What is Password Policy?
Password policy is the policy which is used to restrict some credentials on windows server 2016 and previous versions of Server 2012, 2008 and 2003.
A password policy is a set of rules designed to enhance computer security by encouraging users to employ strong passwords and use them properly. A password policy is often part of an organisation’s official regulations and may be taught as part of security awareness training. The password policy may either be advisory or mandated by technical means. Some governments have national authentication frameworks that define requirements for user authentication to government services, including requirements for passwords. So follow the under instructions to know how to configure password policy with windows server 2016. “Wikipedia”
How to Configure Password Policies with Windows Server 2016?
You can open up Group Policy Management Editor into three various ways.
First Method: press windows key and type control panel and now select administrative tools and then select local security policy. A new window will pop up, click account policies, Password Policy. Here you will see about six policies. If you don’t want to use the graphical way just type gpedit.msc on the RUN window then hit enter. Now go to this path. Computer Configuration/Windows Settings/Security Settings/Password Policy.
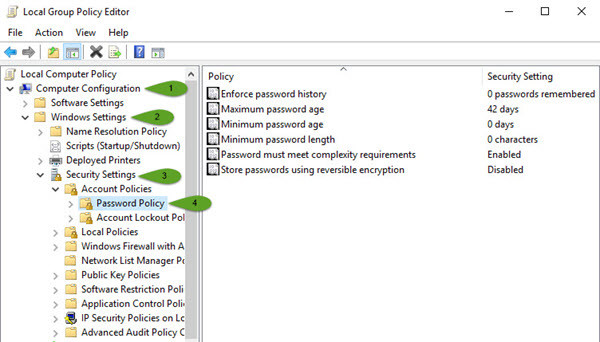
Local Group Policy Editor
Second Method: If you don’t want to use the graphical way just type gpedit.msc on the RUN window then hit enter. Now go to this path. Computer Configuration>Windows Settings>Security Settings>Password Policy.
Group Policy Editor
Third Method: Open Server Manager and click on Tools. Scroll down until you see the GPO (Group Policy Management). Right, click on the Domain then choose Edit. Now you will see the same window as before. Go to Computer Configuration> Windows Settings> Security Settings> Password Policy.
These were three different ways that you can apply password policy on the network computers.
What is Enforce Password History?
Enforce password history is the policy that doesn’t allow the users to use the same password for many times. For example, Once your Device password is Admin, and for the next time, you can’t use this password for login on your computer. After some months or year, it may expire. When it is expired, so you must use another password. Here I have set it to 10 times. It means that I can’t use my old password less than 10 times. In ten times, I must use a different password. After 10 times, I can use my first password. For more information, look at the chart below.
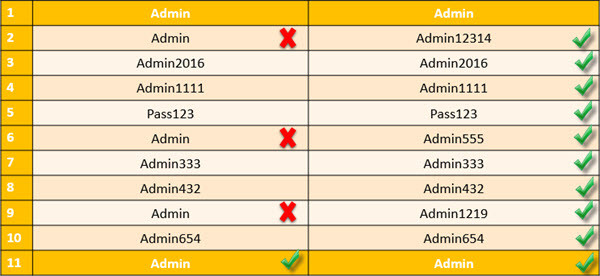
Enforce Password History rules
What is Maximum password Age?
This security setting determines the time in days that a password can be used before the system requires the user to change it. You can set passwords to expire after several days between 1 to 999, or you can specify that passwords never expire by setting the number of days to 0 if the maximum password age is between 1 and 999 days. The minimum password age must be less than the maximum password age if the maximum password age is set to 0. The minimum password age can be any value between 0 and 998 days.
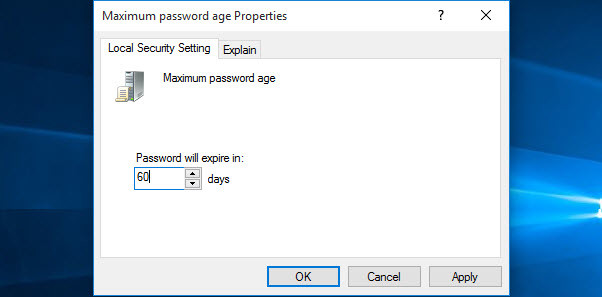
Maximum Password Age
Note: It is a security best practice to have passwords expire every 30 to 90 days, depending on your environment. This way, an attacker has a limited amount of time to crack a user’s password and have access to your network resources.
