Парольная политика в домене Active Directory задает базовые требования безопасности к паролям учетных записей пользователей такие как сложность, длину пароля, частоту смены пароля и т.д. Надежная политика паролей AD позволяет снизить возможность подбора или перехвата паролей пользователей.
Содержание:
- Настройка политики паролей в Default Domain Policy
- Основные параметры политики паролей в домене
- Управление параметрами политики паролей AD с помощью PowerShell
- Несколько парольных политик в домене Active Directory
Настройка политики паролей в Default Domain Policy
Настройки политика паролей пользователей в домене AD по умолчанию задаются через групповую политику Default Domain Policy. Вы можете просмотреть и изменить настройки парольной политики в домене с помощью консоли управления консоль управления доменными GPO
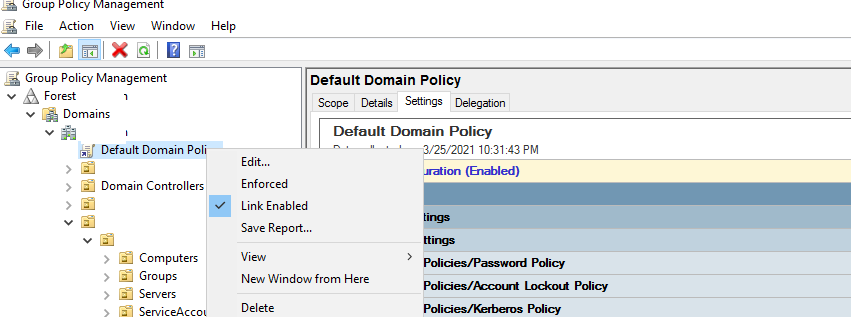
- Откройте консоль
gpmc.msc
и выберите Default Domain Policy, которая назначена на корень домена; - Щелкните правой кнопкой по Default Domain Policy и выберите Edit;
- Разверните Конфигурация компьютера -> Политики -> Конфигурация Windows -> Параметры безопасности -> Политики учетных записей -> Политика паролей (Computer configuration -> Policies -> Windows Settings -> Security Settings -> Account Policies -> Password Policy
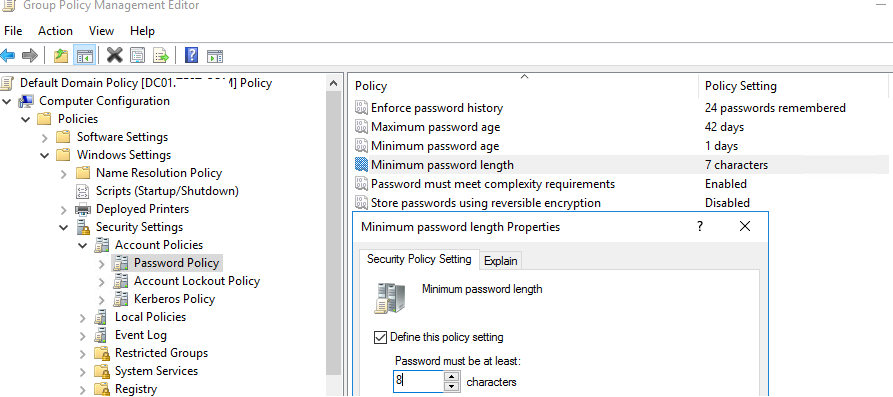
- В этом разделе есть шесть параметров политики паролей (описаны ниже);
- Чтобы изменить настройки параметра, дважды щелкните по ней. Чтобы включить политику, отметьте галку Define this policy settings и укажите необходимую настройку (в примере на скриншоте я задал минимальную длину пароля пользователя 8 символов). Сохраните изменения;
- Новые настройки парольной политики применяться ко всем пользователям домена после обновления настроек GPO на контролере домена с FSMO ролью PDC Emulator.
Основные параметры политики паролей в домене
Всего доступно шесть параметров политики паролей:
- Вести журнал паролей (Enforce password history) – задать количество старых паролей, которые хранятся в AD. Пользователь не сможет повторно использовать старый пароль (однако администратор домена или пользователь, которому делегированы права на сброс пароля в AD, может вручную задать для аккаунта старый пароль);
- Максимальный срок действия пароля (Maximum password age) – срок действия пароля в днях. После истечения срока действия пароля Windows потребует у пользователя сменить его. Обеспечивает регулярность смены пароля пользователями;
- Минимальный срок жизни пароля (Minimum password age) – как часто пользователи могут менять пароль. Этот параметр не позволит пользователю несколько раз подряд сменить пароль, чтобы вернуться к старому паролю, перезатерев пароли в журнале Password History. Как правило тут стоит оставить 1 день, чтобы пользователь мог самостоятельно сменить пароль в случае его компрометации;
- Минимальная длина пароля (Minimum password length) – не рекомендуется делать пароль короче, чем 8 символов (если указать тут 0 – значит пароль не требуется);
- Пароль должен отвечать требование сложности (Password must meet complexity requirements) – при включении этой политики пользователю запрещено использовать имя своей учетной записи в пароле (не более чем два символа подряд из
username
или
Firstname
). Также в пароле должны использоваться 3 типа символов из следующего списка: цифры (0 – 9), символы в верхнем регистре, символы в нижнем регистре, спец символы ($, #, % и т.д.).Чтобы исключить использование пользователями простых паролей (из словаря популярных паролей) рекомендуется периодически выполнять аудит паролей в домене.
