You might see either or both of these errors in your Event Viewer:
Log Name: System Source: Microsoft-Windows-WinRM
Event ID: 10149 Level: Warning Keywords: ClassicDescription: The WinRM service is not listening for WS-Management requests.
User Action If you did not intentionally stop the service, use the following command to see the WinRM configuration: winrm enumerate winrm/config/listener
or
Log Name: System Source: Microsoft-Windows-WinRM
Event ID: 10155Description: The WSMan service failed to read configuration of the following plugin:
Microsoft.ServerManager.
The WS-Management service cannot process the request. Configuration for plugin: “Microsoft.ServerManager” is corrupted. This plugin needs to be reconfigured or deleted. Use the following command to delete a plugin configurationwinrm delete http://schemas.microsoft.com/wbem/wsman/1/config/plugin?Name=xyz
Or use the following command to restore default plugin configuration. Note that all external plugins will be unregistered during this restore operation.
winrm invoke Restore http://schemas.microsoft.com/wbem/wsman/1/config/plugin @{}.
User Action Make sure this plugin configuration is valid.


There are two common causes both with easy solutions:
FIX 1 – Add IP Addresses To The Monitor
See if ALL your IP’s are being monitored. That includes your IPv4 address (or addresses if you have more than 1) AND the loopback 127.0.0.1.
You can do this by just running this command: netsh http show iplist
You can see in my case it was not configured to listen to any IP addresses:

If you need to add your IP’s just use netsh http add iplisten 127.0.0.1

FIX 2 – Correct Registry
The registry entries for WinRM and WSMan should look like:

If your is empty or missing settings, here are the defaults taken from a fresh Windows Server 2012 R2 install:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN]
“StackVersion”=”2.0”[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\AutoRestartList]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\CertMapping]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\Client]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\Listener]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\Listener\*+HTTP]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\Plugin]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\Plugin\Event Forwarding Plugin]
“ConfigXML”=””[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\Plugin\Microsoft.PowerShell]
“ConfigXML”=” “[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\Plugin\Microsoft.PowerShell.Workflow]
“ConfigXML”=” “[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\Plugin\Microsoft.PowerShell32]
“ConfigXML”=” “[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\Plugin\Microsoft.Windows.ServerManagerWorkflows]
“ConfigXML”=” “[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\Plugin\SEL Plugin]
“ConfigXML”=” “[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\Plugin\WMI Provider]
“ConfigXML”=””[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\SafeClientList]
“WSManSafeClientList”=hex:00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,01[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\Service]
“allow_remote_requests”=dword:00000001[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\WinRS]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WSMAN\WinRS\CustomRemoteShell]
Note that I copied the setting above from THIS great website.
If you want to know more about WSMan, skim through THIS Microsoft Article
Enjoy!
If you follow the command in the event ID, by running it in an elevated command prompt:
winrm enumerate winrm/config/listener
You should see something like:
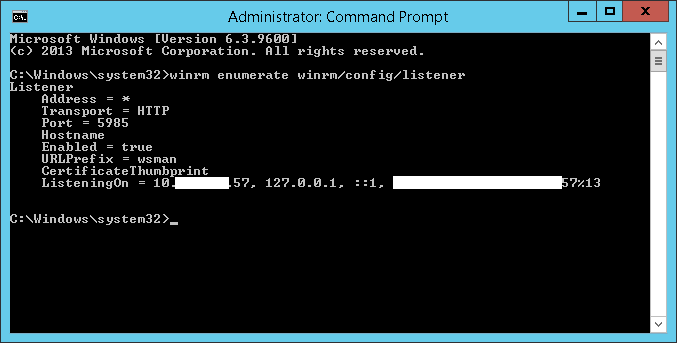
If you do not see the local IP of the server, but only the 127.0.0.1 address then delete the entry with:
netsh http delete iplisten 127.0.0.1
Then run winrm enumerate winrm/config/listener again and see if the local IP is present now.
If the list is blank, run: winrm quickconfig
Refurbished Computers Berkshire
Data Recovery Berkshire
Home
> Security, Windows > Damaged WMI database
When I was cheking Remote Desktop configuration on couple Windows 2008 R2 servers I’ve noticed that I cannot access Remote Desktop Session Host Configuration and I get following error:
Remote Desktop Session Host Configuration
The settings for the Remote Desktop Session Host server cannot be retrieved. The remote server does not support running Remote Desktop Session Host Configuration remotely.

Remote Desktop Session Host Configuration error
I also notived weird events in event viewer:
Event 1065 GroupPolicy
The processing of Group Policy failed. Windows could not evalute the Windows Management Instrumentation (WMI) filter for the Group Policy object…

Event 1064 Group Policy
Event 10149 Windows Remote Management
The WinRM service is not listening for WS-Management requests…
Event 10149 Windows Remote Management
Event 43, WMI
Windows Management Instrumentaion ADAP failed to connect to namespace…

Event 43, WMI
Event 10, WMI
Event filter with query … could not be reactivated in namespace…

