| Operating Systems |
Windows 2008 R2 and 7
Windows 2012 R2 and 8.1 Windows 2016 and 10 Windows Server 2019 and 2022 Windows Server 2025 |
|
Category • Subcategory |
Logon/Logoff • Logon |
| Type | Success |
|
Corresponding events in Windows 2003 and before |
552
|
4648: A logon was attempted using explicit credentials
On this page
- Description of this event
- Field level details
- Examples
This is a useful event for tracking several different situations:
- A user connects to a server or runs a program locally using alternate credentials. For instance a user maps a drive to a server but specifies a different user’s credentials or opens a shortcut under RunAs by shift-control-right-clicking on the shortcut, selecting Run as…, and then filling in a different user’s credentials in the dialog box that appears. Or a user logs on to a web site using new specific credentials. That is the case above in the example — Administrator was logged on to the local computer and then accessed a SharePoint server sp01.icemail.com as rsmith@mtg.com.
- This event is also logged when a process logs on as a different account such as when the Scheduled Tasks service starts a task as the specified user. Logged on user: specifies the original user account.
- With User Account Control enabled, an end user runs a program requiring admin authority. You will get this event where the process information is consent.exe. Unfortunately Subject does not identify the end user.
Unfortunately this event is also logged in situations where it doesn’t seem necessary. For instance logging on interactively to a member server (Win2008 RC1) with a domain account produces an instance of this event in addition to 2 instances of 4624.
Free Security Log Resources by Randy
- Free Security Log Quick Reference Chart
- Windows Event Collection: Supercharger Free Edtion
- Free Active Directory Change Auditing Solution
- Free Course: Security Log Secrets
Description Fields in
4648
Subject:
This is the original account that started a process or connection using new credentials. In this case Administrator was logged on to the local computer.
- Logon ID is a semi-unique (unique between reboots) number that identifies the logon session just initiated. Any events logged subsequently during this logon session will report the same Logon ID through to the logoff event 4647 or 4634.
Account Whose Credentials Were Used:
These are the new credentials. In this case Administrator then logged on as rsmith@mtg.com.
Target Server:
This is the server (in this case a Sharepoint server) Administrator logged on to as rsmith@mtg.com. This section may be blank or indicate the local computer when starting another process on local computer.
Process Information:
This is the process that initiates the connection or new process. In this case it makes sense that it’s Internet Explorer since we’re accessing a Sharepoint site. The Process Name identifies the program executable that processed the logon. This is one of the trusted logon processes identified by 4611. Process ID is the process ID specified when the executable started as logged in 4688.
Network Information:
This is blank in many cases but in the case of Remote Desktop logons network address is filled in with the IP address of the client workstation. Source port, while filled in, is not useful since most protocol source ports are random.
Setup PowerShell Audit Log Forwarding in 4 Minutes
Your browser does not support video
Examples of 4648
A logon was attempted using explicit credentials.
Subject:
Security ID: WIN-R9H529RIO4Y\Administrator
Account Name: Administrator
Account Domain: WIN-R9H529RIO4Y
Logon ID: 0x1ba0e
Logon GUID: {00000000-0000-0000-0000-000000000000}
Account Whose Credentials Were Used:
Account Name: rsmith@mtg.com
Account Domain: WIN-R9H529RIO4Y
Logon GUID: {00000000-0000-0000-0000-000000000000}
Target Server:
Target Server Name: sp01.IceMAIL.com
Additional Information: sp01.IceMAIL.com
Process Information:
Process ID: 0x77c
Process Name: C:\Program Files\Internet Explorer\iexplore.exe
Network Information:
Network Address: —
Port: —
This event is generated when a process attempts to log on an account by explicitly specifying that account’s credentials. This most commonly occurs in batch-type configurations such as scheduled tasks, or when using the RUNAS command.
Top 10 Windows Security Events to Monitor
Free Tool for Windows Event Collection
Readers help support Windows Report. We may get a commission if you buy through our links.
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Event ID 4648 isn’t an error, per se, as it’s the intended result of someone trying to enter a network server using different or new credentials. It’s supposed to block you from entering; that’s its purpose.
