Network traffic Filtering techniques for Windows, either in user-mode or kernel-mode, falls into one of two categories: stream and packet methods. This document presents useful techniques to build robust security software products such as personal firewalls and VPN clients for Windows 2000 or higher.
Before going further with this article, I would personally recommend WPF for Vista and higher, and TDI filters + NDIS Hook for earlier versions to build a combined stream and packet filtering solutions.
Winsock Layered Service Provider
A Winsock Layered Service Provider (LSP) is a DLL that operates on the Winsock functions to inspect, modify and intercept the inbound and outbound Internet traffic as streams and not as packets. LSP also runs in the workspace of the process it intercepts making easy to filter streams based on caller PID, short name or full path.
LSP can be chained and are useful tool for data-monitoring, content filtering, stream based sniffers, Quality of Service (QoS), authentication, encryption … LSP technology is often exploited by spyware and adware programs to bombard users with advertisements and email spam.
There is one known limitation and one common issue with LSPs. On some Windows versions, LSP can be bypassed by calling TCP/IP stack directly via TDI making useless, for instance, Trojan or virus protections at this level. A bogus LSP or improper LSP removal/unregistration operation may break the whole TCP/IP stack or leave the machine without working network connection.
Windows 2000/XP Filter Hook Driver
A Filter Hook driver is supported on Windows 2000/XP only and is implemented as a kernel mode driver. It operates by registering a callback with the IP Filter Driver that gets called when sending a receiving a packet. Filtering rules are limited to pass, drop or forward decision based on IP addresses and ports information.
The callback registration process uses an IRP with IOCTL_PF_SET_EXTENSION_POINTER as an IO control code and a PF_SET_EXTENSION_HOOK_INFO structure filled with a pointer to the callback routine.
A Filter Hook driver is simple to implement but has three serious limitations. Only one callback routine can be installed each time on the system. It is not possible to filter Ethernet frames. Outgoing packets cannot be modified.
Windows 2000/XP Firewall Hook Driver
A Firewall Hook driver is very similar to a Filter-Hook driver but installs a callback in the IP driver. The callback registration process uses an IRP with IOCTL_IP_SET_FIREWALL_HOOK as an IO control code and an IP_SET_FIREWALL_HOOK_INFO structure filled with a pointer to the callback routine.
Although it is not well documented, writing a Firewall Hook driver requires few lines of code. The main limitation is the support of Windows 2000 and XP only.
NDIS Hook Driver
There are two approved techniques to write an NDIS Hook driver. The first one is based on interception of some NDIS wrapper functions at runtime by writing a kernel mode driver that patches NDIS.sys in memory to replace the addresses of NdisRegisterProtocol, NdisDeregisterProtocol, NdisOpenAdapter and NdisCloseAdapter functions with internal ones.
The second one is based on registering a fake NDIS Protocol driver just to get a pointer to an internal NDIS structure NDIS_PROTOCOL_BLOCK.
At this level, both methods have enough information to substitute all protocols and adapters handlers to getting full control over all network traffic.
Although these approaches use sophisticated hacking techniques and require good understanding of different NDIS versions internals, an NDIS Hook driver is easy to install and able to filter, inject or modify packets. Several security software products including personal firewalls and VPN clients use these techniques.
This approach is discouraged for Windows Vista and higher.
NDIS Intermediate Driver
An NDIS intermediate driver, also called NDIS IM driver, is inserted just above miniport drivers and just below transport protocols in the overall networking protocol stack allowing incoming and outgoing packets filtering, inspection or modification. An NDIS Intermediate driver is a documented alternative to NDIS Hook drivers and offers the same functionalities.
NDIS intermediate drivers should be digitally signed at Microsoft to allow silent installations. This technology is replaced by NDIS Lightweight Filter drivers on Vista and higher.
NDIS Lightweight Filter Driver
NDIS Lightweight Filter drivers (LWF drivers) are introduced in Windows Vista and higher to replace NDIS Intermediate driver technology. They offer the same packets filtering, inspection or modification capabilities.
NDIS Lightweight Filter drivers are easier to implement and are designed to improve overall performances.
TDI Filter Driver
The Transport Driver Interface (TDI) defines a kernel mode network interface that is exposed at the upper edge of all transport protocol stacks. TDI also provides standard methods for protocol addressing, sending and receiving datagrams, writing and reading streams, initiating connections, detecting disconnects making it the only socket interface in the kernel.
