Welcome to the second article in this series on Remote Desktop Services in Windows 2008 R2. We were first introduced to the Remote Desktop (RD) Gateway in the first release of Windows 2008 and as previously mentioned in part 1 of this series, the RD Gateway was formerly known as Terminal Server (TS) Gateway. TS Gateway opened up Remote Access barriers providing access to our Terminal Servers via SSL or port 443, as opposed to the conventional “legacy” VPN access through either IPSEC or L2TP. In Windows Server 2008 R2, not much has changed and in today’s article I will provide you with a step by step guide on configuring your RD Gateway which will provide your remote users access to the Remote Desktop Host or RD Web Access via any Internet connection utilising Remote Desktop Connection client over HTTPS. If you missed part 1 of this series which discussed the installation of your Remote Desktop Role and services, you can access it here.
There are a number of prerequisites that are required in order for the RD Gateway to function and these were all setup in part 1 of this series. For reference I have listed these below;
- Remote procedure call (RPC) over HTTP Proxy
- Internet Information Services
Let’s begin by navigating to All Programs / Administrative Tools / Remote Desktop Services / Remote Desktop Gateway Manager. You will be presented with the below screen.

In the left navigation pane of your RD Gateway Manager MMC console, click on your server and select properties under Actions. We will now go through each tab under the server properties and make any necessary configuration changes. Let’s refer to this process as post wizard configuration.
Under the General Tab, we are provided with the ability to configure the maximum number of connections that are allowed to connect to this RD Gateway. If you are concerned with server performance, we can set a hard limit of allowed simultaneous connections. We can also disable new connections if we are performing scheduled maintenance on our server.

The next tab allows us to secure the RD Gateway by using an SSL certificate. We can create a self-signed certificate (recall that this was completed during the initial install wizard in part 1 of this series), select an existing certificate that is located on the server under Certificates / Personal store or Import a certificate that we have requested via a 3rd Party Certification Authority (CA) or utilising an internal CA. It is deemed best practice to utilise a 3rd party CA that participates in the Microsoft Root Certification Members Programme alleviating the headache that is usually involved in exporting the root certificate, distributing them to your end users and then providing them with instructions on how to import them into their local machines. Utilising a self-signed certificate is usually reserved for testing purposes only, and not in a production environment, however it will suffice in this step by step guide.

The third tab introduces the RD CAP Store and provides us with the ability to utilise our local server running Network Policy Server (NPS) or the ability to specify a central server that is already configured and running NPS. This was also initially configured during the installation wizard of our Remote Desktop Services role in part 1.

The next tab, Server Farm, allows us to specify farm members for the RD Gateway. As a minimum we need to Add this RD Gateway server below as follows. You do so by entering the fully qualified domain name of the server and clicking on Add. It will then add it below under Remote Desktop Gateway server farm status as per the below screen capture.

You will notice the above warning regarding the registry not being updated. This warning will disappear and the status will change to OK after clicking on Apply.

The next tab allows you to select or deselect events that you would wish to log. These corresponding events are stored in Event Viewer under Application and Services Logs\Microsoft\Windows\Terminal Services-Gateway\. By default, all items under the Auditing tab are selected to be captured and logged. The below screen capture is an example of the TerminalServices – Gateway Event Viewer on our Windows 2008 R2 server.

SSL bridging is next and is required to be configured if you are utilizing Microsoft ISA Server to further secure the RD Gateway. Microsoft ISA Server is a great application level firewall which offers reverse proxy and can be configured to work hand in hand in providing secure access over SSL.

The last tab in the RD Gateway properties is Messaging which was not present in Windows 2008 TS Gateway. This is a welcome addition for administrators to utilise when pre-planning for system maintenance and wanting to advise users with a global system notification, and the also providing the ability to set a logon message such as the company’s logon policy.
The first area within the Messaging tab is the ability to set a timed system message with the ability to set a start date/time and end date/time.

When a user logs in via the RD Gateway, they will be presented with the following message that we configured above;

The second area under messaging allows you to specify a message such as your company’s logon policy that will appear each time a user logs into the RD Gateway remote computer. This is simply a text file with the contents within.

