Can someone clarify the calculated Windows size in a capture, is this the reciever buffer/window on the source
If the source is the client, then the calculated windows size is on the client side
however if the source is the server is the calculated windows size the server or still the client side
1 Answer
It is the calculated window size on the system that sent that packet. Packets from the client will have the client’s window size; packets from the server will have the server’s window size. Packets from the sender wil have the sender’s window size; packets from the receiver will have the receiver’s window size. With every packet, each system tells the other one, «This is how much space I have for incoming data.»
Your Answer
Please start posting anonymously — your entry will be published after you log in or create a new account.
Question Tools
1 follower
Lesson Contents
TCP (Transmission Control Protocol) is a connection oriented protocol which means that we keep track of how much data has been transmitted. The sender will transmit some data and the receiver has to acknowledge it. When we don’t receive the acknowledgment in time then the sender will re-transmit the data.
TCP uses “windowing” which means that a sender will send one or more data segments and the receiver will acknowledge one or all segments. When we start a TCP connection, the hosts will use a receive buffer where we temporarily store data before the application can process it.
When the receiver sends an acknowledgment, it will tell the sender how much data it can transmit before the receiver will send an acknowledgment. We call this the window size. Basically, the window size indicates the size of the receive buffer.
Typically the TCP connection will start with a small window size and every time when there is a successful acknowledgement, the window size will increase. Here’s an example:
Above we have two hosts, the host on the left side will send one segment and the host on the right side will send an acknowledgment in return. Since the acknowledgement was successful, the windows size will increase:
The host on the left side is now sending two segments and the host on the right side will return a single acknowledgment. Everything is working fine so the window size will increase even further:
The host is now sending four segments and the host on the right side responds with a single acknowledgment.
In the example above the window size keeps increasing as long as the receiver sends acknowledgments for all our segments or when the window size hits a certain maximum limit. When the receiver doesn’t send an acknowledgment within a certain time period (called the round-trip time) then the window size will be reduced.
When an interface has congestion then it’s possible that IP packets are dropped. To deal with this, TCP has a number of algorithms that deal with congestion control. One of them is called slow start.
Congestion occurs when the interface has to transmit more data than it can handle. It’s queue(s) will hit a limit and packets will be dropped.
With TCP slow start, the window size will initially grow exponentially (window size doubles) but once a packet is dropped, the window size will be reduced to one segment. It will then grow exponentially again until the window size is half of what it was when the congestion occurred. At that moment, the window size will grow linearly instead of exponentially.
When an interface gets congested, it’s possible that all your TCP connections will experience TCP slow start. Packets will be dropped and then all TCP connections will have a small window size. This is called TCP global synchronization. Here’s what it looks like:
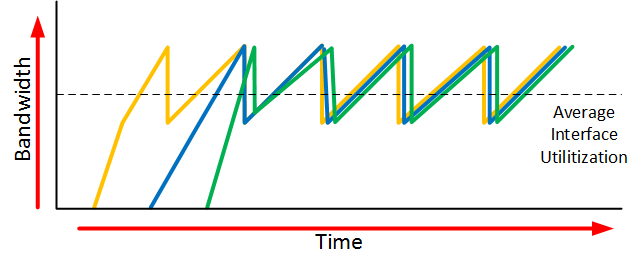
The orange, blue and green lines are three different TCP connections. These TCP connections start at different times and after awhile, the interface gets congested and packets of all TCP connections are dropped. What happens is that the window size of all these TCP connections will drop to one and once the interface congestion is gone, all their window sizes will increase again.
The interface then gets congested again, the window size drops back to one and the story repeats itself. The result of this is that we don’t use all the available bandwidth that our interface has to offer. If you look at the dashed line you can see that we the average interface utilization isn’t very high.
To prevent global synchronization we can use RED (Random Early Detection). this is a feature that drops “random” packets from TCP flows based on the number of packets in a queue and the TOS (Type of Service) marking of the packets. When packets are dropped before a queue is full, we can avoid the global synchronization.
