From Wikipedia, the free encyclopedia
Distributed Component Object Model (DCOM) is a proprietary Microsoft technology for communication between software components on networked computers. DCOM, which originally was called «Network OLE», extends Microsoft’s COM, and provides the communication substrate under Microsoft’s COM+ application server infrastructure.
The extension COM into Distributed COM was due to extensive use of DCE/RPC (Distributed Computing Environment/Remote Procedure Calls) – more specifically Microsoft’s enhanced version, known as MSRPC. [1]
In terms of the extensions it added to COM, DCOM had to solve the problems of:
- Marshalling – serializing and deserializing the arguments and return values of method calls «over the wire».
- Distributed garbage collection – ensuring that references held by clients of interfaces are released when, for example, the client process crashed, or the network connection was lost.
- Combining significant numbers of objects in the client’s browser into a single transmission in order to minimize bandwidth utilization.
One of the key factors in solving these problems is the use of DCE/RPC as the underlying RPC mechanism behind DCOM. DCE/RPC has strictly defined rules regarding marshalling and who is responsible for freeing memory.[2]
DCOM was a major competitor to CORBA.[3] Proponents of both of these technologies saw them as one day becoming the model for code and service-reuse over the Internet. However, the difficulties involved in getting either of these technologies to work over Internet firewalls, and on unknown and insecure machines, meant that normal HTTP requests in combination with web browsers won out over both of them.[4] Microsoft, at one point, attempted to remediate these shortcomings by adding an extra HTTP transport to DCE/RPC called ncacn_http (Network Computing Architecture connection-oriented protocol).[5]
DCOM was publicly launched as a beta for Windows 95 September 18, 1996.[6]
DCOM is supported natively in all versions of Windows starting from Windows 95, and all versions of Windows Server since Windows NT 4.0[7]
Security improvements
[edit]
As part of the initiative that began at Microsoft as part of Secure Development Lifecycle to re-architect insecure code, DCOM saw some significant security-focused changes in Windows XP Service Pack 2.[8]
In response to a security vulnerability reported by Tencent Security Xuanwu Lab in June 2021,[9] Microsoft released security updates for several versions of Windows and Windows Server, hardening access to DCOM.[10]
Alternative versions and implementations
[edit]
COMsource is a Unix based implementation of DCOM, allowing interoperability between different platforms. Its source code is available, along with full and complete documentation, sufficient to use and also implement an interoperable version of DCOM. COMsource comes directly from the Windows NT 4.0 source code, and includes the source code for a Windows NT Registry Service. [11]
In 1995, Digital and Microsoft announced Affinity for OpenVMS (also known as NT Affinity) which was intended to allow OpenVMS to serve as the persistence layer for Windows NT client-server applications.[12] As part of this initiative, an implementation of the Distributed Component Object Model (DCOM) was added to OpenVMS Alpha.[13] In order to support DCOM, VMS was provided with implementations of the Windows Registry, NTLM authentication, and a subset of Win32 APIs needed to support COM.[14] DCOM was first added to OpenVMS V7.2-1 for the Alpha.[15] A similar implementation of DCOM was added to Digital Unix as part of the AllConnect program.[13]
TangramCOM was a separate project from Wine, focusing on implementing DCOM on Linux-based smartphones.[16]
- ActiveX
- Dynamic Data Exchange (DDE)
- .NET Remoting
- OLE for Process Control
- ^ «What is Distributed Component Object Model (DCOM)?». WhatIs.com. Retrieved 2022-08-03.
- ^ «DCE 1.1: Remote Procedure Call — Introduction to the RPC API». pubs.opengroup.org. Retrieved 2022-08-03.
- ^ Nowak, Filip; Qasim, Mohsin. «A Comparison of Distributed Object Technologies CORBA vs DCOM» (PDF). Archived (PDF) from the original on 2017-08-29.
- ^ «Object Technology Jeff Sutherland: Web Services: Better than CORBA or DCOM?». Retrieved 2022-08-03.