The below similar notice is what will appear when logging on to your Remote Desktop Host via the RD Gateway

You will notice that the system will not continue to login (the OK button is dimmed) unless you accept the terms of this policy.
The last option allows you to specify that connections to the Remote Desktop Host via the RD Gateway will be restricted to clients that support RD Gateway messaging which is anything greater than Remote Desktop Client version 7.
Now prior to connecting to the RD Gateway and testing our setup, we will need to export the self-signed SSL certificate located on the RD Gateway and install it on our client computer that we will be connecting from. The easiest way to accomplish this is to open the Certificates MMC snap-in, locate the certificate from the Personal / Certificates store, and right click, All Tasks / Export.

This will invoke the below Certificate Export Wizard.

Click Next
Select Yes, export the private key.

Click Next.
Select, Include all certificates in the certificate path if possible

Click Next. Type and confirm a password and then click Next again.
Specify a name and location to export the pfx certificate file.
Click Next and then Finish.
We can now copy or email the exported certificate to our end users who will then install the certificate to their local personal store. This can be easily achieved by double clicking on the exported certificate and invoking the Certificate Import Wizard. Please ensure that when you come to the Certificate Store section of the Import Wizard that you select “Place all certificates in the following store” and select “Trusted Root Certification Authorities”.

Now that we have successfully imported the root self signed certificate authority, we can now test our setup and login to our remote computer via the RD Gateway. Before we begin, you need to ensure that you are running the latest Remote Desktop Connection client which is version 7. This version is already included with Windows 7 and is made available for download to Windows Vista SP1 and SP2 clients and to Windows XP SP3 clients. This can be downloaded from the Microsoft Support site; http://support.microsoft.com/kb/969084
The above article also provides you with a comprehensive list of new features and their explanations that are only possible with RDC 7 and Windows 2008 R2. I have listed these below for convenience;
- Web Single Sign-On (SSO) and Web forms-based authentication
- Access to personal virtual desktops by using RD Connection Broker
- Access to virtual desktop pools by using RD Connection Broker
- Status & disconnect system tray icon
- RD Gateway-based device redirection enforcement
- RD Gateway system and logon messages
- RD Gateway background authorization & authentication
- NAP remediation with RD Gateway
- Windows Media Player redirection
- Bidirectional audio
- Multiple monitor support
- Enhanced video playback
From a client machine running RDC 7, navigate to Start / All Programs / Accessories / Remote Desktop Connection or just search for mstsc.
Click Options and then navigate to the advanced tab.

Click Settings and then select Use these RD Gateway server settings:
Enter your server name and logon method details as follows;

Then click OK. Ensure that Bypass RD Gateway server for local addresses is deselected. Navigate back to the General Tab and enter the Computer and User name details and then click Connect when ready.
The following Windows Security popup will appear asking you to authenticate prior to launching a full remote desktop session.

After entering your credentials and clicking OK, You will be prompted to accept the login policy that we specified earlier under the Messaging tab of the RD Gateway properties.
So that’s it, we are now logged in to the Remote Desktop Host via the RD Gateway. We can confirm this by clicking on the spanner located on the top toolbar which will output the Remote Computer and Gateway Server that we are connected to. It also states that the connection to the remote computer was made using a Remote Desktop Gateway server.