This Event ID is a problem because it’s a sign that someone has or is trying to hack into your computer. To help out, we’ll show you what you can do to address this problem and beef up security.
How can I protect my computer when Event ID 4648 appears?
1. Check event logs
- Open the Windows Search bar and bring up Event Viewer.
- Expand Windows Logs in the left-hand menu and select Security.
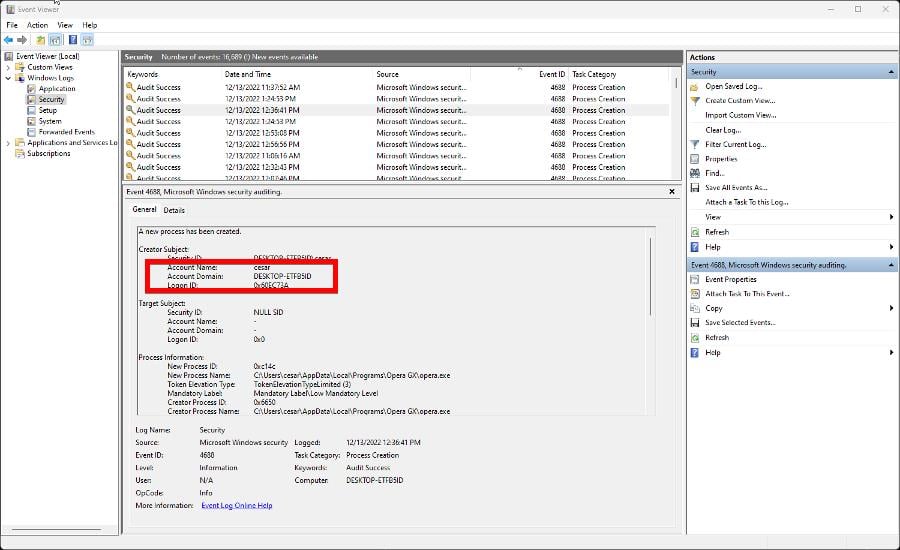
- Scroll through the various logs and locate one with Event ID 4648. This guide doesn’t have that but let’s say it does as an example.
- Once you locate a log with Event ID 4648, make note of the Account Name that attempted to log in
.
This solution and the next one go hand in hand. The purpose of the first is to do a bit of threat hunting, or in other words, figure out who is trying to gain access.
2. Remove account credentials
- Bring up the Control Panel and ensure the View By entry in the upper right corner is set to Large Icons.
- Select User Accounts.
- Click Manage your credential on the left-hand side.
- Select Windows Credentials in the new window.
- Expand the user account you don’t recognize or no longer want. In the dropdown, click Remove to get rid of that user.
This solution is meant to remove users from a network that you no longer want them to have access to. External people or bad actors require another approach.
- Microsoft will enhance the Defender platform with 3 new Advanced Hunting tables for Teams
- D3dx11_42.dll Not Found: How to Fix it
- Windows 11 Shutdown After Inactivity: 4 Ways to Stop it
- Windows Shuts Down Instead of Restarting: 4 Ways to Fix it
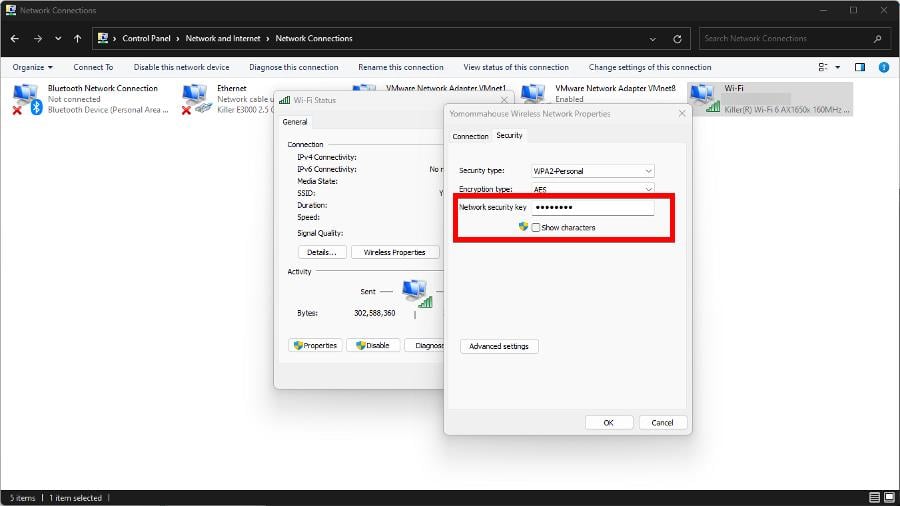
3. Change your Wi-Fi password
- Open up Control Panel and change the View By entry to Category.
