When it comes to Windows security logs, understanding where they are stored is crucial for effective monitoring and analysis. These logs hold valuable information about system events and user activities that can help detect and investigate potential security threats. So, where exactly are these logs located?
Windows security logs are stored in the Event Viewer, which is a built-in Windows tool for managing and viewing system events. Within the Event Viewer, you can access the security logs by navigating to the ‘Windows Logs’ folder and selecting the ‘Security’ option. This folder contains logs detailing security-related events, including logins, logouts, file access, account changes, and more. By examining these logs, security professionals can gain insights into potential security breaches and take appropriate actions to protect their systems.
Windows security logs are stored in the Event Viewer tool. To access the Event Viewer, go to the Start menu and type «Event Viewer» in the search bar. Click on the app to open it. Once open, you can navigate to the «Windows Logs» folder and choose «Security» to view the security logs. The logs are stored in binary format (.evtx) and can provide valuable information for monitoring and troubleshooting security issues on your system.

Understanding the Importance of Windows Security Logs
Windows Security Logs play a critical role in monitoring and managing the security of Windows-based systems. They provide a detailed record of events and activities occurring on a computer or network, allowing administrators and security professionals to detect, investigate, and respond to security incidents. To effectively utilize these logs, it is essential to know where they are stored and how to access them. In this article, we will explore the various locations where Windows Security Logs are stored, enabling you to effectively manage and analyze security events.
1. Event Viewer — The Primary Location
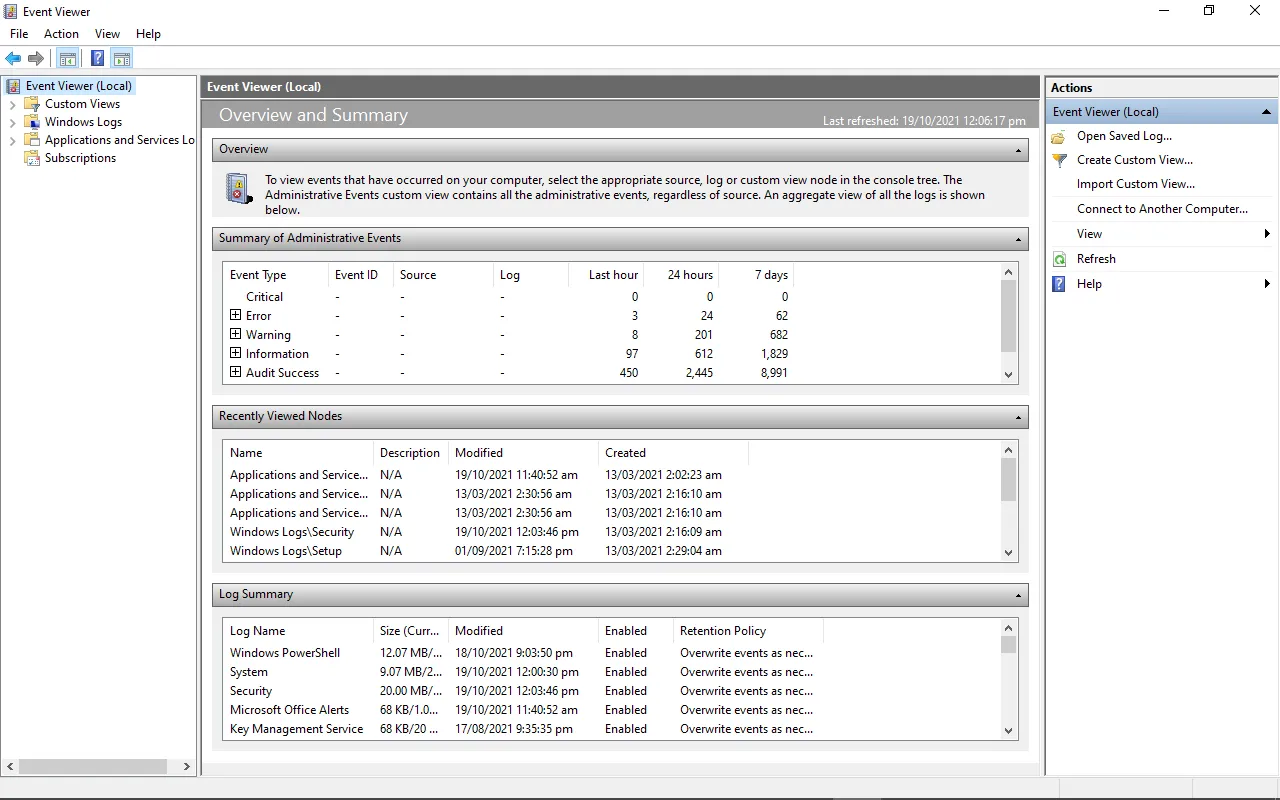
The primary location for storing Windows Security Logs is the Event Viewer, a built-in Microsoft Management Console (MMC) application that provides a centralized view of system logs and events. To access the Event Viewer, open the start menu, type «Event Viewer,» and click on the application. Within the Event Viewer, navigate to the «Windows Logs» folder, where you will find the different log categories, including «Security logs.»
Within the Security logs category, you will find specific event logs, such as «Audit Success» and «Audit Failure.» These logs contain detailed information about security-related events, such as successful or failed login attempts, account lockouts, changes to user accounts, and more. The Event Viewer allows you to view, filter, and export these logs for analysis and troubleshooting purposes.
It is important to note that the Event Viewer stores logs locally on the system where it is accessed. Therefore, if you need to review logs from multiple computers or a centralized location, you’ll need to utilize other methods like remote event log management tools or forward logs to centralized log management solutions.
2. Windows Event Log Files
In addition to the Event Viewer, Windows Security Logs are stored as event log files on the file system. The event log files have the file extension «.evt» and are located in the «C:\Windows\System32\winevt\Logs» directory. Each event log file corresponds to a specific log category, including the Security log.
By default, the Security event log file is named «Security.evtx.» However, there may be additional log files if you have enabled specialized security auditing or have configured custom log settings. These log files are binary files and can’t be easily viewed or analyzed without specialized tools, such as event log parsers or log management solutions.
It is worth noting that the event log files stored on the file system can be adjusted based on your system’s configuration and event log retention policies. Ensure that you have adequate storage space and retention settings in place to retain the necessary log data for compliance, troubleshooting, and forensic purposes.
3. Centralized Log Management Solutions
In enterprise environments or organizations with multiple Windows systems, managing and analyzing security logs across all systems can be a challenging task. To address this, many organizations opt for centralized log management solutions.