- Хранить пароли, использую обратимое шифрование (Store passwords using reversible encryption) – пароли пользователей в базе AD хранятся в зашифрованном виде, но иногда нужно предоставить доступ некоторым приложениям к паролю. При включении этой политики пароли хранятся в менее защищенной виде (по сути, в открытом виде), что небезопасно (можно получить доступ к базе паролей при компрометации DC). При включении этой опции нужно дополнительно защищать пароли привилегированных пользователей на удаленных площадках с помощью внедрения Read-Only контроллеров домена (RODC).
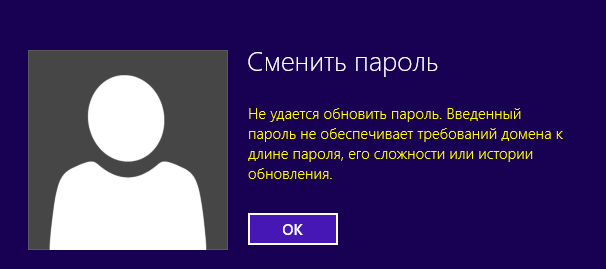
Если пользователь попытается задать пароль, которые не соответствует политике паролей в домене, Windows выдаст ошибку:
Не удается обновить пароль. Введенный пароль не обеспечивает требований домена к длине пароля, его сложности или истории обновления.
Unable to update the password. The value provided for the new password does not meet the length, complexity, or history requirements of the domain.
Обычно вместе с политикой паролей нужно настроить параметры блокировки пользователей при неправильном введении пароля. Эти настройки находятся в разделе GPO: Политика блокировки учетной записи (Account Lockout Password):
- Пороговое значение блокировки (Account Lockout Threshold) – через сколько попыток набрать неверный пароль учетная запись пользователя будет заблокирована;
- Продолжительность блокировки учетной записи (Account Lockout Duration) – длительность блокировки учетной записи, в течении которой вход в домен будет невозможен;
- Время до сброса счетчика блокировки (Reset account lockout counter after) – через сколько минут счетчик неверных паролей (Account Lockout Threshold) будет сброшен.
Если учетные записи блокируются слишком часто, вы можете найти компьютер/сервер источник блокировки так.
Настройки парольных политик домена Active Directory по-умолчанию перечислены в таблице:
| Политика | Значение по-умолчанию |
| Enforce password history | 24 пароля |
| Maximum password age | 42 дня |
| Minimum password age | 1 день |
| Minimum password length | 7 |
| Password must meet complexity requirements | Включено |
| Store passwords using reversible encryption | Отключено |
| Account lockout duration | Не определено |
| Account lockout threshold | 0 |
| Reset account lockout counter after | Не определено |
Управление параметрами политики паролей AD с помощью PowerShell
Для просмотра настроек и изменения конфигурации политики паролей в AD можно использовать командлеты PowerShell из модуля Active Directory:
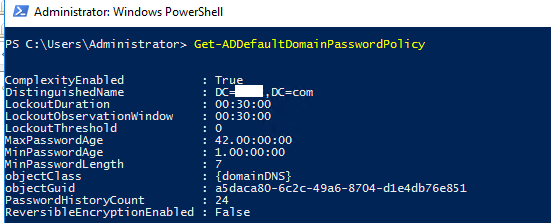
Вывести настройки дефолтной политики паролей:
Get-ADDefaultDomainPasswordPolicy
ComplexityEnabled : True
DistinguishedName : DC=winitpro,DC=ru
LockoutDuration : 00:30:00
LockoutObservationWindow : 00:30:00
LockoutThreshold : 0
MaxPasswordAge : 42.00:00:00
MinPasswordAge : 1.00:00:00
MinPasswordLength : 7
objectClass : {domainDNS}
objectGuid :
PasswordHistoryCount : 24
ReversibleEncryptionEnabled : False
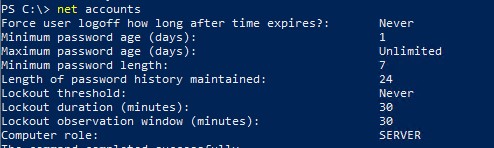
Или с помощью команды:
net accounts
Также вы можете узнать текущие настройки политики паролей AD на любом компьютере в отчете результирующей политики, сгенерированном с помощью консольной утилиты gpresult.
Вывести информацию о том, когда пользователь менял пароль последний раз, и когда истекает его пароль:
net user aivanov /domain
Изменить параметры политики паролей AD:
Set-ADDefaultDomainPasswordPolicy -Identity winitpro.ru -MinPasswordLength 14 -LockoutThreshold 10
Несколько парольных политик в домене Active Directory
С помощью групповых политик на домен можно назначить только одну политику, которая будет действовать на всех пользователей без исключения. Даже если вы создадите новую GPO с другими парольными настройками и примените ее к OU с пользователями, эти настройки фактически не применяться.
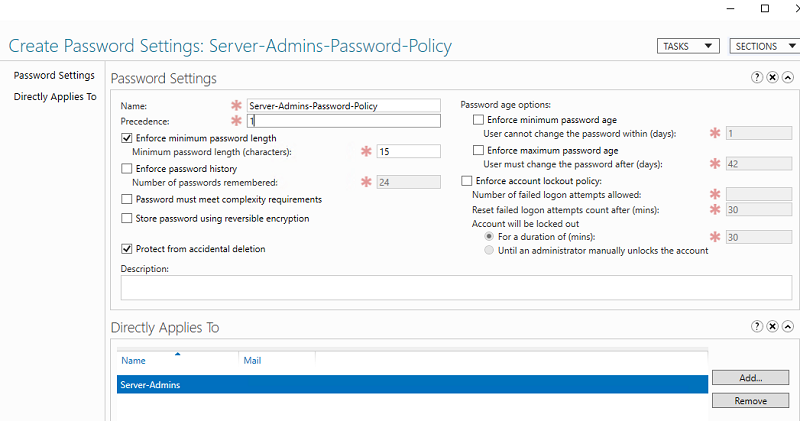
Начиная с версии Active Directory в Windows Server 2008 с помощью гранулированных политик паролей Fine-Grained Password Policies (FGPP) можно применять индивидуальный параметры политики паролей для конкретных пользователей или групп. Например, вы хотите, чтобы пользователи из группы Server-Admins использовали пароли с минимальной длиной 15 символов.
