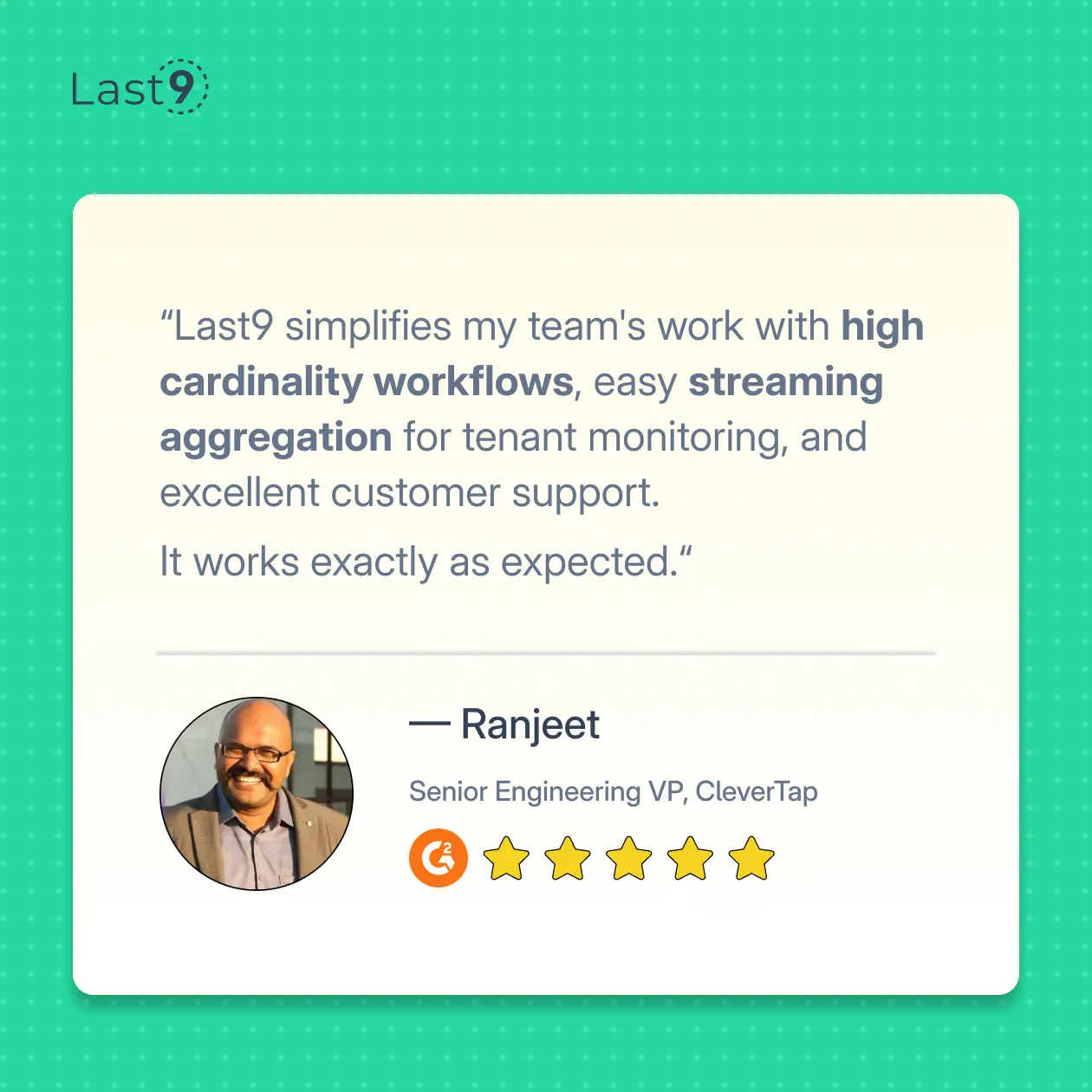
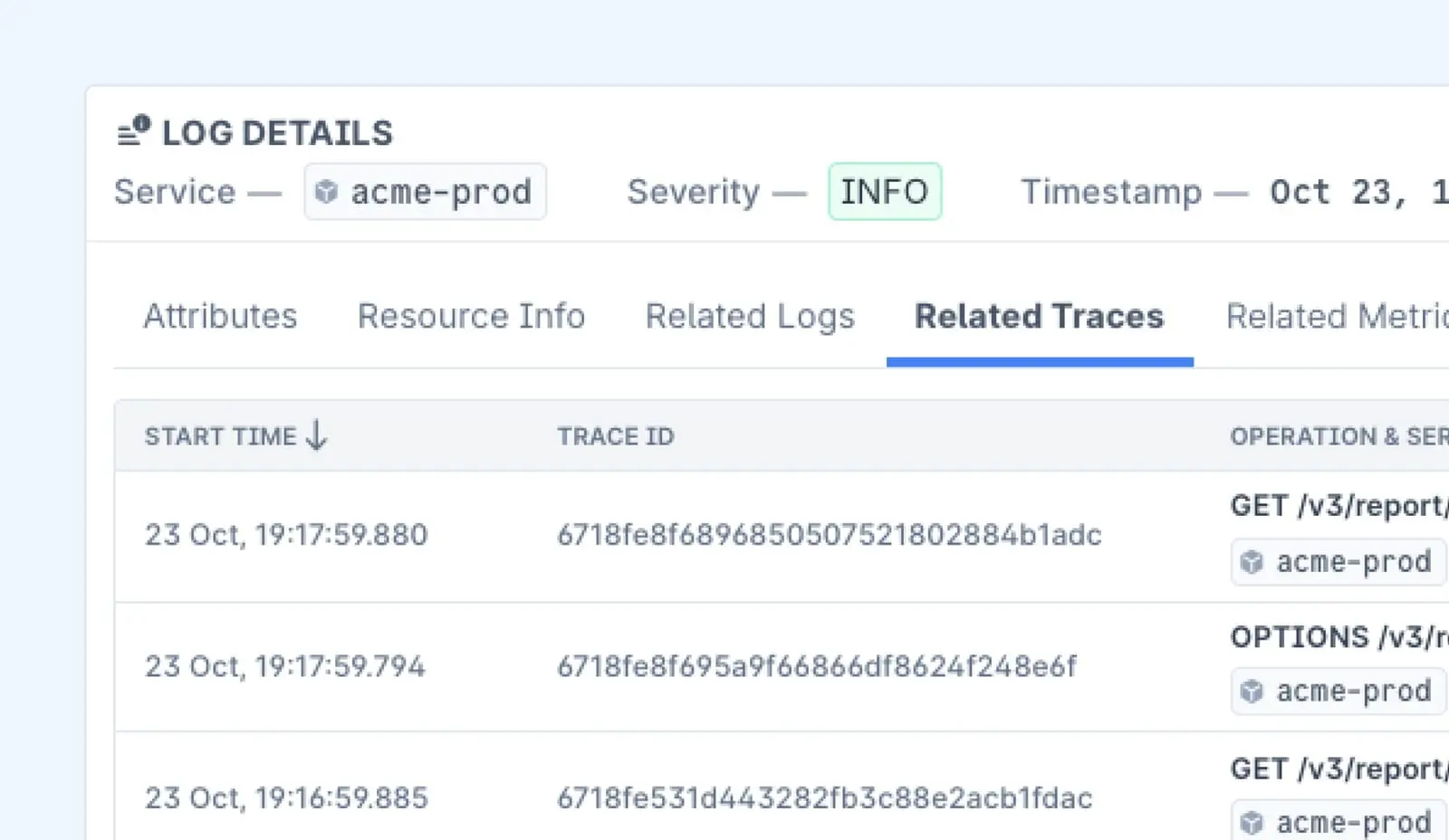
This is my write-up on THM’s Windows Event Logs Room.
Task 1: What are event logs?
Event logs essentially contain the records of events or activities that have transpired in a machine or host, that would help system administrators, IT technicians, etc, audit and trouble shoot issues in the system.
But for blue teams, windows event logs serve a different purpose. These logs are analyzed for malicious activities or indicators of compromise. Windows Event Logs can also be forwarded to SIEMs where analyst can aggregate, analyze, and correlate log data from various sources to provide security insights of a network.
For a Linux system, the logging system is knows as Syslog.
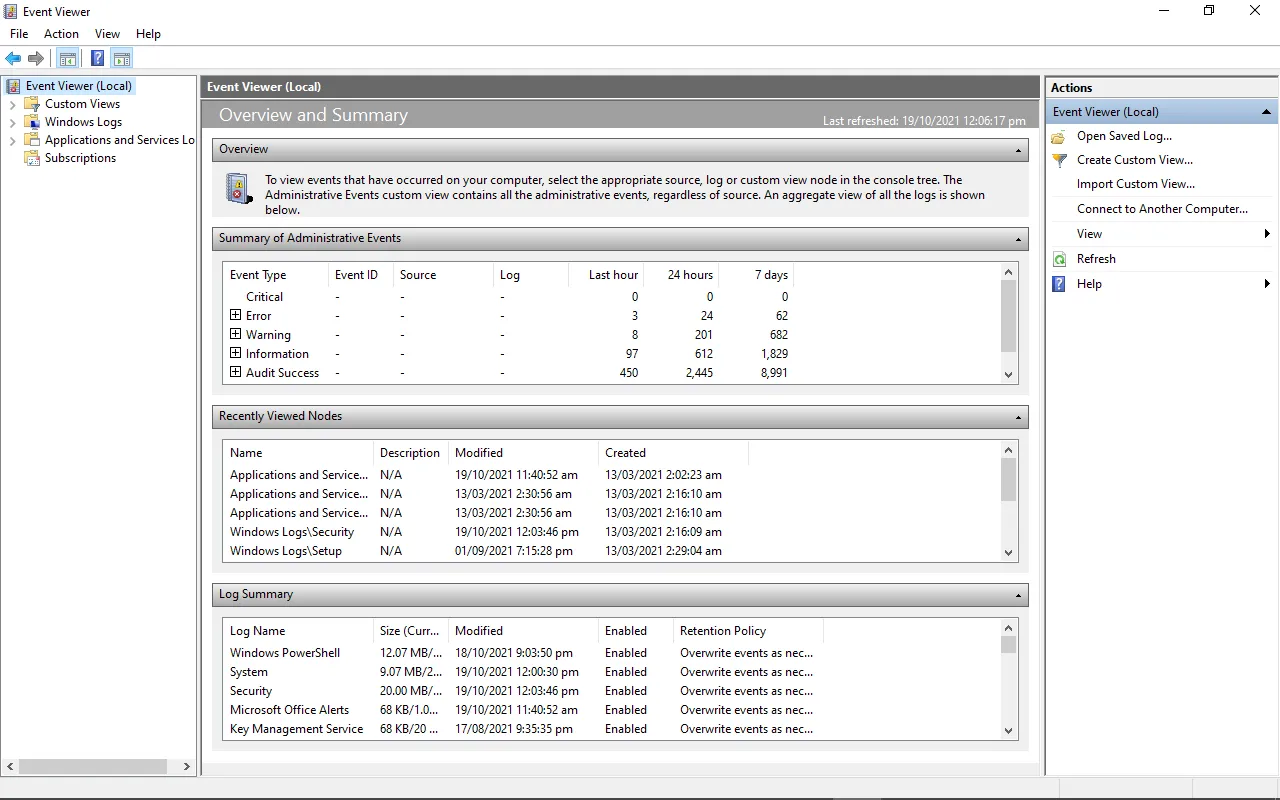
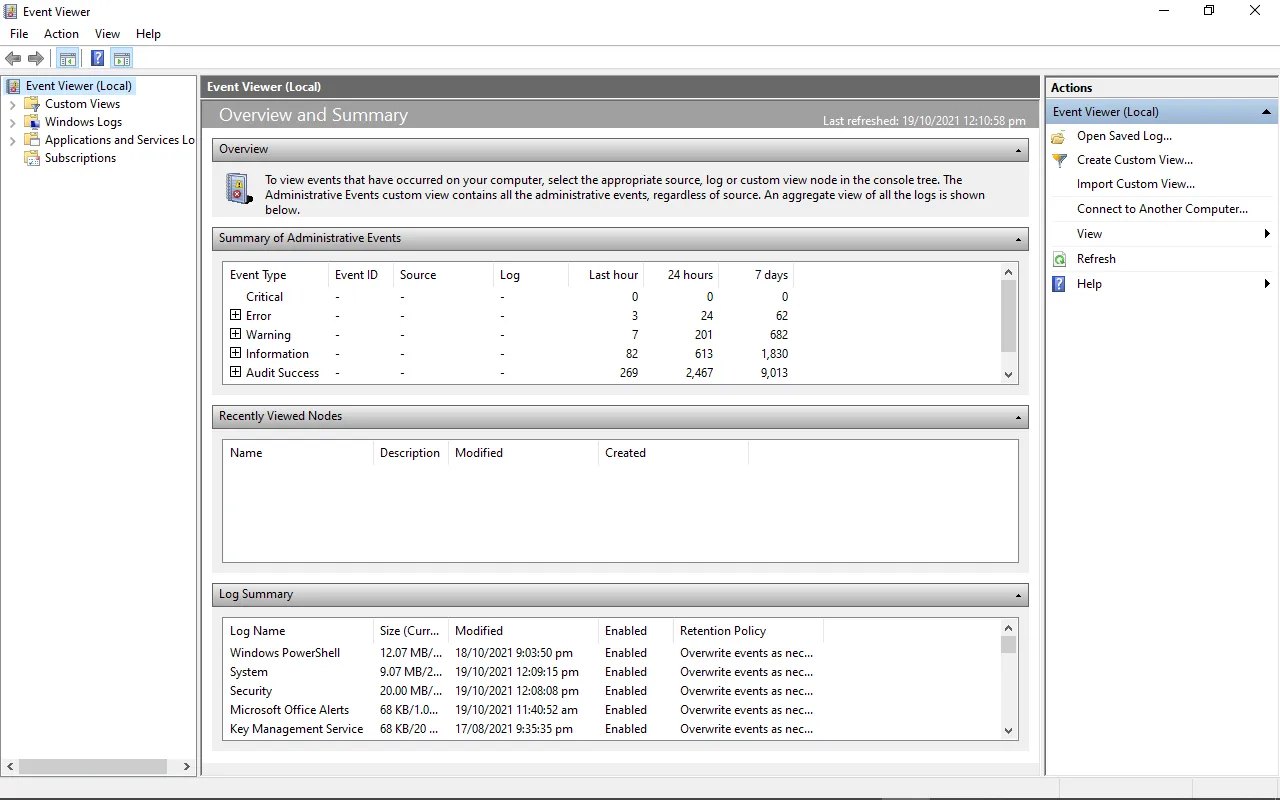
Task 2: Event Viewer
The Windows Event Logs are stored with an .evt or .evtx extension and are located in C:\\Windows\\System32\\winevt\\Logs.
Before moving on to Event Viewer, we first need to understand the different elements of a Windows Event Logs system. This would help us understand where to look at if we are trying to solve an issue or analyzing a specific kind of event.
- System Logs: Records events associated with the Operating System segments. They may include information about hardware changes, device drivers, system changes, and other activities related to the device.
- Security Logs: Records events connected to logon and logoff activities on a device. The system’s audit policy specifies the events.
- Application Logs: Records events related to applications installed on a system. The main pieces of information include application errors, events, and warnings.
- Directory Service Events: Active Directory changes and activities are recorded in these logs, mainly on domain controllers.
- File Replication Service Events: Records events associated with Windows Servers during the sharing of Group Policies and logon scripts to domain controllers, from where they may be accessed by the users through the client servers.
- DNS Event Logs: DNS servers use these logs to record domain events and to map out
- Custom Logs: Events are logged by applications that require custom data storage. This allows applications to control the log size or attach other parameters, such as ACLs, for security purposes.
The following table describes the five event types used in event logging.
| Event type | Description |
|---|---|
| Error | An event that indicates a significant problem such as loss of data or loss of functionality. For example, if a service fails to load during startup, an Error event is logged. |
| Warning | An event that is not necessarily significant, but may indicate a possible future problem. For example, when disk space is low, a Warning event is logged. If an application can recover from an event without loss of functionality or data, it can generally classify the event as a Warning event. |
| Information | An event that describes the successful operation of an application, driver, or service. For example, when a network driver loads successfully, it may be appropriate to log an Information event. Note that it is generally inappropriate for a desktop application to log an event each time it starts. |
| Success Audit | An event that records an audited security access attempt that is successful. For example, a user’s successful attempt to log on to the system is logged as a Success Audit event. |
| Failure Audit | An event that records an audited security access attempt that fails. For example, if a user tries to access a network drive and fails, the attempt is logged as a Failure Audit event. |
Event Viewer
The Windows Event Logs can be accessed with three methods; Event Viewer, Wevtutil.exe (command-line), and Get-WinEvent (PowerShell). The latter two methods will be discussed in the succeeding tasks.
Event Viewer allows interaction with and analyzing the logs in a GUI application.