- Select Network and Internet, then Network and Sharing Center.
- Click Change adapter settings.
- Right-click your Wi-Fi connect, and in the context menu, select Status.
- Click the Wireless Properties button then go to the Security tab in the following window.
- Enter a new password in the Network security key entry. Click OK to finish.
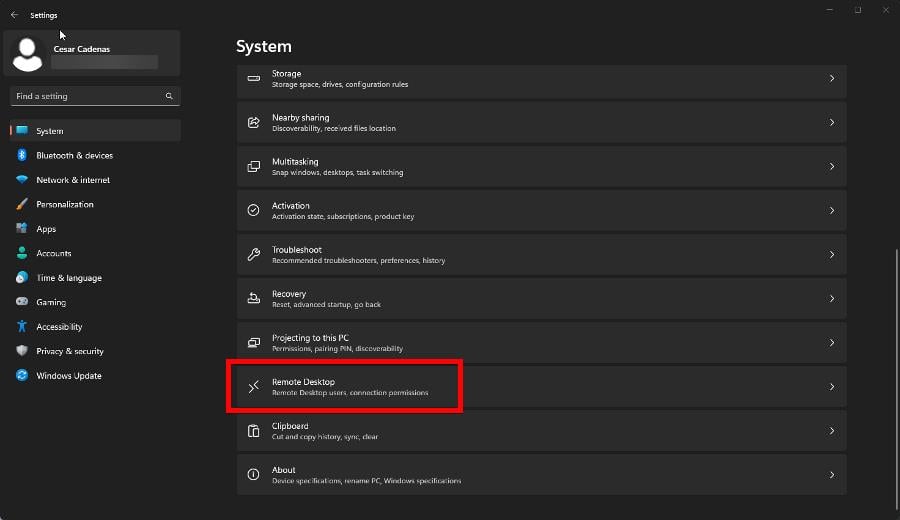
4. Disable Remote Access
- Open the Settings app, stay on the System tab, and scroll down to Remote Desktop.
- In this new section, toggle the switch next to Remote Desktop in order to disable the feature.
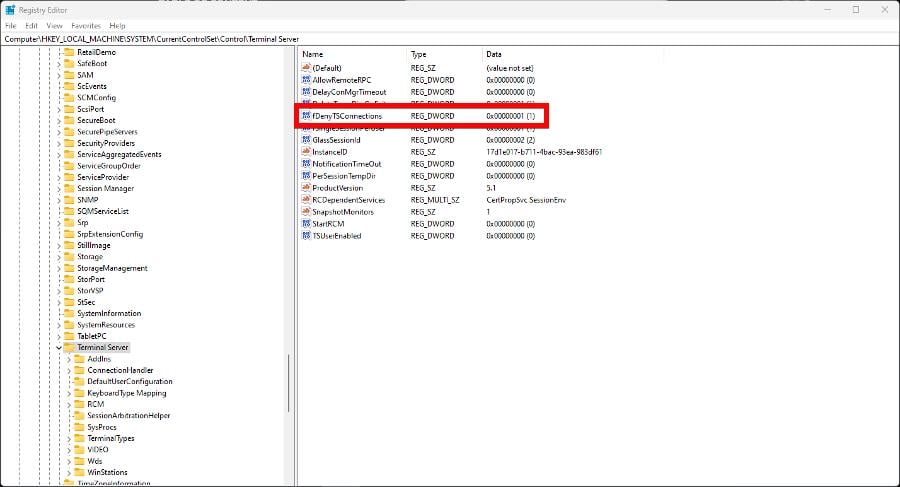
- To disable the feature, first, open the Registry Editor. Select Yes if the User Account Control asks if you want to make any changes.