- ^ stevewhims (23 August 2019). «Remote Procedure Calls Using RPC over HTTP — Win32 apps». docs.microsoft.com. Retrieved 2022-08-03.
- ^ Press Release Announcing DCOM Beta
- ^ «Distributed Component Object Model (DCOM) Remote Protocol» (PDF). Microsoft — Distributed Component Object Model (DCOM) Remote Protocol. June 25, 2021. Archived (PDF) from the original on 2021-05-09. Retrieved August 3, 2022.
- ^ DCOM Security Enhancements
- ^ «Security Update Guide — Microsoft Security Response Center». msrc.microsoft.com. Retrieved 2022-08-03.
- ^ «KB5004442—Manage changes for Windows DCOM Server Security Feature Bypass (CVE-2021-26414)». support.microsoft.com. Retrieved 2022-08-03.
- ^ «DataSheet COMsource for Solaris, Tru64 UNIX and other Platforms». DataSheet COMsource for Solaris, Tru64 UNIX and other Platforms.
- ^ «OpenVMS at 20 Nothing stops it» (PDF). Digital. October 1997. Archived (PDF) from the original on 2021-04-19. Retrieved 2021-02-12.
- ^ a b Gene Cronin, Terence P. Sherlock (2000). COM Beyond Microsoft: Designing and Implementing COM Servers on Compaq Platforms. Digital Press. ISBN 1555582265.
- ^ «OpenVMS Connectivity Developer Guide». hpe.com. July 2000. Archived from the original on 2020-12-04. Retrieved 2021-01-01.
- ^ «OpenVMS Alpha V7.2-1 Release Notes». odl.sysworks.biz. January 1999. Retrieved 2021-01-01.
- ^ «Home — TangramCOM». www.andjoin.com. Retrieved 2022-08-03.
- Distributed Component Object Model Protocol — DCOM/1.0
- The Open Groups COMsource Archived 2020-01-13 at the Wayback Machine
- TangramCOM
The Distributed Component Object Model (DCOM) is a Microsoft technology for software components distributed across multiple network locations. Building upon the Component Object Model (COM), which enables inter-process communication and dynamic object creation, DCOM extends these capabilities over a network, allowing applications to interact across various computers in a network. This article aims to delve deeply into the intricacies of DCOM, illustrating how it facilitates distributed computing and its impact on software development. For a foundational understanding of COM, refer to our main article on COM. Our focus here is to explore DCOM’s architecture, operation, and applications, providing college-level insights into this pivotal technology.
Table of Contents:
- What is DCOM?
- How it Works
- DCOM Architecture
- Technologies that have supplanted DCOM
- References
1. What is DCOM (Distributed Component Object Model)?
DCOM is a technology for component-based development of software that is network-aware. Using Distributed Component Object Model (DCOM), developers can create network-aware applications using Component Object Model (COM) components. DCOM works under various network transports, including TCP/IP.
DCOM, or Distributed Component Object Model, is a technology that dates back to the late 1990s. It was developed by Microsoft as an extension of COM (Component Object Model) to support distributed computing. While DCOM was a significant advancement in its time, enabling applications to communicate across different machines in a network, it is considered somewhat outdated in modern computing environments.
The use of DCOM has declined over the years for several reasons:
- Complexity: DCOM is known for its complex configuration, especially in terms of security and network settings. This complexity often makes it difficult to manage, particularly in large-scale and diverse network environments.
- Platform Dependency: DCOM is heavily tied to the Windows operating system, which limits its interoperability with other platforms. In today’s multi-platform environments, this is a significant limitation.
- Evolution of Technology: Newer technologies have emerged that offer more flexibility, better security, and easier cross-platform integration. These technologies have largely replaced DCOM in most applications.
2. How it works
DCOM is a client/server protocol that provides distributed network services to COM, allowing DCOM-enabled software components to communicate over a network similarly to the method by which COM components communicate among themselves on a single machine.
DCOM client objects make requests for services from DCOM server objects on different machines on the network using a standard set of interfaces.
