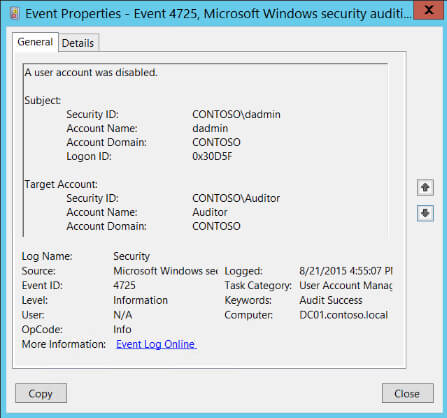
The user identified by Subject: disabled the user identified by Target Account:.
This event is logged both for local SAM accounts and domain accounts.
You will also see event ID4738 informing you of the same information.
Description Fields in
4725
Subject:
The user and logon session that performed the action.
- Security ID: The SID of the account.
- Account Name: The account logon name.
- Account Domain: The domain or — in the case of local accounts — computer name.
- Logon ID is a semi-unique (unique between reboots) number that identifies the logon session. Logon ID allows you to correlate backwards to the logon event (4624) as well as with other events logged during the same logon session.
Target Account:
- Security ID: SID of the account
- Account Name: name of the account
- Account Domain: domain of the account
Stay up-to-date on the Latest in Cybersecurity
Sign up for the Ultimate IT Security newsletter
to hear about the latest webinars, patches, CVEs, attacks, and more.
Hello All,
Hope this post finds you in good health and spirit.
This event is generated when a user or computer object is disabled. This even us to find out Who Disabled a User Account in Active Directory.
On domain controllers, member servers, and workstations, this event is generated for user accounts.
This event only appears for computer accounts on domain controllers.
The name of the account that requested the “disable account” operation is provided in the Account Name [Type = UnicodeString] field.
Account Domain: The subject’s domain or computer name [Type = UnicodeString]. several formats, some of which are as follows:
Example of a domain name on NETBIOS: WindowsTechnoFull domain name in lowercase: windowstechno.local
Full domain name in capital letters: WINDOWSTECHNO.LOCAL
The value of this field is "NT AUTHORITY" for several well-known security concepts, such as LOCAL SERVICE or ANONYMOUS LOGON.
The name of the machine or device that this account belongs to will be included in this column for local user accounts, for instance: "Mohan.thakur."
Logon ID As an example, “4624: An account was successfully logged on” is a hexadecimal number that you can use to compare this event to more recent ones that could also have the same Logon ID.
Target Account:
Security ID [Type = SID]: SID for the disabled account. Automatically, Event Viewer tries to resolve SIDs and display the account name. You will see the source data in the event if the SID cannot be resolved.
Account Name [Type = UnicodeString]: This field contains the name of the disabled account.
Account Domain [Type = UnicodeString]: The domain or computer name of the target account. several formats, some of which are as follows:
Example of a domain name on NETBIOS: WINDOWSTECHNOFull domain name in lowercase: windowstechno.local
Full domain name in capital letters: WINDOWSTECHNO.LOCAL
The name of the machine or device that this account belongs to will be included in this column for local user accounts, for instance: "Mohan.Thakur."
Recommendations for Security Monitoring
For 4725:- A user/computer account was disabled.
- Use the “Target AccountSecurity ID” that corresponds to the account to monitor all 4725 events if you have a high-value domain or local account that you need to keep track of every change for.
- You may monitor all 4725 events using the “Target AccountSecurity ID” that matches to any domain or local accounts that shouldn’t ever be disabled (such as service accounts).
- We advise keeping an eye on all 4725 events for local accounts because they often don’t change very often. Critical servers, administrative workstations, and other high-value assets are particularly affected by this.
So, that’s all in this blog. I will meet you soon with some other stuff. Have a nice day !!!
