Introduction
DNS recursion can be used maliciously in DNS amplification attacks and other forms of DNS abuse. Disabling DNS recursion on your Windows server is an important step to improve your network security. This guide will walk you through the process of disabling DNS recursion in the Windows DNS server.
Prerequisites
- Administrative access to the Windows server.
- Access to the DNS Manager.
Steps to Disable DNS Recursion
Step 1: Open DNS Manager
- Click on the Start menu, type dnsmgmt.msc , and press Enter to open the DNS Manager. Alternatively, you can find DNS Manager in the Administrative Tools in the Control Panel
Step 2: Access Server Properties
- In the console tree, right-click the applicable DNS server, then click Properties.
- Click the Advanced tab.
Step 3: Modify the Server Options
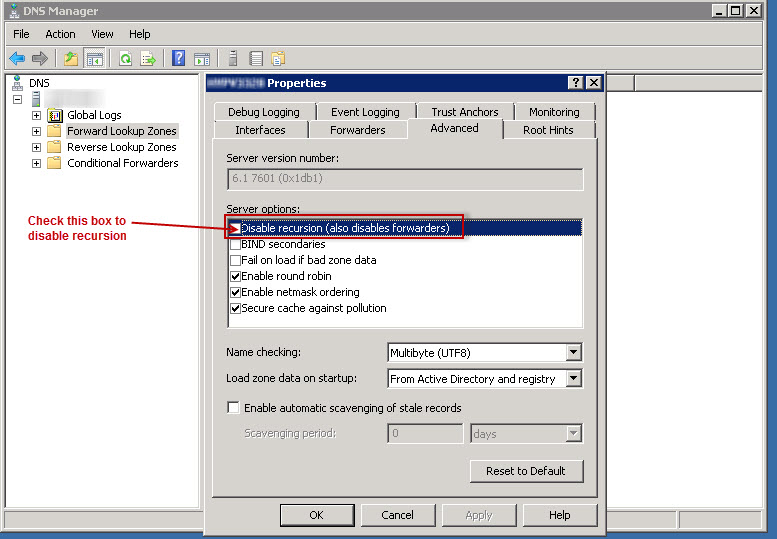
- In Server options, select the Disable recursion check box
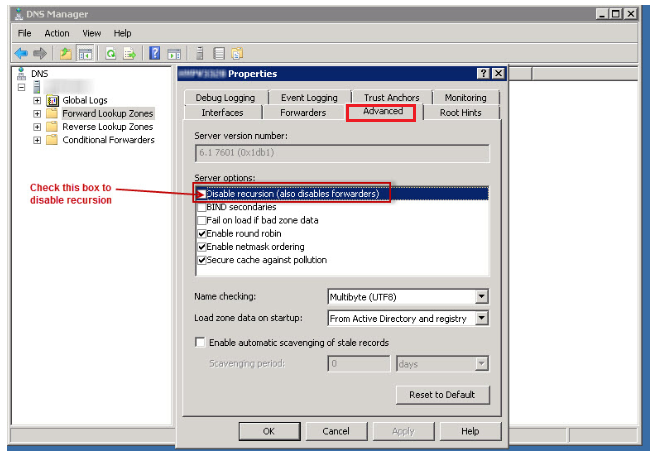
Step 4: Deleting root hint entries:
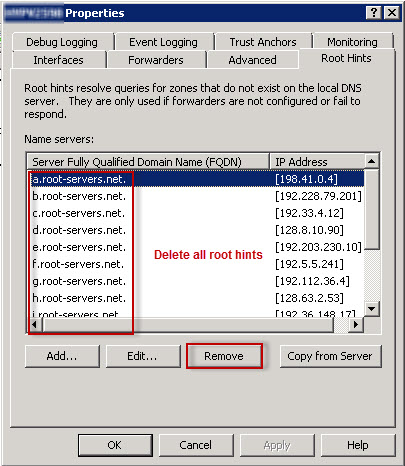
- Under the Root Hints tab, delete all root hints entries, and then click OK.
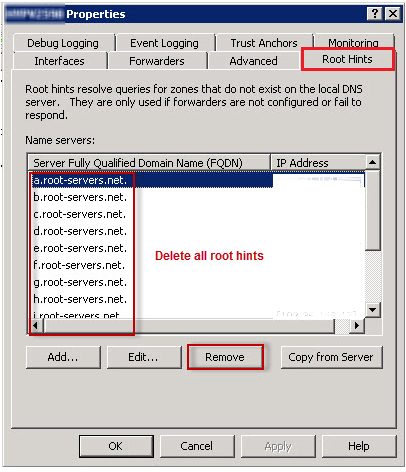
Step 5: Confirm Changes
- After applying these changes, restart the DNS service from the Services control panel.
Conclusion
Disabling DNS recursion on your Windows server can significantly enhance your network’s security posture by mitigating the risk of being involved in DNS amplification attacks and other malicious activities. After completing these steps, your server should no longer perform recursive query resolutions for external domains, thus reducing its vulnerability to such exploits.
Should you have any inquiries about the guidelines, please feel free to open a ticket through your portal account or contact us at support@ipserverone.com. We’ll be happy to assist you further.
Note: If your server has a legitimate need to perform DNS recursion (example – you have applications that need to resolve external DNS), you can alternately disable and/or scope the local Windows Firewall rule that allows incoming DNS requests.
Windows 2003: Uncheck or remove any rules for DNS, DNS.exe or exceptions for port 53.
Windows 2008 and higher: You’ll want to disable or scope both DNS TCP and DNS UDP rules.
To disable DNS Recursion in Windows DNS:
-
Open DNS Manager (To open DNS Manager, click Start, point to Administrative Tools, and then click DNS.)
-
In the console tree, right-click the applicable DNS server, then click Properties.
-
Click the Advanced tab.
-
In Server options, select the Disable recursion check box
-
Under the Root Hints tab, delete all root hints entries, and then click OK.
-
Restart the DNS service (from the Services control panel)
How to disable recursion:
How to delete root hints:
For further reading:
http://technet.microsoft.com/en-us/library/cc771738.aspx
Why DNS Recursion should be disabled for public access:
http://www.computerworld.com/s/article/9232892/Open_DNS_resolvers_increasingly_abused_to_amplify_DDoS_attacks_report_says
http://www.us-cert.gov/ncas/alerts/TA13-088A
http://openresolverproject.org/
Content retrieved from: https://support.appliedi.net/kb/a1010/how-to-disable-recursion-on-a-windows-dns-server.aspx.
Updated on November 11, 2019
Was this article helpful?
Related Articles
Customer Support Portal
Can’t find the answer you’re looking for? Don’t worry we’re here to help!
CONTACT SUPPORT
Background
I will like to start a series of articles on how to harden a Microsoft DNS Server.
Before we dig in too deep let us first start talking about the weeds out there.
What prompts us
Reviewing the MS Windows Event Viewer discovered entries that looks like this:
Textual:
The DNS server encountered an invalid domain name in a packet from 90.23.83.107. The packet will be rejected. The event data contains the DNS packet.
Image:

