This comprehensive guide explores the most crucial Windows log file locations essential for cybersecurity professionals, including credential logs, system and event logs, malware indicators, and persistence paths. Learn how to use these files for threat hunting, incident response, and digital forensics with actionable insights and a summary table.
Table of Contents
- Credential and Access Logs
- System and Event Logs
- Malware and Threat Hunting Indicators
- Persistence and Startup Investigations
- Windows Log File Locations
- Conclusion
- Frequently Asked Questions (FAQs)
In the world of cybersecurity, access to the right information at the right time can make or break an investigation. When analyzing a compromised Windows system, knowing where to find crucial log files can help you uncover evidence of unauthorized access, malware infections, and persistent threats.
This guide will walk you through the most important Windows log file locations used in digital forensics, incident response, and threat hunting, grouped into four main categories: Credential Logs, Event Logs, Threat Indicators, and Persistence Mechanisms.
Credential and Access Logs
These files are the first stop when you need to investigate how a threat actor may have accessed the system or dumped user credentials.

Key File Locations:
-
C:\Windows\System32\config\SAM
Stores local password hashes. Attackers frequently target this file to extract passwords using tools like Mimikatz. -
C:\Windows\repair\SAM
This is a backup of the SAM file, often overlooked, but can also be targeted to extract credential information. -
C:\Windows\System32\config\SECURITY
Contains security policies and access control settings, which can help track privilege escalations and unauthorized changes.
System and Event Logs
These logs are the backbone of digital forensics, providing information on system changes, user actions, and software behavior.
Key File Locations:
-
C:\Windows\System32\winevt
Stores Windows Event Logs used for event correlation, timeline creation, and alert generation in SIEM systems. -
C:\Windows\System32\config\SYSTEM
Logs system-wide configuration changes, driver loads, and hardware info. Helps in mapping system behavior before and after compromise. -
C:\Windows\System32\config\SOFTWARE
The registry hive that provides details on installed software, version changes, and potential rogue installations.
Malware and Threat Hunting Indicators
When malware strikes, these files can reveal what was executed, when, and by whom — crucial data for forensic timeline reconstruction and lateral movement detection.
Key File Locations:
-
C:\Windows\Prefetch
Tracks recently executed programs. Useful in building a forensic timeline and understanding attacker behavior. -
C:\Windows\AppCompat\Programs\Amcache.hve
Contains data about executed applications, file hashes, and execution paths. Ideal for detecting malicious binaries. -
C:\Users\\NTUSER.dat
A user-specific registry file that holds data on settings and preferences. Often abused to maintain persistence.
Persistence and Startup Investigations
To survive reboots and maintain presence, attackers plant themselves in startup folders or exploit registry keys. These file paths can help uncover such methods.
Key File Locations:
-
C:\Users\\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
Location for user-specific startup programs. Used by both legitimate software and malware for persistence. -
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup
A global startup folder for all users. Malware often drops executables here to run on every boot.
Windows Log File Locations
| Category | File Path | Purpose |
|---|---|---|
| Credential & Access Logs | C:\Windows\System32\config\SAM |
Stores local password hashes |
C:\Windows\repair\SAM |
Backup SAM file (credentials) | |
C:\Windows\System32\config\SECURITY |
Security policies & access settings | |
| System & Event Logs | C:\Windows\System32\winevt |
Windows Event Logs for SIEM & incident tracking |
C:\Windows\System32\config\SYSTEM |
System-wide config and change logs | |
C:\Windows\System32\config\SOFTWARE |
Installed software & registry changes | |
| Malware & Threat Indicators | C:\Windows\Prefetch |
Tracks recently executed files |
C:\Windows\AppCompat\Programs\Amcache.hve |
Logs executed binaries with metadata | |
C:\Users\\NTUSER.dat |
User-specific registry for persistence | |
| Persistence & Startup | C:\Users\\AppData\Roaming\...\Startup |
User startup folder |
C:\ProgramData\Microsoft\Windows\...\Startup |
Global startup folder |
Conclusion
If you’re in digital forensics, threat hunting, or incident response, knowing these Windows log locations can dramatically speed up investigations and help identify suspicious activity more effectively. Tools like Sysinternals, Autoruns, and SIEM platforms can help automate the parsing and monitoring of these logs.
Pro Tip: Always monitor these paths using endpoint detection and response (EDR) tools and alert on unauthorized changes or newly added executables in startup folders.
FAQs
What are Windows log file locations used for in cybersecurity?
They are used to track activities, detect malware, and investigate security breaches on Windows systems.
Where is the SAM file located in Windows?
Located at C:\Windows\System32\config\SAM, it stores local user credentials.
What is the purpose of the SECURITY file in Windows?
It contains security policy and access control data crucial for forensic analysis.
How do attackers use the Prefetch folder?
They analyze Prefetch to determine recently executed files, often revealing attacker activity.
What is Amcache.hve used for?
This registry file logs metadata about executed applications, helpful in threat hunting.
What can be found in NTUSER.dat?
User-specific registry settings often targeted for persistence.
Where are Windows Event Logs stored?
In the C:\Windows\System32\winevt folder.
How does SYSTEM log file help in investigations?
It shows system-wide changes, like driver loads or hardware modifications.
What does the SOFTWARE registry hive track?
It tracks installed applications and configuration changes.
What is a global startup folder?
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup — used by all users for automatic program execution.
How is the Startup folder used in malware attacks?
Malware often places itself here to run every time the system boots.
Can attackers modify NTUSER.dat?
Yes, attackers modify it for stealthy persistence mechanisms.
Why are Prefetch files important in timeline analysis?
They show when and how often applications were executed.
What is the significance of AppCompat Programs logs?
