Microsoft’s Windows Server 2008 and 2008 R2 customers still represent a large group, as Microsoft has announced an additional year of Extended Security Updates (ESU) with a caveat. Only available for Microsoft Azure customers, the ESU program will allow Windows Server 2008 and R2 users on Azure cloud to get security updates until January 9, 2024. By no means is this not a free program, and Microsoft will bill this extensively as it is available internationally. Many customers are forced to join the ESU program for their Windows Server 2008 and R2 systems, as upgrading the OS to the latest version is not always possible without significant downtime or a hardware update.
The following customer base has legibility to the fourth year of the ESU program:
- Windows Server 2008 R2 Service Pack 1 (SP1)
- Windows Server 2008 Service Pack 2 (SP2)
- Windows Embedded POSReady 7
- Windows Embedded Standard 7
- All Azure virtual machines (VMs) running Windows Server 2008 R2 and Windows Server 2008 operating systems on Azure, Azure Stack, Azure VMWare Solutions, or Azure Nutanix Solution.
Introduction
Announced by Microsoft back in March 12, on January 14, 2020, Windows 7 and Windows Server 2008/2008 R2 has gone out of support. One must install Year 2 ESU MAK Key to continue to receive security updates for your Windows 7/Windows Server 2008/2008 R2.
If you have not yet updated to a modern operating system and still want security patches, you will need to sign up for these through the Extended Security Updates (ESUs) program. This blog will not provide you the ESU MAK Key.
In this blog post, I cover the prerequisite and how to deploy and activate Year 2 ESU license for your Windows 7/Windows Server 2008/2008 R2 on both internet connected computers and air-gaped computers. Note, the assumption is you already obtained and purchased the Year 2 ESU MAK Key. Important note, if you haven’t purchased Year 1 ESU, you must do so before being able to purchase Year 2 ESU.
Prerequisite For Deploying ESU
Prerequisite for Year 2 ESU is similar to Year 1 ESU which can be found here. As long as your clients are kept up to date with security patches you will should not have any issues installing Year 2 ESU.
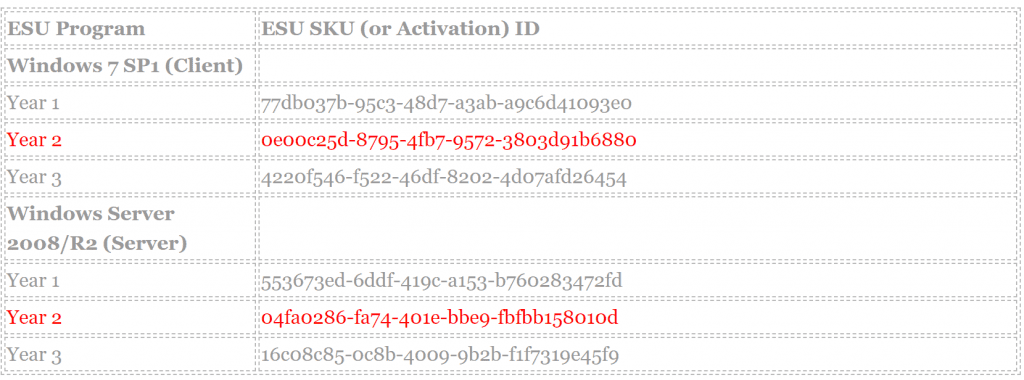
The Windows 7 ESU Activation ID
The Activation IDs are provided by Microsoft and can be here. For Year 2 ESU we will be using the following Activation ID in red below depending on your clients.
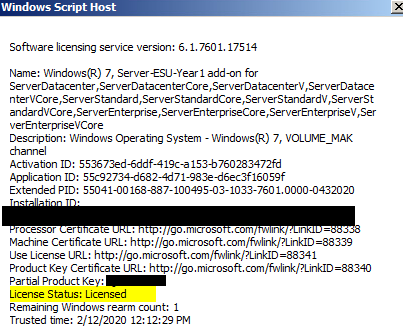
How To Install And Activate The Windows 7 Extended Security Update Year 2 MAK Key On Internet Connected Computers
After you have purchased Year 2 ESUs, you will receive a MAK key. This MAK is unique to your organization, but not unique for each devices, which means you will use the same MAK key to activate all of your devices.
Please note that the Year 2 ESU MAK Key can be installed with the existing Year 1 ESU MAK key. You do not need to remove Year 1 ESU MAK key.