Data
Since we are referred to the “event data”, let us try to make sense of it:

.cz
What does the error mean?
It means that the host listed as the packet from w.x.y.z is sending us a request for a domain suffix that is different from the ones we have explicitly declared we are handling.
The reasons are myriad and can include:
- An application on that host is specifically sending DNS requests to us
- The original request was directed at a DNS Server that has been configured to forward DNS requests
Network Monitoring
Let us use a Network Monitoring tool to read Network requests.
As we already have the Microsoft Network Monitoring Tool installed, we will use it.
Configure Microsoft Network Monitoring Tool
Filter
I will suggest that you tighten your filtering and only bring in DNS Traffic.
You can do so by using the Application’s menu.
In our version, Filter \ Load Filter \ Standard Filters \ DNS \ Protocol Filter – DNS
Here is what the Application generates based on this request:

Please click the “Apply” button to effect the filtering.
Output
We will be interested in correlating Network Traffic flows with entries in the MS Event Viewer and so will add “Time Date Local Adjusted” to the list of columns to display.
That way we will be better able to match specific Event Viewer entries with items we capture from our Network Monitoring tool.
To do so, please click on the Columns \ Choose Columns:

Here is what things look like once we moved “Time Date Local Adjusted” from the “Select the desired columns” area to the “Enabled Columns” area.

Our Domain, but invalid hostname
DNS Query Request

Explanation:
- Our instigator is sending UDP requests to our port 53 ( DNS )
- The QueryId is 0x4F2 and Query Identifier is 1266
- The full query is xmq.[full-doman-name]
DNS Query Response

Explanation:
- We replied via UDP from port 53 ( DNS )
- The QueryId is 0x4F2 and Query Identifier is 1266
- Our Reply Code is “Rcode = Name Error“
Invalid Domain
DNS Query Request

Quick Explanation:
- We are receiving numerous simultaneous DNS requests bearing QueryID 26025 (0x65A9)
- The query is requesting 067.cz and it is requesting “all” records
- We can also confirm from the request dump that Recursion is desired (Recursion Desired = 1)
DNS Query Response

Quick Explanation:
- On behalf of the requester, our DNS Server connected to 77.78.104.139 and requested data
- The query is requesting 067.cz and it is requesting “all” records
- We can also confirm from the request dump that Recursion is desired (Recursion Desired = 1)
- We received the following set of data
- All Name Server ( ns1, ns2, ns3 )
- SOA ( Start of Authority )
- MX ( Mail )
- spf1 ( Send Framework Record )
Resolution
Server – Properties – Advanced Tab
Disable recursion – GUI

Disable recursion – Command Line
dnscmd . /config /norecursion 1
Disable recursion – Query
Syntax
dnscmd . /info
Output

