В этой статье мы рассмотрим два способа организации условного разрешения имен в DNS сервере на Windows Server 2016: DNS conditional forwarding и DNS policy. Эти технологии позволяют настроить условное разрешение DNS имен в зависимости от запрошенного имени, IP адреса и местоположения клиента, времени суток и т.д.
Содержание:
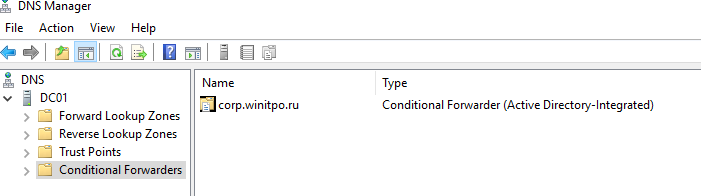
- Настройка DNS Conditional Forwarder в Windows Server
- Настройка DNS Conditional Forwarding с помощью PowerShell
- Фильтрация запросов DNS, политики разрешения имен в Windows Server 2016
Условная пересылка DNS (Conditional Forwarding) позволяет перенаправить DNS запросы об определенном домене на определенные DNS-сервера. Обычно Conditional Forwarders используется, когда нужно настроить быстрое разрешение имен между несколькими внутренними приватными доменами, или вы не хотите, чтобы DNS запросы с вашего сервера пересылались через публичную сеть Интернет. В этом случае вы можете создать на DNS сервере правило DNS пересылки DNS запросов для определенной доменной зоны (только !!!) на определенный DNS сервер.
Настройка DNS Conditional Forwarder в Windows Server
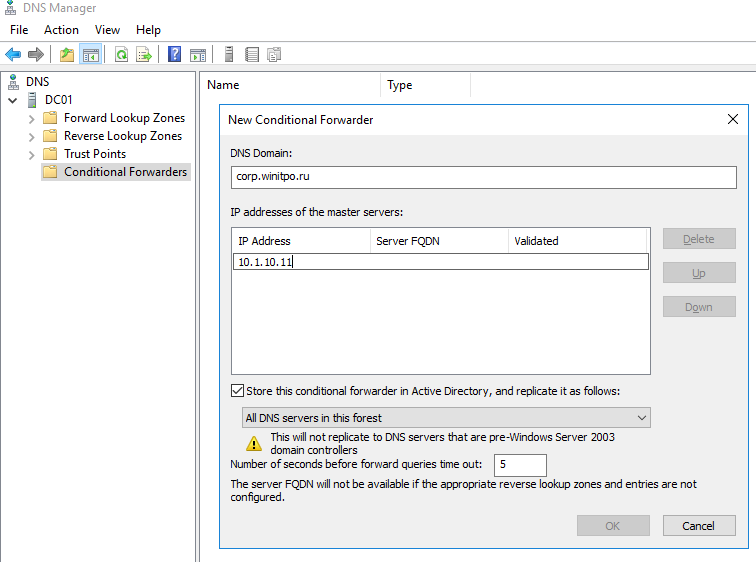
Попробуем настроить условное перенаправление DNS запросов для определенной доменной зоны на Windows Server 2016. Например, я хочу, чтобы все DNS запросы к зоне corp.winitpro.ru пересылались на DNS сервер 10.1.10.11.
- Запустите консоль управления DNS (
dnsmgmt.msc
); - Разверните ваш DNS сервер, щелкните правой кнопкой по разделу Conditional Forwarders и выберите New Conditional Forwarder;
- В поле DNS domain укажите FQDN имя домена, для которого нужно включить условную пересылку;
- В поле IP addresses of the master servers укажите IP адрес DNS сервера, на который нужно пересылать все запросы для указанного пространства имен;
- Если вы хотите хранить правило условной переадресации не только на этом DNS сервере, вы можете интегрировать его в AD. Выберите опцию “Store this conditional forwarder in Active Directory”;
- Выберите правило репликации записи conditional forwarding (All DNS servers in this forest, All DNS servers in this domain или All domain controllers in this domain).