TDI Filter drivers sit between TDI clients (such as AFD.sys, NETBT.sys) and TDI transports (such as TCPIP.sys) and intercept the communication between them. In case of TCP/IP filtering, the technique consists in writing a kernel-mode driver that layers itself over devices created by TCPIP.sys driver (\Device\RawIp, \Device\Udp, \Device\Tcp, \Device\Ip and \Device\MULTICAST) using IoAttachDevice routine. A good understanding of how to handle and interact with IRPs is required.
It is recommended to stop using TDI filters and move to Windows Filtering Platform (WFP) on Vista and later platforms. Windows makes it possible for TDI filters to see TCP/IP traffic is just for compatibility reasons and it does not yield good performance.
Windows Filtering Platform
Windows Filtering Platform (WPF) is a new architecture available in Windows Vista and higher that was built to replace all existing packet filtering technologies such as Winsock LSP, TDI filter and NDIS Intermediate driver and to provide better performance and less development complexities. Callout drivers, Filter Engine, Base Filtering Engine and Shims are components of the WPF architecture.
The WFP API consists of a user-mode API and a kernel-mode API that interacts with the packet processing that takes place at several layers in the networking stack. With WFP, incoming and outgoing packets can be filtered and modified before they reach their destinations, making this architecture ideal for implementing various filtering applications or solutions (such as personal firewalls, intrusion detection systems, antivirus programs, network monitoring tools, and parental controls). WFP arbitration rules also minimize the risk that software components get affected by any future Service Pack release.
WPF is highly recommended for developing security related solutions on Vista and higher.
This driver filters all network traffic at the lowest level (before the data is transferred to the network card). The driver monitors all kinds of network protocols possible — Ethernet, IP, TCP, UDP. Thought, it is possible to implement custom router, firewall, sniffer, anti-virus or whatever solution needed. The driver is written using the Windows Driver Development kit and NDIS technology. Installs as Network Miniport driver. Has an API for external access using DLL.
We can build any kind of kernel-mode and user-mode solutions that involve Windows drivers. We can build both for 32 bit and 64-bit platforms and sign the drivers using digital signature.
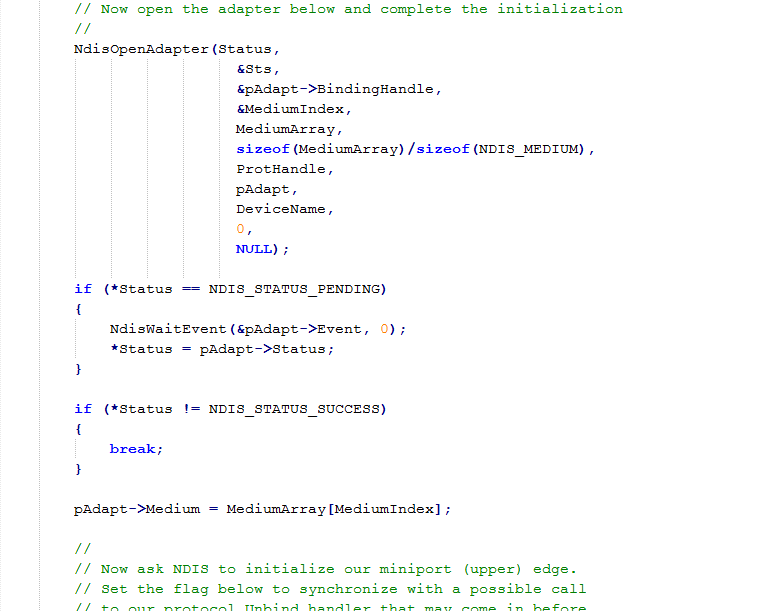
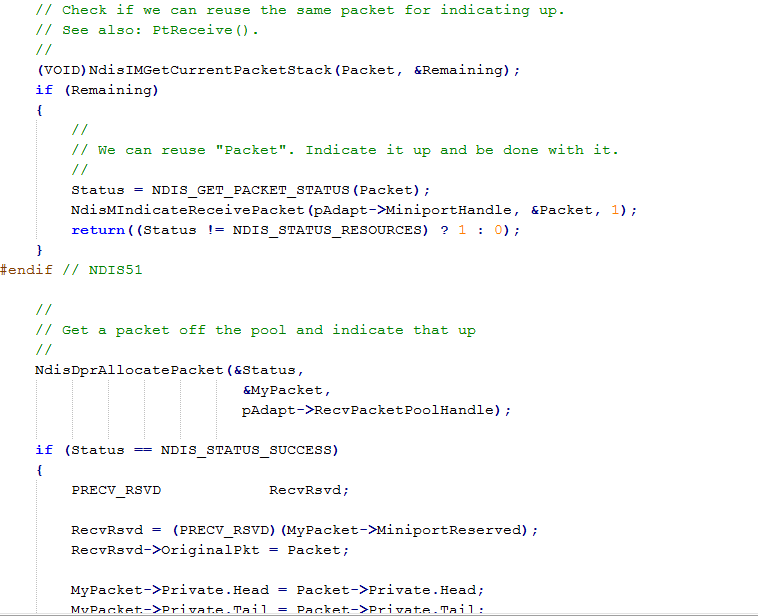
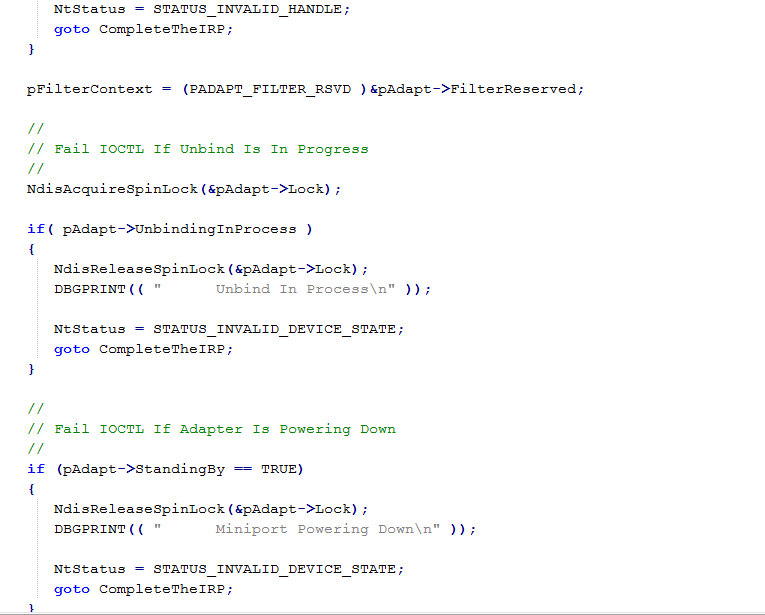
