С помощью сервера обновлений Windows Server Update Services (WSUS) вы можете развернуть собственную централизованную систему обновления продуктов Microsoft (операционных систем Widows, Office, SQL Server, Exchange и т.д.) на компьютерах и серверах в локальной сети компании. В этой статье мы рассмотрим, как установить и настроить сервер обновлений WSUS в Windows Server 2019/2016/2012R2.
Содержание:
- Установка роли WSUS в Windows Server
- Начальная настройка сервера обновлений WSUS в Windows Server
- Установка консоли администрирования WSUS в Windows 10/11
- Оптимизация производительности WSUS
Как работает WSUS?
Сервер WSUS реализован в виде отдельной роли Windows Server. В общих словах сервис WSUS можно описать так:
- После установки сервер WSUS по расписанию синхронизируется с серверами обновлений Microsoft Update в Интернете и скачивает новые обновления для выбранных продуктов;
- Администратор WSUS выбирает, какие обновления нужно установить на рабочие станции и сервера компании и одобряет их установку;
- Клиенты WSUS в локальной сети скачивают и устанавливают обновления с вашего сервера обновлений согласно настроенным политикам.
Установка роли WSUS в Windows Server
Начиная с Windows Server 2008, сервис WSUS выделен в отдельную роль, которую можно установить через консоль управления сервером или с помощью PowerShell.
Если вы развертываете новый сервер WSUS, рекомендуется сразу устанавливать его на последнем релизе Windows Server 2022 (возможна установка на Windows Serve Core).
Чтобы установить WSUS, откройте консоль Server Manager и отметьте роль Windows Server Update Services (система автоматически выберет и предложит установить необходимые компоненты веб сервера IIS).
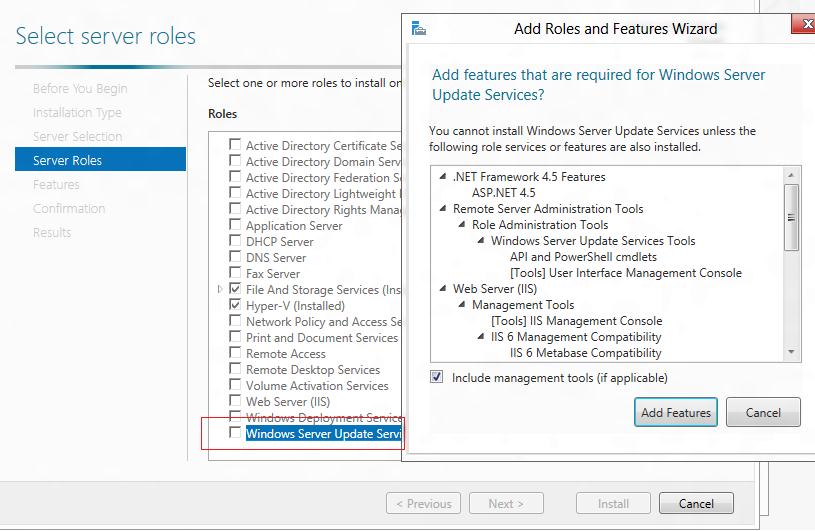
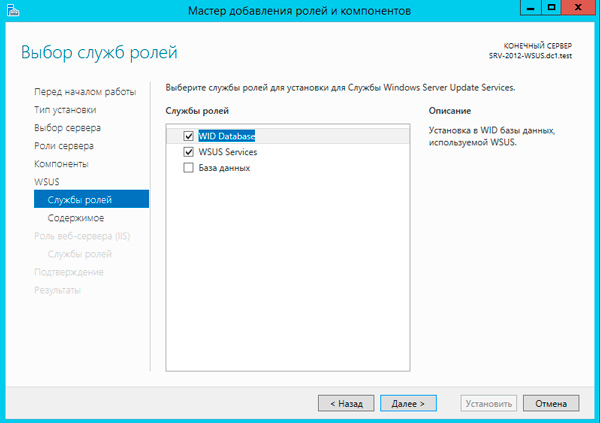
В следующем окне нужно выбрать, какие компоненты WSUS нужно установить. Обязательно отметьте опцию WSUS Services. Две следующие опции зависят от того, какую базу данных вы планируете использовать для WSUS.
Настройки сервера, метаданные обновлений, информация о клиентах WSUS хранятся в базе данных SQL Server. В качестве базы данных WSUS вы можете использовать:
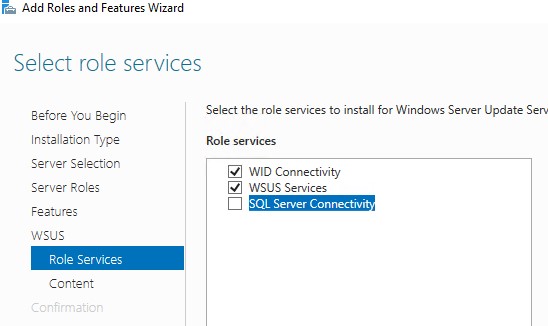
- Windows Internal Database (WID) – встроенную базу данных Windows, опция WID Connectivity (это рекомендуемый и работоспособный вариант даже для больших инфраструктур);
- Отдельную базу Microsoft SQL Server, развернутую на локальном или удаленном сервере. Вы можете использовать редакции MS SQL Enterprise, Standard (требуют лицензирования) или бесплатную Express редакцию. Это опция SQL Server Connectivity.
Внутреннюю базу Windows (Windows Internal Database) рекомендуется использовать, если:
- У вас отсутствуют лицензии MS SQL Server;
- Вы не планируется использовать балансировку нагрузки на WSUS (NLB WSUS);
- При развертывании дочернего сервера WSUS (например, в филиалах). В этом случае на вторичных серверах рекомендуется использовать встроенную базу WSUS.
В бесплатной SQL Server Express Edition максимальный размер БД ограничен 10 Гб. Ограничение Windows Internal Database – 524 Гб. Например, в моей инфраструктуре размер базы данных WSUS на 3000 клиентов составил около 7Гб.
При установке роли WSUS и MS SQL Server на разных серверах есть ряд ограничений:
- SQL сервер с БД WSUS не может быть контроллером домена Active Directory;
- Сервер WSUS нельзя разворачивать на хосте с ролью Remote Desktop Services.
База WID по умолчанию называется SUSDB.mdf и хранится в каталоге windir%\wid\data\. Эта база поддерживает только Windows аутентификацию (но не SQL). Инстанс внутренней (WID) базы данных для WSUS называется server_name\Microsoft##WID.
Базу WID можно администрировать через SQL Server Management Studio (SSMS), если указать в строке подключения
\\.\pipe\MICROSOFT##WID\tsql\query
.
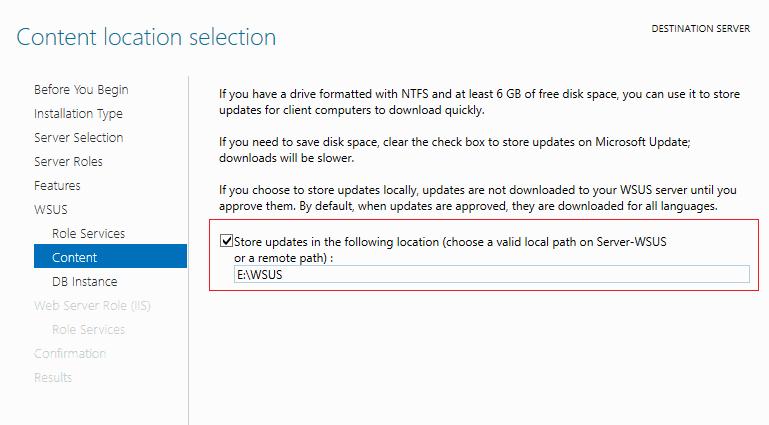
Если вы хотите хранить файлы обновлений локально на сервере WSUS, включите опцию Store updates in the following locations и укажите путь к каталогу. Это может быть папка на локальном диске (рекомендуется использовать отдельный физический или логический том), или сетевой каталог (UNC путь). Обновления скачиваются в указанный каталог только после их одобрения администратором WSUS.
Размер базы данных WSUS сильно зависит от количества продуктов и версий ОС Windows, которое вы планируете обновлять. В большой организации размер файлов обновлений на WSUS сервере может достигать сотни Гб.
Если у вас недостаточно места на дисках для хранения файлов обновлений, отключите эту опцию. В этом случае клиенты WSUS будут получать одобренный файлы обновлений из Интернета (вполне рабочий вариант для небольших сетей).
Также вы можете установить сервер WSUS с внутренней базой данный WID с помощью PowerShell командлета Install-WindowsFeature:
Install-WindowsFeature -Name UpdateServices, UpdateServices-WidDB, UpdateServices-Services, UpdateServices-RSAT, UpdateServices-API, UpdateServices-UI –IncludeManagementTools
Начальная настройка сервера обновлений WSUS в Windows Server
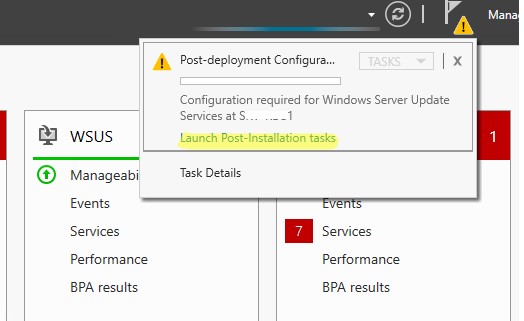
После окончания установки роли WSUS вам нужно выполнить его первоначальную настройку. Откройте Server Manager и выберите Post-Deployment Configuration -> Launch Post-Installation tasks.
Для управления WSUS из командной строки можно использовать консольную утилиту
WsusUtil.exe
. Например, чтобы указать путь к каталогу с файлами обновлений WSUS, выполните:
CD "C:\Program Files\Update Services\Tools"
WsusUtil.exe PostInstall CONTENT_DIR=E:\WSUS
Или, например, вы можете перенастроить ваш WSUS на внешнюю базу данных SQL Server:
wsusutil.exe postinstall SQL_INSTANCE_NAME="SQLSRV1\SQLINSTANCEWSUS" CONTENT_DIR=E:\WSUS_Content
Затем откройте консоль Windows Server Update Services. Запустится мастер первоначальной настройки сервера обновлений WSUS.
Укажите, будет ли сервер WSUS скачивать обновления с сайта Microsoft Update напрямую (Synchronize from Microsoft Update) или он должен получать их с вышестоящего WSUS сервера (Synchronize from another Windows Update Services server). Дочерние WSUS сервера обычно развертываются на удаленных площадках с большим количеством клиентов (300+) для снижения нагрузки на WAN канал.
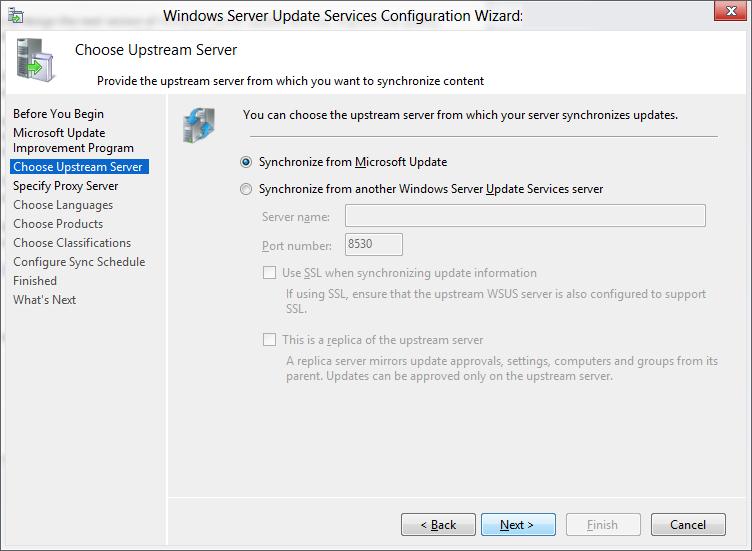
Если в вашей сети используется прокси-сервер для доступа в Интернет, далее нужно указать адрес и порт прокси сервера, и логин/пароль для аутентификации.
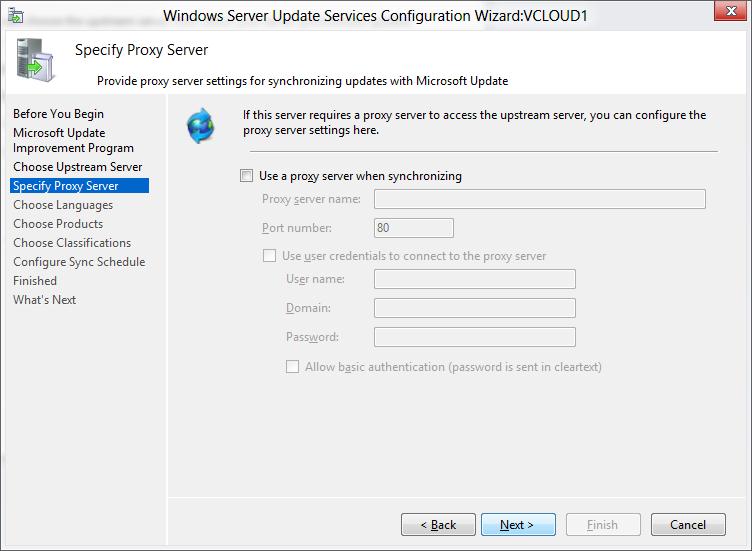
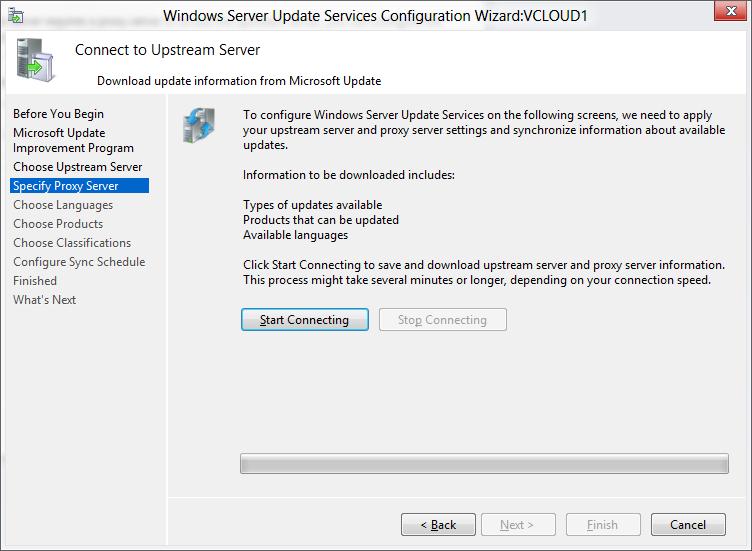
Проверьте подключение к вышестоящему серверу обновлений (или Windows Update). Нажмите кнопку Start Connecting.
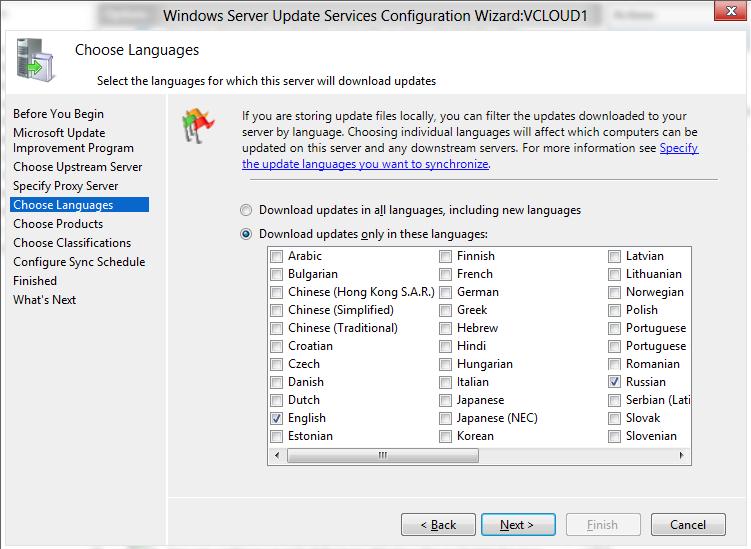
Выберите языки продуктов, для которых WSUS будет получать обновления. Мы укажем English и Russian (список языков может быть в дальнейшем изменен из консоли WSUS).
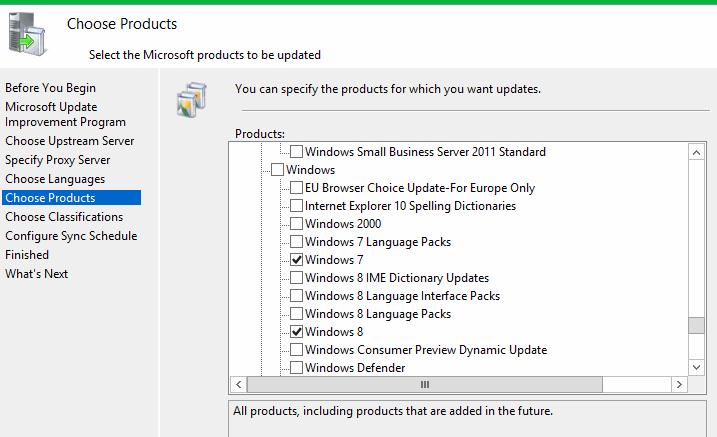
Затем выберите продукты, для которых WSUS должен скачивать обновления. Выберите только те продукты Microsoft, которые используются в Вашей корпоративной сети. Например, если вы уверены, что в вашей сети не осталось компьютеров с Windows 7 или Windows 8, не выбирайте эти опции.
Обязательно включите в классификации следующие общие разделы:
- Developer Tools, Runtimes, and Redistributable — для обновления библиотек Visual C++ Runtime
- Windows Dictionary Updates в категории Windows
- Windows Server Manager – Windows Server Update Services (WSUS) Dynamic Installer
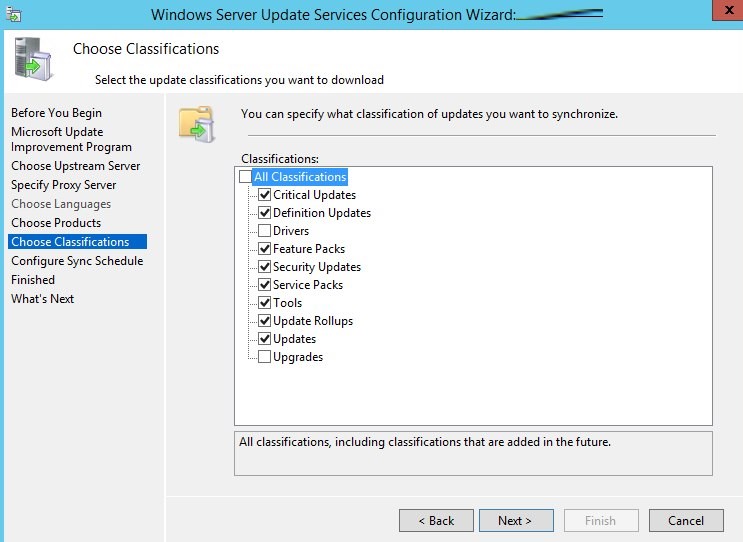
На странице Classification Page, нужно указать типы обновлений, которые будут распространяться через WSUS. Рекомендуется обязательно указать: Critical Updates, Definition Updates, Security Packs, Service Packs, Update Rollups, Updates.
Обновления редакций (билдов) Windows 10 (21H2, 20H2, 1909 и т.д.) в консоли WSUS входят в класс Upgrades.
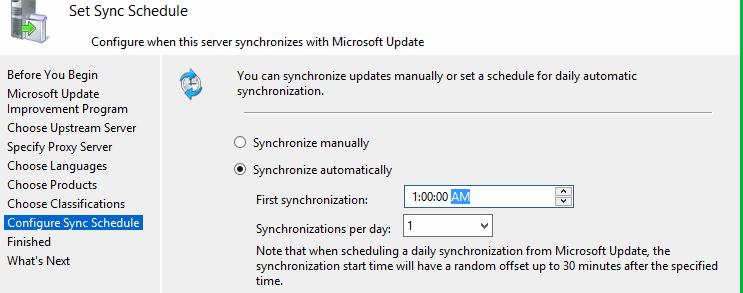
Настройте расписание синхронизации обновлений. В большинстве случаев рекомендуется использовать автоматическую ежедневную синхронизацию сервера WSUS с серверами обновлений Microsoft Update. Рекомендуется выполнять синхронизацию в ночные часы, чтобы не загружать канал Интернет в рабочее время.
Первоначальная синхронизация сервера WSUS с вышестоящим сервером обновлений может занять несколько дней (в зависимости от количества продуктов, которое вы выбрали ранее).
После окончания работы мастера запустится консоль WSUS.
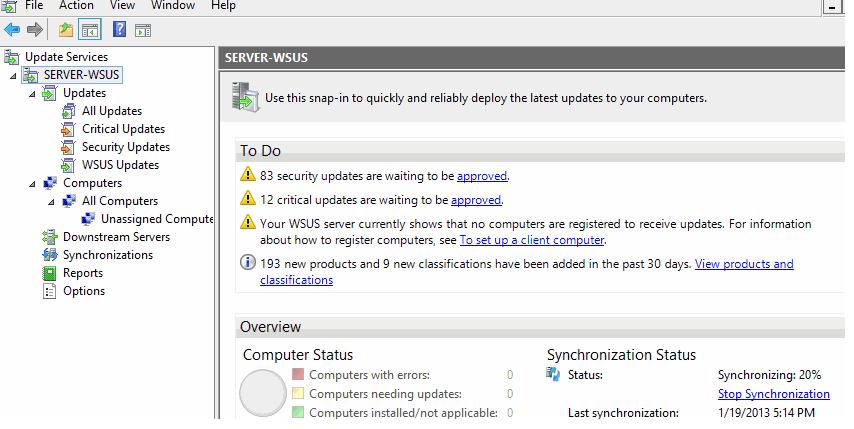
Консоль WSUS состоит из нескольких разделов:
- Updates – обновления, доступные на сервере WSUS (здесь можно управлять одобрением обновлений и назначать их для установки)
- Computers – здесь можно создать группы клиентов WSUS (компьютеры и серверы)
- Downstream Servers – позволяет настроить, будете ли вы получать из обновления Windows Update или вышестоящего сервера WSUS
- Syncronizations –расписание синхронизации обновлений
- Reports – отчёты WSUS
- Options – настройка сервера WSUS
Клиенты теперь могут получать обновления, подключившись к WSUS серверу по порту 8530 (в Windows Server 2003 и 2008 по умолчанию использоваться 80 порт). Проверьте, что этот порт открыт на сервере обновлений:
Test-NetConnection -ComputerName wsussrv1 -Port 8530
Можно использовать защищенное SSL подключение по порту 8531. Для этого нужно привязать сертификат в IIS.
