,
If you want to view the user login history in Windows 10/11, then this article contains step by step instructions on how to do that.
When a user logs on to a computer, Windows records the time and date of the logon in the Event Viewer. This allows system administrators to find out the last login time or view the full login history of users to gather information about their activity.
This tutorial is divided into two parts. The first part contains instructions on how to view a user’s last login time, and the second part shows how to view the entire user’s login history in Windows 10/11.
- Related article: How to View Last Login Time of a User in Active Directory.
Part 1. View Last Login Time in Windows 10/11.
- View Last Login Date/Time from Command Prompt.
- View Last Logon Time from PowerShell.
Part 2. View Users Login History in Windows 10/11.
- View Login-Logout History in Event Viewer.
- View Login/Logoff History with WinLogOnView.
Part 1. How to View Last Login Time and Date in Windows 11/10.
Method 1. Find Last Login Time using NET USER Command.
The easiest way to find a user’s last logon date and time in Windows 10/11, is by simply executing «NET USER <USERNAME>» command in Command Prompt or in PowerShell. To do that:
1. Open Command Prompt or PowerShell and give the following command to view all the accounts on the machine.
- net user
2. Notice the username of the account that you want to view it’s last logon time, and give the following command to find user’s last logon date and time:*
- net user Username
* Note: Replace the «Username» with the username of the user you want to view the last login time. (e.g. «John» in this example.)
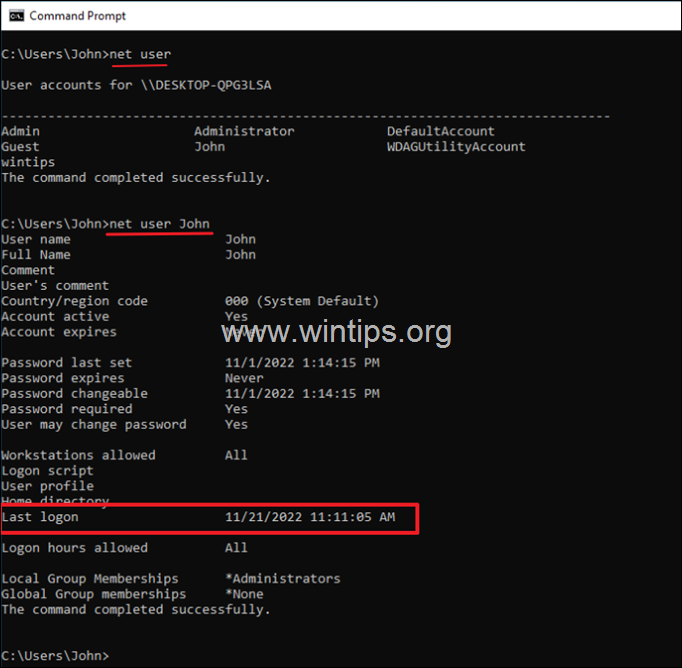
Method 2. Find Last Login Time of All Accounts in PowerShell.
If you want to view the last login date and time of all users in Windows 10/11, then open PowerShell and give the following command:*
- Get-LocalUser | Select Name, Lastlogon
* Note: The above command will show you the last login time of all accounts on your Windows 10/11 computer. If the last logon time for a user is blank, it means that the user has never logged on to the computer.
Part 2. How to View User Login History in Windows 10/11.
Method 3. View User Login-Logout History in Event Viewer.
The Windows Event Viewer allows system users to view all events logged by the system, such as errors or additional information about what has happened, for troubleshooting purposes.
To check the login history in Event Viewer, go to Security logs and view the events with Event ID 4624 or 4648 to view the Logon times, or look at 4647 events to view the Logout times. To do that:
1. Type event viewer on the search box and then open the Event Viewer app.
2. Expand the Windows Logs and select Security.
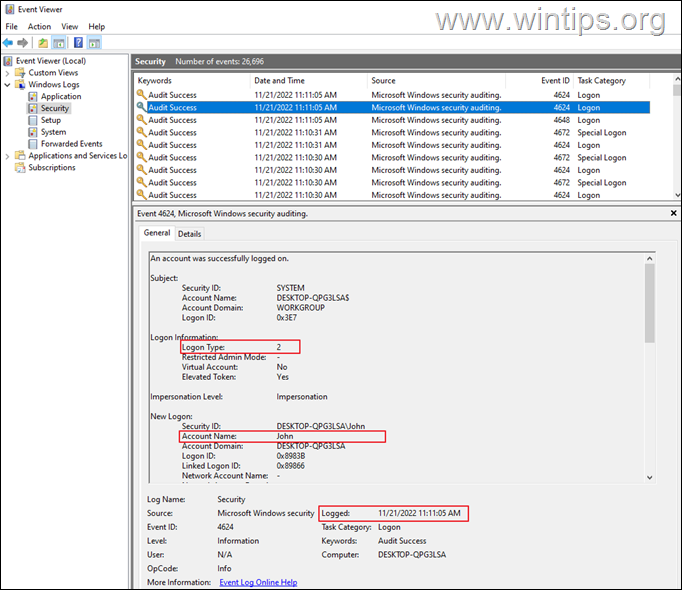
3a. In Security logs, open one-by-one all the events with Event ID 4624 (or 4648), and find which one has as Logon Type = 2 & at Account Name shows the username of a user (and not SYSTEM, NETWORK SERVICE, etc.).*
3a. Finally, view the Logged time, to see the login time and date of the user.
4. To view the Logoff times of a user, see the events with Event ID 4647.*
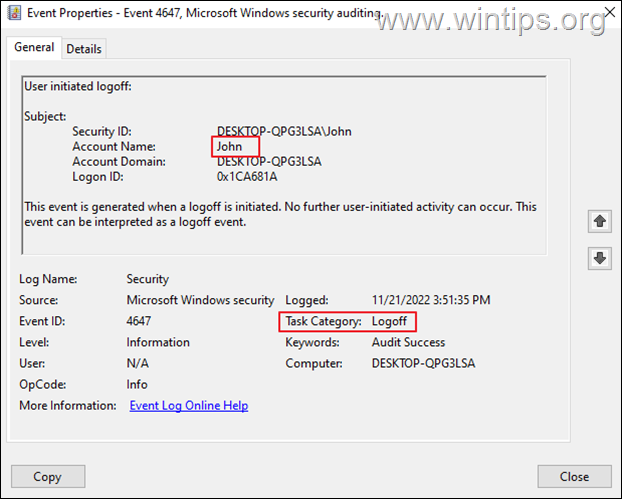
* Note: To make you life easier, Create a custom view and type 4624 or 4648 for Logon, or 4647 for Logoff, or see the next method.
Method 4. View Logon & Logoff Times with WinLogOnView.
In my opinion, the easiest way to see all users’ login and logout history, is by using the third-party utility WinLogOnView by NirSoft. To do that:
1. Download WinLogOnView and extract the ZIP file to a folder.
2. Explore the extracted folder and run the WinLogOnView application.
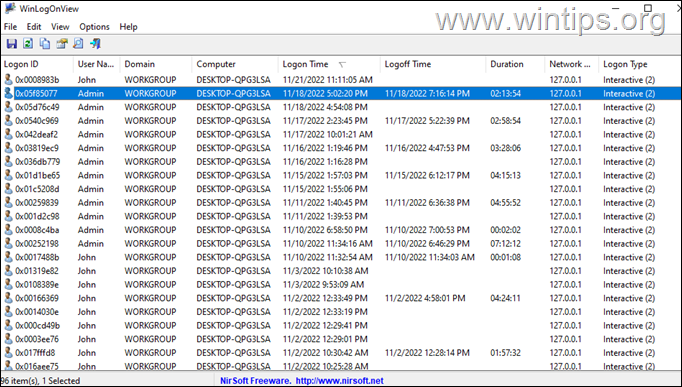
3. On your screen you will see the login and logout time of each computer user, the total duration of their connection and the IP address from which they connected (127.0.0.1 = locally).
That’s it! Which method worked for you?
Let me know if this guide has helped you by leaving your comment about your experience. Please like and share this guide to help others.
If this article was useful for you, please consider supporting us by making a donation. Even $1 can a make a huge difference for us in our effort to continue to help others while keeping this site free:
- Author
- Recent Posts
Konstantinos is the founder and administrator of Wintips.org. Since 1995 he works and provides IT support as a computer and network expert to individuals and large companies. He is specialized in solving problems related to Windows or other Microsoft products (Windows Server, Office, Microsoft 365, etc.).
In this tutorial, you’ll learn how to find the user’s last logon time using different methods. You can use any of these methods to determine an Active Directory user’s last sign-in date and time.
As a system administrator, there are many situations in which you want to find the user’s last logon date and time. You may probably want to audit any activity or gather all the inactive users in Active Directory over a period of time, etc.
There are numerous third-party software programs available that can help you determine a user’s last logon time. However, many people opt not to use these programs because they typically demand a license. Even if some of them are free, they have certain limitations. These programs must communicate with your Active Directory to retrieve information, and some businesses do not utilize it for security reasons.