Windows Defender Network Stream Filter by Microsoft Corporation.
The Windows Defender Network Stream Filter Driver service exists only in:
- Windows 10 Home 1709
- Windows 10 Pro 1709
- Windows 10 Education 1709
- Windows 10 Enterprise 1709
Default Settings
| Startup type: | Manual |
| Display name: | Windows Defender Network Stream Filter Driver |
| Service name: | wdnsfltr |
| Service type: | kernel |
| Error control: | normal |
| Group: | NDIS |
| Path: | %SystemRoot%\system32\drivers\wdnsfltr.sys |
| Registry key: | HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\wdnsfltr |
Default Behavior
Windows Defender Network Stream Filter Driver is a kernel device driver. In Windows 10 it is starting only if the user, an application or another service starts it. If Windows Defender Network Stream Filter Driver fails to start, the failure details are being recorded into Event Log. Then Windows 10 will start up and notify the user that the wdnsfltr service has failed to start due to the error.
Restore Default Startup Configuration of Windows Defender Network Stream Filter Driver
1. Run the Command Prompt as an administrator.
2. Copy the command below, paste it into the command window and press ENTER:
sc config wdnsfltr start= demand
3. Close the command window and restart the computer.
The wdnsfltr service is using the wdnsfltr.sys file that is located in the C:\Windows\system32\drivers directory. If the file is removed or corrupted, read this article to restore its original version from Windows 10 installation media.
Mastering Network Filter Drivers: Unraveling the Mystery
In this article, we’ll dive into the world of network filter drivers, exploring their significance in monitoring network activities and how they can be employed effectively using Windows Defender and Velociraptor. We’ll discuss different types of network activities, such as TCP and UDP connections, URL access, DNS queries, and file downloads, and provide examples of how network filter drivers can be utilised for enhanced monitoring and security. Additionally, we’ll explore how to detect malicious traffic on NetBIOS, SMB, RDP, and NTLM network traffic, and enable advanced detection in Windows Defender for networks.
Tip 1: Grasping the Concept of Network Filter Drivers
Network filter drivers are kernel-mode drivers that monitor, intercept, and modify network traffic in real-time. They play an essential role in monitoring network activities like TCP and UDP connections, URL access, DNS queries, and file downloads. You can use Windows Defender and Velociraptor to analyse the data captured by these drivers for any suspicious or unauthorised activities.
