Windows Packet Filter (WinpkFilter©) is a high-performance packet filtering framework for Windows that allows developers to transparently filter (view and modify) raw network packets at the NDIS level of the network stack with minimal impact on network activity and without having to write any low-level driver code.
Windows Packet Filter includes NDIS 3.1/4 hooking VxD driver (Windows 95/ME), NDIS 4 hooking filter driver (Windows NT/2000/XP), NDIS 5 Intermediate (Windows XP/2003) and NDIS 6 Lightweight Filter (LWF) drivers as well as companion user-mode API DLL and samples.
A key advantage of Windows Packet Filter in comparison to other packets filtering frameworks for Windows (based on Windows Filtering Platform (WFP) callout drivers, Layered Service Providers (LSP), TDI filters etc…) is the ability to manipulate raw Ethernet frames achieved by installing driver below all network protocol drivers and just above network interface driver. Thus, WinpkFilter driver has an ultimate control over all network traffic flow destined to or originated from your system and allows you to modify any packet, drop it or even forge and insert an entirely new one. Using Windows Packet Filter requires no experience in kernel mode programming on your behalf, since it provides you with a powerful user level API. However, if you need to implement your solution (to achieve better performance) in kernel mode, you can do that as well by adding your functional code directly to Windows Packet Filter driver’s code.
System Requirements
| Windows 95/98/Millennium | Windows Server 2008* | Windows Server 2012 R2 |
| Windows NT 4.0 | Windows 7 | Windows 10 |
| Windows 2000 | Windows Server 2008 R2 | Windows Server 2016 |
| Windows XP | Windows 8 | Windows Server 2019 |
| Windows Server 2003 | Widows Server 2012 | Windows 11 |
| Windows Vista* | Windows 8.1 | Windows Server 2022 |
The following connections types are supported for the operating systems above:
- Wired Ethernet (802.3)
- Wi-Fi (802.11)
- WAN (Analog/ISDN modems, PPPoE, 3G/4G mobile modems)
- Mobile Broadband (PPIP)
Product features
- Reliability and stability confirmed by hundreds of satisfied customers since product launch in 2002 ranged from small shareware companies to world known corporations.
- High performance. WinpkFilter allows handling Gigabit network bandwidth in user mode application without noticeable performance degradation.
- Complete and easy portability across all Windows desktop platforms.
- Operates on RAS/PPP adapters and supports Windows 7 Mobile Broadband stack(PPIP)
- Passive network listening (collecting network packets) and active filtering (with capability to edit/drop network packets) modes
- Interface for injecting raw Ethernet frames into the network stack (either destined from the TCP/IP to the network and in reversed direction)
- Support for MTU decrement (allows setting system-wide MTU decrement). This option is useful if you plan to add additional headers to IP packets (implement IP in IP packet tunneling, IPSEC based VPN and so on).
- The powerful built-in network filters engine allows setting rules to pass, block or redirect a network packet to a Windows Packet Filter-based application for further processing.
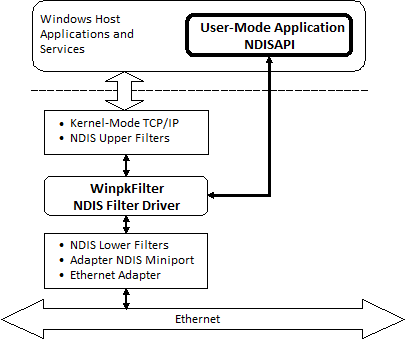
Applicability/Usage Scope
Windows Packet Filter can be used as a base for the following kinds of network applications (including but not limited to):
- User-mode firewall and content filtering solutions. No more need to write kernel mode drivers to implement the firewall!
- Kernel-mode firewall and content filtering solutions. This requires kernel-mode programming skills and Source Code license (to integrate your network packet processing code directly into the drivers) but provides the maximum possible performance.
- Internet Connection Sharing (Network Address Translation) that can be implemented either in user or kernel depending on performance requirements.
- Virtual Private Network solution (IPSEC, SSL VPN, Wireguard etc.) that can also be implemented both in user and kernel depending on performance requirements.