Centralized log management solutions collect and store log data from multiple systems in a central repository, making it easier to search, analyze, and correlate events from different sources. These solutions typically utilize agents or collectors installed on individual systems to forward logs to the central repository.
When it comes to Windows Security Logs, centralized log management solutions can collect logs from the Event Viewer, event log files, or other log sources. By forwarding logs to a central repository, organizations can ensure that security events are captured, stored, and monitored in a consistent and efficient manner.
4. Cloud-Based Log Management Services
With the growing popularity of cloud computing, many organizations are migrating their systems and applications to the cloud. In this scenario, it is essential to understand where Windows Security Logs are stored in cloud environments.
Cloud service providers, such as Microsoft Azure or Amazon Web Services (AWS), offer native services for log management and analysis. These services, such as Azure Monitor or AWS CloudWatch, provide centralized log storage, search, and analysis capabilities for cloud-based systems. Windows Security Logs can be collected and stored in these cloud-based log management services, ensuring that log data is readily available for monitoring and investigation purposes.
When deploying systems in cloud environments, it is essential to configure the appropriate logging options and leverage cloud-native log management services to ensure visibility and control over security events.
Exploring Additional Storage Locations for Windows Security Logs
While the Event Viewer, event log files, centralized log management solutions, and cloud-based log management services are the primary locations for storing Windows Security Logs, it is worth mentioning a few additional storage locations for completeness.
1. Windows Performance Monitor
Windows Performance Monitor, also known as PerfMon, is a powerful tool that provides in-depth monitoring and analysis capabilities for various system components. While it is primarily used for performance monitoring, PerfMon also allows you to collect and display security-related events.
PerfMon can be used to create data collector sets that include security-related counters and events. These data collector sets can be configured to write the collected data to log files, which can be stored in a specified location. By utilizing PerfMon, you can collect security events alongside performance data, providing a more comprehensive view of system health and security.
When configuring data collector sets in PerfMon, it is important to ensure that the appropriate security counters and events are selected to capture the desired information for analysis.
2. Third-Party Security Information and Event Management (SIEM) Solutions
Organizations with advanced security requirements often turn to third-party Security Information and Event Management (SIEM) solutions for comprehensive security monitoring and analysis. These solutions integrate with various log sources, including Windows Security Logs, to collect, normalize, and correlate security events.
SIEM solutions typically have their own storage mechanisms, which may include databases or file systems. Administrators can configure these solutions to collect Windows Security Logs and store them in the SIEM solution’s designated storage location.
SIEM solutions provide advanced log analysis, threat intelligence, and reporting capabilities, enabling organizations to effectively monitor and respond to security incidents. They are particularly useful in large-scale environments with complex security requirements.
3. Custom Log Storage Locations
In certain scenarios, organizations may implement custom log storage solutions to meet specific requirements. This could involve deploying a dedicated log server, using network-attached storage (NAS) devices, or leveraging other storage technologies.
When using custom log storage locations, it is important to ensure proper security controls, redundancy, and scalability to handle the volume of log data generated by Windows Security Logs.
Implementing custom log storage solutions can be beneficial for organizations that require fine-grained control over the log data, have stringent compliance requirements, or need to meet the specific needs of their industry or regulatory standards.
Overall, the various storage locations discussed in this article provide flexibility and options for managing and storing Windows Security Logs based on the specific requirements and constraints of each organization.

Windows Security Logs Storage
Windows security logs contain crucial information about the security events and activities occurring on a Windows operating system. These logs play a vital role in monitoring and investigating security incidents, as well as detecting and preventing potential threats.
The storage location of Windows security logs varies depending on the version of Windows:
- Windows Server 2008 and earlier versions: The security logs are stored in %SystemRoot%\System32\Config folder. Specifically, the file «SecEvent.evt» contains the security events.
- Windows Server 2012 and later versions, and Windows 10: The security logs are stored in the Event Log service. They can be accessed using the Event Viewer tool. The security logs are organized into categories such as «Security,» «Application,» and «System.»
It is important to regularly review and analyze the Windows security logs to identify any suspicious or malicious activities, as well as to maintain a strong security posture for the Windows environment.
Key Takeaways — Where Are Windows Security Logs Stored
- Windows security logs are stored in a folder called Event Viewer.
- The Event Viewer logs can be found in the «Windows\System32\winevt\Logs» directory.
- Security logs are stored as .evtx files.
- The Event Viewer provides detailed information about various security events and activities.
- Windows security logs are essential for monitoring and troubleshooting system security.
Frequently Asked Questions
Understanding where Windows security logs are stored is essential for monitoring and troubleshooting security events on your system. Here are some commonly asked questions about the location of Windows security logs.
1. How can I find the location of Windows security logs?
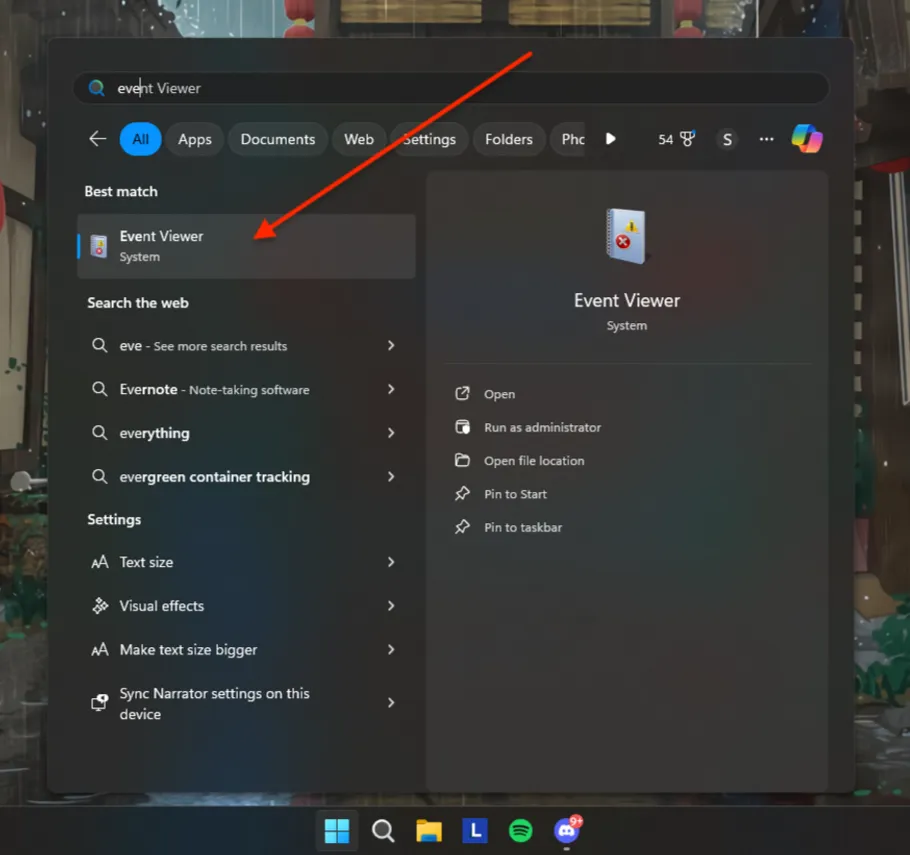
Windows security logs are typically stored in the Event Viewer tool. To access the Event Viewer, go to the «Start» menu, type «Event Viewer» in the search bar, and click on the app in the search results. Within the Event Viewer, you can navigate to «Windows Logs» and find the security logs stored under the «Security» category.
