Если в вашей организации несколько системных администраторов, у вас периодически может возникать вопрос “Кто перезагрузил сервер?”. В этой статье я покажу как найти определения пользователя, который перезагрузил или выключил компьютер/сервер Windows.
Информация об учетной записи, которая отправила команду перезагрузки Windows сохраняется в журнал событий.
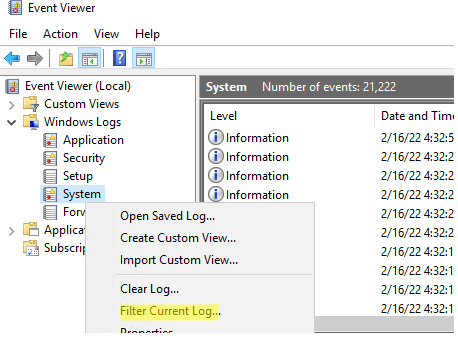
- Откройте консоль Event Viewer (
eventvwr.msc
) и перейдите в раздел Windows Logs -> System; - Включите фильтр журнала событий, выбрав в контекстном меню пункт Filter Current Log;
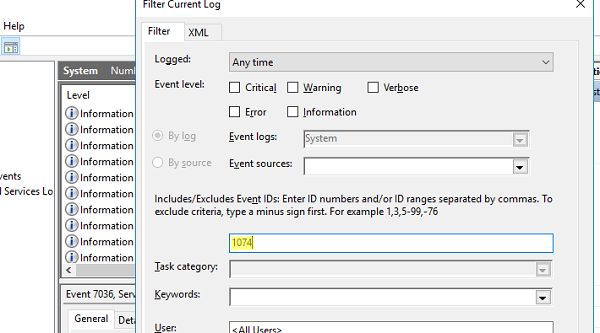
- В поле фильтра укажите EventID 1074 и нажмите OK;
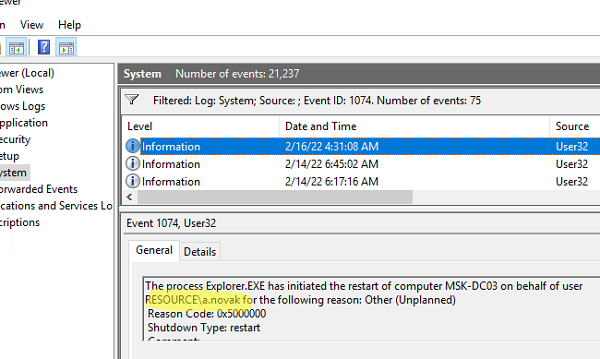
- В журнале событий останутся только события выключения (перезагрузки), откройте любое из них;
- В событии от источника User32 будет указан пользователь, который инициировал перезагрузку Windows. В этом примере это пользователь a.novak.
The process C:\Windows\Explorer.EXE (MSK-DC03) has initiated the restart of computer MSK-DC03 on behalf of user WINITPRO\a.novak for the following reason: Other (Unplanned) Reason Code: 0x5000000 Shutdown Type: restart Comment:
Рассмотрим еще несколько примеров событий перезагрузки/выключения Windows. В качестве пользователя, запустившего перезагрузку операционную систему может быть указан NT AUTHORITY\SYSTEM.
Это означает, что перезагрузку инициировала одна из служб или программ Windows, запущенная от имени SYSTEM.. Например, это может быть процесс службы
wuauserv
, который закончил установку обновлений Windows и выполнил перезагрузку согласно настроенной политике Windows Update или с помощью задания модуля PSWindowsUpdate.
The process C:\Windows\uus\AMD64\MoUsoCoreWorker.exe (WKS-PC11S22) has initiated the restart of computer WKS-PC11S22 on behalf of user NT AUTHORITY\SYSTEM for the following reason: Operating System: Service pack (Planned) Reason Code: 0x80020010 Shutdown Type: restart Comment:
Если ваша Windows запущена внутри виртуальной машины VMware, то если выполнить Restart Guest из консоли управления VMware, событие (выключения) будет выглядеть так:
The process C:\Program Files\VMware\VMware Tools\vmtoolsd.exe (MSK-DC03) has initiated the shutdown of computer MSK-DC03 on behalf of user NT AUTHORITY\SYSTEM for the following reason: Legacy API shutdown Reason Code: 0x80070000 Shutdown Type: shutdown
В этом случае выключение Windows также инициировано NT AUTHORITY\SYSTEM, т.к. службы интеграции VMware Tools запущены от имени системы.
