ID.
Get Product ID on Windows 7 and Older
-
Open the Control Panel by typing in “control” in the Run Command box.
-
Click “System.”
-
Look for the 20-characters product ID after the activation info.
What is Windows Product Key
Product Key is a 25-character unique code that is assigned to every copy of the Windows operating system. This key serves as an authentication mechanism that confirms that the copy of Windows you are using is genuine and has been purchased legally. In simpler terms, it is like a digital license that grants you access to all the features of your Windows operating system.
What makes the product key so important?
Firstly, it ensures you use a legal and authorized copy of Windows. This helps in preventing piracy and other illegal activities which could harm the software industry. Secondly, it helps maintain the security and stability of your operating system by providing regular updates and patches.
Moreover, a product key is necessary if you want to enjoy all the features of your Windows operating system. Some features, such as personalization options, advanced settings, and security features, are only available to users who have activated their copy of Windows using a valid product key.
How to Find Windows Product Key
There are multiple ways of finding a product key in Windows. However, steps to the simplest and the most common way that works for everyone is via Command Prompt. Here is how to do it:
-
Open an elevated Command Prompt.
-
Run the following cmdlet:
wmic path softwareLicensingService get OA3xOriginalProductKeyFind Product Key via Command Prompt
To know more about other methods for finding your product key, refer to our detailed guide: 4 Ways To Find Windows 10 Product Key.
Difference in Windows Product ID vs. Product Key
All in all, product ID and product key in Windows may seem similar, but they serve different purposes. A product ID is a unique identifier for each installation of Windows and is primarily used for technical support and troubleshooting. In contrast, a product key is a code used to activate Windows and verify a genuine license.
Understanding the difference between these two identifiers can help ensure proper activation and access to technical support when needed.
Frequently Asked Questions (FAQs)
Are product ID and product key the same in Windows?
No, product ID and product keys are two different things. A product ID determines the level or serviuce you are entitled to, like the version and edition of your operating system. In contrast, the product key pairs your license with your computer and defines the operating system’s authenticity.
Is a license key and product key the same in Windows?
Technically, the answer is yes. A Windows key is referred to as a “product key” if you buy a physical disc (Fully Packed Product (FPP) license) and the key is printed on its covered. Whereas, the same key is referred to as a “license key” if you purchase a digital key from Microsoft or one of its retailers.
If you’re a long time Windows user, you might have already heard about Product ID and Product Key terms. While if you’re new to Windows, these terms might also be new for you. First of all, you must know that Product ID and Product Key are not same thing. They are different terms and have different usage.
So if you’re just wondering what are these terms and how you can differentiate in between them. To clear your doubts further, we’ll provide in-depth comparison between both these terms in this post.
Page Contents
Product ID vs. Product Key In Windows
About Product ID: Importance and Usage
Product ID is usually used to identify the channel which originated the software. It also provides information about level of support that is associated with software. The Product ID is not a unique code. There is a possibility that multiple machines may have same Product ID.
A Product ID is typically seen in XXXXX-XXX-XXXXXXX-XXXXX format. Here, the second set of characters may define the Windows licensing channel. Microsoft provides Windows license via different channels depending upon need of their customers. For example, well known channels are retail, OEM, volume. To learn about type of license or channel you’ve, refer this guide.
To check your Product ID, go to Settings app > Update & Security > Activation in Windows 10, Windows Server 2019. For other Windows OS, open Control Panel and go to System, Product ID should be located in bottom, after activation info.
About Product Key: Importance and Usage
A Product Key is used to activate Windows software. It is 25-character unique code in XXXXX-XXXXX-XXXXX-XXXXX-XXXXX format. If you lose your unique Product Key, you may have trouble activating your Windows OS. A Product Key can be located depending upon how you got your license. To find your Product Key, please refer this article.
You can locate Product Key at Settings app > Update & Security > Activation in Windows 10. However, the Product Key is not shown by default, unlike the Product ID. This is to prevent misuse of your Product Key by someone else other than you. Remember, you should always keep your Product Key confidential and never share it with anyone.
We hope above information should have cleared your doubts about Product ID and Product Key terms and there is no confusion further.
That’s it!
RELATED ARTICLES
From Wikipedia, the free encyclopedia
A product key, also known as a software key, serial key or activation key, is a specific software-based key for a computer program. It certifies that the copy of the program is original.