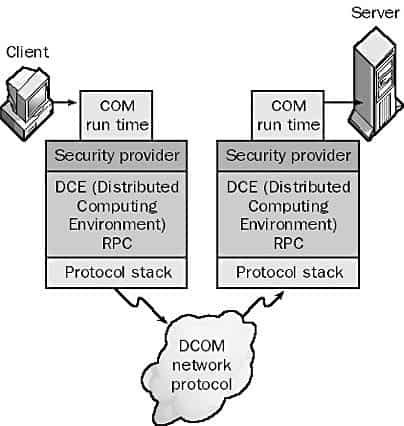
The client object cannot call the server object directly. Instead, the operating system intercepts the DCOM request and uses interprocess communication mechanisms such as remote procedure calls (RPCs) to provide a transparent communication mechanism between the client and server objects. The COM run time provides the necessary object-oriented services to the client and server objects. The COM run time also uses the security provider and RPCs to create network frames that conform to the DCOM standard.
3.1 Components and Interfaces
The architecture of DCOM (Distributed Component Object Model) is an extension of COM (Component Object Model), designed to support communication among software components at different locations on a network. DCOM defines a set of interfaces and objects which cooperate to achieve object creation, event handling, and other functionalities over a network. The key components include the client, server, and the DCOM network layer. The client initiates requests for services, the server hosts the objects providing these services, and the network layer manages communication between client and server. Each object in DCOM is identified by a unique identifier, ensuring precise object handling across the network.
3.2 Communication Mechanisms
DCOM uses a combination of remote procedure calls (RPCs) and additional protocols to facilitate communication between distributed components. RPCs allow a program on one machine to execute procedures on a remote machine as if they were local calls. DCOM enhances this with object-oriented methodologies and manages the complexities of network communication, including marshalling and unmarshalling of data, handling network transports, and managing object references across different machines. This ensures that DCOM can efficiently handle the nuances of distributed computing, like network latency and partial failures, while maintaining a seamless interface for developers.
Some of the technologies that have supplanted DCOM include:
- Web Services and SOA (Service-Oriented Architecture): Web services, often implemented using protocols such as SOAP (Simple Object Access Protocol) and REST (Representational State Transfer), allow different applications to communicate over the Internet. SOA provides a way to structure applications as a collection of services that can be reused and combined.
- .NET Remoting and WCF (Windows Communication Foundation): For applications within the Microsoft ecosystem, .NET Remoting and later WCF were developed to provide more flexible and secure ways to build distributed applications.
- CORBA (Common Object Request Broker Architecture): In non-Microsoft environments, technologies like CORBA have been used for distributed object-oriented programming.
- Microservices Architecture: More recently, the microservices architectural style has gained popularity, where applications are structured as collections of loosely coupled services.
While DCOM might still be in use in some legacy systems, especially in enterprise settings where older applications are maintained, it’s generally not the technology of choice for new distributed applications. The modern landscape favors technologies that are more adaptable, secure, and platform-agnostic.
5. References
- “Understanding DCOM” by William Rubin and Marshall Brain.
- “Programming Distributed Applications with COM+ and Microsoft Visual Basic” by Ted Pattison.
- “Inside COM+: Base Services” by Guy and Henry Eddon.
- Microsoft’s official documentation on DCOM.
The Distributed Component Object Model (DCOM) protocol is a Microsoft technology that extends the Component Object Model (COM) to support communication between objects across a network. COM is a binary-interface standard that enables communication between software components, allowing them to work together as a single application. DCOM extends this communication to work over a network, allowing components on different computers to interact as if they were local.
DCOM is built on top of the Remote Procedure Call (RPC) protocol, which enables one process to call functions in another process running on a remote computer. It uses the Object Remote Procedure Call (ORPC) layer to provide a higher level of abstraction that allows clients to interact with server objects.
Key concepts in DCOM:
- Interface: An interface is a collection of methods (functions) that a COM object implements. Clients communicate with COM objects by calling methods on their interfaces.
- Object: A COM object is an instance of a class that implements one or more interfaces. An object can provide services to clients by exposing interfaces.