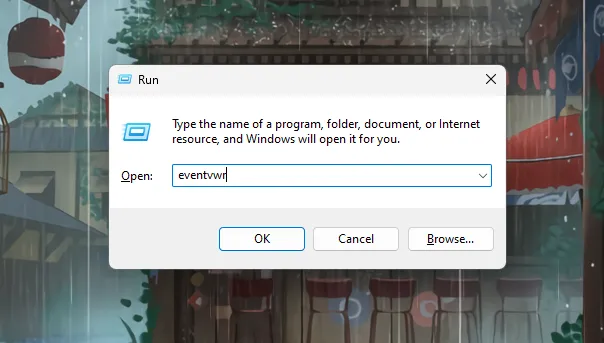
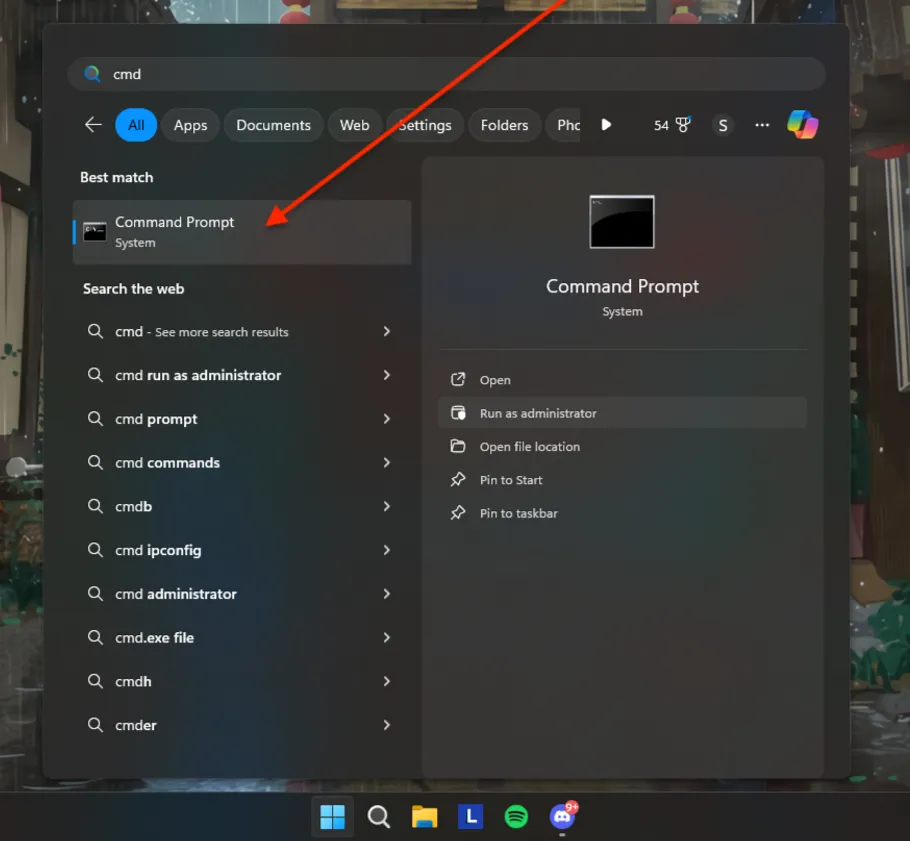
Alternatively, you can also access the security logs by opening the «Run» dialog box (press Windows key + R), typing «eventvwr.msc,» and pressing Enter. This will directly open the Event Viewer.
2. Are Windows security logs stored locally or can they be stored remotely?
Windows security logs are stored locally on the system by default. However, you can configure your system to store the logs remotely on a different server if needed. This can be useful in larger network environments where centralized log storage and monitoring are preferred.
To configure remote log storage, you would need to modify the Event Log settings in the Group Policy Editor or use specialized log management software.
3. Can I change the default location of Windows security logs?
Yes, it is possible to change the default location of Windows security logs if desired. However, it is recommended to exercise caution when modifying the default log storage location to ensure the logs are still accessible and properly managed.
To change the location, you would need to modify the Event Log settings in the Group Policy Editor and specify the new storage location for the security logs.
4. How long are Windows security logs stored?
By default, Windows security logs are set to overwrite events as the log file grows larger. This means that older events may be replaced by newer events once the log reaches its maximum size.
However, you can configure the log retention policies to specify how long the logs should be kept before being overwritten or cleared. This can be adjusted based on your specific requirements for auditing and compliance purposes.
5. Are there any third-party tools available to manage Windows security logs?
Yes, there are several third-party tools available that provide advanced log management and analysis capabilities for Windows security logs. These tools offer features such as real-time monitoring, centralized log storage, alerting, and customizable reporting.
Some popular third-party log management tools for Windows include Splunk, LogRhythm, and SolarWinds Log & Event Manager.
In conclusion, Windows security logs are stored in specific locations on your computer. These logs contain important information about security events and activities on your system.
By default, the security logs are stored in the Event Viewer tool, which can be accessed through the Windows Administrative Tools in the Control Panel. The logs are saved in the Windows Event Log format (.evt or .evtx) and can be viewed using the Event Viewer or exported for further analysis.
Where Are Windows Security Logs Stored?