They record execution history, helping spot lateral movement.
What is the difference between SAM and SECURITY file?
SAM stores credentials, while SECURITY handles policy and access rights.
How can I detect persistence via startup paths?
Check both user and global startup folders for suspicious programs.
Are Event Logs useful for SIEM systems?
Yes, they are essential for correlation, alerting, and investigation.
Can deleted logs be recovered?
Sometimes, using forensic tools that read slack or unallocated space.
How do malware authors abuse the Registry?
By adding keys or values that launch malware at startup.
Is it safe to delete the Prefetch folder?
It is not recommended unless necessary, as it impacts system performance and forensic value.
Can the Amcache file be cleared?
Yes, but doing so removes valuable forensic data.
How do I access registry hives for forensic analysis?
Use tools like RegRipper or load them in offline registry editors.
What are common indicators of persistence in logs?
Repeated startup entries, modified NTUSER.dat, and unusual registry keys.
Can logs indicate a brute-force attack?
Yes, via failed login attempts in the SECURITY log.
Are log files readable in plain text?
Some are, while others require tools to parse them.
How do I monitor Windows logs in real-time?
Use EDR tools, Windows Event Viewer, or PowerShell scripts.
What tools analyze these log paths?
Tools like Autoruns, Volatility, RegRipper, and SIEM platforms.
How often should logs be reviewed?
Regularly—daily for high-risk environments or as part of SOC monitoring.
Do attackers delete log files?
Yes, it’s a common tactic to cover tracks post-breach.
What is the best practice for preserving logs during incident response?
Create a forensic image and avoid writing to the drive directly.
Introduction
The Windows event log is an itemized record of the framework, security, and application notices the Windows working framework chairpersons put away to analyze framework issues and anticipate future problems.
Applications and the operating system (OS) utilize these event logs to record significant equipment and programming activities that the manager can use to investigate issues with the operational system. The Windows operating system tracks explicit events in its log documents, like application establishments, security of the executives, framework arrangement procedure on beginning startup, and issues or blunders.
Where are Windows logs stored?
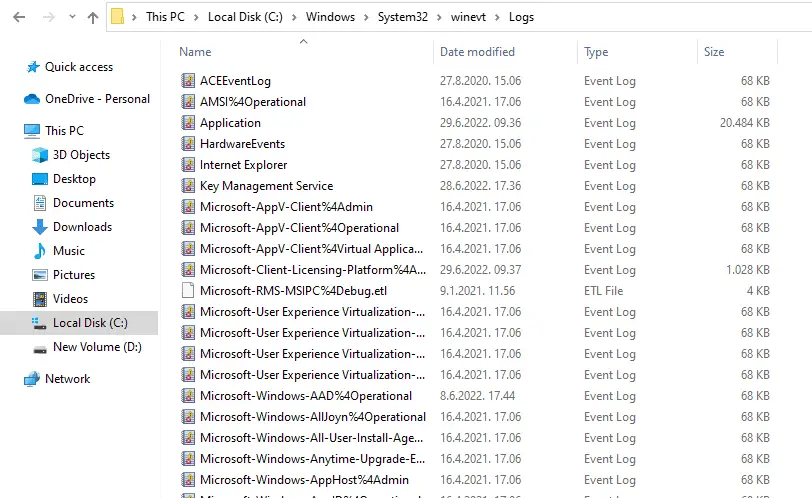
If your installation is on a C drive, the location of the Windows event logs is C: WindowsSystem32winevtLogs. Event log files have the extension .evtx.When a Windows application crashes, the event log stores information about the application name, why the application crashed, and the incident time.
Below is presented Windows 11 log location from 2022:
What is the EVTX file?
EVTX file represents Microsoft Event Viewer logs that users can see in Event Viewer. You can run Microsoft Event Viewer logs using the Windo” “>eventvwr co” m”d. m”c”
The “o”ponents of a Windows event log
Every Event in a log passage contains the accompanying data:
Date: The date the Event happened.
Time: The time the Event occurred.
Client: The client was signed onto the machine when the Event occurred.
PC: The name of the PC.
Occasion ID: A Windows ID number that determines the event type.
Source: The program or part that caused the Event. Type: The sort of Event, including data, cautioning, mistake, security achievement review, or security disappointment review.
For instance, a data event may show up as:
Data 3/19/2021 8:21:15 AM Service Kernel-Event Tracing 1 Logging
An admonition event may resemble:
Cautioning 3/19/2021 10:29:47 AM
By examination, a mistake event may show up as:
Mistake 3/19/2021 AM Service Control Manager 7001 None
A primary event may look like this:
Basic 3/19/2021 8:55:02 AM Kernel-Power 41 (63)
The sort of data put away in Windows event logs
The Windows working framework records events in five zones: application, security, arrangement, framework, and sent events—Windows stores event signs in the C:\WINDOWS\system32\config\ envelope.
Application events are occurrences with the product introduced on the neighborhood PC. If an application, such as Microsoft Word, crashes, the Windows event log will create a section about the issue, the application name, and why it was slammed.
Security events store data depending on the framework, and the ordinary events stored incorporate login endeavors and asset access. For instance, the security log stores a record of the PC checking account certifications when a client attempts to sign on to a machine.
Arrangement events incorporate centered events identifying with the control of spaces, like the area of logs after a plate setup.
Framework events identify with episodes on Windows-explicit frameworks, like the situation with gadget drivers.
Sent events appear from different machines in a similar organization when a chairperson needs to utilize a PC that accumulates numerous logs.
Utilizing the Event Viewer
Microsoft remembers the Event Viewer for its Windows Server and customer working framework to see Windows event logs. Clients access the Event Viewer by tapping the Start catch and entering the Event Viewer into the hunt field. Clients can then choose and investigate the ideal log.