What is LastLogonTimeStamp in Active Directory?
The purpose of the LastLogonTimeStamp is to help identify stale user and computer accounts. Administrators can use the lastLogontimeStamp attribute to determine if a user or computer account has recently logged onto the domain.
What is the difference between LastLogon and LastLogonTimeStamp?
The lastlogon attribute is the most accurate way to check active directory users last login time. Lastlogon is only updated on the domain controller that performs the authentication and is not replicated. Whereas LastLogontimestamp is replicated, but by default only if it is 14 days or older than the previous value.
Method 1: Find the user’s logon time in Active Directory
Finding the last logon time of a user is pretty simple using Active Directory.
- Login to a Domain Controller.
- Launch Active Directory Users and Computers console (dsa.msc).
- Click View and ensure Advanced features is turned on.
- On the left pane, click Users and select any user, right click the user account and click Properties.
- In the list of attributes, look for lastLogon. This attribute shows the time the user was last logged in the domain.
Method 2: Find User’s last logon time using CMD
Using the command prompt, you can find the last logon time of the user. You don’t need a domain admin account to get AD user information.
- Click Start and launch the command prompt.
- Run the command: net user username /domain| findstr “Last”
- The CMD output shows the user’s last logon time and date.

Method 3: Find User Last Logon time using PowerShell
You can find the user logon date and time using PowerShell command. You can run the below command either on a domain controller or a member server.
- Log in to a Domain Controller.
- Import the Active Directory PowerShell module, Import-Module ActiveDirectory.
- Run the below PowerShell command to find the user’s login time with date.
Get-ADUser -Identity "username" -Properties LastLogon
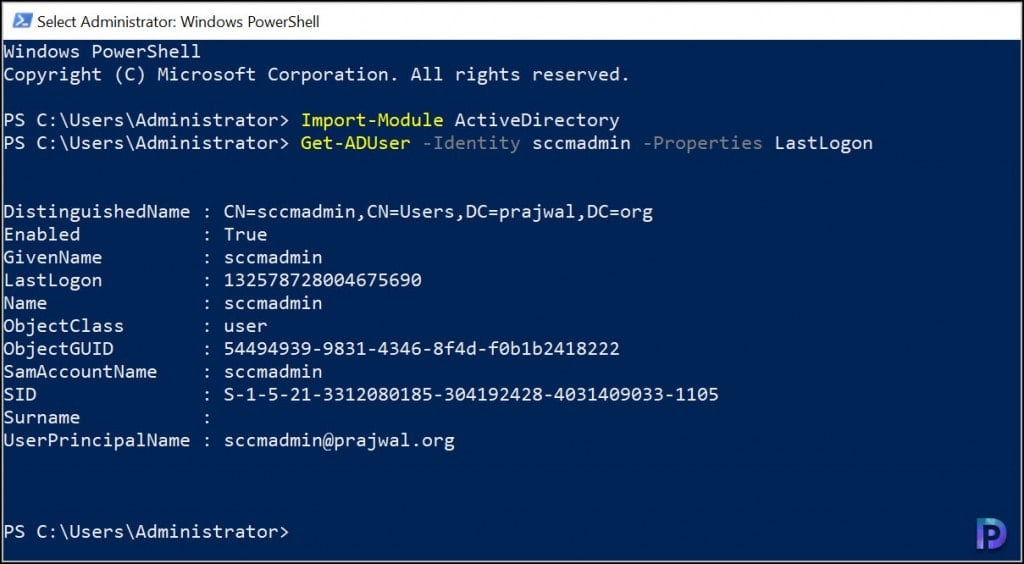
When you run the above command, notice that Lastlogon value is in a different format. It’s in a timestamp format and you need to convert the value to a readable format. Use the below command to convert the value to normal time. Do not forget to replace the user name with your username.
Get-ADUser -Filter {Name -eq "username"} -Properties * | Select-Object Name, @{N='LastLogon'; E={[DateTime]::FromFileTime($_.LastLogon)}}

Method 4: Find last Logon Time of User using SCCM
From the SCCM console, you can find the previous logon time of the user account. SCCM uses Active Directory to fetch the information when you run the discovery methods. Discovery creates a discovery data record (DDR) for each discovered object and stores this information in the SCCM database.
There are two prerequisites before you use SCCM to find the logon time of a user:
- You should have enabled the SCCM discovery methods before you intend to determine the user logon details. The Active Directory user discovery method must be enabled.
- On the Active Directory user discovery properties, ensure lastLogon and lastLogonTimestamp attributes are enabled for discovery.
To find the last logon time of a user using SCCM, follow the below steps.
- Launch the Configuration Manager console.
- Navigate to Assets and Compliance\Overview\Users\All Users.
- Search for the user account and right-click the User object.
- On the user properties box, click General tab.
- The LastLogon attribute should reveal the last logon time of a user account.