Execute the following commands in a Elevated Command Prompt:
cscript c:\windows\system32\slmgr.vbs /ipk <MAK Key>cscript slmgr.vbs /dlv*Note, take note of the Activation ID which should also be listed in the above chart.cscript c:\windows\system32\slmgr.vbs /ato <Activation ID>slmgr.vbs /dlihit enter (You should now see ESU status is Licensed)
(Note, image is from Year 1 ESU)
How To Install And Activate The Windows 7 Extended Security Update Year 2 MAK Key On Air-Gapped Computers
Execute the following commands in a Elevated Command Prompt:
slmgr.vbs /ipk <MAK Key>cscript slmgr.vbs /dlv*Note, take note of the Activation and Installation ID (Do not close this command prompt window)- Call MS: 1-888-725-1047 and provide the Installation ID. MS will provide you with the Confirmation ID: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx, write it down
slmgr.vbs /atp <ConfirmationID> space <ActivationID>slmgr.vbs /dlihit enter (You should now see ESU status is Licensed)
(Note, image is from Year 1 ESU)
Conclusion
It is important to ensure your organization has a strategy in place for Windows 7 and Server 2008/2008 R2 upgrade. In the meantime its highly recommended you obtain a ESU license to ensure your operating system is kept protected. Is your organization purchasing ESUs license? How are you handling the Windows 7/Server 2008 and or Server 2008 R2 end of support? Please leave a comment below!
Hello World,
By now, you should be fully aware that Windows 7, Windows 2008 SP2 and Windows 2008 R2 and SQL server 2008 R2 products have reached end of extended support. Officially, these products have reached end of support since January 14, 2020. This means that no more free updates and patches will be made available for these operating systems and products. Microsoft provided enough time and early notifications to bring awareness about discontinuation of these products. However, it seems that there is still a large number of organizations running these legacy operating systems.
This situation has “obliged” Microsoft to come up with an new program support for organizations willing to pay for the extra support. The Extended Security Updates (ESU) program will ensure that entitled customers (i.e. paying for the support) will still receive critical and important security updates for these legacy products. The ESU program will run for a maximum of three years and no more support will be available after 2023. More specifically, organizations will need to subscribe or renew to the ESU Program every year if support is needed. The price will increment through the years.
Since February 2020, we have seen an increase of requests in either implementing the Extended Security Update (ESU) Program or performing really quickly migration activities to newer products still supported by Microsoft. Our recommendation would be to migrate to newer products so no need to maintain and pay for legacy operating system. However, in some really specific cases, a quick migration is not possible (specific applications that needs to be rewritten).
This post will provide some (technical) information about the ESU and what you would need to do if you need to obtain this extra support for your organization. This post will not explain how to obtain the ESU Key nor the pricing model used. This post will quickly go through what needs to be done in order to prepare your environment and make it ready to receive these Extended Security Updates
So, let’s move forward !
Overview
The ESU program is really the last resort option available to organization willing to pay for extra support on legacy operating system such as Windows 7, Windows 2008, Windows 2008 R2 and SQL 2008 R2 products. After identifying the numbers of ESU licenses you would need for your Windows 7 and Windows 2008/R2 running machines, you can purchase for 12-month period time your Extended Security Updates program. In practice, this means that you will receive a MAK ESU licensing key. This key will be unique to your organization. However, the same key will be used to activate all devices that needs to receive the extended support.
This MAK ESU license key will not be recognized by the legacy operating system if you do not prepare your infrastructure. A series of specific Windows updates needs to be deployed and installed on machines running these legacy products. After installing these updates, you will basically need to distribute and activate the (ESU) MAK key. When activated and when Microsoft would release hot fixes and patches, the supported machine will be able to download and install the patches through the same patching process you are currently using (i.e. WSUS or SCCM or any other third party solution)
To deploy and activate the ESU MAK key through your network, Microsoft is recommending to use the VAMT tool or also known as Volume Activation Management Tool. Volume Activation Management Tool (VAMT) offers a centralized tool and GUI interface that can simplify and automate the ESU Key deployment process through the network. VAMT Tool does not seems to be widely used by sysadmins and few people know about this tool. VAMT Tool can be used in combination with the KMS server and provide an easy way to track licensing usage through your organization. The VAMT tool is totally free. To obtain it, you will need to first download the latest version of ADK Windows 10 1903. You can download the ADK Windows 10 1903 at this location
Note :
Other options might be used to deploy and activate ESU MAK Key (like manual activation, scripted install, third party tool) and if time permit we might want to investigate these options later on.
Preparing the infrastructure
Obtain and Deploy ESU Updates for Windows 7, Windows 2008/R2
The following link provide the latest information about which updates are needed to support ESU Support (please check this, https://support.microsoft.com/en-us/help/4522133/procedure-to-continue-receiving-security-updates).
Before being able to benefit from ESU program, your organization will need to obtain the required updates and installed them accordingly. Based on your infrastructure, you will be able to deploy these additional and required patches through WSUS, SCCM or any other patch management solution you are currently using. You will have to approve these patches and deploy them to targeted computers running Windows 2008R2 or Windows 7.
Download and install the following Windows updates on target computers in the specified order
- KB4474419 (SHA2-Update)
- KB4490628 (Service Update Stacks)
- KB4536952 (Service Update Stacks)
Then download and install the Extended Updates Security (ESU) Licensing Preparation package which is
- KB4538483 (for Windows 2008R2 and Windows 7 SP1)
Note:
If you are running Windows 2008 SP1, we recommend to upgrade to Windows 2008 R2 or later if possible.