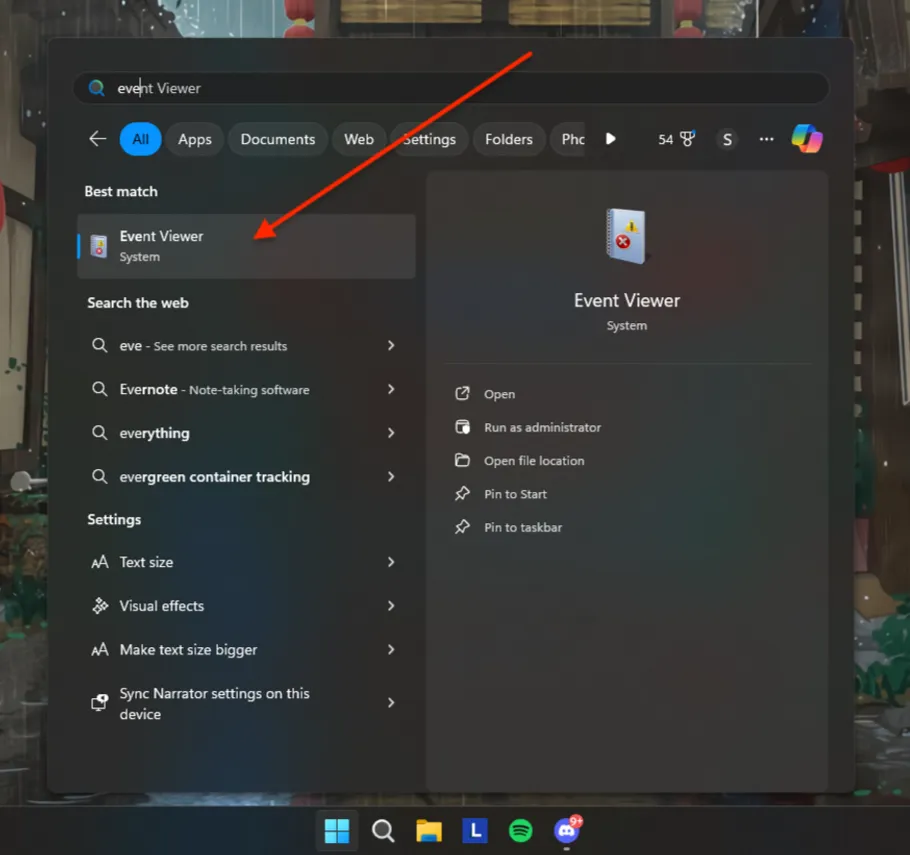
How to open Event Viewer in Windows?
- Press Sta”t” butt”n”
- Click” “Contr” l”Pan” S” s” and Securi” A” m” “s” rating Too”s.”
- Doub “e”clic” “Event “V”ew”r”
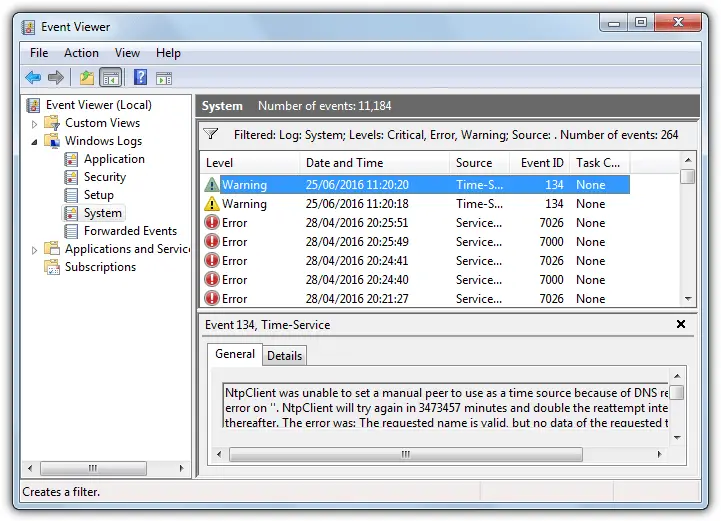
Window” orders each Event with severity based on data, caution, blunders, and the basics.
Most logs comprise data-based events. Logs with this section typically mean the experience happened without an episode or issue. An illustration of a framework-based data event is Event 42, Kernel-Power, which shows the framework is entering rest mode.
Cautioning level events depend on specific events, for example, an absence of extra room. Cautioning messages can focus on potential issues that don’t prompt activity. Occasion 51, Disk illustrates a framework-based admonition identified with a paging mistake on the thmachine’machine’sAsA blunder level demonstrates a gadget may have neglected to stack or work expectedly. Occasion 5719, NETLOGON illustrates a framework mistake whenn’t a safe meeting with an area regulator.
Basic-level events show the most severe issues. Occasion ID 41, Kernel-Power, illustrates a basic framework when a machine reboots without a spotless closure.
Different devices to see Windows event logs.
Microsoft likewise gives the order line utility in the System32 organizer that recovers event logs, runs questions, sends out logs, files logs, and clears logs.
Outsider utilities that work with Windows event logs incorporate SolarWinds Log and Event Manager, providing event connection and remediation, record trustworthiness observation, USB gadget checking, and danger location. Log and Event Manager gathers logs from workers, applications, and organization gadgets.
ManageEngine EventLog Analyzer fabricates custom reports from log information and sends constant instant messages and email alarms dependent on explicit events.
Utilizing PowerShell to question events
Microsoft fabricates Windows event signs in an extensible markup language (XML) design with an EVTX augmentation. XML gives more granular data and a reliable organization for organized information.