Если порт закрыт, создайте соответствующее правило в Windows Defender Firewall.
Установка консоли администрирования WSUS в Windows 10/11
Для администрирования сервера обновления WSUS используется консоль Windows Server Update Services (
wsus.msc
). Вы можете управлять серверов WSUS как с помощью локальной консоли, так и по сети с удаленного компьютера.
Консоль администрирования WSUS для десктопных компьютеров с Windows 10 или 11 входит в состав RSAT. Для установки компонента Rsat.WSUS.Tool, выполните следующую PowerShell команду:
Add-WindowsCapability -Online -Name Rsat.WSUS.Tools~~~~0.0.1.0
Если вы хотите установить консоль WSUS в Windows Server, выполните команду:
Install-WindowsFeature -Name UpdateServices-Ui
При установке WSUS в Windows Server создаются две дополнительные локальные группы. Вы можете использовать их для предоставления доступа пользователям к консоли управления WSUS.
- WSUS Administrators
- WSUS Reporters
Для просмотра отчетов по установленным обновлениям и клиентам на WSUS нужно установить:
- Microsoft System CLR Types для SQL Server 2012 (SQLSysClrTypes.msi);
- Microsoft Report Viewer 2012 Runtime (ReportViewer.msi).
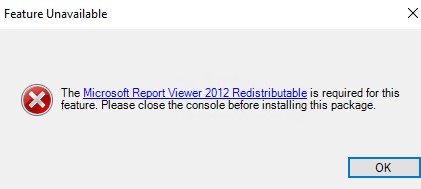
Если компоненты не установлен, при формировании любого отчета WSUS появится ошибка:
The Microsoft Report Viewer 2012 Redistributable is required for this feature. Please close the console before installing this package.
Оптимизация производительности WSUS
В этом разделе опишем несколько советов, касающихся оптимизации производительности сервера обновлений WSUS в реальных условиях.
- Для нормальной работы WSUS на сервере обновлений нужно должно быть свободным минимум 4 Гб RAM и 2CPU;
- При большом количестве клиентов WSUS (более 1500) вы можете столкнутся с существенным снижением производительность пула IIS WsusPoll, который раздает обновления клиентам. Может появляться ошибка 0x80244022 на клиентах, или при запуске консоль WSUS падать с ошибкой Error: Unexpected Error + Event ID 7053 в Event Viewer (The WSUS administration console has encountered an unexpected error. This may be a transient error; try restarting the administration console. If this error persists). Для решения проблемы нужно добавить RAM на сервер и оптимизировать настройки пула IIS в соответствии с рекомендациями в статье. Воспользуетесь такими командами:
Import-Module WebAdministration
Set-ItemProperty -Path IIS:\AppPools\WsusPool -Name queueLength -Value 2500
Set-ItemProperty -Path IIS:\AppPools\WsusPool -Name cpu.resetInterval -Value "00.00:15:00"
Set-ItemProperty -Path IIS:\AppPools\WsusPool -Name recycling.periodicRestart.privateMemory -Value 0
Set-ItemProperty -Path IIS:\AppPools\WsusPool -Name failure.loadBalancerCapabilities -Value "TcpLevel" - Включите автоматическое одобрения для обновлений антивируса Microsoft В противном случае WSUS станет существенно тормозить и потреблять всю доступную оперативную память.
Антивирусные проверки могут негативно влиять на производительность WSUS. Во встроенном Microsoft Defender антивирусе в Windows Server рекомендуется исключить следующие папки из области проверки:
- \WSUS\WSUSContent;
- %windir%\wid\data;
- \SoftwareDistribution\Download.
Тема настройки локального сервера обновлений (WSUS) уже поднималась на нашем сайте, но так как с тех пор прошло довольно много времени и произошли довольно серьезные изменения, то назрела необходимость обновить статью. Сегодня мы расскажем о настройке роли WSUS на платформе Windows Server 2012, данный процесс во многом стал проще и легче, а службы WSUS теперь полноценно интегрированы в систему.
Онлайн-курс по устройству компьютерных сетей
На углубленном курсе «Архитектура современных компьютерных сетей» вы с нуля научитесь работать с Wireshark и «под микроскопом» изучите работу сетевых протоколов. На протяжении курса надо будет выполнить более пятидесяти лабораторных работ в Wireshark.
Наш предыдущий материал рассматривал установку WSUS на платформе Windows Server 2008, тогда это была довольно непростая задача для неподготовленного администратора. Требовалось установить дополнительные пакеты, специальным образом настроить веб-сервер, да и сами службы WSUS устанавливались как отдельное приложение.
Начиная с Windows Server 2008 R2, WSUS был включен в состав ОС в качестве одной из ролей, поэтому, несмотря на то, что мы будем рассматривать платформу Windows Server 2012 R2, все сказанное, за незначительными поправками, будет справедливо и для Server 2008 R2.
Из сторонних пакетов потребуется установить только Microsoft Report Viewer 2008 SP1 Redistributable, однако он не является обязательным и на работу службы не влияет, а требуется только для формирования отчетов. Поэтому даже если вы забудете его установить — ничего страшного не произойдет, при первом обращении к отчетам система сообщит вам об этом и даст ссылку на скачивание.
Важно! Существует ряд ограничений на установку служб ролей WSUS. Сервер БД WSUS не может быть контроллером домена, Сервер WSUS не может быть одновременно сервером терминалов Remote Desktop Services.
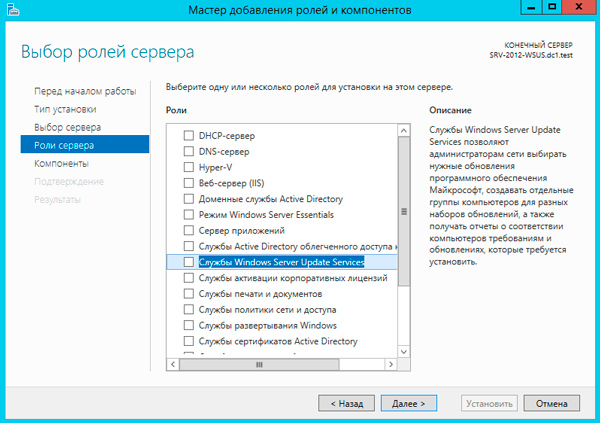
Для установки WSUS откроем Диспетчер серверов и перейдем в Управление — Добавить роли и компоненты. В открывшемся мастере добавляем роль Службы Windows Server Update Services.
Следующим шагом будут добавлены все необходимые роли и компоненты, таким образом больше ничего настраивать отдельно не придется.
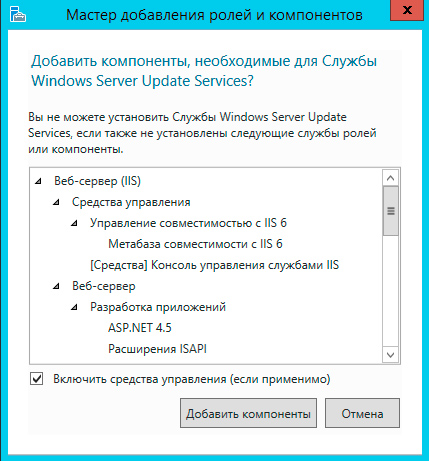
В качестве хранилища по умолчанию WSUS предлагает использовать внутреннюю базу данных Windows (Windows Internal Database, WID). Для небольших внедрений мы не видим смысла в установке отдельного SQL-сервера, никаких существенных преимуществ это не даст.
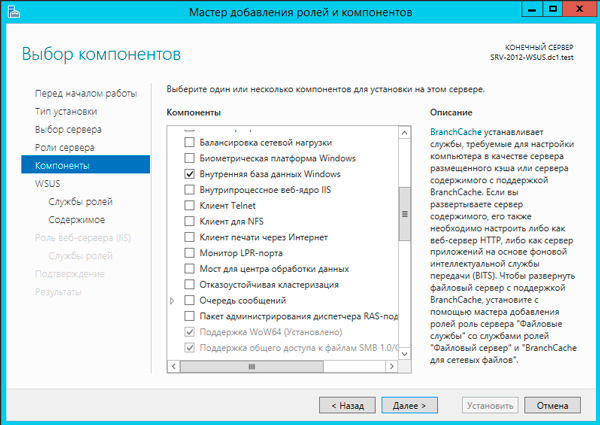
Следующим шагом переходим к базовым настройкам служб роли. В нашем случае потребуется выбрать опции WID Database и WSUS Services, если вы собираетесь использовать SQL-сервер, то вместо WID Database следует выбрать опцию База данных. Сам сервер баз данных к этому моменту уже должен быть развернут в вашей сети.
Следующим шагом укажите размещение хранилища обновлений, рекомендуем выделить для этих целей отдельный жесткий диск или раздел диска.
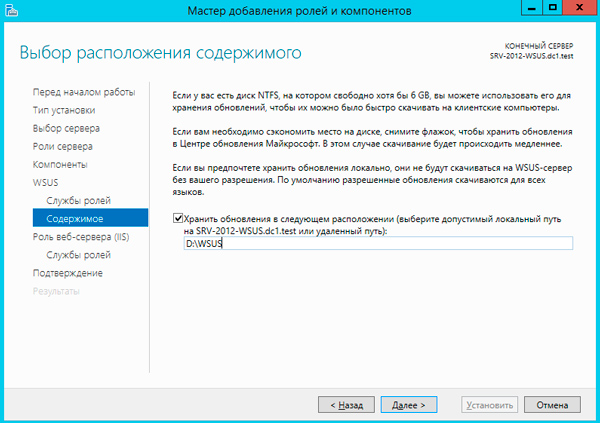
Также возможен вариант, когда на сервере WSUS будет храниться только информация об обновлениях, сами пакеты обновлений будут, после их одобрения и назначения администратором, скачиваться с серверов Microsoft. На наш взгляд такая схема будет удобна небольшим компаниям с хорошим интернет каналом, действительно, ради десятка машин организовывать локальное хранилище большого смысла не имеет, особенно если WSUS не единственная роль данного сервера.
Для приблизительной оценки требуемого места приведем данные с одной реальной инсталляции, произведенной летом 2012 года. На текущий момент выбраны следующие продукты: все клиентские ОС от Windows XP до Windows 8.1, кроме Vista, все серверные ОС от Server 2003 до Server 2012 R2, Office 2010, Exchange 2010, SQL Server 2008 — 2012, а также ряд дополнительных продуктов из разряда Распространяемых пакетов Visual C++ и т.п.
Размер обновлений в хранилище на текущий момент (два года после установки) — 173 ГБ, размер SQL базы данных — около 10 ГБ.
Если вы выбрали внешнюю базу данных, то также потребуется указать параметры подключения к SQL серверу. После чего можно переходить к установке роли, перезагрузка не требуется. После установки нажмите на флажок с желтым восклицательным знаком в Диспетчере серверов и щелкните Запуск послеустановочных задач, дождитесь окончания процедуры (восклицательный знак исчезнет).

На этом установку роли можно считать законченной и переходит к настройке службы WSUS, мы подробно освещали этот процесс в предыдущей статье и не видим смысла заострять на этом внимание.
Если коротко, то сначала нужно выбрать источник синхронизации: сервера Microsoft или вышестоящий WSUS сервер.
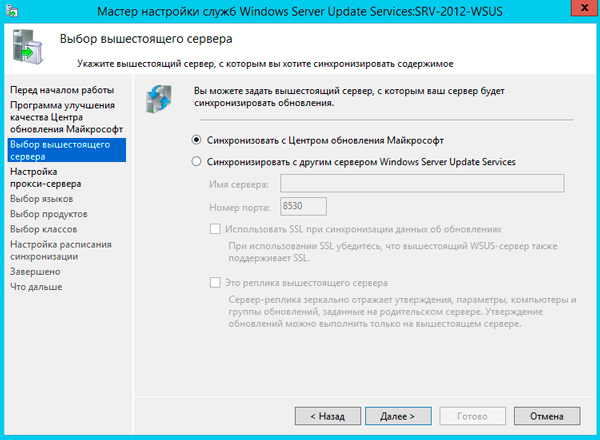
Затем выбрать языки и продукты.

Указать классы обновлений.
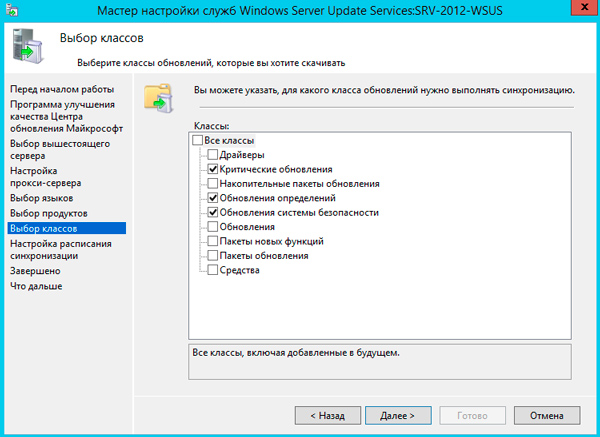
И задать параметры автоматической синхронизации.

Процесс первоначальной синхронизации может занять продолжительное время, зависящее от выбранного набора продуктов и классов, а также скорости вашего интернет канала.
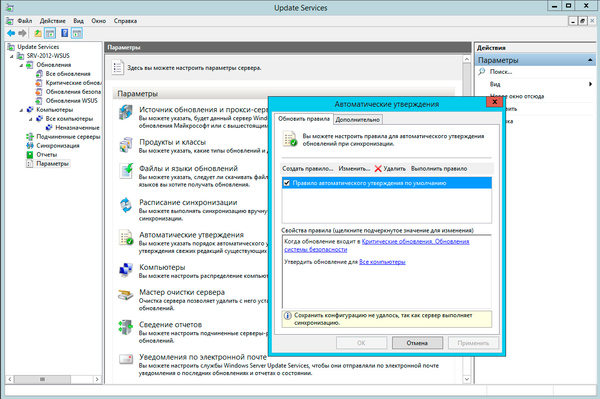
Не забудьте указать правила автоматического одобрения и одобрить уже скачанные обновления.
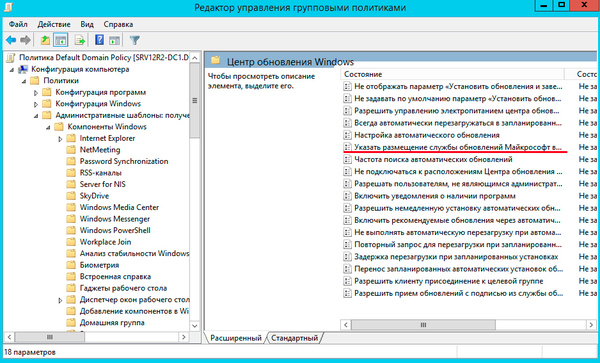
После чего потребуется сообщить клиентам расположение вашего WSUS сервера, это можно сделать через групповые политики: Конфигурация компьютера — Политики — Административные шаблоны — Центр обновления Windows — Указать размещение службы обновлений Microsoft в интрасети.
Или в локальных политиках: Пуск — Выполнить — gpedit.msc, затем Конфигурация компьютера — Административные шаблоны — Центр обновления Windows (Windows Update)- Указать размещение службы обновлений Microsoft в интрасети.
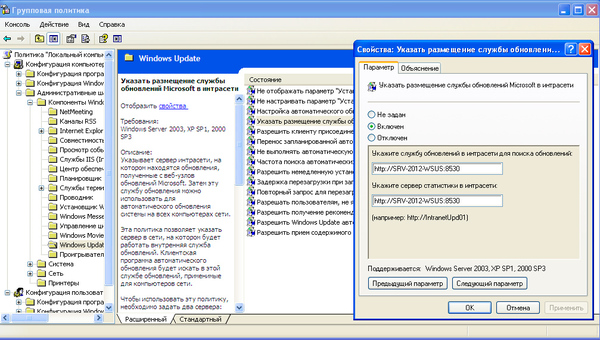
Путь к серверу следует прописывать как http://SERVER_NAME:8530, при этом рекомендуем явно указывать порт службы. Через некоторое время компьютеры начнут получать обновления и появятся в консоли сервера, где можно получить детальную информацию по уже установленным и требующимся обновлениям.

Кстати, если вы забыли установить Microsoft Report Viewer 2008 SP1 Redistributable, то при попытке вызвать отчет получите следующее сообщение, которое содержит ссылку на скачивание необходимого пакета. :
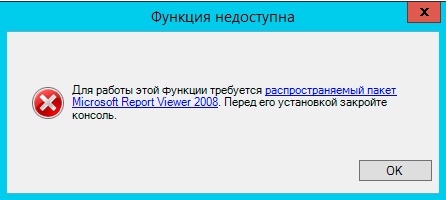
Как видим, Microsoft проделало большую работу по совершенствованию службы WSUS, теперь это одна из ролей системы и ее установка и настройка не должна вызывать затруднений даже у новичков.
Онлайн-курс по устройству компьютерных сетей
На углубленном курсе «Архитектура современных компьютерных сетей» вы с нуля научитесь работать с Wireshark и «под микроскопом» изучите работу сетевых протоколов. На протяжении курса надо будет выполнить более пятидесяти лабораторных работ в Wireshark.
Hello World,
Today, we will be speaking about WSUS or Windows Server Update Service. WSUS helps administrators to deploy hotfixes and updates to your IT infrastructure. By using WSUS server and configuring your group policies accordingly, you can protect and keep all the computer presented on your network up to date. You can also decide which updates or hotfix you want to deploy within your infrastructure. Microsoft offers other options to keep your infrastructure up to date (i.e. SCCM 2012) but this one come at no cost.
This post will focus on WSUS 4.0 which come as a Windows 2012 Server role and not anymore as a separate downloadable package. WSUS 4.0 is not a revolution but more an evolution of the existing product. The principle and concepts have not really changed. However, WSUS 4.0 provides some nice improvements compared to the previous version WSUS 3.2. One of the best thing is that you will be able to use powershell to automate your patch management process. Another nice thing (not directly related to WSUS) is the new Cluster aware update feature provided by Windows 2012 Server which ease the update process for cluster.
In this post, we will see how to perform a basic installation of the windows Update server role. In the future (I do not know when), we will explain how you can perform a migration from WSUS 3.2 to version WSUS 4.0. The migration process will be based on a side by side migration strategy. Finally, we will have a look at how the Cluster Aware Update Feature works and how you can use it in your environment.
But for the moment, let’s focus on the installation process of the new and fresh WSUS 4.0 server roles; Let’s go !
Installing the Server Role
Since Windows 2008, the Wsus server is defined as a Server role and can be installed directly from the server Manager console. If you open your Server Manager Console, Click on the Add/remove Server Roles, this will start the wizard.
In the before you begin page, Press Next
click on picture for better resolution
In the Select installation type page, select the role based installation option and press Next
click on picture for better resolution
In the Select a destination server page, select the appropriate server and press Next
click on picture for better resolution
In the Select Server role, tick the option Windows Server Update Services. If you are missing some components, you might see the Add Roles and features dialog box popping up. Select Add Features if this is the case
click on picture for better resolution
In the Select features Page, Simply press Next
click on picture for better resolution
In the Web Server Role page, Press Next
click on picture for better resolution
In the Role Services Page, accept the default and Press Next
click on picture for better resolution
In the Windows Server Update Services Page, Press Next
click on picture for better resolution
In the Select Role Services, we will select the 2 first options. In our deployment, we will be using the Windows Internal database option. If you do not want to use this WID database, you can select the Database option. If this option is selected, you will be able to use a local or remote database in conjunction with WSUS.
click on picture for better resolution
In the Content location page, specify the path where the update files will be stored and Press Next. Best practices is to use a dedicated partition for that (and not the operating system partition)
click on picture for better resolution
In the Confirmation page, Review your settings and Press the Install Button
click on picture for better resolution
You can monitor the installation progress
click on picture for better resolution
When the installation is completed, do not close yet the server role Wizard. If you look at the screen, you will see a small option that can be used to perform post installation tasks. Click on it
click on picture for better resolution
You can again see that the Wizard is configuring some additional settings on your server. Wait for completion
click on picture for better resolution
At the end of the process, you should see in the wizard page, a small comment stating that the installation is complete. You can close the Server role Wizard.
click on picture for better resolution
Initial WSUS Configuration
If you open your server manager console, you will see that an additional link has been added on the left side menu. Click on the WSUS link. In the WSUS Server manager page, right-click on the WSUS server object and select Windows Server Update Services. This will open the Initial Configuration Wizard for WSUS.
click on picture for better resolution
In the Before you Begin page of the WSUS Wizard, Press Next
click on picture for better resolution
In the Join Improvement Program Page, select the appropriate option and Press Next
click on picture for better resolution
In the Choose Upstream Server, Select the appropriate Option (This will depends on your deployment scenario)
click on picture for better resolution
In the Specify a Proxy Server Page, Select the appropriate option based on your network and Press Next
click on picture for better resolution
In the Connect to Upstrean Server, Click on the Start Connecting. Wait for completion
click on picture for better resolution
In the Choose Language Page, Select the language you need and Press Next. In my environment, everything is set to english
click on picture for better resolution
In the Choose Product Page, select categories of products you want to patch using WSUS. This can be Windows OS as well as Exchange Products. When your selection is complete, Press Next.
click on picture for better resolution
In Classification Page, Select which type of update you want to deploy using WSUS. When your selection is done, Press Next
click on picture for better resolution
In the Set Sync Schedule, adjust your options and Press Next
click on picture for better resolution
In the Finished Page, Accept default and Press Next
click on picture for better resolution
In the What’s Next Page, You can see the additional steps you need to perform in order to have a fully functional WSUS infrastructure.
click on picture for better resolution
Note : Here, We have been using the Wizard. You can perform the same configuration by opening the WSUS console and start specifying your configuration stetings.