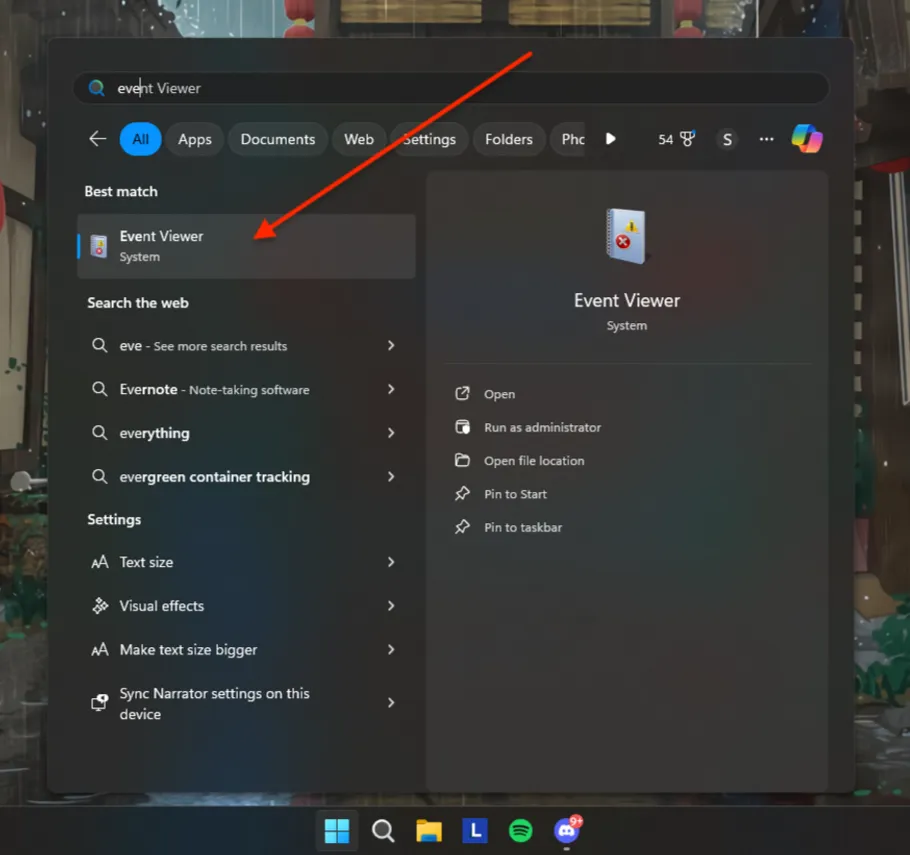
Event Viewer can be started by right-clicking the Windows icon and selecting Event Viewer.
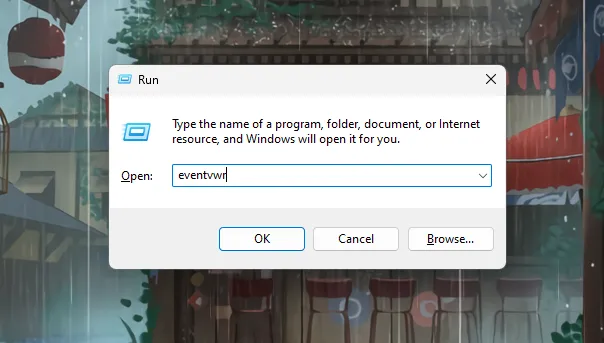
Or by typing “eventvwr.msc” in the command line.
Answer the questions below
For the questions below, use Event Viewer to analyze Microsoft-Windows-PowerShell/Operational log.
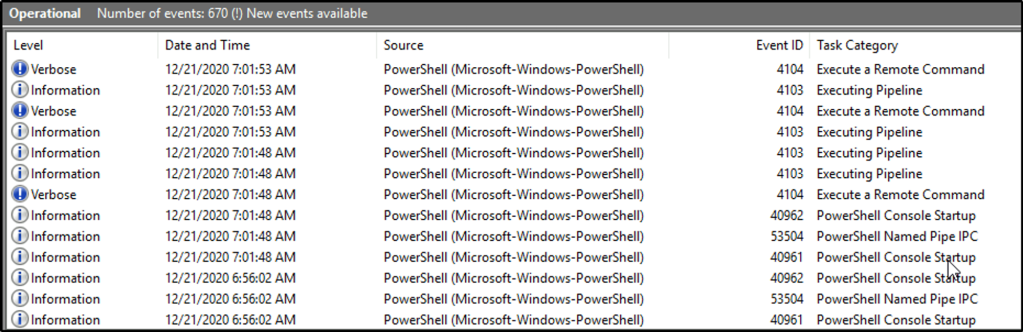
What is the Event ID for the first recorded event?
Answer: 40961
Open Event Viewer and go to Applications and Services Logs then to Microsoft > Powershell > Operational log.
The first event is found at the bottom of the window pane. We can also click on “Date and Time” column to sort the events based on the date and time of the occurrence of events.
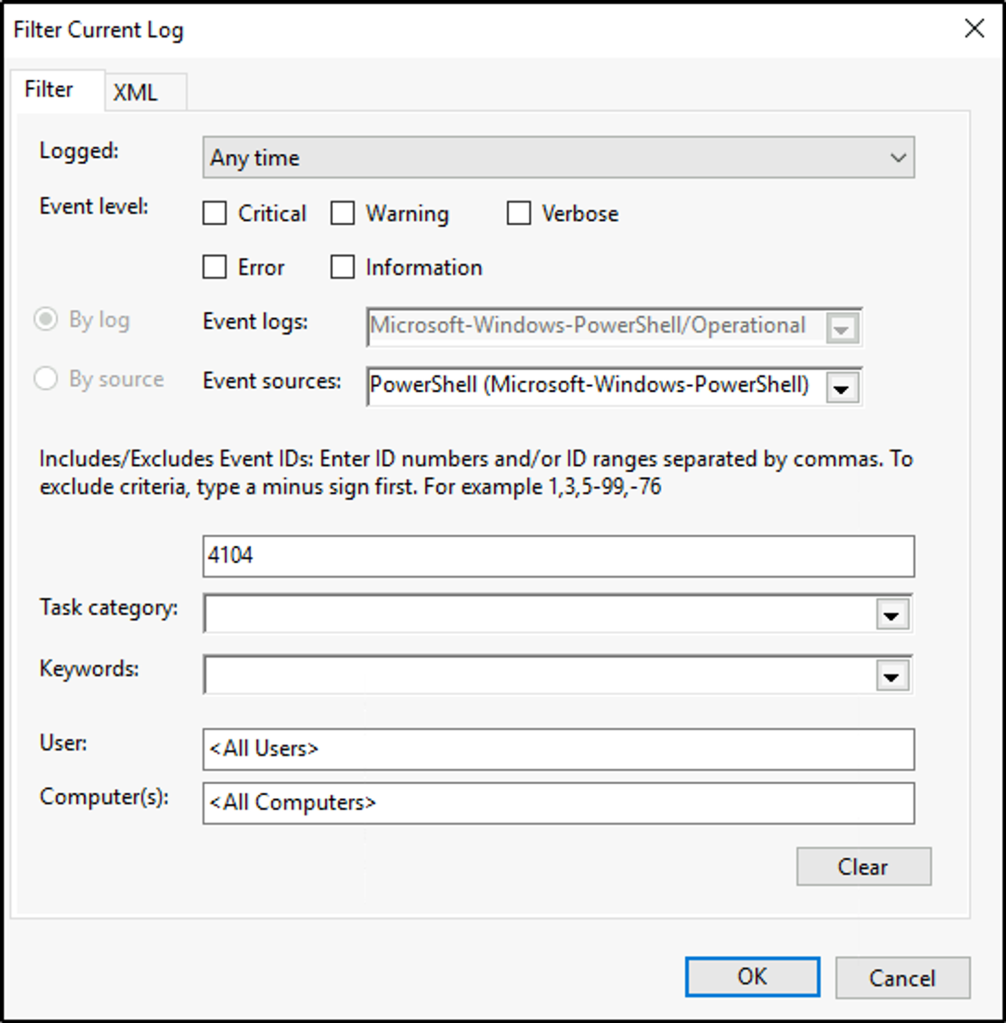
Filter on Event ID 4104. What was the 2nd command executed in the PowerShell session?
Answer: whoami
To create a filter, go to the right pane. Under “Operational” click on “Filter current Log”
We will filter the events with the Event ID 4104.
Once the results are in, sort the events based on date and time. Select the second event. Select the “Details” tab and the PowerShell command is displayed with the tag “ScriptBlockText”.
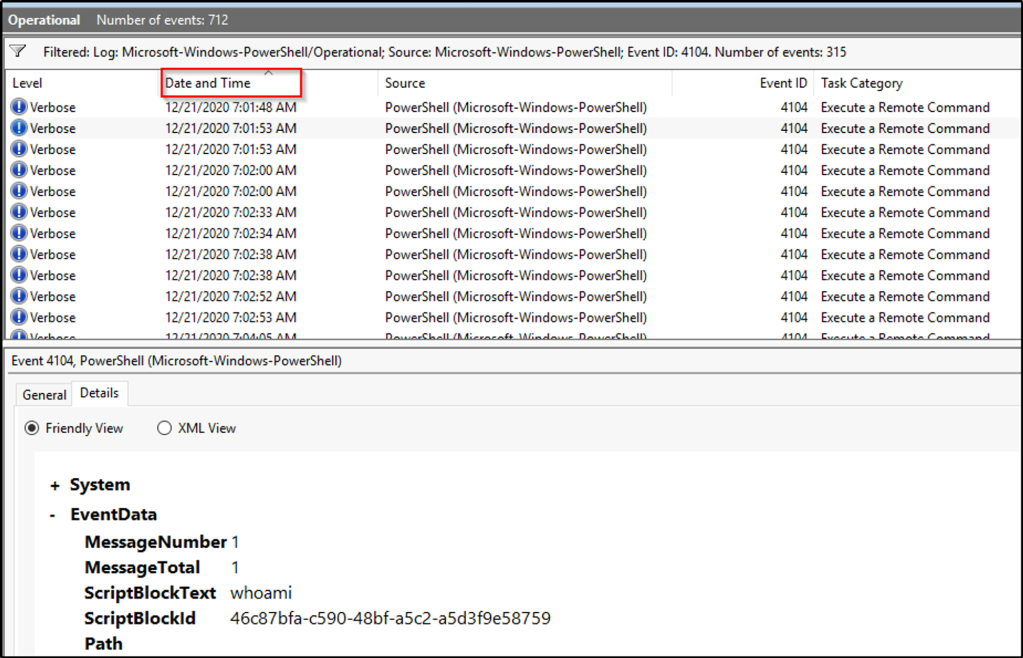
What is the Task Category for Event ID 4104?
Answer: Execute a Remote Command
We can find the answer by looking at the middle pane, similar to the image above. The “Task Category” column shows the category for Event ID 4104.
Analyze the Windows PowerShell log. What is the Task Category for Event ID 800?
Answer: Pipeline Execution Details
Clear the filter first. We would be returned to the same PowerShell event logs.
The middle pane, under the “Task Category” column would show the task category for Event ID 800.

Task 3: wevtutil.exe
Wevtutil.exe (Windows Event Utility) is a command line tool that would help us query event logs. By writing scripts with this tool, we would be more efficient in sifting through thousands of event logs.
To access its help files, we will run wevtutil.exe /?.
The tool would follow this syntax.
- wevtutil COMMAND [ARGUMENT [ARGUMENT] …] [/OPTION:VALUE [/OPTION:VALUE] …]
The commands are the following:
el | enum-logs List log names. gl | get-log Get log configuration information. sl | set-log Modify configuration of a log. ep | enum-publishers List event publishers. gp | get-publisher Get publisher configuration information. im | install-manifest Install event publishers and logs from manifest. um | uninstall-manifest Uninstall event publishers and logs from manifest. qe | query-events Query events from a log or log file. gli | get-log-info Get log status information. epl | export-log Export a log. al | archive-log Archive an exported log. cl | clear-log Clear a log.
Note: We can use the short or long versions of the command, example el or enum-logs
Common options are;
Common Options:
/{r | remote}:VALUE
If specified, run the command on a remote computer. VALUE is the remote computer name. Options /im and /um do not support remote operations.
/{u |username}:VALUE
Specify a different user to log on to the remote computer. VALUE is a user name in the form of domain\\user or user. Only applicable when option /r is specified.
/{p | password}:VALUE
Password for the specified user. If not specified, or if VALUE is "*", the user will be prompted to enter a password. Only applicable when the /u option is specified.
/{a | authentication}:[Default|Negotiate|Kerberos|NTLM]
Authentication type for connecting to remote computer. The default is Negotiate.
/uni | unicode}:[true|false]
Display output in Unicode. If true, then output is in Unicode.
To learn more about a specific command, type the following:
wevtutil COMMAND /?
If we want to know how to use a specific command, as provided in the help files, we will use wevtutil COMMAND /?. For example, if we want to get more information on the command qe (query-events), we would use wevtutil qe /?.
More info can be found on docs.microsoft.com.
Answer the questions below
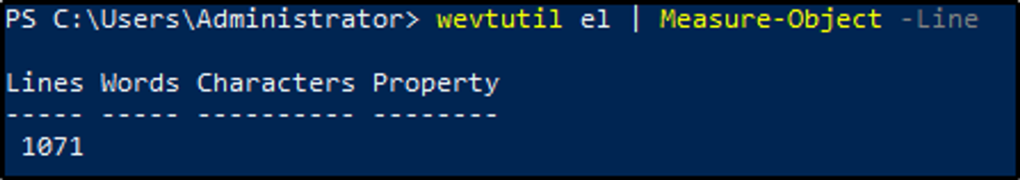
How many log names are in the machine?
Answer: 1071
The command el would list the log names and the results would then be piped to the next command to count the list of log names by line.
wevtutil el | Measure-Object -Line
What event files would be read when using the query-events command?
Answer: event log, log file, structured query
For us to find more info about the command, we would use wevtutil qe /?.
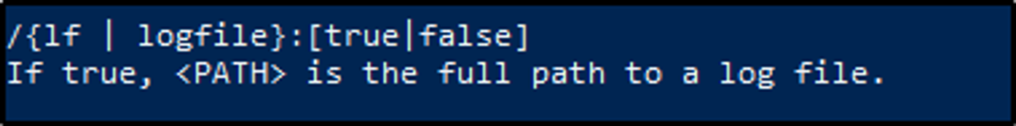
What option would you use to provide a path to a log file?
Answer: /lf:true
After running the command, we see the options we can use with qe. The option we would use to include a log file path is /lf:true.
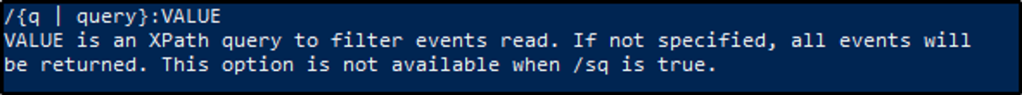
What is the VALUE for /q?
Answer: query XPATH
Scrolling through the options, we can see the value for /q? is XPATH query.
The questions below are based on this command: wevtutil qe Application /c:3 /rd:true /f:text
What is the log name?
Answer: Application
From the command given to us, wevtutil is querying events from Application logs.
What is the /rd option for?
Answer: event read redirection
When we run wevtutil qe /?, we would see the options for this command. /rd would refer to event read redirection.

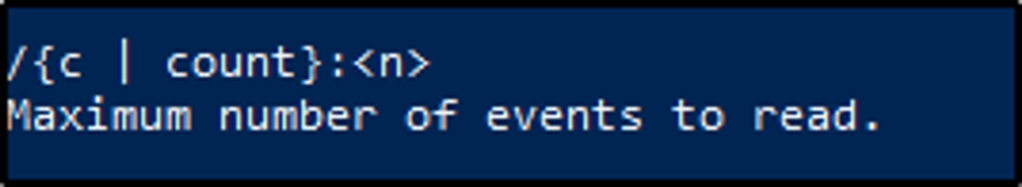
What is the /c option for?
Answer: Maximum number of events to read
/c option refers to the number of events that we wold want to query from the logs.
Task 4: Get-WinEvent
Get-WinEventis a Powershell cmdlet. Per Microsoft, the Get-WinEvent cmdlet “gets events from event logs and event tracing log files on local and remote computers.” The tool can provide information on event logs and event log providers. We can also combine events from different sources by using a single command and filtering these events with XPath queries, structured XML queries, and hash table queries.
Note: The Get-WinEvent cmdlet replaced the Get-EventLog cmdlet.
Refer to the Get-Help information online at docs.microsoft.com.
Examples of how to use Get-WinEvent
Example 1: Get all logs from a computer
The first list will be classic logs, then by new Windows Event logs. RecordCount can have zero or null logs.
Example 2: Get event log providers and log names
This will get us the event log providers and their associated logs. The Name is the provider, and LogLinks is the log that is written to.
Get-WinEvent -ListProvider *
Example 3: Log filtering
Log filtering allows us to select events from an event log. We can then filter event logs from a specific Provider using the Where-Object cmdlet:
Get-WinEvent -LogName Application | Where-Object { $_.ProviderName -Match 'WLMS' }
Where-Object is inefficient to use when working with large event logs. Therefore, the suggested Get-WinEvent cmdlet’s FilterHashtable parameter is recommended to filter event logs.
Get-WinEvent -FilterHashtable @{
LogName='Application'
ProviderName='WLMS'
}Get-WinEvent -FilterHashtable @{ LogName='Application'; ProviderName= 'WLMS'}
The syntax of a hash table is as follows:
@{ <name> = <value>; [<name> = <value> ] ...}
Guidelines for defining a hash table are:
- Begin the hash table with an @ sign.
- Enclose the hash table in braces {}
- Enter one or more key-value pairs for the content of the hash table.
- Use an equal sign (=) to separate each key from its value.
Note: Using semicolon is not needed if each key/value are separated with a new line, as in the first set of commands above for the -FilterHashtable for ProviderName='WLMS'.
Below is a table that displays the accepted key/value pairs for the Get-WinEvent FilterHashtable parameter.
| Key name | Value data type | Accepts wildcard characters? |
|---|---|---|
| LogName | <String[]> |
Yes |
| ProviderName | <String[]> |
Yes |
| Path | <String[]> |
No |
| Keywords | <Long[]> |
No |
| ID | <Int32[]> |
No |
| Level | <Int32[]> |
No |
| StartTime | <DateTime> |
No |
| EndTime | <DateTime> |
No |
| UserID | <SID> |
No |
| Data | <String[]> |
No |
<named-data> |
<String[]> |
No |
Check the official Microsoft documentation docs.micro-soft.com for more info on querying using Filterhashtable.