The end result will look similar to this:
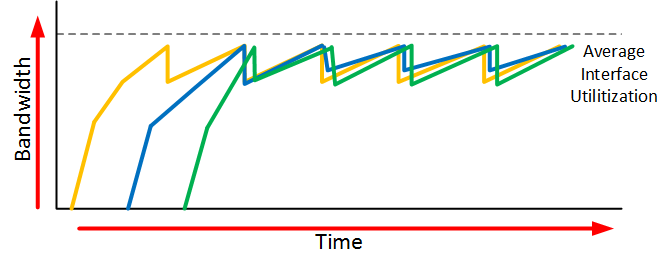
When we use RED, our average interface utilization will improve.
Now you have an idea what the TCP window size is about, let’s take a look at a real example of how the window size is used. We can use wireshark for this.
Wireshark Captures
To examine the TCP window size I will use two devices:
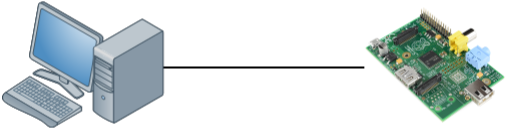
The device on the left side is a modern computer with a gigabit interface. On the right side, we have a small raspberry pi which has a FastEthernet interface. The raspberry pi is a great little device but it’s cpu / memory / ethernet interface are limited. To get an interesting output, I will copy a large file through SSH from my computer to the raspberry pi which will be easily overburdened.
Here’s what happened, take a look at this picture:
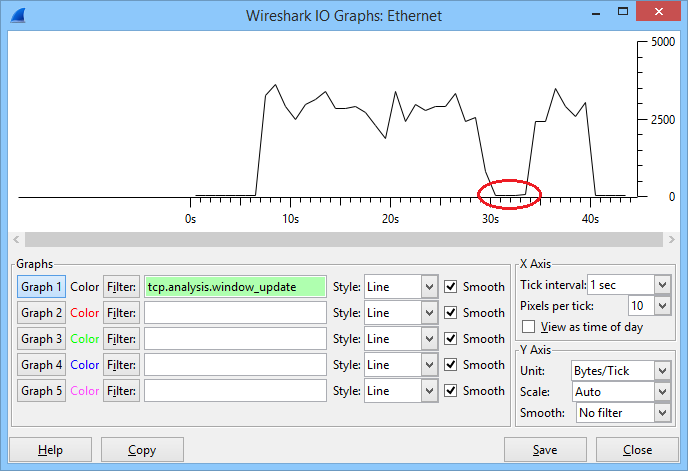
In the graph above you can see the window size that was used during this connection. The file transfer started after about 6 seconds and you can see that the window size increased fast. It went up and down a bit but at around 30 seconds, it totally collapsed. After a few seconds it increased again and I was able to complete the file transfer. Let’s take a closer look at this file transfer, which starts with the three way handshake:
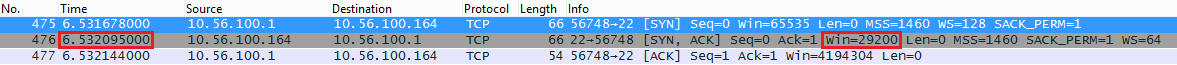
My fast computer uses 10.56.100.1 and the raspberry pi uses 10.56.100.164. Above you can see that in the SYN,ACK message that the raspberry pi wants to use a window size of 29200. My computer wants to use a window size of 8388480 (win=65535 * ws=128) which is irrelevant now since we are sending data to the raspberry pi.
After a few packets, the window size of the raspberry pi looks like this:
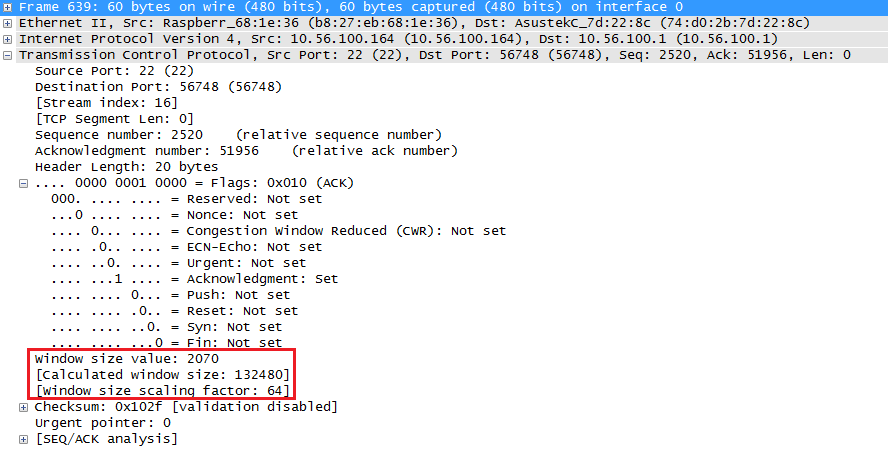
Above you can see that the window size has increased to 132480. Originally the window size is a 16 bit value so the largest window size would be 65535. Nowadays we use a scaling factor so that we can use larger window sizes.