Overview WSUS MMC Console
The WSUS option is available since Windows 2003 and this version has not changed dramatically. If you are used to work with WSUS server, you will see that this version does not change much from the version available in Windows 2008 R2.
In the following screenshot, you can see how the WSUS console look like.
click on picture for better resolution
In order to configure your WSUS server settings, on the left pane, you can click on the Options link and you will see the following console. All the options you have selected using the Configuration Wizard can be set/changed through this page as well.
click on picture for better resolution
As you can see from the screenshot, you can configure a bunch of stuff. You can
- start the configuration Wizard
- Configure schedule sync
- Configure Languages
- Configure Classifications
- Configure Products
- Configure Computers
- Configure Automatic Approval
- Perform a Server Cleanup (using the Server Wizard Cleanup)
- ….
We will have a look at these configuration options in another post (if I have time : -p).
During the configuration wizard, we did not start the synch process. From the left pane, if you click on the Synchronization node, you will be able to manually start your download.
click on picture for better resolution
Finally, If you click on the reports node, you will see that you can generate a bunch of reports related. However, before being able to generate them, do not forget (like I did) to install the MS Report Viewer component first.
click on picture for better resolution
When the component is installed, you will be able to generate some nice reports.
Click on Picture for Better Resolution
Final Notes
Voila ! That’s it for this post ! The installation process has changed a little bit compared to the previous version but as you have seen the way of working and the MMC console have not really changed. With this post, we have performed an installation from scratch of WSUS. We have seen also how to perform the initial configuration. Because there is a lot of people out there using WSUS 3.2, the next post might be more useful as we will be describing the migration process from WSUS 3.2 to WSUS 4.0
Till next time
See ya
For more information, please have a look at http://technet.microsoft.com/en-us/library/hh852340.aspx
Windows Server Update Services (WSUS) is a free patch management tool by Microsoft. It allows sysadmins to centrally push Microsoft product updates to computers that are running Windows on their network.
This guide will help you set up your very own WSUS server on Windows Server 2012 R2.
Why WSUS?
How do Windows computers usually update? In a non-WSUS environment (generally all home environments), each PC independently connects to Microsoft Update to get its patches and MS product updates.
This may not be always preferred in a corporate environment. Instead of each workstation manually connecting to Microsoft Update, testing updates and then deploying updates using traditional methods, administrators can use WSUS to download updates centrally to an internal server. Once updates are authorised in WSUS, they’re also deployed internally and reporting tools keep administrators informed of patch progress. This is a very efficient way of working, allowing administrators full control of which updates are deployed to workstations.
In Windows Server 2012 and 2012 R2, WSUS is integrated with the operating system as a server role. In previous versions of Windows Server (2003, 2008, 2008 R2), you had to separately install WSUS 3.0.
Also, seems like Microsoft will be moving away from WSUS to an entirely new product called Windows Update for Business (WUB). You can read more about it here.
Ok, so now, let’s see how we can set up WSUS on Windows Server 2012 R2
What you need:
- A machine with Windows Server 2012 R2 installed
- Internet connection
- 20 minutes (not including download times)
I started with a fresh install of Windows Server 2012 R2 on a VM and connected it to my domain.
Step 1:
On your Windows Server 2012 R2 machine, launch Server Manager as shown below.
You can either launch it using the icon in the taskbar or you can click the Start button and just search for “server manager”.
Step 2:
Once Server Manager is open, select Add roles and features.
Step 3:
In the Add Roles and Features Wizard, click next on the Before You Begin page. You can optionally select to Skip this page by default for the future.
Step 4:
Select Role-based or feature-based installation
Step 5:
Select your server from the server pool. If you’re not using Hyper-V, you will see only one server, i.e., your soon-to-be WSUS server.
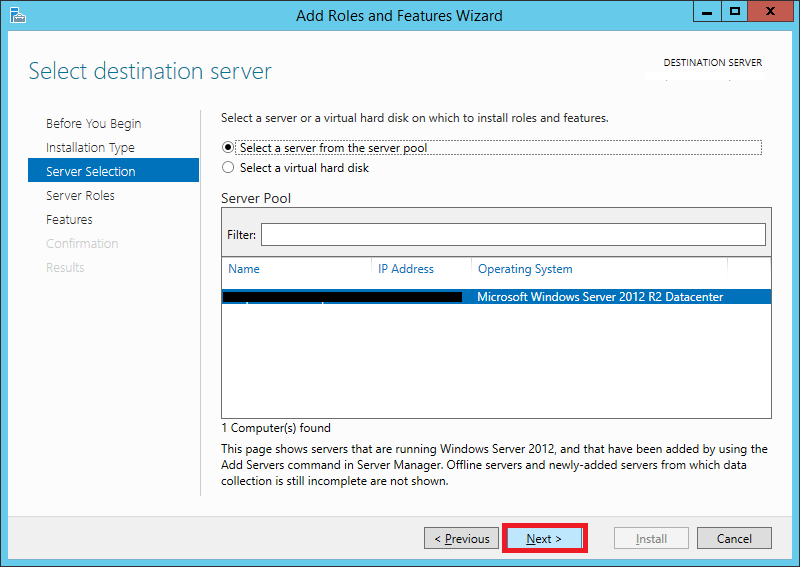
Step 6:
In the Server Roles list, scroll down and select Windows Server Update Services
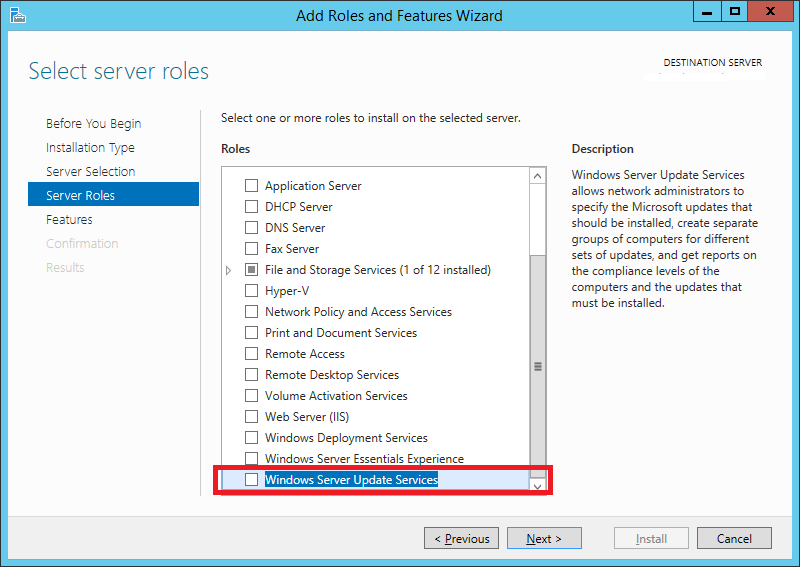
Step 7:
A window will pop up showing you the features that are required for WSUS which will be enabled. Click Add Features
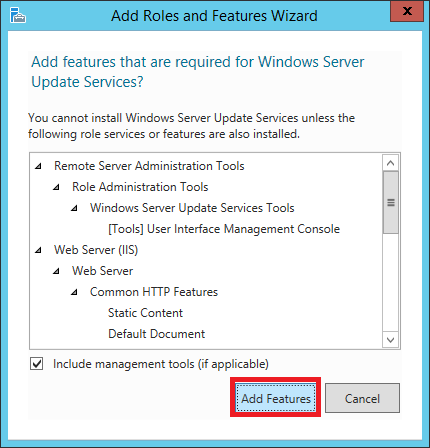
Step 8:
You will notice that IIS has been automatically selected. Leave everything as default and click Next
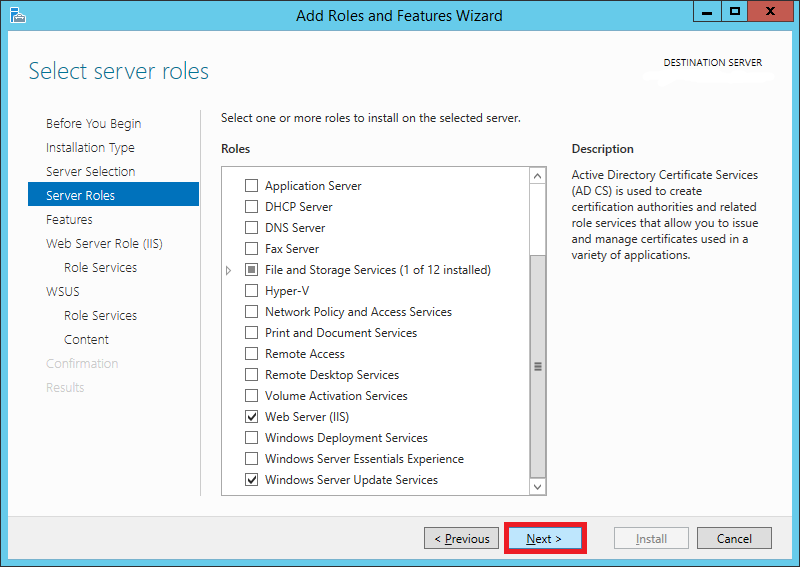
Step 9:
On the Features screen, leave the default selections and click Next
Step 10:
On the Web Server Role (IIS) page, click Next
Step 11:
Leave all selections as default on the Role Services page and click Next
Step 12:
Click Next on this screen
Step 13:
On the Role Services page, make sure WID Database and WSUS Services are selected (They should be selected by default). Click Next
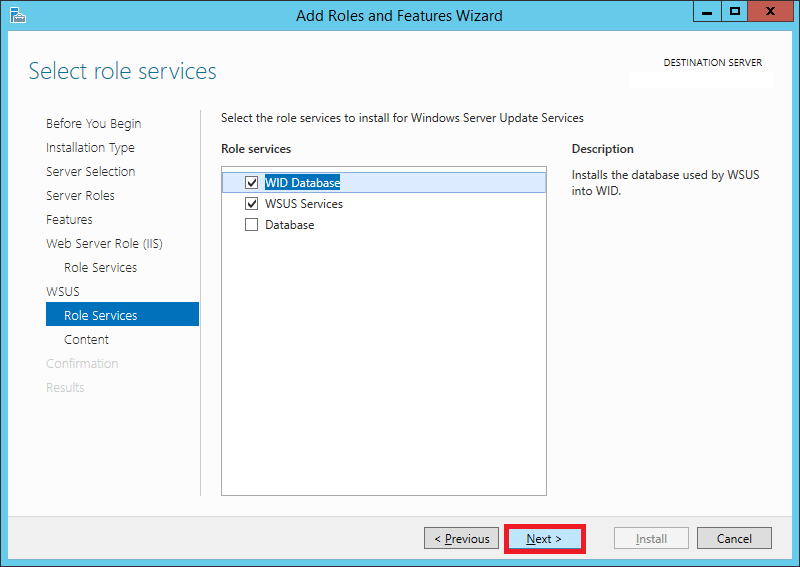
Step 14:
This page will allow you to set the destination directory for the downloaded updates. Tick the checkbox for Store updates in the following location.
Enter the path here. It can either be a local or a remote path.
Keep in mind that WSUS will take up considerable amount of storage as time goes on. It is not unusual to find update folders of sizes greater than 100 GB.
Choose your destination accordingly.
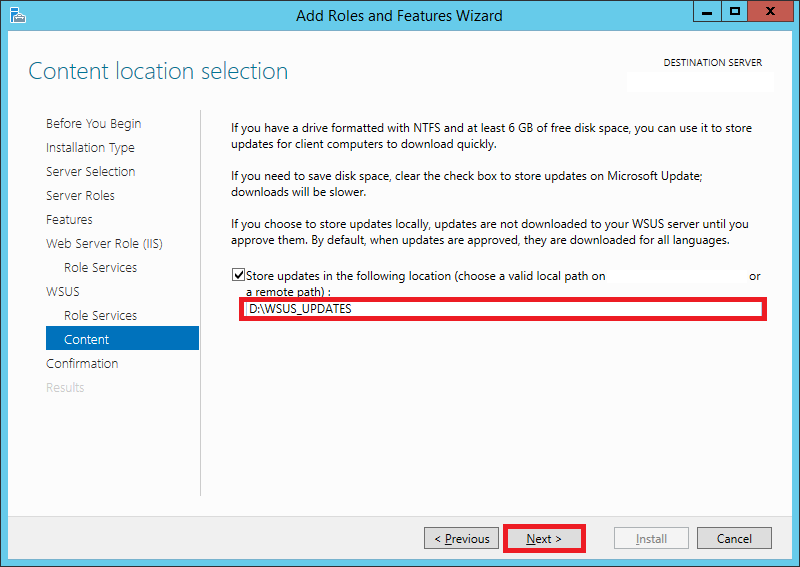
Step 15:
On the Confirmation screen, check the Restart the destination server automatically if required option if you wish to do so, otherwise you can leave it unchecked.
Click Install
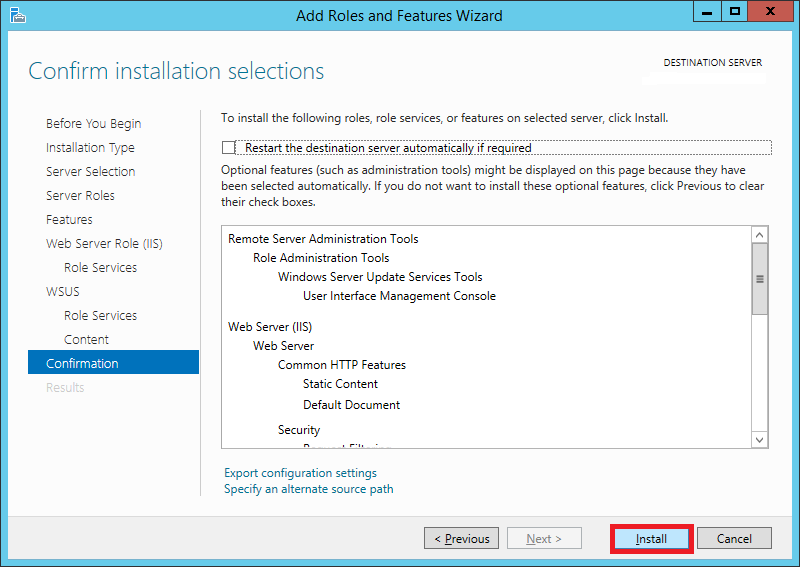
Step 16:
Sit back and grab a coffee. This will take about 5-10 minutes.
Step 17:
Once its installed, hit Close
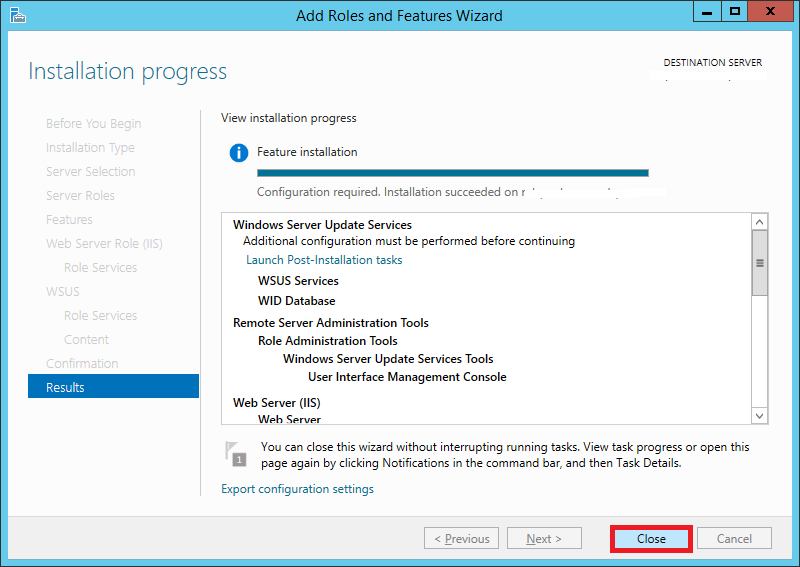
Step 18:
Search for WSUS or Windows Server Update Services and launch it
Step 19:
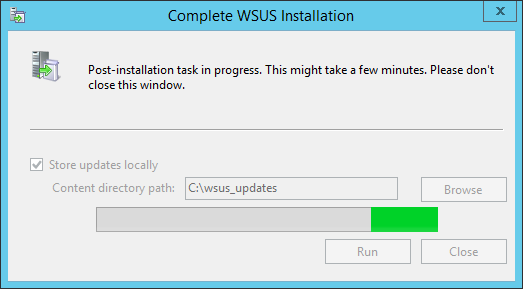
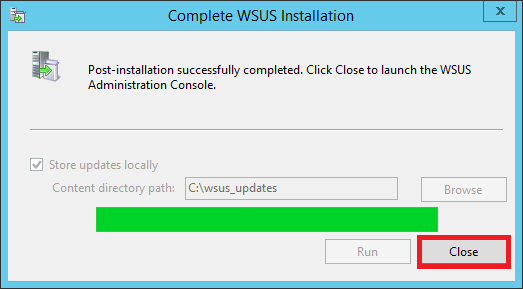
Since it’s the first time you’re opening it, it’ll take a while to set up. Wait for it to complete and then hit Close
Step 20:
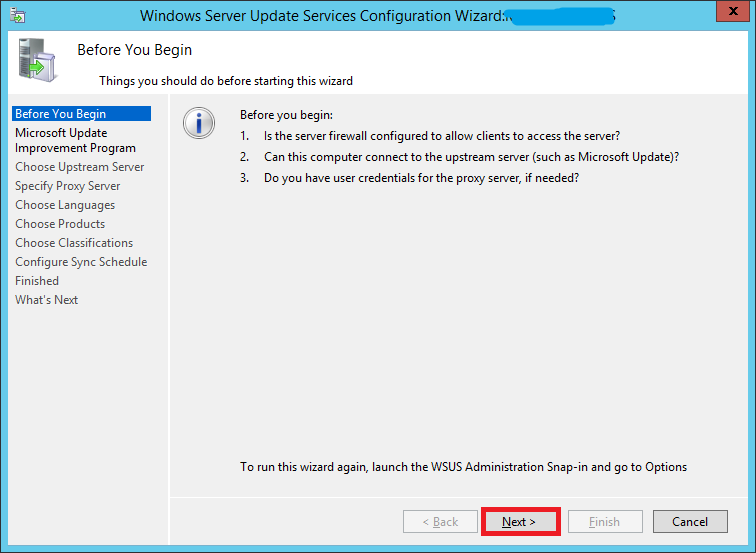
You will now see a wizard that will walk you through a series of steps to configure your installation.
Before starting, make sure of the following:
- Confirm whether the PCs on your network can communicate with this server.
- Your WSUS server should be able to communicate with Microsoft Update (Make sure your firewall isn’t blocking it)
- If your environment uses a proxy, make sure you have the proxy server credentials before continuing.
If all seems well, click Next
Step 21:
If you would like to join the Microsoft Update Improvement Program, check the box. Otherwise uncheck it. Click Next
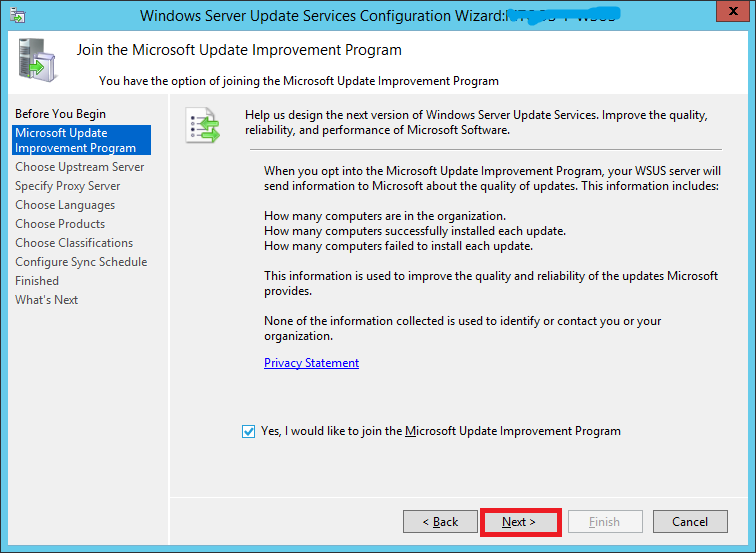
Step 22:
If you want to synch updates directly from Microsoft Update (the most likely scenario in your case since you’re reading this guide), enable the first option and click Next.
If you have already have a WSUS server in your environment and want your new WSUS to synch updates from that instead of Microsoft Update, enable the second option.