What is the Minimum Password Age?
The minimum password age must be less than the maximum password age unless the maximum password age is set to 0, indicating that passwords will never expire. If the maximum password age is set to 0, the minimum password age can be set to any value between 0 to 998. It’s vital that you have to use the minimum password age. If you don’t use, the user may cycle the password history till they get their old favourite password. If you set the minimum password age, so they will not change their password quickly.
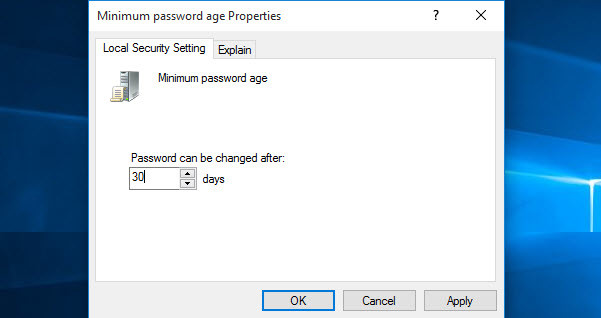
Minimum Password Age
What is the Minimum Password Length?
This is security setting determines the least number of characters that a password for a user account may contain. You can set a value of between 1 and 14 characters, or establish that no password is required by setting the number of characters to 0. Here I have set up to 8 characters. Mostly you see this policy on websites or social accounts.
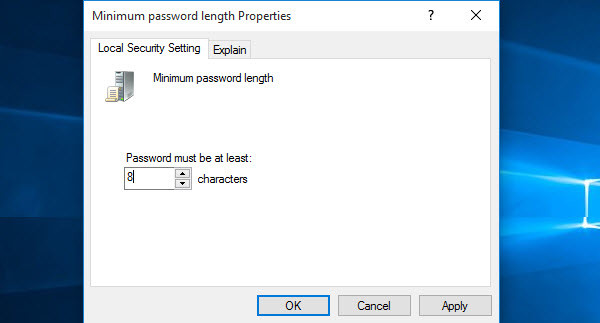
Minimum Password Length
What are Password Complexity Requirements?
If this policy is enabled, passwords must meet the following minimum requirements.
- Be at least six characters in length
- Contain characters from three of the following four categories
- English uppercase letters (A through Z)
- English Lowercase letters (a through z)
- Base 10 digit (0 through 9)
- Non-alphabetic characters ( !,@,#,$,%&,*)
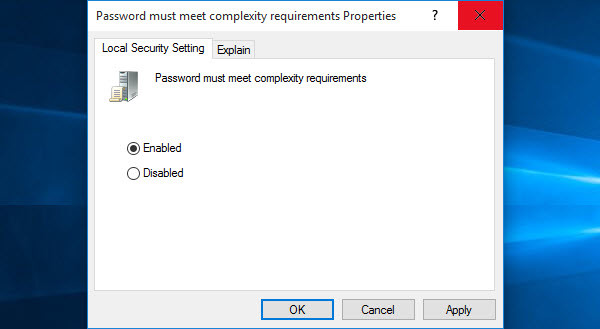
Password Must Meet Complexity Requirements
It’s beneficial and restricts vulnerabilities. You can see this policy when you create an Apple ID.
Store Passwords Using Reversible Encryption
This policy provides support for applications that use protocols that require knowledge of the user’s password for authentication purposes. Storing passwords using reversible encryption is essentially the same as storing plaintext versions of the passwords. For this reason, this policy should never be enabled unless application requirements outweigh the need to protect password information. I should tell you when you enabled this option; it will encrypt the password and no-one can access your password very easily.
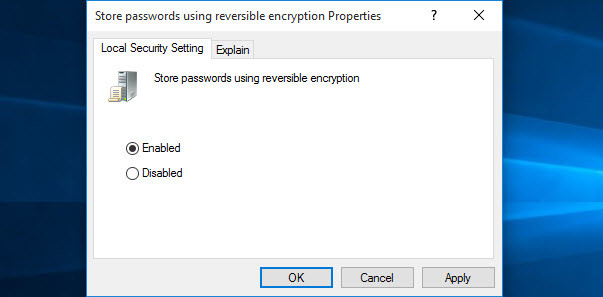
Store Passwords Using Reversible Encryption
It was all about how to configure password policies with windows server 2016. It does not only work on windows server 2016 but also work on later versions. Thanks for being with us.