Event 10, WMI
Windows Management Instrumentation service was up and running. This looked like damaged WMI database. I remeber that this was happening in W2003 environment lots of times during new software installations or just from time to time 🙂
To solve this issue, you need to make WMI consistent again with command:
winmgmt /salvagerepository
This command checks if WMI database is consistent and if it finds any problem it rebuild repository. More info at http://msdn.microsoft.com/en-us/library/windows/desktop/aa394525(v=vs.85).aspx. When this does not help, you can try using switch “/resetrepository” which resets WMI to initial settings.
PS: I hoped that Microsoft solved problems with WMI from W2003 times.
source:Microsoft-Windows-WinRM
Event ID:10149
Source Name:Microsoft-Windows-WinRM
Event Source Name:WinRM
log:System
level:Warning
Task category:None
ope code:Info
keyword:Classic
message:The WinRM service is not listening for WS-Management requests.
User Action
If you did not intentionally stop the service, use the following command to see the WinRM configuration:
winrm enumerate winrm/config/listener
Resolution
Displayed during shutdown
If this event is displayed while the OS is stopped (shutdown), there is no particular problem.
Configure
If the Win-RM function cannot be used, check if the listener is properly configured.
(1) Start the service
Start the «Windows Remote Management (WS-Management)» service.
To always start the service, execute the following command with administrator privileges.
C:\>sc config WinRM Start= auto
[SC] ChangeServiceConfig SUCCESS
(2) Configure the listener
Configure the listener.
C:\> winrm enumerate winrm/config/listener
Post Comment
Содержание страницы
- Первоначальная настройка
- Удаление настроек
- Исправление ошибок
- Код события:10154 Источник: Microsoft-Windows-WinRM
Первоначальная настройка
Для включения и первоначальной настроики службы WinRM в Windows, есть несколько вариантов
- CMD
winrm quickconfig winrm e winrm/config/listener
- PowerShell
Enable-PSRemoting –Force Enable-WSManCredSSP -Role server –Force
Удаление настроек
Disable-PSRemoting -Force
Исправление ошибок
Код события:10154 Источник: Microsoft-Windows-WinRM
Event ID: 10154, Source: Microsoft-Windows-WinRM, Type: Warning
Службе WinRM не удалось создать следующие имена участников-служб: WSMAN/dc1.notdev.local, WSMAN/dc1
Дополнительные данные
Была получена ошибка “8344”: %%8344.
Проблема чаще всего возникает с серверами Hyper-V и AD DC, проблема существует очень давно и до сих пор не решена, либо MS не желает объяснять почему эту процедуру нужно выполнять самостоятельно либо просто игнорируют данную ошибку, которая редко когда мешает работе служб.
Исправить данную ошибку проще всего используя командную строку
dsacls "CN=DC1,OU=Domain Controllers,DC=notdev,DC=local" /G "S-1-5-20:WS;Validated write to service principal name" dsacls "CN=DC2,OU=Domain Controllers,DC=notdev,DC=local" /G "S-1-5-20:WS;Validated write to service principal name" dsacls "CN=HVS1,OU=Hyper-V,DC=notdev,DC=local" /G "S-1-5-20:WS;Validated write to service principal name" dsacls "CN=HVS2,OU=Hyper-V,DC=notdev,DC=local" /G "S-1-5-20:WS;Validated write to service principal name" dsacls "CN=HVS3,OU=Hyper-V,DC=notdev,DC=local" /G "S-1-5-20:WS;Validated write to service principal name" dsacls "CN=HVS4,OU=Hyper-V,DC=notdev,DC=local" /G "S-1-5-20:WS;Validated write to service principal name"
CN=DC1,OU=Domain Controllers,DC=notdev,DC=local – путь до указанного сервера
S-1-5-20 – это учетная запись Сетевая служба / NETWORK SERVICE
Validated write to service principal name /в русской локализации Удостоверенная запись на узел с именем участника службы или Удостоверенная запись на узел с именем субъекта-службы
Решение через графический интерфейс
Вариант через оснастку Редактирование ADSI (ADSIEDIT)
- Запустите adsiedit.msc
- Подключитесь к домену
- Перейдите к DC=notdev,DC=local далее OU=Domain Controllers и выберите узел CN=DC1
- Щелкните правой кнопкой мыши CN=DC1, нажмите Свойства
- Перейдите на вкладку Безопасность
- Добавьте учетную запись сетевой службы NETWORK SERVICE
- Затем установите флажок (X), чтобы разрешить доступ Validated write to service principal name, в русской локализации Удостоверенная запись на узел с именем участника службы или Удостоверенная запись на узел с именем субъекта-службы
- Нажмите ОК
- Перезапустите службу Удаленное управление Windows (WS-Management)
- Проверьте журнал событий на наличие ошибок
Вариант через оснастку Active Directory Пользователи и Компьютеры (ADUC)
- Запустите dsa.msc
- Подключитесь к домену
- Включите отображение дополнительных компонентов, Вид -> Дополнительные компоненты
- Перейдите в OU=Domain Controllers и выберите узел DC1
- Щелкните правой кнопкой мыши DC1, нажмите Свойства
- Перейдите на вкладку Безопасность
- Добавьте учетную запись сетевой службы NETWORK SERVICE
- Затем установите флажок (X), чтобы разрешить доступ Validated write to service principal name, в русской локализации Удостоверенная запись на узел с именем участника службы или Удостоверенная запись на узел с именем субъекта-службы
- Нажмите ОК
- Перезапустите службу Удаленное управление Windows (WS-Management)
- Проверьте журнал событий на наличие ошибок
–
Дополнительные материалы
- Идентификаторы безопасности