- Network packets tunneling solution. An example, packets captured from the network can be tunneled from the client to the remote system inside the SSL, SSH, HTTP, ICMP etc., extracted by the remote host and injected into the real network (after required packet headers modifications). Response packets can be returned to the client in the same manner. This may allow bypassing certain network access limitations.
- Packet sniffer. You can capture and inspect all packets sent to (received from) TCP/IP.
- IP shaping solutions (when you need to limit bandwidth for Internet users).
- Network traffic counting and bandwidth management solutions.
- Wireless Firewall Gateways, even with HTTP authorization.
- Transparent proxy solution based on NDIS level packet redirection. This can be used, an example, to decrypt SSL(Man-In-The-Middle), parent content control, e-mail SPAM filtering etc…
- Transparent filtering bridge
NDISAPI
NDISAPI is a comprehensive user-mode interface library designed for seamless interaction with the Windows Packet Filter driver. It stands out by offering a straightforward, safe, and efficient interface for filtering (inspecting and modifying) raw network packets at the NDIS level of the network stack, ensuring minimal impact on network performance.
Windows Packet Filter (WinpkFilter) is a robust and efficient packet filtering framework tailored for Windows environments. It empowers developers to handle raw network packets at the NDIS level with ease, providing capabilities for packet inspection, modification, and control. WinpkFilter boasts user-friendly APIs, compatibility across various Windows versions, and streamlines network packet manipulation without the need for kernel-mode programming skills.
Key Features
- Network Adapter Management: Enumerate and manage network adapter properties.
- Packet Analysis and Modification: Capture, filter, and modify network packets.
- Packet Transmission: Send raw packets directly through the network stack.
Resources
- Homepage: Windows Packet Filter
- Comprehensive Documentation: Windows Packet Filter Documentation
Library Components
- ndisapi.dll: Native Win32 DLL wrapper (x86/x64/ARM64 versions).
- ndisapi.lib: Native Win32 static library wrapper (x86/x64/ARM64 versions).
- ndisapi.net: .NET C++/CLI mixed class library (x86/x64/ARM64 versions).
- ndisapi.vs2012: Visual Studio 2012 project for native Win32 DLL wrapper, supporting Windows XP/2003 (x86/x64).
- ndisapi.vc6: Visual C++ 6.0 project for native Win32 DLL wrapper, supporting legacy Windows versions prior to Windows XP/2003.
Build Prerequisites for Examples
The example projects included with NDISAPI are set up to automatically manage their dependencies using vcpkg manifests when built with Visual Studio 2022. This process is designed to be straightforward and requires no additional manual installation of dependencies.
Automated Dependency Management with Visual Studio 2022
- Building the examples in Visual Studio 2022 will automatically resolve and install the required dependencies through the vcpkg manifests. This approach is the simplest and is recommended for most users.
Alternative: Standalone vcpkg Installation
For those using an environment other than Visual Studio 2022 or preferring manual installation, the following vcpkg commands with specific triplets can be used to install the necessary dependencies:
-
Microsoft GSL (Guideline Support Library): Required for all examples.
vcpkg install ms-gsl:x86-windows ms-gsl:x64-windows ms-gsl:arm64-windows ms-gsl:x86-windows-static ms-gsl:x64-windows-static ms-gsl:arm64-windows-static
-
PcapPlusPlus: Required only for the
pcapplusplusexample.vcpkg install pcapplusplus:x86-windows pcapplusplus:x64-windows
-
Hyperscan and llhttp: Required only for the
hyperscanexample.- Install Hyperscan:
vcpkg install hyperscan:x86-windows hyperscan:x64-windows
- Install llhttp:
vcpkg install llhttp:x86-windows llhttp:x64-windows
- Install Hyperscan:
Note
- Using Visual Studio 2022 with built-in vcpkg support is the preferred method for building the examples, as it greatly simplifies the process of dependency management.
- The standalone vcpkg commands with specific triplets are provided as an alternative for those who require manual installation or are working in different environments.
Example Projects
Basic C++ Examples
Ideal for beginners, these examples showcase the fundamental capabilities of NDISAPI. They are adaptable to different development environments and Windows versions:
- With Visual C++ 6.0: Binaries are compatible with Windows 95/NT and later operating systems.