Настройка DNS Conditional Forwarding с помощью PowerShell
Вы можете создать правило Conditional Forward для определенной DNS зоны с помощью PowerShell. Воспользуйтесь командлетом Add-DnsServerConditionalForwarderZone:
Add-DnsServerConditionalForwarderZone -Name dmz.winitpro.ru -MasterServers 192.168.1.11,192.168.101.11 -ReplicationScope Forest
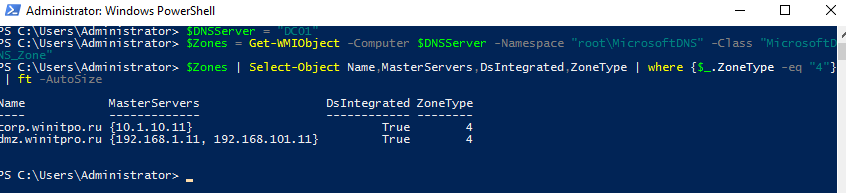
Чтобы вывести список DNS Conditional Forwarders на определенном сервере, выполните следующий PowerShell скрипт:
$DNSServer = "DC01"
$Zones = Get-WMIObject -Computer $DNSServer -Namespace "root\MicrosoftDNS" -Class "MicrosoftDNS_Zone"
$Zones | Select-Object Name,MasterServers,DsIntegrated,ZoneType | where {$_.ZoneType -eq "4"} | ft -AutoSize
Фильтрация запросов DNS, политики разрешения имен в Windows Server 2016
В Windows Server 2016 появилась новая фича в службе DNS сервера – DNS политики. DNS политики позволяют настроить DNS сервер так, чтобы он возвращал различные ответы на DNS запросы в зависимости от местоположения клиента (с какого IP адреса или подсети пришел запрос), интерфейса DNS сервера, времени суток, типа запрошенной записи (A, CNAME, PTR, MX) и т.д. DNS политики в Windows Server 2016 позволяют реализовать сценарии балансировки нагрузки, фильтрации DNS трафика, возврата DNS записей в зависимости от геолокации (IP адреса клиента) и многие другие сложные сценарии.
Вы можете создать политику как на уровне DNS сервера, так и на уровне всей зоны. Настройка DNS политик в Windows Server 2016 возможна только из командной строки PowerShell.
Попробуем создать простую политику, которая позволяет вернуть разный ответ на DNS запрос в зависимости от геолокации клиента. Допустим, вы хотите, чтобы клиенты в каждом офисе использовали собственный прокси на площадке. Вы создали политику назначения прокси в домене (на всех клиентах будет указано proxy.winitpro.ru). Но клиент из каждого офиса должен резолвить этот адрес по-разному, чтобы использовать для доступа свой локальный прокси-сервер.
Я создал 3 подсети для разных офисов компании:
Add-DnsServerClientSubnet -Name "MSK_DNS_Subnet" -IPv4Subnet "192.168.1.0/24"
Add-DnsServerClientSubnet -Name "EKB_DNS_Subnet" -IPv4Subnet "192.168.11.0/24"
Add-DnsServerClientSubnet -Name "SPB_DNS_Subnet" -IPv4Subnet "192.168.21.0/24"
Эти команды придется выполнить на всех DNS серверах, на которых должна работать условная политика DNS. Эти записи не реплицируются в DNS и хранятся локально в реестре DNS сервера. Вы можете указать имя сервера с помощью параметра
-ComputerName dc01
.
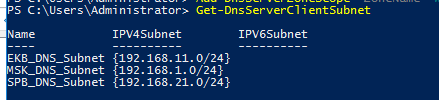
Чтобы вывести список всех IP подсетей клиентов, выполните:
Get-DnsServerClientSubnet
Теперь нужно для каждого офиса создать отдельную DNS область:
Add-DnsServerZoneScope -ZoneName “winitpro.ru” -Name “MSKZoneScope”
Add-DnsServerZoneScope -ZoneName “winitpro.ru” -Name “EKBZoneScope”
Add-DnsServerZoneScope -ZoneName “winitpro.ru” -Name “SPBZoneScope”
Следующие команды добавят 3 DNS записи с одним именем, но указывающие на разные IP адреса в разных областях DNS:
Add-DnsServerResourceRecord -ZoneName “winitpro.ru” -A -Name “proxy” -IPv4Address “192.168.1.10” -ZoneScope “MSKZoneScope”
Add-DnsServerResourceRecord -ZoneName “winitpro.ru” -A -Name “proxy” -IPv4Address “192.168.11.10” -ZoneScope “EKBZoneScope”
Add-DnsServerResourceRecord -ZoneName “winitpro.ru” -A -Name “proxy” -IPv4Address “192.168.21.10” -ZoneScope “SPBZoneScope”
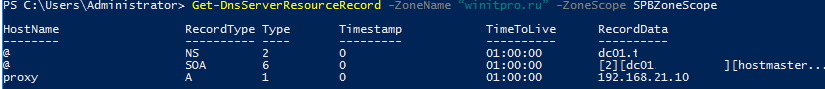
Вы можете вывести все ресурсные DNS записи для области с помощью команды:
Get-DnsServerResourceRecord -ZoneName “winitpro.ru” -ZoneScope SPBZoneScope
Теперь нужно создать DNS политики, которые свяжут IP подсети, DNS области и A записи.