Парольная политика в домене Active Directory задает базовые требования безопасности к паролям учетных записей пользователей такие как сложность, длину пароля, частоту смены пароля и т.д. Надежная политика паролей AD позволяет снизить возможность подбора или перехвата паролей пользователей.
Содержание:
- Настройка политики паролей в Default Domain Policy
- Основные параметры политики паролей в домене
- Управление параметрами политики паролей AD с помощью PowerShell
- Несколько парольных политик в домене Active Directory
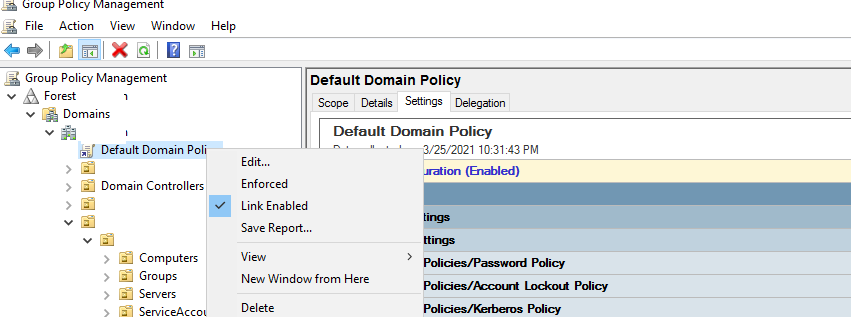
Настройка политики паролей в Default Domain Policy
Настройки политика паролей пользователей в домене AD по умолчанию задаются через групповую политику Default Domain Policy. Вы можете просмотреть и изменить настройки парольной политики в домене с помощью консоли управления консоль управления доменными GPO
- Откройте консоль
gpmc.msc
и выберите Default Domain Policy, которая назначена на корень домена; - Щелкните правой кнопкой по Default Domain Policy и выберите Edit;
- Разверните Конфигурация компьютера -> Политики -> Конфигурация Windows -> Параметры безопасности -> Политики учетных записей -> Политика паролей (Computer configuration -> Policies -> Windows Settings -> Security Settings -> Account Policies -> Password Policy
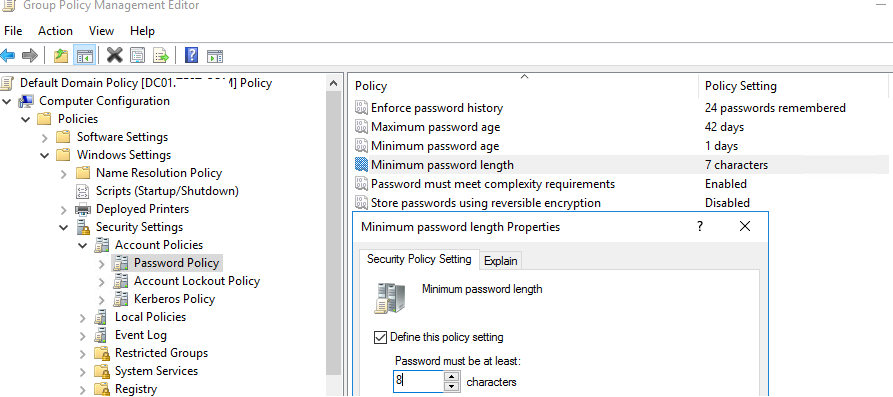
- В этом разделе есть шесть параметров политики паролей (описаны ниже);
- Чтобы изменить настройки параметра, дважды щелкните по ней. Чтобы включить политику, отметьте галку Define this policy settings и укажите необходимую настройку (в примере на скриншоте я задал минимальную длину пароля пользователя 8 символов). Сохраните изменения;
- Новые настройки парольной политики применяться ко всем пользователям домена после обновления настроек GPO на контролере домена с FSMO ролью PDC Emulator.