Directors can construct convoluted XML inquiries with the Get-WinEvent PowerShell cmdlet to add or reject events from a question. With issues related to corrupted event logs, we recommend you first try a software cleanup of your Windows event log. These software tools, such as ReconLogger or Software Events Cleaner, automatically clean Windows event logs to eliminate all the junk, such as unused files, configuration files, and garbage. Alternatively, try System Reliability; search and filter it by date range and service to find specific issues. The graphs in the Window Event Viewer can help detect subtle behavior changes in your system.
- About
- Latest Posts
The event logs are located in Windows or WINNT directory under %WinDir%\system32\config. These files end in .
- Where is Windows event log file location?
- How do I find Windows event log?
- How do I view the event log in CMD?
- What is system event log?
- What are the 3 types of logs available through the Event Viewer?
- How do I view a log file?
- How do I open event log?
- Where are RDP logs stored?
- What is eventvwr MSC?
- How do I open Event Viewer in Task Manager?
- What does Windows event log do?
- How many Windows event logs are there?
- Why are system logs important?
Where is Windows event log file location?
By default, Event Viewer log files use the . evt extension and are located in the %SystemRoot%\System32\Config folder. Log file name and location information is stored in the registry. You can edit this information to change the default location of the log files.
How do I find Windows event log?
Click Start > Control Panel > System and Security > Administrative Tools. Double-click Event Viewer. Select the type of logs that you wish to review (ex: Windows Logs)
How do I view the event log in CMD?
Start Windows Event Viewer through the command line
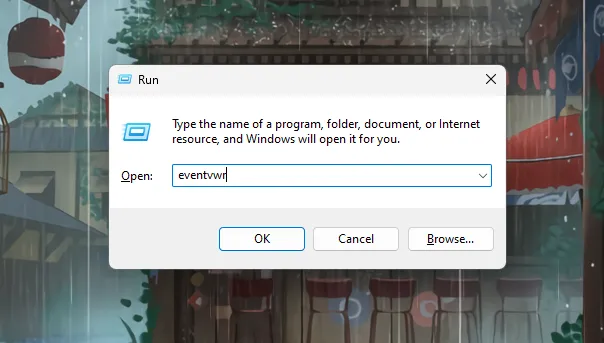
To open a command prompt, click Start , click All Programs , click Accessories and then click Command Prompt . As a shortcut you can press the Windows key + R to open a run window, type cmd to open a, command prompt window. Type eventvwr and click enter.
What is system event log?
The Windows event log is a detailed record of system, security and application notifications stored by the Windows operating system that is used by administrators to diagnose system problems and predict future issues.
What are the 3 types of logs available through the Event Viewer?
Types of Event Logs
They are Information, Warning, Error, Success Audit (Security Log) and Failure Audit (Security Log).
How do I view a log file?
You can read a LOG file with any text editor, like Windows Notepad. You might be able to open one in your web browser, too. Just drag it directly into the browser window, or use the Ctrl+O keyboard shortcut to open a dialog box to browse for the file.
How do I open event log?
To open Event Viewer: Windows versions with the Start menu: Choose Start menu > Control Panel > Administrative Tools > Event Viewer. Select the Application log. Windows versions with the Start screen: Open Search, then type eventvwr.mc to find the Event Viewer.
Where are RDP logs stored?
Every time a user successfully connects remotely, an event log will be recorded in the Event Viewer. To view this remote desktop activity log, go to the Event Viewer. Under Applications and Services Logs -> Microsoft -> Windows -> Terminal-Services-RemoteConnectionManager > Operational.
What is eventvwr MSC?
msc) You can use Event Viewer (Eventvwr. msc) to view logs that can help you to identify system problems when you are able to start the system in safe or normal mode. Application logs The Application log contains events logged by applications or programs. …
How do I open Event Viewer in Task Manager?
Use the Run window to open Event Viewer (all versions of Windows) A rapid method is to open the Run window (Windows + R), type eventvwr. msc in the Open field, and click or tap OK.
What does Windows event log do?
What are Windows Event Logs? At their core, Windows event logs are records of events that have occurred on a computer running the Windows operating system. These records contain information regarding actions that have taken place on the installed applications, the computer, and the system itself.
How many Windows event logs are there?
The Navigation pane is where you choose the event log to view. By default, there are five categories of Windows logs: Application – Information logged by applications hosted on the local machine. Security – Information related to login attempts (success and failure), elevated privileges, and other audited events.
Why are system logs important?
Logging is essential to a network because it gives the ability to troubleshoot, secure, investigate or debug problems that arise in the system. … The logs record messages and times of events occurring on the system. It can also identify system problems that can result in server down time.
If you’re using a Windows server and want to know what happened to your machine, Windows logs are an essential resource. Windows logs record various system activities, errors, and other significant events, providing valuable information for troubleshooting, auditing, and ensuring system integrity. Understanding how to access, interpret, and utilise these logs enables efficient, problem solving, enables security measures and ensures the smooth operation of your system.
In this guide, you will learn about Windows event logs, its different categories, how to filter and create Custom Views.
What is a Windows Event Log?
A Windows event log is a file that keeps track of system events and errors, application issues, and security events. Windows Event log can also provide insights into an application’s behavior by tracking its interactions with other processes and services. With the right knowledge of the information stored in these logs, you can easily diagnose and easily resolve issues within your system and applications.
You can access the windows events logs as follows:
Using the Start Menu:
- Click on the Start button or press the Windows key.
- Type
Event Viewerin the search box and select it from the search results.
Using the Run Dialog:
- Press
Windows + Rto open the Run dialog. - Type
eventvwrand press Enter.
Using the Control Panel:
- Open the Command Prompt and run as administrator.