- Class: A class is a blueprint for creating objects. It defines the properties, methods, and events that an object can have.
- Class Factory: A class factory is responsible for creating instances of a specific class. When a client requests an object, the class factory creates it and returns a reference to one of its interfaces.
- Server: A server is an application that hosts COM objects. It can be a standalone application (EXE) or a dynamic-link library (DLL).
- Client: A client is an application that consumes the services provided by COM objects. It communicates with these objects by calling methods on their interfaces.
- Proxy: A proxy is a local object that represents a remote object. It is used by the client to communicate with the remote object.
- Stub: A stub is a remote object that represents a local object. It is used by the server to communicate with the local object.
DCOM’s main features include:
- Location Transparency: DCOM allows clients to access remote objects as if they were local, hiding the complexity of network communication.
- Language Independence: DCOM supports various programming languages, allowing components written in different languages to interact seamlessly.
- Security: DCOM provides multiple levels of security, including authentication, authorization, and encryption, to protect data during communication.
- Scalability: DCOM enables the distribution of components across multiple machines, allowing applications to scale as needed.
- Object Activation: DCOM supports object activation, which allows clients to create remote objects on demand.
While DCOM was widely used in the past, it has been largely replaced by more modern and flexible technologies like the .NET Framework, Web Services, and RESTful APIs. However, DCOM is still used in some legacy systems, and understanding its principles can provide insights into distributed application development.
DCOM enables components residing on different computers to interact as if they were local, allowing for the creation of distributed applications. It is built on top of the Remote Procedure Call (RPC) protocol, which facilitates communication between processes on different computers. DCOM uses the Object Remote Procedure Call (ORPC) layer to provide a higher level of abstraction for clients to interact with server objects.
The main features of DCOM include:
- Location Transparency: Clients can access remote objects as if they were local, hiding the complexity of network communication.
- Language Independence: DCOM supports various programming languages, allowing components written in different languages to interact seamlessly.
- Security: DCOM provides multiple levels of security, including authentication, authorization, and encryption, to protect data during communication.
- Scalability: DCOM enables the distribution of components across multiple machines, allowing applications to scale as needed.
- Object Activation: DCOM supports object activation, which allows clients to create remote objects on demand.
The Purpose Of DCOM
The primary purpose of DCOM (Distributed Component Object Model) is to enable the development of distributed applications by allowing software components to communicate and interact with each other across a network. DCOM extends the capabilities of the Component Object Model (COM) to support communication between components on different computers as if they were on the same machine. This facilitates the creation of scalable, distributed applications that can leverage resources and functionality distributed across an organization’s infrastructure.
Benefits Of DCOM
DCOM provides several benefits for distributed application development. These benefits include:
- Location Transparency: DCOM allows developers to create applications that can access remote objects as if they were local, simplifying the development process and providing a consistent programming model for both local and remote objects.
- Language Independence: DCOM supports various programming languages, enabling components written in different languages to interact seamlessly. This promotes interoperability and allows developers to choose the most suitable language for a specific task.
- Reusability and Modular Design: DCOM encourages the creation of reusable, modular software components that can be combined and reused in various configurations. This can lead to reduced development time, easier maintenance, and increased software quality.
- Scalability: DCOM enables the distribution of components across multiple machines, allowing applications to scale as needed. This is particularly important for enterprise-level applications that need to handle large workloads or adapt to changing demands.
- Security: DCOM provides multiple levels of security, including authentication, authorization, and encryption, to protect data during communication between components. This ensures that sensitive information is not exposed during the execution of distributed applications.
- Object Activation: DCOM supports object activation, which allows clients to create remote objects on demand. This can help reduce resource usage and improve application performance by only activating objects when they are needed.
- Integration with Existing Technologies: DCOM integrates with other Microsoft technologies, such as Active Directory for security and administration, and OLE (Object Linking and Embedding) for embedding and linking objects in documents and applications.