- Enter the following in the Registry Editor and press Enter:
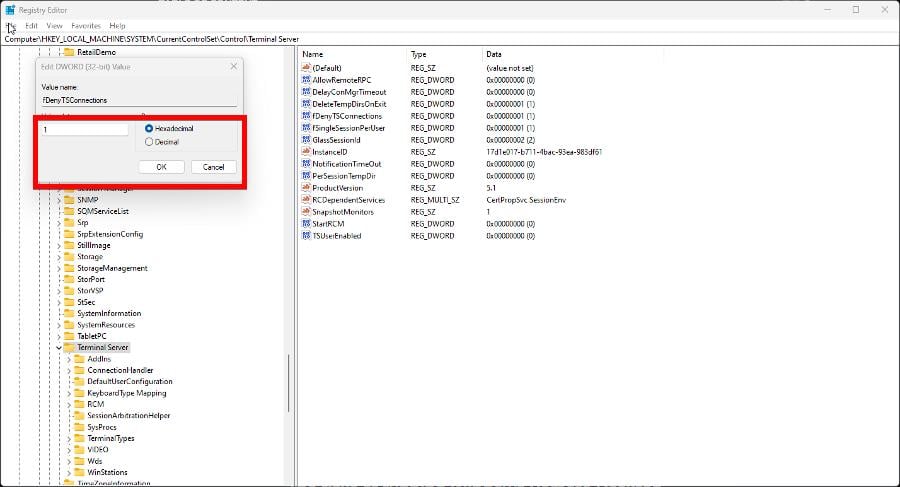
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server - Double-click fDenyTSConnections to open it.
- Set the value data to 1, then click OK to finish up.
You can also:
- Turn on your firewall. That is the easiest thing that you can do. Can’t turn on Windows Firewall? Check out these fixes and get things back to normal.
- Download the latest Windows update so your computer has the latest protections available. Microsoft consistently cracks them out.
- Limit the number of people who can access your network. The more people on the network, the higher the risk a bad actor will gain access.
- Move the Wi-Fi router to a different part of the house. If it is by a wall, someone from outside will have an easier time gaining access to your house network.
How can someone gain access to my Windows 11 computer?
A lot of the time, whenever people wonder how a hacker got into their machine, they usually think that person cracked open the computer’s tough defenses.
That’s certainly possible, but the more likely reason is that your computer’s or network’s own security is rather lacking.
- Your router’s firmware is out of date: Make sure to keep all of your systems up to date. Updating a router’s firmware requires you to connect it directly to your computer.
- Your router’s firewall is turned off: This is by far the worst gap you can have in your network’s security. Turn the firewall quickly, but be aware you have trouble accessing the router’s page.
- The computer is out of date: Every month, Microsoft has a Patch Tuesday where it rolls out a variety of fixes. We recommend staying up to date with those patches to protect your computer.
- You have too many people connected to the network: Not everyone will stay mindful of their device’s security. Perhaps you should clear out some users to keep things secure.
Event ID 4648 is just one of many different warning notices on Windows 11. There are two in particular that we want to shout out specifically. The first one is Event ID 157: Disk has been surprise removed.
This warning occurs when interrupts your computer’s communication with a disk and can render a virtual drive unusable. Fixing this may require you to tweak the computer’s registry a little.
The other one is Event ID 7000 which indicates some software services cannot start. We recommend either adjusting with the Group Policy Editor or restarting the offending service.
For fixes and logon errors, you can check our Navigating the Logon Balancing Error 88 in SAP GUI: Our step-by-step solutions guide.
Feel free to comment below if you have questions about other Event IDs. You can also leave comments about guides that you’d like to see or information on other errors.
Cesar Cadenas
Networking & Security Specialist
Cesar has been writing for and about technology going on for 6 years when he first started writing tech articles for his university paper. Since then, his passion for technology blossomed into a prosperous writing career. He first started writing about tech in the entertainment world and would later move on to write about smart life tech and social media. He was recently a Technical Writer for tech company Extron where he wrote user guides for audio and video equipment.