In the realm of computer security, understanding how logs are managed and accessed is crucial to both system administrators and users alike. Windows operating systems integrate an extensive logging mechanism designed for monitoring system events, which plays a vital role in tracking security incidents, troubleshooting, and maintaining compliance with regulations. One critical area of this logging architecture pertains to Windows Security Logs. This comprehensive discussion will delve into «Where Are Windows Security Logs Stored?» exploring multiple aspects of security logs, their significance, storage locations, retrieval methods, and more.
Understanding Windows Security Logs
Windows Security Logs are an essential aspect of Windows Event Logging, a system that records various system events and operations. The Windows Security Log specifically records events related to system security, such as logon attempts, access to files and folders, and changes to user privileges. These logs are invaluable for auditing purposes, enabling administrators to ensure compliance with policies and detect potentially malicious activities.
Significance of Security Logs
-
Monitoring and Auditing: Security logs provide a historical record of sensitive activities, making them indispensable for monitoring user actions and auditing compliance. Organizations often need to prove adherence to standards such as HIPAA, PCI DSS, or GDPR, and security logs play a pivotal role in this process.
-
Investigation and Forensics: When a security breach occurs, the first step in the investigation involves reviewing logs to identify the point of entry, the actions taken by the attacker, and the extent of the damage.
-
Real-Time Alerts: Many security solutions can be configured to analyze security logs in real time, triggering alerts when suspicious activities are detected.
-
User Behavior Analysis: Analyzing security logs can help organizations understand user behavior, allowing them to implement policies and training to mitigate human errors.
Where Are Windows Security Logs Stored?
Windows Security Logs are stored locally on the computer or server where they are generated. They are accessible through the Windows Event Viewer, a built-in utility that provides a graphical interface for viewing event logs. The security logs’ storage mechanisms can sometimes confuse users because log files can be stored in different locations depending on the configuration and Windows version.
Storage Location in File System
While the primary way of accessing security logs is through the Event Viewer, it’s essential to understand that these logs are not stored in a traditional file format on the disk. Instead, they are part of the Windows Event Log system, which manages log entries in a proprietary format.
The security logs reside in the following default path in Windows:
- For Windows Server:
C:WindowsSystem32winevtLogsSecurity.evtx - For Windows Client (Home/Pro):
C:WindowsSystem32winevtLogsSecurity.evtx
The .evtx file extension indicates that these logs are stored in an Event Log format, which is optimized for performance, allowing efficient querying of log entries.
Accessing Windows Security Logs
Using Windows Event Viewer
-
Open Event Viewer: To access the security logs, you can open the Event Viewer by typing
eventvwr.mscin the Run dialog (accessible via Win + R) or searching for «Event Viewer» in the Start menu. -
Navigating to Security Logs: In the Event Viewer, expand the
Windows Logssection on the left pane, and you will find «Security.» Clicking on this will display all recorded security events. -
Filtering and Sorting Logs: Event Viewer allows you to filter logs based on different criteria such as Event ID, Source, and Level (Information, Warning, Error). This feature is useful for narrowing down the search when investigating specific incidents.
Using PowerShell
For advanced users and system administrators, PowerShell offers a more powerful way to retrieve and analyze security logs. You can leverage the Get-EventLog or Get-WinEvent cmdlets. For example:
Get-WinEvent -LogName SecurityThis command outputs all events recorded in the security log with details and can be further customized with filters.
Command Prompt Access
If you prefer using the command prompt, you can retrieve security logs using the wevtutil command. Here is how you might access security logs via Command Prompt:
- Open Command Prompt with administrative privileges.
- Use the following command:
wevtutil query-securityThis command will provide a list of entries in the security log.
Understanding Security Event IDs
Windows Security logs categorize events through unique identifiers known as Event IDs. Each ID corresponds to a particular action or security incident. This categorization is crucial for pinpointing specific types of activities or alerts. Some commonly referenced Security Event IDs include:
- 4624 – Successful logon
- 4625 – Failed logon
- 4663 – Access to an object
- 4672 – Special privileges assigned to a logon session
- 5140 – Network share object accessed
By familiarizing yourself with these Event IDs, you can swiftly diagnose and respond to security incidents as they arise.
Managing Security Logs
Given the critical nature of security logs, it is imperative to manage them effectively. This management process includes regular monitoring, retention policies, and adequate storage to ensure logs do not become overwhelming or unusable.
Log Retention Policies
Windows has predefined retention settings for security logs but administrators can customize these settings based on organizational needs. Retention policies dictate how long logs should be kept before they are overwritten:
- Overwrite as needed (default): If the storage limit is reached, the earliest log entries are first to be overwritten.
- Archive the logs: Administrators can configure the logs to archive. This method does require a proper backup and storage strategy.
- Prevent overwrite: This setting prohibits any log overwriting until logs are manually cleared, which can lead to logs filling up quickly.
Storage Limits
Security logs are stored in the Windows Event Log database, which may impose a limit on the log size – typically around 20 MB or more, depending on the system configuration. This means that if not managed effectively, critical log entries may be lost.
Best Practices for Security Log Management
To make the most of Windows Security Logs, administrators should consider implementing the following best practices:
-
Regular Monitoring: Set up daily checks to review security logs for unusual activities. Utilize automated tools and scripts where feasible.
-
Establish a Baseline: Understanding normal activities on the system will make it easier to spot anomalies. Baselines help in tuning alerts to minimize false positives.
-
Retention Policy: Define specific retention policies that satisfy compliance requirements while balancing storage costs and administrative effort.
-
Backup Logs: Regularly back up security logs to ensure they are preserved for compliance and forensic investigations.
-
Utilize SIEM Tools: Security Information and Event Management (SIEM) tools can centralize log collection from diverse sources, facilitating correlation and analysis.
Correlating Security Logs with Other Logs
For a more holistic view of system security, it’s beneficial to correlate Windows Security Logs with other log types, such as Application Logs, System Logs, and even network logs. Many SIEM solutions facilitate this correlation, providing a broader context and enhancing threat detection capabilities.
Conclusion
Windows Security Logs constitute an invaluable resource in maintaining system security, performing audits, and investigating incidents. Storing locally on the host systems, these logs are manageable through tools such as Windows Event Viewer and PowerShell. However, their true power lies in effective monitoring, retention, and analysis as part of a comprehensive security strategy. By understanding where Windows Security Logs are stored and how to access them, users and administrators can better harness this resource to protect their environments against potential threats.