At around the 10 second mark the window size decreased. Here’s what happened:
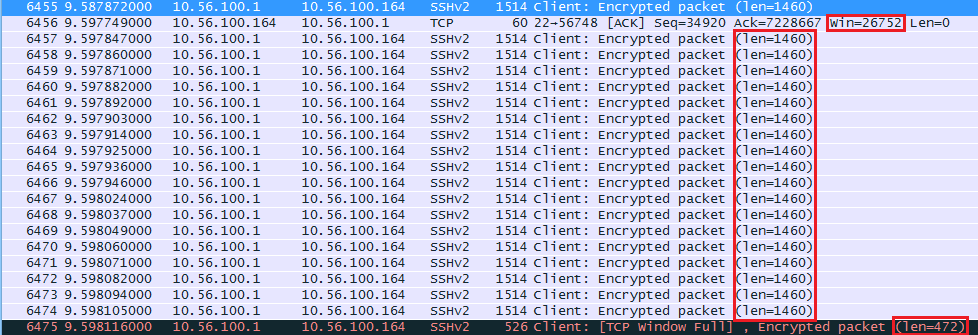
The raspberry pi seems to have trouble keeping up and its receive buffer is probably full. It tells the computer to use a window size of 26752 from now on. The computer sends 18 segments with 1460 bytes and one segment of 472 bytes (26752 bytes in total). The last packet shows us “TCP Window Full” message. This is something that wireshark reports to us, our computer has completely filled the receive buffer of the raspberry pi.
Once the raspberry pi has caught up a bit and around the 30 second mark, something bad happens. Take a look at the wireshark capture below:
Above you can see that the raspberry pi sends an ACK to the computer with a window size of 0. This means that the window size will remain at 0 for a specified amount of time, the raspberry pi is unable to receive any more data at this moment and the TCP transmission will be paused for awhile while the receive buffer is processed.
Here’s the actual packet:
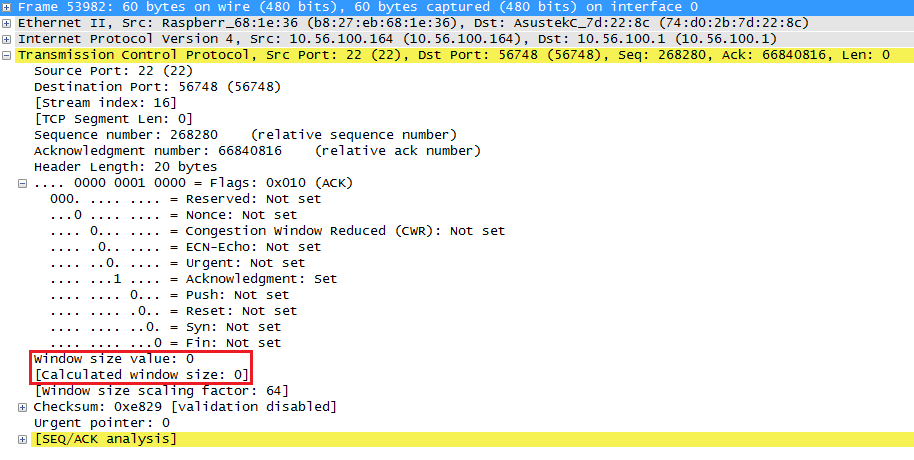
Above you can see that the window size is now 0. Once the receive buffer has been processed, the raspberry pi will send an ACK with a new window size:
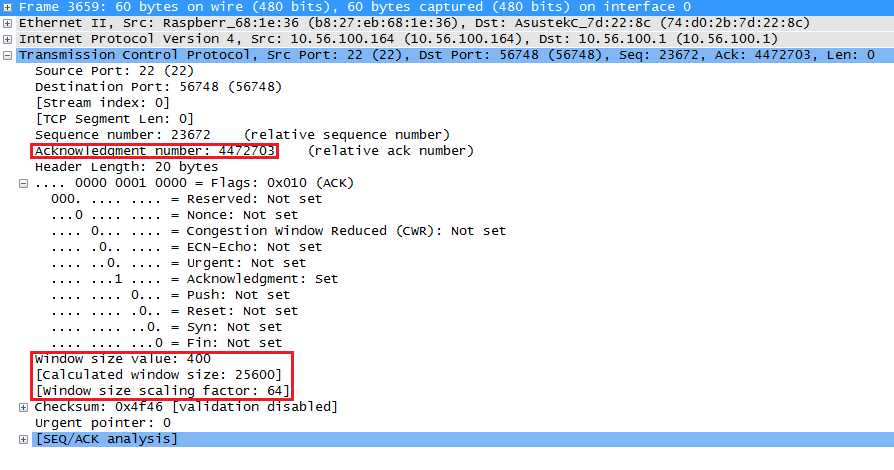
The window size is now only 25600 bytes but will grow again. The rest of the transmission went without any hiccups and the file transfer completed.
Conclusion
You have now seen how TCP uses the window size to tell the sender how much data to transmit before it will receive an acknowledgment. I also showed you an example of how the window size is used when the receiver is unable to process its receive buffer in time.
UDP, unlike TCP is a connectionless protocol and will just keep sending traffic. There is no window size, for this reason you might want to limit your UDP traffic or you might see starvation of your TCP traffic when there is congestion.
I hope you have enjoyed this lesson, if you have any more questions feel free to leave a comment in our forum.
Why do 80% of the code farmers can’t be architects? >>>
Recently, when I found out that my two machines were issued in the project, one of them had a slower collection. I wanted to catch a package and look at it. I used to just look at the captured data.
This time I really care about the window. At first glance, I feel strange. I used the following catching command:
tcpdump -i eth0 tcp and port 9981 -w /data/steven/tcpdump/tcpdump.cap -C 1 -s 0&Mainly -C, limit the file size to 1M to cut the file. Since the two programs are long-connected, the packets captured in the middle have no SYN handshake process.
Looking at the data, I feel very strange.
99 machine tells 100 machines, win=36 but immediately after 100 sent 99 a len=180 data, this does not meet the implementation of the sliding window!
I haven’t found the relevant information for a long time, because I did not check the method before, and then let my colleagues restart the program, and then catch a handshake package.
The SYN package, at first glance, seems to be normal:
This package win looks a bit normal, although there is still a problem here, 99 win is much smaller than 100. Why do I think the first package is not working properly?
Because RFC says MSS Ethernet is 1460 bytes (1500 -40), and the minimum MSS seems to be 536 bytes (576 minimum reassembly buffer bytes — 40).
Click on the SYN package and see the following two fields caught my attention:
Google got a wireshark window size value calculated window size foundReference linkTwo articles in the second due to the second
After being walled, I can only see the first one. I did find the answer here:
Since TCP’s header window field is only 16 bits, it represents up to 64k. In order to represent a larger window, an optional magnification is used.
1. In the TCP three-way handshake, in the SYN or SYN, ACK packet, inform the options optional information, telling the other party to use the magnification.
2.SYN itself does not enlarge
3. So the window size value indicates the value of the message, and the calculated window size indicates the enlarged value, which is the actual available value.
This value should be wireshark for the sake of friendliness and figure it out.
Back to the beginning of the problem, I used the -C parameter when tcpdump, that is, when the file exceeds 1M, it will be cut into multiple files, when your
When the file does not contain a three-way handshake (SYN), wireshark does not know your magnification, so the displayed value will have my doubts:
Why win only 36 but can send len=180.
As you can see, in the tcpdump file that does not contain the SYN package, wireshark does not know your multiple, so it displays -1 (unknown), and
In your package, this value is displayed as win = 37. If 128 is corrected (actually 128), the calculated window size is correct.