Here is a command by @mubix on using Get-WinEvent -FilterHashtable
Get-WinEvent -FilterHashtable @{LogName='Microsoft-Windows-PowerShell/Operational'; ID=4104} | Select-Object -Property Message | Select-String -Pattern 'SecureString'
Answer the questions below
Answer the following questions using the online help documentation for Get-WinEvent
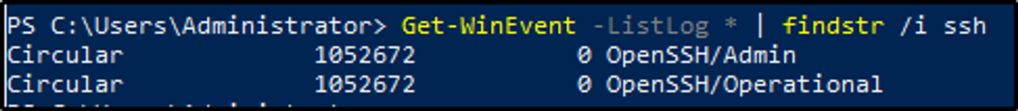
Execute the command from Example 1 (as is). What are the names of the logs related to OpenSSH?
Answer: OpenSSH/Admin,OpenSSH/Operational
We will use the command from example 1, then pipe the result to find the strings that matches ssh. We see two logs being displayed.
Get-WinEvent -ListLog * | findstr /i ssh
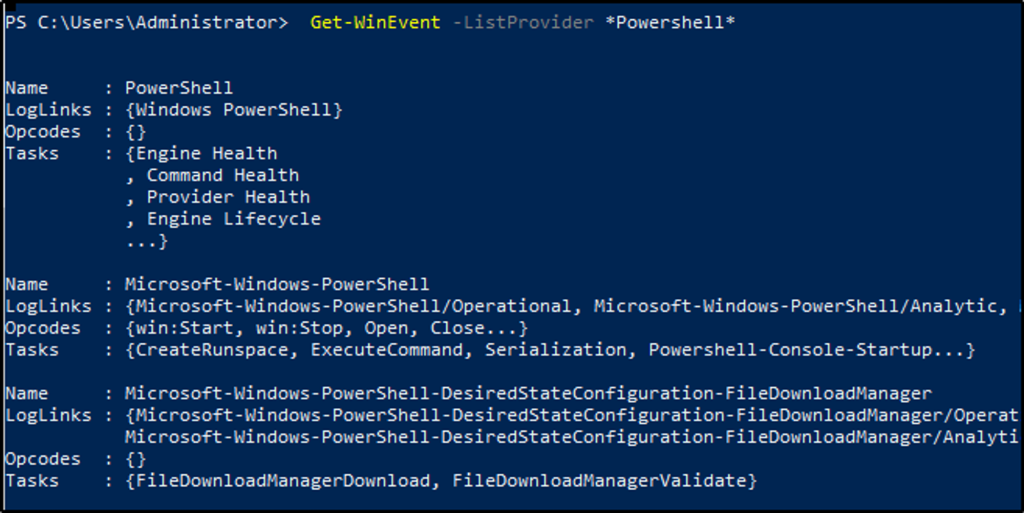
Execute the command from Example 8. Instead of the string Policy search for PowerShell. What is the name of the 3rd log provider?
Answer: Microsoft-Windows-PowerShell-DesiredStateConfiguration-FileDownloadManager
We will simply copy the command and change the string policy to Powershell. This will display all events relatd to the filter.
Get-WinEvent -ListProvider *Powershell*
Alternatively, we can modify the command to display only the third log provider.
Get-WinEvent -ListProvider *Powershell* | Select-Object -Property Name -Skip 2 -First 1
Execute the command from Example 9. Use Microsoft-Windows-PowerShell as the log provider. How many event ids are displayed for this event provider?
Answer: 192
We will be using the provided command and changing the log provider to Microsoft-Windows-PowerShell. We will also be modifying it by adding Measure-Object -Line to count the results by line.
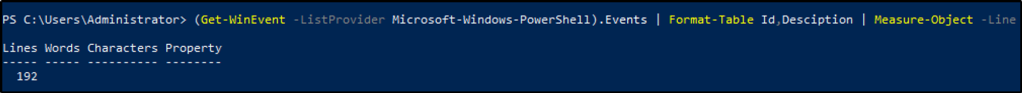
(Get-WinEvent -ListProvider Microsoft-Windows-PowerShell).Events | Format-Table Id, Description | Measure-Object -Line
How do you specify the number of events to display?
Answer: -MaxEvents
Example 13 provided us the options we can use to display only a certain number of events.
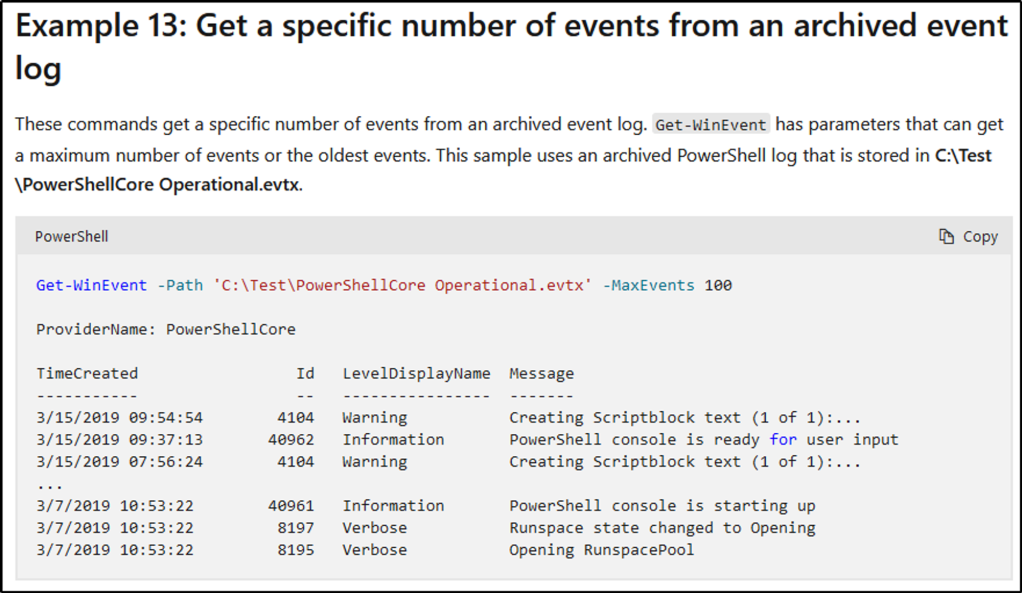
If we want to know more about -MaxEvents, we could use the Get-Help cmdlet.
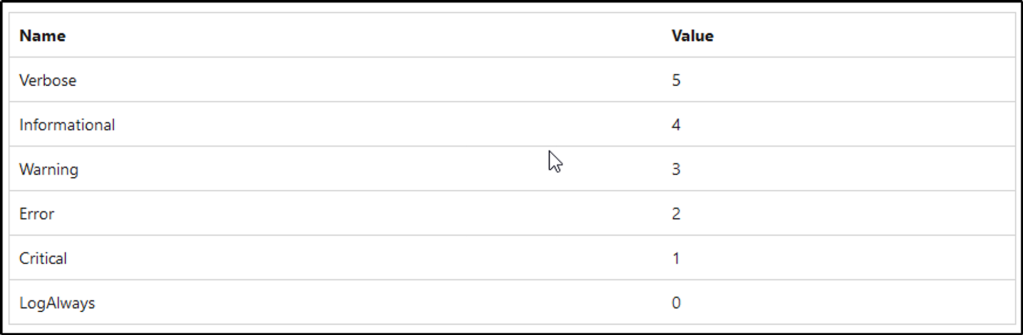
When using the FilterHashtable parameter and filtering by level, what is the value for Informational?
Answer: 4
This resource for FilterHashtable contains the numerical value of each Level.
Task 5: XPath Queries
The third method of filtering events is by using XPath or XML Path Language, which was created by W3C. The Windows Event Log supports a subset of XPath 1.0.
Here is an example of an XPath query along with its explanation:
// The following query selects all events from the channel or log file where the severity level is less than or equal to 3 and the event occurred in the last 24 hour period. XPath Query: *[System[(Level <= 3) and TimeCreated[timediff(@SystemTime) <= 86400000]]]
See docs.microsoft.com for more examples of XPath queries.
Note: An XPath event query starts with ‘*’ or ‘Event‘. wevtutil and Get-WinEvent support XPath queries.
To create an XPath query, Event Viewer would be the reference point.
We look at the bottom of the middle pane, click on the “Details” tab and select the “XML View”. The sructure presented would help use construct a valid XPath query.
The first tag is the starting point. This can either be an ‘*' or Event.
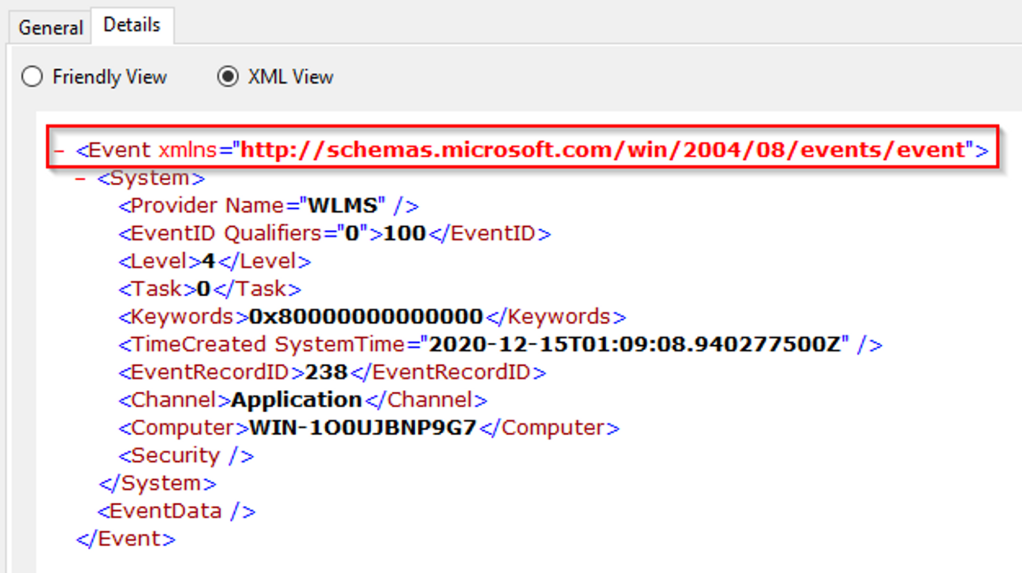
The command would look like this:
Get-WinEvent -LogName Application -FilterXPath '*'Working our way down, the next tag is System.

Let’s add that to our command:
Get-WinEvetnt -LogName Application -FilterXPath '*/System/'Next is the EventID tag. We would use the tag name and include the Event ID we want to filter. In this example, the Event ID is 100.
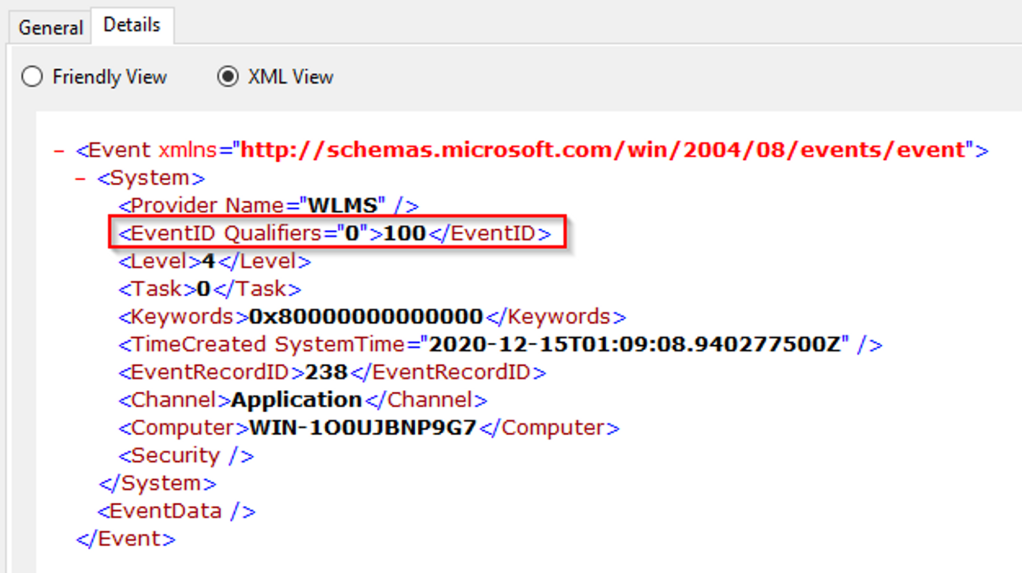
The command would look like something like this:
Get-WinEvetnt -LogName Application -FilterXPath '*/System/EventID=100'The following would be the result if using wevtutil.exe and XPath to query for the same event log and ID.:
wevtutil.exe qe Application /q:*/System[EventID=100] /f:text /c:1
Two additional options were added to filter only one event with no XML tags.
If we want to query a different element, such as the Provider Name, we need to use the Name attribute of Provider.
Therefore, to query for the Provider name with XPath:
Get-WinEvent -LogName Application -FilterXPath '*/System/Provider[@Name="WLMS"]'
We can also combine two queries in one command.
For example, if we want to query Event IDs of 100 with the Provider Name “WLMS”, we would arrive at this command:
Get-WinEvent -LogName Application -FilterXPath '*/System/Provider[@Name="WLMS"]'
Creating XPath queries with EventData
Querying for elements within EventData with XPath will be a little bit different
Note: The EventData element doesn’t always contain information.
We will use the below XML view of an event to build the XPath query
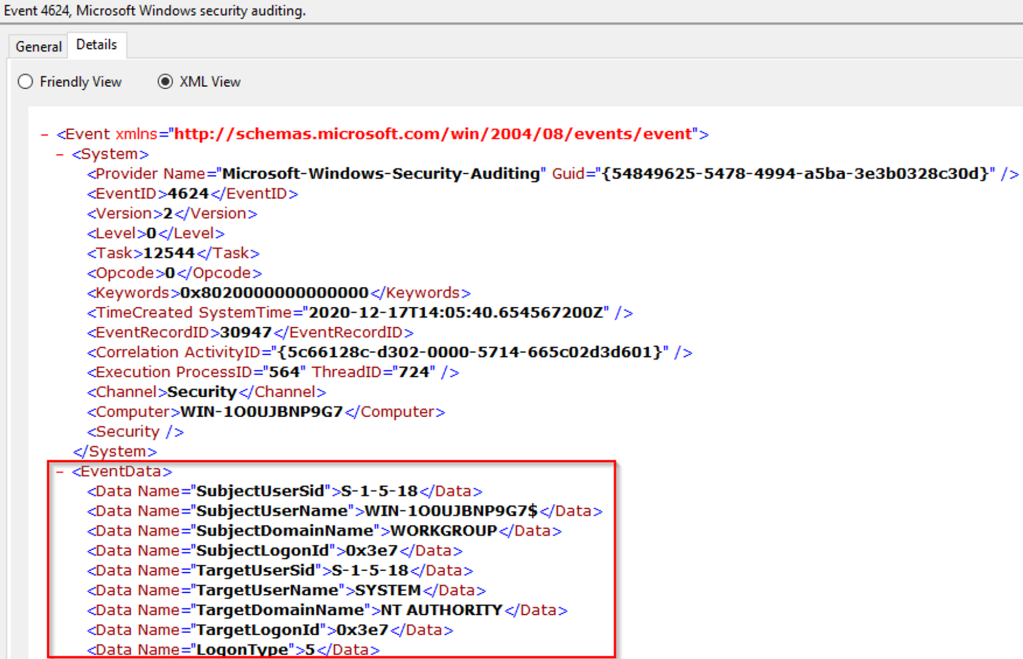
For this example, we will be creating a query for the TargetUserName of System. The XPath query would be:
Get-WinEvent -LogName Security -FilterXPath '*/EventData/Data[@Name="TargetUserName"]="System"' -MaxEvents 1
The parameter -MaxEvents will return just 1 event.
Read the official Microsoft XPath Reference for more information.
Answer the questions below
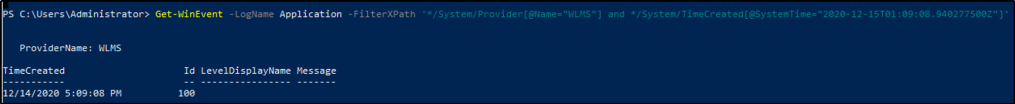
Using the knowledge gained on Get-WinEvent and XPath, what is the query to find WLMS events with a System Time of 2020-12-15T01:09:08.940277500Z?
Answer: Get-WinEvent -LogName Application -FilterXPath ‘*/System/Provider[@Name=”WLMS”] and */System/TimeCreated[@SystemTime=”2020-12-15T01:09:08.940277500Z”]’
The steps provided above in building an XPath query would help us create the command.
Using Get-WinEvent and XPath, what is the query to find a user named Sam with an Logon Event ID of 4720?
Answer: Get-WinEvent -LogName Security -FilterXPath ‘*/EventData/Data[@Name=”TargetUserName”]=”Sam” and */System/EventID=4720’
We will be be creating two queries in one command. The first query is to query within the EventData the tag TargetUsername, and specifying the username to be “Sam”. The second query is within Event, looking through System, and specifying the EventID of 4720.
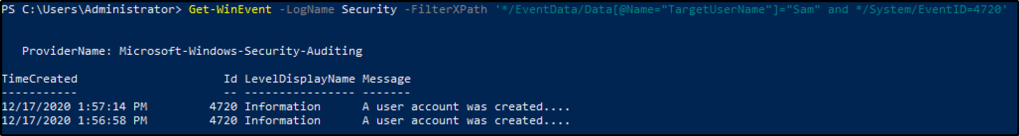
Based on the previous query, how many results are returned?
