This is how to easily install ADK and MDT in Windows Server 2016 for Windows Deployment. The current version of Microsoft Deployment Toolkit is MDT 2013 update 1. MDT is a solution accelerator for operating system and application deployment. MDT supports the deployment of client operating systems and server operating systems. In this post, we are going to show you how to install and configure MDT and ADK for Windows 10 in Windows Server 2016 which works the same as Windows Server 2012 R2.
The methods of installation and configuration of all Microsoft Deployment Tool kits are the same. So don’t worry, just download the MDT required components ADK for Windows 10 or for older Windows and start installing.
You might need to read for Windows deployment Services:
- How to install Windows Deployment Service WDS In Windows Server 2012 R2?
- Configure Windows Deployment Services on Server 2012 R2
- Deploying Windows 10 Using WDS Server 2012 R2
Download and Install ADK and MDT
The first kit we need to download is the Windows ADK for Windows 10. The second one is the latest update of the Microsoft deployment tool kit. Download the Microsoft deployment tool kit update 1 files from the Microsoft website. Always try to download the latest version of MDT.
In our practicing lab, we are using MDT 2013 update 1 which supports Windows 10 and Windows Server Server 2016. You can download Windows ADK for Windows 10 with two methods. Download and Install at the same time or download all components in a separate Windows and move it to Windows Server. So I have selected the second one. First, download all Windows ADK for Windows 10 and now try to install it.
1. Let’s download all components of Windows ADK for Windows 10 and then install it.
-
- Download the Windows ADK for Windows 10 and run the setup.
2. Select the Download the Windows Assessment and Deployment Kit – Windows 10 for installation on a separate computer and Browns to specify the path then click Next.
3. It’s a test lab so select No and click Next. On the license terms and agreement page click Accept to accept the Windows Kits privacy.
4. It is almost 3 and a half GB in size. When the download is complete successfully, move or copy files to Windows Server 2016 then run the adksetup file to install it.
5. Specify a location or click Next to select the default location. Then on the Windows Kits privacy page select No and on the license terms and agreement page Accept.
6. Now select the features you want to install. Don’t select unnecessary features. Click Next to install it.
7. It will take a few minutes to complete. When it is finished, close the page.
Now the Windows ADK for Windows 10 is installed successfully in Windows Server 2016. The next step is to install the Microsoft Deployment tool kit.
How to Download and Install MDT?
So the installation of Windows ADK for Windows 10 has finished successfully. Now try to download and install Microsoft Deployment tool kit update 1.
- Microsoft Deployment Toolkit (MDT) 2013 Update 1 and run the setup.
1. Run the downloaded Microsoft deployment tool kit setup file and click Next.
2. Select I accept the terms in the license agreement and click Next.
3. Click Next and do nothing on this page because we need tools and documents.
4. For testing lab select I don’t want to join the program at this time and click Next.
5. Click Install to start the installation. Let the installation will be finished. Finally, click Finish to close the page.
Yes, that’s it. The Microsoft deployment tool kit was also installed successfully. If you are faced with some errors or problems during the installation, try to search for the title on Google or comment to us through this post.
6. Now go to Windows Server 2016 start menu and run the Deployment Workbench.
Here is the Windows deployment Workbench. It is ready for Windows Deployment and Application Deployment.
Now the Microsoft Deployment Toolkit is ready for configuration and deploying new operating systems and Applications.
It’s time to configure the MDT and start deploying Windows 10 with MDT. Continue the article about deploying Windows 10 using MDT in Windows Server 2016. So that’s all you need to install ADK and MDT for your Windows Deployment Server in Windows Server 2016.

Download the Windows 10 ADK to match the version of SCCM you are installing. For Windows 10 1803, you will need AD 1803 and SCCM 1803:
https://docs.microsoft.com/en-us/windows-hardware/get-started/adk-install
- Launch ADKSetup.exe
-
At the Specify Location screen, accept the default installation path and click <Next>:
-
Select ‘No’ to ‘Send anonymous usage data’ and click <Next>:
- At the ‘License Agreement’ screen click <Accept>.