Product keys consist of a series of numbers and/or letters. This sequence is typically entered by the user during the installation of computer software, and is then passed to a verification function in the program. This function manipulates the key sequence according to an algorithm or mathematical formula and attempts to match the results to a set of valid solutions. If they match, the program is activated, permitting its use or unlocking features. With knowledge about the algorithm used, such as that obtained via reverse engineering of the program, it is possible to create programs called keygens that generate these keys for a particular program.
Effectiveness
Standard key generation, where product keys are generated mathematically, is not completely effective in stopping copyright infringement of software, as these keys can be distributed. In addition, with improved communication from the rise of the Internet, more sophisticated attacks on keys such as cracks (removing the need for a key) and product key generators have become common.
Because of this, software publishers use additional product activation methods to verify that keys are both valid and uncompromised. One method assigns a product key based on a unique feature of the purchaser’s computer hardware, which cannot be as easily duplicated since it depends on the user’s hardware. Another method involves requiring one-time or periodical validation of the product key with an internet server (for games with an online component, this is done whenever the user signs in). The server can deactivate unmodified client software presenting invalid, duplicated, missing or otherwise compromised keys. Modified clients may bypass these checks,[1] but the server can still deny those clients information or communication.
Examples
Windows 95 retail key
Windows 95 retail product keys take the form XXX-XXXXXXX.[2] To determine whether the key is valid, Windows 95 performs the following checks:
- The first 3 characters must not be equal to 333, 444, 555, 666, 777, 888 or 999.
- The last 7 characters must all be numbers from 0-8.
- The sum of the last 7 numbers must be divisible by 7 with no remainder.
- The fourth character is unchecked.
If all checks pass, the product key is valid. Consequently a product key of 000-0000000 would be considered valid under these conditions.
Windows 95 OEM key
Windows 95 OEM keys take the form XXXXX-OEM-XXXXXXX-XXXXX.
- The first 3 characters must be a number between 0-366.
- The next 2 characters must be a number between 04-93.
- The next 3 characters must be OEM.
- The sum of the next 7 numbers must be divisible by 7 with no remainder.
- The rest of the characters are unchecked.
Windows XP retail key
Windows XP uses an installation ID, product ID, and a product key for activation.[3][4]
Installation ID
The installation ID is a 50 digit decimal string that is divided into 5 groups of six digits each with 2 digits at the end, which takes the form of XXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX-XX. The installation ID is regenerated every time msoobe.exe is ran.
Check digits
The right most digit in each group of the installation ID is a check digit.
- Each check digit is calculated by adding the other five digits in its group.
- Then adding the digits in that group in the even positions a second time.
- Then dividing the sum of them by 7.
- The remainder is the value of the check digit in its group.
Decoding
Removing the check digits results in a 41-digit decimal encoded 136 bit multi precision integer, which is stored in little endian byte order as a byte array.
Decryption
The lower 16 bytes of the Installation ID are encrypted, whereas the most significant byte is kept in plaintext. The cryptographic algorithm used to encrypt the Installation ID is a proprietary four-round Feistel cipher. Since the block of input bytes passed to a Feistel cipher is divided into two blocks of equal size, this class of ciphers is typically applied to input blocks consisting of an even number of bytes in this case the lower 16 of the 17 input bytes. The round function of the cipher is the SHA-1 message digest algorithm keyed with a four-byte sequence.
Let + denote the concatenation of two byte sequences, ^ the XOR operation, L and R the left and right eight-byte input half for one round, L’ and R’ the output halves of said round, and First-8() a function that returns the first eight bytes of an SHA-1 message digest.
Then one round of decryption looks as follows.
L’ = R ^ First-8(SHA-1(L + Key))
R’ = L
The result of the decryption is 16 bytes of plaintext, which are together with the 17th unencrypted byte which will be interpreted as four double words in little endian byte order followed by a single byte.
| Name | Size | Offset |
|---|---|---|
| H1 | Double word | 0 |
| H2 | Double word | 4 |
| P1 | Double word | 8 |
| P2 | Double word | 12 |
| P3 | Byte | 16 |
H1 and H2 specify the hardware configuration that the Installation ID is linked to. P1 and P2 as well as the remaining byte P3 contain the Product ID associated with the Installation ID.
Product ID
The Product ID consists of five groups of decimal digits, as in AAAAA-BBB-CCCCCCC-DDEEE.