Основные параметры политики паролей в домене
Всего доступно шесть параметров политики паролей:
- Вести журнал паролей (Enforce password history) – задать количество старых паролей, которые хранятся в AD. Пользователь не сможет повторно использовать старый пароль (однако администратор домена или пользователь, которому делегированы права на сброс пароля в AD, может вручную задать для аккаунта старый пароль);
- Максимальный срок действия пароля (Maximum password age) – срок действия пароля в днях. После истечения срока действия пароля Windows потребует у пользователя сменить его. Обеспечивает регулярность смены пароля пользователями;
- Минимальный срок жизни пароля (Minimum password age) – как часто пользователи могут менять пароль. Этот параметр не позволит пользователю несколько раз подряд сменить пароль, чтобы вернуться к старому паролю, перезатерев пароли в журнале Password History. Как правило тут стоит оставить 1 день, чтобы пользователь мог самостоятельно сменить пароль в случае его компрометации;
- Минимальная длина пароля (Minimum password length) – не рекомендуется делать пароль короче, чем 8 символов (если указать тут 0 – значит пароль не требуется);
- Пароль должен отвечать требование сложности (Password must meet complexity requirements) – при включении этой политики пользователю запрещено использовать имя своей учетной записи в пароле (не более чем два символа подряд из
username
или
Firstname
). Также в пароле должны использоваться 3 типа символов из следующего списка: цифры (0 – 9), символы в верхнем регистре, символы в нижнем регистре, спец символы ($, #, % и т.д.).Чтобы исключить использование пользователями простых паролей (из словаря популярных паролей) рекомендуется периодически выполнять аудит паролей в домене.
- Хранить пароли, использую обратимое шифрование (Store passwords using reversible encryption) – пароли пользователей в базе AD хранятся в зашифрованном виде, но иногда нужно предоставить доступ некоторым приложениям к паролю. При включении этой политики пароли хранятся в менее защищенной виде (по сути, в открытом виде), что небезопасно (можно получить доступ к базе паролей при компрометации DC). При включении этой опции нужно дополнительно защищать пароли привилегированных пользователей на удаленных площадках с помощью внедрения Read-Only контроллеров домена (RODC).
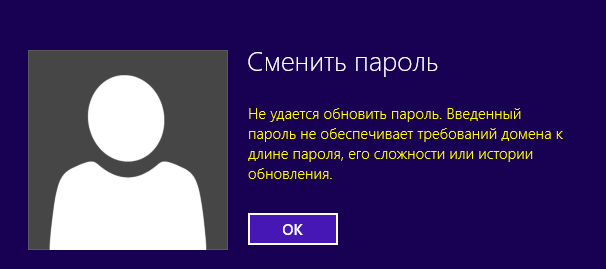
Если пользователь попытается задать пароль, которые не соответствует политике паролей в домене, Windows выдаст ошибку:
Не удается обновить пароль. Введенный пароль не обеспечивает требований домена к длине пароля, его сложности или истории обновления.
Unable to update the password. The value provided for the new password does not meet the length, complexity, or history requirements of the domain.
Обычно вместе с политикой паролей нужно настроить параметры блокировки пользователей при неправильном введении пароля. Эти настройки находятся в разделе GPO: Политика блокировки учетной записи (Account Lockout Password):
- Пороговое значение блокировки (Account Lockout Threshold) – через сколько попыток набрать неверный пароль учетная запись пользователя будет заблокирована;
- Продолжительность блокировки учетной записи (Account Lockout Duration) – длительность блокировки учетной записи, в течении которой вход в домен будет невозможен;
- Время до сброса счетчика блокировки (Reset account lockout counter after) – через сколько минут счетчик неверных паролей (Account Lockout Threshold) будет сброшен.
Если учетные записи блокируются слишком часто, вы можете найти компьютер/сервер источник блокировки так.