- With Visual Studio 2012: Suitable for running on Windows XP/2003 and later.
The examples include:
- listadapters: Enumerates network adapters and their properties.
- packetsniffer: Introduces the basics of network packet sniffing.
- passthru: Demonstrates single packet processing techniques.
- packthru: Explores handling of multiple network packets simultaneously.
- ndisrequest: Shows how to send NDIS requests to network adapters.
- filter: Uses built-in static filters for selective packet filtering.
- wwwcensor: Implements content filtering in HTTP packets based on specific keywords.
- gretunnel: Demonstrates IP over GRE tunneling, modifying packet headers.
Advanced C++ Examples (Visual Studio 2012)
Designed for users with advanced knowledge, these examples delve into more complex functionalities of NDISAPI.
- snat: A simple MFC Internet Connection sharing application.
- lfnemu: Long Fat Network (LFN) Emulator for simulating LFN behavior over local networks.
Advanced C++ Examples (Visual Studio 2022)
These examples are intended for experienced users, showcasing sophisticated use of NDISAPI:
- capture: Captures and saves network packets in PCAP format.
- dns_proxy: Implements a transparent UDP proxy for the DNS protocol.
- dnstrace: Intercepts and decodes DNS responses.
- ethernet_bridge: Bridges wired and wireless network connections.
- ipv6_parser: Intercepts IPv6 packets and parses protocol headers.
- sni_inspector: Extracts SNI and Host headers from HTTPS and HTTP packets.
- socksify: Redirects TCP connections through a SOCKS5 proxy.
- udp2tcp: Converts between UDP and TCP protocols.
- rebind: Rebinds TCP/UDP connections to different network interfaces.
- pcapplusplus: Utilizes PcapPlusPlus for packet parsing and TLS fingerprinting.
- hyperscan: Detects HTTP sessions using Hyperscan and parses HTTP with llhttp.
Very Advanced C++ Example
- ProxiFyre: An advanced evolution of the Windows Packet Filter’s socksify example, ProxiFyre enhances its capabilities by adding UDP support and facilitating the management of multiple proxy instances.
C# Examples
For C# developers:
- TestDotNet: Showcases NDISAPI in filtering scenarios, using PacketDotNet for network packet header analysis.
Introduction
As a Windows developer, you may have encountered situations where you need to filter or modify raw network packets on the NDIS level. However, writing low-level TDI or NDIS driver code can be a daunting task, requiring extensive knowledge of kernel mode programming. This is where WinpkFilter comes in – a high-performance packet filtering framework that allows developers to transparently filter raw network packets on the NDIS level with minimal impact on network activity.
What is WinpkFilter?
WinpkFilter is a Windows Packet Filter Kit that provides a powerful user-level API for filtering and modifying raw network packets on the NDIS level. With WinpkFilter, you can create applications that insert themselves into the Windows network packets flow, allowing you to develop custom firewall solutions, internet connection sharing (NAT), IP shaper, VPN, and many other low-level network solutions completely in user-mode.
Key Features of WinpkFilter
- High-Performance Packet Filtering: WinpkFilter provides a high-performance packet filtering framework that allows developers to filter and modify raw network packets on the NDIS level with minimal impact on network activity.
- User-Level API: WinpkFilter provides a powerful user-level API that allows developers to create applications that insert themselves into the Windows network packets flow without requiring extensive knowledge of kernel mode programming.
- Support for Various Network Connections: WinpkFilter supports dial-up connections (analog modem, ISDN modem), Ethernet (LAN and WLAN) connections, cable/DSL modem using DHCP or «PPP over Ethernet» (EnterNet, RasPPPoE, WinPoET), and mobile broadband connections.
- Support for Various Development Environments: WinpkFilter supports various development environments, including Visual C++, Delphi, Visual Basic, C++ Builder, and others.
Benefits of Using WinpkFilter
- Easy to Use: WinpkFilter provides a powerful user-level API that makes it easy to filter and modify raw network packets on the NDIS level.
