Question
Question 3
What would be displayed if the netstat -abno command was entered on a Windows PC?
a local routing table
only active TCP connections in an ESTABLISHED state
only active UDP connections in an LISTENING state
all active TCP and UDP connections, their current state, and their associated process ID (PID)

Key Concept
netstat command
UndergraduateScienceComputer Science
The netstat command is a networking utility used to display network connections, routing tables, interface statistics, and more. The -abno options show all active connections and listening ports, along with their process IDs.
1 Answer
Correct Answer
- d. all active TCP and UDP connections, their current state, and their associated process ID (PID)
Explanation of the Correct Answer
- The
netstat -abnocommand in Windows is designed to provide a comprehensive overview of all active network connections. The-aflag shows all connections and listening ports,-bshows the executable involved in creating the connection or listening port, and-ndisplays addresses and port numbers numerically. Therefore, the output includes both TCP and UDP connections. - The command displays the state of each connection (e.g., ESTABLISHED, LISTENING, CLOSE_WAIT), providing crucial information about the connection’s lifecycle.
- Crucially, the
-oflag adds the Process ID (PID) to the output, allowing you to identify which process is using each connection. This is vital for troubleshooting network issues.
Analysis of Other Options
- a. local routing table: The
netstatcommand doesn’t directly display the routing table. Other commands, likeroute print, are used for that purpose. - b. only active TCP connections in an ESTABLISHED state: This is incorrect because
netstat -abnoshows all connection states (ESTABLISHED, LISTENING, etc.) for both TCP and UDP. - c. only active UDP connections in an LISTENING state: This is incorrect as it only considers UDP connections in the LISTENING state and ignores other states and TCP connections entirely.
Key Takeaways
- The
netstatcommand is a powerful tool for network troubleshooting on Windows. Understanding its various options (-a,-b,-n,-o) is essential for effective network diagnostics. - Always check the documentation for the specific command and operating system to ensure you understand the output.
- The PID information provided by the
-oflag is invaluable for identifying the processes responsible for network activity.
See Full Answer
Open in App
Answered Feb 9 at 18:36 (Basic Model)
😉Want a more accurate answer?
We bring the world’s top AI models — our Super AI, OpenAI o1, Claude 3.5, GPT-4o, Gemini 2.0 — together in one place. Pick one and see how it solves your question!
1. What contains information on how hard drive partitions are organized?
- CPU
- MBR
- BOOTMGR
- Windows Registry
B. The master boot record (MBR) contains a small program that is responsible for locating and loading the operating system. The BIOS executes this code and the operating system starts to load.
2. Which net command is used on a Windows PC to establish a connection to a shared directory on a remote server?
- net use
- net start
- net share
- net session
A. The net command is a very important command in Windows. Some common net commands include the following:
net accounts: Sets password and logon requirements for users
net session: Lists or disconnects sessions between a computer and other
computers on the network
net share: Creates, removes, or manages shared resourcesnet start: Starts a network service or lists running network services
net stop: Stops a network service
net use: Connects, disconnects, and displays information about shared
network resources
net view: Shows a list of computers and network devices on the network
3. Which type of startup must be selected for a service that should run each time the computer is booted?
- Boot
- Manual
- Automatic
- Start
- Startup
C. An automatic startup will start the service automatically when the PC starts. The manual startup process will occur when the application is launched by a user. There is no boot, start, or startup service type that can be configured.
4. A user creates a file with a .ps1 extension in Windows. What type of file is it?
- PowerShell cmdlet
- PowerShell function
- PowerShell documentation
- PowerShell script
D. The types of commands that PowerShell can execute include the following:
Cmdlets: Perform an action and return an output or object to the next command that will be executed
PowerShell scripts: Files with a .ps1 extension that contain PowerShell commands that are executed
PowerShell functions: Pieces of code that can be referenced in a script
5. When a user makes changes to the settings of a Windows system, where are these changes stored?
- Control panel
- Registry
- win.ini
- boot.ini
B. The registry contains information about applications, users, hardware, network settings, and file types. The registry also contains a unique section for every user, which contains the settings configured by that particular user.