Limitations Of DCOM
While DCOM provided several benefits for distributed application development, it also has some limitations that have led to its replacement by more modern technologies like the .NET Framework, Web Services, and RESTful APIs. Some of these limitations include:
- Platform Dependency: DCOM is primarily designed for Windows-based systems, making it less suitable for cross-platform development. Although there have been attempts to implement DCOM on other platforms, the support is limited and not as seamless as other technologies.
- Complexity: DCOM can be challenging to configure, especially when dealing with security settings and network configurations. This complexity may lead to increased development time and difficulty in troubleshooting issues.
- Firewall Issues: DCOM relies on the Remote Procedure Call (RPC) protocol, which uses dynamic port allocation. This can create issues when passing through firewalls, as they typically require specific ports to be opened, and DCOM’s dynamic port allocation can make this difficult to manage.
- Limited Internet Support: DCOM was designed for use within local area networks (LANs) and is not optimized for the Internet. While it can be used over the Internet, it can suffer from performance and security issues, making it less suitable for modern web-based applications.
- Interoperability: Although DCOM supports various programming languages, it can struggle with interoperability between different platforms or when integrating with non-DCOM technologies.
- Maintenance and Debugging: Debugging and maintaining DCOM-based applications can be challenging, especially when dealing with remote objects and distributed components. This can increase the time required to identify and resolve issues in the application.
- Obsolescence: With the introduction of newer technologies like .NET Framework, Web Services, and RESTful APIs, DCOM has become less relevant in the world of distributed application development. These modern technologies offer better performance, security, and ease of development, making them more suitable for current development practices.
Despite these limitations, DCOM is still used in some legacy systems, and understanding its drawbacks can help developers make informed decisions when choosing technologies for distributed application development.
How Does DCOM Work
DCOM is a Microsoft technology that extends the capabilities of the Component Object Model (COM) to support communication between software components across a network. Here is an overview of how DCOM works:
- Client-Server Model: DCOM follows a client-server model, where clients request services from server objects hosted on remote machines. Clients and servers communicate through interfaces, which are a collection of methods exposed by the server objects.
- Interface and Object: Clients interact with server objects using interfaces, which act as contracts that define methods and properties that the object supports. Objects are instances of classes, and they implement one or more interfaces to provide their services.
- Object Activation: When a client wants to use a remote object, it requests the object’s activation. DCOM activates the object on the server and returns a reference to the client. The client can then call methods on the object through the reference.
- RPC and ORPC: DCOM is built on top of the Remote Procedure Call (RPC) protocol, which enables one process to call functions in another process running on a remote computer. DCOM uses the Object Remote Procedure Call (ORPC) layer to provide a higher level of abstraction, allowing clients to interact with server objects instead of dealing with low-level RPC details.
- Proxies and Stubs: To communicate with remote objects, DCOM uses proxies and stubs. A proxy is a local object that represents a remote object in the client process, while a stub is a remote object that represents the local object in the server process. Proxies and stubs handle the marshaling and unmarshaling of data between the client and server during method calls.
- Security: DCOM provides multiple levels of security, including authentication, authorization, and encryption. Authentication verifies the identity of the client and server, authorization determines what actions the client is allowed to perform, and encryption protects the data during communication.
- Distributed Garbage Collection: DCOM implements distributed garbage collection to manage the lifecycle of remote objects. When a client no longer needs a remote object, it releases the reference, and DCOM checks if there are any remaining references to the object. If there are no remaining references, DCOM deactivates the object and reclaims the resources.
DCOM enabled the development of distributed applications by providing a framework for communication between software components on different computers.
Security Concerns Of DCOM
While DCOM provides several security features, including authentication, authorization, and encryption, it also has some security concerns that developers should be aware of. These concerns include:
- Complexity: DCOM’s complexity, particularly when configuring security settings and network configurations, can lead to misconfigurations and security vulnerabilities. Misconfigurations may expose sensitive data or allow unauthorized access to system resources.
- Firewall Issues: DCOM relies on the Remote Procedure Call (RPC) protocol, which uses dynamic port allocation. This can create challenges when working with firewalls, as they typically require specific ports to be opened. DCOM’s dynamic port allocation can make it difficult to manage and secure network communications, potentially leaving openings for attackers.