As cybersecurity threats continue to evolve, the role of security logs in strengthening defenses has never been more critical. Embracing a proactive approach toward log management will contribute not only to immediate benefit but to long-term resilience and security posture. Understanding the ins and outs of Windows Security Logs empowers users, fosters informed decision-making, and ultimately fortifies the overall security of computer systems.
If you’re using a Windows server and want to know what happened to your machine, Windows logs are an essential resource. Windows logs record various system activities, errors, and other significant events, providing valuable information for troubleshooting, auditing, and ensuring system integrity. Understanding how to access, interpret, and utilise these logs enables efficient, problem solving, enables security measures and ensures the smooth operation of your system.
In this guide, you will learn about Windows event logs, its different categories, how to filter and create Custom Views.
What is a Windows Event Log?
A Windows event log is a file that keeps track of system events and errors, application issues, and security events. Windows Event log can also provide insights into an application’s behavior by tracking its interactions with other processes and services. With the right knowledge of the information stored in these logs, you can easily diagnose and easily resolve issues within your system and applications.
You can access the windows events logs as follows:
Using the Start Menu:
- Click on the Start button or press the Windows key.
- Type
Event Viewerin the search box and select it from the search results.
Using the Run Dialog:
- Press
Windows + Rto open the Run dialog. - Type
eventvwrand press Enter.
Using the Control Panel:
- Open the Command Prompt and run as administrator.
- Type
eventvwrand press Enter.
You can see the detailed steps below. Now let’s discuss and understand windows events logs in detail.
Understanding Windows Event Logs categories & Types
There are different Windows logs, each serving a specific purpose in tracking and recording events related to your system, applications, and security. They include:
- System Events: System events log information is about the core operations of your Windows operating system. System events are essential for maintaining your system’s health and functionality because it records events related to the system’s hardware and software components. Some system events are as follows:
- Hardware Failures: Logs any issues related to hardware components, such as disc failures or memory errors.
- Driver Issues: Records events related to the loading, unloading, or malfunctioning of device drivers. This helps in identifying driver-related problems that could affect system stability.
- System Startups and Shutdowns: Tracks the times when the system starts up or shuts down. This can be useful for understanding system uptime and diagnosing issues related to improper shutdowns or startup failures.
- Application Events: Data related to software applications running on the system includes application errors, warnings, and informational messages. If you are using a Windows server to run your production-level application, you can use the application errors, warnings, and messages provided here to solve the issue. There are different types of Application events some are as follows:
- Application Errors: Application errors are events generated by software applications when they encounter issues that prevent them from functioning correctly.
- Warnings: Logs warnings from applications about potential issues that might not be critical but could lead to problems if not addressed.
- Informational Messages: Provides general information about application activities, such as successful operations or status updates, helping to understand the normal functioning of applications.
- Security Events: Security events are logs that capture all security-related activities on your Windows system. They are essential for monitoring, maintaining, and auditing the security of your system. These events help detect unauthorised access attempts, monitor access to sensitive resources, and track changes to system policies. Some security events are as follows:
- Successful and Failed Login Attempts: Successful and failed login attempts are critical events that are logged by a system to monitor access and ensure security. These logs provide valuable insights into user activity, helping to detect unauthorised access attempts and identify potential security threats.
- Resource Access: These events log attempts to access protected resources such as files, folders, or system settings. Monitoring these logs ensures that sensitive data is accessed appropriately and helps identify unauthorised access attempts.
- System Policy Changes: These logs record any changes to system policies, including modifications to user permissions or security settings. This is important for auditing purposes and ensuring compliance with security policies, helping to maintain the integrity and security of the system.
- Setup Events: Setup events are logs that contain detailed information about the installation and setup processes on your Windows system. These logs are valuable for diagnosing and resolving issues that occur during the installation or configuration of software and system components. Some Setup events are as follows:
- Installation Processes: Installation processes refer to the series of steps and operations carried out to install software, updates, or system components on a Windows system. It contains log details about software installation, updates, or system components. This helps in diagnosing issues related to incomplete or failed installations.
- Setup Configurations: Records information about system configurations during the setup process. This can be useful for understanding your system’s initial setup and configuration.
- Forwarded Events: Forwarded events are logs sent from other computers to a centralised logging server. This is particularly useful in larger environments where centralised log management is needed. They include:
- Logs from Remote Systems: Collects event logs from multiple systems, allowing for centralised monitoring and management.
- Centralised Logging Scenarios: Useful for organisations that need to aggregate logs from various systems to a single location for easier analysis and monitoring.
Accessing the Windows Event Viewer
Windows Event Viewer is a Windows application that lets you see your computer’s logs, warnings, and other events. Each application you open generates entries that are recorded in an activity log, which can be viewed from the Event Viewer.
There are several ways to access the Windows Event Viewer. Here are some of them:
-
Using the Start Menu:
- Click on the Start button or press the Windows key.
- Type
Event Viewerin the search box.
Using start menu to open Event viewer — Select Event Viewer from the search results which will popup something like this.
Event Viewer main page 2. Using the Run Dialog: — Press
Windows + Rto open the Run dialog. — Typeeventvwrand press Enter.Windows Run App to open Event Viewer Windows Event viewer landing page 3. Using Control Panel: — Open the Command Prompt and run as administrator
Open CMD as Administrator from start menu — Once open, type
eventvwrand press enter, and you will be redirected to Event Viewer page.CMD terminal
Windows Log Location
Windows event logs are stored in files located in the C:\\Windows\\System32\\winevt\\Logs directory. Each log file corresponds to a specific log category, such as System, Application, or Security. It may differ depending on which version of Windows you are using.
The main event log files are:
- Application.evtx: Logs events from applications and programs.
- Security.evtx: Logs security events like successful or failed logins.
- System.evtx: Logs events related to Windows system components and drivers
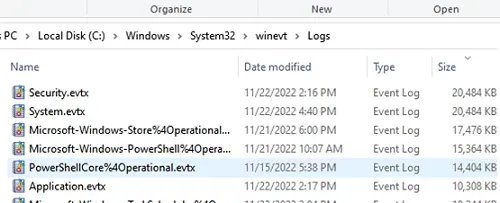
You can find many other log files which could be related to system operations & other processes that are happening inside the Windows System. Windows 11uses the .evtx format rather than using the classic EVT format.
Understanding Event Viewer Entries
Event Viewer entries provide detailed information about each logged event. It is like a log book for your Windows system. They record important happenings within the system, including applications, systems, security, failed events, etc. Understanding these entries is key to effective log management.
The key components of an Event Viewer entry are:
- Date and Time: When the event occurred.
- Source: The application or system component that generated the event.