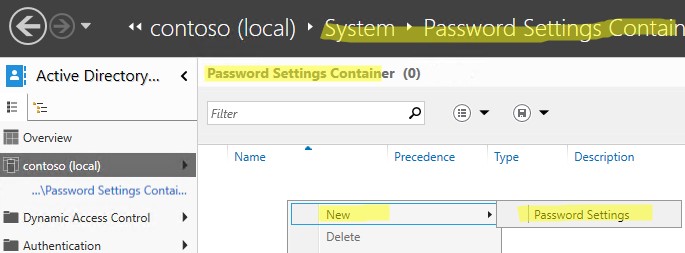
- Откройте консоль Active Directory Administrative Center (
dsac.exe
); - Перейдите в раздел System -> Password Settings Container и создайте новый объект PSO (Password Settings Object);
- В открывшемся окне укажите название политики паролей и ее приоритет. Включите и настройте параметры парольной паролей, которые вы хотите применить. В разделе Directly Applies to нужно добавить группы или пользователей, для которых должны применяться ваши особые настройки политики паролей.
Чтобы проверить, применяются ли к конкретному пользователю особая политика паролей, выполните команду:
Get-ADUserResultantPasswordPolicy -Identity aivanov
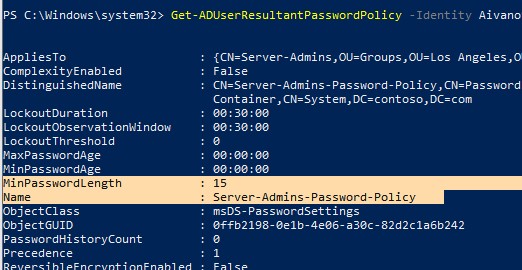
Команда выведет результирующие настройки политики паролей, которые дейсвтуиют на пользователя.
Салимжанов Р.Д
Настройка парольной политики в Windows 10 важна для обеспечения безопасности вашего устройства и данных. Включение и соблюдение парольных политик помогают защитить ваш компьютер от несанкционированного доступа и предотвратить утечку конфиденциальных данных.
Для настройки парольной политики в Windows 10, можно использовать инструменты локальной групповой политики или через Windows PowerShell.
Чтобы настроить парольную политику через локальную групповую политику, выполните следующие шаги:
Нажмите Win + R, чтобы открыть окно «Выполнить», введите gpedit.msc и нажмите Enter.
В локальной групповой политике перейдите в «Конфигурация компьютера», «Настройки Windows», «Параметры безопасности», «Политика паролей».
В этом разделе мы можем настроить различные параметры парольной политики, такие как минимальная длина пароля, требования к сложности пароля, максимальный период действия пароля и другие.
Давайте немного поиграемся и выставим параметры.
Минимальная длина пароля:
Число уникальных паролей:
Сложность пароля:
Если вдруг, кто-либо не понимает какой-либо из параметров window прекрасным образом предоставил кнопочку “Объяснение”, где о каждом из них можно прочитать.
Запускаем PowerShell Windows от имени Администратора.
Далее прописываем команду net accounts, она используется для просмотра и конфигурирования политик учетных записей в домене. С помощью этой команды можно просмотреть текущие настройки политик учетных записей, такие как минимальная и максимальная длина пароля, время протухания пароля и другие параметры.
А далее пользуемся командами для настройки парольной политике:
— minpwlen: Этот параметр определяет минимальную длину пароля, которая должна быть установлена для пользователей. Например, net accounts /minpwlen:8 устанавливает минимальную длину пароля равной 8 символам.
— maxpwage: Этот параметр определяет максимальный возраст пароля, после которого пользователь должен его изменить. Например, net accounts /maxpwage:90 устанавливает максимальный возраст пароля в 90 дней.
— minpwage: Этот параметр определяет минимальный возраст пароля, после которого пользователь может его изменить. Например, net accounts /minpwage:1 устанавливает минимальный возраст пароля в 1 день.
— uniquepw: Этот параметр определяет, можно ли использовать предыдущие пароли при изменении пароля. Значение yes означает, что предыдущие пароли запрещены, а no — что позволяется использовать предыдущие пароли. Например, net accounts /uniquepw:yes запрещает использование предыдущих паролей.
Пример роботы net accounts /minpwlen:8
Ну вроде все, здесь все очень легко. Точно также можно настроить политику паролей на сервере Windows 19.
В целом, настройка парольной политики в Windows способствует обеспечению безопасности вашего устройства и данных и является важным элементом защиты в мире цифровых технологий.
1) Пароль не отвечает требованиям политики — как исправить? // [электронный ресурс]. URL: https://remontka.pro/password-doesnt-meet-requirements/ (дата обращения 24.07.2024).
3) Настройка AD GP: Тонкая настройка политики паролей в домене Active Directory // [электронный ресурс]. URL: https://www.youtube.com/watch?v=zQeliHLUdQI (дата обращения 24.07.2024).
One of the most common ways for attackers to slip into a corporate network is by compromising the username and password of a legitimate user account. Usernames are typically trivial to guess because they follow an established standard in a given organization, such as FirstnameLastname@domain.com.