-
At the ‘Select the feature you want to install’ screen, tick ‘Deployment Tools’, ‘Windows Preinstallation Environment’ and ‘User State Migration Tool’ – untick all other boxes and click <Install>:
- Click <Close> once complete.
Here is a step-by-step quick guide on building the perfect Windows Server 2016 reference image. This guide is divided in two parts: The first part covers how to create a Windows Server 2016 reference image in just a few minutes using offline servicing. The quick-and-dirty method. The second part is about creating a Windows Server 2016 reference image using MDT 8443. The SHINY method.
Creating a Windows Server 2016 reference image using offline servicing (and PowerShell)
If you need to create a Windows Server 2016 reference image very quickly, containing only the latest cumulative update (CU) and .NET Framework 3.5. You can use the below PowerShell script to do so. This script assumes you have downloaded the Windows Server 2016 ISO and KB3201845 to C:\Setup.
Note: KB3201845 is just an example with the December 2016 CU, please download the latest CU and update the script.
Download the Create-WS2016RefImage.ps1 script from GitHub: http://github.com/DeploymentResearch/DRFiles/blob/master/Scripts/Create-WS2016RefImage.ps1
Creating a Windows Server 2016 reference image using MDT 8443
Why using MDT to create the reference image instead of PowerShell? Well, you get so many more options, you can add components that cannot be serviced offline like Visual C++ runtimes, and when using a build and capture process, all components can be easily updated. Also, unlike using offline servicing, when using a build and capture process, all components are completely installed, instead of just staged in the image.
MDT 8443 can be installed either on a file server, or on your own laptop, but in this scenario I use a file server named MDT01. MDT 8443 requires Windows ADK 10, and I recommend using Windows ADK 10 v1607.
In this guide I also assume that you have a local WSUS server in your network, to which you have approved Windows Server 2016 updates, Feature Packs (to get Microsoft .NET Framework updates) and Developer Tools, Runtimes and Redistributables / Visual Studio* (to get updates to Visual C++ runtimes).
Note: If you want to build a Windows Server 2016 reference image for SCVMM 2016, simply follow this guide to get the WIM file, and then use the Convert-WindowsImage.ps1 script on TechNet Script Center / Gallery to convert it to a VHD or VHDX file for VMM.
For this guide you need the following software.
- Windows Server 2016.
- Windows ADK 10 v1607, here is the direct download link. For more info, see the Windows ADK 10 page on MSDN:
- MDT 8443
- Visual C++ runtimes (2005,2008,2010,2012,2013 and 2015) available on Microsoft Download Center.
- Visual C++ runtimes install wrapper (Optional, but helpful)
Step-by-Step Guide
The entire process for creating a Windows Server 2016 image using MDT 8443 takes about 45 minutes, fully automated. The initial setup of the solution takes about 30 – 45 minutes if done manually, and about 10 minutes if scripted. This guide covers the following eight steps:
- Step 1 – Install Windows 10 ADK v1607 and MDT 8443
- Step 2 – Create the MDT Build Lab Deployment Share
- Step 3 – Import the Windows Server 2016 operating system
- Step 4 – Import Packages (KB3201845), or the latest Windows Server 2016 CU (recommended)
- Step 5 – Add applications (Optional)
- Step 6 – Create the MDT Task Sequence
- Step 7 – Configure the deployment share
- Step 8 – Create Windows Reference Images
Step 1 – Install Windows ADK 10 v1607 and MDT 8443
- On MDT01, install Windows 10 ADK v1607, and select the following components:
- Deployment Tools
- Windows Preinstallation Environment (Windows PE)
- Imaging and Configuration Designer (ICD)
- User State Migration Tool (USMT

Windows ADK 10 v1607 Setup on Windows Server 2016. When started on an older server, you have fewer options, for example UE-V and App-V are missing.