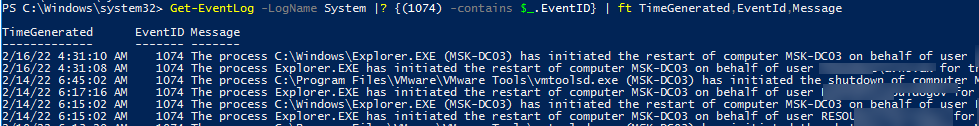
Вы можете получить информацию о событиях перезагрузки с помощью PowerShell. Следующая команда выберет все события с EventID 1074:
Get-WinEvent -FilterHashtable @{logname=’System’;id=1074}|ft TimeCreated,Id,Message
Команда вернула описания всех событий перезагрузки и выключения Windows.
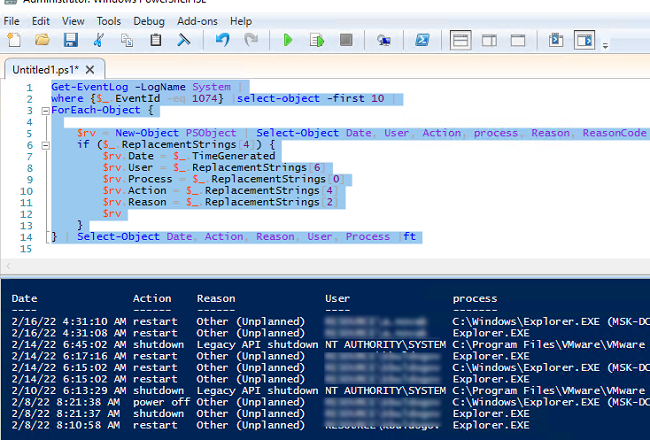
Можно использовать следующий скрипт PowerShell, который возвращает более короткий список с последними десятью событиями с именами пользователей, и процессами, которые инициировали перезагрузку/выключение сервера.
Get-EventLog -LogName System |
where {$_.EventId -eq 1074} |select-object -first 10 |
ForEach-Object {
$rv = New-Object PSObject | Select-Object Date, User, Action, process, Reason, ReasonCode
if ($_.ReplacementStrings[4]) {
$rv.Date = $_.TimeGenerated
$rv.User = $_.ReplacementStrings[6]
$rv.Process = $_.ReplacementStrings[0]
$rv.Action = $_.ReplacementStrings[4]
$rv.Reason = $_.ReplacementStrings[2]
$rv
}
} | Select-Object Date, Action, Reason, User, Process |ft
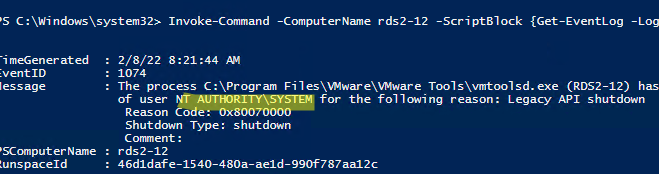
Также с помощью PowerShell можно быстро получить имя пользователя, который перезагрузил удаленный компьютер. Получить доступ к журналу событий на удаленном хосте можно с помощью формата Get-EventLog -ComputerName или вы можете подключиться к компьютеру через PSRemoting с помощью командлета Invoke-Command:
Invoke-Command -ComputerName rds2-12 -ScriptBlock {Get-WinEvent -FilterHashtable @{logname=’System’;id=1074} |select-object TimeCreated,Id,Message -first 1}
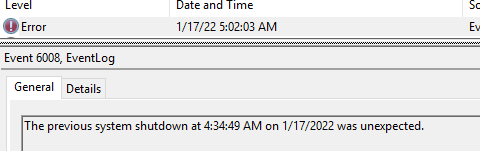
По событию 1074 можно найти только причины корректных (штатных) перезагрузок сервера. Если Windows была перезагружена не штатно (например, при потере электропитания, или появления BSOD), тогда нужно искать события с EventID 6008.
The previous system shutdown at 4:34:49 AM on 1/17/2022 was unexpected.
И конечно, вы не сможете понять, кто перезагрузил Windows, если журналы событий были очищены, или старые события перезатерты более новыми (в домене желательно настроить увеличенный размер журналов событий с помощью GPO).