Add-DnsServerQueryResolutionPolicy -Name “MSKResolutionPolicy” -Action ALLOW -ClientSubnet “eq,MSK_DNS_Subnet” -ZoneScope “MSKZoneScope,1” -ZoneName “winitpro.ru” –PassThru
Add-DnsServerQueryResolutionPolicy -Name “EKBResolutionPolicy” -Action ALLOW -ClientSubnet “eq,EKB_DNS_Subnet” -ZoneScope “EKBZoneScope,1” -ZoneName “winitpro.ru” -PassThru
Add-DnsServerQueryResolutionPolicy -Name “SPBResolutionPolicy” -Action ALLOW -ClientSubnet “eq,SPB_DNS_Subnet” -ZoneScope “SPBZoneScope,1” -ZoneName “winitpro.ru” –PassThru
В DNS политиках доступны следующие действия:
-
-Action ALLOW -
-Action DENY -
-Action IGNORE
Можно использовать следующие параметры в фильтре DNS:
-InternetProtocol "EQ,IPv4,NE,IPv6"
-TransportProtocol "EQ,UDP,TCP"
-ServerInterfaceIP "EQ,192.168.1.21"
-QType "EQ,A,AAAA,NE,PTR"
-TimeOfDay "EQ,9:00-18:00"
Вывести список всех DNS политик для DNS зоны на сервере можно так:
Get-DnsServerQueryResolutionPolicy -ZoneName winitpro.ru
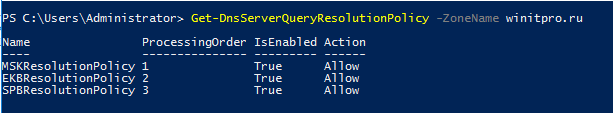
Теперь с устройств из различных офисов проверьте, что DNS сервер на один и тот же запрос возвращает различные IP адреса прокси:
nslookup proxy.winitpro.ru
Можно запретить DNS серверу возвращать DNS адреса для определенного пространства имен (домена):
Add-DnsServerQueryResolutionPolicy -Name 'BlockFidhingPolicy' -Action IGNORE -FQDN "EQ,*.cberbank.ru"
As essential parts of a DNS Server, the DNS Forwarders and the DNS Conditional Forwarders are the two topics that we will configure after installing the DNS role and configuring the DNS zones. A DNS Forwarder is responsible for serving external DNS requests. We manually configure the DNS Forwarder on our DNS Server and specify the DNS server(s) it should refer to for any external DNS requests. A DNS Conditional Forwarder resolves the external DNS requests only for a specific domain that we specify. Mainly, we configure it between partners and trusted organisations. With this brief introduction in mind, we will cover how to configure a DNS Forwarder and a DNS Conditional Forwarder in Windows Server 2022. We will cover each one in a separate section following a straightforward step-by-step approach.
Also, read Install DNS In Server 2022 Using Server Manager And Powershell.
Configure a DNS Forwarder in Server 2022
We discussed a brief overview of the DNS Forwarder. In this section, we will go step-by-step to see how we can configure it in a Windows Server 2022.
1. Pull up the DNS Manager console. To do so, press down the Windows Key + R keys on your keyboard. Then, typednsmgmt.mscin the Run dialogue box and hit enter. An alternative way is to navigate through Server Manager >>Tools >> DNS.
2. On the DNS Manager console, select the server name on the left pane and double-click on Forwarders at the right pane.
3. Select the Forwarders tab on the DNS server’s properties, and click on the Edit button, afterwards.
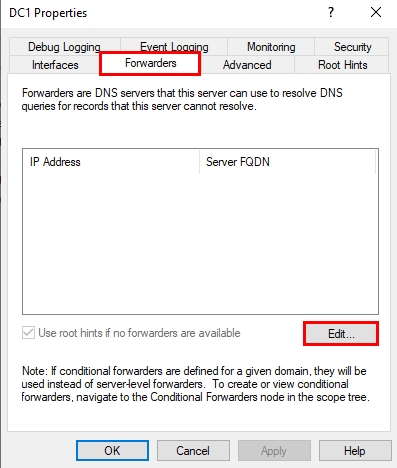
4. Now, add the IP address of the DNS server(s) to which you want to forward the DNS external requests. You can add many DNS servers. As of our example, we have added two Google public DNS servers (8.8.8.8 and 8.8.4.4). Click on a DNS server you have added, and you can set the order or delete it using the buttons on the right pane. Once everything is set, click on the OK button.
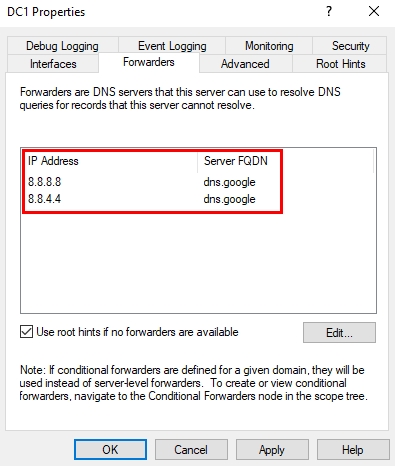
5. As you can see in the below picture, our two DNS servers are added to DNS Forwarders. Now our DNS server forwards any external DNS requests to one of these two DNS servers. Finally, Click on OK to close the window.
All right. In five simple steps with picture illustration, we have explained how to configure a DNS forwarder in Windows Server 2022.