- Type
eventvwrand press Enter.
You can see the detailed steps below. Now let’s discuss and understand windows events logs in detail.
Understanding Windows Event Logs categories & Types
There are different Windows logs, each serving a specific purpose in tracking and recording events related to your system, applications, and security. They include:
- System Events: System events log information is about the core operations of your Windows operating system. System events are essential for maintaining your system’s health and functionality because it records events related to the system’s hardware and software components. Some system events are as follows:
- Hardware Failures: Logs any issues related to hardware components, such as disc failures or memory errors.
- Driver Issues: Records events related to the loading, unloading, or malfunctioning of device drivers. This helps in identifying driver-related problems that could affect system stability.
- System Startups and Shutdowns: Tracks the times when the system starts up or shuts down. This can be useful for understanding system uptime and diagnosing issues related to improper shutdowns or startup failures.
- Application Events: Data related to software applications running on the system includes application errors, warnings, and informational messages. If you are using a Windows server to run your production-level application, you can use the application errors, warnings, and messages provided here to solve the issue. There are different types of Application events some are as follows:
- Application Errors: Application errors are events generated by software applications when they encounter issues that prevent them from functioning correctly.
- Warnings: Logs warnings from applications about potential issues that might not be critical but could lead to problems if not addressed.
- Informational Messages: Provides general information about application activities, such as successful operations or status updates, helping to understand the normal functioning of applications.
- Security Events: Security events are logs that capture all security-related activities on your Windows system. They are essential for monitoring, maintaining, and auditing the security of your system. These events help detect unauthorised access attempts, monitor access to sensitive resources, and track changes to system policies. Some security events are as follows:
- Successful and Failed Login Attempts: Successful and failed login attempts are critical events that are logged by a system to monitor access and ensure security. These logs provide valuable insights into user activity, helping to detect unauthorised access attempts and identify potential security threats.
- Resource Access: These events log attempts to access protected resources such as files, folders, or system settings. Monitoring these logs ensures that sensitive data is accessed appropriately and helps identify unauthorised access attempts.
- System Policy Changes: These logs record any changes to system policies, including modifications to user permissions or security settings. This is important for auditing purposes and ensuring compliance with security policies, helping to maintain the integrity and security of the system.
- Setup Events: Setup events are logs that contain detailed information about the installation and setup processes on your Windows system. These logs are valuable for diagnosing and resolving issues that occur during the installation or configuration of software and system components. Some Setup events are as follows:
- Installation Processes: Installation processes refer to the series of steps and operations carried out to install software, updates, or system components on a Windows system. It contains log details about software installation, updates, or system components. This helps in diagnosing issues related to incomplete or failed installations.
- Setup Configurations: Records information about system configurations during the setup process. This can be useful for understanding your system’s initial setup and configuration.
- Forwarded Events: Forwarded events are logs sent from other computers to a centralised logging server. This is particularly useful in larger environments where centralised log management is needed. They include:
- Logs from Remote Systems: Collects event logs from multiple systems, allowing for centralised monitoring and management.
- Centralised Logging Scenarios: Useful for organisations that need to aggregate logs from various systems to a single location for easier analysis and monitoring.
Accessing the Windows Event Viewer
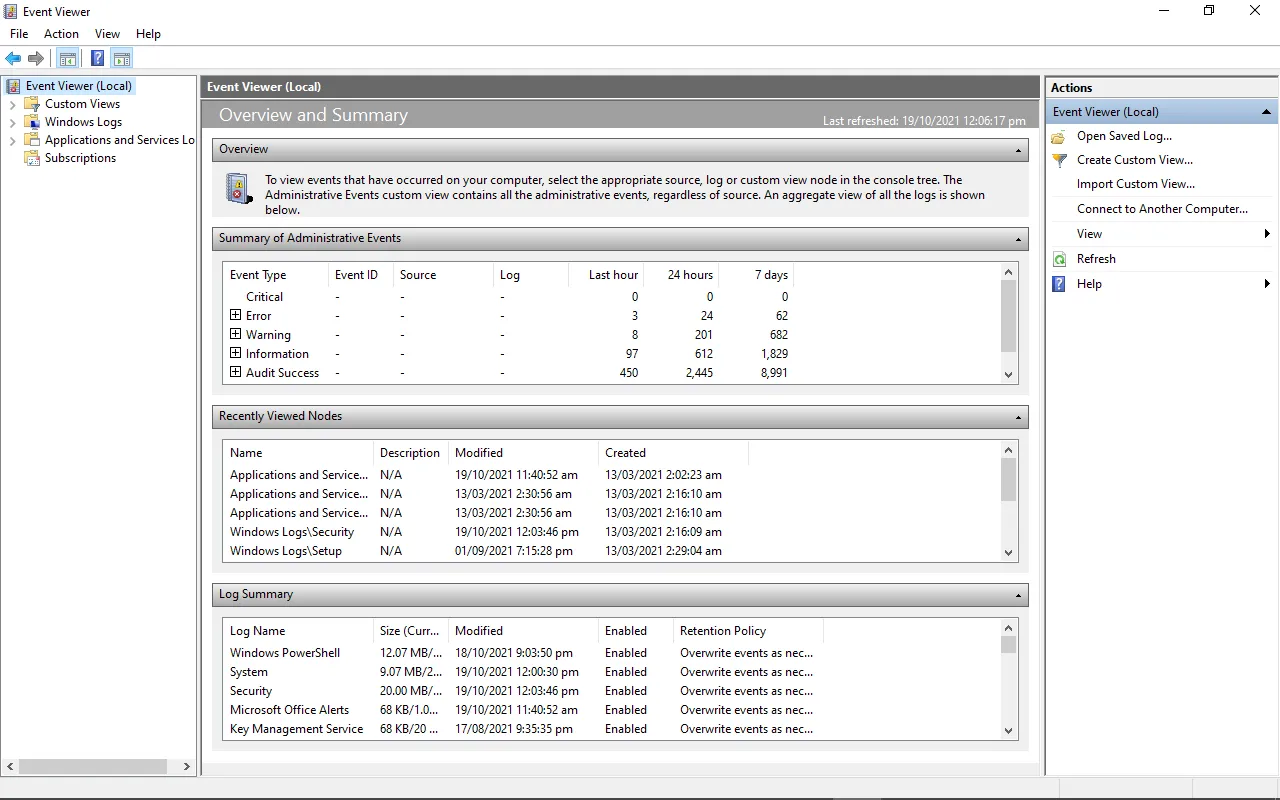
Windows Event Viewer is a Windows application that lets you see your computer’s logs, warnings, and other events. Each application you open generates entries that are recorded in an activity log, which can be viewed from the Event Viewer.