Recommended contents
RODC Installation Guide- Step by step guide to install read only domain controller
RODC Filtered Attribute Set
Installing and configuring a RODC in Windows Server-2012
How to find the GUID of Domain Controller
Group Policy Understanding Group Policy Preferences
Group Policy Verification Tool GPOTool Exe
Group Policy Health Check on Specific Domain Controller
What is Netlogon Folder in Active Directory
How to Create Custom Attributes in Active Directory
How Can I Check the Tombstone Lifetime of My Active Directory Forest
How to Determine a Computers AD Site From the Command Line
How to Check the Active Directory Database Integrity
How to Check the Active Directory Database Integrity
Disabling and Enabling the Outbound Replication
DFS Replication Service Stopped Replication
What is Strict Replication Consistency
The replication operation failed because of a schema mismatch between the servers involved
Troubleshooting ad replication error 8418 the replication operation failed because of a schema mismatch between the servers
How to export replication information in txt file
Repadmin Replsummary
Enabling the outbound replication
Guys please don’t forget to like and share the post. You can also share the feedback on below windows techno email id.
If you have any questions feel free to contact us on admin@windowstechno.com also follow us on facebook@windowstechno to get updates about new blog posts.
Was this article helpful?
YesNo
He is an Active Directory Engineer. He has been working in IT industry for more than 10 years.
He is dedicated and enthusiastic information technology expert who always ready to resolve any technical problem.
If you guys need any further help on subject matters, feel free to contact us on admin@windowstechno.com
Please subscribe our Facebook page as well website for latest article.
https://www.facebook.com/windowstechno
One of the most challenging tasks Administrators face on a daily basis is managing Active Directory user accounts. It is particularly important to monitor who and why changes are being made to ensure that they are valid.
Why it’s Important to Track Disabled User Accounts in Active Directory
Active Directory configuration changes need to be carefully monitored so that users have access to all the resources they require. If a user’s account becomes disabled, they will not have access to essential system functions including email, files and SharePoint which will disrupt business operations.
Another reason to ensure that disabled users are tracked in Active Directory is to reduce the risk of a data breach. Disabled accounts represent a serious threat as they can be re-enabled and misused by attackers seeking access to Active Directory, Windows servers and other AD-integrated systems. Therefore, it is crucial to have visibility over who disabled a user account to establish the reason for doing this.
In this article, we will discuss the steps you need to take to detect who disabled a user account in Active Directory. We will first look at doing this using native auditing, followed by a more straightforward approach using the Lepide Auditor for Active Directory.
Find Who Disabled a User Account using Event Logs (Event ID 4725)
Please follow the below steps:
- Run gpmc.msc to open the Group Policy Management Console.
- Create a new GPO and Edit it
- Go to Computer Configuration, Policies, Windows Settings, Security Settings, Local Policies > Audit Policy:
- Double click Audit Account Management Policy, Define, Success.
- Click Apply and OK
- Go to Event Log, Define:
- Maximum security log size to 4GB
- Retention method for security log to Overwrite events as needed.
- Link the new GPO to the OU with User Accounts: Go to Group Policy Management, Right-click the defined OU, choose Link an Existing GPO, Choose the GPO that you’ve created.
- Force the group policy update, In Group Policy Management, Right-click the defined OU, Click on Group Policy Update.
- Full Control
- List Contents
- Read all properties
- Read permissions, Click OK.
- Open ADSI Edit, Connect to Default naming context, Right-click DomainDNS object with the name of your domain, Properties, Security (Tab), Advanced (Button), Auditing (Tab), Add Principal Everyone, Type Success, Applies to This object and Descendant objects, Permissions, Select all check boxes except the following:
- Open Event viewer and search Security log for event ID’s 4725 (User Account Management task category).
Note: This event only generates on domain controllers and member servers.
How Lepide Auditor Helps
A quicker and more straightforward way to identify who has disabled a user is to use Lepide Auditor for Active Directory. Our Active Directory auditing software can provide you with in-depth visibility with real-time alerts that help you overcome the limitations of native auditing.