If this is not an option, you can still benefit from ESU program if you install the following Windows Updates
KB4474419 (SHA2-Update)
KB4490628 (Service Update Stacks)
KB4536952 (Service Update Stacks)
KB4538484 (Licensing preparation tool for Windows 2008 SP2)
After installing these patches, target computers will need to be restarted!!! So, you might need to plan the deployment of these patches. To deploy these patches, you can use manual approach or use some scripts or use your standard patch management infrastructure (WSUS,SCCM,…)
Download the VAMT Tool
When your windows 7 SP1, Windows 2008 SP2 and Windows 2008R2 have received the needed patches mentioned above, we are ready to deploy and activate the MAK ESU key. Microsoft recommends to use the Volume Activation Management tool (VAMT) which is part of the ADK (Automated Deployment Kit). This tool has been around for some time but was not really extensively used by sysadmins.
Volume Activation Management Tool (VAMT) offers a centralized tool and GUI interface that can simplify and automate the ESU Key deployment process through the network. The VAMT tool is totally free. To obtain it, you will need to first download the latest version of ADK Windows 10 1903 (at this location).
Click on Picture for Better Resolution
Based on your infrastructure and your internet connectivity, you can decide to install directly the VAMT Tool on the target machine or you can decide to download the ADK Offline sources files and perform the installation even if you do not have internet connectivity.
Click on Picture for Better Resolution
When you have the access to the VAMT source files, you will need to perform the installation. VAMT needs to connect to a SQL database which can be locally hosted (i.e. SQL Express) or can be located on a Centralized database infrastructure that might be available on your network.
Click on Picture for Better Resolution
When your VAMT server is installed and operational, you will need to create queries to identify your Windows 7 and Windows 2008/R2 computers and you will be ready to deploy the ESU Key through your network.
Click on Picture for Better Resolution
Note : In a coming post, we will describe how to perform the VAMT installation and configuration…..
ESU Key Activation – Online or Proxy Activation
ESU Key Activation process has also been a little bit confusing for people (based on our experience and feedback received). Usually, organizations are not directly connected to Internet to perform activation. Instead, majority of organizations we are working with are using the KMS (Key Management server) infrastructure which allow “offline” activation through your organization. Initially, a lot of people thought that ESU Key would get activated through KMS Infrastructure. This is a wrong assumptions as ESU are MAK (Multiple Activation Keys) based. This means that computers getting the ESU MAK key would either need to have direct access to internet so activation can be performed directly with Microsoft. This is referred as Online Activation
For organization not connected or not willing to grant direct access to Microsoft Activation services, a Proxy Activation Process exists as well and it’s based on VAMT Tool. The Proxy Activation assume that you have a VAMT installed on the “disconnected” network. Another VAMT infrastructure (or server) is then also needed that needs to be connected to Internet. This VAMT infrastructure on the disconnected network will collect the necessary information needed for activation process. The information can be exported to a file and moved the VAMT that is connected to internet. When Activation process is completed, you can then import back the necessary file into the disconnected network infrastructure which will ensure that your machines will get activated
Final Notes
This conclude the first part of this series about ESU Key, VAMT and activation. We have just provided a quick overview of the process that needs to be used in order to obtain extra support for your Windows 7, Windows 2008/R2 operating systems. Based on the feedback from our customers and colleagues, initially, the ESU process was quite confusing as Microsoft had changed the updates and the information that was needed to benefit from this program.
We would recommend to initiate projects to move away from these legacy Windows 7 and Windows 2008 R2 instead of paying for extra support for legacy operating systems. We understand that some software might not be compatible yet with newer operating systems. For these specific cases, you could decide to benefit from the ESU program but we would also recommend to work on upgrading these legacy software whenever possible
In the next post, we will focus more on how to install the VAMT software.
Till next time
See ya
[German]Support for Windows 7 SP1 and Windows Server 2008 R2 expired on January 14, 2020. However, Microsoft had provided a paid Extended Security Update Support for the two operating systems, which provides updates until January 10, 2023. Now it has been announced that Microsoft is extending this ESU support for Windows Server 2008 R2 for another year.
What is ESU?
After Windows 7 SP1 and Windows Server 2008 R2 reached the end of support on Jan. 14, 2020, there are no more security updates by default. Since then, however, corporate customers have had the option of purchasing an ESU license for Windows 7 SP1 and Windows Server 2008 R2 in order to continue receiving security updates between January 2020 and January 2023 at the latest. To that end, Microsoft has announced Extended Security Updates (ESU) support as a separate program for enterprise customers (see Wow! Windows 7 get extended support until January 2023). ESU licenses are available for the following operating systems:
- Windows 7 SP1
- Windows 7 Professional for Embedded Systems
- Windows Server 2008 R2 SP1 and Windows Server 2008 SP2
- Windows Server 2008 R2 SP1 for Embedded Systems and Windows Server 2008 SP2 for Embedded Systems
The third year of ESU support will start in January 2022. I have a machine running WIndows 7 SP1 Ultimate here with an ESU license for 2020/2021 (I had referred to the ESU package for the second year in the blog post Windows 7 SP1: ESU Support for 2021 – Part 1). For Windows Server 2008 R2, however, the conclusion of a corresponding volume license contribution is required.