That’s it for now. In our next and final article I will discuss Remote Desktop (RD) Web Access and the publishing of Remote Desktop Applications, so stay tuned.
_________________________________________
Articles in this series;
- Remote Desktop Services in Windows 2008 R2 -Part 1 , Installation and Configuration
- Remote Desktop Services in Windows 2008 R2 – Part 2 – RD Gateway
- Remote Desktop Services in Windows 2008 R2 – Part 3 – RD Web Access & RemoteApp
Прочитано: 5 079
Когда я разворачивал DHCP на домен контроллере, я не настроил шлюз для систем которые будут входить в домен polygon.local. Чтобы это поправить следует зайти на домен контроллер под учетной записью ekzorchik (состоит в группе Domain Admins). Далее запустить оснастку DHCP:
«Start» – «Control Panel» – «Administrative Tools» – «DHCP»
Открываем текущий домен контроллер dc1.polygon.local, после разворачиваем IPv4, переходим в Scope Options, после вызываем меню “Configure Options…”
См. на скриншот, чтобы понимать, что нужно сделать:
В меню Scope Options выбираем пункт 003 Router и назначаем IPадрес 10.0.3.15 в качестве шлюза.
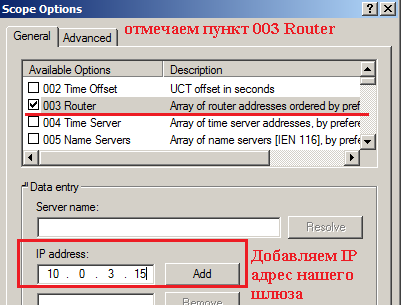
Шлюз добавил, нажимаем Apply и Ok для зафиксирования изменений, а после закрываем оснастку DHCP.
Чтобы настройки применились, следует перезапустить службу DHCP:
C:\Windows\system32>net stop DHCPServer
The DHCP Server service is stopping.
The DHCP Server service was stopped successfully.
C:\Windows\system32>net start DHCPServer
The DHCP Server service is starting…
The DHCP Server service was started successfully.
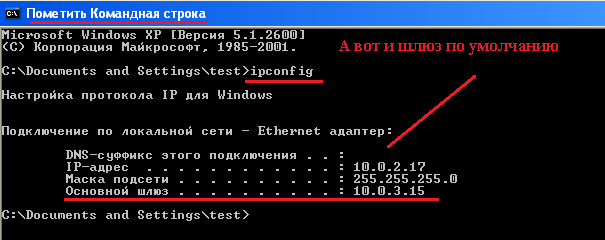
Проверим внесённые изменения на рабочей станции
(Windows XP – WXP86.polygon.local) входящей в домен:
C:\Documents and Settings\test\ipconfig
IP – 10.0.2.17
Netmask – 255.255.255.0
GateWay – 10.0.3.15
Пошаговое руководство по настройке шлюза продемонстрировано. На этом всё, удачи!!!
RD Gateway
Technology review
RD Gateway uses the Remote Desktop Protocol (RDP) over HTTPS to help establish a secure, encrypted connection between remote users on the Internet and the internal network resources on which their productivity applications run.
To function correctly, RD Gateway requires several role services and features to be installed and running. When you use Server Manager to install the RD Gateway role service, the following additional roles, role services, and features are automatically installed and started, if they are not already installed:
- Remote procedure call (RPC) over HTTP Proxy
- Web Server (IIS) [Internet Information Services]
IIS must be installed and running for the RPC over HTTP Proxy feature to function. - Network Policy and Access Services
Step 2: Installing RD Gateway
Updated: June 24, 2009
Applies To: Windows 7, Windows Server 2008 R2
To install and configure an RD Gateway server, you must add the RD Gateway role service. Windows Server 2008 R2 includes the option to install the RD Gateway role service by using Server Manager. This topic covers the installation and configuration of the RD Gateway role service on the RDG-SRV computer in the CONTOSO domain.
Membership in the local Administrators group, or equivalent, on the RD Gateway server that you plan to configure, is the minimum required to complete this procedure. Review details about using the appropriate accounts and group memberships at Local and Domain Default Groups (http://go.microsoft.com/fwlink/?LinkId=83477).
To install the RD Gateway role service
-
Log on to RDG-SRV as CONTOSO\Administrator.
-
Open Server Manager. To open Server Manager, click Start, point to Administrative Tools, and then click Server Manager.
-
Under the Roles Summary heading, click Add Roles.
-
In the Add Roles Wizard, if the Before You Begin page appears, click Next.
-
On the Select Server Roles page, under roles, select the Remote Desktop Services check box, and then click Next.
-
On the Remote Desktop Services page, click Next.
-
On the Select Role Services page, select the Remote Desktop Gateway check box.
-
If prompted to specify whether you want to install the additional role services required for Remote Desktop Gateway, click Add Required Role Services.
-
On the Select Role Services page, click Next.
-
On the Choose a Server Authentication Certificate for SSL Encryption page, select Create a self-signed certificate for SSL encryption, and then click Next.
-