Настройки парольных политик домена Active Directory по-умолчанию перечислены в таблице:
| Политика | Значение по-умолчанию |
| Enforce password history | 24 пароля |
| Maximum password age | 42 дня |
| Minimum password age | 1 день |
| Minimum password length | 7 |
| Password must meet complexity requirements | Включено |
| Store passwords using reversible encryption | Отключено |
| Account lockout duration | Не определено |
| Account lockout threshold | 0 |
| Reset account lockout counter after | Не определено |
Управление параметрами политики паролей AD с помощью PowerShell
Для просмотра настроек и изменения конфигурации политики паролей в AD можно использовать командлеты PowerShell из модуля Active Directory:
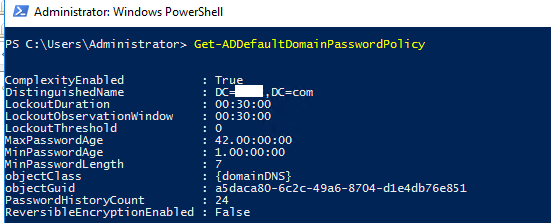
Вывести настройки дефолтной политики паролей:
Get-ADDefaultDomainPasswordPolicy
ComplexityEnabled : True
DistinguishedName : DC=winitpro,DC=ru
LockoutDuration : 00:30:00
LockoutObservationWindow : 00:30:00
LockoutThreshold : 0
MaxPasswordAge : 42.00:00:00
MinPasswordAge : 1.00:00:00
MinPasswordLength : 7
objectClass : {domainDNS}
objectGuid :
PasswordHistoryCount : 24
ReversibleEncryptionEnabled : False
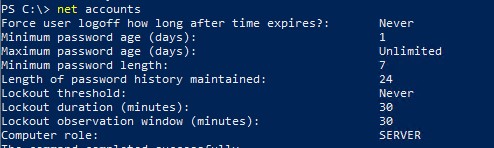
Или с помощью команды:
net accounts
Также вы можете узнать текущие настройки политики паролей AD на любом компьютере в отчете результирующей политики, сгенерированном с помощью консольной утилиты gpresult.
Вывести информацию о том, когда пользователь менял пароль последний раз, и когда истекает его пароль:
net user aivanov /domain
Изменить параметры политики паролей AD:
Set-ADDefaultDomainPasswordPolicy -Identity winitpro.ru -MinPasswordLength 14 -LockoutThreshold 10
Несколько парольных политик в домене Active Directory
С помощью групповых политик на домен можно назначить только одну политику, которая будет действовать на всех пользователей без исключения. Даже если вы создадите новую GPO с другими парольными настройками и примените ее к OU с пользователями, эти настройки фактически не применяться.
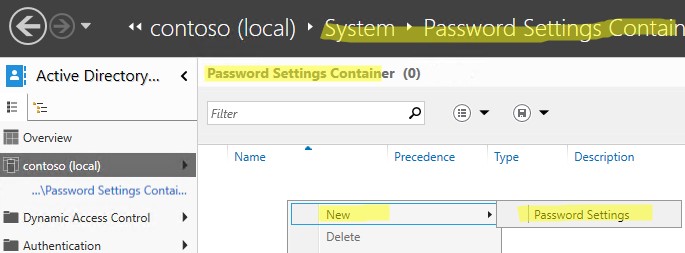
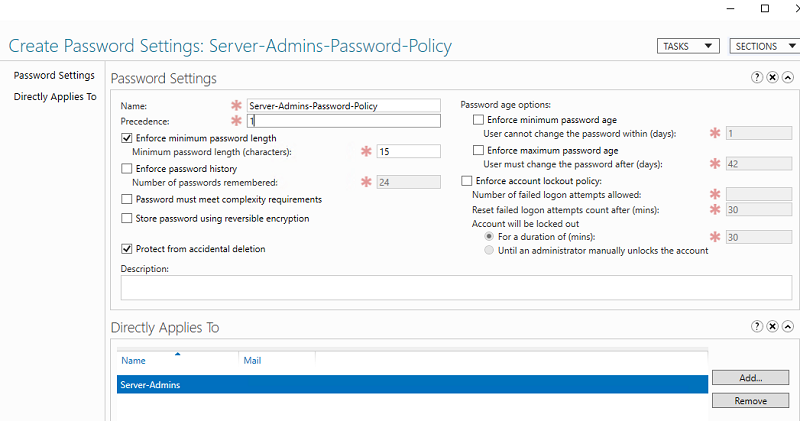
Начиная с версии Active Directory в Windows Server 2008 с помощью гранулированных политик паролей Fine-Grained Password Policies (FGPP) можно применять индивидуальный параметры политики паролей для конкретных пользователей или групп. Например, вы хотите, чтобы пользователи из группы Server-Admins использовали пароли с минимальной длиной 15 символов.
- Откройте консоль Active Directory Administrative Center (
dsac.exe
); - Перейдите в раздел System -> Password Settings Container и создайте новый объект PSO (Password Settings Object);
- В открывшемся окне укажите название политики паролей и ее приоритет. Включите и настройте параметры парольной паролей, которые вы хотите применить. В разделе Directly Applies to нужно добавить группы или пользователей, для которых должны применяться ваши особые настройки политики паролей.