Windows Server 2008 R2: ESU support until January 9, 2024
It looks like customers won’t be able to say goodbye to Windows Server 2008 R2 until January 2023. Via Dr. Windows, I became aware of Microsoft’s ESU support extension for Windows Server 2008 R2. In the 2020 Techcommunity post Update: Extended Security Updates for Windows 7 and Windows Server 2008, an addendum from November 5, 2021 states:
Update 2021.11.05: For Windows 7 SP1 and Windows 7 Professional for Embedded Systems, the Extended Security Update (ESU) Program will be entering its third and final year of extended support beginning on February 8, 2022 and ending on January 10, 2023.
For Windows Server 2008 R2 SP1, Windows Server 2008 SP2, Windows Server 2008 R2 SP1 for Embedded Systems and Windows Server 2008 SP2 for Embedded Systems if running on Microsoft Azure, ESU will have one additional year of extended support available beginning on February 14, 2023, ending on January 9, 2024.
Those who have to continue running Windows Server 2008 R2 can buy extended support from Microsoft until January 9, 2024. For Windows 7 SP1 clients, however, updates are supposed to end in January 2023.
Similar article:
Wow! Windows 7 get extended support until January 2023
Windows 7 Extended Security Updates buyable from April 2019
Microsoft offers Windows 7 Extended Update Support to SMBs
Prices for Windows 7 Extended Security Updates till 2023
Windows 7: Free Extended Update Support and usage
Windows 7: Office 365 ProPlus Updates till 2023
Windows 7 Extended Security Updates (ESU) requirements
Windows 7 Extended Security Update (ESU) program available
Windows 7 Extended Security Updates (ESU) program, price and source for SMEs
Windows 7: Buy and manage ESU licenses – Part 1
Windows 7: Preparing for ESU and license activation – Part 2
Windows 7: ESU Activation in Enterprise Environment – Part 3
Windows 7: ESU questions and more answers – Part 4
Windows 7: Forcing February 2020 Security Updates – Part 1
Windows 7: Securing with the 0patch solution – Part 2
Windows 7/Server 2008/R2: 0patch delivers security patches after support ends
Fix: Windows 7 ESU system does not find updates
This entry was posted in Security, Update, Windows and tagged ESU, Update, Windows Server 2008 R2. Bookmark the permalink.
Extended Security Updates (ESU) Licensing Preparation Package for Windows 7 SP1 and Windows Server 2008 R2 SP1
View products that this article applies to.
This update provides an additional set of licensing changes to enable installation of the ESU add-on key. This is one of the steps to prepare for installation of Extended Security Updates. For the full set of steps, please see KB4522133.
If you previously successfully installed and activated your ESU key on your Windows 7 SP1 device, you do not have to re-install or reactivate it after applying this update.
A restart is required after you apply this update and before you install any other updates.
For more information about the ESU program, see the following resources:
- Lifecycle FAQ-Extended Security Updates
- FAQ about Extended Security Updates for Windows 7
Important Before you apply this update, see the Prerequisites section.
↑ Back to the top
Microsoft is currently not aware of any issues with this update.
↑ Back to the top
Method 1: Microsoft Update Catalog
To get the standalone package for this update, go to the Microsoft Update Catalog website.
Method 2: Windows Server Update Services
This update is available through Windows Server Update Services (WSUS).
Prerequisites
You must have the following updates installed before you apply this update. If you use Windows Update, these updates will be offered automatically as needed.
- You must have the SHA-2 update (KB4474419) that is dated September 23, 2019 or a later SHA-2 update installed and then restart your device before you apply this update. If you use Windows Update, the latest SHA-2 update will be offered to you automatically. For more information about SHA-2 updates, see 2019 SHA-2 Code Signing Support requirement for Windows and WSUS.
- You must have the servicing stack update (SSU) (KB4490628) that is dated March 12, 2019 installed. For more information about the latest SSU updates, see ADV990001 | Latest Servicing Stack Updates.
Important You must restart your device after you install these required updates and before you apply any Monthly Rollup, Security-Only Update, Preview of Monthly Rollup, or standalone update.
Restart information
You must restart your device after you apply this update.
↑ Back to the top
File verification
File hash information
| File name | SHA1 hash | SHA256 hash |
|---|---|---|
| Windows6.1-KB4538483-x64.msu | 8A2752D031959315A93922D0A408DFBA39526C16 | 9F997511F4F6400E766B205FF7316D79DB9F9804BDB950AF094178855904B31B |
| Windows6.1-KB4538483-x86.msu | 8B365DFDC2C06C213E076AC7F5879FD6643AE293 | 7CC823F206A60BCEDC423D337EB91EFF382111A52FDD4461D6A647E9C24BDA5A |
File attributes
The English (United States) version of this software update installs files that have the attributes that are listed in the following tables.