Method 5: Find user sign-in activity in Microsoft 365 admin center
In the Microsoft 365 admin center, an administrator can view the times a user manually signed in with their username and password in the past 30 days. The user sign-in activity details include the date and time of the login, status and failure reason.
To view the user’s last logon date and time in Microsoft 365 admin center:
- Sign in to the Microsoft 365 admin center.
- Expand Users > Active Users and select a user.
- On the User properties window, under Last sign-in, select View last 30 days.
- The sign-in activity screen shows the user’s last logon date and time for the past 30 days.

Method 6: Find user’s last login details in Intune
If your organization manages Windows devices using Intune, you can find the user’s last login details in the Intune admin center. Sign in to the Intune admin center and go to Users. From the list of users, select a user and now click on Sign-in logs. Here, you can see the date and time of the user’s login, including the user’s location, IP address, and request ID.
To export the user’s sign information, you can click on the Download button. The file can be exported in JSON and CSV formats.

Still Need Help?
If you need further assistance on the above article or want to discuss other technical issues, check out some of these options.
When a user logs into a Computer, the logon time is stored in the “Last-Logon-Timestamp” attribute in Active Directory.
Keeping an eye on user logon activities will help you avoid security breaches by catching and preventing any unauthorized user access.
As a System Administrator, you are responsible to keep your organization’s IT infrastructure secure and regularly auditing users’ last login dates in Active Directory is one way to minimize the risk of unauthorized login attempts.
You can also use the Last-Logon-Time reports to find and disable any inactive user accounts.
In this tutorial, we will show you how to generate last logon reports using 3 different methods:
1. Free Utility by SolarWinds
2. PowerShell
3. Active Directory GUI tool
1. Free AD Bundle Utility
Through some digging, we found a Free tool from SolarWinds that shows you additional login data/time for a user – and its completely free!
This tool is part of the Free Admin Bundle for Active Directory which comes with 3 separate utilities that help you manage AD quickly.
The Tool we’re interested in is the Inactive User Account Removal Tool which is installed with the bundle.