Tip 2: Monitoring TCP Connections with Velociraptor
To monitor TCP connections, you can use Velociraptor’s VQL query to intercept and analyze the traffic for any suspicious or unauthorised connections:
SELECT * FROM network_connections WHERE family = 2 AND protocol = 6
VQL query to identify potentially malicious TCP connections, you can narrow down the results based on specific criteria such as connections to known malicious IP addresses, non-standard ports, or suspicious connection durations. Here’s an example of a refined query:
javaCopy code
SELECT * FROM network_connections
WHERE family = 2 AND protocol = 6
AND (
remote_address IN ('<malicious_IP_1>', '<malicious_IP_2>', '<malicious_IP_3>') OR
remote_port NOT IN (80, 443) OR
duration > <suspicious_duration_threshold>
)
Replace <malicious_IP_1>, <malicious_IP_2>, <malicious_IP_3> with known malicious IP addresses that you want to monitor. Replace <suspicious_duration_threshold> with a value (in seconds) that you consider suspicious for connection duration.
Adjust the list of remote ports as needed, depending on the standard ports you want to exclude from the results.
Keep in mind that these refinements are just examples and should be tailored to your specific environment and threat intelligence sources.
Book your free IR consultation now!
Tip 3: Keeping an Eye on UDP Connections
Velociraptor Similarly, Velociraptor can be employed to track and inspect UDP connections, helping you identify any unusual or malicious traffic patterns. Use the following VQL query to monitor UDP connections:
SELECT * FROM network_connections WHERE family = 2 AND protocol = 17
Tip 4: Analyzing URL Access with Windows Defender
Windows Defender can be configured to monitor and log URL access, allowing you to identify any potentially harmful websites being accessed by users or applications on your network. To enable URL access monitoring in Windows Defender, follow these steps:
-
Open Windows Security.
-
Click on «Virus & threat protection.»
-
Click on «Manage settings» under «Virus & threat protection settings.»
-
Turn on «Block potentially unwanted apps.»
Tip 5: Inspecting DNS Queries with Velociraptor
By using Velociraptor, you can examine DNS queries and detect any attempts to access malicious domains or perform DNS-based attacks. Use the following VQL query to monitor DNS queries:
Tip 6: Tracking File Downloads with Windows Defender
To monitor file downloads, you can configure Windows Defender to log and inspect any files being downloaded, ensuring that only legitimate and safe files are being transferred. Follow these steps to enable file download monitoring in Windows Defender:
-
Open Windows Security.
-
Click on «App & browser control.»
-
Click on «Reputation-based protection settings.»
-
Turn on «Check apps and files» and «SmartScreen for Microsoft Edge.»
Tip #7: Detecting Malicious Traffic on NetBIOS, SMB, RDP, and NTLM Network Traffic with Velociraptor
Velociraptor can be utilized to monitor and analyze network traffic for NetBIOS, SMB, RDP, and NTLM protocols, helping you identify any suspicious or unauthorized activities. Use the following VQL queries to monitor these protocols:
— NetBIOS:
SELECT * FROM network_connections WHERE remote_address LIKE '139.%' OR remote_address LIKE '137.%'
— SMB:
SELECT * FROM network_connections WHERE remote_address LIKE '445.%'
— RDP:
SELECT * FROM network_connections WHERE remote_address LIKE '3389.%'
— NTLM:
SELECT * FROM windows_events WHERE event_id = 4624 AND logon_type = 3
Tip 8: Enabling Advanced Detection on Windows Defender for Networks
To enable advanced detection capabilities in Windows Defender for network traffic, follow these steps:
1. Open Windows Security.
2. Click on «Firewall & network protection.»
3. Click on «Advanced settings.»
4. In the Windows Defender Firewall with Advanced Security window, click on «Inbound Rules» and «Outbound Rules» to create and configure custom rules for monitoring network traffic based on specific protocols, ports, or IP addresses.
Conclusion:
Network filter drivers play a critical role in monitoring network activities and ensuring the security of your systems. By understanding their capabilities and employing them effectively using Windows Defender and Velociraptor, you can gain greater visibility and control over your network traffic, ultimately enhancing your security posture.
Meta Description: Uncover the power of network filter drivers in monitoring network activities like TCP, UDP, NetBIOS, SMB, RDP, and NTLM traffic using Windows Defender and Velociraptor.
Hope you liked the article about how to discover the potential of network filter drivers for monitoring network activities, including advanced protocols, with Windows Defender and Velociraptor! 🌐🔍🔒.