For all supported x64-based versions
| File name | File version | File size | Date | Time |
| Sppwinob-spp-plugin-manifest-signed.xrm-ms | Not applicable | 7,298 | 17-Jul-2020 | 04:08 |
| Sppwinob.dll | 6.1.7601.24558 | 418,816 | 17-Jul-2020 | 03:19 |
| Pkeyconfig-embedded.xrm-ms | Not applicable | 28,072 | 18-Mar-2020 | 18:57 |
| Pkeyconfig.xrm-ms | Not applicable | 28,072 | 18-Mar-2020 | 18:57 |
| Pkeyconfig-embedded.xrm-ms | Not applicable | 26,764 | 18-Mar-2020 | 18:57 |
| Security-spp-component-sku-server-fes-esu-year1-ppdlic.xrm-ms | Not applicable | 3,078 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-server-fes-esu-year1-vl-dmak-pl.xrm-ms | Not applicable | 13,531 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-fes-esu-year1-vl-dmak-ul-oob.xrm-ms | Not applicable | 12,378 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-fes-esu-year1-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,900 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-server-fes-esu-year1-ppdlic.xrm-ms | Not applicable | 3,023 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-server-fes-esu-year2-ppdlic.xrm-ms | Not applicable | 3,078 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-server-fes-esu-year2-vl-dmak-pl.xrm-ms | Not applicable | 13,531 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-fes-esu-year2-vl-dmak-ul-oob.xrm-ms | Not applicable | 12,378 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-fes-esu-year2-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,900 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-server-fes-esu-year2-ppdlic.xrm-ms | Not applicable | 3,023 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-server-fes-esu-year3-ppdlic.xrm-ms | Not applicable | 3,078 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-server-fes-esu-year3-vl-dmak-pl.xrm-ms | Not applicable | 13,531 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-fes-esu-year3-vl-dmak-ul-oob.xrm-ms | Not applicable | 12,378 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-fes-esu-year3-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,900 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-server-fes-esu-year3-ppdlic.xrm-ms | Not applicable | 3,023 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-client-esu-year1-ppdlic.xrm-ms | Not applicable | 3,066 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-client-esu-year1-vl-bypass-rac-private.xrm-ms | Not applicable | 5,278 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year1-vl-bypass-rac-public.xrm-ms | Not applicable | 4,116 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year1-vl-bypass-ul-oob.xrm-ms | Not applicable | 12,018 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year1-vl-bypass-ul.xrm-ms | Not applicable | 11,289 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year1-vl-dmak-pl.xrm-ms | Not applicable | 13,406 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year1-vl-dmak-ul-oob.xrm-ms | Not applicable | 12,007 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year1-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,529 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-client-esu-year1-ppdlic.xrm-ms | Not applicable | 3,015 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-client-esu-year2-ppdlic.xrm-ms | Not applicable | 3,066 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-client-esu-year2-vl-bypass-rac-private.xrm-ms | Not applicable | 5,278 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year2-vl-bypass-rac-public.xrm-ms | Not applicable | 4,116 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year2-vl-bypass-ul-oob.xrm-ms | Not applicable | 12,018 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year2-vl-bypass-ul.xrm-ms | Not applicable | 11,289 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year2-vl-dmak-pl.xrm-ms | Not applicable | 13,406 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year2-vl-dmak-ul-oob.xrm-ms | Not applicable | 12,007 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year2-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,529 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-client-esu-year2-ppdlic.xrm-ms | Not applicable | 3,015 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-client-esu-year3-ppdlic.xrm-ms | Not applicable | 3,066 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-client-esu-year3-vl-bypass-rac-private.xrm-ms | Not applicable | 5,278 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year3-vl-bypass-rac-public.xrm-ms | Not applicable | 4,116 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year3-vl-bypass-ul-oob.xrm-ms | Not applicable | 12,018 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year3-vl-bypass-ul.xrm-ms | Not applicable | 11,289 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year3-vl-dmak-pl.xrm-ms | Not applicable | 13,406 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year3-vl-dmak-ul-oob.xrm-ms | Not applicable | 12,007 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-esu-year3-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,529 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-client-esu-year3-ppdlic.xrm-ms | Not applicable | 3,015 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-server-esu-year1-ppdlic.xrm-ms | Not applicable | 3,066 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-server-esu-year1-vl-bypass-rac-private.xrm-ms | Not applicable | 5,278 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year1-vl-bypass-rac-public.xrm-ms | Not applicable | 4,116 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year1-vl-bypass-ul-oob.xrm-ms | Not applicable | 12,381 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year1-vl-bypass-ul.xrm-ms | Not applicable | 11,652 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year1-vl-dmak-pl.xrm-ms | Not applicable | 13,527 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year1-vl-dmak-ul-oob.xrm-ms | Not applicable | 12,370 