On the Create Authorization Policies for RD Gateway page, select Now, and then click Next.
- On the Select User Groups That Can Connect Through RD Gateway page, click Add. In the Select Groups dialog box, specify Domain Users, and then click OK to close the Select Groups dialog box. Click Next.
- On the Create an RD CAP for RD Gateway page, enter the name RD_CAP_01 for the Remote Desktop connection authorization policy (RD CAP), select Password, and then click Next.
- On the Create an RD RAP for RD Gateway page, enter the name RD_RAP_01 for the Remote Desktop resource authorization policy (RD RAP), and then select Allow users to connect to any computer on the network. Click Next.
- On the Select User Groups That Can Connect Through RD Gateway page, click Add. In the Select Groups dialog box, specify Domain Users, and then click OK to close the Select Groups dialog box. Click Next.
-
On the Network Policy and Access Services page (which appears if this role service is not already installed), review the summary information, and then click Next.
-
On the Select Role Services page, verify that Network Policy Server is selected, and then click Next.
-
On the Web Server (IIS) page (which appears if this role service is not already installed), review the summary information, and then click Next.
-
On the Select Role Services page, accept the default selections for Web Server (IIS), and then click Next.
-
On the Confirm Installation Selections page, verify that the following role services will be installed:
- Remote Desktop Services\RD Gateway
- Network Policy and Access Services\Network Policy Server
- Web Server (IIS)
- RPC over HTTP Proxy
-
Click Install.
-
On the Installation Progress page, installation progress will be noted.
-
On the Installation Results page, confirm that installation for these roles, role services, and features was successful, and then clickClose.
To export the SSL certificate for the RD Gateway server and copy it to the CONTOSO-CLNT computer
-
On the RD Gateway server, open the Certificates snap-in console. If you have not already added the Certificates snap-in console, you can do so by doing the following:
- Click Start, click Run, type mmc and then click OK.
- On the File menu, click Add/Remove Snap-in.
- In the Add or Remove Snap-ins dialog box, in the Available snap-ins list, click Certificates, and then click Add.
- In the Certificates snap-in dialog box, click Computer account, and then click Next.
- In the Select Computer dialog box, click Local computer: (the computer this console is running on), and then click Finish.
- In the Add or Remove snap-ins dialog box, click OK.
-
In the Certificates snap-in console, in the console tree, expand Certificates (Local Computer), expand Personal, and then clickCertificates.
-
Right-click the certificate RDG-SRV.contoso.com, point to All Tasks, and then click Export.
-
On the Welcome to the Certificate Export Wizard page, click Next.
-
On the Export Private Key page, click No, do not export private key, and then click Next.
-
On the Export File Format page, ensure that DER encoded binary X.509 (.CER) is selected, and then click Next.
-
On the File to Export page, in the File name box, click Browse.
-
In the Save As dialog box, in the File name box, enter RDG-SRV, and then click Save.
-
On the File to Export page, click Next.
-
On the Completing the Certificate Export Wizard page, confirm that the correct certificate is specified, that Export Keys is set toNo, and that Include all certificates in the certification path is set to No, and then click Finish.
-
After the certificate export has successfully completed, a message appears confirming that the export was successful. Click OK.
-
Close the Certificates snap-in.
-
Copy the RD Gateway server certificate c:\users\administrator.CONTOSO\Documents\RDG-SRV.cer, to the CONTOSO-CLNT computer.
To verify the functionality of the RD Gateway deployment, complete the following:
- Install the SSL certificate for the RD Gateway server on the CONTOSO-CLNT computer.
- Enable certificate revocation checking on the CONTOSO-CLNT computer. (Optional)
- Log on to CONTOSO-CLNT as Morgan Skinner and use Remote Desktop Connection (RDC) to connect to the RD Session Host server (RDSH-SRV) by using the RD Gateway server (RDG-SRV).
To install the SSL certificate for the RD Gateway server on the CONTOSO-CLNT computer
-
Log on to CONTOSO-CLNT as CONTOSO\Administrator.
-