Чтобы проверить, применяются ли к конкретному пользователю особая политика паролей, выполните команду:
Get-ADUserResultantPasswordPolicy -Identity aivanov
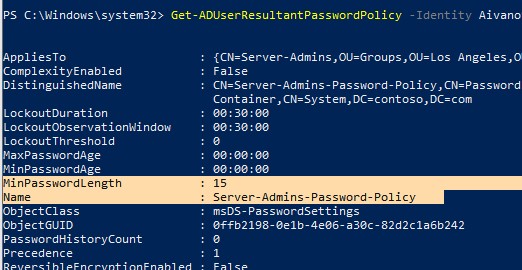
Команда выведет результирующие настройки политики паролей, которые дейсвтуиют на пользователя.
How To Change Password In Windows Server 2016 4 Methods Itechguides How to configure password policies with windows server 2016? you can open up group policy management editor into three various ways. first method : press windows key and type control panel and now select administrative tools and then select local security policy. You can change your password on a windows server 2016 using one of the 4 methods discussed in this guide. option 1: change password with ctrl alt delete this is the easiest way to change password in windows server 2016.
How To Change Password In Windows Server 2016 4 Methods Itechguides To change the password history setting of the passwordpolicy policy, run the following command. replace passwordpolicy with the desired policy name. set adfinegrainedpasswordpolicy passwordpolicy passwordhistorycount:»30″. There are six windows password policy settings that you can configure with the gpo: enforce password history – set the number of old passwords stored in ad. users cannot reuse old passwords. How to change default password policy in server 2016. About press copyright contact us creators advertise developers terms privacy policy & safety how works test new features nfl sunday ticket press copyright.
How To Change Password In Windows Server 2016 4 Methods Itechguides How to change default password policy in server 2016. About press copyright contact us creators advertise developers terms privacy policy & safety how works test new features nfl sunday ticket press copyright. In this blog, i’ll be walking you through how to change password policies on windows server so that you can make sure that those in your network will make stronger passwords . Today i am writing about how to modify maximum password age on windows server domain controller. we have faced this issue in our organization; our dc password used to expire every 42 days which was restricting access to users, sharepoint sites, and project server sites. Edit password expiration policies with local policies in windows server. the first method we will see is to edit the local directives. with this intention press the win r combination and run the following command: gpedit.msc. How to change windows server 2016 local administrator or other user accounts’ password if you forgot your administrator password? or your password was expired? here i will show you two fast ways to change your password easily and safely.
How To Change Password In Windows Server 2016 4 Methods Itechguides In this blog, i’ll be walking you through how to change password policies on windows server so that you can make sure that those in your network will make stronger passwords . Today i am writing about how to modify maximum password age on windows server domain controller. we have faced this issue in our organization; our dc password used to expire every 42 days which was restricting access to users, sharepoint sites, and project server sites. Edit password expiration policies with local policies in windows server. the first method we will see is to edit the local directives. with this intention press the win r combination and run the following command: gpedit.msc. How to change windows server 2016 local administrator or other user accounts’ password if you forgot your administrator password? or your password was expired? here i will show you two fast ways to change your password easily and safely.
How To Change Password In Windows Server 2016 4 Methods Itechguides Edit password expiration policies with local policies in windows server. the first method we will see is to edit the local directives. with this intention press the win r combination and run the following command: gpedit.msc. How to change windows server 2016 local administrator or other user accounts’ password if you forgot your administrator password? or your password was expired? here i will show you two fast ways to change your password easily and safely.
How To Change Password In Windows Server 2016 4 Methods Itechguides
,
The «Password must meet complexity requirements» policy setting in Server 2016, determines the minimum requirements when passwords are changed or created. The rules that are included in the Windows Server password complexity requirements are part of Passfilt.dll, and they cannot be directly modified.
By default in Server 2016, passwords must meet the following minimum requirements:
1. Passwords must not contain the user’s account name or parts of the user’s full name that exceed two consecutive characters.