2. Install MDT 8443 using the default settings.

Installing MDT 8443.
- On MDT01, using the Deployment Workbench (available on the start screen), right-click Deployment Shares and select New Deployment Share. Use the following settings for the New Deployment Share Wizard (my data volume on MDT01 is E:)
a. Deployment share path: E:\MDTBuildLab
b. Share name: MDTBuildLab$
c. Deployment share description: MDT Build Lab
d. Options:
2. Once the deployment share is created you also want to relax the security a bit. MDT locks it down to hard by default. Use the following PowerShell script to set some better permissions:
# Check for elevation
Write-Host "Checking for elevation"
If (-NOT ([Security.Principal.WindowsPrincipal] [Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole(`
[Security.Principal.WindowsBuiltInRole] "Administrator"))
{
Write-Warning "Oupps, you need to run this script from an elevated PowerShell prompt!`nPlease start the PowerShell prompt as an Administrator and re-run the script."
Write-Warning "Aborting script..."
Break
}
# Configure NTFS Permissions for the MDT Build Lab deployment share
$DeploymentShareNTFS = "E:\MDTBuildLab"
icacls $DeploymentShareNTFS /grant '"VIAMONSTRA\MDT_BA":(OI)(CI)(RX)'
icacls $DeploymentShareNTFS /grant '"Administrators":(OI)(CI)(F)'
icacls $DeploymentShareNTFS /grant '"SYSTEM":(OI)(CI)(F)'
icacls "$DeploymentShareNTFS\Captures" /grant '"VIAMONSTRA\MDT_BA":(OI)(CI)(M)'
# Configure Sharing Permissions for the MDT Build Lab deployment share
$DeploymentShare = "MDTBuildLab$"
Grant-SmbShareAccess -Name $DeploymentShare -AccountName "EVERYONE" -AccessRight Change -Force
Revoke-SmbShareAccess -Name $DeploymentShare -AccountName "CREATOR OWNER" -ForceStep 3 – Import the Windows Server 2016 operating system
- On MDT01, mount the Windows Server 2016.iso media (or whatever you named it). On my server it was mounted to the D: drive.
- Using the Deployment Workbench, expand the Deployment Shares node, expand MDT Build Lab, select the Operating Systems node and create a folder named Windows Server 2016.
- Right-click the Windows Server 2016 node, and select Import Operating System. Use the following settings for the Import Operating System Wizard.
- Full set of source files
- Source directory: D:\
- Destination directory name: WS2016
- After adding the operating system, using the Deployment Workbench, in the Windows Server 2016 node, change the operating system names to the following:
Windows Server 2016 Datacenter
Windows Server 2016 Datacenter Core
Windows Server 2016 Standard
Windows Server 2016 Standard Core

The Windows Server 2016 operating system imported to deployment workbench.
Step 4 – Import Packages
In order for having Windows Server 2016 somewhat up to date, and to use a recent Windows Update agent, you should offline service the latest cumulative update (KB3201845 in this case) into the image. In MDT that is done by adding it as a package in the Deployment Workbench, and create a selection profile for Windows Server 2016.
- Download KB3201845 or a later Windows Server 2016 CU (recommended), and save it in C:\Setup\Windows Server 2016 Updates on MDT01.
- On MDT01, using the Deployment Workbench, expand Deployment Shares / MDT Build Lab / Packages and create a folder named Windows Server 2016.
- In the Windows Windows Server 2016 folder, right-click and select Import OS Packages. Point to the C:\Setup\Windows Server 2016 Updates folder.
- Expand the Advanced Configuration node, and create a selection profile named Windows Server 2016. When creating the selection profile, select the Packages / Windows Server 2016 folder.

The KB3201845 package imported into the Deployment Workbench.