Answer: 2
We got two results.
Based on the output from the question #2, what is Message?
Answer: A user account was created
The query filters user account creation.
Still working with Sam as the user, what time was Event ID 4724 recorded? (MM/DD/YYYY H:MM:SS [AM/PM])
Answer: 12/17/2020 1:57:14 PM
Working with the same command from above, we just need to change the EventID to 4724.
Get-WinEvent -LogName Security -FilterXPath '*/EventData/Data[@Name="TargetUserName"]="Sam" and */System/EventID=4724'
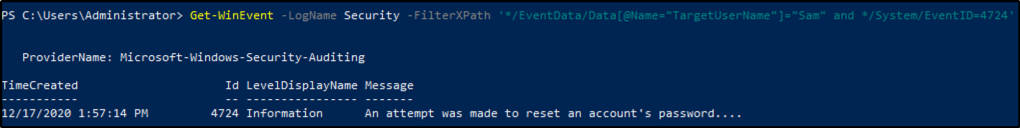
What is the Provider Name?
Answer: Microsoft-Windows-Security-Auditing
We found the answer when we run the command from above.
Task 6: Event IDs
With the large number of Event IDs in use, we will definitely need resources to help us monitor and hunt events. This section will be covering us in that aspect.
First on the list is The Windows Logging Cheat Sheet (Windows 7 – Windows 2012). The last version update is October 2016, but it’s still a good resource. The document covers a few things that need to be enabled and configured and what event IDs to look for based on different categories, such as Accounts, Processes, Log Clear, etc.
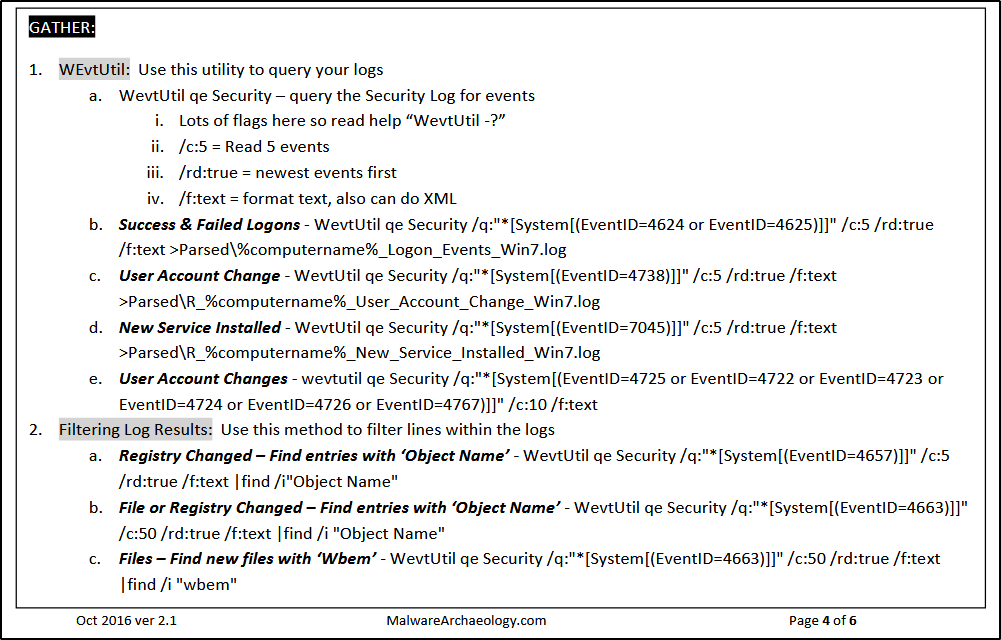
From the resource, if we want to detect if a new service was installed, look for Event ID 7045 within the System Log. The command would be as follows
wevtutil qe System /q:"*/System[EventID=7045]" /c:5 /rd:true /f:text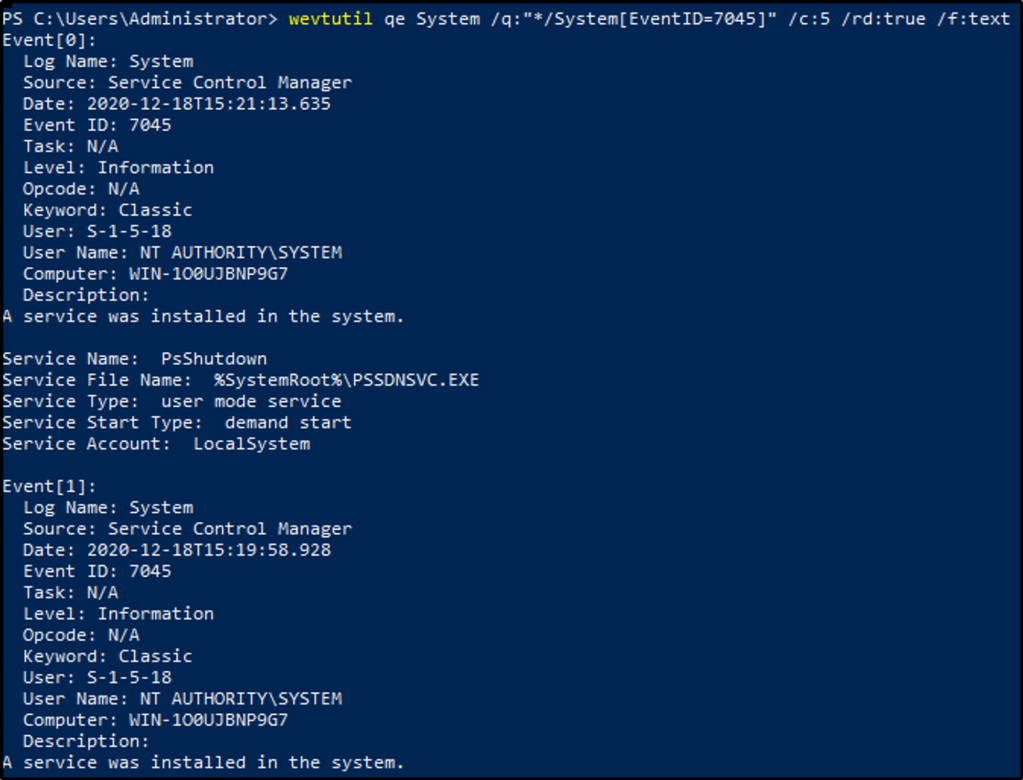
Spotting the Adversary with Windows Event Log Monitoring is another resource.
I was unable though to connect and download the resource.
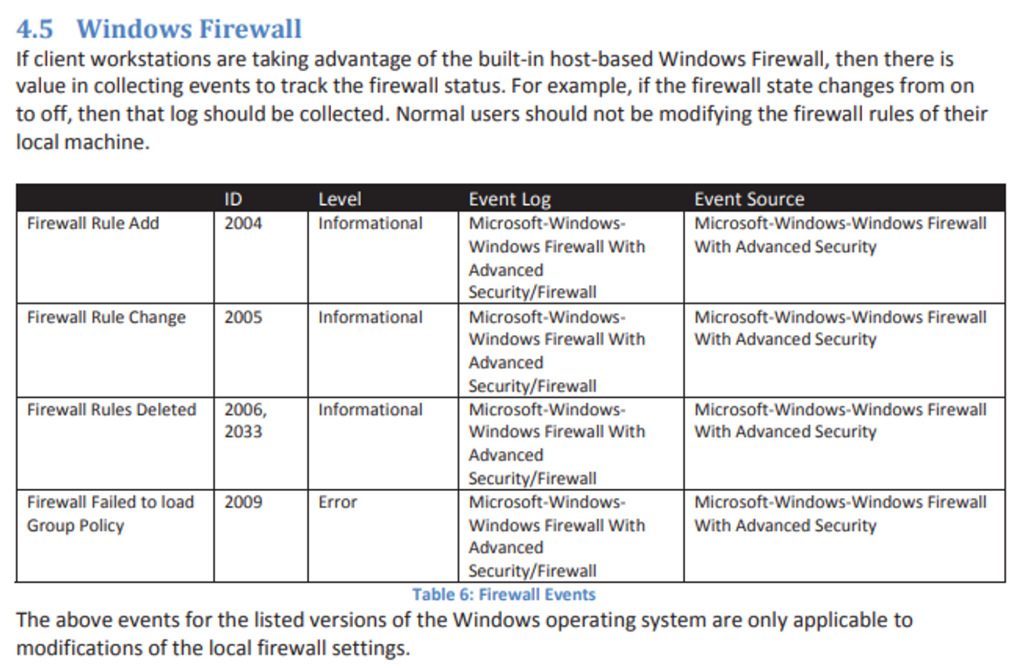
But from the room, a snippet is provided from the document where we see Event IDs related to Firewall Rules.
MITRE ATT&CK is also on the list for monitoring or hunting Event IDs.
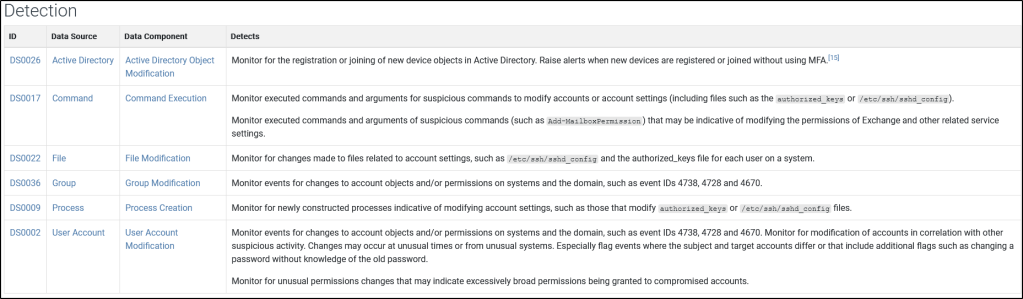
We can look at a Technique and identify the related Event IDs that we should monitor and hunt. For example, if we look at ATT&CK ID T1098 (Account Manipulation), the “Detection” section contains the Event IDs that are triggered.
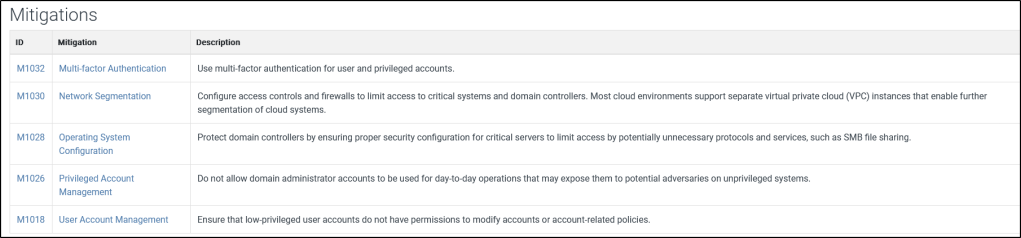
The MITRE ATT&CK framework also contains information on how to mitigate each techniques.
The last two resources are from Microsoft:
- Events to Monitor (Best Practices for Securing Active Directory)
- The Windows 10 and Windows Server 2016 Security Auditing and Monitoring Reference (a comprehensive list [over 700 pages])
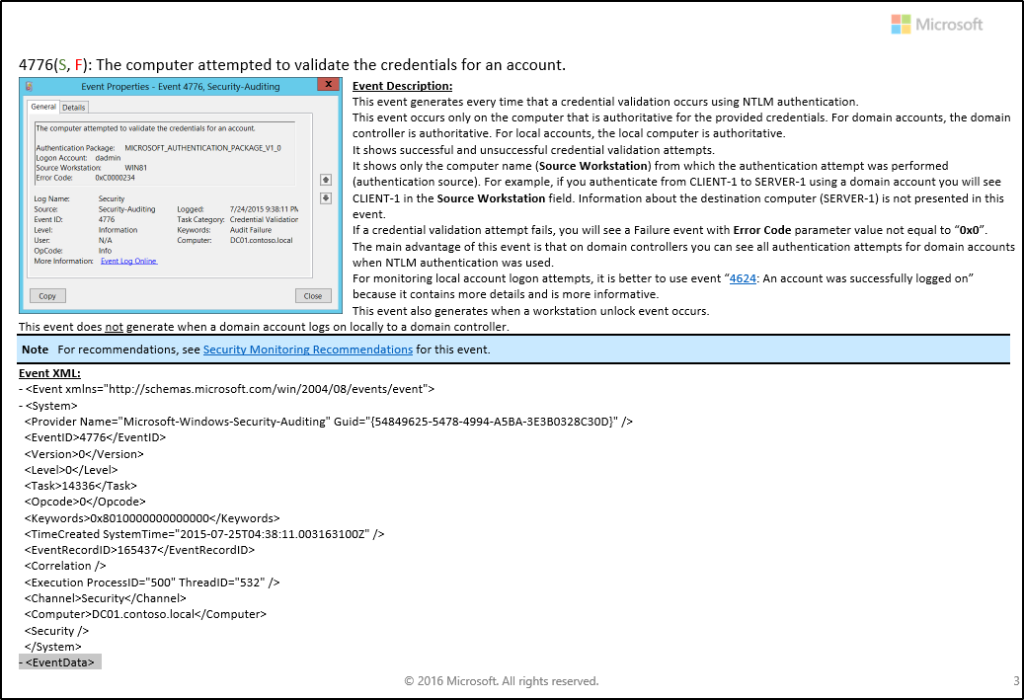
- Here is a snippet of the 700-page Windows 10 and Windows Server 2016 Security Auditing and Monitoring Reference
Note: There are certain events that are not generated by default, one of them is PowerShell logging. This feature can be enabled via Group Policy or the Registry.
Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > Windows PowerShell
Press the Windows icon on the keyboard + R to open the Run dialog and type gedit.msc to open the Group Policy Management Console.
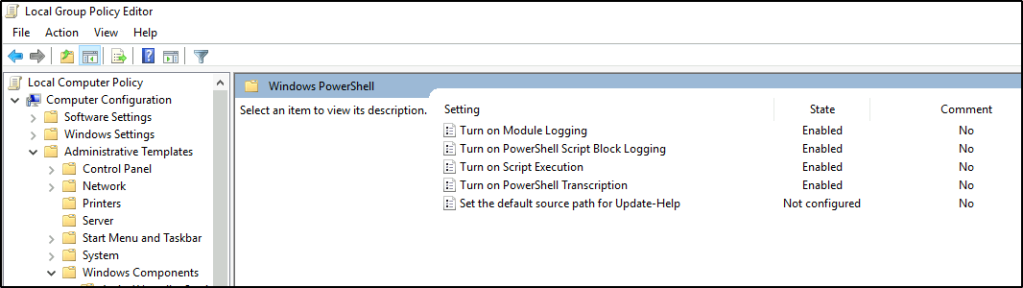
Some resources to provide more information about enabling this feature, along with its associated event IDs:
- About Logging Windows
- Greater Visibility Through PowerShell Logging
- Configure PowerShell logging to see PowerShell anomalies in Splunk UBA
Another feature to enable/configure is Audit Process Creation, which will generate event ID 4688 and will allow command-line process auditing.
Local Computer Policy > Computer Configuration > Administrative Templates > System > Audit Process Creation
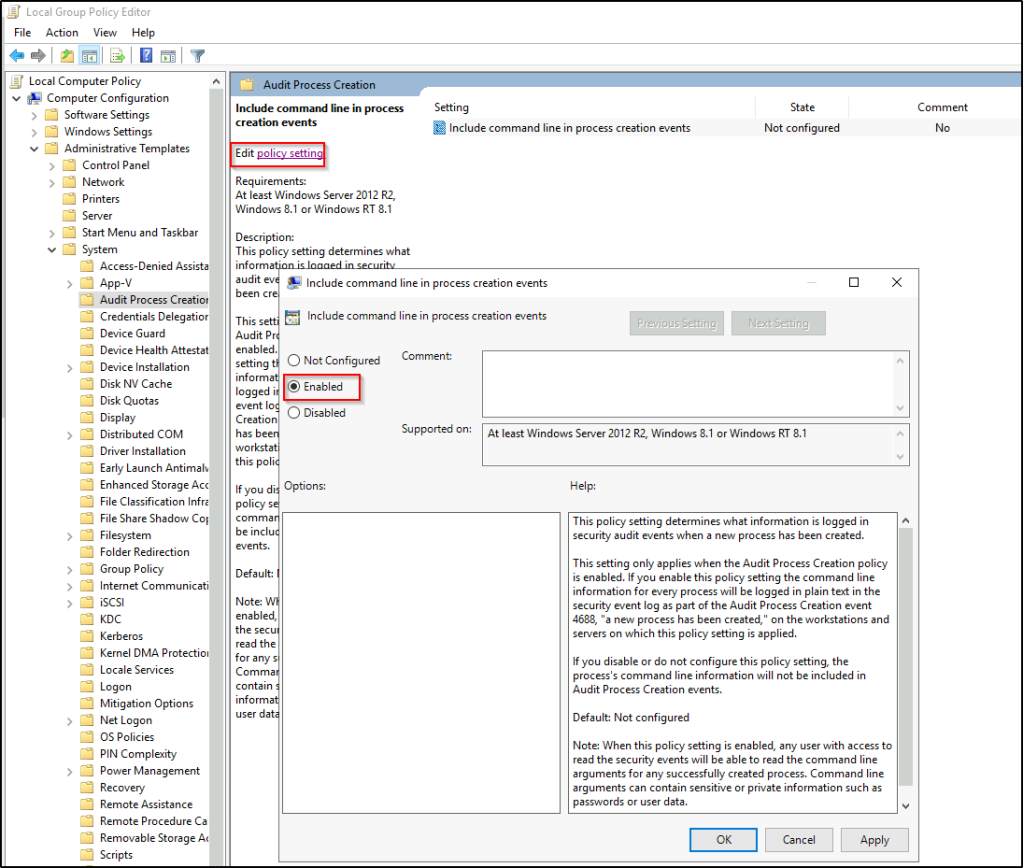
We have already enabled Audit Process Creation
We will now perform step 2.