It should show 37 * 128 = 4736 This is not much worse than the following, much better than 180, of course, can send 180.
The following package is caught in the SYN containing, and he can tell you that the multiple is 128, which is actually 5760.
I finally figured out this, and then there are actually two questions:
-
Why is there so much difference between the two sides when shaking hands, 100 is at least 2.4 times that of 99.
-
When does TCP start this magnification?
A: Check the information, it seems that Linux has a kernel configuration parameter.
[steven@KFJK ~]$ more /proc/sys/net/ipv4/tcp_window_scaling
1
Detailed information here is a brief description[Original] TCP receiving window adjustment algorithm (on)
“If the maximum value of the receive window is limited by tcp_rmem[2] = 4194304, then rcv_wscale = 7, the window expansion factor is 128. ”
And my system settings seem to be just right (but the factor is far more than this):
[steven@KFJK ~]$ cat /proc/sys/net/ipv4/tcp_rmem
4096 87380 4194304
This article recommended by colleagues is not bad.TCP Windows and Window Scaling
By the way, recommend a colleague’s articleWireshark tcp protocol analysis It is also very well written.
I still have time to read it.TCP/IP detailed volumeHere, I recommend everyone to look at two articles written in high handwriting, fast food:
CoolshellThose things about TCP (on)withThose things about TCP (below)
—
Reference link
-
TCP transmission behavior analysis, interpretation of common fields of wireshark
-
www.wireshark.orgThis is the wall, there is a chance to see
Tcp window scaling is a key design in tcp protocol to improve network performance. Today we will dive into this topic to see how tcp window scale works in Linux.
- What is tcp window scaling?
- Benefit of tcp_window_scaling
- How to Check tcp_window_scaling in Linux?
- How to enable tcp_window_scaling?
- Tips for tcp_window_scaling
- Example of tcp_window_scaling
Table of Contents
What is tcp window scaling?
The TCP Window Scale option allows window size larger than 65K bytes by using a scale factor to multiply the window size value. This factor is set based on maximum size of receive buffer used by TCP sockets.
In the following example, maximum size of receive buffer is 4194304, so the scale factor is 7.
net.ipv4.tcp_rmem = 4096 87380 4194304

Get Your Free Linux training!
Join our free Linux training and discover the power of open-source technology. Enhance your skills and boost your career!
Start Learning Linux today — Free!
Note: The largest supported scaling factor is 14. This allows TCP window sizes of up to one Gigabyte.We can get more info from here. https://www.ietf.org/rfc/rfc1323.txt
Benefit of tcp_window_scaling
The base window size can not exceed 65535 bytes due to the limitations of the TCP header. This makes the window size too small.This option improves network bandwidth a lot. We can get the window size up to 1GB.Here’s the formula for calculating the maximum throughput of a single TCP connection: Window size / (RTT latency in milliseconds / 1,000) = maximum bytes/second
This table shows the maximum megabytes/per second throughput of a single TCP connection.

After tcp window scale is enabled, we can see that the bandwidth improves a lot.

Related:
How to Check tcp_window_scaling in Linux?
This is enabled by default in most Linux distributions. We can check it by the following command. cat /proc/sys/net/ipv4/tcp_window_scaling
If the output is 1, that means tcp window scaling is enabled.If the output is 0, that means tcp window scaling is disabled.
How to enable tcp_window_scaling?
We can use the following command to enable TCP window scaling. sysctl -w net.ipv4.tcp_window_scaling=1
To make this reboot persistent, we can add the following line to /etc/sysctl.conf. net.ipv4.tcp_window_scaling=1
Tips for Tcp_window_scaling
The window scaling option only appears in the first two packets of a TCP connection, it cannot be changed afterwards.
This only works by enabling this option on both sender and receiver ends. This wouldn’t improve the performance of existing connection since the tcp handshark was finished before. We need to restart the tcp connection to utilize this.
Window Scaling only works if both sides include it as an option during the initial 3-way handshake (even if their multipliers are different). The protocol recommends using the option even if the shift-count is 0 (meaning 2^0, which would multiply the window size by 1). That way, if one side doesn’t plan on using scaling, it doesn’t prevent the other side from taking advantage of the increased buffer space.