2. Passwords must be at least seven characters in length.
3. Passwords must contain characters from three of the following four categories:
a. English uppercase characters (A through Z)
b. English lowercase characters (a through z)
c. Base 10 digits (0 through 9)
d. Non-alphabetic characters (for example, !, $, #, %)
This tutorial contains instructions on how to turn off the Password Complexity requirements on a Stand-Alone Server 2016 or in a Active Directory Domain Controller 2016.
How to Remove the Password Complexity requirements in Active Directory Server 2016 or a Stand Alone Server 2016.
Part 1. How to Disable Password Complexity requirements in Active Directory 2016.
Part 2. How to Disable Password Complexity requirements on a stand-alone Server 2016.
Part 1. How to Turn Off Password Complexity requirements in Active Directory Domain Server 2016.
To remove the password complexity in Active Directory 2016.
1. In Server 2016 AD Domain Controller, open the Server Manager and then from Tools menu, open the Group Policy Management. *
* Additionally, navigate to Control Panel -> Administrative Tools -> Group Policy Management.
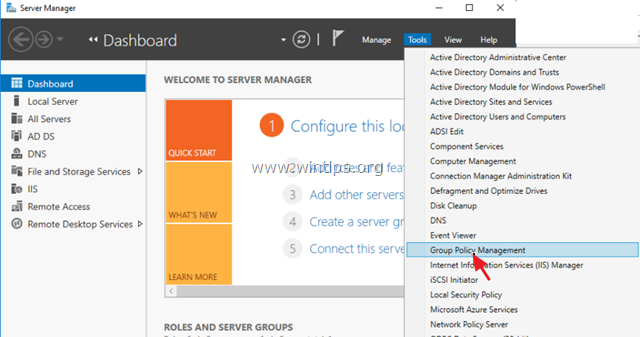
2. Under Domains, select your domain and then right click at Default Domain Policy and choose Edit.
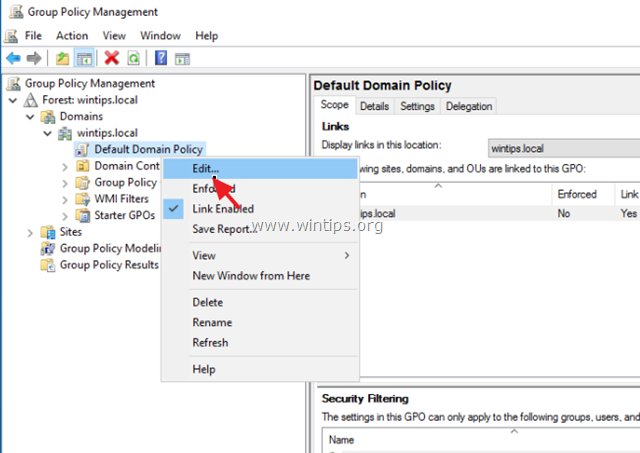
3. Then navigate to:
- Computer Configuration\Policies\Windows Settings\Security Settings\Account Policies\Password Policy
4. At the right pane, double click at Password must meet complexity requirements.
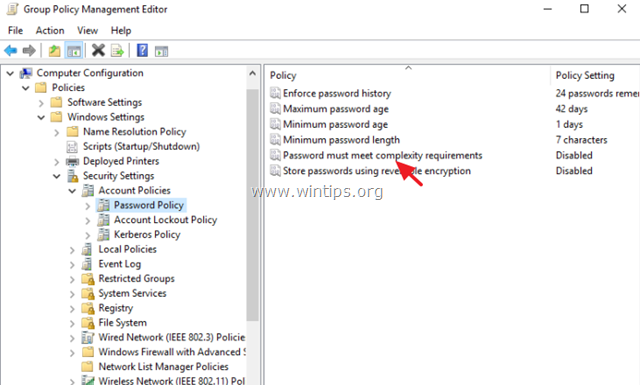
5. Select Define this Policy setting: Disabled and then click OK.
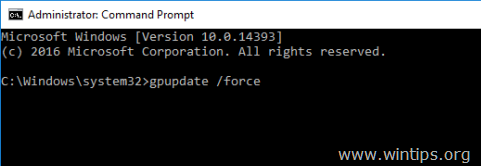
6. Finally, open Command Prompt as Administrator and give the following command to update the group policy.
- gpupdate /force
Part 2. How to Turn Off Password Complexity requirements in a standalone Server 2016.
1. From Server Manager go to Tools and open Local Security Policy, or (additionally), go to Control Panel open Administrative Tools and then open the Local Security Policy.