- High-Performance: WinpkFilter provides a high-performance packet filtering framework that minimizes the impact on network activity.
- Flexible: WinpkFilter supports various network connections and development environments, making it a versatile tool for developers.
- No Kernel Mode Programming Required: WinpkFilter provides a user-level API that eliminates the need for extensive knowledge of kernel mode programming.
How to Use WinpkFilter
Using WinpkFilter is relatively straightforward. Here are the general steps to follow:
- Download and Install WinpkFilter: Download the WinpkFilter SDK and install it on your development machine.
- Choose Your Development Environment: Choose your preferred development environment, such as Visual C++, Delphi, Visual Basic, C++ Builder, or others.
- Create a New Project: Create a new project in your chosen development environment.
- Include the WinpkFilter Header Files: Include the WinpkFilter header files in your project.
- Use the WinpkFilter API: Use the WinpkFilter API to filter and modify raw network packets on the NDIS level.
Example Use Case: Creating a Custom Firewall Solution
Here’s an example use case for creating a custom firewall solution using WinpkFilter:
- Create a New Project: Create a new project in Visual C++.
- Include the WinpkFilter Header Files: Include the WinpkFilter header files in your project.
- Use the WinpkFilter API: Use the WinpkFilter API to filter and modify raw network packets on the NDIS level.
- Implement Firewall Logic: Implement your custom firewall logic using the WinpkFilter API.
- Test Your Firewall Solution: Test your custom firewall solution to ensure it’s working as expected.
Conclusion
WinpkFilter is a powerful packet filtering framework that allows developers to transparently filter and modify raw network packets on the NDIS level with minimal impact on network activity. With its user-level API and support for various network connections and development environments, WinpkFilter is an ideal tool for developers who need to create custom firewall solutions, internet connection sharing (NAT), IP shaper, VPN, and other low-level network solutions. By following the steps outlined in this article, you can easily get started with using WinpkFilter to create your own custom network solutions.
System Requirements
- Windows 9x/ME/NT/2000/XP/2003/Vista/2008/7/2008R2/8/2012/8.1/2012R2: WinpkFilter supports Windows 9x/ME/NT/2000/XP/2003/Vista/2008/7/2008R2/8/2012/8.1/2012R2.
- Development Environment: WinpkFilter supports various development environments, including Visual C++, Delphi, Visual Basic, C++ Builder, and others.
Troubleshooting
If you encounter any issues while using WinpkFilter, here are some troubleshooting tips to help you resolve the problem:
- Check the WinpkFilter Documentation: Check the WinpkFilter documentation to ensure you’re using the API correctly.
- Check the WinpkFilter Examples: Check the WinpkFilter examples to see how to use the API in different scenarios.
- Check the WinpkFilter Forums: Check the WinpkFilter forums to see if other developers have encountered similar issues.
- Contact WinpkFilter Support: Contact WinpkFilter support for further assistance.
Frequently Asked Questions
Here are some frequently asked questions about WinpkFilter:
- Q: What is WinpkFilter?
A: WinpkFilter is a high-performance packet filtering framework that allows developers to transparently filter and modify raw network packets on the NDIS level with minimal impact on network activity. - Q: What are the system requirements for WinpkFilter?
A: WinpkFilter supports Windows 9x/ME/NT/2000/XP/2003/Vista/2008/7/2008R2/8/2012/8.1/2012R2 and various development environments, including Visual C++, Delphi, Visual Basic, C++ Builder, and others. - Q: How do I use WinpkFilter?
A: To use WinpkFilter, download and install the WinpkFilter SDK, choose your development environment, create a new project, include the WinpkFilter header files, and use the WinpkFilter API to filter and modify raw network packets on the NDIS level.
WinpkFilter Q&A: Frequently Asked Questions
=====================================================
Q: What is WinpkFilter?
A: WinpkFilter is a high-performance packet filtering framework that allows developers to transparently filter and modify raw network packets on the NDIS level with minimal impact on network activity.
Q: What are the key features of WinpkFilter?
A: The key features of WinpkFilter include:
- High-Performance Packet Filtering: WinpkFilter provides a high-performance packet filtering framework that allows developers to filter and modify raw network packets on the NDIS level with minimal impact on network activity.