I run a simple command of whoami
Go to Event Viewer to see if the command was logged. We should look under Windows Logs > Security. It can be observed that it was not logged at all.
Now for step 3, Enable the command line process auditing.
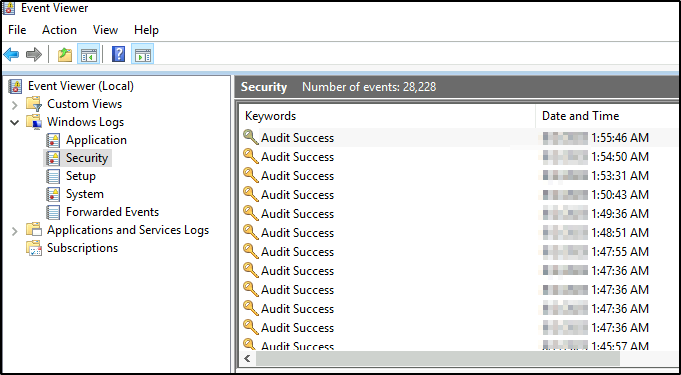
- In the Group Policy Editor, go to “Computer Configuration” > “Windows Settings” > “Security Settings” > “Advanced Audit Policy Configuration” > “Audit Policies” > “Detailed Tracking.”
- In the right pane, locate the “Audit Process Creation” policy, and double-click on it to open the properties.
- In the properties window, select the “Define these policy settings” option.
- Check the “Success” and “Failure” boxes to enable auditing for successful and failed process creations. Click Apply and Ok.
We’ll run the same command and notice if there’s a difference.
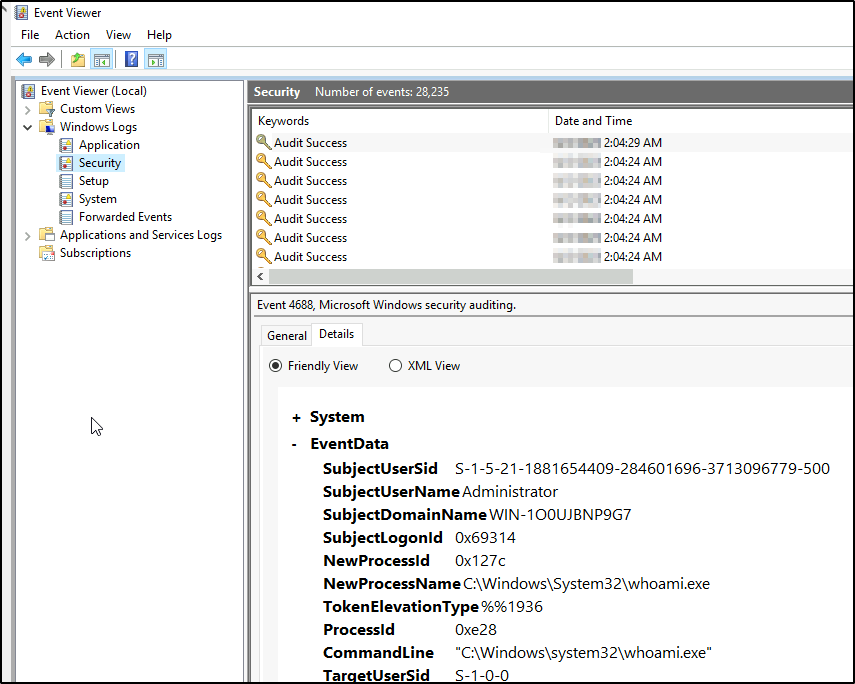
The command was logged this time.
The steps to test the configuration are at the bottom of the document.
The resources are not exhaustive list, hence we need to read more about this topic.
To effectively monitor and hunt, we need to know what to look for.
Answer the questions below
I’m ready to look at some event logs…
Task 7: Putting theory into practice
Let’s now test our newly acquired pool of knowledge on Windows Event Logs with the different scenarious presented below.
The next scenarios/questions are based on the external event log file titled merged.evtx found on the Desktop.
Scenario 1 (Questions 1 & 2): The server admins have made numerous complaints to Management regarding PowerShell being blocked in the environment. Management finally approved the usage of PowerShell within the environment. Visibility is now needed to ensure there are no gaps in coverage. You researched this topic: what logs to look at, what event IDs to monitor, etc. You enabled PowerShell logging on a test machine and had a colleague execute various commands.
Scenario 2 (Questions 3 & 4): The Security Team is using Event Logs more. They want to ensure they can monitor if event logs are cleared. You assigned a colleague to execute this action.
Scenario 3 (Questions 5, 6 & 7): The threat intel team shared its research on Emotet. They advised searching for event ID 4104 and the text “ScriptBlockText” within the EventData element. Find the encoded PowerShell payload.
Scenario 4 (Questions 8 & 9): A report came in that an intern was suspected of running unusual commands on her machine, such as enumerating members of the Administrators group. A senior analyst suggested searching for “C:\\Windows\\System32\\net1.exe“. Confirm the suspicion.
Answer the questions below
Open the merged.evtx file with event viewer
What event ID is to detect a PowerShell downgrade attack?
Answer: 400
A search on google would yield us about detecting PowerShell downgrade attacks. Here is an interesting article why attackers would downgrade to older versions of PowerShell.
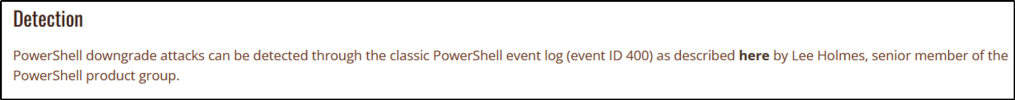
What is the Date and Time this attack took place? (MM/DD/YYYY H:MM:SS [AM/PM])
Answer: 12/18/2020 7:50:33 AM
I used PowerShell for this task, added –Path parameter to indicate the source of the log file.
Get-WinEvent -Path .\\Desktop\\merged.evtx -FilterXPath '*/System/EventID=400' -MaxEvents 10
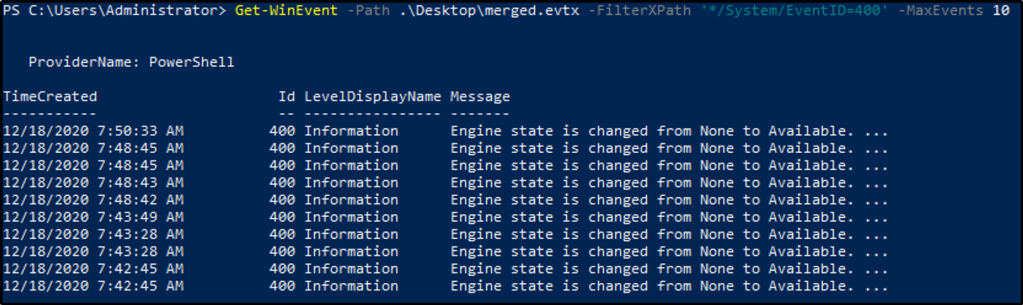
We can add the following to sort the results.
Sort-Object -Property TimeCreated -Descending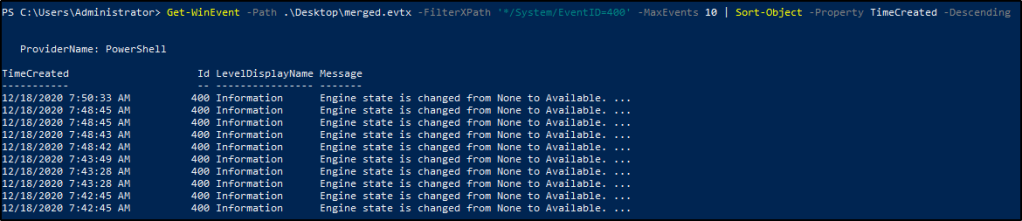
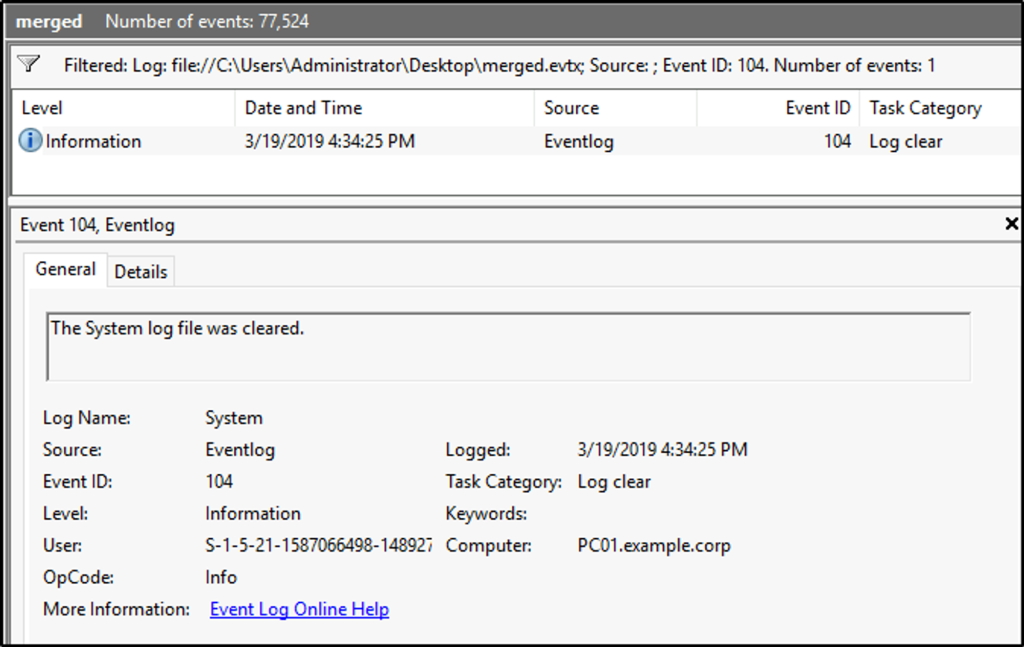
A Log clear event was recorded. What is the ‘Event Record ID’?
Answer: 27736
In one of the resources provided, an EventID of 104 is generated when the Application or System log were cleared.
Now that we know the Event ID, let’s filter the logs with eEentID 104.
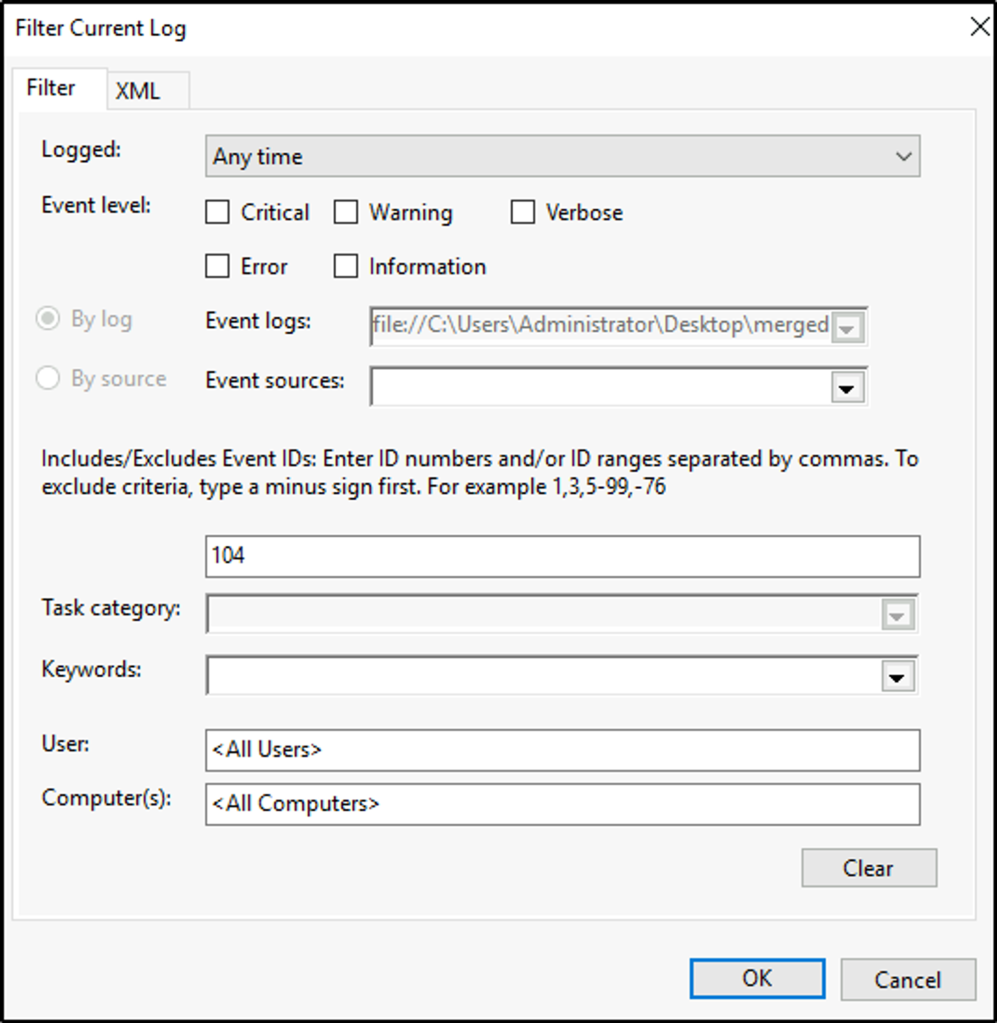
Select the windows event. In the lower pane, click on the “Details” tab and select “XML View”. We now see the ID for the recorded event.
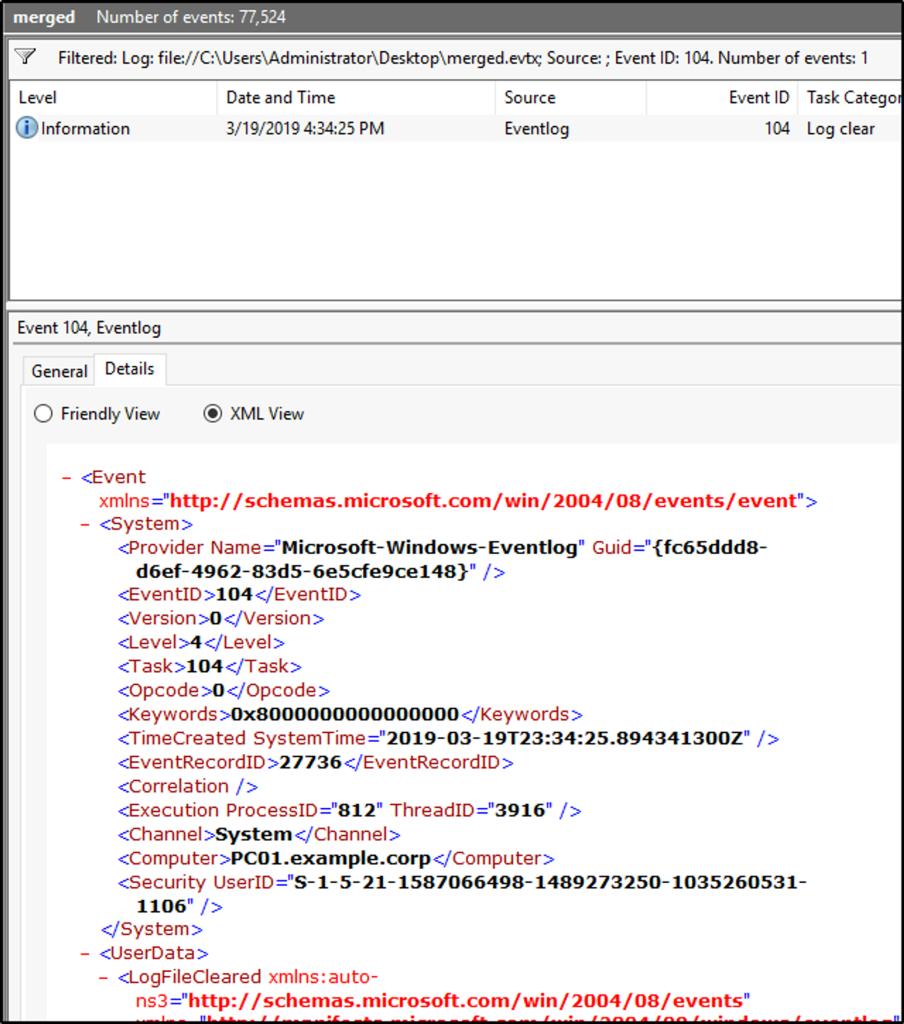
What is the name of the computer?
Answer: PC01.example.corp
The computer name is seen in the tag “Computer” or in the “General” tab.
What is the name of the first variable within the PowerShell command?
Answer: $Va5w3n8=
It is important to know, that only when Script Block Logging is enabled, that these blocks of code, when executed by PowerShell are logged. Such events are recorded with EventID 4104.