- Limited Internet Support: DCOM was designed primarily for use within local area networks (LANs) and is not optimized for the Internet. When used over the Internet, DCOM can suffer from performance and security issues, making it less suitable for modern web-based applications.
- Vulnerabilities: Over the years, DCOM has had several known security vulnerabilities, some of which have been exploited by malicious actors. Ensuring that all patches and updates are applied is critical to mitigating these risks, but it may not be enough to protect against all potential threats.
- Interoperability: While DCOM supports various programming languages, it can struggle with interoperability between different platforms or when integrating with non-DCOM technologies. This can lead to security challenges when trying to establish secure communication channels between disparate systems.
- Maintenance and Debugging: Debugging and maintaining DCOM-based applications can be challenging, particularly when dealing with remote objects and distributed components. This can make it harder to identify and resolve security issues in a timely manner.
- Obsolescence: With the rise of more modern and secure technologies like the .NET Framework, Web Services, and RESTful APIs, DCOM has become less relevant in distributed application development. These technologies offer better performance, security, and ease of development, making them more suitable for current development practices.
Despite these security concerns, DCOM is still used in some legacy systems. Developers working with DCOM should be aware of these concerns and implement proper security measures to mitigate risks. However, for new applications, more modern and secure technologies like the .NET Framework, Web Services, and RESTful APIs are recommended.
Attack Examples Using DCOM
One significant example of an attack that exploited the DCOM protocol is the MSBlast worm, also known as the Blaster worm or Lovsan worm. This worm targeted a vulnerability in the DCOM protocol implementation on Windows operating systems and caused widespread damage.
The MSBlast worm exploited a buffer overflow vulnerability in the DCOM Remote Procedure Call (RPC) interface of Windows operating systems (specifically, Windows XP and Windows 2000). The vulnerability allowed attackers to execute arbitrary code on the affected systems with SYSTEM level privileges, enabling them to take control of the compromised machines.
Once a machine was infected, the worm would replicate itself and scan for other vulnerable systems on the network, spreading rapidly without any user intervention. The worm also launched a denial-of-service (DoS) attack against windowsupdate.com, attempting to disrupt Microsoft’s update service and prevent users from patching their systems.
The MSBlast worm caused significant disruption, infecting hundreds of thousands of computers worldwide and causing millions of dollars in damages. In response to the attack, Microsoft released a security patch (MS03-026) to address the vulnerability and urged users to update their systems.
This attack highlights the importance of keeping systems up-to-date and implementing proper security measures, particularly when using protocols like DCOM that have known vulnerabilities. Although DCOM has been largely replaced by more modern and secure technologies, understanding past attacks can help inform better security practices for distributed application development.
WireX Systems NDR can Help with DCOM Investigations
WireX Systems Ne2ition NDR (Network Detection and Response) is a security technology that focuses on detecting and analyzing network traffic to identify and respond to potential threats and attacks. Ne2ition NDR can help with investigations of attacks over DCOM (Distributed Component Object Model) by providing visibility into network activities, detecting unusual or malicious behaviors, and facilitating incident response. Here’s how NDR can help:
- Traffic Analysis: Ne2ition NDR solutions continuously monitor and analyze network traffic, enabling security teams to identify anomalies or suspicious activities that may indicate an attack. By examining DCOM-related network traffic, Ne2ition NDR can help detect unauthorized attempts to access remote objects or exploit vulnerabilities in the DCOM protocol.
- Anomaly Detection: Ne2ition NDR uses advanced analytics, machine learning, and artificial intelligence to establish a baseline of normal network behavior and detect deviations from this baseline. If there is unusual DCOM traffic or activity that deviates from the norm, Ne2ition NDR can flag it for further investigation.
- Threat Intelligence: Ne2ition NDR integrates with external threat intelligence sources, providing context and up-to-date information about known threats and attack patterns. This can help security teams identify known DCOM-related attacks or vulnerabilities, and take appropriate action to protect their environment.