- User-Level API: WinpkFilter provides a powerful user-level API that allows developers to create applications that insert themselves into the Windows network packets flow without requiring extensive knowledge of kernel mode programming.
- Support for Various Network Connections: WinpkFilter supports dial-up connections (analog modem, ISDN modem), Ethernet (LAN and WLAN) connections, cable/DSL modem using DHCP or «PPP over Ethernet» (EnterNet, RasPPPoE, WinPoET), and mobile broadband connections.
- Support for Various Development Environments: WinpkFilter supports various development environments, including Visual C++, Delphi, Visual Basic, C++ Builder, and others.
Q: What are the benefits of using WinpkFilter?
A: The benefits of using WinpkFilter include:
- Easy to Use: WinpkFilter provides a powerful user-level API that makes it easy to filter and modify raw network packets on the NDIS level.
- High-Performance: WinpkFilter provides a high-performance packet filtering framework that minimizes the impact on network activity.
- Flexible: WinpkFilter supports various network connections and development environments, making it a versatile tool for developers.
- No Kernel Mode Programming Required: WinpkFilter provides a user-level API that eliminates the need for extensive knowledge of kernel mode programming.
Q: How do I get started with using WinpkFilter?
A: To get started with using WinpkFilter, follow these steps:
- Download and Install WinpkFilter: Download the WinpkFilter SDK and install it on your development machine.
- Choose Your Development Environment: Choose your preferred development environment, such as Visual C++, Delphi, Visual Basic, C++ Builder, or others.
- Create a New Project: Create a new project in your chosen development environment.
- Include the WinpkFilter Header Files: Include the WinpkFilter header files in your project.
- Use the WinpkFilter API: Use the WinpkFilter API to filter and modify raw network packets on the NDIS level.
Q: What are some example use cases for WinpkFilter?
A: Some example use cases for WinpkFilter include:
- Creating a Custom Firewall Solution: Use WinpkFilter to create a custom firewall solution that filters and modifies raw network packets on the NDIS level.
- Implementing Internet Connection Sharing (NAT): Use WinpkFilter to implement internet connection sharing (NAT) and allow multiple devices to share a single internet connection.
- Creating an IP Shaper: Use WinpkFilter to create an IP shaper that limits the amount of bandwidth available to certain applications or devices.
- Implementing a VPN: Use WinpkFilter to implement a VPN that encrypts and decrypts raw network packets on the NDIS level.
Q: What are some common issues that developers may encounter when using WinpkFilter?
A: Some common issues that developers may encounter when using WinpkFilter include:
- Incorrectly Configured WinpkFilter: Ensure that WinpkFilter is correctly configured and installed on your development machine.
- Incorrectly Used WinpkFilter API: Ensure that you are using the WinpkFilter API correctly and following the documentation.
- Network Connection Issues: Ensure that your network connection is stable and functioning correctly.
- Development Environment Issues: Ensure that your development environment is correctly configured and functioning correctly.
Q: How do I troubleshoot issues with WinpkFilter?
A: To troubleshoot issues with WinpkFilter, follow these steps:
- Check the WinpkFilter Documentation: Check the WinpkFilter documentation to ensure you are using the API correctly.
- Check the WinpkFilter Examples: Check the WinpkFilter examples to see how to use the API in different scenarios.
- Check the WinpkFilter Forums: Check the WinpkFilter forums to see if other developers have encountered similar issues.
- Contact WinpkFilter Support: Contact WinpkFilter support for further assistance.
Q: What are the system requirements for WinpkFilter?
A: The system requirements for WinpkFilter include:
- Windows 9x/ME/NT/2000/XP/2003/Vista/2008/7/2008R2/8/2012/8.1/2012R2: WinpkFilter supports Windows 9x/ME/NT/2000/XP/2003/Vista/2008/7/2008R2/8/2012/8.1/2012R2.
- Development Environment: WinpkFilter supports various development environments, including Visual C++, Delphi, Visual Basic, C++ Builder, and others.
Q: Is WinpkFilter compatible with 64-bit operating systems?