Configure a DNS Conditional Forwarder in Server 2022
A Conditional Forwarder, as we discussed earlier, resolves the external DNS requests only for a specific domain. We define that external domain in our DNS server. Our DNS server then resolves the external DNS request only for that domain. It forwards any external DNS requests other than for that domain to the DNS server(s) defined in forwarders or to the DNS servers in the root hint. Having said this stuff, let’s move on and see the steps to configure a DNS Conditional Forwarder in Windows Server 2022.
1. Open up the DNS Manager console (step 1 of the previous section)
2. Expand the DNS server and right-click on Conditional Forwarders. Select the New Conditional Forwarder option from the list.
3. On the New Conditional Forwarder window, first, enter the domain’s name that your DNS server should resolve the request for it. Then, enter the IP address of that domain. Next, if you want to store this conditional forwarder in the active directory, check out the relevant checkbox (labelled 3 in the below picture) and choose the appropriate replication option. Otherwise, leave this option unchecked. Finally, click on the OK button.
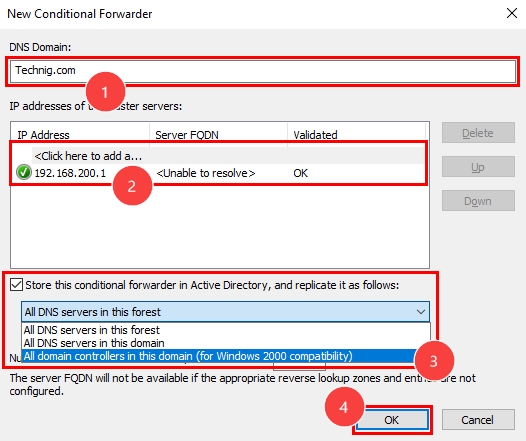
These are all the steps required to configure a conditional forwarder on a DNS server with Windows Server 2022. Pretty easy!
Conclusion
Throughout this article, first, we discussed a brief overview of the DNS Forwarder and DNS Conditional Forwarder. Then, in two separate sections, we covered a step-by-step guide on how to configure a DNS Forwarder and DNS Conditional Forwarder in Windows Server 2022.
I hope you find this article helpful in any way. Make sure to share your thoughts and queries in the comment section below.
Read More:
- DHCP PowerShell Commands.
- How To See Wi-Fi Password On Windows 11?
- How To Bypass Windows 11 Requirements?
In this article, we will look at two ways to organize conditional name resolution in a DNS server on Windows Server 2016/2019/2022: DNS Conditional Forwarding and DNS Policies. These technologies allow you to configure conditional DNS name resolution based on the requested name, IP address, client location, time of day, etc.
Contents:
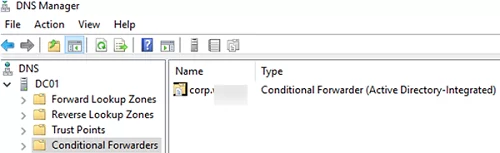
- How to Configure DNS Conditional Forwarder on Windows Server?
- Configure DNS Conditional Forwarding with PowerShell
- Filter DNS Queries with the Windows Server DNS Policies
DNS Conditional Forwarding allows to forward DNS requests about a particular domain to specific DNS servers. Usually, Conditional Forwarders are used when you want to configure fast name resolution between multiple private internal domains, or if you do not want DNS requests from your server to be sent through the Internet. In this case, you can create a rule on your DNS server to forward DNS requests for a particular domain zone (only!!!) to a specified DNS server.
How to Configure DNS Conditional Forwarder on Windows Server?
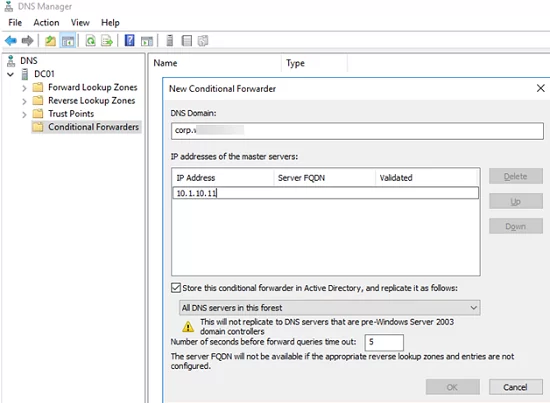
Let’s try to configure DNS conditional forwarding for a specific domain zone on Windows Server 2019. For example, all DNS requests to corp.woshub.com zone should be forwarded to the DNS server 10.1.10.11.
- Open the DNS management console (
dnsmgmt.msc); - Expand your DNS server, right-click Conditional Forwarders, and select New Conditional Forwarder;
- Enter the FQDN of the domain for which you want to enable conditional forwarding in the DNS domain field;
- Specify the IP address of the DNS server to which all requests for the specified namespace should be forwarded in the IP addresses of the master servers field;
- If you want to store a conditional forwarding rule on more than just this one DNS server, you can integrate it with AD. Check the option Store this conditional forwarder in Active Directory;
- Configure the conditional forwarding replication option (All DNS servers in this forest, All DNS servers in this domain, or All domain controllers in this domain).