- Incident Response: In the event of a detected attack or security incident involving DCOM, Ne2ition can help security teams investigate the scope, impact, and root cause of the issue. Ne2ition NDR provides features such as packet capture, network forensics, and automated response capabilities to assist with incident investigation and containment.
- Alerting and Reporting: Ne2ition NDR solutions can generate alerts and provide detailed reports on detected security incidents, including DCOM-related attacks. This information can help security teams prioritize their response efforts and track the progress of investigations.
- Integration with Security Ecosystem: Ne2ition NDR solutions can be integrated with other security tools and technologies, such as Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), and firewall solutions. This integration allows for a more comprehensive and coordinated approach to detecting and responding to DCOM-related attacks.
While Ne2ition NDR can be instrumental in investigating attacks over DCOM, it’s essential to remember that DCOM is an older technology that has been largely replaced by more modern and secure alternatives. Organizations should consider migrating to more secure technologies like the .NET Framework, Web Services, and RESTful APIs to minimize the risk of DCOM-related attacks.
Overall, WireX Systems leverages the power of network analysis to detect and protect against cyber threats.
WireX Systems Ne2ition analyzes DCOM traffic, extracts and indexes dozens of different attributes including the ones displays below to provide in-depth visibility and context for detection, response, forensics and hunting scenarios over DCOM
| Client IP | Packet Time | Preview of event | Errors |
| Auth Level | Interface Method | Client Port | Server ip |
| Server port | Interface | Return value | Security binding |
| Security provider | Class id | Class Name | Minor Version |
| Major Version | Casualty ID | Session Owner ID | CLS id |
| OX Id | IP ID | Response | Client Host name |
| Client Process ID | Principal Name | Protocol ID |
These attributes will also help WireX Systems map into the MITRE ATT&CK framework techniques and tactics.
MITRE ATT&CK and DCOM
The MITRE ATT&CK framework is a comprehensive knowledge base that classifies adversarial tactics, techniques, and procedures used by threat actors. While the framework doesn’t have specific techniques for DCOM (Distributed Component Object Model) attacks, some tactics and techniques can be related to DCOM exploitation. Here are a few examples:
- Execution (TA0002): DCOM attacks may involve the execution of arbitrary code on a target system, which aligns with the Execution tactic in the MITRE ATT&CK framework. An example of this is the MSBlast worm that exploited a buffer overflow vulnerability in the DCOM RPC interface, allowing remote code execution.
Technique: T1203 – Exploitation for Client Execution
- Lateral Movement (TA0008): DCOM attacks might leverage the protocol to move laterally within a network, taking advantage of DCOM’s ability to communicate with remote objects on other systems.
Technique: T1021 – Remote Services
- Persistence (TA0003): Some DCOM attacks may involve maintaining persistence on compromised systems. For instance, an attacker could create a remote object on a target system and use the object to execute code or maintain access.
Technique: T1021.002 – Remote Services: SMB/Windows Admin Shares
- Defense Evasion (TA0005): Attackers may use DCOM to evade defenses by leveraging the protocol’s inherent functionality and complexity to avoid detection or circumvent security measures.
Technique: T1090 – Proxy
- Discovery (TA0007): In the context of a DCOM attack, threat actors may use the protocol to discover information about remote systems, such as available objects, interfaces, and services.
Technique: T1018 – Remote System Discovery
- Privilege Escalation (TA0004): Exploiting DCOM vulnerabilities might lead to privilege escalation, allowing attackers to gain higher privileges and access to sensitive resources.
Technique: T1068 – Exploitation for Privilege Escalation
Keep in mind that the mapping of DCOM attacks to MITRE ATT&CK tactics and techniques depends on the specific attack scenario and the methods used by the threat actor. The examples provided above may not cover all possible DCOM-related attack techniques.
Conclusion
In conclusion, DCOM is a Microsoft technology that extends the capabilities of COM (Component Object Model) to facilitate communication between software components across a network. DCOM follows a client-server model, enabling clients to access and interact with remote objects as if they were local. This technology has provided numerous benefits for distributed application development, such as location transparency, language independence, reusability, and scalability.