Unfortunately, compromising basic passwords is also surprisingly easy for threat actors today. For example, they can run a program that tries out various potential passwords for a particular user account. When they hit the right one, they can slip into the network and begin moving laterally to steal sensitive data, unleash ransomware, or cause other damage.
Accordingly, it’s essential to establish a strong password policy that makes passwords difficult to guess. If your organization uses Active Directory (AD) as its primary identity store, this article can help. It explains the available domain password policy settings in AD, shows how to check your current policy, and details the modern password policy best practices to follow. Then it explores how third-party solutions can help you reap the benefits of strong password policies without frustrating users or increasing helpdesk call volume.
Benefits of Strong Password Policies
Password policies set standards for password composition, such as minimum password length and complexity requirements. They can also prevent the reuse of previous passwords, control how often passwords must be changed, and even ensure that an excessive number of failed login attempts will result in account lockout.
Having strong and consistent password requirements for all user accounts policy can significantly reduce the risk of account compromise by thwarting password spraying, brute force, and credential-stuffing attacks. Moreover, having strong password policies is necessary for compliance with a wide range of regulations and industry standards, such as HIPAA and GDPR.
How to Configure Active Directory Password Policies
How to Configure Your Password Policy
To configure the Password Policy, open the Group Policy Management Console (GPMC) on a Windows server and navigate to Computer Configuration > Windows Settings > Security Settings > Account Policies. Select Password Policy and configure each of the policy settings on the right.
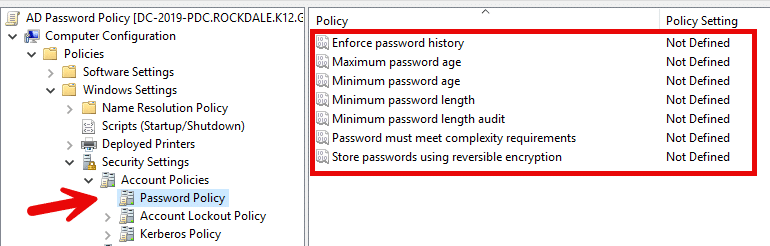
What settings should you choose? Approaches to password management have evolved significantly in recent years, with current best practices placing less emphasis on frequent password changes and more on password strength. The default settings from Microsoft should be regarded as a starting point; for strong security and compliance, consider the following guidance:
| Setting | Description | Default | Best Practices |
| Enforce password history | The number of unique passwords a user must create before reusing an old password | 24 | Enforce password history to prevent users from reusing old passwords repeatedly. |
| Maximum password age | How long a password can exist before it expires and the user must choose a different one | 42 days | Consider setting a high maximum password age and forcing users to change their passwords only when an event like a breach makes it prudent. |
| Minimum password age | How long a password must exist before the user is permitted to change it | 1 day | Keep the default setting to prevent users from circumventing the “enforce password history” setting by performing multiple password resets in a row in order to reuse a preferred password. |
| Minimum password length | The fewest number of characters a password can have | 7 | Microsoft recommends a setting of at least 12 characters because modern password cracking tools can crack 8-character strings in seconds. |
| Minimum password length audit | Allows administrators to audit password changes that would violate a potential new minimum password length policy before actually enforcing it. | 1 | Microsoft recommends leaving the auditing policy enabled for three to six months to detect all software that does not support the proposed minimum password length. |
| Password must meet complexity requirements | Controls whether passwords must meet the following two requirements: A password may not contain the user’s account name value or display name.A password must include characters from 3 of the following categories:Uppercase letters Lowercase letters Base 10 digits Special characters, such as $ or % | Enabled | Keep the password complexity setting enabled. Requiring passwords to meet complexity requirements can slow down automated attacks and reduce the likelihood of users reusing passwords across multiple accounts. |
| Store passwords using reversible encryption | Supports apps that require users to enter a password for authentication | Disabled | Keep this setting disabled to prevent attackers from decrypting passwords that they manage to steal. |
How to Configure Your Account Lockout Policy
You should supplement your Password Policy with an Account Lockout Policy to ensure that adversaries do not get unlimited attempts to guess an account password.
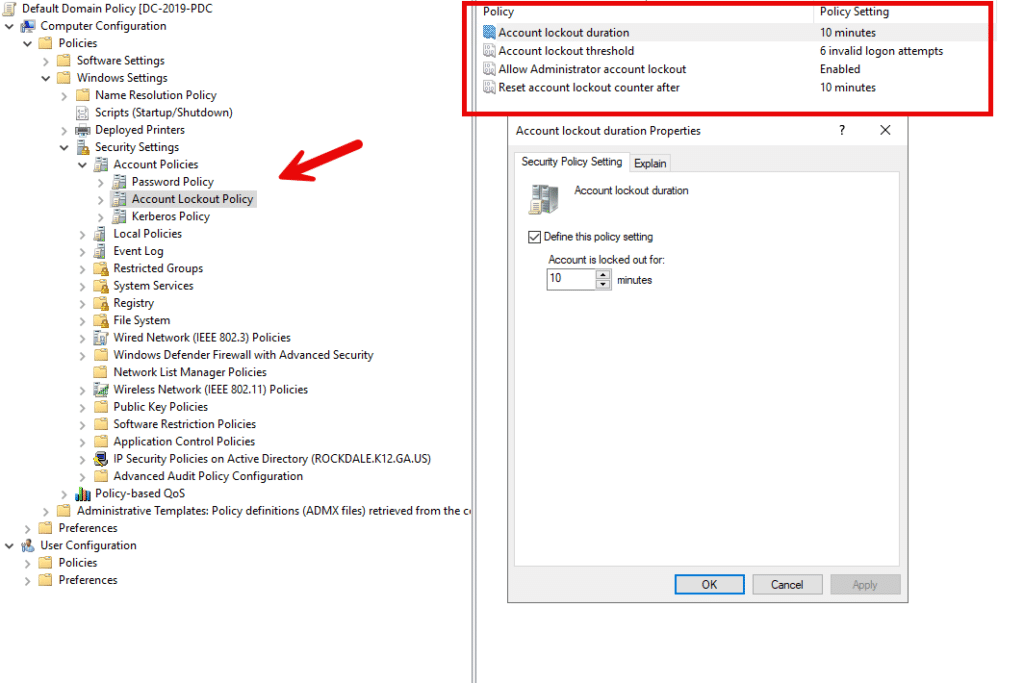
In GPMC, under Account Policies, select Account Lockout Policies. The available settings will appear on the right. In particular, you can specify how many failed logon attempts will trigger a lockout and how long the lockout will last.