Open the Certificates snap-in console by doing the following:
- Click Start, click Run, type mmc and then click OK.
- On the File menu, click Add/Remove Snap-in.
- In the Add or Remove Snap-ins dialog box, in the Available snap-ins list, click Certificates, and then click Add.
- In the Certificates snap-in dialog box, click Computer account, and then click Next.
- In the Select Computer dialog box, click Local computer: (the computer this console is running on), and then click Finish.
- In the Add or Remove snap-ins dialog box, click OK.
-
In the Certificates snap-in console, in the console tree, expand Certificates (Local Computer), and then click Trusted Root Certification Authorities.
-
Right-click the Trusted Root Certification Authorities folder, point to All Tasks, and then click Import.
-
On the Welcome to the Certificate Import Wizard page, click Next.
-
On the File to Import page, in the File name box, click Browse, and then browse to the location where you copied the SSL certificate for the RD Gateway server. From the file type drop-down list, select All Files (*.*). Select the certificate RDG-SRV.cer, click Open, and then click Next.
-
On the Certificate Store page, accept the default option (Place all certificates in the following store – Trusted Root Certification Authorities), and then click Next.
-
On the Completing the Certificate Import Wizard page, confirm that the correct certificate has been selected and that the following certificate settings appear:
- Certificate Store Selected by User: Trusted Root Certification Authorities
- Content: Certificate
- File Name: FilePath\RDG-SRV.cer
-
Click Finish.
-
After the certificate import has successfully completed, a message appears confirming that the import was successful. Click OK.
-
With Certificates selected in the console tree, in the details pane, verify that the correct certificate appears in the list of certificates on the CONTOSO-CLNT computer.
-
Log off from the CONTOSO-CLNT computer.
To enable certificate revocation checking on the CONTOSO-CLNT computer (Optional)
-
Log on to CONTOSO-CLNT as CONTOSO\Administrator.
-
Click Start, point to All Programs, and then click Accessories.
-
Right-click Command Prompt, and then click Run as administrator.
-
If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Yes.
-
At the command prompt, type
reg add "HKCU\Software\Microsoft\Terminal Server Gateway\Transports\Rpc" /v CheckForRevocation /t REG_DWORD /d 1.Warning
The publishing and maintenance of the certificate revocation list is an integral part of the public key infrastructure (PKI) and is external to RD Gateway. Please do not enable certificate revocation checking on RD Gateway clients until you have confirmed that your deployment can support this; otherwise, even the basic connection to an end resource through the RD Gateway server will not work. This is the reason why certificate revocation checking is disabled by default on the RD Gateway client, and the recommendation is to turn it on as a security best practice only after ensuring that the certificate revocation list is accessible from the Internet.
-
Log off the computer.
To connect to RDSH-SRV with RDC by using RDG-SRV
-
Log on to CONTOSO-CLNT as Morgan Skinner.
-
Click Start, point to All Programs, point to Accessories, and then click Remote Desktop Connection.
-
In the Remote Desktop Connection dialog box, click Options.
-
On the Advanced tab, click Settings.
-
On the RD Gateway Server Settings page, click Use these RD Gateway server settings, enter the following settings, and then click OK.
- Server name: RDG-SRV.contoso.com
- Logon method: Allow me to select later
- Bypass RD Gateway server for local addresses: Clear check box
-
On the General tab, in the Computer box, type rdsh-srv, and then click Connect.
-
In the Windows Security dialog box, type the password for contoso\mskinner, and then click OK.
-
If the connection is successful, a Windows desktop will appear on the screen for RDSH-SRV.
You have successfully deployed and demonstrated the functionality of RD Gateway on Remote Desktop Services by using the simple scenario of connecting to an RD Session Host server by using RD Gateway with an authorized remote user account by using Remote Desktop Connection. You can also use this deployment to explore some of the additional capabilities of Remote Desktop Services through additional configuration and testing.