He has since moved on to being a freelance writer looking to have a career in copywriting and hopes to share his love and knowledge of technology with the world. Recently, Cesar has written for the cryptocurrency news site, BTCPro and helping people understand tech.
4648 — Explicit Credentials Success
https://learn.microsoft.com/en-us/windows/security/threat-protection/auditing/event-4648
Event ID 4648 in the Windows Security Event Log is a significant security event that indicates a logon attempt was made using explicit credentials. This event occurs when a user attempts to log on to a computer or access network resources by specifying credentials different from those associated with the current session. Such behavior is typical in scenarios where the «RunAs» command is used, or when scheduled tasks and services are configured to run under a specific account. Monitoring Event ID 4648 is crucial for identifying potential security risks, such as credential misuse or lateral movement attempts within a network.
Logged by the Security subsystem whenever a process or user initiates a logon attempt with explicit credentials.
Category: Audit Logon
Significance:
-
Security Implications: Event ID 4648 may indicate legitimate use cases, such as administrators managing multiple accounts or services configured with specific user credentials. However, it can also signal malicious activities, including pass-the-hash attacks, where attackers use stolen credentials to move laterally across a network.
-
Operational Context: In benign scenarios, this event helps track administrative activities and application behaviors requiring alternate credentials. In security contexts, it aids in detecting unauthorized access attempts and potential compromise.
Details Included in Event ID 4648
-
Subject: Information about the user or process that initiated the logon attempt. This includes:
-
Security ID: The SID of the initiating user.
-
Account Name: The name of the initiating account.
-
Account Domain: The domain of the initiating account.
-
Logon ID: A reference to the logon session of the initiating account.
-
-
Logon Type: Specifies the type of logon that was attempted. Common types include interactive (2), network (3), and batch (4).
-
Account Whose Credentials Were Used: Details about the account whose credentials were explicitly specified. This includes:
-
Account Name: The name of the account whose credentials were used.
-
Account Domain: The domain of the account whose credentials were used.
-
-
Process Information: Provides details about the process that requested the logon. This includes:
-
Process ID: The identifier of the process.
-
Process Name: The name of the process.
-
-
Network Information: Details about the network address and port number involved in the logon attempt.
How to Use Event ID 4648 for Security
Monitoring and Alerting: Setting up alerts for unexpected or unauthorized use of Event ID 4648 can help detect potential security threats early. Special attention should be given to patterns or anomalies, such as logon attempts at unusual hours or from unusual locations.
Forensic Analysis: In the aftermath of a security incident, analyzing occurrences of Event ID 4648 can help in understanding how an attacker might have used stolen credentials to access resources or move laterally within the environment.
Access Reviews and Audits: Regular reviews of logs containing Event ID 4648 are important for ensuring that the use of explicit credentials aligns with organizational policies and security best practices.
Best Practices for Monitoring Event ID 4648
-
Enable Detailed Auditing: Ensure that «Audit Logon» is enabled in Group Policy to capture detailed events related to logon activities, including the use of explicit credentials.
-
Implement Least Privilege Principle: Minimize the number of users and accounts with permissions to use alternate credentials to reduce the risk of misuse or attack.
-
Educate Users and Administrators: Provide training on the secure management of credentials and the potential risks associated with their misuse.
-
Use SIEM Solutions: Employ Security Information and Event Management (SIEM) systems to correlate Event ID 4648 with other indicators of compromise, enhancing the ability to detect malicious activities.
While Event ID 4648 provides valuable information about the use of explicit credentials, it does not inherently distinguish between legitimate and malicious activities. Contextual analysis, correlation with additional indicators, and understanding normal usage patterns within the organization are necessary to accurately interpret these events.

This event is generated when a process attempts an account logon by explicitly specifying that account’s credentials. This most commonly occurs in batch-type configurations such as scheduled tasks.
It is also a routine event that periodically occurs during normal operating system activity, what’s abnormal? Hunting specific processes at the timeline of the event ID 4648 provides more insights on adversaries. Please find the below cheatsheet.
Hunting with Event ID 4648:
- Event ID 4648 contains with the process name “C:\windows\System32\mstsc.exe” which is the indicator for user machine with outbound RDP connections detected. This can be mapped to T1076 of mitre and the active traces of lateral movement.