Account lockout duration: The number of minutes that an account will be locked once the maximum number of failed login attempts has been reached.
Account lockout threshold: The number of failed login attempts that will trigger a lockout of the account
Allow Administrator account lockout: Determines whether the built-in Administrator account will be subject to the account lockout policy.
Reset account lockout counter after: Determines the number of minutes that must elapse after a failed login attempt before the failed login attempt counter is set back to zero.
How to Modify Your Password Policies
At some point, you may need to update your Password Policy or Account Lockout Policy. For instance, you might want a different setting after a security incident or need to comply with new regulatory requirements. Modifying your existing password policy GPO is as easy as returning to GPMC and altering the settings. The process takes mere minutes to complete.
How to Create Different Password Policies for Different Groups
Active Directory supports fine-grained password policies, which enable you to apply different policies to different groups and users. (Note that your forest functional level must be at least Windows Server 2008.) For example, you can require high-risk groups like admins to have longer passwords and change them more frequently than other users.
You can create and manage fine-grained password policies in two ways:
- In Active Directory Management Center (ADAC), click on your domain, navigate to the System folder, click on the Password Settings container, and configure a Password Settings object (PSO). Then apply the PSO to the desired groups.
- Alternatively, you can use the PowerShell command New-ADFineGrainedPasswordPolicy.
How to Monitor and Troubleshoot Password Policy
How to Check Password Policy in Active Directory
You should keep a close eye on your Active Directory password policy settings. Methods for doing this include the following:
- Group Policy Management Console — One option is to use GPMC, as shown earlier.
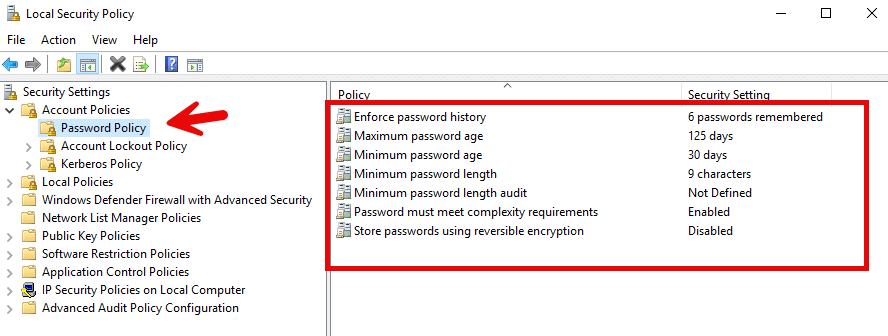
- Local Security Policy — To open this tool on a domain-joined computer, type secpol.msc in the Run dialog or search bar. Then navigate to the Password Policy settings.
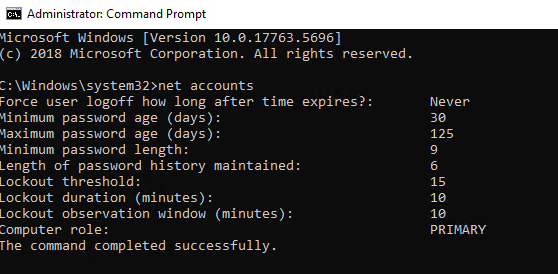
- Command prompt — You can open a command prompt with administrative privileges and use the command net accounts to display the current password policy settings.
- PowerShell — Another way to display the domain’s password policy settings is to use the Get-ADDefaultDomainPasswordPolicy command.
How to Troubleshoot Password Policy Issues
If a user is not receiving the most up-to-date password policy, you can run the following commands on their machine to investigate and attempt to resolve the problem:
- gpresult /r — Shows the GPOs applied to the user and computer
- gpupdate /force — Applies the current GPO settings
Password policy issues can also be related to problems with domain controller (DC) replication — if not all DCs have the same password policy settings, users might experience inconsistent results depending on which DC they authenticate to. To view any replication failures or delays between domain controllers, use the repadmin /replsummary command.
Overcoming Common Password Policy Challenges
The most fundamental challenge in implementing password policies is balancing the desire for strong security with the reality that users often respond to overly strict rules in ways that undermine security. For example, requiring frequent password changes mitigates the risk from stolen password databases — but it can lead users to engage in workarounds that undermine security, such as choosing weaker passwords or simply incrementing a number at the end their password each time. Similarly, requiring users to create long and complex passwords reduces the risk that hackers will be able to guess or crack those passwords to gain access to the corporate network. However, users might resort to writing down their passwords to avoid frustrating lockouts.
Proper communication can help mitigate this problem. Security teams should not only tell users what the password requirements are but explain why they are necessary and how trying to circumvent them can lead to breaches and other security incidents. Whenever the password policy is changed, be sure to have your help desk team ready to provide extra support for users.
There are also third-party tools that can help. In particular, consider the following types of solutions:
- Password policy enforcement software enables you to implement changes to password policy gradually, providing a grace period during which users are encouraged but not forced to comply with the new requirements.