Step 5 – Add applications
Not a hard requirement, but it make sense to add at least the various Visual C++ runtimes to your reference because quite frankly, you are installing Windows Server 2016 to run apps, and many apps are depending on one or more of these runtimes. As you probably know, there are x86 and x64 versions of the runtimes, and for Windows Server 2016, you need both.
For the Visual C++ runtimes, you make the install a bit easier by using a VBScript wrapper that installs all of them.
- On MDT01, extract the Visual C++ runtimes install wrapper to C:\Setup.
- Download each runtime from Microsoft Download Center, and copy to the corresponding folder in C:\Setup\Install – Microsoft Visual C++ – x86-x64\source.

- Using the Deployment Workbench, expand Deployment Shares / MDT Build Lab / Applications and create a folder named Microsoft.
- Right-click the Microsoft folder, and select New Application. Use the following settings for the New Application Wizard:
a. Application with source files
b. Publisher:
c. Application name: Install – Microsoft Visual C++ – x86-x64
d. Version:
e. Source Directory: C:SetupInstall – Microsoft Visual C++ – x86-x64
f. Specify the name of the directory that should be created: Install – Microsoft Visual C++ – x86-x64
g. Command Line: cscript Install-MicrosoftVisualC++x86x64.wsf
h. Working directory:
Step 6 – Create and Configure the MDT Task Sequence, and edit Unattend.xml
- On MDT01, using the Deployment Workbench, in the MDT Build Lab deployment share, select the Task Sequences node, and create a folder named Windows Server 2016.
- Expand the Task Sequences node, right-click on the Windows Server 2016 node, and select New Task Sequence. Use the following settings for the New Task Sequence Wizard:
- Task sequence ID: REFWS2016-001
- Task sequence name: Windows Server 2016 Standard
- Task sequence comments: Reference Build
- Template: Standard Client Task Sequence
- Select OS: Windows Server 2016 Standard
- Specify Product Key: Do not specify a product key at this time
- Full Name: ViaMonstra
- Organization: ViaMonstra
- Internet Explorer home page: about:blank
- Do not specify an Administrator password at this time
- Edit the task sequence, by navigating to the Task Sequences / Windows Server 2016 folder, right-click the Windows Server 2016 Standard task sequence, and select Properties.
- On the Task Sequence tab, configure the Windows Server 2016 Standard task sequence with the following settings:
- Preinstall. Configure the Apply Patches action to use the Windows Server 2016 Standard selection profile.
- State Restore. After the Tattoo action, add a new Group action with the following setting:
Name: Custom Tasks (Pre-Windows Update)
- State Restore. Enable the Windows Update (Pre-Application Installation) action.
- State Restore. Enable the Windows Update (Post-Application Installation) action.
- State Restore. After the Windows Update (Post-Application Installation) action, rename the existing Custom Tasks group to Custom Tasks (Post-Windows Update).
- State Restore / Custom Tasks (Pre-Windows Update). Add a new Install Roles and Features action with the following settings:
Name: Install – Microsoft NET Framework 3.5.1Select the operating system for which roles are to be installed: Windows Server 2016 Standard Select the roles and features that should be installed: .NET Framework 3.5 (includes .NET 2.0 and 3.0)
- State Restore – Custom Tasks (Pre-Windows Update). After the Install – Microsoft NET Framework 3.5.1 action, add a new Install Application action with the following settings:
Name: Install – Visual C++ 2005 SP1 – x86-x64
Install a Single Application: Install – Visual C++ 2005 SP1 – x86-x64
- After the Install – Microsoft Visual C++ 2015 – x86-x64 action, add a Computer Restart action.
- Click OK.

Task Sequence configured for the reference image build and capture.
5. Edit the task sequence, by navigating to the Task Sequences / Windows Server 2016 folder, right-click the Windows Windows Server 2016 Standard task sequence, and select Properties.
6. In the OS Info tab, click Edit Unattend.xml. A catalog file will now be generated, and then Windows System Image Manager (WSIM) will start.