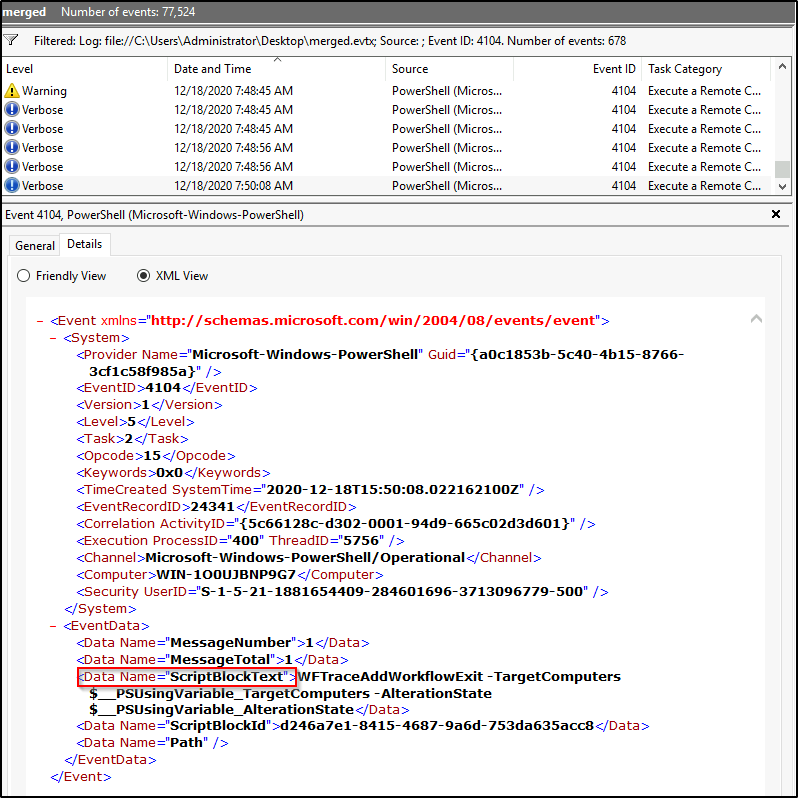
The following command would query, using XPath, all events with a 4104 ID, within “EventData” focusing on the tag “Data” that has the strings “ScriptBlockText”. Note: Variables always start with ‘$’.
Get-WinEvent -Path .\\Desktop\\merged.evtx -FilterXPath '*/System/EventID=4104 and */EventData/Data[@Name="ScriptBlockText"]' -Oldest -MaxEvents 1 | Format-List
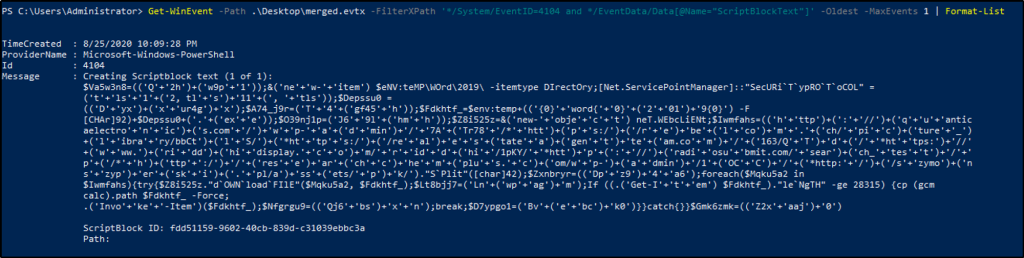
It took me a while to realize that the details displayed are incomplete, and I try not to rely on Event Viewer too much, because imagine if we have thousands of events to crumb through.
These commands would display all the info about the events and would also provide the answer for the next two questions.
Get-WinEvent -Path .\Desktop\merged.evtx -FilterXPath '*/System/EventID=4104 and */EventData/Data[@Name="ScriptBlockText"]' -Oldest -MaxEvents 1 | Select-Object -Property *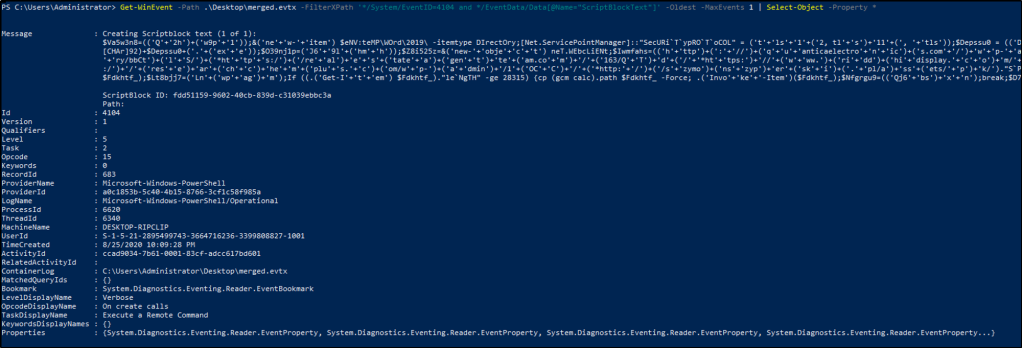
What is the Date and Time this attack took place? (MM/DD/YYYY H:MM:SS [AM/PM])
Answer: 8/25/2020 10:09:28 PM
What is the Execution Process ID?
Answer: 6620
What is the Group Security ID of the group she enumerated?
Answer:S-1-5-32-544
To confirm if she enumerated the “Administrators” group in her local machine, we would run the following commands. We will filter events with XPath within the elements of “EventData” and include the location of the suspected executed file. The piped results would display all the information about the queried events.
Get-WinEvent -Path .\merged.evtx -FilterXPath '*/EventData/Data[@Name="CallerProcessName"]="C:\Windows\System32\net1.exe"' | Select-Object -Property *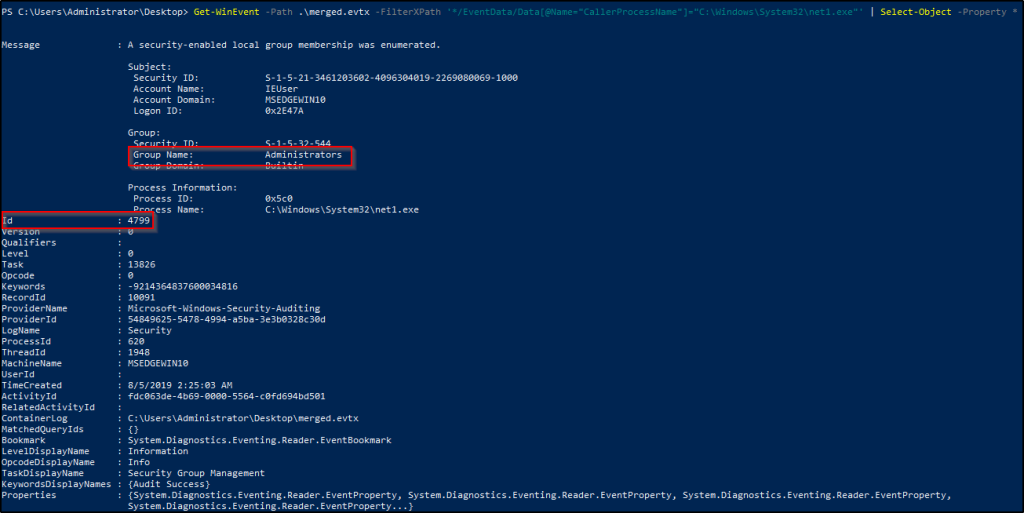
There were three events logged, but we are interested in the event where the local group “Administrators” was enumerated.
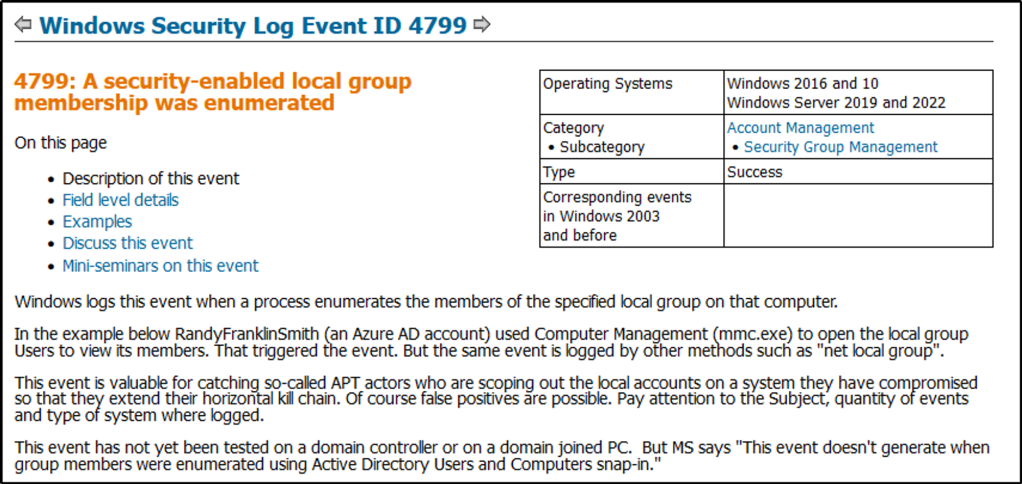
What is the event ID?
Answer: 4799
For reference, check this out.
Task 8: Conclusion
We have covered a lot about Windows Event Logs, the important Event IDs we should monitor and hunt, and how to query them with the different tools and techniques.
We also touched on the features that need to be enabled or configured so that they can be logged for further visibility.
Windows event logs from various endpoints are also forwarded to SIEMs for easy filtering of evnts, correlating rules, generating reports, and detecting suspicous activities.
TryHackme provided us parting gifts for additional reading:
- EVTX Attack Samples (a few were used in this room)
- PowerShell ❤ the Blue Team
- Tampering with Windows Event Tracing: Background, Offense, and Defense
That concludes this room.
Thank you for reading 🙂
Happy learning!.
If you’re using a Windows server and want to know what happened to your machine, Windows logs are an essential resource. Windows logs record various system activities, errors, and other significant events, providing valuable information for troubleshooting, auditing, and ensuring system integrity. Understanding how to access, interpret, and utilise these logs enables efficient, problem solving, enables security measures and ensures the smooth operation of your system.
In this guide, you will learn about Windows event logs, its different categories, how to filter and create Custom Views.
What is a Windows Event Log?
A Windows event log is a file that keeps track of system events and errors, application issues, and security events. Windows Event log can also provide insights into an application’s behavior by tracking its interactions with other processes and services. With the right knowledge of the information stored in these logs, you can easily diagnose and easily resolve issues within your system and applications.
You can access the windows events logs as follows:
Using the Start Menu:
- Click on the Start button or press the Windows key.
- Type
Event Viewerin the search box and select it from the search results.
Using the Run Dialog:
- Press
Windows + Rto open the Run dialog. - Type
eventvwrand press Enter.
Using the Control Panel:
- Open the Command Prompt and run as administrator.
- Type
eventvwrand press Enter.
You can see the detailed steps below. Now let’s discuss and understand windows events logs in detail.
Understanding Windows Event Logs categories & Types
There are different Windows logs, each serving a specific purpose in tracking and recording events related to your system, applications, and security. They include:
- System Events: System events log information is about the core operations of your Windows operating system. System events are essential for maintaining your system’s health and functionality because it records events related to the system’s hardware and software components. Some system events are as follows:
- Hardware Failures: Logs any issues related to hardware components, such as disc failures or memory errors.
- Driver Issues: Records events related to the loading, unloading, or malfunctioning of device drivers. This helps in identifying driver-related problems that could affect system stability.
- System Startups and Shutdowns: Tracks the times when the system starts up or shuts down. This can be useful for understanding system uptime and diagnosing issues related to improper shutdowns or startup failures.
- Application Events: Data related to software applications running on the system includes application errors, warnings, and informational messages. If you are using a Windows server to run your production-level application, you can use the application errors, warnings, and messages provided here to solve the issue. There are different types of Application events some are as follows:
- Application Errors: Application errors are events generated by software applications when they encounter issues that prevent them from functioning correctly.
- Warnings: Logs warnings from applications about potential issues that might not be critical but could lead to problems if not addressed.
- Informational Messages: Provides general information about application activities, such as successful operations or status updates, helping to understand the normal functioning of applications.
- Security Events: Security events are logs that capture all security-related activities on your Windows system. They are essential for monitoring, maintaining, and auditing the security of your system. These events help detect unauthorised access attempts, monitor access to sensitive resources, and track changes to system policies. Some security events are as follows:
- Successful and Failed Login Attempts: Successful and failed login attempts are critical events that are logged by a system to monitor access and ensure security. These logs provide valuable insights into user activity, helping to detect unauthorised access attempts and identify potential security threats.
- Resource Access: These events log attempts to access protected resources such as files, folders, or system settings. Monitoring these logs ensures that sensitive data is accessed appropriately and helps identify unauthorised access attempts.
- System Policy Changes: These logs record any changes to system policies, including modifications to user permissions or security settings. This is important for auditing purposes and ensuring compliance with security policies, helping to maintain the integrity and security of the system.
- Setup Events: Setup events are logs that contain detailed information about the installation and setup processes on your Windows system. These logs are valuable for diagnosing and resolving issues that occur during the installation or configuration of software and system components. Some Setup events are as follows:
- Installation Processes: Installation processes refer to the series of steps and operations carried out to install software, updates, or system components on a Windows system. It contains log details about software installation, updates, or system components. This helps in diagnosing issues related to incomplete or failed installations.
- Setup Configurations: Records information about system configurations during the setup process. This can be useful for understanding your system’s initial setup and configuration.
- Forwarded Events: Forwarded events are logs sent from other computers to a centralised logging server. This is particularly useful in larger environments where centralised log management is needed. They include:
- Logs from Remote Systems: Collects event logs from multiple systems, allowing for centralised monitoring and management.
- Centralised Logging Scenarios: Useful for organisations that need to aggregate logs from various systems to a single location for easier analysis and monitoring.
Accessing the Windows Event Viewer
Windows Event Viewer is a Windows application that lets you see your computer’s logs, warnings, and other events. Each application you open generates entries that are recorded in an activity log, which can be viewed from the Event Viewer.
There are several ways to access the Windows Event Viewer. Here are some of them:
-
Using the Start Menu:
- Click on the Start button or press the Windows key.
- Type
Event Viewerin the search box.
Using start menu to open Event viewer — Select Event Viewer from the search results which will popup something like this.
Event Viewer main page 2. Using the Run Dialog: — Press
Windows + Rto open the Run dialog. — Typeeventvwrand press Enter.Windows Run App to open Event Viewer Windows Event viewer landing page 3. Using Control Panel: — Open the Command Prompt and run as administrator
Open CMD as Administrator from start menu — Once open, type
eventvwrand press enter, and you will be redirected to Event Viewer page.CMD terminal
Windows Log Location
Windows event logs are stored in files located in the C:\\Windows\\System32\\winevt\\Logs directory. Each log file corresponds to a specific log category, such as System, Application, or Security. It may differ depending on which version of Windows you are using.
The main event log files are:
- Application.evtx: Logs events from applications and programs.
- Security.evtx: Logs security events like successful or failed logins.
- System.evtx: Logs events related to Windows system components and drivers
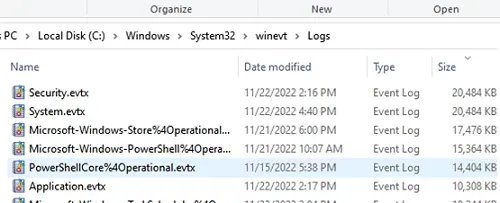
You can find many other log files which could be related to system operations & other processes that are happening inside the Windows System. Windows 11uses the .evtx format rather than using the classic EVT format.
Understanding Event Viewer Entries
Event Viewer entries provide detailed information about each logged event. It is like a log book for your Windows system. They record important happenings within the system, including applications, systems, security, failed events, etc. Understanding these entries is key to effective log management.
The key components of an Event Viewer entry are:
- Date and Time: When the event occurred.
- Source: The application or system component that generated the event.
- Event ID: A unique identifier for the event type.
- Level: The severity of the event (Information, Warning, Error, Critical).
- User: The user account under which the event occurred.
- Computer: The name of the computer where the event was logged.
- Description: Detailed information about the event.
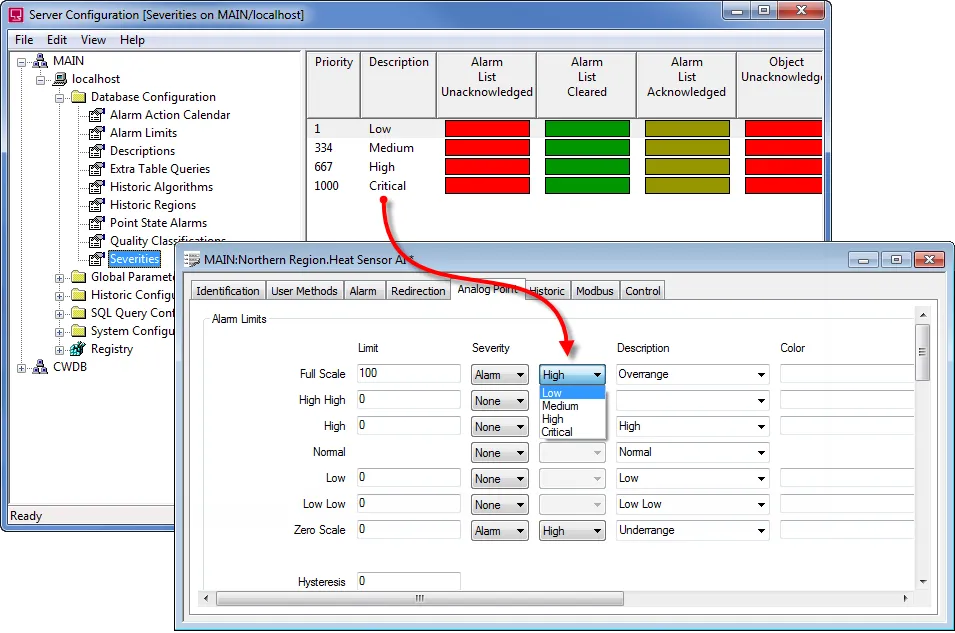
Each event in the Event Viewer has a severity level, indicating the importance and type of the event:
- Information (Green Light): These events resemble a green traffic light, signifying smooth sailing. They indicate successful operations or occurrences within your system.