- Password manager tools make it easy for users to comply with strict policies. The software will generate and store a strong and unique password for each of their accounts and enter it for them whenever it is needed. That way, a user needs to create and remember only one password — the one for the password manager application.
- Self-service password reset software enables users to securely reset or change their own passwords and unlock their accounts without calling the help desk. Since lockouts are less painful, users are less likely to try to avoid them with insecure workarounds.
Conclusion
Strong password policies are a key element in a robust cybersecurity strategy. By following the best practices detailed here, you can reduce the risk of account takeover by adversaries, thereby enhancing security and compliance.
To add an extra layer of security, require multifactor authentication (MFA) instead of just a user ID and password, especially for risky use cases such as administrative logons and requests to access sensitive or regulated data.
For more information, read our password policy best practices for strong security in AD.
FAQ
What are password policies in Active Directory?
AD Group Policy offers a Password Policy that enables administrators to establish standards for user passwords. For example, they can establish a minimum password length, prevent the reuse of previous passwords, and control how often passwords must be changed.
Where can I see password requirements in Active Directory?
You can view the Group Policy password policy settings using any of the following methods:
- Group Policy Management Console — Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Password Policy.
- PowerShell — Use the Get-ADDefaultDomainPasswordPolicy cmdlet.
- Local Security Policy tool — On a domain-joined computer, run secpol.msc.
- Active Directory Administrative Center — Check the Password Settings container.
How do I edit the password policy in Active Directory?
You can easily edit the AD password policy using the Group Policy Management Console. In most cases, the password settings will be a part of the Default Domain policy.
How can I check password expiry in Active Directory?
There are multiple ways to do this. Here are two options:
- In Group Policy Management Console, navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Password Policy.
- Run the following PowerShell command: Get-ADDefaultDomainPasswordPolicy | Select MaxPasswordAge.
How long can an AD password be?
The maximum length for an AD user account password is 256 characters. However, for standard users, 12–14 characters will suffice.
What is password complexity?
Password complexity refers to rules that control the composition of passwords themselves. The goal is to prevent users from selecting weak passwords, such as a simple dictionary word or name, which are easier for hackers to guess or crack. When enabled, the AD password complexity policy forces users to choose passwords that:
- Do not contain the user’s account name value or display name
- Do include characters from three of the following categories: Uppercase letters, lowercase letters, base 10 digits, and special characters such as $ or %
How should I assign a Group Policy for passwords?
In Active Directory, password policies are configured and applied using Group Policy. While Microsoft recommends that group policies, in general, be assigned to at the organizational unit (OU) level, it is a best practice to control GPO password policy settings using the Default Domain Policy, which applies to all users and computers in the Active Directory domain. This is to ensure that the password policy is applied to all domain user accounts.
Ian has over two decades of IT experience, with a focus on data and access governance. As VP of Pre Sales Engineering at Netwrix, he is responsible for ensuring smooth product deployment and identity management integration for customers worldwide, His long career has positioned him to serve the needs of organizations of all sizes, with positions that include running the security architecture team for a Fortune 100 US financial institution and providing security solutions to small and medium businesses.

Windows Gpo Password Policy is a powerful tool that helps protect users in a Windows environment. It ensures that users make use of secure passwords and have strong security measures in place to keep their accounts safe. By making sure that passwords are strong and up to date, Windows Gpo Password Policy provides a reliable solution for keeping user data secure. With stronger password control, it can help protect against potential malicious attacks, reducing the chances of data loss or theft. With long and complex passwords and regular updates, Windows Gpo Password Policy can safeguard user passwords and accounts from malicious actors. This makes it an essential feature for companies who want to ensure that their data is secure.
1. What Is Windows GPO Password Policy?
Windows GPO Password Policy Basics
Windows GPO (Group Policy Object) is a powerful mechanism available in Windows Active Directory to help protect your network. It includes a password policy that outlines the parameters under which users can create and manage their passwords. This policy establishes the rules for how frequently passwords must be changed, the complexity of passwords created, and other considerations for creating secure passwords.
The first step in setting up a Windows GPO password policy is to understand the limits set by the policy. To strengthen security, passwords must contain at least eight characters and contain at least three out of four character sets: uppercase letters, lowercase letters, numbers, and symbols. Additionally, users must frequently change their passwords (every 60-90 days is recommended). Other restrictions, such as not using previously used passwords, preventing accounts from being locked after several incorrect attempts, and disabling blank passwords, can also be enabled.
By setting up a GPO password policy, you’ll ensure that your network is protected from malicious attackers and inappropriate password creation practices. All users will be encouraged to create secure, frequent passwords that follow the rules set by the GPO.
2. Key Benefits of Windows GPO Password Policy
1. Improved Security: Windows Group Policy Password Policy (GPO) provides automated security for end-users and their data. With GPO, admins can securely set password requirements – ensuring users choose secure, complex passwords that are difficult to guess. It also sets a minimum password length and requires a password to be changed every 30 days to boost security.
2. Increased Efficiency: By taking the hassle out of setting password policies, Windows GPO makes the process of setting passwords more efficient. It automatically generates complex passwords for users, eliminating the need to create and remember long, complicated strings of characters. It also synchronizes time-out values across multiple computers, bypassing the hassle of manually setting them up each time. In addition, Windows GPO can be used to selectively lock accounts and create audit trails for improved monitoring and archiving.
3. How to Implement Windows GPO Password Policy
Windows Group Policy Objects (GPOs) allow administrators to centrally manage settings across different computers in a network. Creating effective password policies is an important step in enhancing security throughout the network. Here are the steps to implementing these policies in Windows:
- Step 1: Open the Group Policy Management Console and create a new policy or edit an existing one.