There are several ways to access the Windows Event Viewer. Here are some of them:
-
Using the Start Menu:
- Click on the Start button or press the Windows key.
- Type
Event Viewerin the search box.
Using start menu to open Event viewer — Select Event Viewer from the search results which will popup something like this.
Event Viewer main page 2. Using the Run Dialog: — Press
Windows + Rto open the Run dialog. — Typeeventvwrand press Enter.Windows Run App to open Event Viewer Windows Event viewer landing page 3. Using Control Panel: — Open the Command Prompt and run as administrator
Open CMD as Administrator from start menu — Once open, type
eventvwrand press enter, and you will be redirected to Event Viewer page.CMD terminal
Windows Log Location
Windows event logs are stored in files located in the C:\\Windows\\System32\\winevt\\Logs directory. Each log file corresponds to a specific log category, such as System, Application, or Security. It may differ depending on which version of Windows you are using.
The main event log files are:
- Application.evtx: Logs events from applications and programs.
- Security.evtx: Logs security events like successful or failed logins.
- System.evtx: Logs events related to Windows system components and drivers
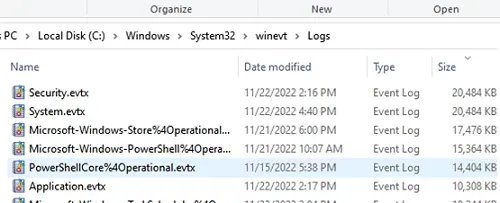
You can find many other log files which could be related to system operations & other processes that are happening inside the Windows System. Windows 11uses the .evtx format rather than using the classic EVT format.
Understanding Event Viewer Entries
Event Viewer entries provide detailed information about each logged event. It is like a log book for your Windows system. They record important happenings within the system, including applications, systems, security, failed events, etc. Understanding these entries is key to effective log management.
The key components of an Event Viewer entry are:
- Date and Time: When the event occurred.
- Source: The application or system component that generated the event.
- Event ID: A unique identifier for the event type.
- Level: The severity of the event (Information, Warning, Error, Critical).
- User: The user account under which the event occurred.
- Computer: The name of the computer where the event was logged.
- Description: Detailed information about the event.
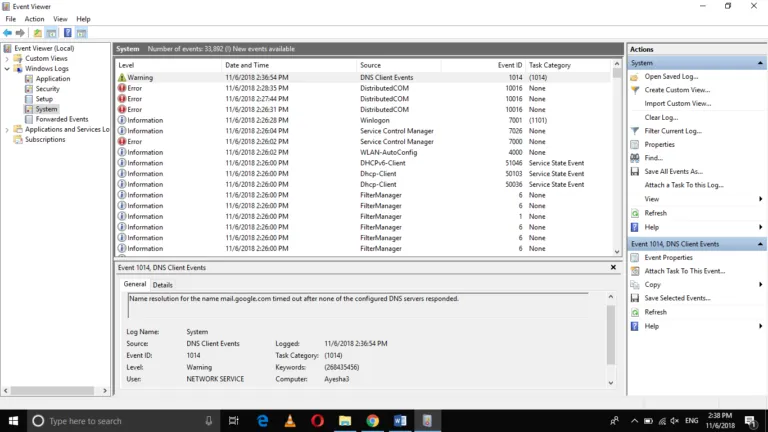
Each event in the Event Viewer has a severity level, indicating the importance and type of the event:
- Information (Green Light): These events resemble a green traffic light, signifying smooth sailing. They indicate successful operations or occurrences within your system.
- Warning (Yellow Light): Treat these entries with caution, like a yellow traffic light. They signal potential issues that warrant attention but might not cause immediate problems.
- Error (Orange Light): Think of error entries as an orange traffic light; proceed with care. They denote significant problems that could affect system functionality. Imagine an error message indicating a driver failure.
- Critical (Red Light): Critical entries are akin to a red traffic light; stop and address the situation immediately. They represent severe errors that have caused a major failure. A critical event might report a complete system shutdown or a critical service crashing.
Filtering and Custom Views
Event Viewer allows you to filter events using a variety of parameters, including date, event level, source, and more. Consider the following scenario: your system exhibits weird behaviour, but the Event Viewer is overflowing with hundreds, if not thousands, of entries. Filtering steps and generating custom views can significantly reduce the workload. You may also construct custom views to focus on specific kinds of events:
- In the Event Viewer, you’ll see Administrative Events, to create special logs right-click on «Custom Views» and select «Create Custom View.»