RD Gateway
The Remote Desktop Gateway
(RD Gateway) role service allows users to access network resources
(like RD Session Host servers, RD Session Host servers running RemoteApp
programs, RD Virtualization Host–based virtual machines, or computers
with Remote Desktop enabled) that are located behind firewalls in a
private network from any Internet-based client (or internally based
clients if TCP 3389 is an internally restricted port). To do this, the
RD Gateway employs something that is called an SSL relay (also known as
an SSL VPN). In short, an SSL relay allows clients to connect to
internal resources over a secure, encrypted HTTPS connection. In this
case, the traffic that is being passed through the SSL relay is just RDP
(TCP 3389).
Note
RD Gateway must be installed on
Windows Server 2008 R2 servers, but it can perform SSL relay for both
Windows Server 2008 R2 RD Session Host servers and Windows Server
2008/2003 Terminal Servers.
RD Gateway was first
introduced in Windows Server 2008 as the TS Gateway. The reason
Microsoft has included this feature in Windows Server 2008 was because
security measures were typically put into
place to block traffic such as RDP (TCP 3389). In other words, IT
security departments typically blocked RDP or were reluctant to open
ports on their firewalls for it. Microsoft took a card from networking
companies and built an SSL VPN solution into their Remote Desktop
Services offerings. The result of this effort is the RD Gateway, which
allows users to gain access to the services that are provided by Remote
Desktop Services, regardless of their location.
As hinted previously, the
RD Gateway uses an HTTP Secure Sockets Layer/Transport Layer Security
(SSL/TLS) tunnel to transmit RDP traffic. Because the RD Gateway server
is using HTTPS, a server authentication certificate needs to be
installed. Furthermore, the certificate that is installed needs to be
issued by a certificate authority (CA) that is trusted on clients
accessing the RD Gateway. In other words, the certificate of the CA that
signed the RD Gateway server certificate must be located in the
client’s Trusted Root Certification Authority store. A trusted
certificate can either be obtained from a publicly trusted CA or an
internal CA to your organization that is already trusted by clients.
The following are some
additional requirements that should be taken into account when using the
RD Gateway:
-
The Remote Procedure
Call (RPC) over HTTP Proxy service must be installed (this is installed
when you install the RD Gateway role service). -
Internet Information Services 7.5
must be installed and running for the RPC over HTTP Proxy service to
function. -
The
Network Policy Server (NPS) service must be installed or an existing NPS
server must be present that can be used by the RD Gateway. -
RD Gateway servers and
Remote Desktop Services clients can be configured to use Network Access
Protection (NAP). -
Active
Directory Domain Services is required if the RD Gateway authorization
policy is defined such that clients must be a member of a domain-based
group.
Note
The RD Gateway feature
is only supported on clients running Windows Server 2008 (R2), Windows
7, Windows Vista, Windows XP with Service Pack 2 or higher, or Windows
Server 2003 with Service Pack 1 or higher that have the Remote Desktop
Connection (RDC) client installed.
The new features that
have been introduced in Windows Server 2008 R2 for the RD Gateway role
service are discussed in the following sections.
Configurable Idle and
Session Timeouts
In Windows Server 2008
R2, an administrator can now configure idle and session timeouts for an
RD Gateway server. An idle timeout is used to reclaim unused resources.
If a user’s session is idle longer than the specified time, that user’s
RD Gateway session is disconnected. When this occurs, a user will still be able to
reestablish the session, if they choose to. A session timeout allows for
the ability to periodically enforce new policies on active user
connections. Policy refreshes mean that Remote Desktop connection
authorization policy (RD CAP) changes or Remote Desktop resource
authorization policy (RD RAP) changes can be enforced on existing
sessions.
Background Session
Authentication and Authorization
If a timeout is reached, a
session can either be disconnected or silently reauthenticated and
reauthorized. When enabled for background authentication and
authorization, the authentication and authorization requests for the
session are automatically done in the background with no interaction.
System and Logon
Messages
Now when a user starts a new
RD Gateway session, an administrator can define system and logon
messages. System messages can be used to inform users about system
status changes, upcoming server maintenance, and so on, whereas a logon
message can be used to display a legal-logon notice to users before they
gain access to any protected resources.
Device Redirection
Enforcement
RD Gateway now has the option
to only allow Remote Desktop clients to connect to RD Session Host and
RD Virtualization Host servers that enforce secure device redirection.
This change was put in place to prevent non-Microsoft Remote Desktop
clients from overriding the gateway device redirection controls.
However, this new feature is only supported on RDC 7.0 or later clients.
Network Access
Protection (NAP) Remediation
When using a Windows
Server 2008 R2 RD Gateway server, clients that are found