The following is an example of the User Status Modifications report, one of many pre-defined reports included the Lepide Auditor:
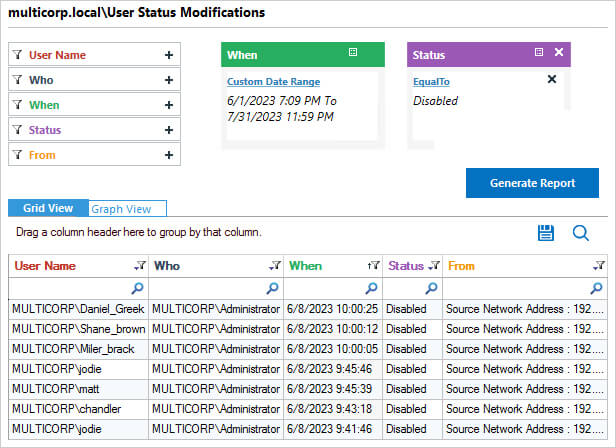
The report includes information showing the User Name of the account which has been disabled together with Who has disabled it.
To run the report:
- From the States & Behavior window, choose Active Directory Reports and select User Status Modifications
- Specify a date range, select Disabled from the Status filter and click Generate Report
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Indicates that a user account was successfully disabled.
Find more information about this event on ultimatewindowssecurity.com. Corresponding events on other OS versions:
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Sample: | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Log Name: Security Source: Microsoft-Windows-Security-Auditing Date: 10/28/2009 8:29:33 PM Event ID: 4725 Task Category: User Account Management Level: Information Keywords: Audit Success User: N/A Computer: dcc1.Logistics.corp Description: A user account was disabled. Subject: Security ID: S-1-5-21-1135140816-2109348461-2107143693-500 Account Name: ALebovsky Account Domain: LOGISTICS Logon ID: 0x2a88a Target Account: Security ID: S-1-5-21-1135140816-2109348461-2107143693-1148 Account Name: wrks12$ Account Domain: LOGISTICS |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Log Type: | Windows Event Log | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Uniquely Identified By: | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Field Matching |
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Always fun to try to figure out what is happening on your network or [easyazon_link identifier=”0735666318″ locale=”US” tag=”wn0d5-20″] server [/easyazon_link]. Especially if something happened and no one knows who did it. It is not much fun for user if he cannot login and his or her account has been disabled, either by accident or maliciously. If you setup properly audit in Active Directory it is very easy to find out in event logs who did what and why.
Here are steps how to setup detection of who disabled account in Active Directory on [easyazon_link identifier=”0735682674″ locale=”US” tag=”wn0d5-20″] Windows Server 2012 R2 [/easyazon_link].
- Run gpedit.msc > Create a new GPO > Edit it > Go to “Computer Configuration” > Policies > Windows Settings > Security Settings > Local Policies > Audit Policy:
- Click Audit account management > Define > Success
In next step
- Go to Event Log > Define:
- Maximum security log size 4 GB
- Retention method for security log to Overwrite events as needed
In next step link this created GPO to your USERS OU in Active Directory.
- Force the group policy update > In “Group Policy Management” > Right-click the defined OU > Click on “Group Policy Update“
- Open ADSI Edit > connect to Default naming context > Right-click DomainDNS object with the name of your domain
- Click Properties > Security Tab > Advanced button > Auditing Tab > Permissions > Select all check boxes except the following:
- Full ControlList ContentsRead all propertiesRead permissions > click “OK“
Now you can go to test your new audit policy in Active Directory, go to USERS OU and disable some user account. Open Event viewer and search Security log for event ID 4725 (User Account Management task category). Once you located the event ID you should see the disabled account and your name as the one who disabled the account in [easyazon_link identifier=”1449320023″ locale=”US” tag=”wn0d5-20″] Active Directory [/easyazon_link].
Incase you want to pull all these events from log in PowerShell:
PS C:\>Get-EventLog -LogName Security -Newest 10 | Where-Object { $_.EventID -eq 4725 }
This way you can check if such events happened on your server before you want to see details about the event.
[easyazon_image align=”none” height=”160″ identifier=”0672336227″ locale=”US” src=”http://blog.technotesdesk.com/wp-content/uploads/2015/12/41Wm2-bgH2L._SL160_.jpg” tag=”wn0d5-20″ width=”123″]