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year1-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,892 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-server-esu-year1-ppdlic.xrm-ms | Not applicable | 3,015 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-server-esu-year2-ppdlic.xrm-ms | Not applicable | 3,066 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-server-esu-year2-vl-bypass-rac-private.xrm-ms | Not applicable | 5,278 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year2-vl-bypass-rac-public.xrm-ms | Not applicable | 4,116 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year2-vl-bypass-ul-oob.xrm-ms | Not applicable | 12,381 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year2-vl-bypass-ul.xrm-ms | Not applicable | 11,652 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year2-vl-dmak-pl.xrm-ms | Not applicable | 13,527 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year2-vl-dmak-ul-oob.xrm-ms | Not applicable | 12,370 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year2-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,892 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-server-esu-year2-ppdlic.xrm-ms | Not applicable | 3,015 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-server-esu-year3-ppdlic.xrm-ms | Not applicable | 3,066 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-server-esu-year3-vl-bypass-rac-private.xrm-ms | Not applicable | 5,278 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year3-vl-bypass-rac-public.xrm-ms | Not applicable | 4,116 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year3-vl-bypass-ul-oob.xrm-ms | Not applicable | 12,381 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year3-vl-bypass-ul.xrm-ms | Not applicable | 11,652 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year3-vl-dmak-pl.xrm-ms | Not applicable | 13,527 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year3-vl-dmak-ul-oob.xrm-ms | Not applicable | 12,370 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-year3-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,892 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-server-esu-year3-ppdlic.xrm-ms | Not applicable | 3,015 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-client-fes-esu-year1-ppdlic.xrm-ms | Not applicable | 3,078 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-client-fes-esu-year1-vl-dmak-pl.xrm-ms | Not applicable | 13,375 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-fes-esu-year1-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,910 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-fes-esu-year1-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,432 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-client-fes-esu-year1-ppdlic.xrm-ms | Not applicable | 3,023 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-client-fes-esu-year2-ppdlic.xrm-ms | Not applicable | 3,078 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-client-fes-esu-year2-vl-dmak-pl.xrm-ms | Not applicable | 13,375 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-fes-esu-year2-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,910 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-fes-esu-year2-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,432 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-client-fes-esu-year2-ppdlic.xrm-ms | Not applicable | 3,023 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-client-fes-esu-year3-ppdlic.xrm-ms | Not applicable | 3,078 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-client-fes-esu-year3-vl-dmak-pl.xrm-ms | Not applicable | 13,375 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-fes-esu-year3-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,910 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-client-fes-esu-year3-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,432 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-client-fes-esu-year3-ppdlic.xrm-ms | Not applicable | 3,023 | 17-Jul-2020 | 04:05 |
| Pkeyconfig.xrm-ms | Not applicable | 1,076,484 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-pos-esu-year1-ppdlic.xrm-ms | Not applicable | 3,057 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-pos-esu-year1-vl-dmak-pl.xrm-ms | Not applicable | 13,307 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-pos-esu-year1-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,713 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-pos-esu-year1-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,235 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-pos-esu-year1-ppdlic.xrm-ms | Not applicable | 3,009 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-pos-esu-year2-ppdlic.xrm-ms | Not applicable | 3,057 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-pos-esu-year2-vl-dmak-pl.xrm-ms | Not applicable | 13,307 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-pos-esu-year2-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,713 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-pos-esu-year2-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,235 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-pos-esu-year2-ppdlic.xrm-ms | Not applicable | 3,009 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-pos-esu-year3-ppdlic.xrm-ms | Not applicable | 3,057 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-pos-esu-year3-vl-dmak-pl.xrm-ms | Not applicable | 13,307 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-pos-esu-year3-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,713 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-pos-esu-year3-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,235 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-pos-esu-year3-ppdlic.xrm-ms | Not applicable | 3,009 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-server-esu-pa-ppdlic.xrm-ms | Not applicable | 3,057 | 17-Jul-2020 | 04:04 |