- Enter the server name and port number (For WSUS on Windows Servere 2012 R2, the default port is 8530)
- Enable/disable SSL based on your environment
- Decide whether it is going to be a replica server or not and click Next
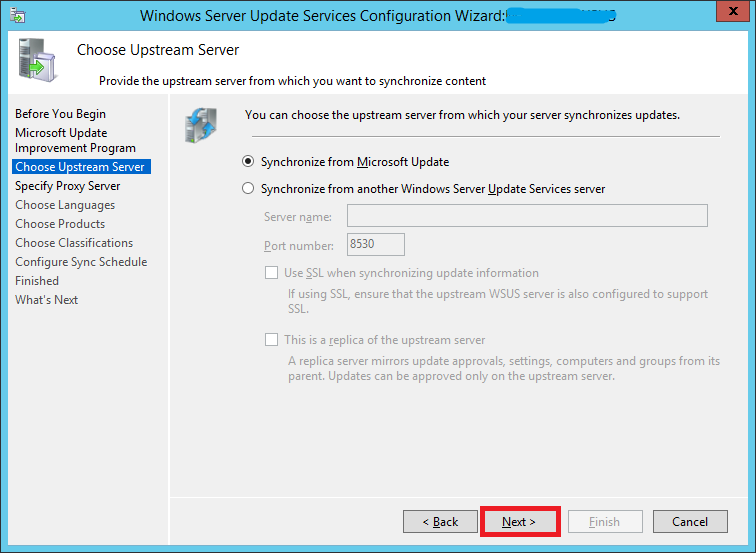
Step 23:
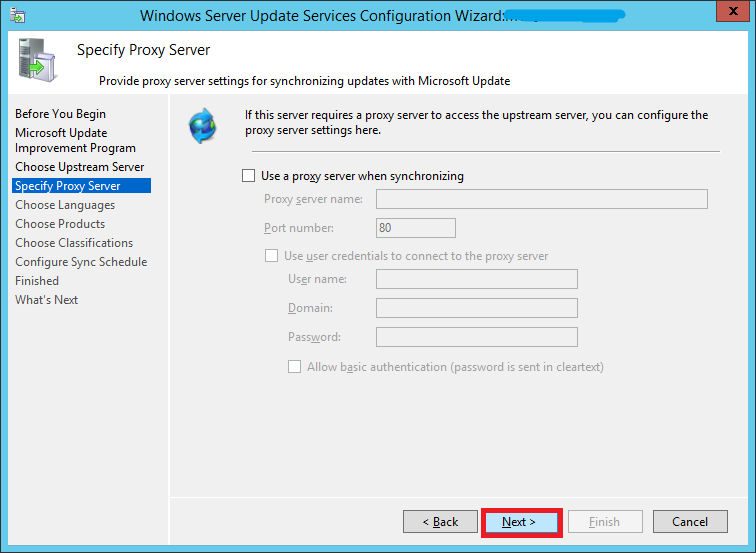
If you use a proxy server, enter the details here, otherwise leave the checkbox unchecked and click Next
Step 24:
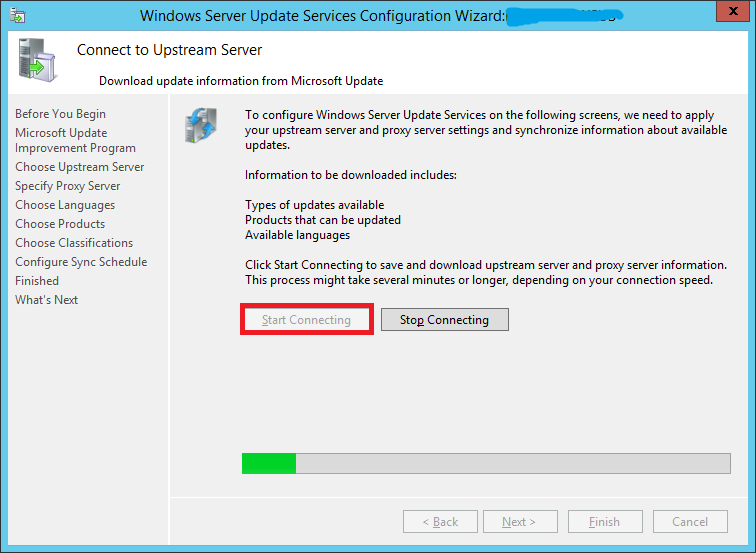
Your server will now need to connect to Microsoft Update and find out information about all available updates.
Click Start Connecting. This might take upto 20 minutes or more depending upon your connection.
Once it’s done, hit Next
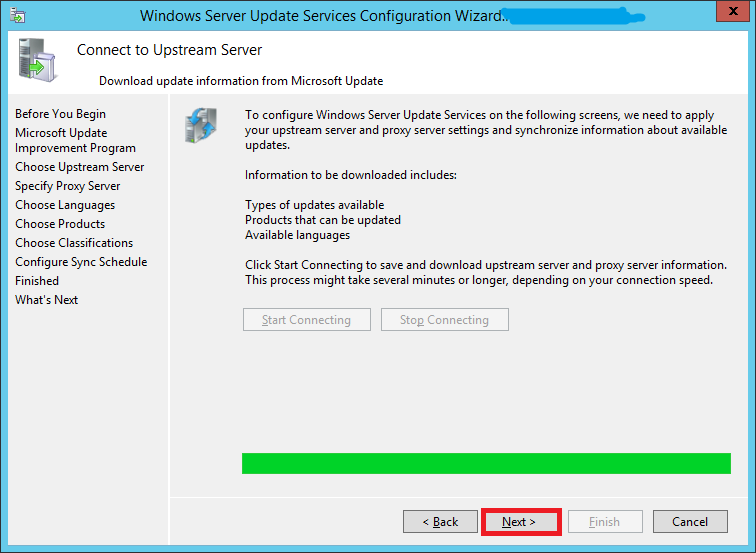
Step 25:
Choose which all languages do you need updates for and click Next. You can always modify this later.
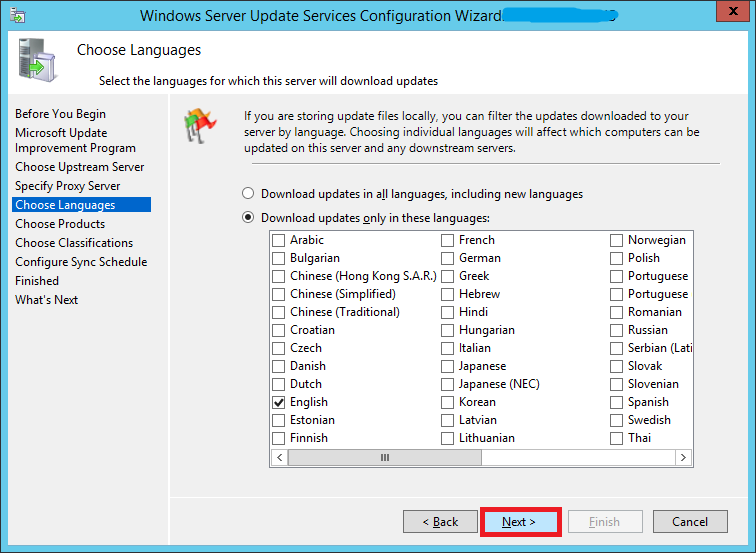
Step 26:
The Choose Products screen will allow you to subscribe for updates for different Microsoft products.
After selecting your products, click Next
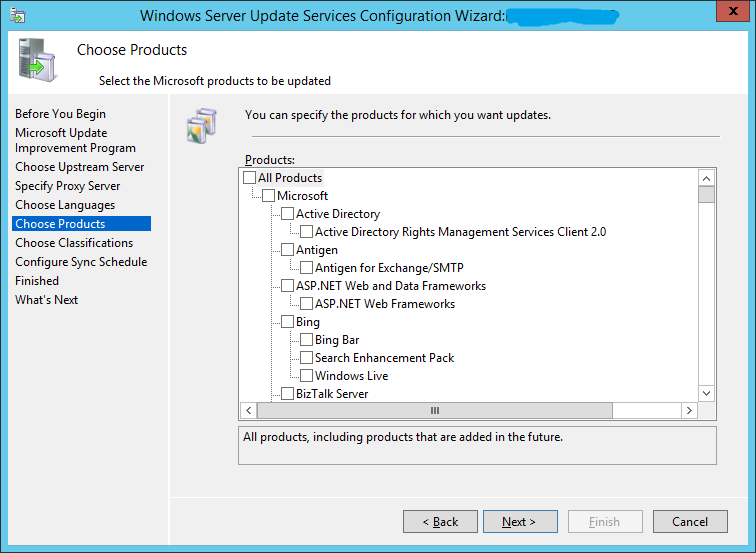
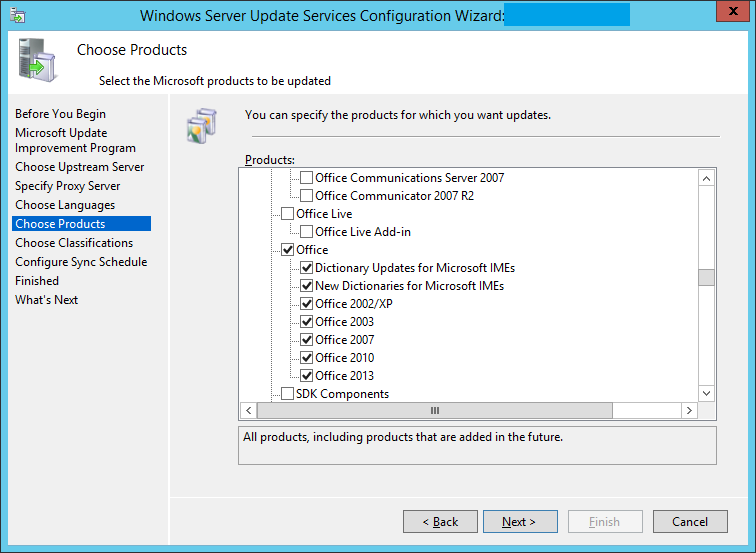
Step 27:
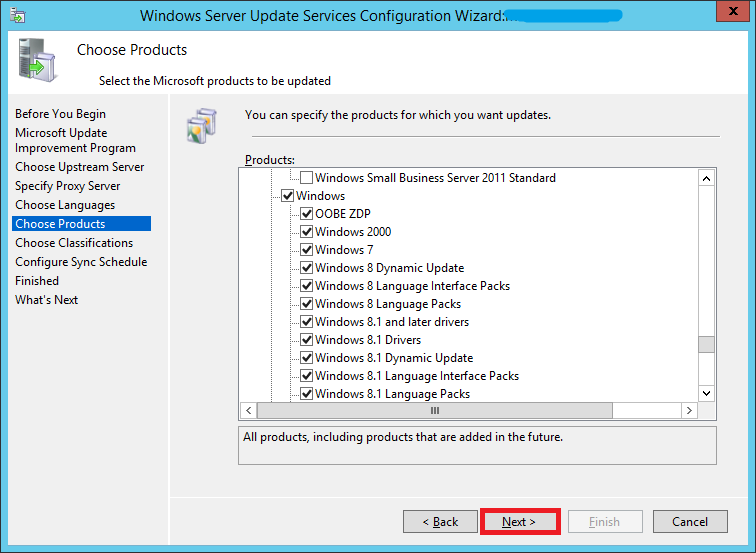
Here you can choose what type of updates you want to subscribe to. Do you want just critical & security updates? Or do you want everything? This is where you can specify that.
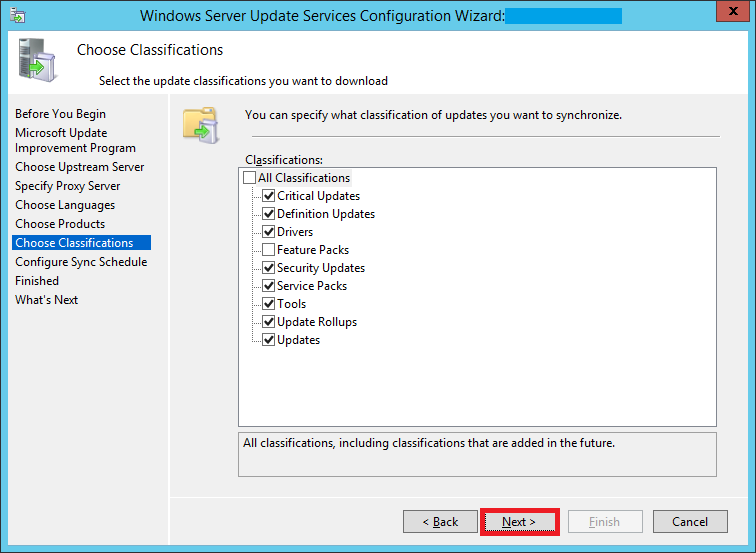
Step 28:
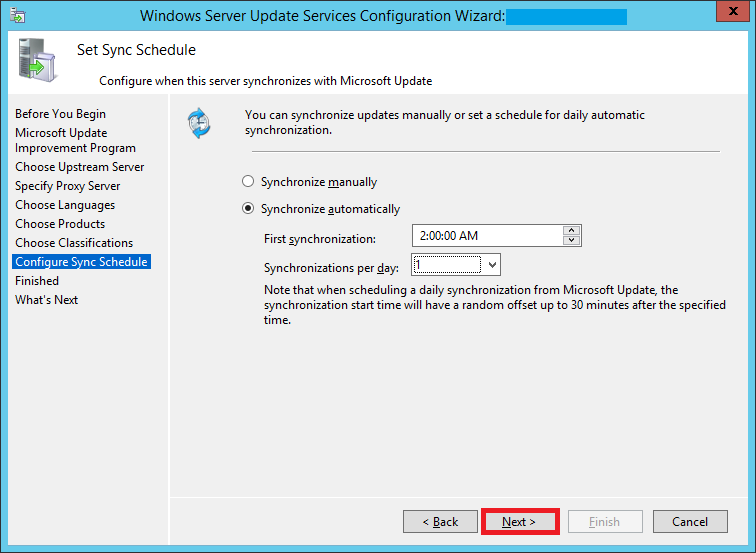
Configure your sync schedule for updates here. The synchronization process involves downloading updates from Microsoft Update or another WSUS server. WSUS determines if any new updates have been made available since the last time you synchronized. If this is the first time you are synchronizing the WSUS server, all of the updates are made available for approval.
I chose to automatically sync my server with Microsoft Update daily at 2 AM.
Step 29:
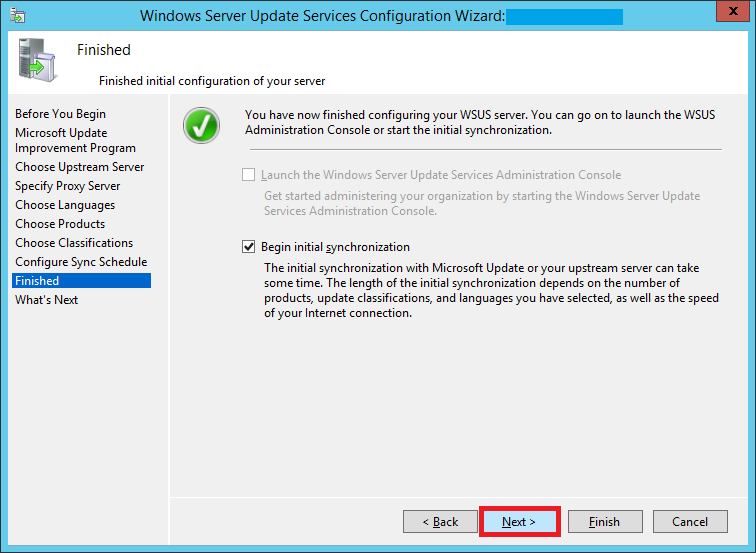
Select Begin initial synchronization to sync with Microsoft Update and click Next and then Finish

Step 30:
The Update Services console will now launch.
This is going to be the place from where you can control everything.
Right now, under the To Do section, you will not see much. Wait for the server to synchronize with Microsoft Update. Once it syncs, you will see information like how many updates are available, how many are approved, etc.
Under the Overview section, you can see the Synchronization Status.

Synchronization status is now 12%
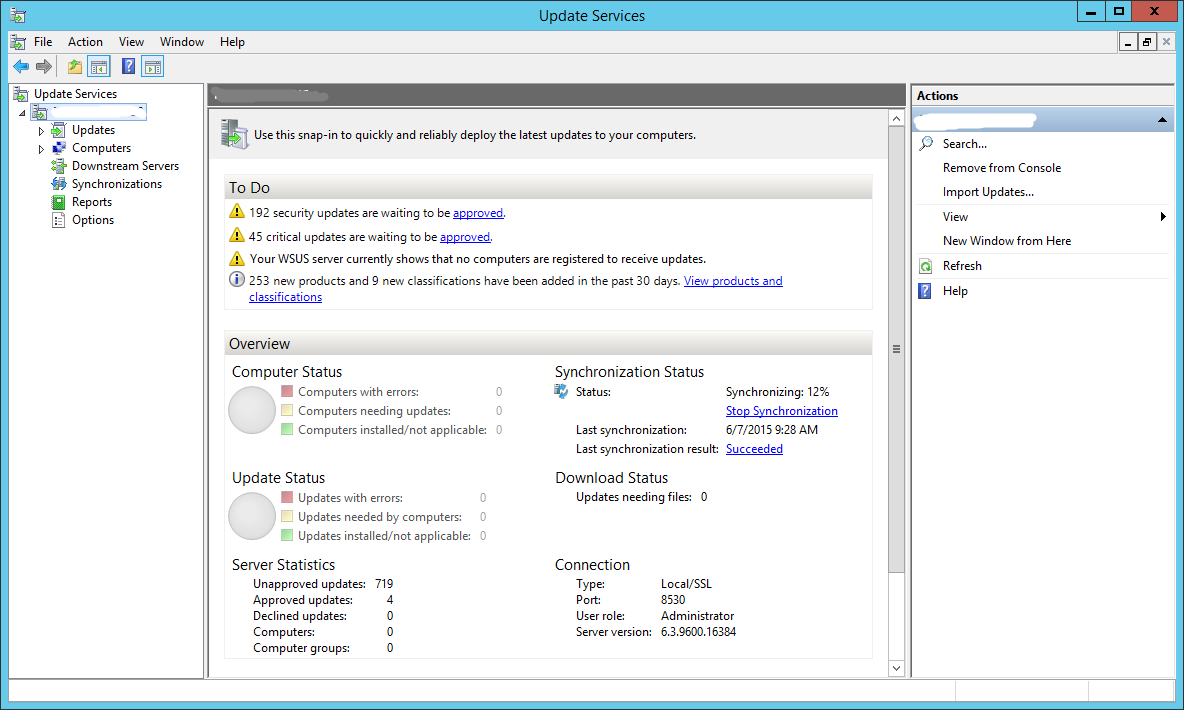
Step 31:
Synchronization is finally complete. You can now see the number of updates that are available to you under the To Do section.
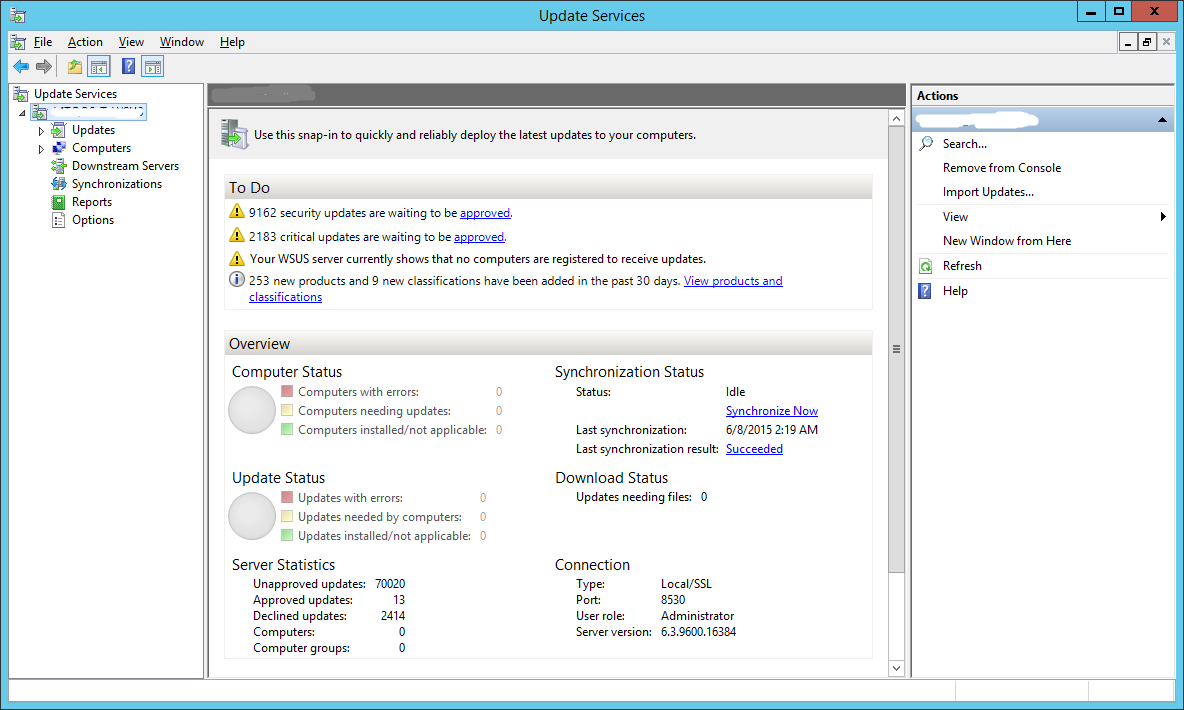
This completes the installation and initial configuration of our WSUS server. However, this server is not going to be much use to you right now. It still isn’t pushing any updates to your workstations still.
Lets fix that.
Step 32:
We will be using a GPO to register the workstations on our network with our newly created WSUS server.
Fire up your Group Policy Management console. Right-click Group Policy Objects and create a new GPO.
Give it an easy-to-identify name.
After its created, right-click and choose Edit. We will now configure the GPO.