- Event message contains “*/TERMSRV/*” with the Event ID 4648 , Which is known to a RDP outbound connection from end user machine.Indicator for possible lateral movement detection.
- Process name “C:\Windows\System32\sc.exe” with the Event ID 4648 shows remote machine services are queried and executed.Indicator for Possible lateral movement detection. This can be mapped to mitre T1021/T1035.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
- Threat actor persistence with new service account with alternate credentials were Event ID 4648 at the time of incident.This includes services running with specfic account other than local system or Network Service , I.E “Account Name” equals sshd_server & process_name equals services.exe , This can be mapped to mitre T1050.
- Adversaries may use Valid Accounts to interact with remote machines by taking advantage of Distributed Component Object Model (DCOM) , Mostly it is called as RPC Calls , Remote Procedure Call (RPC) is a protocol that one program can use to request a service from a program located in another computer on a network without having to understand the network’s details. A procedure call is also sometimes known as a function call or a subroutine call.To detect such behaviours , Check for event messages contains Event ID 4648 contains with the event message contains “RPCSS/“. This can be mapped to mitre T1021/T1175.
The RPCSS service is the Service Control Manager for COM and DCOM servers. It performs object activations requests, object exporter resolutions, and distributed garbage collection for COM and DCOM servers. If this service is stopped or disabled, programs using COM or DCOM will not function properly – Microsoft Says
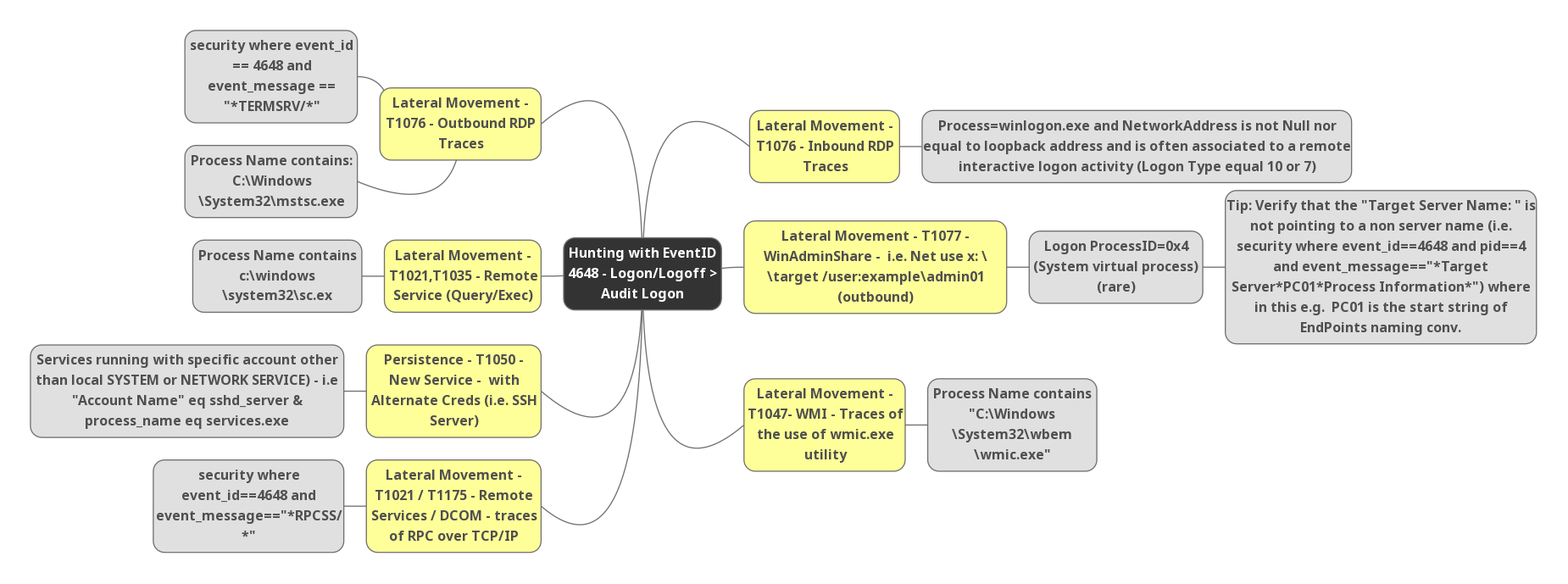
- Detecting possible inbound RDP Connections , Event ID 4648 detected with Process name “Winlogon.exe” and Network address is not empty nor equal to loopback address and this is often associated with a remote interactive logon activity ( Logon Type equals 10 or 7 ) . This can be mapped to mitre T1076.