| Security-spp-component-sku-server-esu-pa-vl-bypass-rac-private.xrm-ms | Not applicable | 5,278 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-pa-vl-bypass-rac-public.xrm-ms | Not applicable | 4,116 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-pa-vl-bypass-ul-oob.xrm-ms | Not applicable | 12,375 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-pa-vl-bypass-ul.xrm-ms | Not applicable | 11,646 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-pa-vl-dmak-pl.xrm-ms | Not applicable | 13,524 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-pa-vl-dmak-ul-oob.xrm-ms | Not applicable | 12,364 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-server-esu-pa-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,886 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-server-esu-pa-ppdlic.xrm-ms | Not applicable | 3,009 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-wes-esu-year1-ppdlic.xrm-ms | Not applicable | 3,057 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-wes-esu-year1-vl-dmak-pl.xrm-ms | Not applicable | 13,307 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-wes-esu-year1-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,713 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-wes-esu-year1-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,235 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-wes-esu-year1-ppdlic.xrm-ms | Not applicable | 3,009 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-wes-esu-year2-ppdlic.xrm-ms | Not applicable | 3,057 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-wes-esu-year2-vl-dmak-pl.xrm-ms | Not applicable | 13,307 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-wes-esu-year2-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,713 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-wes-esu-year2-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,235 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-wes-esu-year2-ppdlic.xrm-ms | Not applicable | 3,009 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-wes-esu-year3-ppdlic.xrm-ms | Not applicable | 3,057 | 17-Jul-2020 | 04:05 |
| Security-spp-component-sku-wes-esu-year3-vl-dmak-pl.xrm-ms | Not applicable | 13,307 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-wes-esu-year3-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,713 | 17-Jul-2020 | 04:08 |
| Security-spp-component-sku-wes-esu-year3-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,235 | 17-Jul-2020 | 04:08 |
| Slc-component-sku-wes-esu-year3-ppdlic.xrm-ms | Not applicable | 3,009 | 17-Jul-2020 | 04:05 |
| Sppobjs-spp-plugin-manifest-signed.xrm-ms | Not applicable | 11,758 | 17-Jul-2020 | 04:08 |
| Sppobjs.dll | 6.1.7601.24558 | 1,098,752 | 17-Jul-2020 | 03:19 |
| Security-spp-ppdlic.xrm-ms | Not applicable | 3,787 | 17-Jul-2020 | 04:05 |
| Sppsvc.exe | 6.1.7601.24558 | 4,425,728 | 17-Jul-2020 | 03:11 |
| Pkeyconfig.xrm-ms | Not applicable | 1,076,484 | 17-Jul-2020 | 03:40 |
For all supported x86-based versions
| File name | File version | File size | Date | Time |
| Sppwinob-spp-plugin-manifest-signed.xrm-ms | Not applicable | 7,298 | 17-Jul-2020 | 03:44 |
| Sppwinob.dll | 6.1.7601.24558 | 412,672 | 17-Jul-2020 | 03:17 |
| Pkeyconfig-embedded.xrm-ms | Not applicable | 28,072 | 25-Oct-2019 | 10:00 |
| Pkeyconfig.xrm-ms | Not applicable | 28,072 | 25-Oct-2019 | 10:00 |
| Pkeyconfig-embedded.xrm-ms | Not applicable | 26,764 | 25-Oct-2019 | 10:00 |
| Security-spp-component-sku-client-esu-year1-ppdlic.xrm-ms | Not applicable | 3,066 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-client-esu-year1-vl-bypass-rac-private.xrm-ms | Not applicable | 5,278 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year1-vl-bypass-rac-public.xrm-ms | Not applicable | 4,116 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year1-vl-bypass-ul-oob.xrm-ms | Not applicable | 12,018 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year1-vl-bypass-ul.xrm-ms | Not applicable | 11,289 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year1-vl-dmak-pl.xrm-ms | Not applicable | 13,406 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year1-vl-dmak-ul-oob.xrm-ms | Not applicable | 12,007 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year1-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,529 | 17-Jul-2020 | 03:43 |
| Slc-component-sku-client-esu-year1-ppdlic.xrm-ms | Not applicable | 3,015 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-client-esu-year2-ppdlic.xrm-ms | Not applicable | 3,066 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-client-esu-year2-vl-bypass-rac-private.xrm-ms | Not applicable | 5,278 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year2-vl-bypass-rac-public.xrm-ms | Not applicable | 4,116 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year2-vl-bypass-ul-oob.xrm-ms | Not applicable | 12,018 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year2-vl-bypass-ul.xrm-ms | Not applicable | 11,289 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year2-vl-dmak-pl.xrm-ms | Not applicable | 13,406 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year2-vl-dmak-ul-oob.xrm-ms | Not applicable | 12,007 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year2-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,529 | 17-Jul-2020 | 03:43 |
| Slc-component-sku-client-esu-year2-ppdlic.xrm-ms | Not applicable | 3,015 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-client-esu-year3-ppdlic.xrm-ms | Not applicable | 3,066 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-client-esu-year3-vl-bypass-rac-private.xrm-ms | Not applicable | 5,278 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year3-vl-bypass-rac-public.xrm-ms | Not applicable | 4,116 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year3-vl-bypass-ul-oob.xrm-ms | Not applicable | 12,018 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year3-vl-bypass-ul.xrm-ms | Not applicable | 11,289 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year3-vl-dmak-pl.xrm-ms | Not applicable | 13,406 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year3-vl-dmak-ul-oob.xrm-ms | Not applicable | 12,007 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-esu-year3-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,529 | 17-Jul-2020 | 03:43 |