Decoding
The mapping between the Product ID in decimal representation and its binary encoding in the double words P1 and P2 and the byte P3 is summarized in the following table.
| Digits | Length | Encoding | Meaning |
|---|---|---|---|
| AAAAA | 17 Bits | Bit 0 to bit 16 of P1 | Always 55034 (in Windows XP RC1) |
| BBB | 10 Bits | Bit 17 to bit 26 of P1 | Most significant three digits of Raw Product Key |
| CCCCCCC | 28 Bits | Bit 27 to bit 31 of P1 (lower 5 bits) and Bit 0 to bit 22 of P2 (upper 23 bits) | Least significant six digits of Raw Product Key and check digit |
| DDEEE | 17 Bits | Bit 23 to bit 31 of P2 (lower 9 bits) and Bit 0 to bit 7 of P3 (upper 8 bits) | DD = Index of the public key used to verify the Product key
EEE = Random value |
Product key
The Product key takes the form as XXXXX-XXXXX-XXXXX-XXXXX-XXXXX. Each character is one of the following 24 letters and digits: B C D F G H J K M P Q R T V W X Y 2 3 4 6 7 8 9
The 25 characters of the Product Key form a base-24 encoding of the binary representation of the Product Key. The Product Key is a multi-precision integer of roughly 115 bits, which is stored in little endian byte order in an array of 15 bytes. Of these 15 bytes the least significant four bytes contain the Raw Product Key in little endian byte order. The least significant bit is removed by shifting this 32-bit value to the left by one bit position. The eleven remaining bytes form a digital signature, allowing verification of the authenticity of the Product Key by means of a hard-coded public key.
To obtain the CCCCCCC component, a check digit is appended, and the check digit that is chosen such that the sum of all digits, including the check digit, is divisible by seven. For verifying a Product Key, more than one public key is available. If verification with the first public key fails, the second is tried, etc. The DD component of the Product ID specifies which of the public keys in this sequence was successfully used to verify the Product Key.
Hardware information bit-fields
The hardware configuration linked to the Installation ID is represented by the two double words H1 and H2. For this purpose, the double words are divided into twelve bit-fields.
| Double Word | Offset | Length | Bit-Field-value based on |
|---|---|---|---|
| H1 | 0 | 10 | Volume serial number string of system volume |
| H1 | 10 | 10 | Network adapter MAC address string |
| H1 | 20 | 7 | CD-ROM drive hardware identification string |
| H1 | 27 | 5 | Graphics adapter hardware identification string |
| H2 | 0 | 3 | Unused, set to 001 |
| H2 | 3 | 6 | CPU serial number string |
| H2 | 9 | 7 | Hard drive hardware identification string |
| H2 | 16 | 5 | SCSI host adapter hardware identification string |
| H2 | 21 | 4 | IDE controller hardware identification string |
| H2 | 25 | 3 | Processor model string |
| H2 | 28 | 3 | RAM size |
| H2 | 31 | 1 | 1 = dockable, 0 = not dockable |
If docking is possible, the activation mechanism will be more tolerant with respect to future hardware modifications. If the hardware component corresponding to one of the remaining ten bit-fields is present, the respective bit-field contains a non-zero value describing the component. A value of zero marks the hardware component as not present. All hardware components are identified by a hardware identification string obtained from the registry. Hashing this string provides the value for the corresponding bit-field.
Hashing
The hash result is obtained by feeding the hardware identification string into the MD5 message digest algorithm and picking the number of bits required for a bit-field from predetermined locations in the resulting message digest. Different predetermined locations are used for different bit-fields. In addition, a hash result of zero is avoided by calculating . Where BitFieldMax is the maximal value that may be stored in the bit-field in question, e.g. 1023 for a 10-bit bit-field, and ‘x % y’ denotes the remainder of the division of x by y. This results in values between 1 and BitFieldMax. The obtained value is then stored in the respective bit-field.
RAM bit-field
The bit-field related to the amount of RAM available to the operating system is calculated differently from the other bit-fields as shown in the table.
| Value | Amount of RAM possible |
|---|---|
| 0 | (bit-field is unused) |
| 1 | Below 32 MB |
| 2 | between 32 MB and 63 MB |
| 3 | Between 64 MB and 127 MB |
| 4 | Between 128 MB and 255 MB |
| 5 | Between 256 MB and 511 MB |
| 6 | Between 512 MB and 1023 MB |
| 7 | Above 1023 MB |
Note that the amount of RAM is retrieved by calling the GlobalMemoryStatus() function, which reports a few hundred kilobytes less than the amount of RAM physically installed. So, 128 MB of RAM would typically be classified as «between 64 MB and 127 MB».