Also Read: FireEye’s Open-Source Tool – CAPA to Identify Malware Capabilities
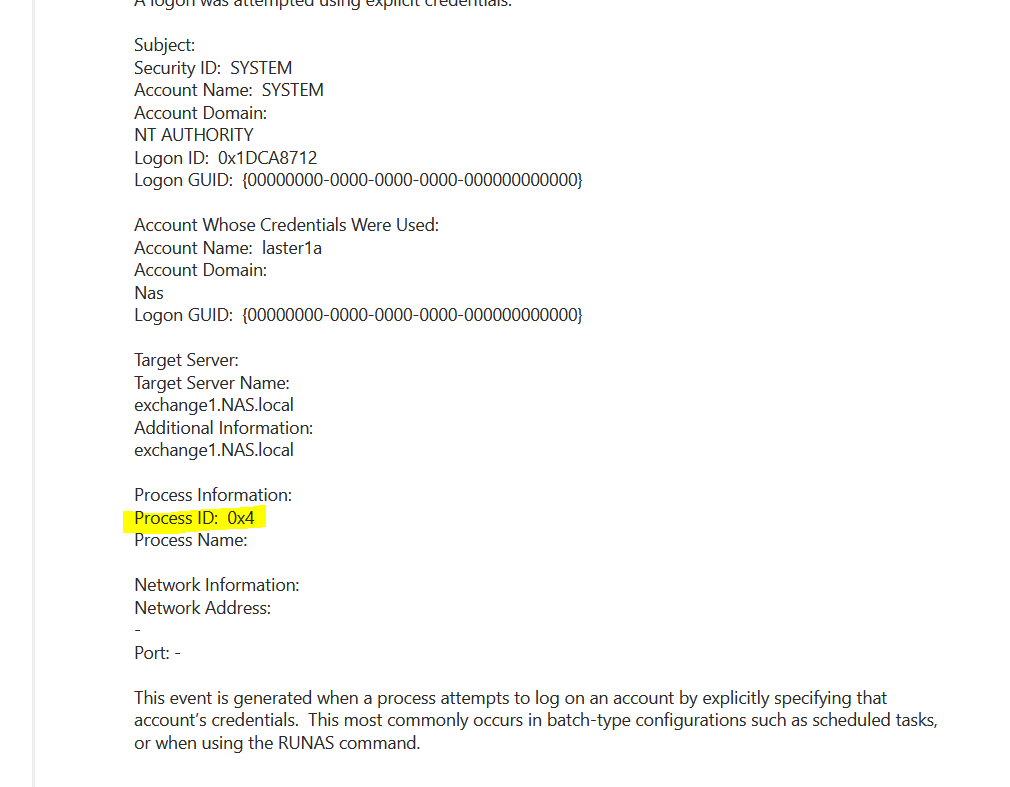
- Possible windows admin shares access , Event ID 4648 with cmd commands I.E Net use x:\target/user:example\admin01 ( Outbound connections ) , and logon process ID “0x4” or 4 and target server name contains *Targetserver*PC01*processinfromation* , Where in this example PC01 start sting of endpoint naming conversions. This can be mapped to mitre T1077.
Also Read: Threat Hunting using DNS logs – Soc Incident Response Procedure
- Event ID 4648 contains with the process name “wmic.exe” , Indicator of lateral movement with Windows Management Instrumentation. This can be mapped to mitre T1047.