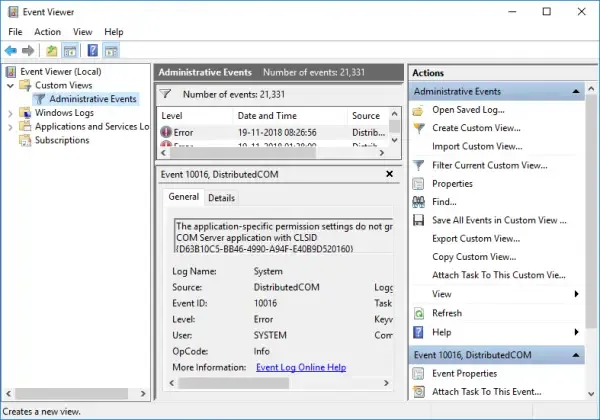
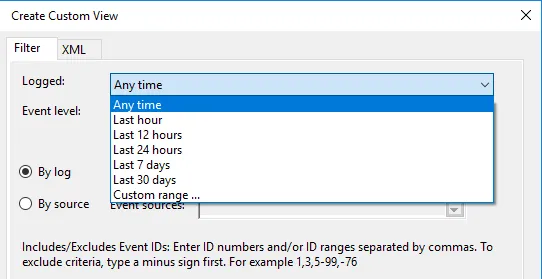
1. In the Custom View page, you can see logged drop down, choose a preferred time or it gives you an option to create a custom time to set. 2. On the Event Level choose an appropriate level for your custom view, You can choose among the 5 levels.
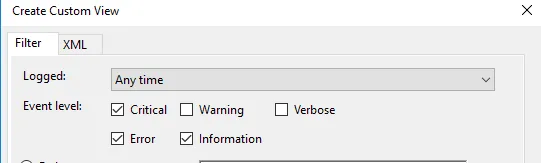
1. Once done, choose how you want the events to be filtered, By log or By source.
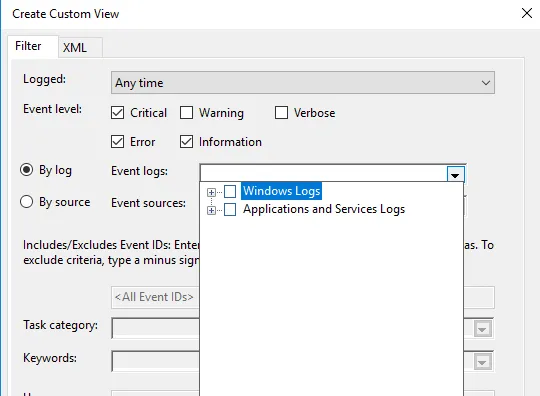
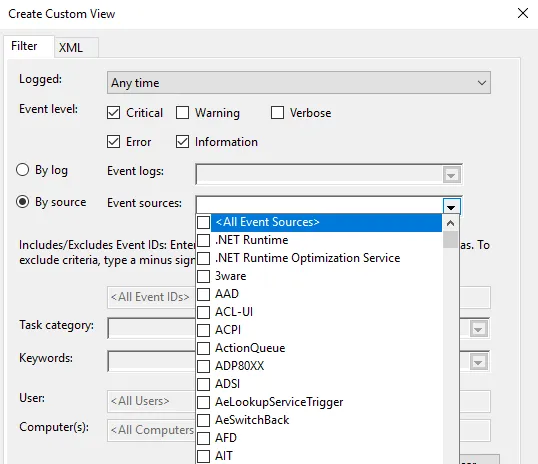
Once everything is set up according to your needs, save all events in Custom View as
from the drop-down menu and choose an appropriate location to save the logs. Click on the Save button. (A log file with the extension .evtx will be saved on your device).
Conclusion
This blog provides an understanding how you can use the Windows Event Viewer which is provided by the Windows in default and using it to monitor Windows logs.
- Main event log files are stored in
C:\\Windows\\System32\\winevt\\Logs. - Windows logs are crucial for understanding the activities, errors, and significant events on your machine. They provide valuable information for troubleshooting, auditing, and ensuring system integrity.
- They record a variety of system activities, errors, and other significant events, providing valuable information for troubleshooting, auditing, and ensuring system integrity.
- We learnt how to setup Filtering and Custom Views to optimise what we see and solve the problems and where it happened.
By grasping the significance of different event types such as System, Application, Security, Setup, and Forwarded Events, and knowing how to filter and export logs, you can effectively manage your Windows system.
FAQ’s
How to view Windows logs?
To view Windows logs, use the built-in Event Viewer:
- Press
Win + R, typeeventvwr, and press Enter. - Navigate through the console tree to find the log you want to view (e.g., Windows Logs > Application).
Where are Microsoft logs?
Microsoft logs, including Windows logs, can be found in the Event Viewer under sections like Application, Security, and System. Log files are also located in the C:\Windows\System32\winevt\Logs directory.
How do I audit Windows logs?
To audit Windows logs:
- Open Event Viewer.
- Navigate to Security logs under Windows Logs.
- Configure auditing policies via the Local Security Policy or Group Policy Management Console.
How do I check my Windows activity log
Check your Windows activity log by viewing the Security logs in Event Viewer. These logs record user logins, logoffs, and other security-related activities.
Which is Windows log key?
The Windows log key, often referred to as the Windows key, is the key on your keyboard with the Windows logo. It is used in various shortcuts to open system tools, including Event Viewer (Win + X > Event Viewer).
Where is the logs folder?
The logs folder is located at C:\Windows\System32\winevt\Logs. This folder contains all the event log files in .evtx format.
Why are Windows logs important?
Windows logs are important because they provide detailed information about system operations, security events, and application behavior, which is crucial for troubleshooting, auditing, and ensuring system integrity.
How to view log files?