- Step 2: Access the ‘Password Policy’ settings and change the minimum length, complexity, and expiration time as required.
- Step 3: Ensure that all other organizational security policy requirements are accounted for, such as forcing information security-related updates.
- Step 4: Link the GPOs to the relevant group of computers in the organizational hierarchy.
Once the GPOs have been configured, the changes need to be applied to active computers. Select the domain or organizational unit you wish to apply the policies to, and now select ‘Group Policy Update’. Your new security policies will now be applied to all computers in the given domain.
4. Make Sure Your Windows GPO Password Policies Are Secure
Setting up good password policies can help protect your business from data breaches caused by hackers. Windows allows you to customize your password policy to ensure the best security for your business. Here’s how you can make sure your Windows password policies are secure:
- Set an optimum password length – Short passwords can be easily guessed, but long ones can be hard to remember. A good password should have at least eight characters. The longer it is, the harder it is to break.
- Disable guest accounts – People who don’t have an account for your business shouldn’t be allowed to access your network. With guest accounts enabled, hackers can easily gain access to your data.
- Enable passphrase recovery – Passphrases are secure and easy to remember. However, if your users forget their passphrase, make sure you have a recovery option so that they can regain access to the network.
- Set an expiration date – Passwords should be changed regularly to ensure that hackers can’t obtain access to your data. Set an expiration date in the policy so that passwords are changed automatically after a certain period of time.
Windows GPO is an effective way of creating secure passwords for your business. Following these tips will help ensure that your passwords are kept safe and secure, protecting your business from cyber threats.
Windows Gpo Password Policy allows administrators to define fine-grained password policies for their organization. These policies include settings for password complexity, such as requiring special characters, uppercase letters, and a minimum length for passwords.
The default domain password policy applies to all user accounts in a domain, including domain controllers and admin accounts. Weak passwords, shorter passwords, and common passwords are all security risks that these policies aim to mitigate. In addition, the policy includes requirements for password expiration, history, and lockout settings to enhance security.
The use of multi-factor authentication and regular password audits are recommended to further safeguard against credential stuffing attacks and compliance failures. Overall, a robust password policy is essential for protecting digital identities and sensitive data in today’s interconnected world.
Windows Group Policy Objects (GPO) provide administrators with the ability to define and enforce password policies within their organization. The default domain policy allows for the configuration of settings such as uppercase characters, password lists, and the reuse of previous passwords. Security Settings within Windows GPOs can also govern requirements for consecutive characters, Unicode characters, and the disablement of certain settings.
It is crucial for organizations to establish strong password standards for user passwords, corporate passwords, and device account passwords to protect against security threats. By utilizing password dictionaries, admins can verify the strength of passwords and ensure compliance with company standards.
The implementation of complex password requirements, such as the inclusion of non-alphabetic characters and the enforcement of lockout thresholds, can enhance the security of the network. Through the use of tools like Specops Password Auditor, admins can conduct Active Directory password audits to identify weak passwords and make necessary adjustments to the password policies. Overall, a robust password policy implemented through Windows GPOs is essential for maintaining the security of an organization’s network and preventing unauthorized access.
Benefits of Windows GPO Password Policy
| Key Benefit | Explanation |
|---|---|
| Improved Security | Automated security for end-users and data with secure password requirements. |
| Increased Efficiency | Streamlined process of setting passwords and synchronization of time-out values. |
| Enhanced Monitoring | Selective account locking, audit trails, and monitoring enhancements. |
| Central Management | Central management of password policies across the network via Group Policy Objects. |
| Customizable Policies | Customizable settings for password length, complexity, and expiration time. |
Q&A
Q: What is Windows GPO Password Policy?
A: Windows GPO Password Policy is a set of rules that help protect your computer and the information stored on it. It requires you to set passwords for your accounts and make sure they are strong and secure.
Q: What is a Windows GPO Password Policy?
A: A Windows GPO password Policy is a set of rules defined within a Group Policy Object (GPO) that governs the password settings for user accounts in a Windows domain. The policy includes settings such as Minimum password age, Complexity requirements, Maximum password age, and more to ensure strong password security within the organization.
Q: What are some key components of a Windows Gpo Password Policy?
A: Some key components of a Windows GPO password Policy include settings for password complexity requirements, password expiration policies, lockout policies, and password history. These settings help enforce strong password security and protect against potential password attacks such as brute force attacks and dictionary attacks.
Q: How can a Windows GPO Password Policy help prevent security risks?
A: A Windows Gpo Password Policy can help prevent security risks by enforcing strong password policies, such as requiring the use of complex passwords, setting minimum and maximum password ages, and implementing lockout policies for failed login attempts. By adhering to these policies, organizations can mitigate the risk of unauthorized access and potential security incidents.
Q: What are some best practices for creating a robust Windows Gpo Password Policy?
A: Best practices for creating a robust Windows GPO Password Policy include implementing strong password complexity requirements, setting password expiration periods, enforcing password history policies, and regularly auditing password settings for compliance. It is also recommended to use password management tools to enhance password security and compliance posture.
Q: How can organizations ensure compliance with password security standards through a Windows Gpo Password Policy?
A: Organizations can ensure compliance with password security standards by defining and enforcing strong password policies through a Windows GPO Password Policy. Compliance requirements can include setting stringent password requirements, conducting regular password audits, and actively monitoring password security incidents to maintain a secure environment.
Q: What are some common challenges faced by organizations in managing Windows Gpo Password Policies?
A: Some common challenges faced by organizations in managing Windows GPO Password Policies include enforcing password complexity requirements, addressing password expiration policies, and managing password resets efficiently. Additionally, organizations may struggle with ensuring compliance with password security standards and adapting password policies to evolving security risks.