- Warning (Yellow Light): Treat these entries with caution, like a yellow traffic light. They signal potential issues that warrant attention but might not cause immediate problems.
- Error (Orange Light): Think of error entries as an orange traffic light; proceed with care. They denote significant problems that could affect system functionality. Imagine an error message indicating a driver failure.
- Critical (Red Light): Critical entries are akin to a red traffic light; stop and address the situation immediately. They represent severe errors that have caused a major failure. A critical event might report a complete system shutdown or a critical service crashing.
Filtering and Custom Views
Event Viewer allows you to filter events using a variety of parameters, including date, event level, source, and more. Consider the following scenario: your system exhibits weird behaviour, but the Event Viewer is overflowing with hundreds, if not thousands, of entries. Filtering steps and generating custom views can significantly reduce the workload. You may also construct custom views to focus on specific kinds of events:
- In the Event Viewer, you’ll see Administrative Events, to create special logs right-click on «Custom Views» and select «Create Custom View.»
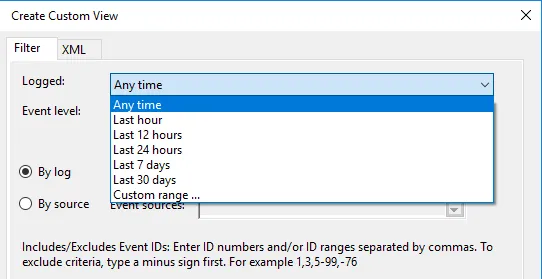
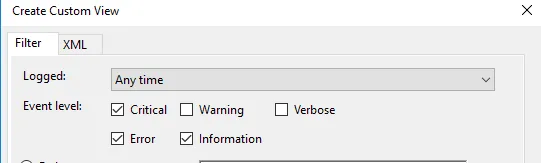
1. In the Custom View page, you can see logged drop down, choose a preferred time or it gives you an option to create a custom time to set. 2. On the Event Level choose an appropriate level for your custom view, You can choose among the 5 levels.
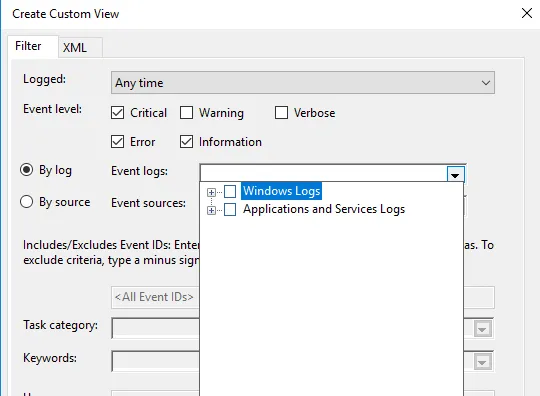
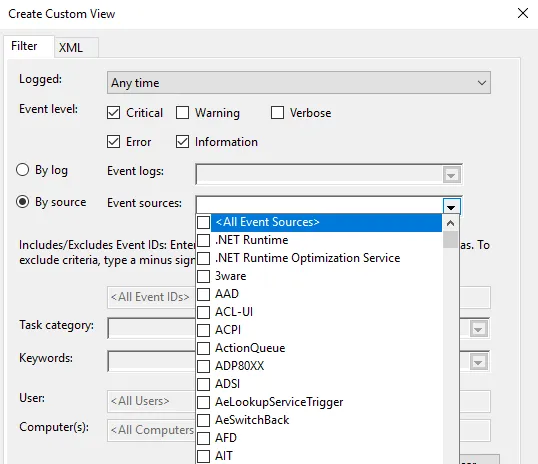
1. Once done, choose how you want the events to be filtered, By log or By source.
Once everything is set up according to your needs, save all events in Custom View as
from the drop-down menu and choose an appropriate location to save the logs. Click on the Save button. (A log file with the extension .evtx will be saved on your device).
Conclusion
This blog provides an understanding how you can use the Windows Event Viewer which is provided by the Windows in default and using it to monitor Windows logs.
- Main event log files are stored in
C:\\Windows\\System32\\winevt\\Logs. - Windows logs are crucial for understanding the activities, errors, and significant events on your machine. They provide valuable information for troubleshooting, auditing, and ensuring system integrity.
- They record a variety of system activities, errors, and other significant events, providing valuable information for troubleshooting, auditing, and ensuring system integrity.
- We learnt how to setup Filtering and Custom Views to optimise what we see and solve the problems and where it happened.
By grasping the significance of different event types such as System, Application, Security, Setup, and Forwarded Events, and knowing how to filter and export logs, you can effectively manage your Windows system.
FAQ’s
How to view Windows logs?
To view Windows logs, use the built-in Event Viewer:
- Press
Win + R, typeeventvwr, and press Enter. - Navigate through the console tree to find the log you want to view (e.g., Windows Logs > Application).
Where are Microsoft logs?
Microsoft logs, including Windows logs, can be found in the Event Viewer under sections like Application, Security, and System. Log files are also located in the C:\Windows\System32\winevt\Logs directory.
How do I audit Windows logs?
To audit Windows logs:
- Open Event Viewer.
- Navigate to Security logs under Windows Logs.
- Configure auditing policies via the Local Security Policy or Group Policy Management Console.
How do I check my Windows activity log
Check your Windows activity log by viewing the Security logs in Event Viewer. These logs record user logins, logoffs, and other security-related activities.
Which is Windows log key?
The Windows log key, often referred to as the Windows key, is the key on your keyboard with the Windows logo. It is used in various shortcuts to open system tools, including Event Viewer (Win + X > Event Viewer).
Where is the logs folder?
The logs folder is located at C:\Windows\System32\winevt\Logs. This folder contains all the event log files in .evtx format.
Why are Windows logs important?
Windows logs are important because they provide detailed information about system operations, security events, and application behavior, which is crucial for troubleshooting, auditing, and ensuring system integrity.
How to view log files?
View log files using Event Viewer:
- Open Event Viewer (
Win + R, typeeventvwr, press Enter). - Expand the Windows Logs section and select the log you want to view.
Where are login logs?
Login logs are located in the Security logs section of Event Viewer. They record all login attempts, both successful and failed.
What are system logs?
System logs contain information about the core operations of the Windows operating system, including hardware events, driver issues, and system startups and shutdowns. They are found under the System section in Event Viewer.
How do I find Windows log files?
Find Windows log files in the Event Viewer or directly in the C:\Windows\System32\winevt\Logs directory.
How do I view user logs in Windows 10?
View user logs in Windows 10 through the Event Viewer:
- Open Event Viewer.
- Go to Windows Logs > Security to see logs related to user activities, including logins and logoffs.
How do I view Windows setup logs?
To view Windows setup logs:
- Open Event Viewer.
- Navigate to Applications and Services Logs > Microsoft > Windows > Setup.
How do I view Windows app logs?
To view Windows application logs:
- Open Event Viewer.
- Navigate to Windows Logs > Application to see logs related to software applications running on your system.
Was this page helpful?
When you’re managing Windows systems, one tool you’ll quickly come to appreciate is the Event Viewer.
It’s like a detailed diary of your system’s activities, giving you insight into everything that’s going on behind the scenes.
Whether you’re diagnosing issues, keeping tabs on performance, or ensuring your system’s security, the event logs are your go-to resource.
For IT pros, knowing how to tap into these logs can make troubleshooting faster, save you time, and even help with stay on top of compliance.
What Are Event Logs in Windows?
Event logs in Windows are records of system events, including everything from hardware failures to software crashes. These logs capture system messages, warnings, errors, and informational events, offering insights into your system’s behavior.
Windows logs events in a structured manner, allowing you to access them using the Event Viewer tool.
The logs are classified into different categories, which makes it easier to filter and search for specific data:
- Application logs: Events related to installed applications.
- System logs: Information about the operating system and its components.
- Security logs: These logs contain security-related events, including login attempts and account changes.
- Setup logs: Events related to the installation and setup of the system and software.
- Forwarded events: Logs collected from remote machines.
Each event entry in these logs contains a timestamp, event ID, level (such as critical or warning), and a description, making it easier to understand the context of an issue.
Key Components of Event Logs
Event logs are vital for tracking and troubleshooting activities within systems. Understanding their components can make it easier to navigate and analyze them.
Let’s break down the key components you’ll typically encounter:
Timestamp:
Every event in a log is timestamped, indicating the exact time the event occurred. This helps in tracking the sequence of events and identifying issues that happened at a specific point.
Event Type:
The event type describes what kind of event has occurred. It could be an error, warning, informational message, or success notification. Knowing the event type lets you prioritize issues based on severity.
Event Source:
The event source indicates which part of the system generated the log. Whether it’s a web server, database, or application service, the source helps pinpoint where things went wrong.
Message/Description:
This is the human-readable part of the log that explains what happened. It could be something like «Database connection failed» or «User logged in successfully.» These messages are crucial for understanding the context of the event.
Event ID:
Some systems assign a unique identifier to each event. This helps reference specific events, especially when dealing with large sets of logs.
Severity Level:
Severity levels help categorize the event based on how critical it is. Common levels include Critical, Error, Warning, Information, and Debug. This component allows you to prioritize responses effectively.
User Information:
If the event involves a user (like logging in or performing an action), the log will often include details such as the user’s ID or username. This makes it easier to trace actions back to specific individuals.
Host or Device Info:
For systems with multiple servers or devices, the log will also include information about which host or device the event came from. This helps when managing distributed systems.
Why Event Logs Are Important
Event logs are crucial for several reasons:
Troubleshooting: They provide a detailed history of what happened before and after a problem occurred. This helps identify the root cause of system crashes, network failures, or application errors.
Performance monitoring: Logs show system health, indicating if resources are being strained or if specific components are not functioning properly.
Security: Event logs are an essential part of tracking security breaches or unauthorized access. By monitoring security-related events, IT administrators can spot potential threats early.
Compliance and auditing: Many businesses need to comply with regulations that require them to maintain and monitor logs for auditing purposes. Event logs help ensure compliance with standards like HIPAA, PCI DSS, or GDPR.
How to Access Event Logs in Windows
To begin working with event logs, you’ll need to access them through the Event Viewer, a built-in Windows tool.
Here’s how to open it:
- Press the Windows key and type «Event Viewer» in the search bar.
- Click on the Event Viewer app.
- Once opened, you’ll see the Event Viewer interface with several logs displayed in the left pane.
Here’s a quick breakdown of the main sections:
Windows Logs: This includes the default logs like Application, Security, Setup, System, and Forwarded Events.
Applications and Services Logs: Logs related to specific applications and services on your computer.
Custom Views: Custom filters that you can create to narrow down the log results to a specific time, severity level, or event type.
You can filter, sort, and search these logs based on different criteria to find exactly what you’re looking for.
Types of Events in Windows Logs
Event logs contain different types of events, each with a specific purpose.
Here’s a quick look at the most common ones:
Information:
Information events are typically not an issue. These logs provide details about system activities or successful operations, such as software installation or system startup.
Warning:
Warning events don’t usually signify a problem, but they indicate that something may be off. For example, low disk space or a driver issue could generate a warning.
Error:
Error events are more serious. They suggest a problem with hardware, software, or services, such as a failed system update or application crash. These are critical to investigate.
Critical:
Critical events indicate a severe issue that can result in system instability or failure. Immediate attention is required when you encounter critical errors.
How do you Monitor and Analyze Event Logs
Once you’ve got your event logs in place, it’s time to monitor and analyze them to ensure your system is running smoothly and to catch potential issues early.
Here’s how you can go about it:
Set Up Centralized Logging
Storing logs from various systems in one central location makes it easier to monitor and analyze. Tools like ELK Stack (Elasticsearch, Logstash, Kibana) or Last9 help aggregate logs from different sources into a single interface for streamlined management.
Real-time Monitoring
Keeping an eye on logs in real-time is crucial, especially when dealing with production environments. Real-time monitoring allows you to react quickly to critical events. Tools like Prometheus, Grafana, or Last9 can help you visualize logs live with customizable dashboards and alerts.
Log Parsing and Filtering
With logs generated in large volumes, it’s easy to get overwhelmed. Parsing and filtering logs by specific fields (like event type or severity level) help narrow down what’s important. Using tools like Fluentd or Logstash for parsing can simplify the process, ensuring you only see the most relevant data.
Threshold-Based Alerts
Set up alerts based on specific thresholds. For example, if the number of error logs exceeds a certain number in a minute, trigger an alert. This enables quick responses to issues before they escalate.
Log Correlation
Event logs don’t exist in a vacuum. Correlating logs across different systems can give you a clearer picture of what happened and why. If an error in your application is tied to a server issue, correlating logs can help identify the root cause.
Analyzing Patterns and Trends
Instead of only focusing on immediate issues, look for recurring patterns or long-term trends in your logs. Analyzing logs over time can reveal chronic problems, performance bottlenecks, or even security vulnerabilities.
Automated Log Analysis
Manual log analysis can be time-consuming, but automation can save you a ton of effort. Set up machine learning algorithms or rule-based engines to detect anomalies or patterns in logs automatically. This can help identify things like unexpected spikes in traffic or unusual error rates that might go unnoticed in a manual review.
Post-Mortem Analysis
After resolving an incident, it’s crucial to conduct a post-mortem analysis. Look through the logs from the event, track the timeline of the issue, and analyze how it was resolved. This helps in learning from the incident and preventing similar ones in the future.
How to Analyze Event Logs for Troubleshooting
Once you’ve accessed your event logs, it’s time to dig deeper and identify the root causes of issues.
Here’s a general approach for effective log analysis:
Use Event IDs
Each event in the log comes with a unique Event ID, which is a great starting point. You can search for these IDs online or refer to the Microsoft Event ID documentation to understand what the event means.
For example, Event ID 41 indicates that the system has rebooted unexpectedly, while Event ID 101 signals a problem with a service or application.
Check Event Details
Clicking on an individual event will show you more detailed information, including the exact error message, source, and sometimes even a solution or link to more resources. This can provide you with clues to address the issue directly.
Correlate with Other Logs
One event log might not provide enough information on its own. Check other logs to find correlations. For example, a critical error in the System log could be related to an application log entry showing a software crash.
Export Logs for External Analysis
If you’re dealing with a particularly tricky issue, it might help to export your logs and analyze them in a different tool. You can export logs in CSV, XML, or EVTX formats and then use external programs or scripts for deeper analysis.
Why Automate Event Log Monitoring
While manually reviewing event logs is helpful, it can become tedious and time-consuming, especially in larger environments. To save time and catch problems earlier, consider using tools to automate event log monitoring.
Windows Performance Monitor
It allows you to set up alerts and create custom reports, making it easier to stay on top of system health without manually sifting through logs.
Log Management Solutions
Tools like Splunk, SolarWinds, and ELK Stack offer centralized log collection, search, and analysis. These tools provide more advanced filtering, visualization, and alerting features to streamline your monitoring process.
Syslog
If you’re managing multiple Windows servers, consider forwarding event logs to a central syslog server. This can simplify management and analysis across your environment.
How to Use Windows Event Viewer
Windows Event Viewer is your go-to tool for managing and analyzing event logs on your system. It gives you insights into what’s happening behind the scenes, helping you troubleshoot and stay on top of things. Here’s how to make the most of it:
Accessing Windows Event Viewer
Opening Event Viewer
To get started, press Win + R to open the Run dialog, type eventvwr.msc, and hit Enter. Or, you can simply search for «Event Viewer» in the Start menu. Once it’s open, you’ll be greeted by a window with different types of logs waiting to be explored.
Navigating the Interface
The left panel is like your map to the logs. It has categories like Windows Logs, Applications and Services Logs, and Custom Views. These sections help you drill down into specific logs—like System, Application, or Security logs—depending on what you’re looking for.
For a deeper look into managing system logs with systemctl, check out our post on Systemctl Logs.
Viewing Event Logs
Choosing a Log
Pick a category, like Application or System, from the left panel to view the logs under that category. You’ll see a list of events with details like the time, event ID, and severity level—a history of what’s been going on.
Examining Event Details
When you click on an event, a window pops up with all the juicy details—Event ID, Source, Description, and more. This info is key for understanding what went wrong when it happened, and its impact.
Filtering Event Logs
Using Filters
Looking for something specific? Filters are your friend. You can narrow down logs based on event level, date/time range, event IDs, or even keywords.
To filter, right-click on a log category (like Application), select Filter Current Log, and set your filter parameters. This will save you time by focusing only on what matters.
Custom Views
Want to see logs based on custom criteria? You can create custom views to group logs that match specific conditions.
For example, set up a view to only show Error events from a certain source. To do this, click on Custom Views in the left panel, select Create Custom View, and define the filter conditions.
Saving Event Logs
Exporting Logs
Sometimes, you’ll want to save event logs for future reference or sharing. To do this, right-click the log category and select Save All Events As. You can choose to save it as an .evtx file for later review or even export it to a CSV for easier analysis in a spreadsheet.
Clearing Event Logs
Clearing Logs
Event logs can pile up, especially on busy systems. If you need to clear them, right-click on the log category (like Application or System) and select Clear Log. You’ll be prompted to save them before clearing, in case you want to keep a backup.
If you’re managing cron jobs and logs, take a look at our post on Crontab Logs for more insights.
Using Event Logs for Troubleshooting
Event Viewer is a great tool when troubleshooting issues like application crashes, security breaches, or hardware failures. Look out for error codes and descriptions in the logs—they’re often a helpful clue for solving the problem.