7. In WSIM, in the Answer File pane, expand 7 oobeSystem / amd64_Microsoft-Windows-Shell-Setup_neutral / OOBE, and then set ProtectYourPC to 3.

Disabling automatic update in the Unattend.xml. Will be handled by the Windows Update action in the task sequence instead.
Since you have added operating system packages (updates) to MDT, you need to configure your deployment share not to add them to your boot image.
In the MDT Build Lab deployment share properties, in the Windows PE tab, select the x64 platform, and in the Drivers and Patches tab, select the Nothing selection profile, and select the Include all drivers from the selection profile option.

Configuring the deployment share not to add any imported packages to the boot image.
Then, to configure the deployment settings, you modify the two rules files (Bootstrap.ini and CustomSettings.ini). You can do the either via the MDT Build Lab deployment share properties, or directly in the file system, in the E:MDTBuildLabControl folder. Below you find the configurations I used in this guide.
Note: In my environment, my WSUS server is named WSUS01, and I’m using the default WSUS port in Windows Server 2016 (and Windows Server 2012 R2) which is 8530.
Bootstrap.ini
[Settings]
Priority=Default
[Default]
DeployRoot=\\MDT01\MDTBuildLab$
UserDomain=VIAMONSTRA
UserID=MDT_BA
UserPassword=P@ssw0rd
SkipBDDWelcome=YESCustomSettings.ini
[Settings]
Priority=Default
[Default]
_SMSTSORGNAME=ViaMonstra
UserDataLocation=NONE
ComputerBackupLocation=NETWORK
DoCapture=YES
OSInstall=Y
AdminPassword=P@ssw0rd
TimeZoneName=Pacific Standard Time
JoinWorkgroup=WORKGROUP
HideShell=NO
FinishAction=SHUTDOWN
WSUSServer=http://wsus01.corp.viamonstra.com:8530
ApplyGPOPack=NO
BackupShare=\\MDT01\MDTBuildLab$
BackupDir=Captures
BackupFile=%TaskSequenceID%_#month(date) & "-" & day(date) & "-" & year(date)#.wim
SkipAdminPassword=YES
SkipProductKey=YES
SkipComputerName=YES
SkipDomainMembership=YES
SkipUserData=YES
SkipLocaleSelection=YES
SkipTaskSequence=NO
SkipTimeZone=YES
SkipApplications=YES
SkipBitLocker=YES
SkipSummary=YES
SkipRoles=YES
SkipCapture=NO
SkipFinalSummary=YES- On MDT01 in the E:L\abfiles\LTI Support File\sMDT Build Lab\Control folder, modify the Bootstrap.ini and CustomSettings.ini per the above examples.
- Using the Deployment Workbench, right-click the MDT Build Lab deployment share and select Properties.
- In the Windows PE tab, in the Platform dropdown list, make sure x86 is selected. Then in the Lite Touch Boot Image Settings area, configure the following settings:
- Image description: MDT Build Lab x86
- ISO file name: MDT Build Lab x86.iso
- In the Windows PE tab, in the Platform dropdown list, make sure x64 is selected. Then in the Lite Touch Boot Image Settings area, configure the following settings:
- Image description: MDT Build Lab x64
- ISO file name: MDT Build Lab x64.iso
- Click OK.
- Update the deployment share, by right-clicking the MDT Build Lab deployment share and select Update Deployment Share. Use the default Options for the Update Deployment Share wizard.
- In the Windows PE tab, in the Platform dropdown list, make sure x86 is selected. Then in the Lite Touch Boot Image Settings area, configure the following settings:

The contents of the E:MDTBuildLabBoot folder after updating the deployment share.
Step 8 – Create Windows Reference Images
Create a Windows Server 2016 Reference WIM Image, fully automated.
- On MDT01, copy the E:\MDTBuildLab\Boot\MDT Build Lab x64.iso file to your VMware or Hyper-V machine.