out-of-compliance with a health policy can now be brought into
compliance via software updates. By using this feature, an administrator
can use a CAP policy to ensure that remote clients that connect to
internal resources through an RD Gateway are always kept current with
the latest software updates.
Pluggable
Authentication and Authorization
The pluggable
authentication and authorization feature exposes a set of APIs that
allow organizations custom or third-party authentication and
authorization plug-ins that integrate with RD Gateway. By using this
feature, RD Gateway authentication and authorization can be tailored to
fit a wide range of security requirements.
Windows Server 2008 R2
Feature Requirements
For an administrator to
utilize the new RD Gateway features introduced in Windows Server 2008
R2, the following requirements must be met:
-
RD Session Host servers must be Windows
Server 2008 R2. -
RD Gateway servers must
be Windows Server 2008 R2. -
Users must use
the Remote Desktop Connection (RDC) 7.0.
RD Web Access
The
Remote Desktop Web Access role service is designed to allow users
(internally and remotely) to access RemoteApp programs, session-based
remote desktops, or virtual desktops from within a website. Using RD Web
Access, a user accessing a website (hosting the RD Web Access web part)
would be presented with a single consolidated list of published
RemoteApps. This list consists of the application icons for each
RemoteApp that has been published either from a single RD Session Host
server or RD Session Host server farms. By clicking on one of these
icons, a session would then be launched on the remote RD Session Host or
RD Virtualization Host that is hosting the published resource. RD Web
Access is especially useful to administrators who want to deploy Remote
Desktop Services–based programs from a central location, from a
customized web page, or from a Windows SharePoint Services site.
To use RD Web Access, clients
must meet the following requirements:
-
Internet Explorer 6.0
-
Remote Desktop Connection
(RDC) that supports at least Remote Desktop Protocol (RDP) 6.1
The version of the RDC
client on Windows 7 and Windows Server 2008 R2 supports RDP 7.0. The RDC
client that is being used determines which RD Web Access features will
be available to users. Additionally, the Remote Desktop Services ActiveX
Client control must be enabled.
The new features that have
been introduced in Windows Server 2008 R2 for the RD Session Host role
service are discussed in the following sections.
Forms-Based
Authentication
Forms-based
authentication (FBA) is an ASP.NET authentication service that enables
applications to provide their own logon page and do their own credential
verification. Additionally, this service authenticates users, redirects
unauthenticated users to the logon page, and performs all the necessary
cookie management. Like Outlook Web Access (OWA), by supporting FBA, RD
Web Access users will now have an improved logon experience. For
example, administrators can customize the RD Web Access logon page to
include such things as branding stylization and other important
look-and-feel items.
Single Sign-On Between
RD Session Host and RD Web Access
An important feature that was
missing from the Windows Server 2008 Terminal Services version of Web
Access was support for Single Sign-On. In that version, when a user
connected to a RemoteApp program using Web Access, they were prompted
for their credentials twice. Needless to say, the double credential
prompting led to a poor user experience. However, with the Windows
Server 2008 R2 version of Web Access (RD Web Access), support for Single
Sign-On has been added. When used correctly, users will only have to
provide their credential information once when connecting to a RemoteApp
program using RD Web Access.
Note
To
use RD Web Access Single Sign-On, several dependencies must be met.
First, the certificate used to sign the RemoteApp programs must be
trusted. Second, Single Sign-On is only supported from clients running
Remote Desktop Connection (RDC) 7.0.
Public and Private
Computer Option
Like OWA, the RD Web Access
Web page can now be accessed via either a public or private mode. If the
public computer option is used, cookies storing the username are
available for about 20 minutes. If the cookie is left to expire, the
user’s information is technically purged from the system being used.
When the private computer option is used, cookies storing the username
are available for about 4 hours.
Note
A user’s password is never
cached on a system when either the public or private RD Web Access
options are used.
Posted on February 26, 2016 by BjTechNews in Microsoft, Tech News, Windows 2008 R2 // 0 Comments


Remote Desktop Gateway (RD Gateway) is a role service that enables authorized remote users to connect to resources on an internal corporate or private network, from any Internet-connected device that can run the Remote Desktop Connection (RDC) client.
Related
- RD Gateway
- RD Gateway Server
- Remote Desktop Gateway
- Windows Server 2008 R2
About BjTechNews (1086 Articles)
An IT guy trying to learn everything about technology and sharing it with you all. I’m a blogger and video blogger who highlights daily news in the tech industry, promoting tips and hacks for fellow techies.
Leave a Reply
This site uses Akismet to reduce spam. Learn how your comment data is processed.