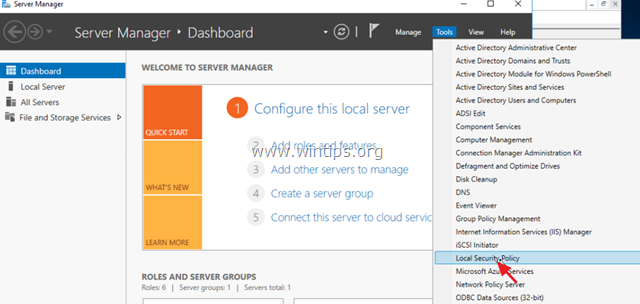
2. Under Security settings, select Password Policy.
3. At the right pane, double click at Password must meet complexity requirements.

4. Select Disabled and then click OK.
5. Finally, open Command Prompt as Administrator and give the following command to update the group policy.
- gpupdate /force

That’s it! Let me know if this guide has helped you by leaving your comment about your experience. Please like and share this guide to help others.
If this article was useful for you, please consider supporting us by making a donation. Even $1 can a make a huge difference for us in our effort to continue to help others while keeping this site free:
- Author
- Recent Posts
Konstantinos is the founder and administrator of Wintips.org. Since 1995 he works and provides IT support as a computer and network expert to individuals and large companies. He is specialized in solving problems related to Windows or other Microsoft products (Windows Server, Office, Microsoft 365, etc.).
Hello! User management in Windows Server is a fundamental issue. Mostly for security and privacy issues. Indeed, some users should not access certain aspects of the organization. Likewise, it is convenient to limit the duration of passwords. That is why we will address this topic today. Stay with us to see how to configure password expiration policy local or domain mode in Windows Server 2019/2016.
Reasons to set password expiration policies.
There are several reasons to set up password expiration policies on Windows Server:
- Temporary users.
- Users who are doing study practices in the company.
- Users whose contract expires. Consequently, the administration orders the deactivation of the account in a determined period of time.
- Test users.
- Security controls
Edit password expiration policies with local policies in Windows Server.
The first method we will see is to edit the local directives. With this intention press the Win+R combination and run the following command:
gpedit.msc
Consequently, it follows the following path: Local Computer Policy>Computer Configuration>Windows Settings>Security Settings>Account Policy>Password Policy.

Once there, several configuration parameters are displayed:
- Enforce password history: This parameter allows you to determine how many new passwords are related to a user. Consequently, it avoids assigning a previous password again.
- Maximum password age: Through this option you define the number of days of use of a password. Even before Windows Server requests the change.
- Minimum password age: With this alternative it is possible to define the number of days of duration of the password. Before being modified by the user.
- Minimum password length: It allows you to define the minimum number of characters in the password.
- Minimum password length: It allows you to define the minimum number of characters the password will contain.
- Password must meet complexity requirements: Determines how passwords should be set with complexity parameters. For example, combination of symbols, numbers, capital letters, etc.
- Storage passwords using reversible encryption: This configuration is related to certain applications. In fact, these are protocols that require knowledge of the user’s password for authentication purposes.
Edit password expiration policies with domain policies in Windows Server.
With this in mind, it is necessary to login to the server manager. Once there, please go to the Tools menu. Then click on Group Policy Management.

The following menu will be displayed immediately.

Please display the forest, and then the domain. Once there, right click on Default Domain Policy.

This window will then be displayed.

Please follow the path below: Default Domain Policy>Computer Configuration>Policies>Windows Settings>Security Settings>Account Policies>Password Policies. As you can see, there are the same options as in the local directives. However, the most important difference is the scope of application. That is, by making changes locally, you can’t modify the domain’s directives. On the contrary, from a computer in a domain it is possible to modify the policies. With this intention, double-click on Maximum Password age.

You can see that for security reasons it is set at 42 days. On the contrary, if you set it to 0 then the password will never expire.

In this way we have seen how to configure password expiration policy local or domain mode in Windows Server 2019/2016. This way you increase the security of the system. All right, that’s it for now. Please keep an eye out for updates on Windows Server. Bye!
— Advertisement —
Everything Linux, A.I, IT News, DataOps, Open Source and more delivered right to you.
Subscribe
«The best Linux newsletter on the web»