- Create a virtual machine named REF001, assign it two vCPUs and 2 GB RAM. Then mount MDT Build Lab x64.iso on the virtual machine.
- Start the REF001 virtual machine, and allow it to boot. Then complete the Deployment Wizard using the below settings:
- Select a task sequence to execute on this computer: Windows Server 2016 Standard
- Specify whether to capture an image: Capture an image of this reference computer.
- Location:
- File name:
The task sequence will now do the following:
- Install the Windows Server 2016 operating system.
- Install the added applications, roles, and features.
- Stage WinPE on the local disk.
- Run Sysprep and reboot into WinPE.
- Capture the Windows Server 2016 installation to a WIM file.

MDT 8443 capturing a Windows Server 2016 Image.
Written by Johan Arwidmark
Businesses that need to deploy Windows in a larger environment often require customization before they can go about their operations and processes. This large-scale deployment is carried out by IT professionals and system administrators on many computers using the toolset, known as the Windows Assessment and Deployment Kit, or simply, Windows ADK.
Microsoft Windows ADK is a collection of tools that you can combine to prepare, assess, and launch image-based large-scale Windows deployments. These tools are also used to test the operating system’s quality and performance, as well as the applications running on it.
The Windows Assessment and Deployment Kit was earlier known as the Windows Automated Installation Kit (WAIK).
Windows ADK can be deployed on a broad range of devices, such as desktops, notebooks, Internet of Things (IoT) devices, etc. This toolkit works across platforms that work with devices with and without screens.
Windows ADK was first introduced in Windows Vista and since then has always been available in the latest Windows operating systems. The tools currently available in Windows ADK have varied through the years, but currently, they include the following:
- Windows System Image Manager
- Windows Preinstallation Environment (WinPE)
- Deployment Image Servicing and Management tool (DISM)
The key advantage of using Windows ADK for IT teams is to apply different tools to test software, drivers, and hardware compatibility before finally moving to Windows 11 or 10.
The Application Compatibility Toolkit, for instance, lets developers and IT professionals test how 32 and 64-bit Windows applications work on a new operating system before the final installation. IT admins can also use Windows ADK to automate large-scale deployments of Windows.
Download Windows 10 and 11 ADK Versions
On a high level, Windows ADK has two different formats, which have their own versions. One format is reserved for Windows Insider Preview users. The other format is available publicly and can be downloaded via the Windows ADK page on Microsoft’s website.
The variant available publicly is usually around 2 MB in size and comes in different versions, where each new release of Windows ADK involves new features and product enhancements.
If you want to know about the version history, take a look at the list below:
| Windows ADK Versions | Download Links |
| Windows ADK for Windows 11 22H2 | Download ADK Download WinPE Addon |
| Windows ADK for Windows 11 21H2 | Download ADK Download WinPE Addon |
| Windows ADK for Windows 10 version 22H2 | Download ADK Download WinPE Addon |
| Windows ADK for Windows 10 version 21H2 | Download ADK Download WinPE Addon |
| Windows ADK for Windows 10 version 21H1 | Download ADK Download WinPE Addon |
| Windows ADK for Windows 10 version 20H2 | Download ADK Download WinPC Addon |
| Windows ADK for Windows 10 version 2004 | Download ADK Download WinPE Addon |
| Windows ADK for Windows 10 version 1909 | Download ADK Download WinPE Addon |
| Windows ADK for Windows 10 version 1903 | Download ADK Download WinPE Addon |
| Windows ADK for Windows 10 version 1809 | Download ADK Download WinPE Addon |
| Windows ADK for Windows 10 version 1803 | Download ADK |
| Windows ADK for Windows 10 version 1709 | Download ADK |
| Windows ADK for Windows 10 version 1703 | Download ADK |
| Windows ADK for Windows 10 version 1607 | Download ADK |
| Windows ADK for Windows Insider Preview | Download ADK |
The Windows Preinstallation Environment (WinPE) comes as a separate download from the Assessment and Deployment Kit (ADK), before Windows 10 version 1809. To add Windows PE to your ADK installation, you need to download and install the Windows PE add-on after installing the ADK.