Configure DNS Conditional Forwarding with PowerShell
You can create a Conditional Forwarder rule for a DNS zone using PowerShell. Use the Add-DnsServerConditionalForwarderZone cmdlet:
Add-DnsServerConditionalForwarderZone -Name dmz.woshub.com -MasterServers 192.168.1.11,192.168.101.11 -ReplicationScope Forest
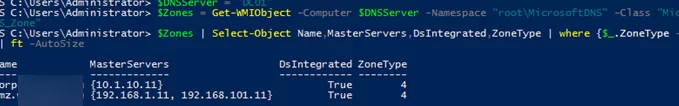
Run the following PowerShell script to list DNS conditional forwarders on a specific server:
$DNSServer = "DC01"
$Zones = Get-WMIObject -Computer $DNSServer -Namespace "root\MicrosoftDNS" -Class "MicrosoftDNS_Zone"
$Zones | Select-Object Name,MasterServers,DsIntegrated,ZoneType | where {$_.ZoneType -eq "4"} | ft -AutoSize
Filter DNS Queries with the Windows Server DNS Policies
Windows Server 2016 adds a DNS policy feature to the DNS server. DNS Policies allow you to configure the DNS server to return different responses to DNS queries depending on where you’re located (depending on the IP address or subnet from which the request was sent), the interface of the DNS server, the time of day, the type of record requested (A, CNAME, PTR, MX), etc. DNS policies in Windows Server allow you to implement load balancing, DNS traffic filtering, DNS record return based on geographic location (client IP address), and other complex scenarios.
You can create a policy at the level of a DNS server or a specific domain zone. The configuration of DNS policies in Windows Server can only be done from the PowerShell command line.
Let’s try to create a simple policy that returns a different response to a DNS query depending on the location of a client. Suppose you want clients in each branch to use their local proxy server on a site.
You have created a GPO to configure proxy settings in the domain (proxy.woshub.com will be specified on all clients). However, in order to use their local proxy server, clients from different offices need to resolve this FQDN differently.
I have created 3 subnets for company branches:
Add-DnsServerClientSubnet -Name "BER_DNS_Subnet" -IPv4Subnet "192.168.1.0/24"
Add-DnsServerClientSubnet -Name "HH_DNS_Subnet" -IPv4Subnet "192.168.11.0/24"
Add-DnsServerClientSubnet -Name "MCH_DNS_Subnet" -IPv4Subnet "192.168.21.0/24"
You must run these commands on all DCs that you want to enable the conditional DNS policy on. These settings are not replicated in DNS and are stored locally in the DNS server’s registry. You can specify a server name using the -ComputerName dc01 option.
List all available IP subnets on the DNS server:
Get-DnsServerClientSubnet
Now you need to create a separate DNS zone for each office:
Add-DnsServerZoneScope -ZoneName "woshub.com" -Name "BERZoneScope"
Add-DnsServerZoneScope -ZoneName "woshub.com" -Name "HHZoneScope"
Add-DnsServerZoneScope -ZoneName "woshub.com" -Name "MCHZoneScope"
The following commands will add 3 DNS records with the same name pointing to different IP addresses in different DNS zones:
Add-DnsServerResourceRecord -ZoneName "woshub.com" -A -Name proxy -IPv4Address "192.168.1.10" -ZoneScope "BERZoneScope"
Add-DnsServerResourceRecord -ZoneName "woshub.com" -A -Name proxy -IPv4Address "192.168.11.10" -ZoneScope "HHZoneScope"
Add-DnsServerResourceRecord -ZoneName "woshub.com" -A -Name proxy -IPv4Address "192.168.21.10" -ZoneScope "MCHZoneScope"
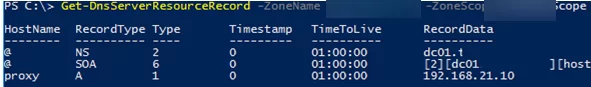
You can list all the DNS resource records in a zone using the command below:
Get-DnsServerResourceRecord -ZoneName "woshub.com" -ZoneScope BERZoneScope
Then create DNS policies that bind IP subnets, DNS zones, and A records.