Keep an eye on warnings and error messages, and use event IDs to search online for targeted troubleshooting advice.
Best Practices for Event Log Management
To get the most out of your event logs, keep these best practices in mind:
Regularly Monitor Logs
Don’t wait for a critical error to happen. Set up a routine to regularly review event logs and identify any emerging issues before they escalate.
Use Filters
Filters make it easier to focus on the most important logs, such as errors or critical events, without having to sift through the entire log.
Archive Logs
Event logs can grow quickly. Make sure to regularly archive older logs and set up automatic log rotation to keep things manageable.
Implement Alerting
Automate alerts for critical or error events so you can address problems immediately, rather than waiting for a user to report them.
Maintain Log Integrity
Ensure that event logs are protected from tampering, as they play a key role in security auditing.
Conclusion
Event logs in Windows are far from just a bunch of system messages—they’re an invaluable resource for monitoring, troubleshooting, and securing your system. Whether you’re keeping an eye on your system’s health or hunting down a pesky issue, logs are key.
If you’re looking for a managed observability solution that simplifies all of this, Last9 is here to help.
We bring together metrics, logs, and traces into one unified view, making it easier for teams to connect the dots, stay on top of alerts, and troubleshoot more efficiently. Last9 integrates easily with tools like Prometheus and OpenTelemetry to enhance your monitoring experience.
Schedule a demo or try it for free to see how it works!
- Windows event logs store the information for hardware and software malfunction, including other successful operations.
- You can view the event logs with different severity across various categories in the Event Viewer (eventvwr.msc), or using the Reliability Monitor (Control Panel > System and Security > Security and Maintenance > Maintenance > View reliability history).
The Windows operating system logs and stores information about the actions performed on it, especially if any errors have occurred. This information is collected from the different Windows applications as well as the Windows components itself.
These errors are recorded in the location “C:\WINDOWS\system32\config\“. However, if you go on to this directory, you will find files that cannot be opened in any apps, and therefore, you won’t be able to view the error logs. For those purposes, the Windows OS includes two useful tools:
- The Windows Event Viewer, and
- The Reliability Monitor
These tools can be used to view and understand the different errors and warnings that occur on your computer. So if your apps keep crashing, or you keep experiencing Blue Screen of Death (BSoD) and you cannot understand why, you can resort to these tools to understand why the error has occurred and how you can mitigate it.
This guide discusses how to access the Event Viewer and the Reliability Monitor on a Windows computer, and how you can use them to understand the different error types and their causes.
Table of Contents
What are Windows Event Logs?
Event logs are files that contain structured information about the happenings of an event. These events can be errors, warnings, or simple operations. These files provide information about the different hardware and software-based operations on the system.
On a Windows computer, event logs are used to determine the cause of an error or a warning. These contain error codes and often an explanation for why something happened. For example, if the system crashes all of a sudden, Windows will generate a log explaining why it crashed.
Sometimes, the explanation is simple enough to resolve the issue. At other times, you may only be able to get a certain error code (eg. 0xC000021A) which doesn’t explain much on its own. However, you can search for this code on the internet and obtain detailed answers for the causes of the error and its possible fixes.
Event logs can contain the following information on a Windows computer:
- Log name: This is the category of the event log for which the log was generated. The different categories have been discussed below.
- Source: Name of the component or app that caused the event.
- Event ID: This is the identification number that helps administrators identify a specific logged event. This is usually the code that is used to further research the error that caused the logged event.
- Level (Type): This indicates the severity of the event log. These can be information, error, verbose, warning, or critical.
- User: Name of the user account who logged onto the computer when the event occurred.
- OpCode: When a program raises the event, it executes an activity or a certain point within an activity, and the OpCode defines a numeric value that identifies the particular activity.
- Event date/time (Logged): Indicates the date and time when the event occurred and when the log was generated.
- Task Category: This indicates what kind of recorded event log it is. To provide more details about the event, developers can include task categories in their apps if needed.
- Keywords: Event logs categorize events using keywords. These keywords help classify the type of event and provide additional context. One such common keyword is “classic”.
- Computer: Name of the computer logging the event.
Types and Categories of Windows Event Logs
If you are new to the event logs on a Windows computer, then it will be important for you to understand its types and categories. With this knowledge, you will be able to look for the right error log and understand it better.
Types/Level of event logs
Regardless of the category of an event log, there are 5 types of error logs, which are as follows:
- Information: Indicates that a service or application is running smoothly. For instance, the event will be recorded as an information event when a Windows Service is started successfully.
- Warning: These are insignificant incidents that raise the possibility of future problems. A warning event may be logged when your device is running on low disk space.
- Error: An error log, identified with a red exclamation mark, describes a serious problem that arises when a system is unable to operate as intended, such as when the operating system or an app crashes.
- Success Audit: Such type of event logs document a legitimate effort to obtain the security log through auditing. An effective login attempt, for instance, will be classified as a successful audit event.
- Failure Audit: These event logs show the security log’s audited security access failures, like not being able to access the network disc.
When reading the different event logs, we normally look for warnings or error logs, as those usually cause major issues with the system, such as the operating system crashing or resulting in BSoDs.
Categories of event logs
Other than the information about the different types of event logs, you must also understand the different categories of them. This information will let you know where to look for the event log (under which category).
- Application: Event logs regarding apps and software hosted on the computer get logged under this category. For example, an event log will be created if the Paint application or a game fails to launch.
- Security: Any events about the security of the system are stored under this category. Such events are recorded via the Windows auditing process. For example, if an unauthorized access attempt is made to the system, or a secure file deletion attempt is made, an event would be automatically registered.
- Setup: Events that occur during the Windows OS installation are recorded in the setup log. Setup events will also be registered on domain controllers relating to the Active Directory.
- System: Events about the system and its components are recorded in this category. For example, an error with the kernel will be recorded here.
- Forwarded Events: These are the event logs that have been forwarded from other devices on the network.
With this information, when an error occurs on your computer, you should be able to look under the right category and understand why it happened.
Now that you fully understand the use and benefits of event logs, let me show you how to access the event logs and make them useful.
How to view event logs on Windows
As mentioned earlier, you can access the event logs on a Windows computer using the Event Viewer, and the Reliability Monitor.
The Event Viewer can be used to access the different event categories discussed above and view all sorts of events. Whereas the Reliability Monitor provides a timeline of events that can be arranged in days and weeks. The latter focuses on system errors that may affect the reliability and performance of the system and is not as detailed as the Event Viewer.
View event logs with Event Viewer
To access the logged events in the Event Viewer, follow these steps:
-
Press the Windows key + R to launch the Run Command box.
-
Type in “eventvwr.msc” and press Enter to open the Event Viewer.
-
Expand “Windows Logs” from the left navigation pane.
-
Click on the event category that you want to access.
Open log event category -
Now, scroll through the logs in the middle pane and click on the one you need the information for.
Since there are too many logs to go through, you can apply a filter by performing these additional steps. To start, click “Filter Current Log” in the right pane.
Filter the logs -
In the Filter Current Log window, select the following elements to help you find a specific error log file:
- Logged: The duration to show the event logs for.
- Event level: The severity of the log event.
- [Optional] Event ID: If you are looking for a specific error log for which you already have the event ID.
Apply the event filters -
When done, click OK.
When the filters are applied, you can scroll through the event logs in the Event Manager, and double-click the one you want more information on.
I would also like to add that in Step 6 above, you can further narrow your search result by applying additional filters, such as a keyword, a user account name, etc.
Moreover, you can also use the “Custom View” option and filter certain types of event logs from different categories into one frame. To create a custom view, use these steps:
-
In the Event Viewer, click “Create Custom View” in the right pane.
Create a custom filter in Event Viewer -
In the “Create Custom View” window, select “By log” and then expand the drop-down menu in front of it.
-
In the drop-down menu, select the log categories that you want to view.
Select the event log categories to view -
Now select the event levels and click OK.
Create a custom view for event logs -
Now set a name for the custom view and click OK.
Assign a name to custom event view
After performing these steps, you should be able to view the shortlisted even logs directly under one category in the left pane.

In case you want to delete or edit the custom event category, simply right-click on it and select the respective option from the context menu.
View event logs with the Reliability Monitor
You can also use the Reliability Monitor to view the important error logs on your computer. Here is how to access and read the tool:
-
Press the Windows key + R to open the Run Command box.
-
Type in “control” and press Enter to launch the Control Panel.
-
Click “System and Security“.
-
Click “Security and Maintenance“.
-
Expand Maintenance.
Expand Maintenance -
Click “View Reliability History“.
Open Reliability Monitor -
Click on the day’s column for which you want to view the crash log.
Select the day to view the event logs for -
Double-click on the event in the bottom section of the Reliability Monitor to view more details.
Open the event log using the Reliability Monitor
After performing these steps, you should be able to see the complete details for the selected event log.

As you may find in the image above, the details here for the event log are somewhat different than the ones available inside the Event Viewer. However, you can use the error code to find more information about the event online.
Closing words
Understanding the crash and event logs is just as important as accessing them. There is no use in viewing the event logs if you cannot determine what they mean.
This detailed guide shows you exactly how to view and understand the system event logs and look for errors with different severity, inside different categories. You can also view them for specific days if you are not sure exactly when an error occurred.
Windows Event Log Files Explained – Log Types You Must Monitor. There’s no way around Windows event log files if you’re an IT specialist or a system admin. After all, knowing what goes on behind the scenes of Windows based systems and networks is essential to troubleshoot problems quickly and efficiently. Which only increases when you start getting into more complex structures like Active Directory domains.
But digging deep into all available logs can be overwhelming! So to make things easier for yourself, why not take this chance to go over the basics: how types of records work within the event logging system in different versions of Windows?
Let’s explore everything from what exactly happens behind the scenes in Windows log events to common problems with them and some best practices that are worth taking note of – whether you’re a beginner just starting your career as an IT professional or already have years of experience under your belt.
Shall we start the article blog about Windows Event Log Files Explained – Log Types You Must Monitor.
What is a Windows Event Log?
First of all, event logs are technical documents that keep track of significant events on your device, for example, when a user signs in or when an issue occurs in software. So, Windows keeps an event log of such occurrences. The information included in event logs may be useful for users experiencing problems with Windows or other applications.
Microsoft’s events log isn’t a file format like Linux MySQL. Hence you can’t open it in most code editors. Instead, an event log is a file in Microsoft Windows containing unique data called Windows events.
The Event Log System handles log management, event publication settings, and log activities in Windows. The Windows Event Log system provides a unique API for managing and maintaining event logs inside programs.
Initially released in Windows NT 3.1 in 1993, event tracking in Windows has been around for quite some time. The Application event log, the System event log, and the Security information and event log were preinstalled in this Windows version. Newer operating systems have over a hundred different types of Windows records, and additional event logs may be generated by and integrated with Windows logging by third-party apps.
Is There A Way To Look Into Past Events?
The Windows Event Manager or third party Windows activity monitors may be used to examine the system’s event logs. We advise utilizing our Event Log Manager program to manage your event logs effectively.
What is Windows Event Log Service?

As the name implies, Windows Event Log is a feature built into Windows that handles event logs and other related tasks. It allows for the recording of events, the retrieval of previously recorded events, the subscription to previously recorded events, the storage of previously recorded events, and the administration of event information.
Exhibiting data in both XHTML and text formats is helpful. The default behavior for this service is always to be running. It is not recommended that you turn off or pause this feature. Deactivating the Windows Event Log function might affect system safety and stability.
What is a Windows Application Event Log?
Activities tracked by the software are stored in the Application log. One use of the service log might be for database software to document a file issue. Designers of the software select whether actions warrant being recorded.
Hence, Microsoft SQL Server, for instance, keeps a record of memory related and backup related events. Since events might be recorded to a standalone executable log from various sources, analysing the log based on the event ID would be a mistake. Never disregard the significance of the event ID in combination with the event source. All programs do not use the Windows application event log.
Internet Explorer and PowerShell are two examples of such programs. These logs are indistinguishable from the standard Windows logs and may be seen in Event Manager and Event Log Finder. It is widespread knowledge that application logs are helpful to the service helpdesk.
What is a Windows System Event Log?

All in all, Logs created by Windows subsystems may be found in the System log. For instance, if a program or other network device fails to load at start-up, this is documented in the security log. Windows predefines the event categories that various systems will record.
Like an Application log, a system event log contains entries for events that originated from many places. Thus while examining the System log, it is essential to consider both the event ID and the origin. System logs are critical to computer programmers and professionals.
What is a Windows Security Event Log?
Login successes and failures, file and object creation, modification and deletion, and other resource management activities are all recorded in the Security log. What goes into the security log is entirely up to the managers’ discretion.
If you have login monitoring turned on, all efforts to log in will be logged. When crafting an audit plan, proceed with caution. For instance, Windows allows auditing NTFS drives, which means that each connection to an NTFS file is recorded as a separate event.
This may cause hundreds of occurrences every second, filling up the event log and slowing down the system. Keep in mind that only the desired files and directories will be audited by fine-tuning the audit authentication scheme. System administrators, security analysts, and investigators would be lost without access to comprehensive security records.
Windows Event Logs Types for Security

In general, event logs are categorized into a number of primary groups depending on the defective element. Events are recorded for various system elements, including the system itself, its security, the programs it hosts, and more. Some apps have a particular category for recording events rather than the standard Programs class.
1. Security Log:
2. Application Log:
Any action taken by an application is recorded in this log. This function is hardwired into the program and was decided upon before development began. For example, if the user encounters a problem when launching the app, the information will be logged in the application log.
3. File Replication Service Log:
An event log keeps track of everything that happens during remote access deployment. This log is restricted to network elements exclusively.
4. System Log:
The system software keeps a record of what happens in this kind. For instance, if a disk fails to boot up, such information will be stored in the System Logs.
5. DNS Server Log:
This log documents actions taken by the DNS server and name processing. This log is exclusively accessible by DNS servers.
6. Directory Service Log:
Activity logs are used to record instances of AD. This log is only accessible by DNS servers.
Up next we have Windows Event Logs use cases.
Applications/Use Cases of Windows Event Logs

Account Utilization
Domain Controller accounts with elevated privileges, like the domain admins and corporate controllers, need specific monitoring. In addition, you need to be certain that unauthorized users aren’t being added or removed from these categories in your system.
There should be a system in place to keep track of account bans. Brute force attacks are a common indicator of bad intent. It’s possible that these evil guys are attempting to predict a user’s password.
Limiting Access to Certain Programs
You need to have a set of authorized services and software. You should consider suspecting anything that doesn’t present on your list. As a result, the newest versions of Windows have two distinct mechanisms for managing programs:
- Microsoft Defender Device Guard.
- AppLocker.
These methods may function alone or in concert with one another. Device Guard is often regarded as the most complex to set up but also the safest. Due to this, it may be preferred by administrators over AppLocker. If you can compromise the Windows NT Kernel, you can easily get around AppLocker. When compared to other methods of protecting the Windows NT Kernel versus vulnerabilities, Device Guard is far superior.
Group Policy Failures
Your company relies on Group Policy Objects to set and implement its security standards. As a result, your system is at risk if the group rules you’ve established aren’t strictly adhered to. If this happens, it might be because an attacker is trying to block your system from implementing its rules so that they can replace them with their own.
It might, however, be a completely harmless event. It’s possible, for instance, that problems are occurring with the group policy server. No matter what, it is smart to keep an eye on your network regulations in case they reveal suspicious activity.
Randomized Approved Events and Audit Logs
If you find that any of your activities have mysteriously vanished, malicious actors have probably gained access to systems or devices. On the other hand, it’s possible that the bad people are attempting to cover up their nefarious actions by erasing occurrences. It’s worth noting right now that, under usual conditions, files are not deleted.
Upgrades to Windows
Similar to the client OS, Windows Server has to be kept up-to-date. These upgrades are necessary since they frequently include critical bug fixes for the system. In the event that Windows updates perform poorly to install, your machine may become susceptible.
Therefore, you must examine the providers of the System network’s Window Update Client and Maintenance event. You can also construct a controlled view based on these event triggers if you choose. First, however, you should check that there aren’t any warnings or informational events that point to failed Windows Updates.
Software and Service Setup
It’s also possible that your server often receives new versions of its operating system, applications, and services. Yet, new setups happen on a daily basis. This is dependent on the server’s lifespan and level of activity.
Installs, upgrades, and upgrades might be requested every day for newly commissioned systems. However, harmful behaviour conducted by a malicious attacker may be indicated by unusual software and provider events.
Internet Protection Service for Windows
Windows Firewall is turned on by standard. With this security measure in place, you can be certain that your servers and customers are safe inside your own private network.
As a result, it’s as critical to your network’s security as any firewalls you may have. This means you need to make sure your firewall is operational and verify whether or not any changes or updates have been made to the condition or the regulations.
Interruption in Application
Most software eventually malfunctions. On the other hand, they might be a sign of a malicious assault in which a hacker attempts to cause the system to shut down without user intervention. The Windows Error Notification, Application Failure, and Pause events may all be found in the event logs, so users or their network manager should check them often.
Thank you for reading Windows Event Log Files Explained – Log Types You Must Monitor. We shall conclude this article blog.
Windows Event Log Files Explained — Log Types You Must Monitor Conclusion
In addition to the popular log types, there are a plenty of other business systems and security technologies that generate logs. There might be security implications for all of them. However, it is crucial to classify logs for analytical tracking since many businesses have minimal security personnel.
Events like alerts, faults, and malfunctions should be of particular importance. That there is an issue is suggested by all of these factors. In extreme cases, they might indicate an assault or data breach.
You have to have a plan for analysing and auditing events in your event logs, including how to decide which events to set, how important they are, when to get notifications, and how those notifications should be sent.
To read more about our monitoring section, please navigate to our blog here.