Hardware modifications
wpa.dbl is the RC4-encrypted database that stores, expiration information, the confirmation ID of an activated installation, the bit-field values representing the current hardware configuration, and the bit-field values representing the hardware configuration at the time of product activation, etc. The current hardware configuration is automatically updated each time the hardware configuration is modified in order to reflect the changes, while the values representing the hardware configuration at the time of product activation is fixed. When judging whether re-activation is necessary, the bit-field values of the current hardware configuration is compared to the hardware configuration at the time of activation.
Non-dockable computers
All bit-fields with the exception of the unused field and the ‘dockable’ field are compared. If more than three of these ten bit-fields have changed in the current hardware configuration since product activation, re-activation is required.
Dockable computers
If bit 31 of H2 indicates that our computer supports a docking station, only seven of the ten bit-fields mentioned above are compared. The bit-fields corresponding to the SCSI host adapter, the IDE controller, and the graphics board are omitted. Of these remaining seven bit-fields, only up to three may change without requiring re-activation.
Controversy
Some of the most effective product key protections are controversial due to inconvenience, strict enforcement, harsh penalties and, in some cases, false positives. Some product keys use uncompromising digital procedures to enforce the license agreement.
Inconvenience
Product keys are somewhat inconvenient for end users. Not only do they need to be entered whenever a program is installed, but the user must also be sure not to lose them. Loss of a product key usually means the software is useless once uninstalled, unless, prior to uninstallation, a key recovery application is used (although not all programs support this).[5]
Product keys also present new ways for distribution to go wrong. If a product is shipped with missing or invalid keys, then the product itself is useless. For example, all copies of Splinter Cell: Pandora Tomorrow originally shipped to Australia without product keys.[6]
Enforcement and penalties
There are many cases of permanent bans enforced by companies detecting usage violations. It is common for an online system to immediately blacklist an account caught running cracks or, in some cases, cheats. This results in a permanent ban. Players who wish to continue use of the software must repurchase it. This has inevitably led to criticism over the motivations of enforcing permanent bans.[citation needed]
Particularly controversial is the situation which arises when multiple products’ keys are bound together. If products have dependencies on other products (as is the case with expansion packs), it is common for companies to ban all bound products. For example, if a fake key is used with an expansion pack, the server may ban legitimate keys from the original game. Similarly, with Valve’s Steam service, all products the user has purchased are bound into the one account. If this account is banned, the user will lose access to every product associated with the same account.[7]
This «multi-ban» is highly controversial, since it bans users from products which they have legitimately purchased and used.[citation needed]
False positives
Bans are enforced by servers immediately upon detection of cracks or cheats, usually without human intervention. Sometimes, legitimate users are wrongly deemed in violation of the license, and banned. In large cases of false positives, they are sometimes corrected (as happened in World of Warcraft.[8]) However, individual cases may not be given any attention.[citation needed]
A common cause of false positives (as with the World of Warcraft case above) is users of unsupported platforms. For example, users of Linux can run Windows applications through compatibility layers such as Wine and Cedega. This software combination sometimes triggers the game’s server anti-cheating software, resulting in a ban due to Wine or Cedega being a Windows API compatibility layer for Linux, so it is considered third-party (cheating) software by the game’s server.[9] [citation needed]
See also
- Biometric passport
- Cryptographic hash function
- Intel Upgrade Service
- Keygen
- License manager
- Product activation
- Serial number
- Software license server
- Volume license key
References
- ^ Chang, Hoi; Atallah, Mikhail J. (2002). «Protecting Software Codes by Guards». Security and Privacy in Digital Rights Management. Springer. p. 160-175. doi:10.1007/3-540-47870-1_10. ISBN 978-3-540-47870-6.
- ^ Upadhyay, Saket (May 14, 2021). «Reversing Microsoft’s Windows95 Product Key Check Mechanism».
- ^ Purdy, Kevin (2023-05-26). «Green hills forever: Windows XP activation algorithm cracked after 21 years». Ars Technica. Retrieved 2024-06-29.
- ^ Chaussee, Rudower (July 2001). «Inside Windows Product Activation». Licenturion. Retrieved June 28, 2024.
- ^ «ProduKey — Recover lost product key (CD-Key) of Windows/MS-Office/SQL Server». NirSoft. Retrieved 2021-02-09.
- ^ Australian Pandora Tomorrow CD-Key Problems Shack News
- ^ «Valve suspends 20,000 Steam accounts». GameSpot. Retrieved 2013-05-15.
- ^ Blizzard Unbans Linux World of Warcraft Players Softpedia
- ^ «Linux users banned from Diablo 3- End Gamers». Archived from the original on 2012-07-10. Retrieved 2012-08-14.