- Event ID: A unique identifier for the event type.
- Level: The severity of the event (Information, Warning, Error, Critical).
- User: The user account under which the event occurred.
- Computer: The name of the computer where the event was logged.
- Description: Detailed information about the event.
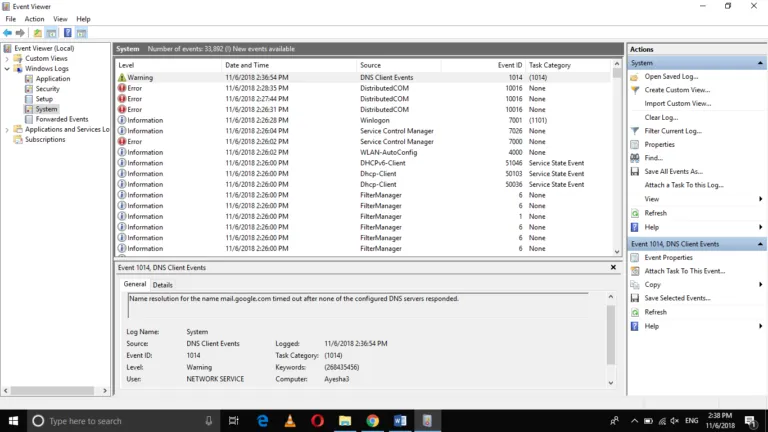
Each event in the Event Viewer has a severity level, indicating the importance and type of the event:
- Information (Green Light): These events resemble a green traffic light, signifying smooth sailing. They indicate successful operations or occurrences within your system.
- Warning (Yellow Light): Treat these entries with caution, like a yellow traffic light. They signal potential issues that warrant attention but might not cause immediate problems.
- Error (Orange Light): Think of error entries as an orange traffic light; proceed with care. They denote significant problems that could affect system functionality. Imagine an error message indicating a driver failure.
- Critical (Red Light): Critical entries are akin to a red traffic light; stop and address the situation immediately. They represent severe errors that have caused a major failure. A critical event might report a complete system shutdown or a critical service crashing.
Filtering and Custom Views
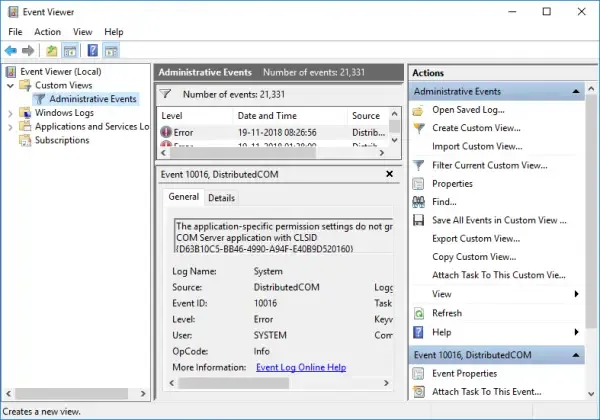
Event Viewer allows you to filter events using a variety of parameters, including date, event level, source, and more. Consider the following scenario: your system exhibits weird behaviour, but the Event Viewer is overflowing with hundreds, if not thousands, of entries. Filtering steps and generating custom views can significantly reduce the workload. You may also construct custom views to focus on specific kinds of events:
- In the Event Viewer, you’ll see Administrative Events, to create special logs right-click on «Custom Views» and select «Create Custom View.»
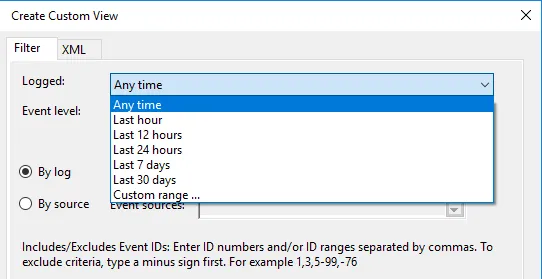
1. In the Custom View page, you can see logged drop down, choose a preferred time or it gives you an option to create a custom time to set. 2. On the Event Level choose an appropriate level for your custom view, You can choose among the 5 levels.
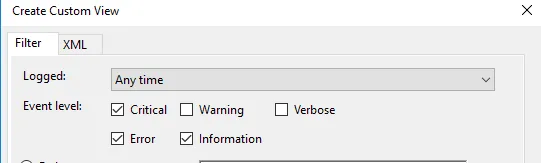
1. Once done, choose how you want the events to be filtered, By log or By source.
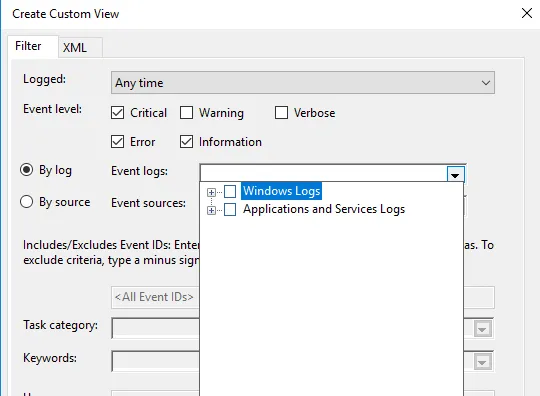
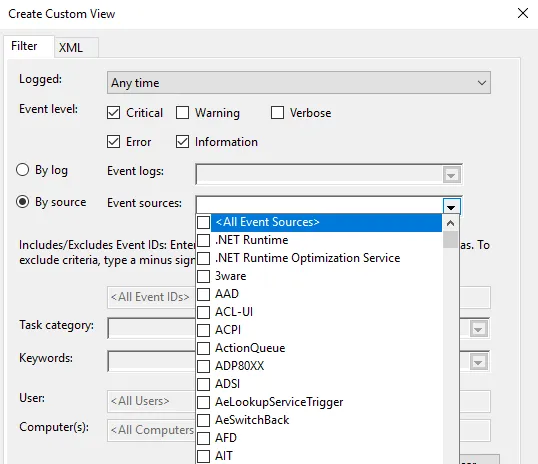
Once everything is set up according to your needs, save all events in Custom View as
from the drop-down menu and choose an appropriate location to save the logs. Click on the Save button. (A log file with the extension .evtx will be saved on your device).
Conclusion
This blog provides an understanding how you can use the Windows Event Viewer which is provided by the Windows in default and using it to monitor Windows logs.