However, DCOM has several limitations, including platform dependency, complexity, firewall issues, limited Internet support, interoperability challenges, and maintenance and debugging difficulties. These limitations have contributed to its decline in popularity, as more modern technologies like the .NET Framework, Web Services, and RESTful APIs have emerged to offer better performance, security, and ease of development.
DCOM also has several security concerns, such as misconfigurations, firewall challenges, and known vulnerabilities. Examples of significant DCOM-related attacks, like the MSBlast worm, highlight the importance of keeping systems up-to-date and implementing proper security measures. NDR (Network Detection and Response) can be instrumental in detecting and responding to DCOM-related attacks by providing visibility into network activities and facilitating incident response.
In light of its limitations and security concerns, organizations should consider migrating to more modern and secure alternatives, such as the .NET Framework, Web Services, and RESTful APIs, for distributed application development. Understanding DCOM’s benefits and drawbacks can provide valuable insights into past and present distributed computing technologies, enabling developers to make informed decisions when choosing the right technology for their needs.
Distributed Component Object Model (DCOM) is an extension to Component Object Model (COM) that enables software components to communicate with each other across different computers on a local area network (LAN), on a wide area network (WAN) or across the internet. Microsoft created DCOM to distribute COM-based applications in a way not possible with COM alone.
Over the years, COM has provided the foundation for numerous Microsoft products and technologies. COM defines a binary interoperability standard for creating reusable software components that can interact with each other at runtime. This includes a standard protocol and wire format that COM objects use to interact when running on different hardware components. COM standardizes function calls between components and provides a base interface for component interaction without requiring an intermediary system component.
DCOM extends COM by enabling clients and components to communicate even if they reside on different machines. To facilitate this communication, DCOM replaces the local interprocess communication used in traditional COM communication with a network protocol. In effect, DCOM provides a longer wire than COM, yet the client and the component are not aware of this difference.
What is DCOM architecture?
The DCOM wire protocol is based on Distributed Computing Environment/Remote Procedure Calls (DCE/RPC), which provides a standard for converting in-memory data structures into network packets. The DCOM protocol uses RPCs to expose application objects, while handling the low-level details of a network protocol. The client can call the component’s methods without incurring any overhead.
DCOM applications do not require a specific network transport protocol for carrying out client-component communications. DCOM can transparently use a variety of network protocols, including User Datagram Protocol, NetBIOS, TCP/IP and Internetwork Packet Exchange/Sequenced Packet Exchange. DCOM also provides a security framework that can be used on any of these protocols, whether connectionless or connection-oriented.
DCOM also includes a marshaling mechanism that enables a component to inject code on the client side. This code serves as a proxy object that can intercept multiple method calls from the client and bundle them into a single RPC. In addition, DCOM includes a distributed garbage collection mechanism that automatically releases unused references to COM objects, helping to free up memory on the host systems. The garbage collection process is transparent to the application.
Since its release, DCOM continues to be integrated into Windows operating systems. However, it has never been embraced outside the Microsoft ecosystem to the degree once anticipated. In addition, a recent discovery of a security vulnerability has caused Microsoft to implement hardening changes into DCOM, which are being rolled out in three stages. The first stage was introduced in 2021. The next is scheduled for 2022. And the final update related to this issue will occur in 2023.
DCOM is Microsoft’s approach to a network-wide environment for program and data objects. In many ways, it is similar to Common Object Request Broker Architecture (CORBA) introduced by Object Management Group. Like DCOM, CORBA provides a specification for distributed objects. However, because of security and scalability concerns, neither approach achieved the universal and widespread use that was once hoped for with the rise of the internet.
See 12 common network protocols and their functions explained.
This was last updated in June 2022
Continue Reading About Distributed Component Object Model (DCOM)
- How to use WMI and the CIM standard with Windows PowerShell
- Creating PowerShell scripts for task automation
- CISSP online training: Software Development Security domain
- Network virtualization benefits in the LAN, WAN and data center
- How enterprise networks use WAN virtualization