Step 33:
Expand Computer Configuration > Policies > Administrative Templates > Windows Components > Windows Update
Step 34:
Double-click Configure Automatic Updates
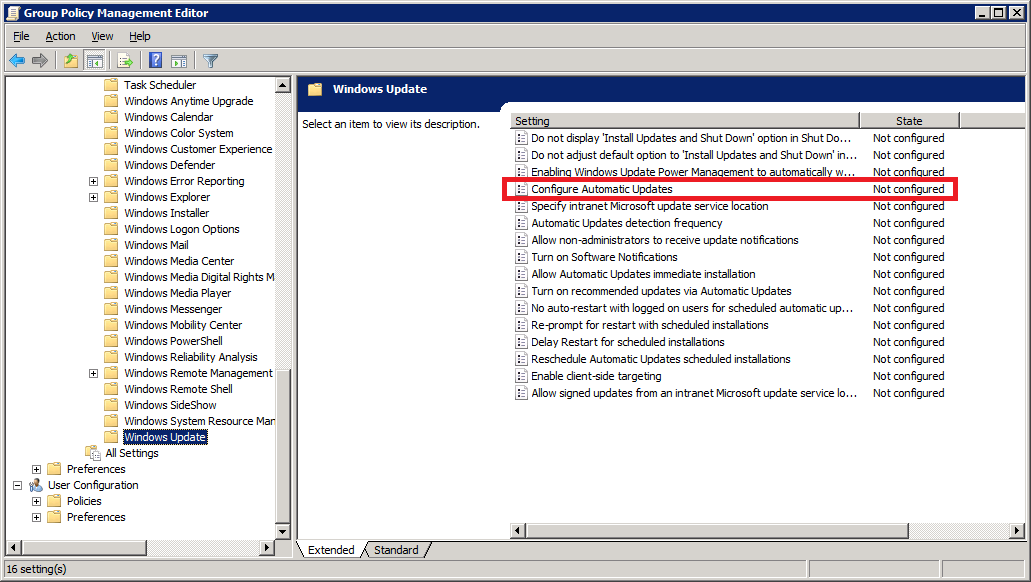
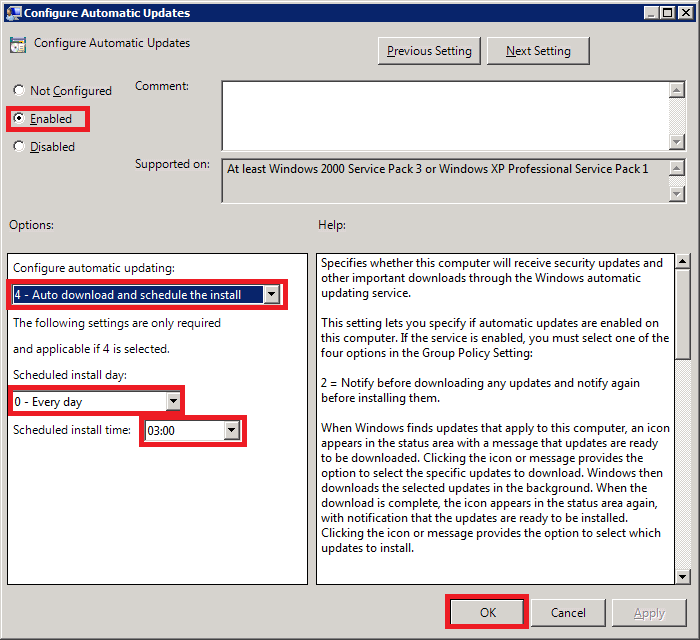
Select Enabled
Under Options, choose how would you want your workstations to update. In my case, I prefer the PCs to download the updates and schedule them to be installed at 3 AM daily.
Once you are satisfied with the options, click OK to exit the screen.
Step 35:
Next, double-click Enable client-side targeting.
Configuring this setting will enable the workstations on your network to register directly with your WSUS server (client-side registration).
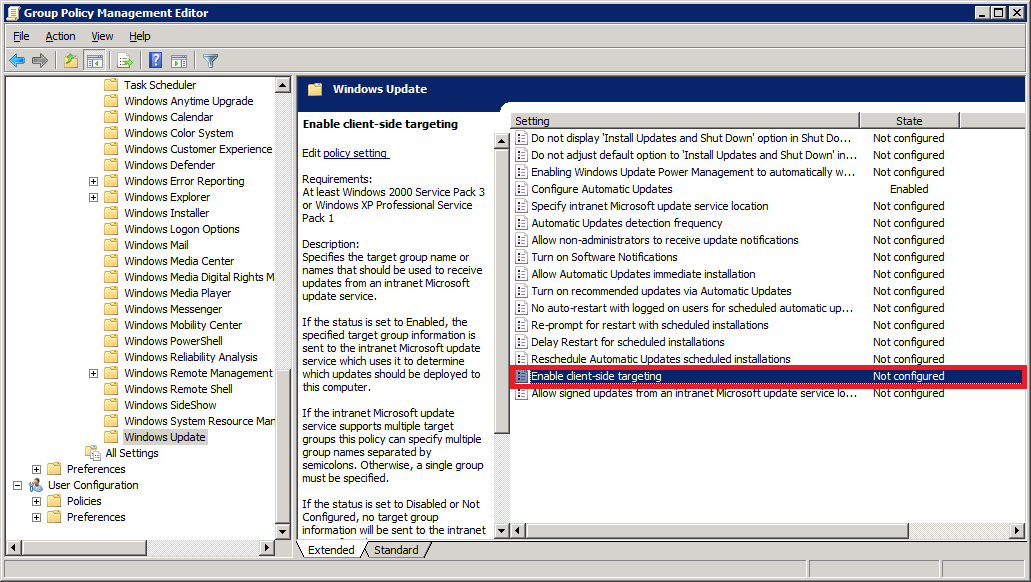
Select Enabled.
In the Options area, type the group name for this computer (Your WSUS server can use this information to group computers into different groups. We will see how this is done further below).
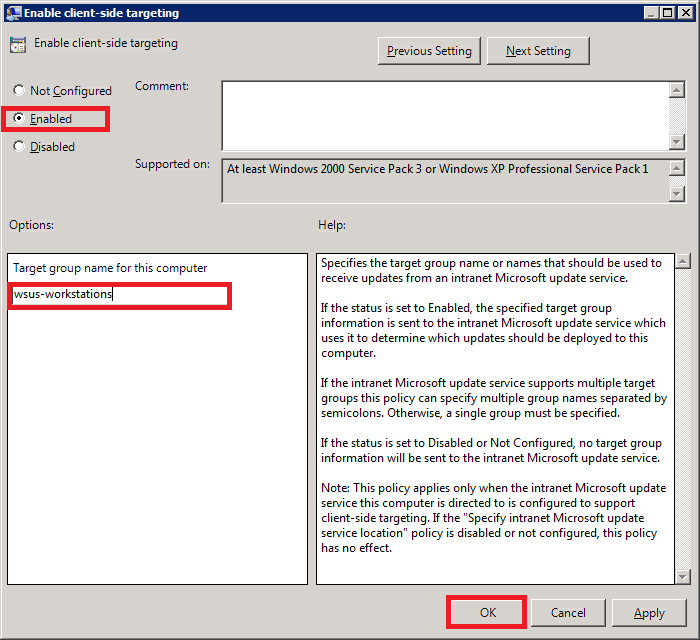
Step 36:
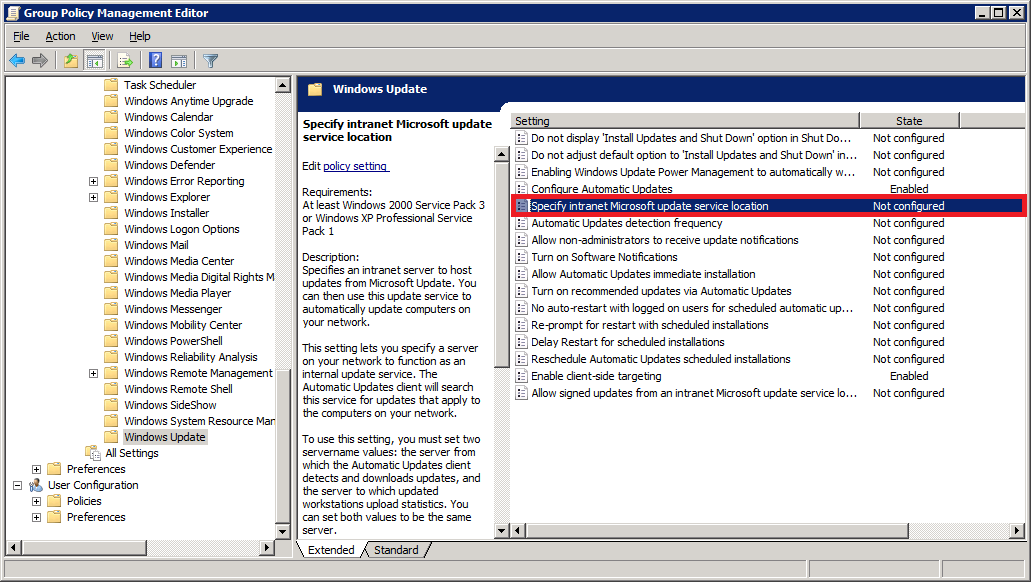
Next, double-click on Specify intranet Microsoft update service location.
This is where you will specify your WSUS server’s address.
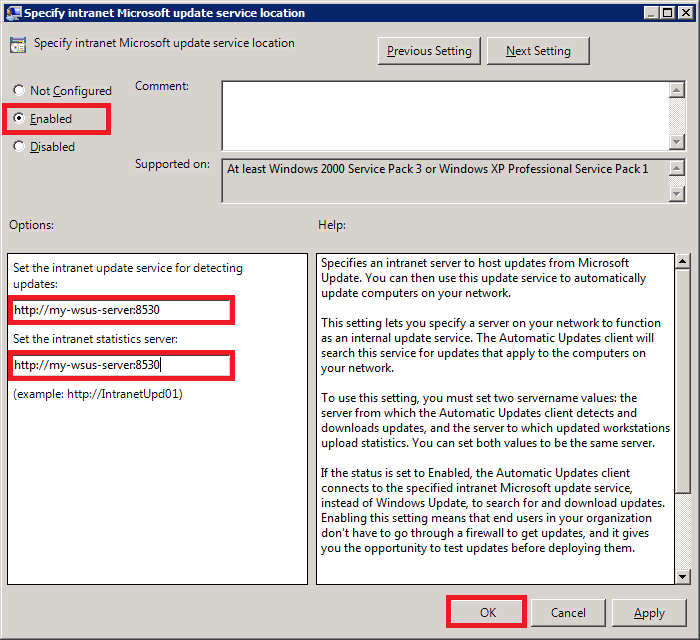
Select Enabled.
In the Options area, specify your server name in the form of a URL as shown below.
My WSUS server’s hostname is my-wsus-server. The default port number for WSUS on Windows Server 2012 R2 is 8530, so my complete server address is:
http://my-wsus-server:8530
Enter the same URL in both the text boxes and click OK.
Step 37:
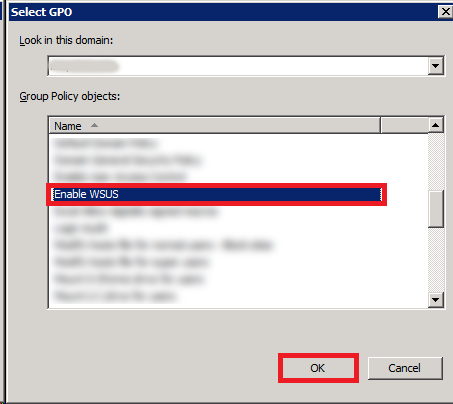
Well, the last step is to link the GPO to an OU. Select an OU which has your test computer. Right-click it and select Link an Existing GPO.

Choose your newly created GPO and click OK.
Step 38:
Let’s go back to our WSUS server and create a new computer group. By default, under All Computers, you’ll see a default group called Unassigned Computers. Any computer that doesn’t belong to a group will appear here.
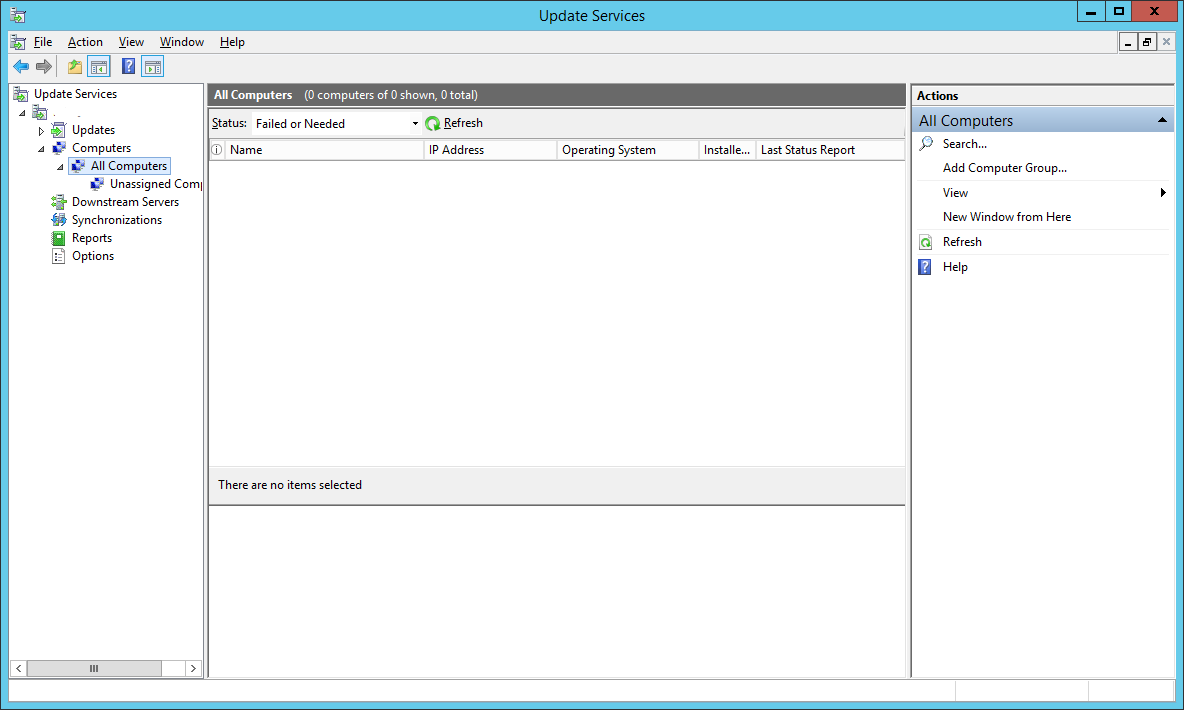
Right-click All Computers and select Add Computer Group…
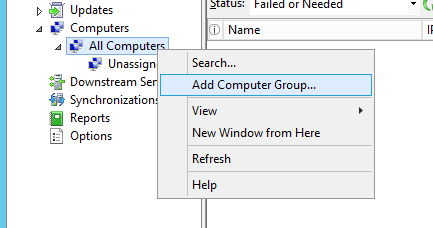
Enter the name of the group. I entered the same group name that I had specified in my GPO (Step 35).
Click Add.
Step 39:
Now, we can either wait for the GPO to be automatically applied to our test computer or, if you are impatient like me, we can speed things up.
Log into your test computer.
Open up Command Prompt as Administrator and run 3 commands as shown below.
gpupdate /forcewuauclt.exe /detectnowwuauclt.exe /reportnow
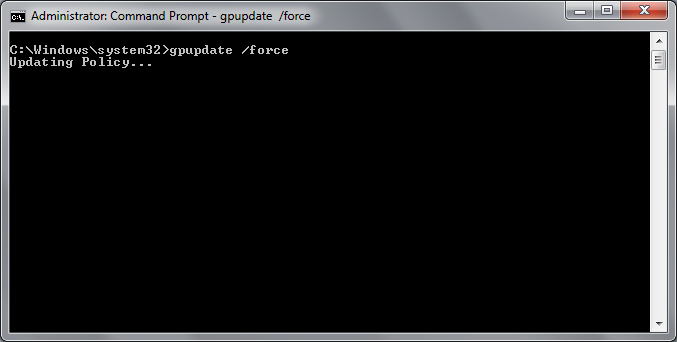
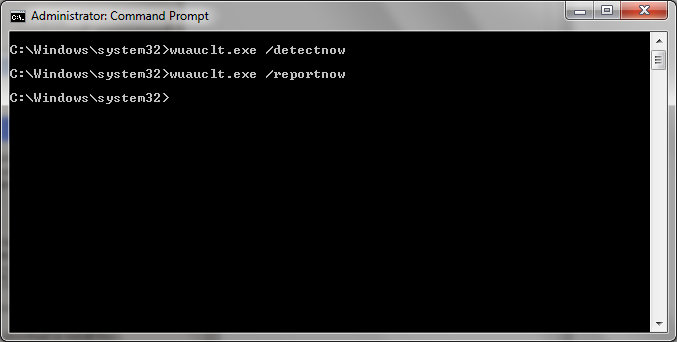
Step 40:
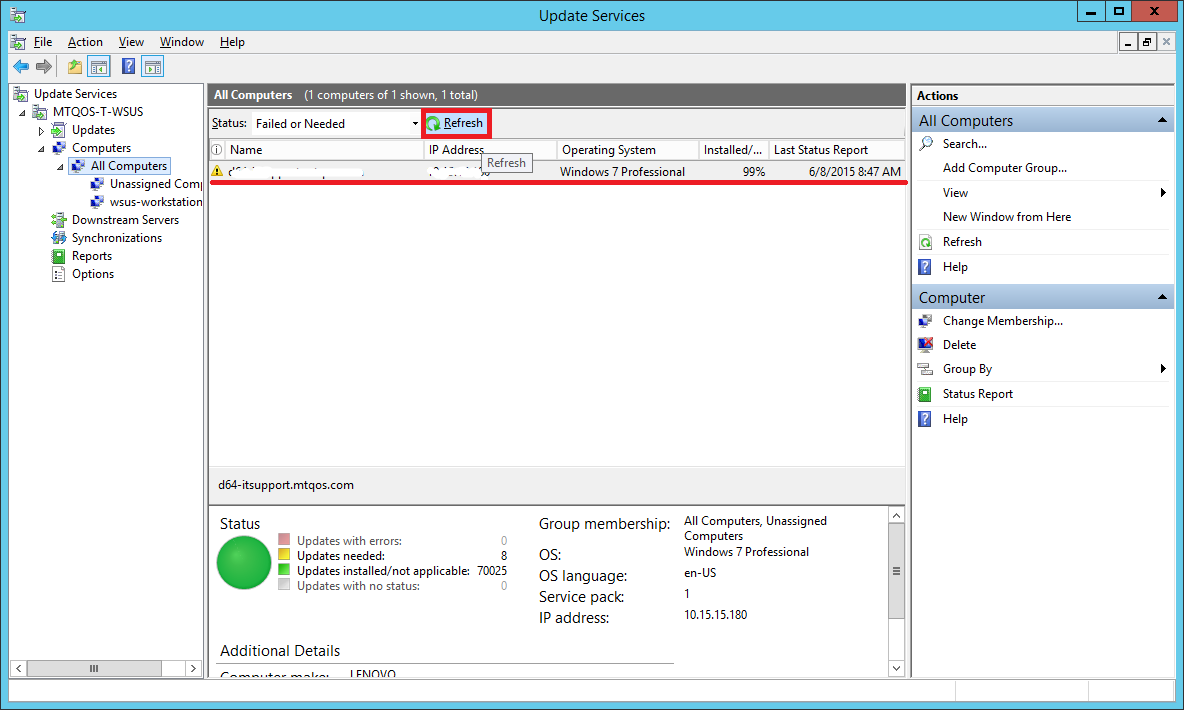
Go back to your WSUS server. Select All Computers group.
Hit refresh.
You will see that your test computer has appeared in the list.
If you don’t see your test computer here, do the following:
- Wait for about 5 minutes and hit Refresh again. Sometimes it takes a while for the PCs to show up even if you have run the above commands.
- Double-check your GPO settings. Make sure you linked it to the correct OU. The OU should have your test computer account and not the user account since its a Computer Configuration policy.
- Run the commands (specified in Step 39) again on your test computer. Make sure you run them from an elevated command prompt.
- Reboot your test computer.
Step 41:
You will notice that even though you have specified the computer to be added to a group wsus-workstations in the GPO, the test computer still appears under Unassigned Computers.