When it comes to features, Windows 10 ADK allows you to select specific features at the time of installation. You can pick and choose the exact features you want to include in the toolkit. The options include:
- Application Compatibility Tools
- Deployment Tools
- Windows Preinstallation Environment (Windows PE)
- Imaging and Configuration Designer (ICD)
- Configuration Designer
- User State Migration Tool (USMT)
- Volume Activation Management Tool (VAMT)
- Windows Performance Toolkit
- Windows Assessment Toolkit
- Microsoft User Experience Virtualization (UE-V)
- Application Virtualization Sequencer (App-V)
- Microsoft Application Virtualization Auto Sequencer (App-V)
- Media experience Analyzer
In general, these features let you perform the following functions:
- Add product branding, applications, along with settings
- Keep Windows up to date with the latest updates, language packs, and drivers
- Look for and identify application compatibility
- Perform user data migration between Windows installations
- Manage bulk activation of Windows
How to Install Windows ADK
Since you can only install one version of Windows ADK at a time, you will need to uninstall any existing ADK installation before installing the new one.

Otherwise, you will need to install the new ADK using the command line for multiple ADK versions working on the same computer.
Follow these steps to install Windows ADK using the traditional method:
-
Download the correct ADK version from above.
-
Run the “adksetup.exe” file to start the installation.
-
Now select “Download the Windows Assessment and Deployment Kit for installation on a separate computer” and click Next.
Install ADK on a separate computer -
Select either Yes or No for Windows Kits Privacy and click Next.
Select privacy preferences -
Click Accept to agree to the licensing terms.
Accept license agreement The download process will now start.
-
Once downloaded, close the wizard.
Close the wizard
After the download process is complete, you can move the downloaded files onto the computer on which you want to install Windows ADK.
If you wish to install it on the current computer, then you must select the first option “Install the Windows Assessment and Deployment Kit on this computer” in Step 3 above and then select the components to install.

Download and Install WinPE Add-On
As discussed earlier in the article, starting with Windows 10 ADK version 1809, WinPE is no longer part of the ADK tool. If you wish to get WinPE, follow these steps to download and install the add-on:
Note: The minimum estimated disk space required is 6.0 GB for the WinPE add-on. Hence, it may take longer for the installation to finish than the ADK. The package includes Windows PE(x86), Windows PE (AMD64), Windows PE (ARM), and Windows PE (ARM64).
-
Begin by downloading the WinPE setup file from the links given above for your respective OS version.
-
Run the downloaded “adkwinpesetup.exe” file.
-
The rest of the process is the same as Windows ADK installation.
Windows ADK Validation
To confirm the Windows ADK installation on a device, follow these steps:
-
Open the Programs and Feature applet by typing in “appwiz.cpl” in the Run Command box.
Open Programs and Features -
Check that Windows ADK and Windows PE have been installed.
Windows ADK has been installed
Conclusion
In order to deploy Windows OS on a large scale, you need a Windows Assessment and Deployment Kit. This article covers the basics of the Windows ADK toolkit, its download links directly from Microsoft, and how to install it.
You can also use this tool and its add-on in conjunction with Windows Deployment Server to level up your automation and operations.
[Update from Microsoft (May 30th, 2017): Good news! Microsoft has released a fix to replace the drivers signed with old certificates with newly signed drivers. This should fix any unsigned driver errors in the installation of ADK. You can read the update and download the files and instructions here. In even betters news, Keith Garner has written and shared a script online that will automate the process of replacing the drivers that Microsoft outlines. His script can be found here.]