Explanation
- In the “Configuration flags” section, fNoRecursion is set to 1
What is the implication?
Service Internal Clients
Can we still properly service DNS queries for our internal clients?
Queries for Authoritative Domains
Query
Syntax:
nslookup -querytype=MX FQDN. nameserver
Sample:
nslookup -querytype=MX labdomain.com. 10.0.7.49
Explanation:
- Request is pretty straight forward
- Please issue prefixed by a period to indicate it is fully formed; that is the DNS Suffix should not be auto-appended when passed to the DNS Server
- We are asking our DNS Server ( 10.0.7.49 ) for Mail ( MX ) records
Output:
Image:

Explanation:
- We received back our MX record
Request Trace – Incoming

Explanation:
- We are requesting MX records for a specific domain
Request Trace – Response

Explanation:
- Response
- We are authoritative
- We replied with MX record(s)
Queries for Non-Authoritative Domains
Query
Syntax:
nslookup -querytype=MX FQDN. nameserver
Sample:
nslookup -querytype=MX talend.com. 10.0.7.49
Explanation:
- We are asking our DNS Server ( 10.0.7.49 ) for Mail ( MX ) records for the Talend (talend.com) domain
- Again, notice that we need the . after the domain name
Output:
Image:

Explanation:
- We replied with “can’t find talend.com.: Server failed“
Request Trace – Incoming

Explanation:
- We are requesting MX records for a specific domain
Request Trace – Response

Explanation:
- Response
- We replied with “Server failure“
- Question Count is 1 (0x1)
- Answer Count is 0 (0x0)
Summary
Once we disabled recursion, we stopped seeing the errors about “invalid domain name“.
We have other areas to cover and will do so in subsequent posts.
Reference
Standards
- List of DNS Record Types
https://en.wikipedia.org/wiki/List_of_DNS_record_types
Download
- Event 5504 is logged when a Windows Server 2003-based DNS server receives a packet that contains a DNAME resource record
https://support.microsoft.com/en-us/kb/920162
Configuration
- Disable recursion on the DNS server
https://technet.microsoft.com/en-us/library/cc787602(v=ws.10).aspx
Q/A
- DNS Event ID 5504 (Invalid domain name in a packet)
http://community.spiceworks.com/topic/340468-dns-event-id-5504-invalid-domain-name-in-a-packet
🛡️ How to Disable DNS Recursion and Delete Root Hints on Windows Server
DNS recursion and root hints are often enabled by default on Windows servers, which can expose your server to DNS amplification attacks. This guide walks you through how to disable DNS recursion and remove root hints to harden your DNS configuration.
✅ Prerequisites
-
Access to your server via Remote Desktop (RDP)
-
Admin rights on a Windows Server with DNS role installed
🔧 Steps to Disable DNS Recursion
1. Login to Your Server
Connect via Remote Desktop to your VPS or dedicated server.
2. Launch DNS Manager
Go to:
Start > Administrative Tools > DNS
This will open the DNS Manager console.
3. Open Server Properties
-
In the left pane, right-click your server name
-
Select Properties
4. Disable Recursion
-
Go to the Advanced tab
-
Check the box for:
✅ Disable recursion (also disables forwarders) -
Click Apply and OK
🗑️ Steps to Delete Root Hints
5. Open Root Hints Tab
-
Still in DNS Manager, open Properties on the server node
-
Go to the Root Hints tab
6. Delete All FQDN Entries
-
Select each listed FQDN Name Server
-
Click Remove until the list is empty
-
Click Apply and OK
🔄 Restart the DNS Service
7. Restart DNS to Apply Changes
-
In DNS Manager, right-click your server name
-
Go to All Tasks > Restart
This ensures the changes take effect.
➕ Optional: Add a “.” Forward Zone (Dot Zone)
Adding a dot zone (.) disables external DNS lookups completely.
1. Create a New Zone
-
Right-click the server name > New Zone
-
Click Next through the prompts until you reach Zone Name
2. Enter a Dot (.) as Zone Name
-
Type a single period
.for the zone name -
Proceed with default options and click Next
3. Complete the Wizard
-
Click Finish on the final screen
This prevents the server from performing DNS lookups on the internet.
Dedicated Servers and SSD Cloud Servers
InetServices helps all forms of companies with their dedicated server hosting and SSD cloud server hosting needs allowing these companies to focus on their core business and on their hosting environment. Big Data is changing the landscape of how businesses are run. Enterprise-class databases are now used to store, sort, and query multiple terabyte amounts of information. So whether you build your Big Data environment with bare metal cloud servers or dedicated servers, InetServices offerings makes it easy for any size business to leverage the exact amount of performance and scalability you need.
Beyond Cloud Server Hosting
InetServices offers a wide range of cloud hosting services. Everything from Public Cloud Hosting to Private Cloud Hosting and from Bare-Metal Cloud to
Big Data Cloud providing a new generation of large-scale, performance-intensive applications for turnkey NoSQL solutions like Hadoop-as-a-Service and MongoDB. See what InetServices cloud server hosting can do for you.
Beyond Bare Metal Server Hosting
Businesses have been using our dedicated hosting for years for their dedicated web hosting and dedicated application hosting services. Now it’s time to look beyond simple dedicated hosting services. Services such as High-Availability hosting and Disaster Recovery hosting are essential in keeping your business alive and successful no matter what.
So look beyond just dedicated server hosting.