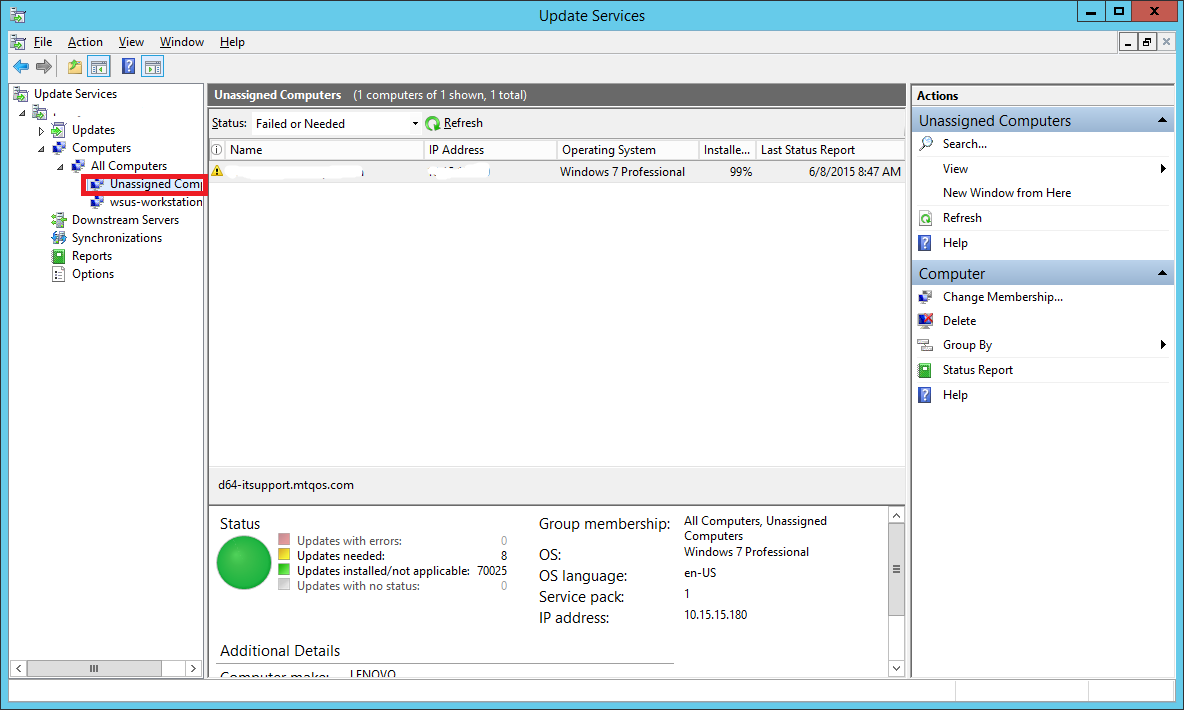
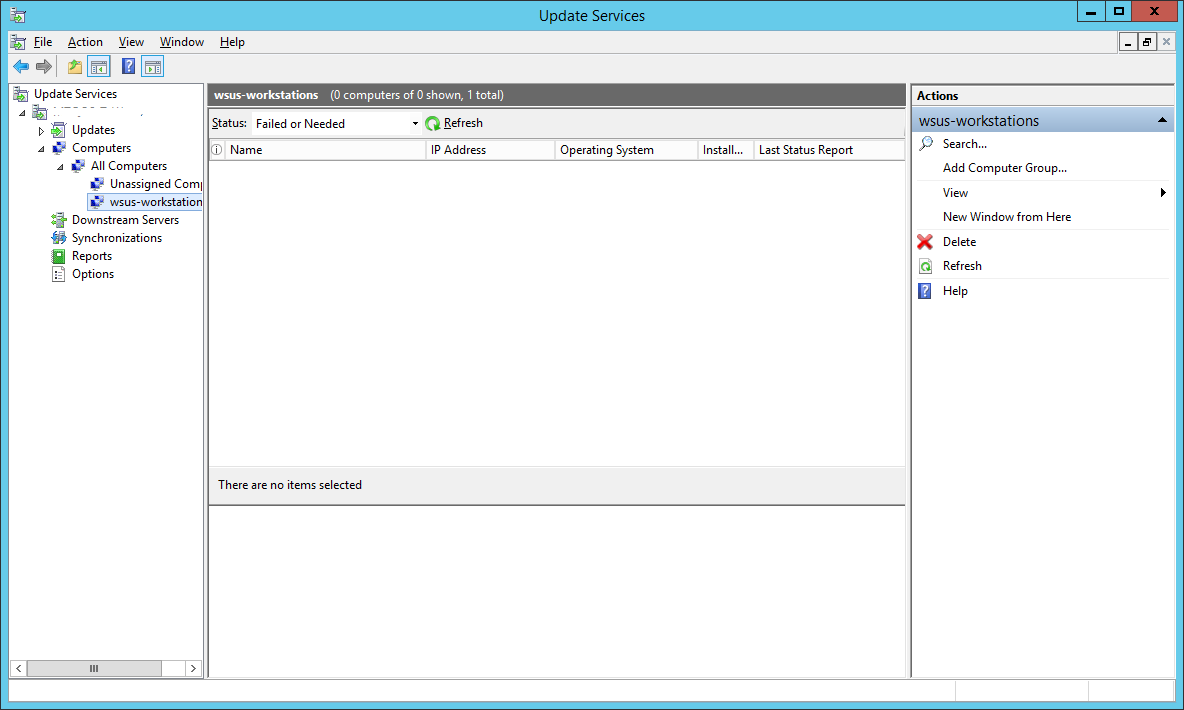
Well, that’s because by default, WSUS ignores the groups and places all discovered computers in the Unassigned Computers group. You can then manually move it to whichever group you want.
You can change this setting. If you want the computers to automatically add themselves to the group specified in the GPO, do the following.
In your Update Services console, select Options. Double-click on Computers
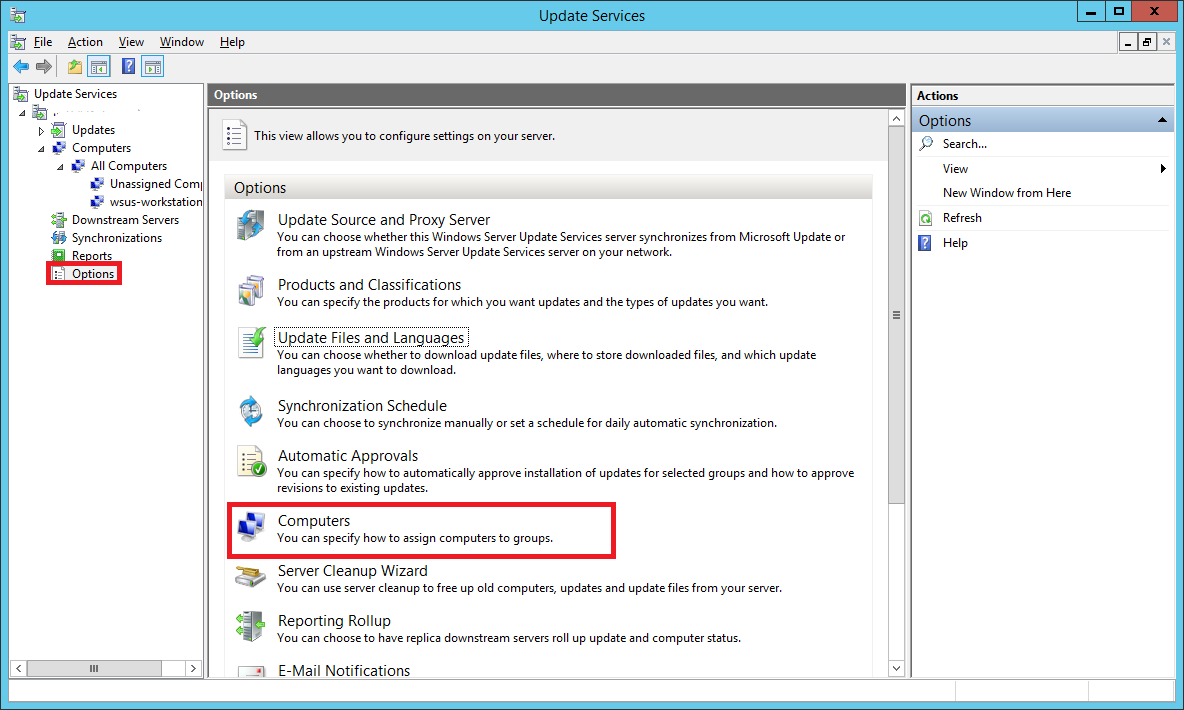
Choose the second option that says Use Group Policy or registry settings on computers.
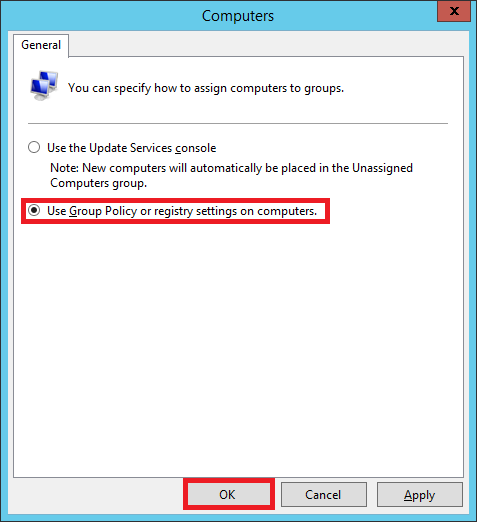
Now any computer that your GPO will apply to, will automatically appear in the group wsus-computers instead of Unassigned Computers.
You can make different GPOs for machines that you want to be grouped differently.
Step 42:
Now, since we have added a test computer, lets see how we can push updates to it.
In your WSUS console, expand the Updates tree and select All Updates. You will see updates which are needed and that are not yet approve.
You will have to Approve them so that they can be pushed out to your test computer.
Select the updates you want to approve using the Shift or Ctrl key.
From the Actions sidebar on the right, select Approve… (you can also right-click the selected updates and do the same)
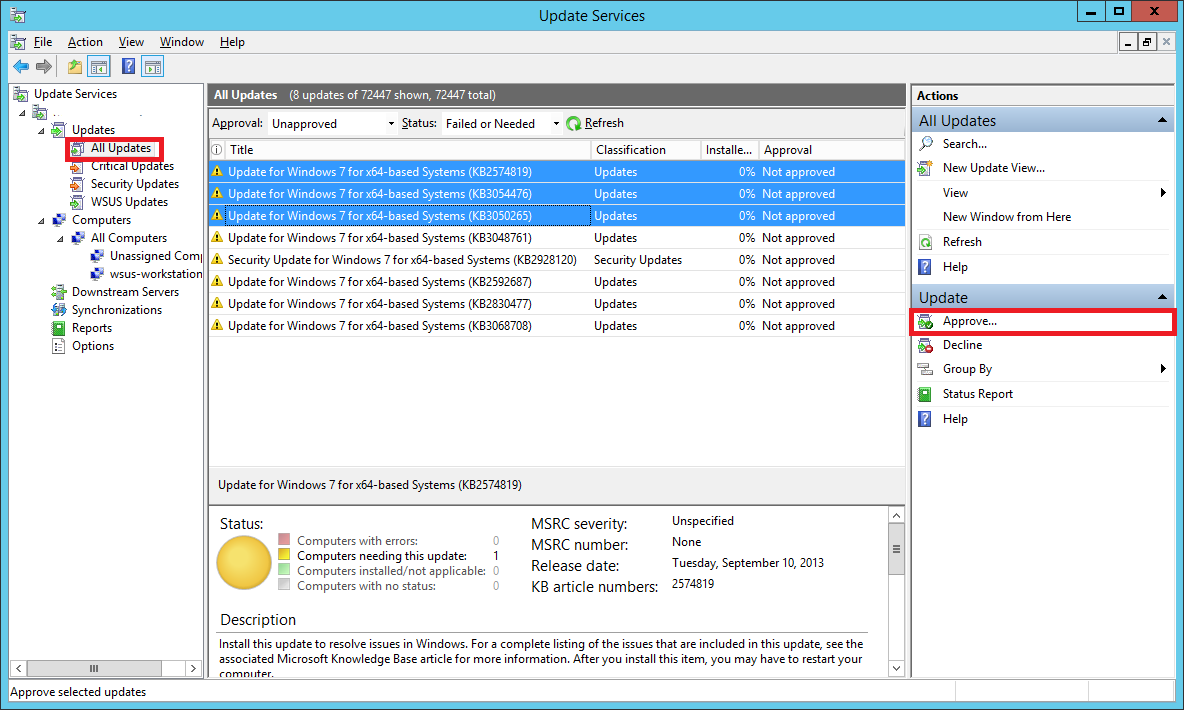
In the window that pops up, right-click All Computers and select Approved for Install.
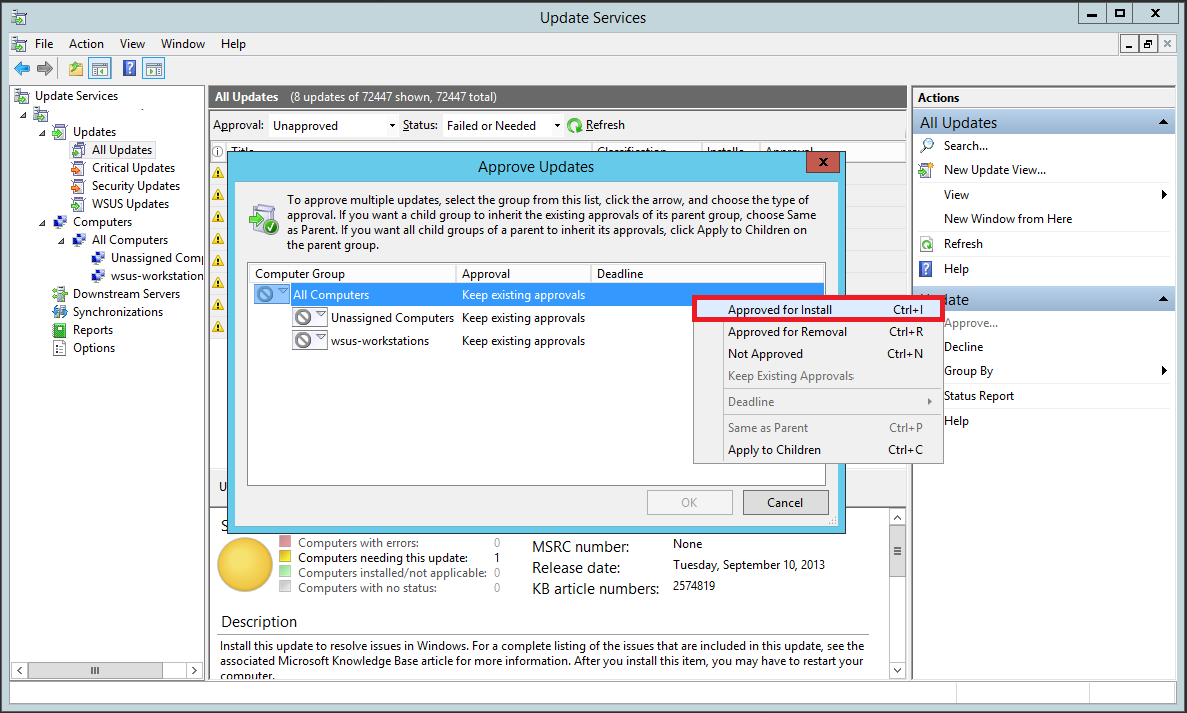
You’ll notice that the updates haven’t been approved for the groups individually. Right-click All Computers again and select Apply to Children. This will approve updates for all the children groups under All Computers.
Since you have just one test computer right now, we have approved it for all the computers. However, in a production environment you should first approve the updates to a test group (instead of all computers) to see if the updates cause any sorts of problems. Once you are certain the updates don’t break anything, you can push it to the critical machines.
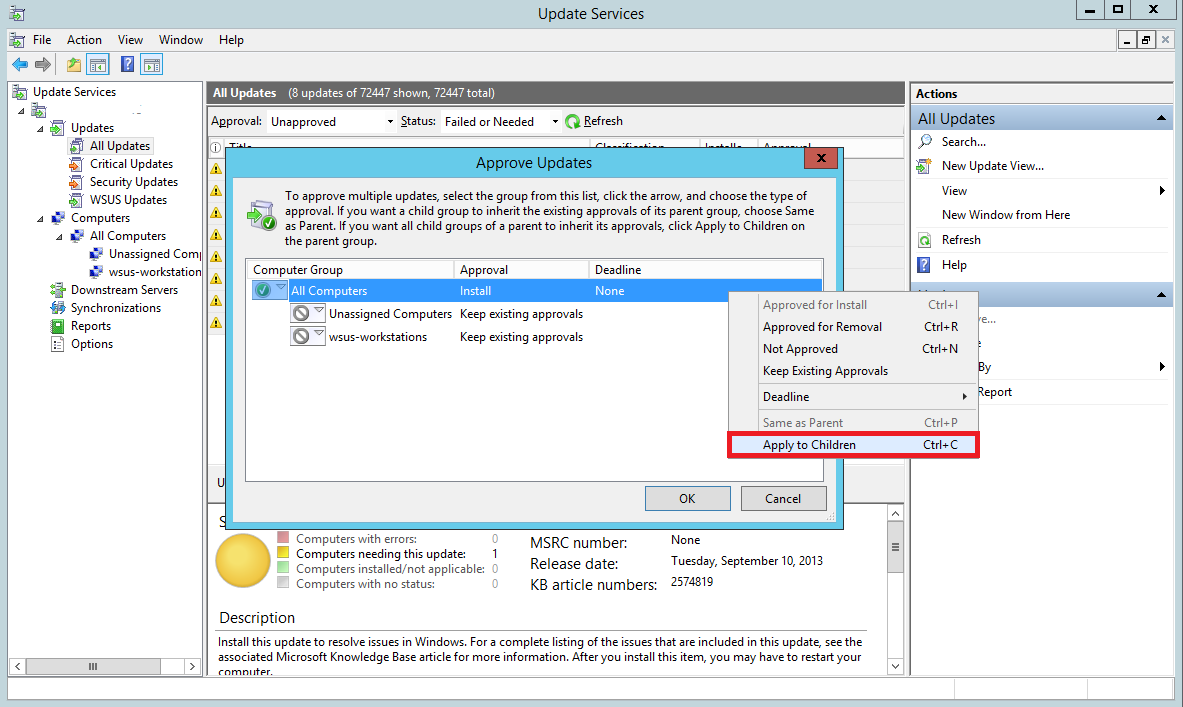
Select OK
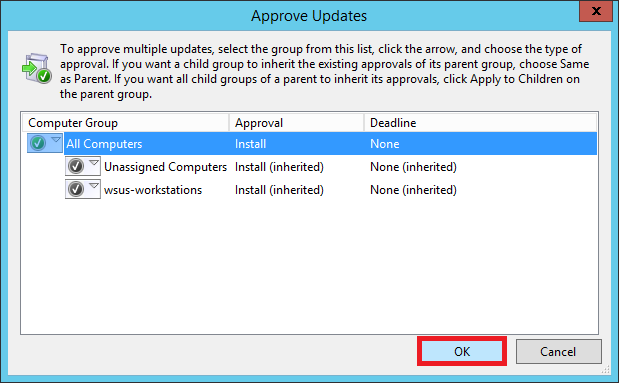
The updates have been approved. Now during the scheduled time (3 AM in our case), these updates will be pushed to out test computer.
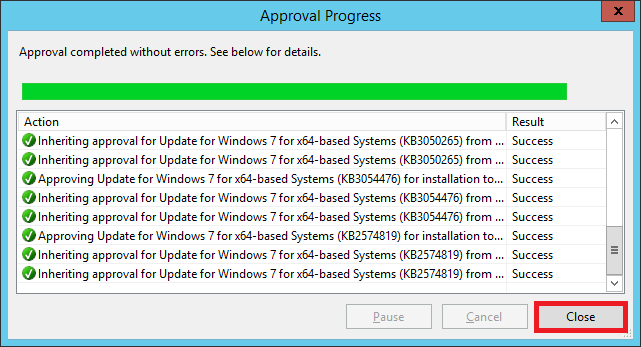
That’s it! Our WSUS server is now set up.
Hope this guide was useful to you. You can leave your feedback in the comments below.
Windows Server Update Services (WSUS) in Server 2012 R2
Table of Contents
Windows Server Update Services (WSUS) enables the administrators to deploy the latest Microsoft product updates. You can use WSUS to fully manage the distribution of product updates onto your organization computers. A WSUS server can also be the update source for other WSUS servers within the organization. The WSUS server that acts as an update source is called an Upstream Server and the server that connects to the upstream server in called Downstream Server. In a WSUS implementation, at least one WSUS server on your network must be able to connect to Microsoft Update to get available update information.
Note: Upgrade from any version of Windows Server that supports WSUS 3.2 to Windows Server 2012 R2 requires you to first uninstall the WSUS 3.2
Install the WSUS Server Role
-
- Log on to the server on which you plan to install the WSUS server role by using an account that is a member of the Local Administrators group.
- In Server Manager, click Manage, and then click add Roles and Features.
- On the Before you begin page, click Next.
- In the select installation type page, confirm that Role-based or feature-based installation option is selected and click Next.
5. On the select destination server page, choose where the server is located (from a server pool or from a virtual hard disk). After you select the location, choose the server on which you want to install the WSUS server role, and then click Next.

6. On the select server roles page, select Windows Server Update Services. To Add features that are required for Windows Server Update Services, click Add Features, and then click Next.

7. On the Select features page, keep the default selections, and then click Next.
8. On the Windows Server Update Services page, click Next.
9. On the Select Role Services page, choose your preferred database type and then click Next. If you are already have a SQL server on same server (or on different server), you can go ahead and uncheck the WID Database option, then check the Database option. If you choose SQL database, you will have to provide SQL connection details as shown in following diagram:
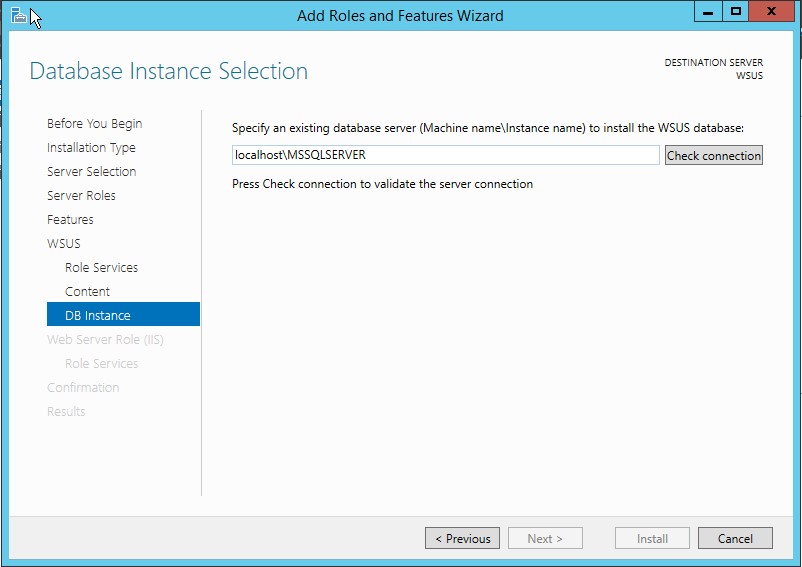
If you want to use Windows Internal Database (WID), just select WID Database and WSUS services option and click Next as shown in following diagram:
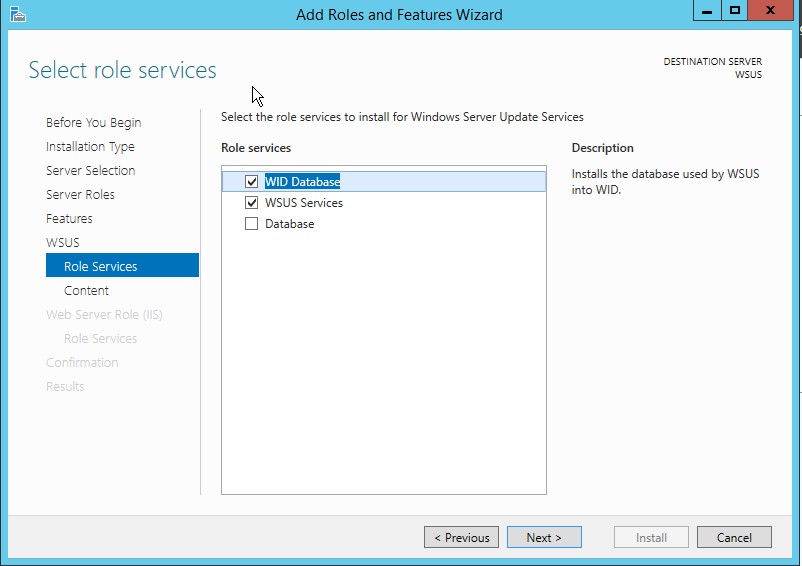
Tip: You must select one Database type. If the database options are all cleared (not selected), the post installation tasks will fail.