While troubleshooting an issue that causes an unexpected reboot or shutdown of a Windows machine, it is important to know which event IDs are related to system reboot/shutdown and how to find the appropriate logs.
In this note i am publishing all the event IDs related to reboots/shutdowns.
I am also showing how to display the shutdown events with date and time, using a Windows Event Viewer or from the command-line using a PowerShell.
Cool Tip: How to boot Windows in Safe Mode! Read more →
The list of the Windows event IDs, related to the system shutdown/reboot:
| Event ID | Description |
|---|---|
| 41 | The system has rebooted without cleanly shutting down first. |
| 1074 | The system has been shutdown properly by a user or process. |
| 1076 | Follows after Event ID 6008 and means that the first user with shutdown privileges logged on to the server after an unexpected restart or shutdown and specified the cause. |
| 6005 | The Event Log service was started. Indicates the system startup. |
| 6006 | The Event Log service was stopped. Indicates the proper system shutdown. |
| 6008 | The previous system shutdown was unexpected. |
| 6009 | The operating system version detected at the system startup. |
| 6013 | The system uptime in seconds. |
Display Shutdown Logs in Event Viewer
The shutdown events with date and time can be shown using the Windows Event Viewer.
Start the Event Viewer and search for events related to the system shutdowns:
- Press the ⊞ Win keybutton, search for the
eventvwrand start theEvent Viewer - Expand
Windows Logson the left panel and go toSystem - Right-click on
Systemand selectFilter Current Log... - Type the following IDs in the
<All Event IDs>field and clickOK:41,1074,1076,6005,6006,6008,6009,6013
Cool Tip: Get history of previously executed commands in PowerShell! Read more →
Find Shutdown Logs using PowerShell
The shutdown/reboot logs in Windows can also be retrieved from the command-line using the PowerShell’s Get-EventLog command.
For example, to filter the 10000 most recent entries in the System Event Log and display only events related to the Windows shutdowns, run:
PS C:\> Get-EventLog System -Newest 10000 | `
Where EventId -in 41,1074,1076,6005,6006,6008,6009,6013 | `
Format-Table TimeGenerated,EventId,UserName,Message -AutoSize -wrap
Cool Tip: Start/Stop a service in Windows from the CMD & PowerShell! Read more →
Was it useful? Share this post with the world!
Web Hosting Knowledge Base
PostedOctober 15, 2024
UpdatedNovember 25, 2024
Views436
Being a Windows server administrator, you may require to regularly check and review your Windows server reboot and shutdown logs. In this article, we will discuss about how to check reboot and shutdown logs in Windows server. In Windows server, all such information are stored in Windows Event log. We can view all theses event logs using Windows Event Viewer. Windows Event Viewer contains reboot Event ID, shutdown Event ID, Windows server crash Event ID or unexpected server reboot Event ID.
Windows VPS Hosting
1 GB RAM
1 vCPU
40 GB SSD Storage
1 IP address
Price: $6.99 / Month
Read More
Managed Windows VPS
4 GB RAM
4 vCPU
100 GB SSD Storage
1 IP Address
Price: $65 / Month
Read More
Hyper-V Windows VPS
2 GB RAM
1 vCPU
30 GB SSD Storage
1 IP address
Price: $10 / Month
Read More
What is Windows Event Viewer?
Windows server logs all important logs and events in Event log. This allows the administrators to review and analyze the events related to any service. We can view all event logs using Windows Event Viewer. You can access it by following the below steps on your server
- Press Windows Key + R start “Run”.
- In dialog box, type eventvwr as shown in the following image:
- Click “Ok” button to open Windows Event Viewer.
Checking Reboot & Shutdown Logs in Windows Server Through Event Viewer
Windows Event log service assigns Event ID to each different event. This helps to filter the service or event specific logs. Following are the important Event IDs which are associated with Windows server reboot and shutdown:
- Event ID 41: This event indicates that your Windows system has rebooted without cleanly shutting down first.
- Event ID 1074: This event is written when an application causes the system to reboot, or when the user initiates a reboot or shutdown by clicking Start or pressing CTRL+ALT+DELETE, and then clicking Shut Down.
- Event ID 6005: The event is logged at boot time noting that the Event Log service was started.
- Event ID 6006: The event is logged at boot time noting that the Event Log service was stopped.