Download From the link below and lets get it installed:
https://www.solarwinds.com/free-tools/active-directory-admin-tools-bundle
After you’ve Downloaded and Installed the bundle, find the Inactive User Account Removal Tool and click on it to launch the utility.
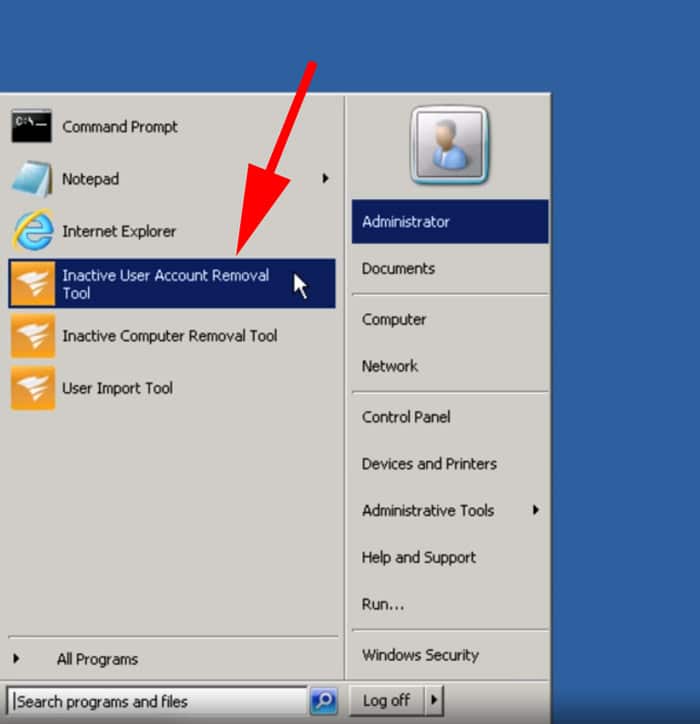
Once the utility has started, enter your Domain Controller IP/Name and AD Domain Admin Credentials at the next screen and click the NEXT button after you’ve tested your credentials to work:
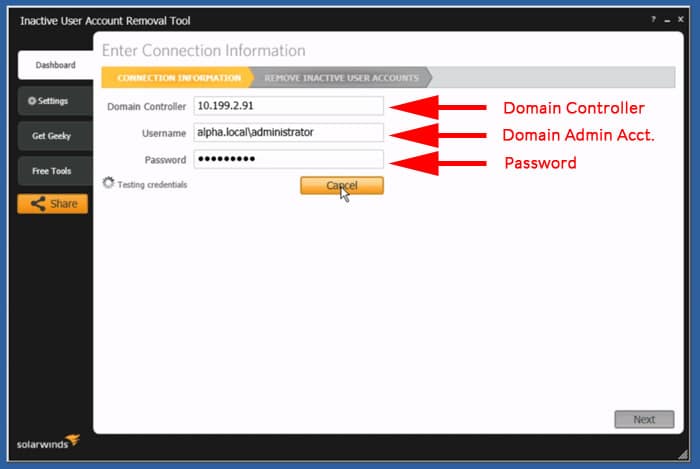
You will then see a screen that is populated with All users and there will be a column for Last Login, as seen in the screenshot below!
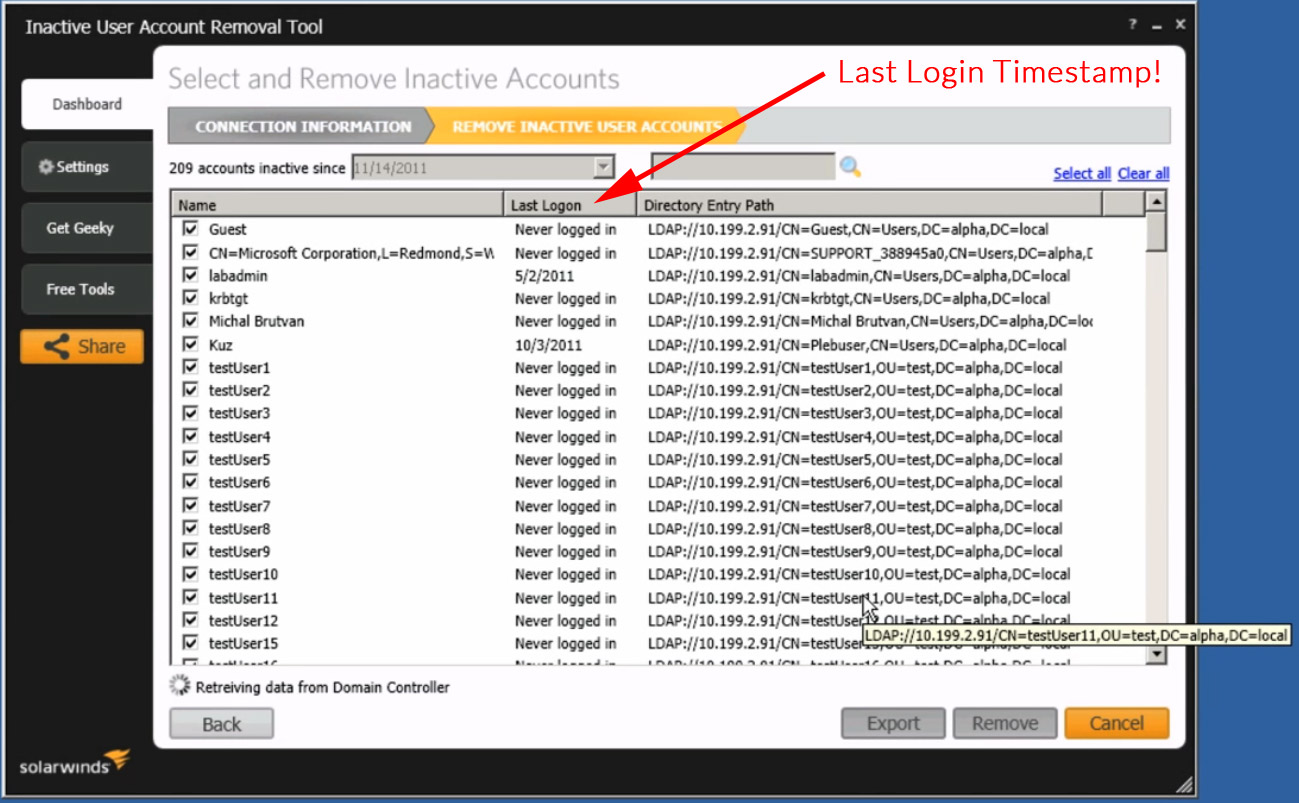
This tool was meant to find inactive accounts, but we’ve noticed that you can use it to quickly find user information as well. If your having issues finding account information, try changing the Inactive Date at the Top to see more recent accounts.
You can download the Free Tool here:
https://www.solarwinds.com/free-tools/active-directory-admin-tools-bundle
Find Specific AD Users Last Logon Time Using PowerShell
You can easily find the last logon time of any specific user using PowerShell.
The basic syntax of finding users last logon time is shown below:
Get-ADUser -Identity username -Properties "LastLogonDate"
For example, you can find the last logon time of user hitesh and simac by running the following command in the PowerShell:
Get-ADUser -Identity "hitesh" -Properties "LastLogonDate"
Get-ADUser -Identity "simac" -Properties "LastLogonDate"
You should see the users last logon time information in the following screen:
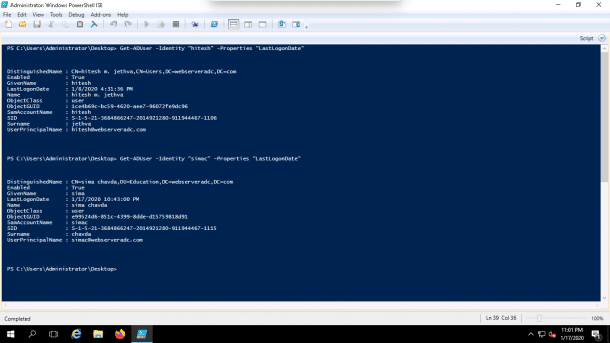
Find All AD Users Last Logon Time Using PowerShell
If you are managing a large organization, it can be a very time-consuming process to find each users’ last logon time one by one.
In this case, you can create a PowerShell script to generate all user’s last logon report automatically.
You can create the PowerShell script by following the below steps:
1. Open your notepad and add the following codes:
Get-ADUser -Filter {enabled -eq $true} -Properties LastLogonTimeStamp |
Select-Object Name,@{Name="Stamp"; Expression={[DateTime]::FromFileTime($_.lastLogonTimestamp).ToString('yyyy-MM-dd_hh:mm:ss')}}
2. Click on the Save as option to save the file
3. Type a name for the script as lastlogon.ps1
4. Click on the Save button to save the file.
5. Right click on the lastlogon.ps1 PowerShell script and click on the Edit button as shown below:

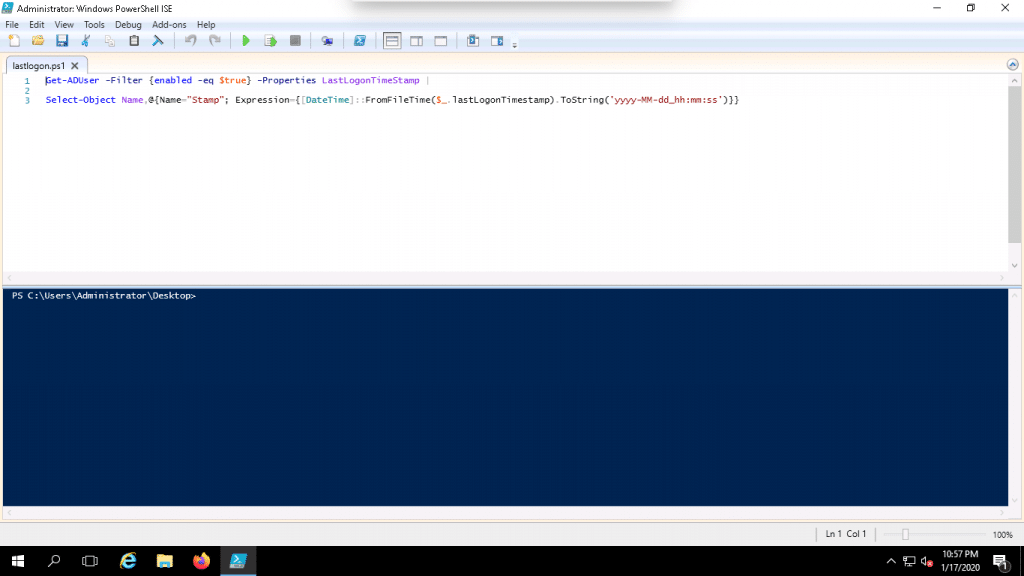
6. Now, click on the green button to run the script. You should see the following screen if it ran successfully:
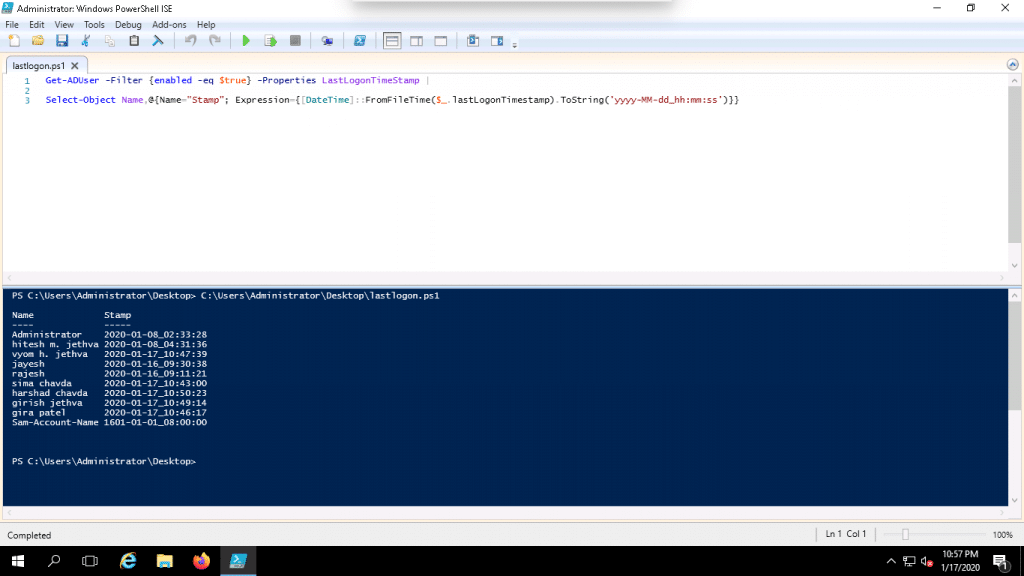
Save the Generated Report
If you want to save the generated report in the CSV file, run the following script in the PowerShell:
Get-ADUser -Filter {enabled -eq $true} -Properties LastLogonTimeStamp |
Select-Object Name,@{Name="Stamp"; Expression={[DateTime]::FromFileTime($_.lastLogonTimestamp).ToString('yyyy-MM-dd_hh:mm:ss')}} | Export-CSV = -Path "C:\alluser_reports.csv"
Save User Metadata with Script
If you want to generate all user’s last logon report with other useful information like, OU and Domain controller name.
Then, you can create the PowerShell script by following the below steps:
1. Open your notepad and add the following codes:
Import-Module ActiveDirectory
function Get-LastLogonEvents
{
$dcs = Get-ADDomainController -Filter {Name -like "*"}
$users = Get-ADUser -Filter *
$time = 0
foreach($user in $users)
{
foreach($dc in $dcs)
{
$hostname = $dc.HostName
$currentUser = Get-ADUser $user.SamAccountName | Get-ADObject -Server $hostname -Properties lastLogon
if($currentUser.LastLogon -gt $time)
{
$time = $currentUser.LastLogon
}
$dt = [DateTime]::FromFileTime($time)
Write-Host $currentUser "last logged on at:" $dt
$time = 0
}
}
}
Get-LastLogonEvents
2. Click on the Save as option to save the file.
3. Type a name for the script as lastlogon_details.ps1
4. Click on the Save button to save the file.
5. Now, right click on the PowerShell script and click on the Edit button as shown below:

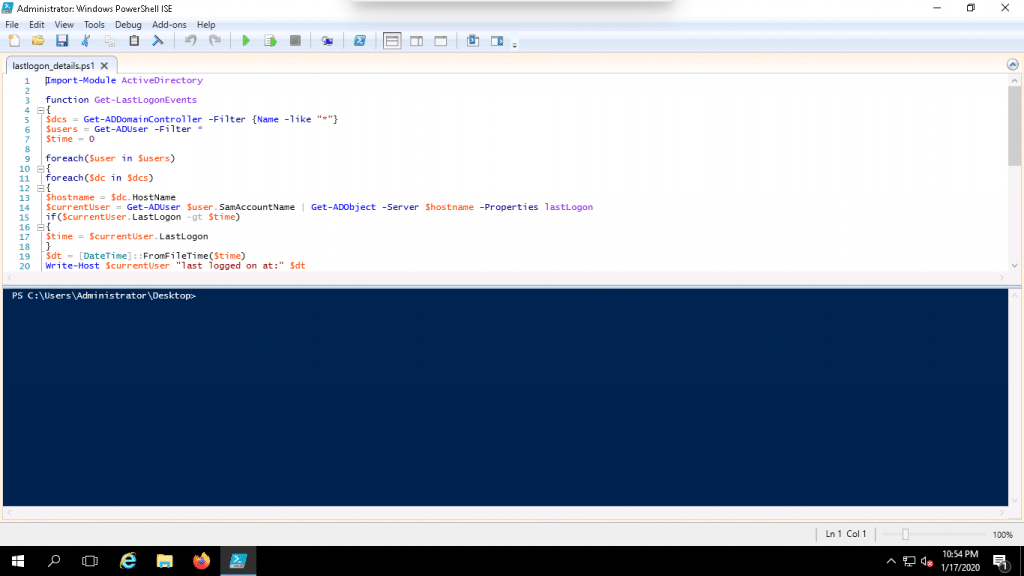
6. Now, click on the green button to run the script. You should see the following screen if it ran successfully:
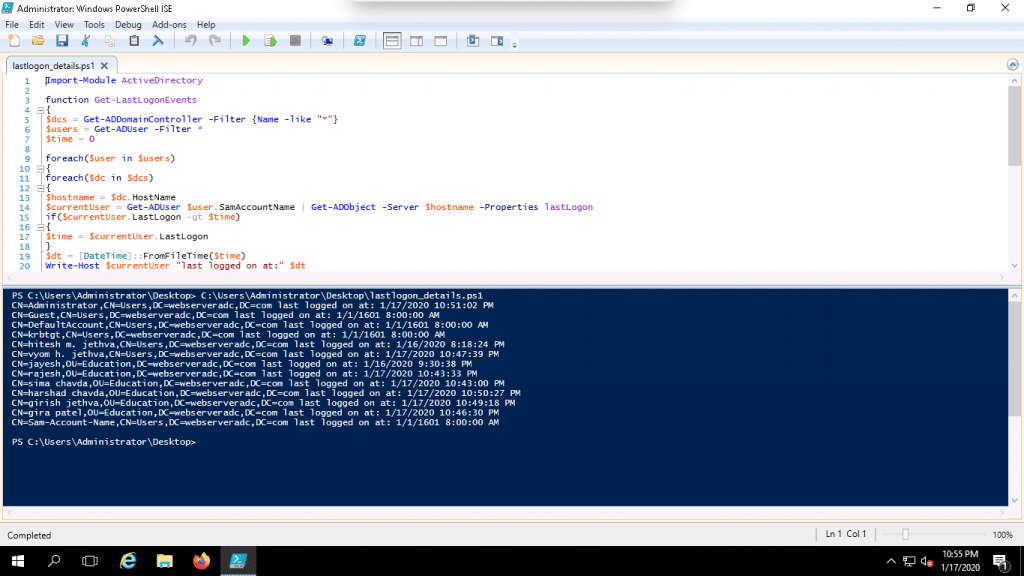
If you want to save the generated report in the CSV file, run the following script in the PowerShell:
Import-Module ActiveDirectory
function Get-LastLogonEvents
{
$dcs = Get-ADDomainController -Filter {Name -like "*"}
$users = Get-ADUser -Filter *
$time = 0
foreach($user in $users)
{
foreach($dc in $dcs)
{
$hostname = $dc.HostName
$currentUser = Get-ADUser $user.SamAccountName | Get-ADObject -Server $hostname -Properties lastLogon
if($currentUser.LastLogon -gt $time)
{
$time = $currentUser.LastLogon
}
$dt = [DateTime]::FromFileTime($time)
Write-Host $currentUser "last logged on at:" $dt
$time = 0
}
}
}
Get-LastLogonEvents | Export-CSV = -Path "C:\alluser_reports_brief.csv"
3. Find AD Users Last Logon Time Using the Attribute Editor
You can also find a Single Users Last logon time using the Active Directory Attribute Editor.
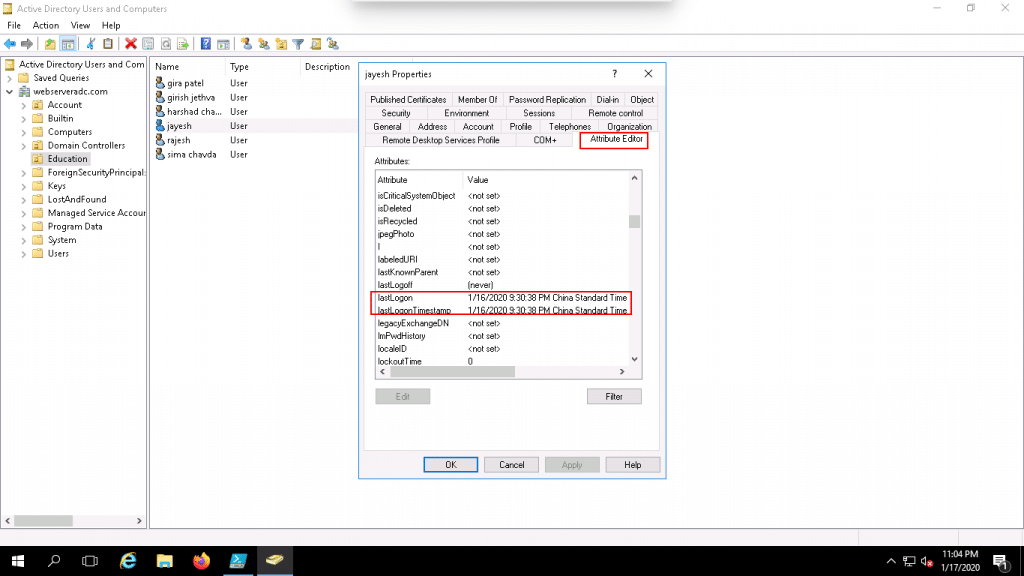
You can follow the below steps below to find the last logon time of user named jayesh with the Active Directory Attribute Editor.
1. Open the Active Directory Users and Computer.
2. Click on the View => Advanced Features as shown below:
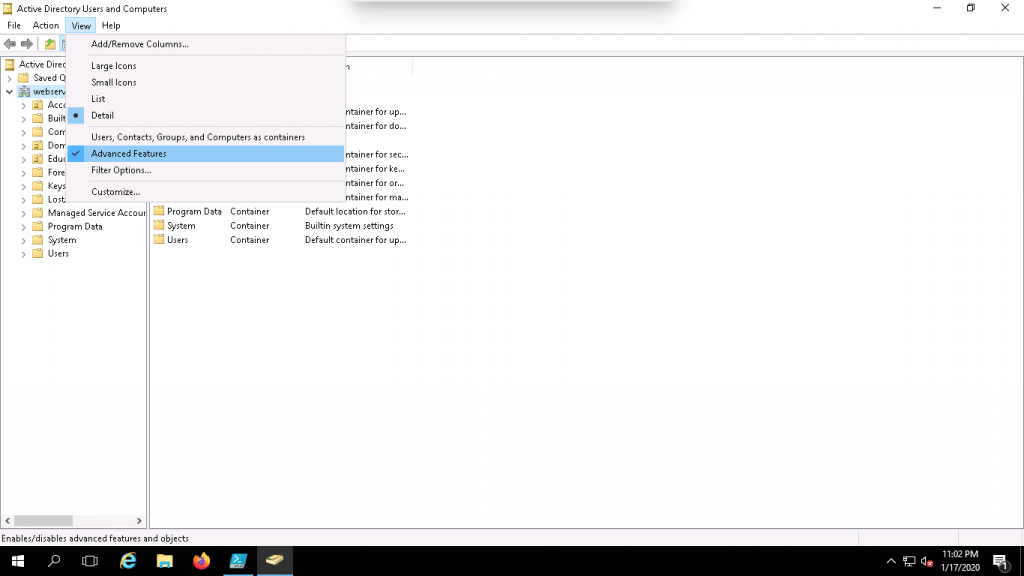
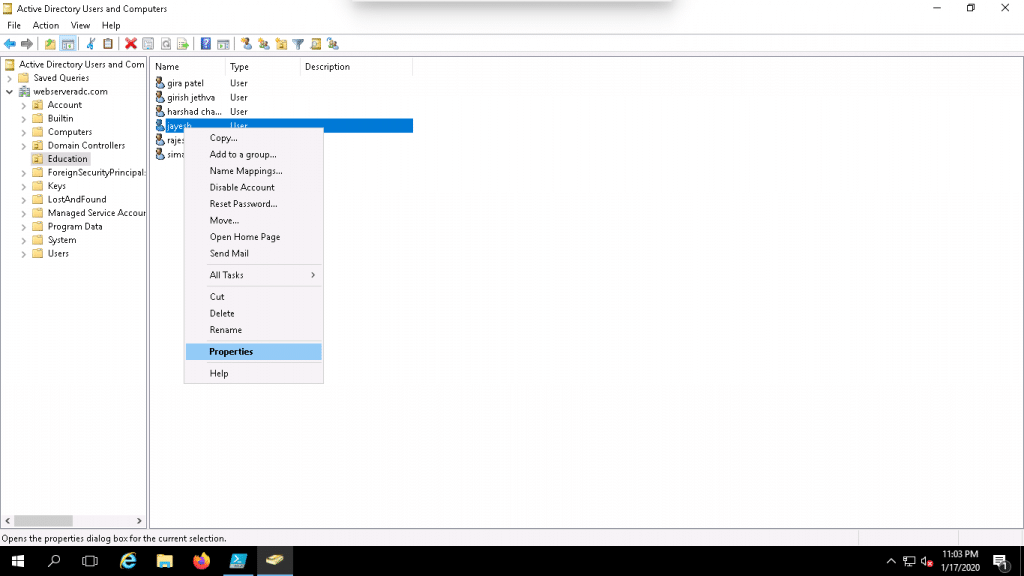
3. Click on the Education OU, Right-click on the jayesh user and click on the Properties as shown below:
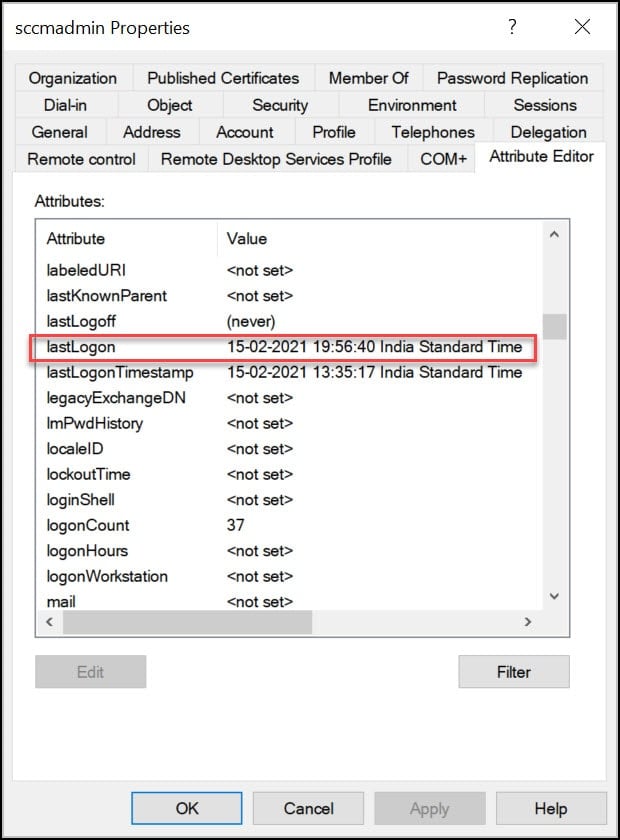
4. Click on the Attribute Editor tab and scroll down to see the last logon time as shown below:
Conclusion
Now that you have all of the information needed to easily generate the last logon report of users, hopefully this helps streamline your day to day tasks of keeping your networks secure.
The motive of this activity is to figure out whether there are accounts that are still enabled, but has not been logged into the AD domain for months (or even years in some cases). There might be test accounts, staff on long leave etc in the mix and hence this exercise always output data that need to be acted on.
Staff on long leave surely needs to be disabled, the same goes for accounts that belonged to the staff who does not work in the organization anymore.
Even though it is quite easy to construct a one-liner that can give us this information using PowerShell, we need to be careful about which attribute we are basing our query on and what the differences are.
There are number of ways in which we can find the last date and time someone logged into the domain – you might be querying for a single user, a subset of users or against the entire domain. Let’s tackle each case one by one.
How to find last logon time for a single user
You can get this information using the Active Directory Users and Computers snap-in and PowerShell.
Follow the steps below to find the info using the graphical tool.
Launch Active Directory Users and Computers.
Click on View tab and make sure that Advanced features is turned on.