View log files using Event Viewer:
- Open Event Viewer (
Win + R, typeeventvwr, press Enter). - Expand the Windows Logs section and select the log you want to view.
Where are login logs?
Login logs are located in the Security logs section of Event Viewer. They record all login attempts, both successful and failed.
What are system logs?
System logs contain information about the core operations of the Windows operating system, including hardware events, driver issues, and system startups and shutdowns. They are found under the System section in Event Viewer.
How do I find Windows log files?
Find Windows log files in the Event Viewer or directly in the C:\Windows\System32\winevt\Logs directory.
How do I view user logs in Windows 10?
View user logs in Windows 10 through the Event Viewer:
- Open Event Viewer.
- Go to Windows Logs > Security to see logs related to user activities, including logins and logoffs.
How do I view Windows setup logs?
To view Windows setup logs:
- Open Event Viewer.
- Navigate to Applications and Services Logs > Microsoft > Windows > Setup.
How do I view Windows app logs?
To view Windows application logs:
- Open Event Viewer.
- Navigate to Windows Logs > Application to see logs related to software applications running on your system.
Was this page helpful?
Для различных событий и ошибок системы и приложений Windows ведёт журналы событий, которые можно просмотреть и получить дополнительную информацию, которая может быть полезной при решении проблем с компьютером.
В этой инструкции для начинающих — способы открыть просмотр событий Windows 11/10 и дополнительная информация на тему, которая может пригодиться. На близкую тему: Как отключить журнал событий в Windows.
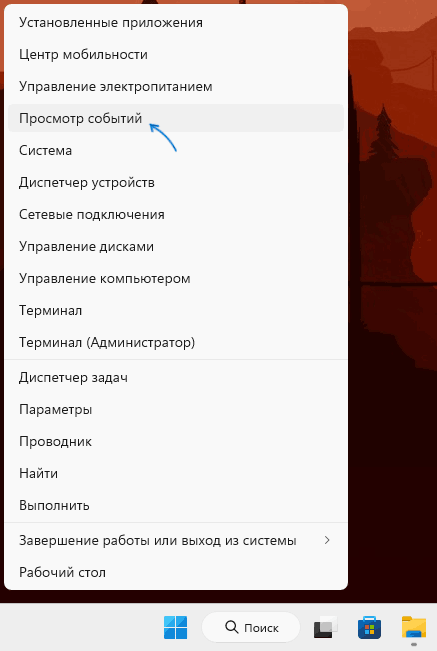
Контекстное меню кнопки Пуск и поиск
Самый быстрый способ перейти к просмотру журналов событий в Windows 11 и 10 — нажать правой кнопкой мыши по кнопке «Пуск» или нажать клавиши Win+X на клавиатуре и выбрать пункт «Просмотр событий» в открывшемся меню.
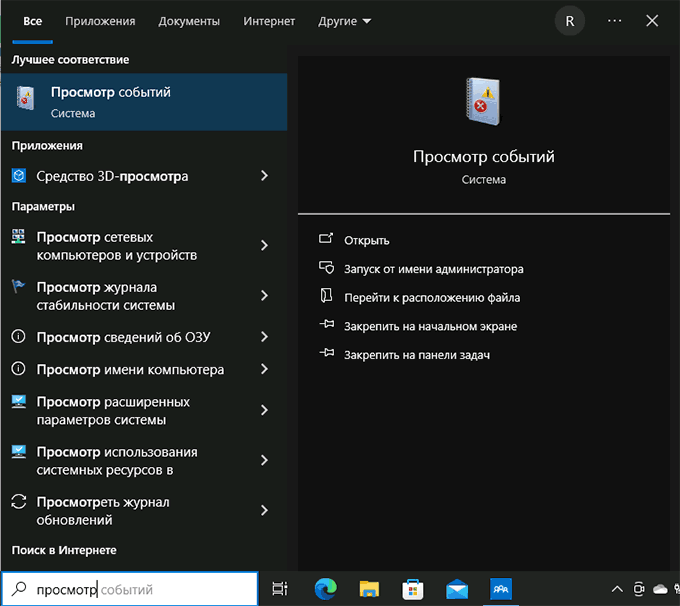
Ещё один простой и в большинстве случаев работающий способ открыть какой-либо системный инструмент, расположение которого вам неизвестно — использовать поиск в панели задач.
Начните вводить «Просмотр событий» в поиске, после чего запустите найденный результат:
Почему не «Журнал событий» или «Журнал ошибок», которые пользователи обычно ищут? Причина в том, что сами журналы — это файлы на диске в папках
C:\Windows\System32\winevt\Logs C:\Windows\System32\LogFiles
Пользователи, задавая вопрос о том, где журнал событий в Windows, обычно имеют в виду именно системный инструмент «Просмотр событий» для удобного просмотра соответствующих журналов.
Команда «Выполнить»
Самый быстрый и часто используемый метод запуска просмотра журналов событий Windows — использование команды «Выполнить»:
- Нажмите клавиши Win+R на клавиатуре, либо нажмите правой кнопкой мыши по кнопке «Пуск» и выберите пункт «Выполнить».
- Введите eventvwr.msc (или просто eventvwr) и нажмите Enter.
- Откроется «Просмотр событий».
Эту же команду можно использовать для создания ярлыка или для открытия журнала событий в командной строке. Возможно, вам пригодится информация о других полезных командах «Выполнить».
Обычно описанных выше вариантов бывает достаточно для открытия просмотра журналов событий и ошибок в Windows, но есть и другие подходы:
Помимо просмотра журнала событий, в Windows присутствует ещё один полезный инструмент — Монитор стабильности системы, позволяющий наглядно получить информацию о работе вашей системы по дням на основании данных из журнала событий.