Source: Microsoft Security Guidelines for Windows
Conclusion
If you’re looking to simplify your password woes and up your security game with Windows GPO policies, look no further than LogMeOnce. LogMeOnce is a free password manager, presented as a secure, convenient and effortless alternative to existing Windows GPO password policies. It offers the convenience and ease of creating and storing passwords in one secure repository without compromising on security or usability. With its strong encryption policies and a robust yet user-friendly interface, LogMeOnce is the ultimate solution to your Windows GPO password policy needs.
Bethany is a seasoned content creator with a rich academic background, blending the art of language with the precision of commerce. She holds a Master of Arts in English Language and Literature/Letters from Bahauddin Zakariya University, a testament to her profound grasp of language and its nuances. Complementing her literary prowess, Bethany also possesses a Bachelor of Commerce from the University of the Punjab, equipping her with a keen understanding of business and commerce dynamics. Her unique educational blend empowers her to craft content that resonates deeply with diverse audiences.
The expiration date of an AD user’s password determines when and how often a user is required to change their domain password. Group Policy is used to configure password expiration in the Active Directory domain. Administrators can improve the security of user and service accounts within organizations by enforcing regular password changes.
If an Active Directory user’s password expires, they won’t be able to log on to the domain or access domain resources until they change their password. The following prompt will appear on the Windows login screen after the user has interactively entered the expired password:
Your password has expired and must be changed.
Configure Password Expiration Settings with Default Domain Policy
By default, the password expiration settings in the domain are configured using the Group Policy Object (GPO).
- Open the Group Policy Management Console (GPMC.msc) on a domain controller;
- Expand the Group Policy Objects container, right-click on the Default Domain Policy and select Edit;
- Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Password Policy. Domain password expiration is configured using is configured using the Maximum password age option. This is the number of days a password can be used before the system requires the domain user to change it. By default, the user account passwords expire after 42 days from the last password change;
- You can edit the default policy value. For example, set the password to expire after 90 days. Save the changes;
- The new value of the password expiration policy will be applied to the DC within 5 minutes. Check new policy settings with the following PowerShell command:
Get-ADDefaultDomainPasswordPolicy |select MaxPasswordAge:
Set the Maximum password age setting to 0 if you want to disable password expiration for users in your domain, so that users’ passwords never expire. In this case, all domain users won’t be required to change their password ever.
How to Get AD User Password Expiration Date
To find out when a specific user’s password expires, you can use PowerShell (requires the PowerShell AD module installed on a computer). Replace alpha with the username you’re need.
Get-ADUser -Identity alpha -Properties "msDS-UserPasswordExpiryTimeComputed" | Select-Object -Property Name, @{Name = "PasswordExpiryDate"; Expression = { [datetime]::FromFileTime($_."msDS-UserPasswordExpiryTimeComputed") } }
This command retrieves the password expiration date for a user.

You can list the password expiration dates for all of your AD users at once. In this example, we’ll only list users without the PasswordNeverExpires option enabled:
Get-ADUser -Filter 'PasswordNeverExpires -eq "False"' -Properties PasswordNeverExpires, "msDS-UserPasswordExpiryTimeComputed" | Select-Object -Property Name, @{Name = "PasswordExpiryDate"; Expression = { [datetime]::FromFileTime($_."msDS-UserPasswordExpiryTimeComputed") } }

Configuring Fine-Grained Password Expiration Policy
The domain-wide Default Domain Policy sets the same password expiration settings for all users. If you want to apply custom (granular) password expiration for specific user groups or individual user accounts, you should use the Fine-Grained Password Policy (FGPP).
The Fine-Grained Password Expiration policies are configured using the Active Directory Administration Center console.
- Open the dsac.exe snap-in and navigate to Domain > System > Password Settings Container;
- Under the Tasks pane, click New → Password Settings;
- Provide a unique name for the password policy, precedence, and the maximum password age in days. Disable other policy options that you don’t want to apply;
- Specify the users or groups to whom the policy should apply by adding them to the “Directly Applies To” section. In this example, we added the CA Server Admins group.
- Click OK to save the password policy.
The FGPE policy will now be applied to the specified user or group, providing a custom password expiration policy that differs from the domain-wide settings.
Also, you can create and Appy fine-grained password expiration policy using PowerShell:
# Create the new Fine-Grained password expiration policy
$policySettings = @{
Name = 'Expire Password after 60-days'
MinPasswordAge = '1.00:00:00'
MaxPasswordAge = '60.00:00:00'
Precedence = 1
}
New-ADFineGrainedPasswordPolicy @policySettings
# Display the new Fine-Grained password expiration policy
Get-ADFineGrainedPasswordPolicy $policySettings['Name']

Now, let’s assign this password expiration policy to target users and AD groups. In this example, we’ll apply the policy to the CA DevOps group and the jsmith user account.
# Add new subjects to the password expiration policy. Add-ADFineGrainedPasswordPolicySubject -Identity 'Expire Password after 60-days' -Subjects 'CA DevOps', 'jsmith' # Display the password expiration policy subjects. Get-ADFineGrainedPasswordPolicySubject -Identity 'Expire Password after 60-days'

Does Microsoft Still Recommend Periodic Password Expiration?
In the modern security baseline, Microsoft recommends you to not implement the password expiration policy, because the periodic password expiration may not be as effective as previously thought. Instead, you should use modern tools to help mitigate this, such as Microsoft Entra Password Protection, Multi-Factor Authentication (MFA), etc.
Cyril Kardashevsky
I enjoy technology and developing websites. Since 2012 I’m running a few of my own websites, and share useful content on gadgets, PC administration and website promotion.