Add-DnsServerQueryResolutionPolicy -Name BERResolutionPolicy -Action ALLOW -ClientSubnet "eq,BER_DNS_Subnet" -ZoneScope "BERZoneScope,1" -ZoneName woshub.com –PassThru
Add-DnsServerQueryResolutionPolicy -Name HHResolutionPolicy -Action ALLOW -ClientSubnet "eq,HH_DNS_Subnet" -ZoneScope "HHZoneScope,1" -ZoneName woshub.com -PassThru
Add-DnsServerQueryResolutionPolicy -Name MCHResolutionPolicy -Action ALLOW -ClientSubnet "eq,MCH_DNS_Subnet" -ZoneScope "MCHZoneScope,1" -ZoneName woshub.com –PassThru
The following actions are available in the DNS policies:
-Action ALLOW-Action DENY-Action IGNORE
You can use the following options in your DNS filters:
-InternetProtocol "EQ,IPv4,NE,IPv6"
-TransportProtocol "EQ,UDP,TCP"
-ServerInterfaceIP "EQ,192.168.1.21"
-QType "EQ,A,AAAA,NE,PTR"
-TimeOfDay "EQ,9:00-18:00"
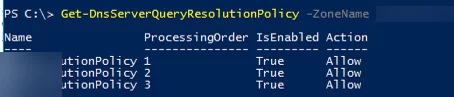
You can display a list of DNS policies for a DNS zone on the server:
Get-DnsServerQueryResolutionPolicy -ZoneName woshub.com
Now check that the DNS server returns different proxy IP addresses for the same request sent from devices in different offices:
nslookup proxy.woshub.com
You can prevent your DNS server from returning DNS addresses for a namespace (domain):
Add-DnsServerQueryResolutionPolicy -Name 'BlockDNSQuery' -Action IGNORE -FQDN "EQ,*.spamorg.org"
Windows DNS forwarders and DNS conditional forwarder are an important part of your DNS infrastructure. In this tutorial, we’re going to cover AD DNS forwarders and how you can manage them in your environment.
Not a reader? Watch this related video tutorial!
Not seeing the video? Make sure your ad blocker is disabled.
You will find that on occasion you need to add or manage these forwarder addresses. Some of these changes need to be made across multiple DNS servers in your enterprise. Thankfully, using commands like PowerShell’s Set-DnsServerForwarder cmdlet and others allow you to easily manage both of these DNS services with ease.
This blog post has a companion video created by TechSnips contributor, David Lamb. Feel free to have a watch or, if you prefer text, read on!
Replacing DNS Forwarders
DNS forwarders are used by a DNS server to lookup queries for addresses that aren’t contained in any zones that the server is authoritative for. This provides your DNS servers with an efficient means for resolving names. Without the forwarders in place, your DNS server would have to query the root hint servers to start resolving unknown addresses.
While these forwarder addresses are configured separately on each DNS server, using PowerShell makes managing them a lot easier by allowing us to use the Set-DnsServerForwarder cmdlet.
Begin by viewing the currently configured forwarders for the local DNS server. We’ll do this by using the Get-DnsServerForwarder cmdlet. We’re using the Get-* cmdlet first because you first need to find all existing forwarders.
As seen below, there are two forwarders configured with IP addresses of 8.8.8.8 and 8.8.4.4.
PS> Get-DnsServerForwarder
Now add an additional forwarder. This forwarder could possibly a new DNS server that you have configured in our DMZ, or perhaps using a forwarding address provided by our ISP. In this case, you’ll use the Set-DnsServerForwarder cmdlet to set the new address and then use Get-DnsServerForwarder to confirm that the address was set correctly.
Set-DnsServerForwarder -IPAddress 192.168.1.1
Get-DnsServerForwarderUnfortunately, this did not have the desired outcome. As you can see above, using the Set-DnsServerForwarder cmdlet actually replaces the list of forwarders rather than adding to it. To add the address to the list, rather than replacing the entire list, you need to use Add-DnsServerForwarder.
To correct this, replace the list with the original two forwarders, add the new address, then check to see if you are successful.
Set-DnsServerForwarder -IPAddress 8.8.8.8, 8.8.4.4
Add-DnsServerForwarder -IPAddress 192.168.1.1
Get-DnsServerForwarder
You now have all three forwarders added.
Removing DNS Forwarders
Let’s say you want to remove a forwarder address, you would use the Remove-DnsServerForwarder cmdlet as shown below. Then, you’d check to see if the address has been removed.
If Set-DnsServerForwarder replaces the DNS forwarder, Remove-DnsServerForwarder removes it completely.
Remove-DnsServerForwarder -IPAddress 192.168.1.1
Get-DnsServerForwarder
Scaling to Multiple DNS Servers
Sometimes, you will need to be able to add or remove a forwarder address on multiple DNS servers. In this instance, Set-DnsServerForwarder will not work. Thankfully PowerShell makes scaling this task to multiple DNS servers relatively easy. If you use Invoke-Command, include a list of all of our DNS servers, then put Add-DnsServerForwarder into the scriptblock parameter value, you can modify all of the DNS servers with a single command. Then using a similar command, view the results of our changes.
Invoke-Command -ComputerName DC01, DC02, DC03 -ScriptBlock {
Add-DnsServerForwarder -IPAddress 192.168.1.1
}
Invoke-Command -ComputerName DC01, DC02, DC03 -ScriptBlock { Get-DnsServerForwarder }
DNS Conditional Forwarders
A special type of forwarder, called a conditional forwarder, cannot be modified with the Set-DnsServerForwarder cmdlet. This type of forwarder can be used when you have been provided with the IP address(es) of the DNS server(s) for a known DNS domain name.