Example of tcp window scaling
The scp speed between our two US datacenters was about 1-2MB/s. From the network packets, it turns out that this option was not enabled on one server. We can get more info about how to use tcpdump to capture packets from here.
After tcp window scale is enabled, the scp speed reaches 40MB/s. This is a huge improvement. This post from Google also shares the same info.
Tcp window size in Wireshark
* Window size is the current size of the window in bytes.
* Scaling factor is a multiplier sent back along with the acknowledgment by the receiver that indicates to the sender that a new window size is requested.
* Calculated window size is the new window size that has been requested. This is determined like so: Window Size * Scaling factor = Calculated window size.
So, we would see on our wireshark output something like this:
window size value:593
{Calculated window size: 151808}
{Window size scaling factor: 256}
We can confirm the above by doing the math: 593*256 = 151808
Related post:
- Troubleshoot Network Problems In Linux
- Linux Performance: TCP active/passive/failed connection openings
Wireshark is a popular network protocol analyzer that helps in monitoring and analyzing network traffic. One of the important aspects of analyzing network communication is understanding the concept of window size value.
The window size value in Wireshark refers to a parameter found in the Transmission Control Protocol (TCP) header. TCP is a reliable transport protocol that ensures the ordered and error-free delivery of data packets over a network.
In TCP, during a connection establishment phase known as the TCP handshake, the two communicating devices negotiate certain parameters, including the window size value. This negotiation determines the maximum amount of data that can be sent before receiving an acknowledgment from the other end.
When a device sends data, it includes a window size value in the TCP header to specify the number of bytes it can receive and buffer at any given time. It indicates the amount of unacknowledged data a device can transmit before waiting for a response.
In Wireshark, the window size value can be observed and analyzed for each TCP packet within a captured network trace. By examining this value, network administrators and analysts can gain insights into the performance characteristics and efficiency of TCP connections.
Frequently Asked Questions (FAQs)
1. How is the window size value represented in Wireshark?
The window size value is represented as a decimal number in the TCP header section of each captured packet within Wireshark.
2. Why is the window size value important in Wireshark?
The window size value helps determine the amount of data that can be transmitted without waiting for an acknowledgment, thereby affecting the overall efficiency and throughput of the TCP connection.
3. Is the window size value fixed for a TCP connection?
No, the window size value can change dynamically during a TCP connection based on several factors such as network conditions and the flow control mechanism.
4. What does a small window size value indicate?
A small window size value suggests that the receiver has a limited buffer capacity and can handle only a small amount of unacknowledged data at a time.
5. What does a large window size value indicate?
A large window size value indicates that the receiver has a larger buffer capacity and can handle a significant amount of unacknowledged data before waiting for acknowledgment.
6. Can the window size value ever be zero?
Yes, in certain scenarios, the window size value can be set to zero, indicating that the device is currently unable to receive any data.
7. How does the window size value affect data transfer speed?
A larger window size allows more data to be sent before waiting for acknowledgment, potentially increasing the overall data transfer speed.
8. Is the window size value the same for both the sender and receiver?
No, the window size value can be different for the sender and receiver, depending on their respective buffer capacities.
9. Can the window size value be modified during a TCP connection?
Yes, the window size value can be modified during a TCP connection using a mechanism called window scaling, which allows for efficient bandwidth utilization.
10. How can the window size value be optimized for better network performance?
Optimizing the window size value involves considering several factors such as network latency, bandwidth, and the characteristics of the application. Fine-tuning these parameters can help achieve better network performance.
11. Can Wireshark automatically analyze the window size value for network traces?
Wireshark provides various analysis features and statistics that can help in understanding the behavior and trends related to window size values within network traces.
12. Are there any limitations to solely relying on window size value analysis?
While window size value analysis provides valuable insights, it should be complemented with other network metrics and analysis techniques for a comprehensive understanding of network performance.
In conclusion, the window size value in Wireshark is a crucial parameter within the TCP header that determines the amount of data that can be transmitted without waiting for acknowledgment. By analyzing this value, network administrators and analysts can gain insights into the performance and efficiency of TCP connections, leading to better network management and optimization.
Dive into the world of luxury with this video!
Your friends have asked us these questions — Check out the answers!