- Main event log files are stored in
C:\\Windows\\System32\\winevt\\Logs. - Windows logs are crucial for understanding the activities, errors, and significant events on your machine. They provide valuable information for troubleshooting, auditing, and ensuring system integrity.
- They record a variety of system activities, errors, and other significant events, providing valuable information for troubleshooting, auditing, and ensuring system integrity.
- We learnt how to setup Filtering and Custom Views to optimise what we see and solve the problems and where it happened.
By grasping the significance of different event types such as System, Application, Security, Setup, and Forwarded Events, and knowing how to filter and export logs, you can effectively manage your Windows system.
FAQ’s
How to view Windows logs?
To view Windows logs, use the built-in Event Viewer:
- Press
Win + R, typeeventvwr, and press Enter. - Navigate through the console tree to find the log you want to view (e.g., Windows Logs > Application).
Where are Microsoft logs?
Microsoft logs, including Windows logs, can be found in the Event Viewer under sections like Application, Security, and System. Log files are also located in the C:\Windows\System32\winevt\Logs directory.
How do I audit Windows logs?
To audit Windows logs:
- Open Event Viewer.
- Navigate to Security logs under Windows Logs.
- Configure auditing policies via the Local Security Policy or Group Policy Management Console.
How do I check my Windows activity log
Check your Windows activity log by viewing the Security logs in Event Viewer. These logs record user logins, logoffs, and other security-related activities.
Which is Windows log key?
The Windows log key, often referred to as the Windows key, is the key on your keyboard with the Windows logo. It is used in various shortcuts to open system tools, including Event Viewer (Win + X > Event Viewer).
Where is the logs folder?
The logs folder is located at C:\Windows\System32\winevt\Logs. This folder contains all the event log files in .evtx format.
Why are Windows logs important?
Windows logs are important because they provide detailed information about system operations, security events, and application behavior, which is crucial for troubleshooting, auditing, and ensuring system integrity.
How to view log files?
View log files using Event Viewer:
- Open Event Viewer (
Win + R, typeeventvwr, press Enter). - Expand the Windows Logs section and select the log you want to view.
Where are login logs?
Login logs are located in the Security logs section of Event Viewer. They record all login attempts, both successful and failed.
What are system logs?
System logs contain information about the core operations of the Windows operating system, including hardware events, driver issues, and system startups and shutdowns. They are found under the System section in Event Viewer.
How do I find Windows log files?
Find Windows log files in the Event Viewer or directly in the C:\Windows\System32\winevt\Logs directory.
How do I view user logs in Windows 10?
View user logs in Windows 10 through the Event Viewer:
- Open Event Viewer.
- Go to Windows Logs > Security to see logs related to user activities, including logins and logoffs.
How do I view Windows setup logs?
To view Windows setup logs:
- Open Event Viewer.
- Navigate to Applications and Services Logs > Microsoft > Windows > Setup.
How do I view Windows app logs?
To view Windows application logs:
- Open Event Viewer.
- Navigate to Windows Logs > Application to see logs related to software applications running on your system.
Was this page helpful?
The event logs are located in Windows or WINNT directory under %WinDir%\system32\config. These files end in .
- Where is the security event log?
- What is a security event log?
- How do I find Windows event log?
- How do I find the event log Reader group?
- How do I view the event log in CMD?
- What information is in event logs?
- How do event logs work?
- Where are Windows security logs stored?
- Which users are in Event Log reader?
- How do I enable Manage auditing and security log?
- How do I give permission to an event log?
- Where are CMD logs stored?
- How do I open Event Viewer in Task Manager?
- How do I open Device Manager from CMD?
Where is the security event log?
To view the security log
In the console tree, expand Windows Logs, and then click Security. The results pane lists individual security events. If you want to see more details about a specific event, in the results pane, click the event.
What is a security event log?
Security event logging and monitoring is a process that organizations perform by examining electronic audit logs for indications that unauthorized security-related activities have been attempted or performed on a system or application that processes, transmits or stores confidential information.
How do I find Windows event log?
Click Start > Control Panel > System and Security > Administrative Tools. Double-click Event Viewer. Select the type of logs that you wish to review (ex: Windows Logs)
How do I find the event log Reader group?
Note: To read the event logs, you also need to grant the «ADAudit Plus» user Read permission over HKLM\SYSTEM\CurrentControlSet\Services\Eventlog\Security. Log in to your Domain Controller with Domain Admin privileges → Open the Group Policy Management Console → Right click on the «ADAudit Plus Permission GPO» → Edit.
How do I view the event log in CMD?
Start Windows Event Viewer through the command line
To open a command prompt, click Start , click All Programs , click Accessories and then click Command Prompt . As a shortcut you can press the Windows key + R to open a run window, type cmd to open a, command prompt window. Type eventvwr and click enter.
What information is in event logs?
An event log is a file that contains information about usage and operations of operating systems, applications or devices. Security professionals or automated security systems like SIEMs can access this data to manage security, performance, and troubleshoot IT issues.
How do event logs work?
Event logging provides a standard, centralized way for applications (and the operating system) to record important software and hardware events. The event logging service records events from various sources and stores them in a single collection called an event log.
Where are Windows security logs stored?
The event logs are located in Windows or WINNT directory under %WinDir%\system32\config. These files end in .
Which users are in Event Log reader?
Event Log Readers group
This group is created when you promote a Windows Server system to the role of domain controller and it’s also present as a built-in group on all of the member servers in each domain of a forest. Members of this group are granted permissions to read the event logs on the local computer.
How do I enable Manage auditing and security log?
Locate the Manage auditing and security log policy and double-click it. In the Manage auditing and security log Properties dialog, click Add User or Group, specify the user that you want to define this policy for. Navigate to Start → Run and type «cmd». Input the gpupdate /force command and press Enter.
How do I give permission to an event log?
Navigate to HKEY_LOCAL_MACHINE > SYSTEM > CurrentControlSet > Services > EventLog > Security, right-click and select «Permissions…» Click «Add…», find the account running Secret Server, then click OK. Check Read in the Allow column, then click OK to apply the permission.
Where are CMD logs stored?
Start > Control Panel > System and Security > Administrative Tools > Event Viewer. In event viewer select the type of log that you want to review. Windows stores five types of event logs: application, security, setup, system and forwarded events.
How do I open Event Viewer in Task Manager?
Use the Run window to open Event Viewer (all versions of Windows) A rapid method is to open the Run window (Windows + R), type eventvwr. msc in the Open field, and click or tap OK.
How do I open Device Manager from CMD?