DNS Conditional forwarders are used by the DNS server before using the server forwarders listed earlier in this article.
For example, if you have a conditional forwarder configured for tailspintoys.com, your DNS server will, after checking that it isn’t a domain it is authoritative for, check the conditional forwarders and find that an entry exists. At this point, your DNS server queries the DNS server listed for the desired address in the tailspintoys.com domain.
One nice feature of DNS conditional forwarders is that they can be replicated to other DNS servers in the same way that any Active Directory Integrated DNS Zone can be.
Start by checking to see if you have a conditional forwarder configured by using the Get-DnsServerZone cmdlet.

Conditional forwarders show up in this list with a ZoneType of forwarder. In this case, we don’t have one configured. So, you will use Add-DnsServerConditionalForwarderZone to create the conditional forwarder, set it to replicate to the entire Active Directory forest, and then confirm it has been created.
PS> Add-DnsServerConditionalForwarderZone `
-Name tailspintoys.com `
-MasterServers 10.10.14.240,10.10.14.241 `
-ReplicationScope Forest
PS> Get-DnsServerZone
The output shows that you have our conditional forwarder configured, and it is ready to go.
Summary
PowerShell really does make managing DNS forwarders a snap! You should now be able to use PowerShell to manage and automate AD DNS forwarders many different ways. We covered these forwarder at just about every angle.
By default name servers resolve the queries using their own zone file. Or use root hints in case of internet. DNS conditional forwarder is way to direct DNS server to use another DNS for name resolution for a specific domain.
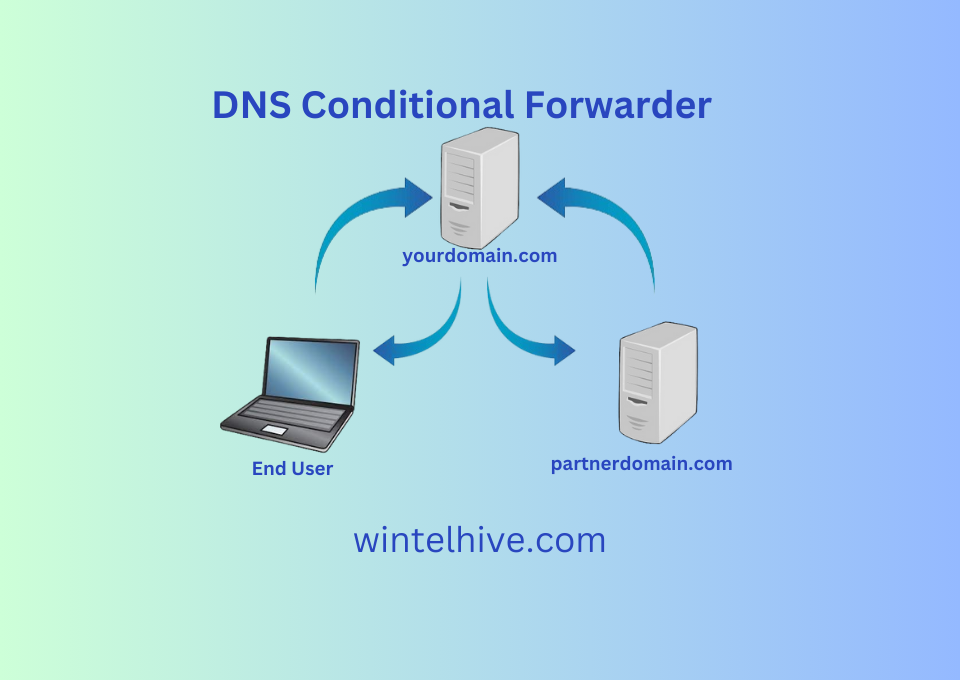
By default whenever a DNS receives a request, server use its internal database called zone file to resolve the request. If it can not find anything, it will go to the public DNS servers through root hints to find appropriate DNS for name resolution.
However there is another way. If you have applied DNS conditional forwarding, instead of going towards public DNS servers it will forward the request to another known DNS and get it resolved from there. Also it will keep the response in its cache to use for future purpose. For example a DNS server having zone yourdomain.com can not resolve your partner domain partnerdomain.com. If you have applied forwarding in your DNS for partnerdomain.com and pointed such queries to partner DNS server. Your clients can resolve partnerdomain.com related through your DNS server and not needed to go to partner DNS server directly.
How to Apply Conditional Forwarding in DNS
- Open DNS Console.
2. Right click the conditional forwarders and select New conditional forwarder.
3. Provide the domain name for which you want to apply forwarding. Add the IP address of DNS. Select time out means number of seconds before forward queries time out (5 sec by default). After validation is ok and you see a green tick.