- Event ID 6008: This event gets logged to the system event log when a system shuts down unexpectedly. you will see the message “The previous system shutdown at time on date was unexpected.”
To check the Reboot Logs:
1. Open Windows Event Viewer as shown above.
2. Go to Event Viewer (Local) >> Expand Windows Logs folder >> Go to System as shown below:
3. From Right side Action pane, click on “Filter Current Log…” to filter the event IDs.
4. Filter the event IDs 41, 1074 to check if the system was rebooted unexpectedly or by user/application.

Event IDs 41 and 1074 are associated with server reboot event ID.
To check the Shutdown Logs:
1. Follow the Steps 1 to 3 from “To check the Reboot Logs“.
2. Filter the logs using event IDs 1074, 6008 as shown below:

Event IDs 1074 and 6008 are associated with server shutdown event ID.
Conclusion
Using the above steps, you can find the event details associated with Windows Server reboot, shutdown or unexpected crash. This helps the server administrator to analyze and troubleshoot the issue.
The Windows Event Viewer is managed by the main event log service. The Event Viewer records the history of server startup and shutdown. It also tracks the actions of each user while the device is in operation. It logs errors, and other messages and warnings that occur on Windows Server.
In this article, we will learn how to check shutdown/reboot logs on Windows 2012, 2016, and 2019 VPS servers.
Let’s look at some of the most common codes related to server startup and shutdown times.
41: indicates that your server rebooted but did not shut down completely.
6005: indicates that the event log service was started.
1074: this event shows when an application forcibly shuts down or reboots your VPS server. This allows you to know when you or someone else restarted or shut down the server from the «Start» menu or via CTRL+ALT+DEL.
6008: this event appears if your computer was shut down or rebooted due to a blue screen of death.
6006: this event shows when the server has properly shut down.
How to view these events in Windows Server?
Press Win + R and enter eventvwr
On the left side of the panel, open «Windows Logs => System«
In the Event ID column, we will see a list of events that occurred during the operation of Windows. The event log can be sorted by event ID.
To sort the events we need, on the right side, select «Filter Current Log«
Now enter the events we need, separated by commas, 41, 1074, 6006, 6008, 6006 and click OK.
Now we can observe the event log with the shutdown of our VPS server.
We can also view the server uptime event log. This corresponds to the identifier 6013.
Viewing the shutdown and restart log using PowerShell
If we need to quickly view the server shutdown/reboot logs, we can use the Get-EventLog command in the PowerShell shell.
To filter the last 1000 entries in the log and display only the events we need, (41, 1074, 6006, 6008, 6006) execute this command in PowerShell:
Get-EventLog System -Newest 1000 | ` Where EventId -in 41,1074,6006,6008 | ` Format-Table TimeGenerated,EventId,UserName,Message -AutoSize -wrapNow you can independently check why your server was rebooted/shut down.
We also suggest you other useful articles:
- How to install updates on Windows Server 2012, Windows Server 2016, and Windows Server 2019
- How to view RDP connection logs in Windows Server 2016, 2019
- Disable UDP for RDP connections to Windows Server
Ever found yourself wondering about an unexpected system reboot, these event IDs are
very useful while one is investigating the cause of unexpected system
shutdown/reboot.
I not sure about others but but always found hard remembering these event IDs so making a note for future reference and believe others will also
find it useful.
Server
reboot/shutdown events:
- Event ID 6005: “The event log
service was started.” This is synonymous to system startup. - Event ID 6006: “The event log
service was stopped.” This is synonymous to system shutdown. - Event ID 6008: «The
previous system shutdown was unexpected.» Records that the system
started after it was not shut down properly.

- Event ID 6009: Indicates the
Windows product name, version, build number, service pack number,
and operating system type detected at boot time. - Event ID 6013: Displays the uptime of the computer. There
is no TechNet page for this id. - Event ID 1074: «The process
X has initiated the restart / shutdown of computer on behalf of user
Y for the following reason: Z.» Indicates that an
application or a user initiated a restart or
shutdown. - Event ID 1076: «The reason
supplied by user X for the last unexpected shutdown of this computer
is: Y.» Records when the first user with shutdown
privileges logs on to the computer after an
unexpected restart or shutdown and supplies a reason for the
occurrence.
Note: In case of unexpected shoutdown due to power failure, there would be no event created.
To know the system boot Time:
C:\systeminfo | find /i “boot time”

That’s
it…