| Slc-component-sku-client-esu-year3-ppdlic.xrm-ms | Not applicable | 3,015 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-client-fes-esu-year1-ppdlic.xrm-ms | Not applicable | 3,078 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-client-fes-esu-year1-vl-dmak-pl.xrm-ms | Not applicable | 13,375 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-fes-esu-year1-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,910 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-fes-esu-year1-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,432 | 17-Jul-2020 | 03:43 |
| Slc-component-sku-client-fes-esu-year1-ppdlic.xrm-ms | Not applicable | 3,023 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-client-fes-esu-year2-ppdlic.xrm-ms | Not applicable | 3,078 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-client-fes-esu-year2-vl-dmak-pl.xrm-ms | Not applicable | 13,375 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-fes-esu-year2-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,910 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-fes-esu-year2-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,432 | 17-Jul-2020 | 03:43 |
| Slc-component-sku-client-fes-esu-year2-ppdlic.xrm-ms | Not applicable | 3,023 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-client-fes-esu-year3-ppdlic.xrm-ms | Not applicable | 3,078 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-client-fes-esu-year3-vl-dmak-pl.xrm-ms | Not applicable | 13,375 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-fes-esu-year3-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,910 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-client-fes-esu-year3-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,432 | 17-Jul-2020 | 03:43 |
| Slc-component-sku-client-fes-esu-year3-ppdlic.xrm-ms | Not applicable | 3,023 | 17-Jul-2020 | 03:40 |
| Pkeyconfig.xrm-ms | Not applicable | 1,076,484 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-pos-esu-year1-ppdlic.xrm-ms | Not applicable | 3,057 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-pos-esu-year1-vl-dmak-pl.xrm-ms | Not applicable | 13,307 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-pos-esu-year1-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,713 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-pos-esu-year1-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,235 | 17-Jul-2020 | 03:43 |
| Slc-component-sku-pos-esu-year1-ppdlic.xrm-ms | Not applicable | 3,009 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-pos-esu-year2-ppdlic.xrm-ms | Not applicable | 3,057 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-pos-esu-year2-vl-dmak-pl.xrm-ms | Not applicable | 13,307 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-pos-esu-year2-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,713 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-pos-esu-year2-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,235 | 17-Jul-2020 | 03:43 |
| Slc-component-sku-pos-esu-year2-ppdlic.xrm-ms | Not applicable | 3,009 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-pos-esu-year3-ppdlic.xrm-ms | Not applicable | 3,057 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-pos-esu-year3-vl-dmak-pl.xrm-ms | Not applicable | 13,307 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-pos-esu-year3-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,713 | 17-Jul-2020 | 03:43 |
| Security-spp-component-sku-pos-esu-year3-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,235 | 17-Jul-2020 | 03:43 |
| Slc-component-sku-pos-esu-year3-ppdlic.xrm-ms | Not applicable | 3,009 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-wes-esu-year1-ppdlic.xrm-ms | Not applicable | 3,057 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-wes-esu-year1-vl-dmak-pl.xrm-ms | Not applicable | 13,307 | 17-Jul-2020 | 03:44 |
| Security-spp-component-sku-wes-esu-year1-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,713 | 17-Jul-2020 | 03:44 |
| Security-spp-component-sku-wes-esu-year1-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,235 | 17-Jul-2020 | 03:44 |
| Slc-component-sku-wes-esu-year1-ppdlic.xrm-ms | Not applicable | 3,009 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-wes-esu-year2-ppdlic.xrm-ms | Not applicable | 3,057 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-wes-esu-year2-vl-dmak-pl.xrm-ms | Not applicable | 13,307 | 17-Jul-2020 | 03:44 |
| Security-spp-component-sku-wes-esu-year2-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,713 | 17-Jul-2020 | 03:44 |
| Security-spp-component-sku-wes-esu-year2-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,235 | 17-Jul-2020 | 03:44 |
| Slc-component-sku-wes-esu-year2-ppdlic.xrm-ms | Not applicable | 3,009 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-wes-esu-year3-ppdlic.xrm-ms | Not applicable | 3,057 | 17-Jul-2020 | 03:40 |
| Security-spp-component-sku-wes-esu-year3-vl-dmak-pl.xrm-ms | Not applicable | 13,307 | 17-Jul-2020 | 03:44 |
| Security-spp-component-sku-wes-esu-year3-vl-dmak-ul-oob.xrm-ms | Not applicable | 11,713 | 17-Jul-2020 | 03:44 |
| Security-spp-component-sku-wes-esu-year3-vl-dmak-ul-phn.xrm-ms | Not applicable | 16,235 | 17-Jul-2020 | 03:44 |
| Slc-component-sku-wes-esu-year3-ppdlic.xrm-ms | Not applicable | 3,009 | 17-Jul-2020 | 03:40 |
| Sppobjs-spp-plugin-manifest-signed.xrm-ms | Not applicable | 11,758 | 17-Jul-2020 | 03:44 |
| Sppobjs.dll | 6.1.7601.24558 | 986,112 | 17-Jul-2020 | 03:17 |
| Security-spp-ppdlic.xrm-ms | Not applicable | 3,787 | 17-Jul-2020 | 03:40 |
| Sppsvc.exe | 6.1.7601.24558 | 3,917,824 | 17-Jul-2020 | 03:09 |
↑ Back to the top
Keywords: kbprb
↑ Back to the top