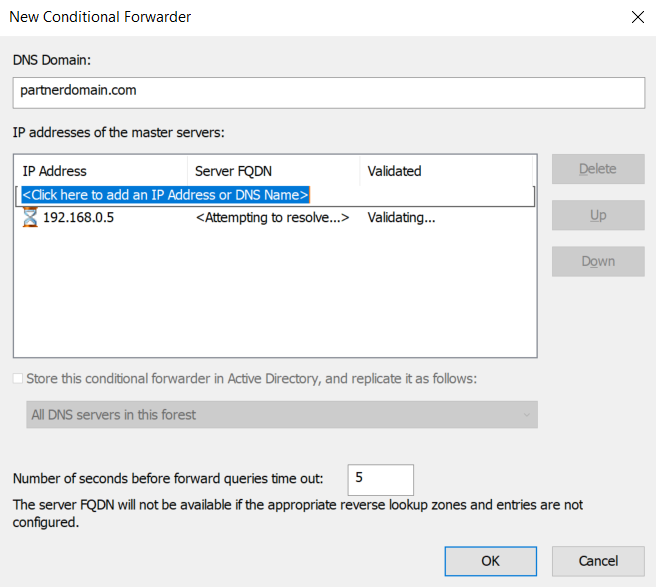
4. Click OK. Conditional forwarding is ready.
Use and Advantages Of Conditional Forwarding In DNS
- Internal and Partner Name Resolution: If you have internal, partner or local domains that you want to resolve quickly, you can use DNS forwarder.
- Less Internet Bandwidth: Typically DNS forwarders are used on local networks, partner network, VPN, extranet etc. As a result internet less queries are sent outside. It saves internet bandwidth. Also your DNS will maintain local cache and future queries will be resolved locally. It will further optimize you internet traffic.
- Better Security: Since internet is mostly not involved here and private network are used, this will be more secure.
- Quick Response and Better User Experience: Since local DNS cache is locally maintained, the response will be quicker. This will improve the performance significantly for frequently access websites.
- Safe Browsing: It is possible that you can use DNS forwarding to block some websites and specific domain too. (However there are better alternates available in the market to control internet access)
- Private Name Resolution: In some cases DNS servers are needed to be kept private. You may not want to put it on internet but still want to resolved the queries for your corporate users. DNS forwarding helps in implementing such scenarios.
Apply windows DNS conditional Forwarders Using PowerShell
- PowerShell to apply forwarding to a single DNS server.
- Add-DnsServerConditionalForwarderZone -name partnerdomain.com 192.168.0.5
- PowerShell to apply forwarding to a multiple DNS server.
- Add-DnsServerConditionalForwarderZone -name partnerdomain.com 192.168.0.5,192.168.0.6
Troubleshooting DNS Forwarding
- DNS record are missing: The administrator need to create the DNS record in case DNS record does not exist.
- Port blocked: It is often observed configuration is correct but the port 53 is blocked either on network or operating system firewall.
- Aging and scavenging: Scavenging is common cause of DNS issue. If you have misconfigured DNS aging or scavenging. No refresh and refresh intervals are too low, it may result into name resolution issues.
- DNS Firewall & Security: Some DNS firewalls and security tools restrict the traffic. You may need to check in your network if such security is implemented and act accordingly.
- DNS Misconfigurations: You maybe be pointing to the wrong DNS server. In such case you need to rectify TCP/IP settings.
Conditional Forwarding in Active Directory Environment
DNS forwarder is frequently used in active directory environments to resolve interdomain, inter-forest, partner and third party name resolution. In complex environments having multiple forests or domain, DNS forwarding helps in quick easy and reliable name resolution without relying on public networks.
You need to have a very good understanding of DNS server to get understand completely about forwarding. The article is written by using Microsoft Windows DNS Server 2019 standard operating system. For other windows servers operating systems process remains same.
Frequently Asked Questions (FAQ)
Can you apply domain forwarding for multiple domain?
Yes. You can use DNS forwarding feature for as many domains as you want.
Which ports are required for DNS forwarder?
DNS server always use port 53. Regardless its a ordinary DNS request or forwarding query.
Is DNS conational forwarding mandatory?
No. It is not mandatory to configure forwarding at all. You need to configure only if you want to resolve a specific domain though a specific target DNS server.
What is the difference between DNS forwarder and conditional forwarder?
DNS forwarder work on the server level. Any query regardless of domain name is forwarded to next DNS server if it can not be resolved locally. However in conditional forwarding only specified domain relate query will be forwarded to next DNS.
DNS forwarding Vs DNS conditional forwarding. Which one has more priority?
If you have implemented both. DNS conditional forwarders has more priority than forwarder. Any query will be tested against conditional forwarder first and forwarder later.
Is active directory windows DNS conditional forwarder mandatory?
No. DNS conditional forwarding can be setup in Non-Active directory environment too. Regardless there is active directory or not. Its always optional.
-
DNS Rebound Robin
Discover how DNS round robin can effortlessly balance traffic across multiple servers, boosting your website’s performance and reliability.
-
What Is DNS Ad Blocking
Learn how DNS ad blocking stops ads at the network level, boosting speed, protecting privacy, and improving browsing in your network.