Happy Hunting
Windows Event 4648 is a useful event for tracking several different situations. This event is generated when a process attempts to log on an account by explicitly specifying that account’s credentials. This most commonly occurs in batch-type configurations such as scheduled tasks, or when using the RUNAS command. The Windows Event can be found on the Windows Event Viewer Logs on: Start – Control Panel – Administrative Tools – Event Viewer:

Windows Event Viewer Logs
Windows Event 4648 can be found on event viewer security section. You can filter the current log by event id 4648 as the following picture:
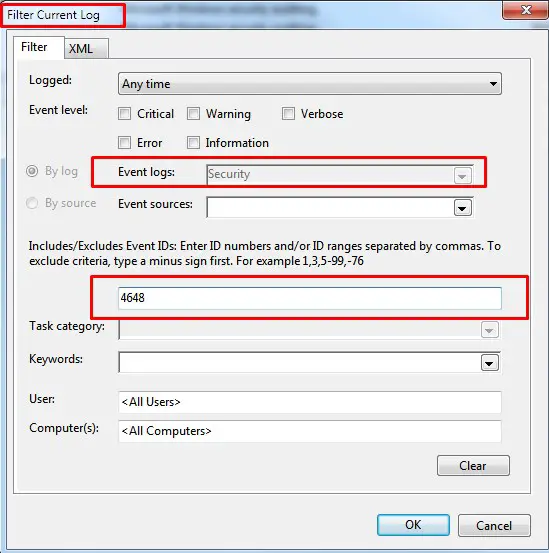
Event viewer security
In our article today we are going to explain WindowsEvent 4648 – A logon was attempted using explicit credentials and the description of fields.
Description of windows event 4648
A user connects to a server, PC or runs a program locally using alternate credentials. For instance a user maps a drive to a server but specifies a different user’s credentials or opens a shortcut under RunAs by shift-control-right-clicking on the shortcut, selecting Run as…, and then filling in a different user’s credentials in the dialog box that appears. Or a user logs on to a web site using new specific credentials.
This event is also logged when a process logs on as a different account such as when the Scheduled Tasks service starts a task as the specified user. Logged on user: specifies the original user account.
With User Account Control enabled, an end user runs a program requiring admin authority. You will get this event where the process information is consent.exe. Unfortunately Subject does not identify the end user.
In situations where it doesn’t seem necessary unfortunately this event is also logged. For instance logging on interactively to a member server (Win2008 RC1) with a domain account produces an instance of this event in addition to 2 instances of 4624.
Examples of event id 4648
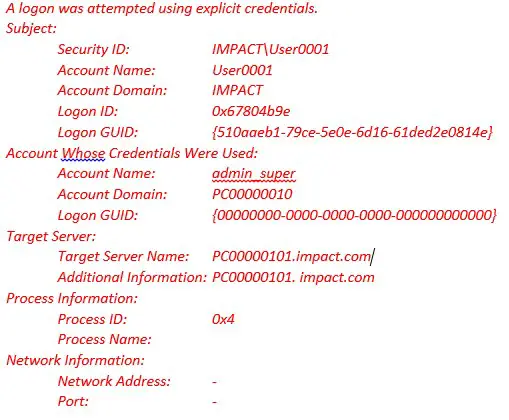
Windows Event 4648
Description Fields in windows event 4648
Subject:
This is the original account that started a process or connection using new credentials. In this case user IMPACT\User0001 was logged on the computer PC00000101 in the same domain from his computer PC00000010 and using Admin’s username and password. He tried to reach the D drive on an another user PC using the following command: \\ PC00000101\d$ where d$ is D drive of computer PC00000101
- Logon ID is a semi-unique (unique between reboots) number that identifies the logon session just initiated. Any events logged subsequently during this logon session will report the same Logon ID through to the logoff event 4647 or 4634.
Account Whose Credentials Were Used:
These are the new credentials. In this case IMPACT\User0001 logged on as admin_super
Target PC:
This is a PC named PC00000101.impact.com (in the same domain IMPACT). User0001 logged on to as admin_super which is a local administrator. This section may be blank or indicate the local computer when starting another process on local computer.
Process Information:
This is the process that initiates the connection or new process. The Process Name identifies the program executable that processed the logon. Event id 4611 identifies one of the trusted logon processes. Process ID is the process ID specified when the executable started as logged in 4688.
Network Information:
The network address in the case of Remote Desktop logons is filled with the IP address of the client workstation.In many cases in blank. Source port, while filled in, is not useful since most protocol source ports are random.