As quickly as we are moving to get clients upgraded to Windows 10, Microsoft is moving just as quickly, recently releasing the Creators Update 1703. If you are looking to install Windows Assessment and Deployment Kit (ADK) for Windows 10 version 1703 on a Server 2016 Hyper-V virtual machine, you may encounter the following roadblock. The first, albeit vague, warning that something is wrong is during the installation of ADK, when the Program Compatibility Assistant prompt is presented stating that an unsigned driver could not be installed.
Once you close out of the prompt, the installation completes with no additional suggestion of a problem. In fact, you won’t be aware of the problem until you are in Microsoft Deployment Toolkit Workbench and ready to generate your first WinPE media. The process will fail with the error “Unable to mount the WIM, so the update process cannot continue”.
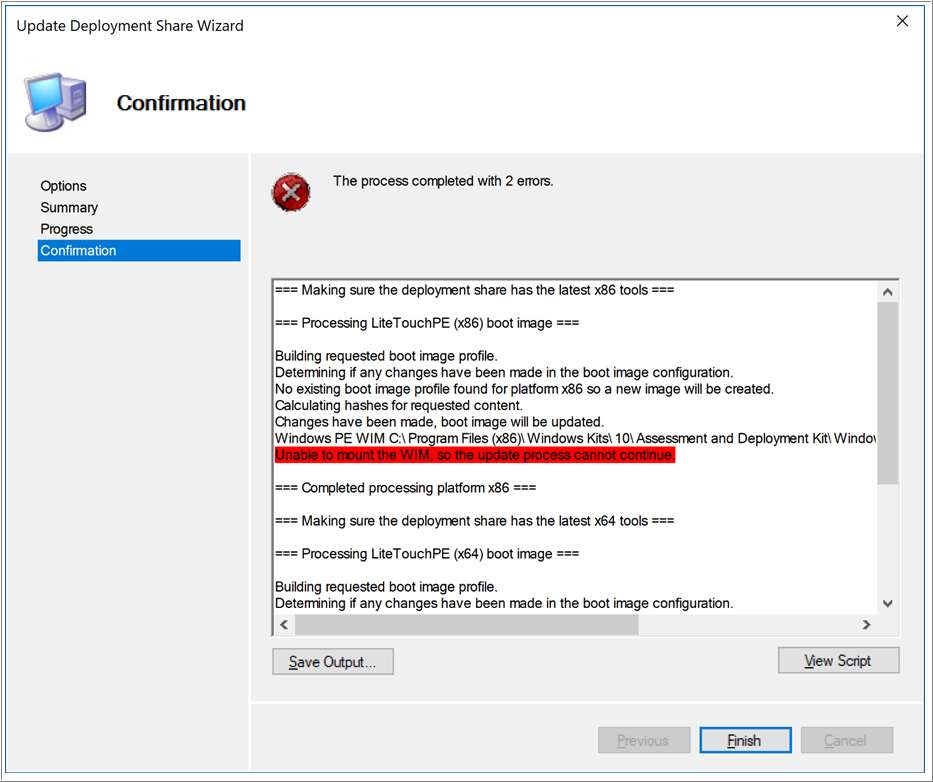
A quick Internet search led us to a TechNet article explaining that some of the files in the ADK installer are signed with an old certificate. Because Hyper-V machines are automatically configured to enable Secure Boot, these unsigned drivers are blocked from installation. The winmount.sys driver is one of those that are blocked, which prevents the generation of boot images. The article discusses using an older version of ADK or disabling Secure Boot as possible workarounds, but neither of these are ideal. We disabled Secure Boot as our workaround, but luckily a day later Michael Niehaus posted this article, explaining that we can switch out the unsigned driver with a newly signed driver already in the OS.
Here is how to do this:
1. Launch regedit.exe
2. Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WIMMount
3. Select the ImagePath key and edit it
4. Replace the value with “system32\drivers\wimmount.sys”
Once this key is updated you can now go back into MDT and successfully generate a boot image. Happy imaging!