A: Yes, WinpkFilter is compatible with 64-bit operating systems, including Windows 8, Windows 8.1, Windows 10, and Windows Server 2012 R2.
Q: Can I use WinpkFilter with other network filtering tools?
A: Yes, you can use WinpkFilter with other network filtering tools, such as firewalls and intrusion detection systems. However, ensure that you are using the tools correctly and following the documentation.
Q: Is WinpkFilter a free tool?
A: No, WinpkFilter is a commercial tool that requires a license to use. However, you can download a free trial version to evaluate the tool before purchasing a license.
Windows Packet Filter Kit
Windows Packet Filter Kit
WinpkFilter is a high performance packet filtering framework for Windows
9x/ME/NT/2000/XP/2003/Vista/2008 that allows developers to transparently filter
(view and modify) raw network packets with minimal impact on network activity
without having to write low level TDI or NDIS driver code. WinpkFilter is more
than just a firewall development kit for Windows. Wide range of solutions can be
implemented using WinpkFilter: custom firewalls, internet connection sharing
(NAT), IP shaper, VPN and many other low-level network solutions completely in
user-mode using your favorite development environment: Visual C++, Visual C#,
Delphi, C++ Builder, Visual Basic and etc. Using WinpkFilter requires no
experience in kernel mode programming on your behalf since WinpkFilter provides
you with powerful user level API. However, if you need to implement your
solution (to achieve better performance) in kernel mode you can use
well-documented raw IOCTL interface as well.
Пример применения http://www.xakep.ru/post/29448/default.asp
Для того, чтобы получить возможность изменять заголовки пакетов на внешнем
(Internet) сетевом интерфейсе, нам понадобится драйвер фильтр пакетов уровня
NDIS. Написание подобного драйвера требует навыков работы в kernel mode и
выходит за рамки данной статьи, желающих разобраться самостоятельно я отсылаю к
документации DDK. Мы же воспользуемся готовым решением, которое позволяет
реализовать прозрачную фильтрацию и обработку пакетов в user mode. Это
библиотека WinpkFilter от ntkernel.com. Продукт сей бесплатный для
некоммерческого использования, скачать run-time библиотеку можно отсюда http://www.ntkernel.com/w&p.php?id=7
Network traffic Filtering techniques for Windows, either in user-mode or kernel-mode, falls into one of two categories: stream and packet methods. This document presents useful techniques to build robust security software products such as personal firewalls and VPN clients for Windows 2000 or higher.
Before going further with this article, I would personally recommend WPF for Vista and higher, and TDI filters + NDIS Hook for earlier versions to build a combined stream and packet filtering solutions.
Winsock Layered Service Provider
A Winsock Layered Service Provider (LSP) is a DLL that operates on the Winsock functions to inspect, modify and intercept the inbound and outbound Internet traffic as streams and not as packets. LSP also runs in the workspace of the process it intercepts making easy to filter streams based on caller PID, short name or full path.
LSP can be chained and are useful tool for data-monitoring, content filtering, stream based sniffers, Quality of Service (QoS), authentication, encryption … LSP technology is often exploited by spyware and adware programs to bombard users with advertisements and email spam.
There is one known limitation and one common issue with LSPs. On some Windows versions, LSP can be bypassed by calling TCP/IP stack directly via TDI making useless, for instance, Trojan or virus protections at this level. A bogus LSP or improper LSP removal/unregistration operation may break the whole TCP/IP stack or leave the machine without working network connection.
Windows 2000/XP Filter Hook Driver
A Filter Hook driver is supported on Windows 2000/XP only and is implemented as a kernel mode driver. It operates by registering a callback with the IP Filter Driver that gets called when sending a receiving a packet. Filtering rules are limited to pass, drop or forward decision based on IP addresses and ports information.
The callback registration process uses an IRP with IOCTL_PF_SET_EXTENSION_POINTER as an IO control code and a PF_SET_EXTENSION_HOOK_INFO structure filled with a pointer to the callback routine.
A Filter Hook driver is simple to implement but has three serious limitations. Only one callback routine can be installed each time on the system. It is not possible to filter Ethernet frames. Outgoing packets cannot be modified.