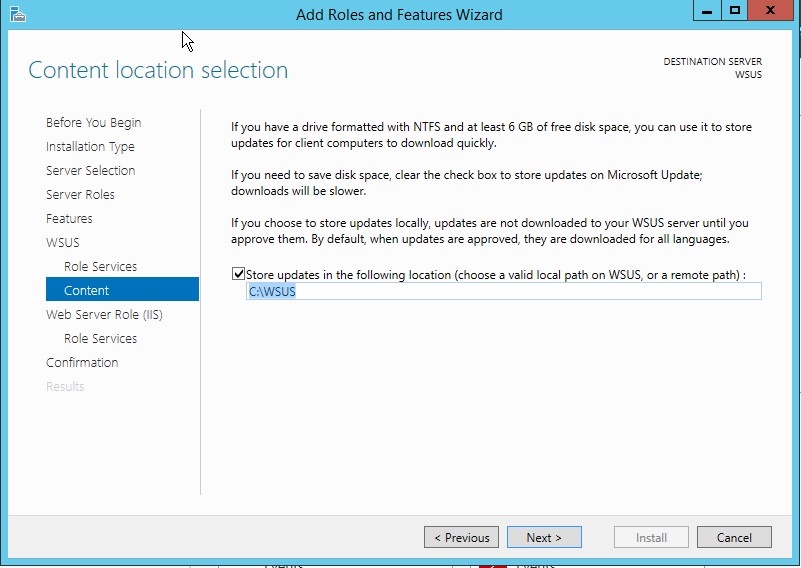
10. On the Content location selection page, type a valid location to store the updates. For example, you can create a folder named WSUS at the root of drive C: specifically for this purpose, and type C:\WSUS as the valid location.
11. Click Next. The Web Server Role (IIS) page opens. Review the information, and then click Next. In select the role services to install for Web Server (IIS), keep the defaults, and then click Next.
12. On the Confirm installation selections page, review the selected options, and then click Install.
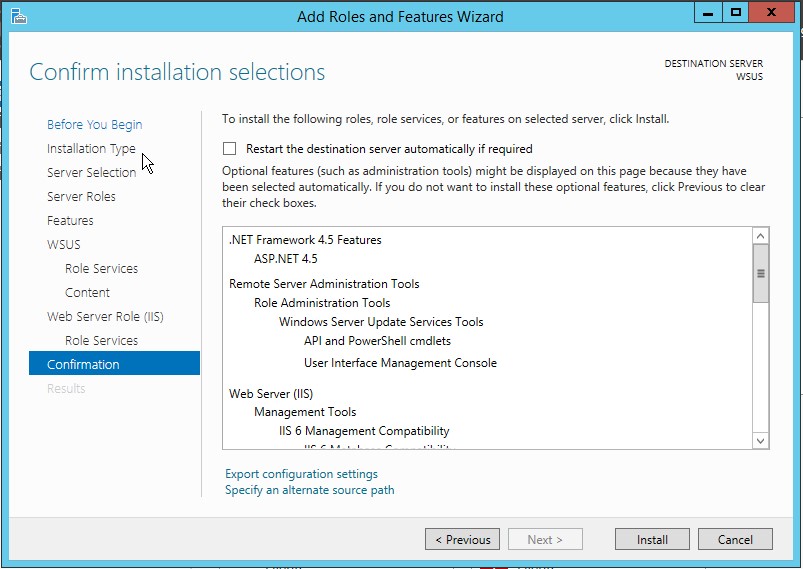
The WSUS installation wizard runs. This might take several minutes to complete.
13. Once WSUS installation is complete, in the summary window on the Installation progress page, click Launch Post-Installation tasks. The text changes, requesting: Please wait while your server is configured.
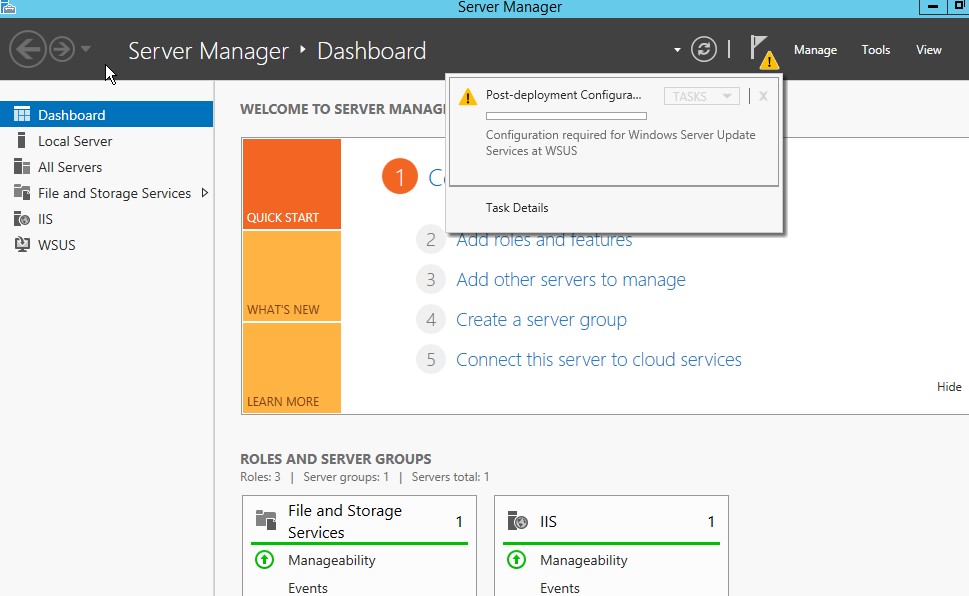
When the task has finished, the text changes to: Configuration successfully completed. Click Close.
14. In Server Manager, verify if a notification appears to inform you that a restart is required. This can vary according to the installed server role. If it requires a restart make sure to restart the server to complete the installation.
WSUS Configuration
- Launch WSUS console.

2. When WSUS Configuration wizard opens up, click Next
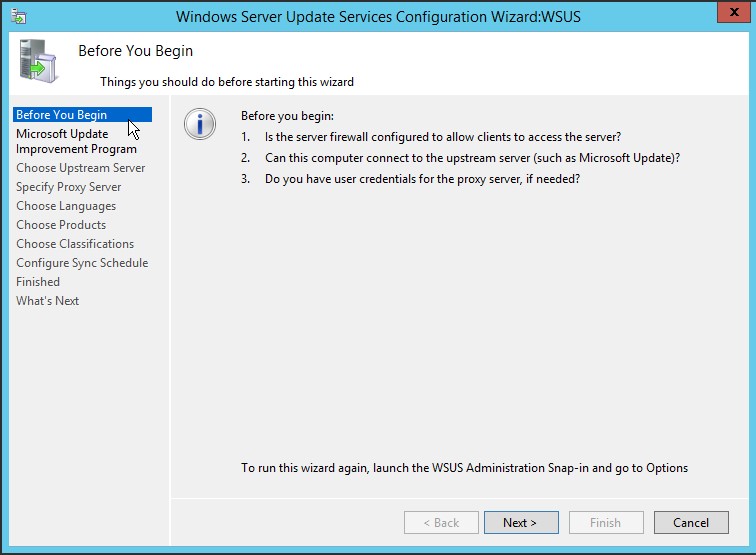
3. Now you are asked to participate into Microsoft Update Improvement plan. If you are fine with Microsoft collecting some information about your organization (like how many computers your organization have, how many computers successfully installed each update etc.), select the checkbox Yes, I would like to join Microsoft Update Improvement Program and click Next.

4. Next screen is to configure your upstream server which defines Where does this WSUS server will download the updates. You can either select Synchronize from Microsoft Update (which is default) or select Synchronize from another Windows Server Update Services server. If this is the first WSUS server in your organization, you should select first option so that the server can download the updates directly from Windows Update. Make sure to adjust your firewall settings for both cases. If you choose to connect to Windows Update, make sure your server has access to internet or if you choose to connect to an upstream server, be sure to allow Port 8530 or 8531 (SSL) on both servers.
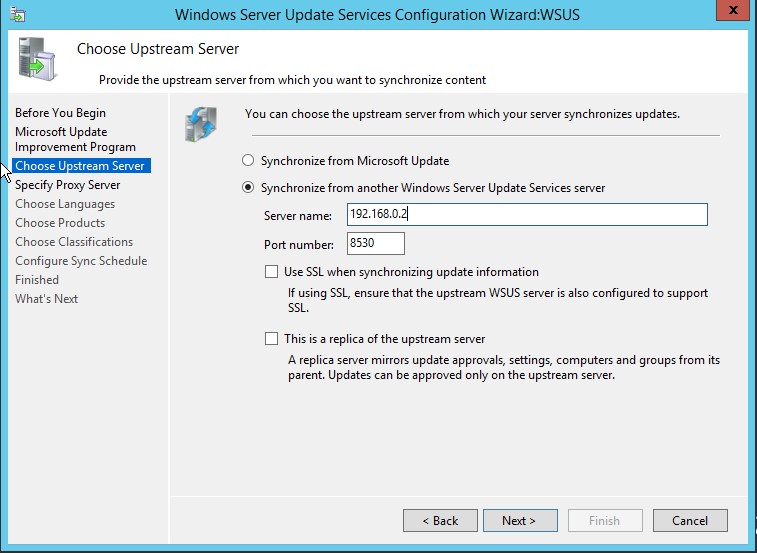
In my case, I already have a WSUS server on 192.168.0.2 server, I will choose to download updates from this server. You can also make this server as a replica server. Replica server picks all the configuration from upstream server and you can not directly approve any update on Replica server, it can only deploy the updates to computers.
5. Next step is to choose Proxy settings, If you use proxy to connect to internet, you can enter the details here. If not, leave everything at its default setting.
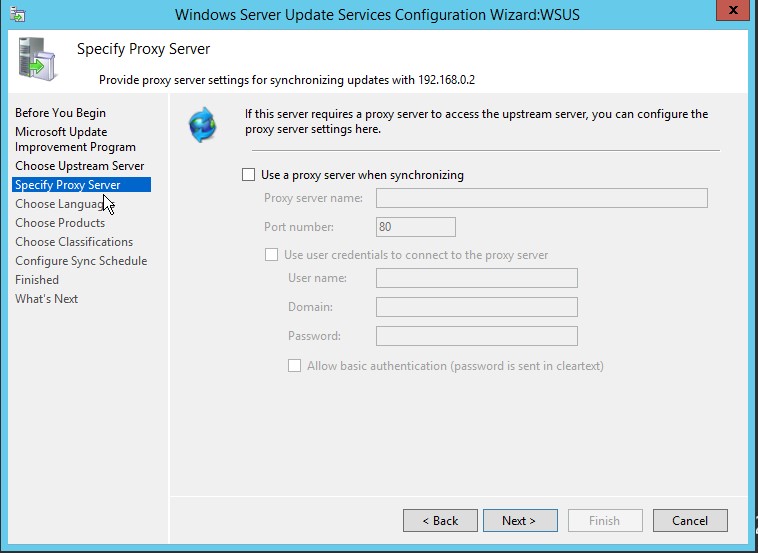
6. Now, click Start Connecting. It will take some time to complete the operation.
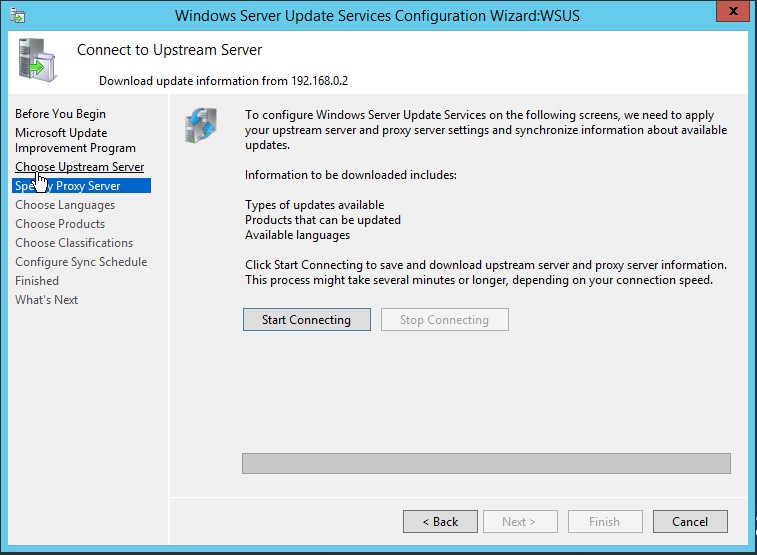
When progress bar turns all green, click Next.
7. On Language selection screen, select the language for your products and click Next.
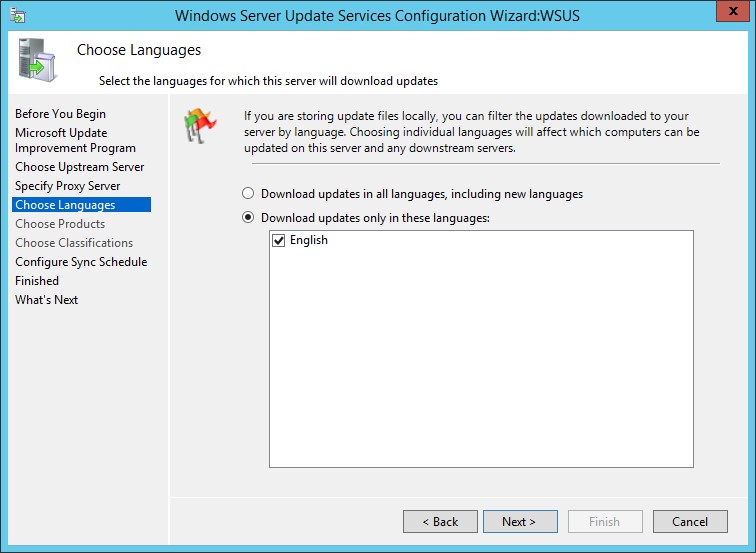
8. Next step is to configure the Sync schedule. If you choose to Synchronize manually, server will not check for new updates and will not download any update until you run the synchronization
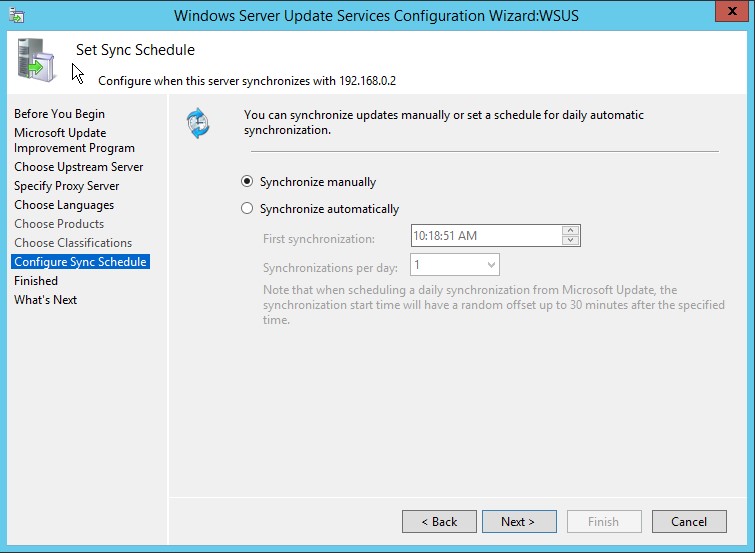
9. In the next step, uncheck the option Begin initial synchronization and click Finish Since initial synchronization takes a lot of time, we will do it after completing all the configuration steps.
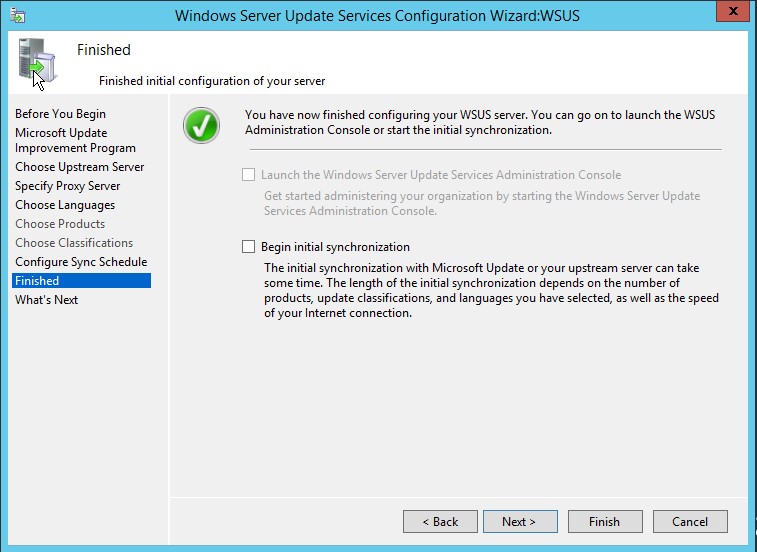
10. Windows Server Update Services wizard will launch automatically.
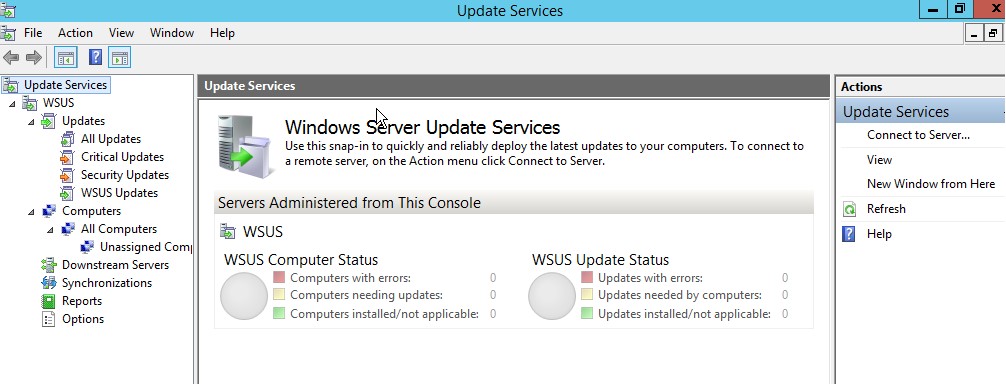
Close the WSUS console for now. We have to install some required updates.
Install some Required Updates on WSUS server
On Windows Server 2012 R2 and Windows Server 2012 R2, you need to install the KB3095113 and KB3159706.
1. KB3095113 enables the WSUS support for Windows 10 feature upgrades. The update can be downloaded from following link:
https://support.microsoft.com/en-us/kb/3095113
2. KB3159706 enables the ESD decryption provision in WSUS in Windows Server 2012 and Windows Server 2012 R2. The update can be downloaded from following link:
https://support.microsoft.com/en-us/kb/3159706
KB3159706 requires some manual steps to complete the installation. If you do not perform these steps, the WSUS server will keep crashing.
Manual Steps
a. Open an elevated Command Prompt, and run the following command (assuming “C” as OS drive):
"C:\Program Files\Update Services\Tools\wsusutil.exe" postinstall /servicing
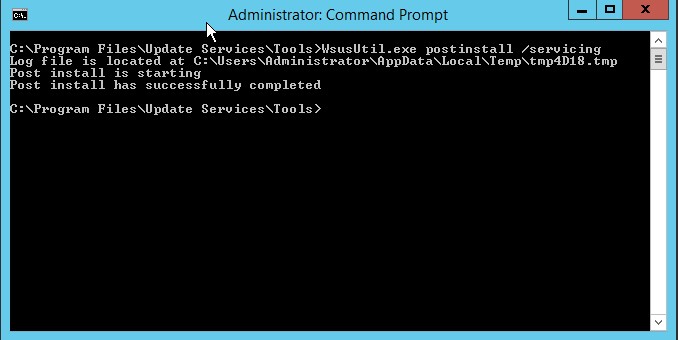
b. Open Server Manager, click Manage and then select Add Roles and Features
c. On Add and Remove Roles wizard, press Next a couple times until you see Features screen. Expand .NET Framework 4.5 features, and then expand WCF Services and select HTTP Activation feature. When prompted to add required role services, click Add Features button and click Next.
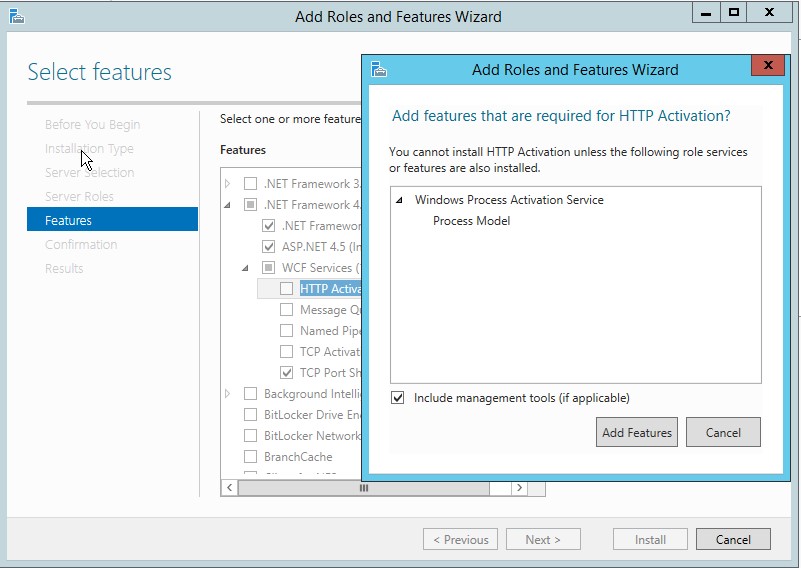
d. Now click Install button and wait for installation to complete.
e. After completing the install either restart the server or restart the WSUS services.