Navigate to the OU where the user account is and double click on the account to open up the properties page. The Attribute Editor tab is not visible if you find the user using the search option and double click on the account.
Look for the attribute LastLogon and LastLogonTimeStamp. These attributes will give you the necessary information. Why are we looking at two attributes for the same info you might ask.

Difference between LastLogon, LastLogonDate and LastLogonTimeStamp
A bit of theory – LastLogon information is local to the domain controller you are querying against. So if a user was last authenticated by DC01, this server will have the correct LastLogon info, whereas DC02 will have incorrect info or no info at all. LastLogon info is NOT replicated to other domain controllers. Hence, LastLogon is good if you are a small organization and only have one or two domain controllers.
If you are a large organization, you are better off using the LastLogonDate as this info gets replicated to all domain controllers. But (there is always a but), the info is replicated only if the ‘new’ value is older than 14 days compared to the previous value (not sure as to why it is this way!).
There is a third attribute LastLogonTimeStamp, which is a replica of the LastLogonDate, however, the output is not in a human readable date format. Also, this timestamp attribute is not just used for the logins, but rather the last time the account accessed something on the network – like connecting to the VPN etc .Check the three attributes info in the screenshot below.

To summarize, use LastLogon if you have have a couple of domain controllers and LastLogonDate if you are a bigger shop.
Find Last Logon Info For Single User Using PowerShell
Now that we know how to get the info using ADUC, run the command below to get the info using PowerShell.
Import-Module ActiveDirectory
Get-ADUser -Identity <username> -Properties LastLogonDateIf you are adamant that you want to use the non-human readable LastLogon attribute, you can use the command below to convert the info into something more meaningful.
Import-Module ActiveDirectory
Get-ADUser -Identity <username> -Properties * | Select Name, @{N=’Last Logon’; E={[DateTime]::FromFileTime($_.LastLogon)}}
Find Last Logon Info For All Users Using PowerShell
Run the command below to get the last login information for all users in the AD domain.
Import-Module ActiveDirectory
Get-ADUser -Filter * -Properties * | Select Name, LastLogonDate, samaccountnameIf the user accounts have never logged into the domain, the LastLogonDate will be blank.
If you use the command below, you will have 1/1/1601 against users who have never logged into the domain.
Import-Module ActiveDirectory
Get-ADUser -Filter * -Properties * | Select Name, @{N=’Last Logon’; E={[DateTime]::FromFileTime($_.LastLogon)}}, samaccountname
You can use the export-csv parameter to get the information to play with in Excel.
Import-Module ActiveDirectory
Get-ADUser -Filter * -Properties * | Select Name, LastLogonDate, samaccountname | export-csv .\AllUsersLoginInfo.csv -NoTypeInformationFind Last Logon Info For All Enabled Users Using PowerShell
If you want to filter the output just to the user accounts thatare enabled, run the command below.
Import-Module ActiveDirectory
Get-ADUser -Filter 'Enabled -eq $true' -Properties * | Select Name, LastLogonDate, samaccountnameYou can use the export-csv parameter to get the information out to a file.
Import-Module ActiveDirectory
Get-ADUser -Filter 'Enabled -eq $true' -Properties * | Select Name, LastLogonDate, samaccountname | export-csv .\EnabledUsersLoginInfo.csv -NoTypeInformationFind Users Who Have Not Logged In The Last 90 Days
A commonly used task is to find the AD user accounts which has not been logged into the domain in the last x number of months, say 3 months.
Run the command below to find users who haven’t logged in the last 90 days. You can vary the number of days in the command based on the output required.
#Change 90 to whatever number of days you need.
$Date = (Get-Date).AddDays(-90)
Import-Module ActiveDirectory
Get-ADUser -Filter 'LastLogonDate -lt $date' -Properties * | Select Name, LastLogonDate, samaccountnameExport the info using the block of commands below.
#Change 90 to whatever number of days you need.
$Date = (Get-Date).AddDays(-90)
Import-Module ActiveDirectory
Get-ADUser -Filter 'LastLogonDate -lt $date' -Properties * | Select Name, LastLogonDate, samaccountname | export-csv .\UsersNotLogged90Days.csv -NoTypeInformationFind and Disable User Accounts Not Logged In The Last 3 Months
You can find the info about which accounts have not logged into the domain in the last 3 months and disable them in one go. Use the command below for this task.
#Change 90 to whatever number of days you need.
$Date = (Get-Date).AddDays(-90)
Import-Module ActiveDirectory
Get-ADUser -Properties LastLogonDate -Filter {LastLogonDate -lt $date} | Disable-ADAccountPlease let me know if you have any questions in the comments section.
Last time a user or computer logged into a domain stored in Active Directory object attributes. To find out the last logon time for AD user or computer accounts, there are a number of tools that an administrator can use.
How to Check the User/Computer Last Logon Date in Active Directory
When a user or computer logs on to a domain, the logon time is written to the lastLogon and lastLogonTimestamp attributes of the corresponding AD object. What are the differences between these attributes?
- The lastLogon attribute value is updated when the account interactively logs on to AD on the domain controller used for authentication (%logonserver%). It is not replicated between domain controllers, meaning each domain controller may have a different value for this attribute.
- The lastLogonTimestamp attribute is an analogue of the lastLogon attribute, but unlike lastLogon, it is replicated to other domain controllers in AD. To minimize replication traffic in AD, the value of this attribute is replicated for up to 14 days.
This means that to get real-time information about when an account last logged into AD, you must get the lastLogon attribute value. However, this requires you to query all the domain controllers in the forest.
If a tolerance of ±19 days is acceptable to you, then you can simply get the lastLogonTimestamp from the nearest domain controller. Therefore, in most cases, the lastLogonTimestamp attribute is used to determine the user’s last logon time, providing a somewhat outdated but consistent latest logon activity across all domain controllers.
You can use the Active Directory Users and Computers (ADUC) snap-in (requires RSAT installation) to check the last time a user or computer logged on.
- Press WIN+R and run dsa.msc to open the ADUC console
- Click View → Advanced Features. This step enables the Attribute Editor tab in ADUC.
- Locate the user or computer and open its properties.
- Go to the Attribute Editor tab and find the lastLogOn and lastLogOnTimeStamp attributes.
Get the Last Logon Date and Time of an AD User or Computer using PowerShell
It is more convenient to use PowerShell to get the user’s last domain logon time. For that, use the Get-ADUser cmdlet from the PowerShell Active Directory module.
For example, to find out the last logon time of a specific domain user account:
Get-ADUser -Identity ebrown -Properties LastLogon, LastLogonTimestamp

In order to convert the lastlogon value from timestamp format to a human readable, use the following command:
Get-ADUser -Identity ebrown -Properties LastLogon, LastLogonTimestamp |
Select-Object SamAccountName, Name,
@{n = 'LastLogon'; e = { [DateTime]::FromFileTime($_.LastLogon) } },
@{n = 'LastLogonTimeStamp'; e = { [DateTime]::FromFileTime($_.LastLogonTimeStamp) } }

Note. The lastlogontimestamp value will be empty if the user or computer has never logged on to the AD domain. The LastLogon value for such an account is always 12/31/1600 4:00:00 PM.

To view the last logon time for a domain computer, change the cmdlet to Get-ADComputer.
Get-ADComputer -Identity DB1 -Properties LastLogonTimestamp |
Select-Object SamAccountName, Name, @{n = 'LastLogonTimeStamp'; e = { [DateTime]::FromFileTime($_.LastLogonTimeStamp) } }

To find inactive users and computers that have not logged on to a domain for more than 90 days, use the PowerShell pipe:
$oldest = (Get-Date).AddDays(-90)
Get-ADUser -Filter { LastLogonTimeStamp -lt $oldest } -Properties LastLogonTimestamp |
Select-Object SamAccountName, Name,
@{n = ‘LastLogonTimeStamp’; e = { [DateTime]::FromFileTime($_.LastLogonTimeStamp) } }

To get the same information for domain computers, replace the Get-ADUser cmdlet with the Get-ADComputer cmdlet.
Get-ADComputer -Filter { LastLogonTimeStamp -lt $oldest } -Properties LastLogonTimestamp |
Select-Object SamAccountName, Name,
@{n = 'LastLogonTimeStamp'; e = { [DateTime]::FromFileTime($_.LastLogonTimeStamp) } }

To query all the DCs in AD to get the current LastLogon value for a specific account, use the PowerShell script. Copy the script below and save it as Get-ADUserLastLogOnTime.ps1 on your computer. You can also download this script from this Gist.
# Get-ADUserLastLogOnTime.ps1
[CmdletBinding()]
param (
[Parameter()]
[String]
$LogonName
)
Import-Module ActiveDirectory
$DCs = (Get-ADDomainController -Filter *).Name
$result = New-Object System.Collections.Generic.List[object]
foreach ($dc in $DCs) {
# “Querying DC: [$($dc)]” | Out-Default
try {
if ($aduser = Get-ADUser $LogonName -Server $dc -Properties lastlogon -ErrorAction Stop) {
$result.Add(
($aduser |
Select-Object SamAccountName, Name,
@{n = ‘DC’; e = { $dc } },
@{n = ‘LastLogon’; e = { [DateTime]::FromFileTime($_.LastLogon) } })
)
}
}
catch {
$_.Exception.Message | Out-Default
}
}
return $result
This PowerShell script retrieves the last logon (lastLogon) of an Active Directory (AD) user account from all domain controllers. It accepts a parameter, $LogonName, which should be the username (SamAccountName) of the user for whom you want to retrieve the last logon time.
.\Get-ADUserLastLogOnTime.ps1 -LogonName USERNAME

Hint. You can also use the built-in NET USER command to quickly find a domain user’s last logon time:
net user ebrown /domain| findstr "Last"
Cyril Kardashevsky
I enjoy technology and developing websites. Since 2012 I’m running a few of my own websites, and share useful content on gadgets, PC administration and website promotion.