Device Manager can also be opened using Command Prompt, in any version of Windows, via its run command, devmgmt. msc.
Introduction
The Windows event log is an itemized record of the framework, security, and application notices the Windows working framework chairpersons put away to analyze framework issues and anticipate future problems.
Applications and the operating system (OS) utilize these event logs to record significant equipment and programming activities that the manager can use to investigate issues with the operational system. The Windows operating system tracks explicit events in its log documents, like application establishments, security of the executives, framework arrangement procedure on beginning startup, and issues or blunders.
Where are Windows logs stored?
If your installation is on a C drive, the location of the Windows event logs is C: WindowsSystem32winevtLogs. Event log files have the extension .evtx.When a Windows application crashes, the event log stores information about the application name, why the application crashed, and the incident time.
Below is presented Windows 11 log location from 2022:
What is the EVTX file?
EVTX file represents Microsoft Event Viewer logs that users can see in Event Viewer. You can run Microsoft Event Viewer logs using the Windo” “>eventvwr co” m”d. m”c”
The “o”ponents of a Windows event log
Every Event in a log passage contains the accompanying data:
Date: The date the Event happened.
Time: The time the Event occurred.
Client: The client was signed onto the machine when the Event occurred.
PC: The name of the PC.
Occasion ID: A Windows ID number that determines the event type.
Source: The program or part that caused the Event. Type: The sort of Event, including data, cautioning, mistake, security achievement review, or security disappointment review.
For instance, a data event may show up as:
Data 3/19/2021 8:21:15 AM Service Kernel-Event Tracing 1 Logging
An admonition event may resemble:
Cautioning 3/19/2021 10:29:47 AM
By examination, a mistake event may show up as:
Mistake 3/19/2021 AM Service Control Manager 7001 None
A primary event may look like this:
Basic 3/19/2021 8:55:02 AM Kernel-Power 41 (63)
The sort of data put away in Windows event logs
The Windows working framework records events in five zones: application, security, arrangement, framework, and sent events—Windows stores event signs in the C:\WINDOWS\system32\config\ envelope.
Application events are occurrences with the product introduced on the neighborhood PC. If an application, such as Microsoft Word, crashes, the Windows event log will create a section about the issue, the application name, and why it was slammed.
Security events store data depending on the framework, and the ordinary events stored incorporate login endeavors and asset access. For instance, the security log stores a record of the PC checking account certifications when a client attempts to sign on to a machine.
Arrangement events incorporate centered events identifying with the control of spaces, like the area of logs after a plate setup.
Framework events identify with episodes on Windows-explicit frameworks, like the situation with gadget drivers.
Sent events appear from different machines in a similar organization when a chairperson needs to utilize a PC that accumulates numerous logs.
Utilizing the Event Viewer
Microsoft remembers the Event Viewer for its Windows Server and customer working framework to see Windows event logs. Clients access the Event Viewer by tapping the Start catch and entering the Event Viewer into the hunt field. Clients can then choose and investigate the ideal log.
How to open Event Viewer in Windows?
- Press Sta”t” butt”n”
- Click” “Contr” l”Pan” S” s” and Securi” A” m” “s” rating Too”s.”
- Doub “e”clic” “Event “V”ew”r”
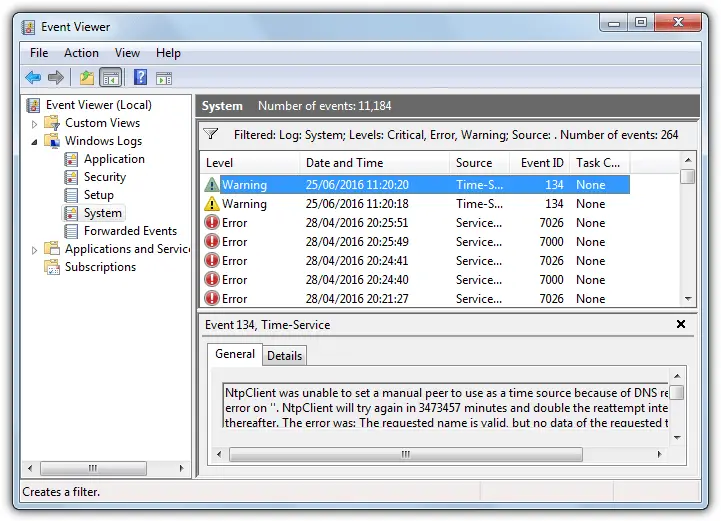
Window” orders each Event with severity based on data, caution, blunders, and the basics.
Most logs comprise data-based events. Logs with this section typically mean the experience happened without an episode or issue. An illustration of a framework-based data event is Event 42, Kernel-Power, which shows the framework is entering rest mode.
Cautioning level events depend on specific events, for example, an absence of extra room. Cautioning messages can focus on potential issues that don’t prompt activity. Occasion 51, Disk illustrates a framework-based admonition identified with a paging mistake on the thmachine’machine’sAsA blunder level demonstrates a gadget may have neglected to stack or work expectedly. Occasion 5719, NETLOGON illustrates a framework mistake whenn’t a safe meeting with an area regulator.
Basic-level events show the most severe issues. Occasion ID 41, Kernel-Power, illustrates a basic framework when a machine reboots without a spotless closure.
Different devices to see Windows event logs.
Microsoft likewise gives the order line utility in the System32 organizer that recovers event logs, runs questions, sends out logs, files logs, and clears logs.
Outsider utilities that work with Windows event logs incorporate SolarWinds Log and Event Manager, providing event connection and remediation, record trustworthiness observation, USB gadget checking, and danger location. Log and Event Manager gathers logs from workers, applications, and organization gadgets.
ManageEngine EventLog Analyzer fabricates custom reports from log information and sends constant instant messages and email alarms dependent on explicit events.
Utilizing PowerShell to question events
Microsoft fabricates Windows event signs in an extensible markup language (XML) design with an EVTX augmentation. XML gives more granular data and a reliable organization for organized information.
Directors can construct convoluted XML inquiries with the Get-WinEvent PowerShell cmdlet to add or reject events from a question. With issues related to corrupted event logs, we recommend you first try a software cleanup of your Windows event log. These software tools, such as ReconLogger or Software Events Cleaner, automatically clean Windows event logs to eliminate all the junk, such as unused files, configuration files, and garbage. Alternatively, try System Reliability; search and filter it by date range and service to find specific issues. The graphs in the Window Event Viewer can help detect subtle behavior changes in your system.
- About
- Latest Posts