Advanced Configuration of WSUS server
Launch the WSUS console and follow the steps to do additional configurations:
Create Computer Groups
Computer groups enable you to target updates to specific computers. There are two default computer groups: All Computers and Unassigned Computers. When each client computer initially contacts the WSUS server, the server adds that client computer to each of these groups.
Let us add three more computer groups with names IT, Testing, and User PCs. To do this:
- Right click on All Computers default group and select Add Computer Group
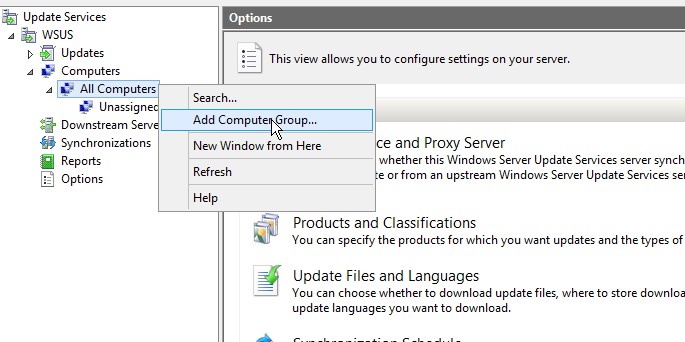
- Enter the name for the group and click Add.
It is a good practice to create a Testing group and then add some test lab PCs to this group so that you can test the updates on these computers before rolling out the updates to whole organization computers. If anything goes wrong, you can identify the offending update and Decline that update so that it does not get installed on your production PCs.
Select Product and Classifications
It is always a good idea to select only the products and classifications you require in your organization. By doing so, you will only download what you need. It will save a lot of hard drive space as well as internet bandwidth. To select Products and Classifications:
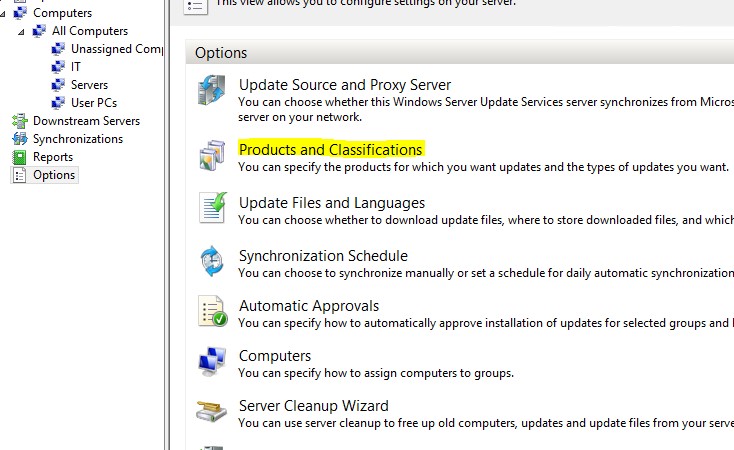
- Click Options in WSUS console.
- Click Products and Classifications.
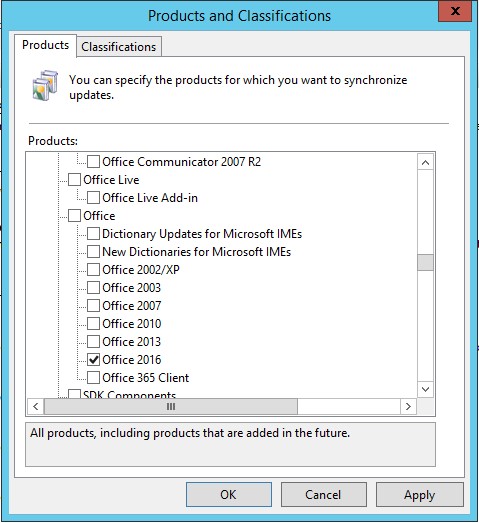
- Under Products tab, only select products that are installed in your organization. By default, a whole lot of products will be selected. For example, in my case, I have only Office 2016 and Windows 10 installed. Therefore, I will only select Office 2016 and Windows 10 and uncheck everything else.
- Under Classifications tab, select the product classification you need. In most of the cases you only need to select Critical Updates, Security Updates, Updates and Upgrades but you can choose anything as per your policy or requirement.
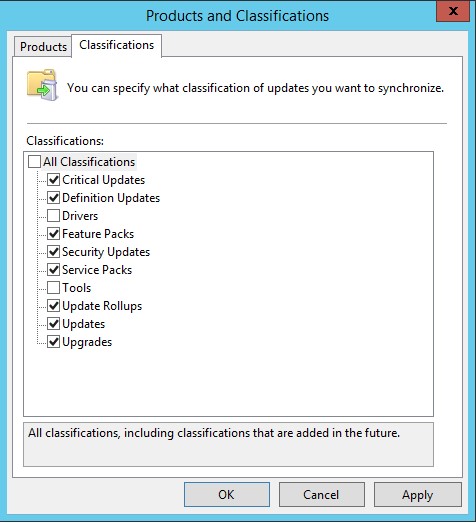
Below are some short descriptions of every classification (source Microsoft documentation):
- Critical Updates: Specifies a broadly released update for a specific problem that addresses a critical, non-security-related bug.
- Definition Updates: Specifies an update to virus or other definition files.
- Feature Packs: Specifies new product features that are distributed outside of a product release and that are typically included in the next full product release.
- Security Updates: Specifies a broadly released update for a product-specific, security-related issue.
- Service Packs: Specifies a cumulative set of hotfixes that are applied to an application. These hotfixes can include: security updates, critical updates, software updates, and so on.
- Tools: Specifies a utility or feature that helps to complete one or more tasks.
- Update Rollups: Specifies a cumulative set of hotfixes that are packaged together for easy deployment. These hotfixes can include security updates, critical updates, updates, and so on. An update rollup generally addresses a specific area, such as security or a product component.
- Updates: Specifies an update to an application or file that is currently installed.
- Upgrade: Specifies an upgrade for Windows 10 features and functionality. Your software update points and sites must run a minimum of WSUS 4.0 with the hotfix 3095113to get the Upgrade
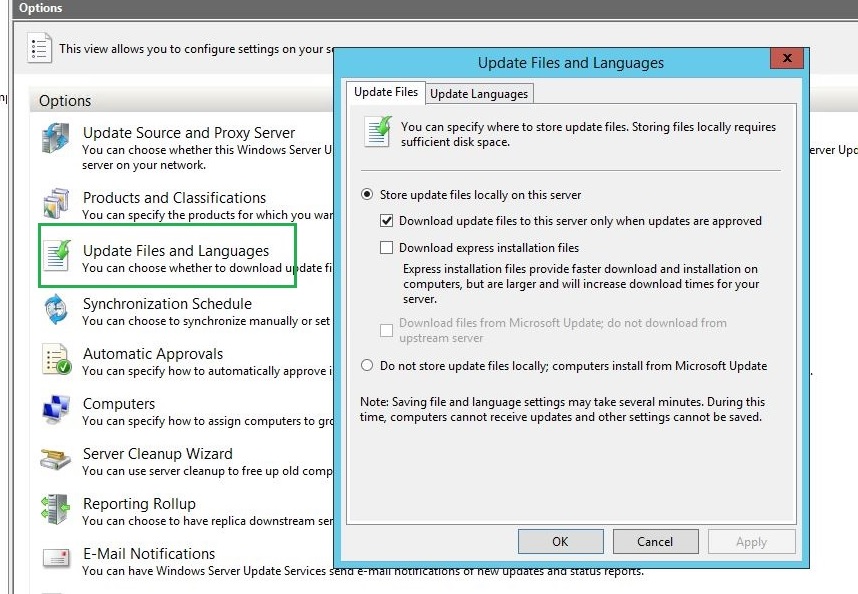
Update Files and Languages
You can specify whether to store update files on your local WSUS server or on Microsoft Update. If you choose to store the updates locally, you can limit the updates downloaded to your server by language. If you choose to store the update files on Microsoft Update, then your WSUS server obtains only update information (metadata) for the criteria you have specified on the Synchronization Options page. In this scenario, the update files come directly from Microsoft Update and are downloaded at the time of installation on the client computers receiving updates. You will need to make sure your client computers have direct access to Microsoft Update in this scenario. This option does not make any sense of deploying the WSUS server in organization if every client computer is supposed to download updates from internet.
To select Update Files and Languages:
- Click Options in WSUS console.
- Click Update Files and Languages option.
On Update Files tab, make sure that the Store update files locally on this server radio button is selected. If you want the updates to start downloading only when you approve the updates, select the checkbox against Download update files to this server only when updates are approved. This option gives you explicit privilege to download only the updates you want. You should consider using this option if your ISP gives you limited monthly data.
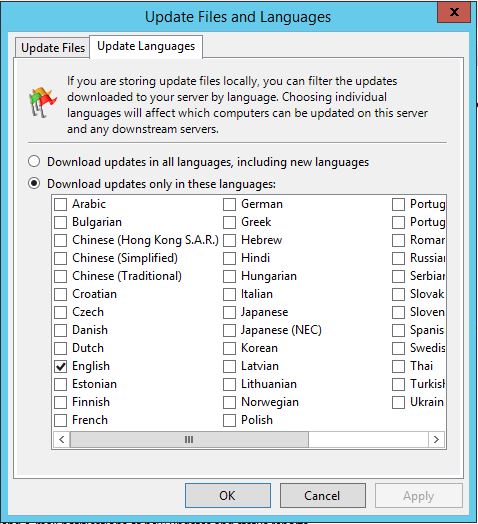
- Under Update Languages tab, only select the languages that are applicable to your products. In my case, I only selected English since I know that every software (including Windows) in my organization is running on US English. Never ever select the radio button Download updates in all languages. This option will unnecessarily cost you huge disk space and internet bandwidth.
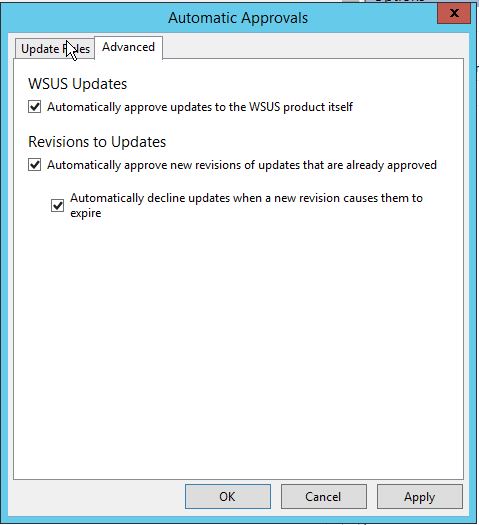
Automatic Approvals
After updates have been synchronized to your WSUS server, you must approve them to initiate a deployment action. When you approve an update, you are essentially telling WSUS what to do with it (for example, your choices are Install, Detect only, Remove, or Decline update). When approving an update, you specify a default approval setting for the All Computers group, and any necessary settings for each computer group in the Approve Updates dialog box. If you do not approve an update, its approval status remains Not approved and your WSUS server performs no action for the update. The exceptions to this are in the Critical Updates and Security Updates classifications, which by default are automatically approved for detection after they are synchronized.
If you do not wish to approve each and every update manually, WSUS console gives you an option to set automatic approval rules.
To open Automatic Approvals:
- Click Options in WSUS console.
- Click Automatic Approvals option.
I would personally recommend creating an automatic approval rule for Testing group we created earlier. In most of the case, WSUS server is set to Sync after business hours. If you do not create any automatic approval rule, what would happen is this:
- Remember previously we selected an option to Download updates only when they are approved.
- If we do not create any automatic approval rule, WSUS server will not download any update after synchronization finishes. It will wait for you to approve the updates. As soon as you approve the updates, the download will start.
- Guess what happens if there are hundreds of updates to be downloaded. The internet connection will get congested which will affect your business applications and production.
- If you want the updates to be downloaded after business hours, you must set the Sync schedule after your business hours and create an automatic approval rule. When WSUS finishes synchronization and it finds new updates to download, the updates will be auto approved and downloaded at the same time thus not impacting production hours. Of course all the updates matching your Products and Classifications criteria will be downloaded. So, be sure to select your Products and Classifications wisely.

If you want to download and approve the Updates for WSUS software itself, go to Advanced tab and select the checkbox against Automatically approve updates to the WSUS product itself option under WSUS Updates.
Assign Computers to Different Groups
We created different Groups (User PC, IT, Testing etc.) so that we could assign the computers into these groups. But how does WSUS assign any computer to a group. This is where Computers option of WSUS console comes into play.
To open the settings:
- Click Options in WSUS console.
- Click Computers option.
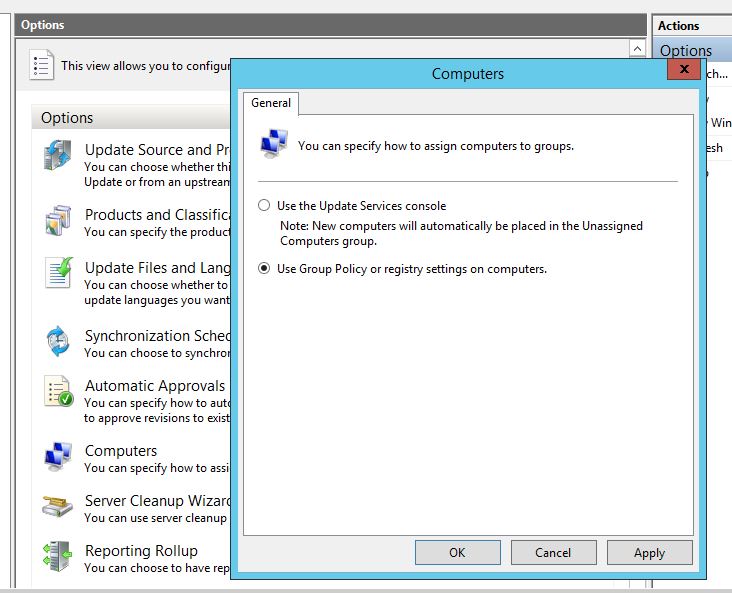
There are only two options:
- Use the Update Services console: This option allows you to manually assign the computers to groups.
- Use Group Policy or registry settings on computers: This is the most preferred way of assigning computers. If you are running an Active Directory Domain, you can use Group policy to provide WSUS settings for all the computers. If you are using Workgroup environment, you can use registry settings.
Group Policy settings are located at Computer Configuration –> Policies –> Administrative Templates –> Windows Components –> Windows Update.
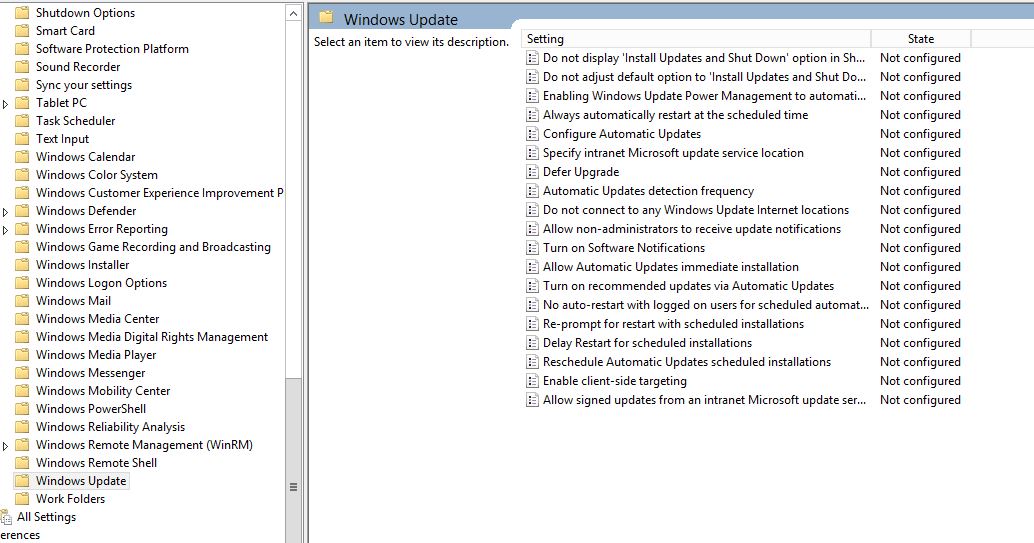
To do so via Registry editing, copy the following code into notepad, save the file with .reg extension and then run this file on target client computer. The client computer will be auto configured to download updates from WSUS server instead of Windows update.
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate] "AcceptTrustedPublisherCerts"=dword:00000001 "ElevateNonAdmins"=dword:00000001 "TargetGroup"="User PCs" "TargetGroupEnabled"=dword:00000001 "WUServer"="http://192.168.0.2:8530" "WUStatusServer"="http://192.168.0.2:8530" [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU] "AUOptions"=dword:00000004 "AUPowerManagement"=dword:00000001 "AutoInstallMinorUpdates"=dword:00000001 "DetectionFrequency"=dword:0000000a "DetectionFrequencyEnabled"=dword:00000001 "IncludeRecommendedUpdates"=dword:00000001 "NoAUAsDefaultShutdownOption"=dword:00000001 "NoAUShutdownOption"=dword:00000001 "NoAutoRebootWithLoggedOnUsers"=dword:00000001 "NoAutoUpdate"=dword:00000000 "RebootRelaunchTimeout"=dword:0000000a "RebootRelaunchTimeoutEnabled"=dword:00000001 "RescheduleWaitTime"=dword:0000000a "RescheduleWaitTimeEnabled"=dword:00000001 "ScheduledInstallDay"=dword:00000007 "ScheduledInstallTime"=dword:00000002 "UseWUServer"=dword:00000001
Of course replace the IP and Port (192.168.0.2:8530) with your WSUS server’s IP (Name) and port.
See the following table for more information about registry code:
| Entry name | Data type | Values |
| AcceptTrustedPublisherCerts | Reg_DWORD | Range = 1|0
– 1 = Enabled. The WSUS server distributes available signed non-Microsoft updates. |
| DisableWindowsUpdateAccess | Reg_DWORD | Range = 1|0
– 1 = Disables access to Windows Update. |
| ElevateNonAdmins | Reg_DWORD | Range = 1|0
– 1 = All members of the Users security group can approve or disapprove updates. |
| TargetGroup | Reg_SZ | Name of the computer group to which the computer belongs. This policy is paired with TargetGroupEnabled. |
| TargetGroupEnabled | Reg_DWORD | Range = 1|0
– 1 = Use client-side targeting. |
| WUServer | Reg_SZ | HTTP(S) URL of the WSUS server that is used by Automatic Updates and API callers (by default). This policy is paired with WUStatusServer, and both keys must be set to the same value to be valid. |
| WUStatusServer | Reg_SZ | The HTTP(S) URL of the server to which reporting information is sent for client computers that use the WSUS server that is configured by the WUServer key. This policy is paired with WUServer, and both keys must be set to the same value to be valid. |
| Entry name | Data type | Values |
| AUOptions | Reg_DWORD | Range = 2|3|4|5
– 2 = Notify before download. |
| AutoInstallMinorUpdates | Reg_DWORD | Range = 0|1
– 0 = Treat minor updates like other updates. |
| DetectionFrequency | Reg_DWORD | Range = n, where n = time in hours (1–22).
– Time between detection cycles. |
| DetectionFrequencyEnabled | Reg_DWORD | Range = 0|1
– 1 = Enable detection frequency. |
| NoAutoRebootWithLoggedOnUsers | Reg_DWORD | Range = 0|1
– 1 = Logged-on user can decide whether to restart the client computer. |
| NoAutoUpdate | Reg_DWORD | Range = 0|1
– 0 = Enable Automatic Updates. |
| RebootRelaunchTimeout | Reg_DWORD | Range = n, where n = time in minutes (1–1,440).
– Time between prompts for a scheduled restart. |
| RebootRelaunchTimeoutEnabled | Reg_DWORD | Range = 0|1
– 1 = Enable RebootRelaunchTimeout. |
| RebootWarningTimeout | Reg_DWORD | Range = n, where n = time in minutes (1–30).
– Length, in minutes, of the restart warning countdown after updates have been installed that have a deadline or scheduled updates. |
| RebootWarningTimeoutEnabled | Reg_DWORD | Range = 0|1
– 1 = Enable RebootWarningTimeout. |
| RescheduleWaitTime | Reg_DWORD | Range = n, where n = time in minutes (1–60).
– Time in minutes that Automatic Updates waits at startup before it applies updates from a missed scheduled installation time. |
| RescheduleWaitTimeEnabled | Reg_DWORD | Range = 0|1
– 1 = Enable RescheduleWaitTime . |
| ScheduledInstallDay | Reg_DWORD | Range = 0|1|2|3|4|5|6|7
– 0 = Every day. |
| ScheduledInstallTime | Reg_DWORD | Range = n, where n = the time of day in 24-hour format (0–23). |
| UseWUServer | Reg_DWORD | Range = 0|1
– 1 = The computer gets its updates from a WSUS server. |
Finally, I would like to say that WSUS is a great tool which every organization should consider to save their monthly internet data and bandwidth. This prevents repeated download of same updates over and over again when each computer of your organization is updated.
As your WSUS keeps downloading new and new updates, it will need more and more disk space. Whatever it downloads over a period of time is not always necessary for you to keep. So, I would suggest to run Server Cleanup Tool (available in Options page of WSUS console) once within 1-2 months so that unnecessary updates (like expired, superseded, not-required) could be removed to reclaim disk space.