Windows 2000/XP Firewall Hook Driver
A Firewall Hook driver is very similar to a Filter-Hook driver but installs a callback in the IP driver. The callback registration process uses an IRP with IOCTL_IP_SET_FIREWALL_HOOK as an IO control code and an IP_SET_FIREWALL_HOOK_INFO structure filled with a pointer to the callback routine.
Although it is not well documented, writing a Firewall Hook driver requires few lines of code. The main limitation is the support of Windows 2000 and XP only.
NDIS Hook Driver
There are two approved techniques to write an NDIS Hook driver. The first one is based on interception of some NDIS wrapper functions at runtime by writing a kernel mode driver that patches NDIS.sys in memory to replace the addresses of NdisRegisterProtocol, NdisDeregisterProtocol, NdisOpenAdapter and NdisCloseAdapter functions with internal ones.
The second one is based on registering a fake NDIS Protocol driver just to get a pointer to an internal NDIS structure NDIS_PROTOCOL_BLOCK.
At this level, both methods have enough information to substitute all protocols and adapters handlers to getting full control over all network traffic.
Although these approaches use sophisticated hacking techniques and require good understanding of different NDIS versions internals, an NDIS Hook driver is easy to install and able to filter, inject or modify packets. Several security software products including personal firewalls and VPN clients use these techniques.
This approach is discouraged for Windows Vista and higher.
NDIS Intermediate Driver
An NDIS intermediate driver, also called NDIS IM driver, is inserted just above miniport drivers and just below transport protocols in the overall networking protocol stack allowing incoming and outgoing packets filtering, inspection or modification. An NDIS Intermediate driver is a documented alternative to NDIS Hook drivers and offers the same functionalities.
NDIS intermediate drivers should be digitally signed at Microsoft to allow silent installations. This technology is replaced by NDIS Lightweight Filter drivers on Vista and higher.
NDIS Lightweight Filter Driver
NDIS Lightweight Filter drivers (LWF drivers) are introduced in Windows Vista and higher to replace NDIS Intermediate driver technology. They offer the same packets filtering, inspection or modification capabilities.
NDIS Lightweight Filter drivers are easier to implement and are designed to improve overall performances.
TDI Filter Driver
The Transport Driver Interface (TDI) defines a kernel mode network interface that is exposed at the upper edge of all transport protocol stacks. TDI also provides standard methods for protocol addressing, sending and receiving datagrams, writing and reading streams, initiating connections, detecting disconnects making it the only socket interface in the kernel.
TDI Filter drivers sit between TDI clients (such as AFD.sys, NETBT.sys) and TDI transports (such as TCPIP.sys) and intercept the communication between them. In case of TCP/IP filtering, the technique consists in writing a kernel-mode driver that layers itself over devices created by TCPIP.sys driver (\Device\RawIp, \Device\Udp, \Device\Tcp, \Device\Ip and \Device\MULTICAST) using IoAttachDevice routine. A good understanding of how to handle and interact with IRPs is required.
It is recommended to stop using TDI filters and move to Windows Filtering Platform (WFP) on Vista and later platforms. Windows makes it possible for TDI filters to see TCP/IP traffic is just for compatibility reasons and it does not yield good performance.
Windows Filtering Platform
Windows Filtering Platform (WPF) is a new architecture available in Windows Vista and higher that was built to replace all existing packet filtering technologies such as Winsock LSP, TDI filter and NDIS Intermediate driver and to provide better performance and less development complexities. Callout drivers, Filter Engine, Base Filtering Engine and Shims are components of the WPF architecture.
The WFP API consists of a user-mode API and a kernel-mode API that interacts with the packet processing that takes place at several layers in the networking stack. With WFP, incoming and outgoing packets can be filtered and modified before they reach their destinations, making this architecture ideal for implementing various filtering applications or solutions (such as personal firewalls, intrusion detection systems, antivirus programs, network monitoring tools, and parental controls). WFP arbitration rules also minimize the risk that software components get affected by any future Service Pack release.
WPF is highly recommended for developing security related solutions on Vista and higher.