6. Which Windows version was the first to introduce a 64-bit Windows operating system?
- Windows NT
- Windows XP
- Windows 7
- Windows 10
B. There are more than 20 releases and versions of the Windows operating system. The Windows XP release introduced 64-bit processing to Windows computing.
7. Two pings were issued from a host on a local network. The first ping was issued to the IP address of the default gateway of the host and it failed. The second ping was issued to the IP address of a host outside the local network and it was successful. What is a possible cause for the failed ping?
- The default gateway device is configured with the wrong IP address.
- The TCP/IP stack on the default gateway is not working properly.
- The default gateway is not operational.
- Security rules are applied to the default gateway device, preventing it from processing ping requests.
D. If the ping from one host to another host on a remote network is successful, this indicates that the default gateway is operational. In this scenario, if a ping from one host to the default gateway failed, it is possible that some security features are applied to the router interface, preventing it from responding to ping requests.
8. Which command is used to manually query a DNS server to resolve a specific hostname?
- net
- tracert
- nslookup
- ipconfig /displaydns
C. The nslookup command was created to allow a user to manually query a DNS server to resolve a given host name. The ipconfig /displaydns command only displays previously resolved DNS entries. The tracert command was created to examine the path that packets take as they cross a network and can resolve a hostname by automatically querying a DNS server. The net command is used to manage network computers, servers, printers, and network drives.
9. What is the purpose of the cd\ command?
- changes directory to the previous directory
- changes directory to the root directory
- changes directory to the next highest directory
- changes directory to the next lower directory
B. CLI commands are typed into the Command Prompt window of the Windows operating system. The cd\ command is used to change the directory to the Windows root directory.
10. How much RAM is addressable by a 32-bit version of Windows?
- 4 GB
- 8 GB
- 16 GB
- 32 GB
A. A 32-bit operating system is capable of supporting approximately 4 GB of memory. This is because 2^32 is approximately 4 GB.
11. How can a user prevent specific applications from accessing a Windowscomputer over a network?
- Enable MAC address filtering.
- Disable automatic IP address assignment.
- Block specific TCP or UDP ports in Windows Firewall.
- Change default usernames and passwords.
C. Network applications have specific TCP or UDP ports that can be left open or blocked in Windows Firewall. Disabling automatic IP address assignment may result in the computer not being able to connect to the network at all. Enabling MAC address filtering is not possible in Windows and would only block specific network hosts, not applications. Changing default usernames and passwords will secure the computer from unauthorized users, not from applications.
12. What utility is used to show the system resources consumed by each user?
- Task Manager
- User Accounts
- Device Manager
- Event Viewe
A. The Windows Task Manager utility includes a Users tab from which the system resources consumed by each user can be displayed.
13. What utility is available on a Windows PC to view current running applications and processes?
- nslookup
- ipconfig
- Control Panel
- Task Manager
On a Windows PC the Task Manager utility can be used to view the applications, processes, and services that are currently running.
14. A user logs in to Windows with a regular user account and attempts to use an application that requires administrative privileges. What can the user do to successfully use the application?
- Right-click the application and choose Run as root.
- Right-click the application and choose Run as Priviledge.
- Right-click the application and choose Run as Administrator.
- Right-click the application and choose Run as Superuser.
As a security best practice, it is advisable not to log on to Windows using the Administrator account or an account with administrative privileges. When it is necessary to run or install software that requires the privileges of the Administrator, the user can right-click the software in the Windows File Explorer and choose Run as Administrator.
15. A technician can ping the IP address of the web server of a remote company but cannot successfully ping the URL address of the same web server. Which software utility can the technician use to diagnose the problem?
- nslookup
- tracert
- netstat
- ipconfig
Traceroute (tracert) is a utility that generates a list of hops that were successfully reached along the path from source to destination.This list can provide important verification and troubleshooting information. The ipconfig utility is used to display the IP configuration settings on a Windows PC. The Netstat utility is used to identify which active TCP connections are open and running on a networked host. Nslookup is a utility that allows the user to manually query the name servers to resolve a given host name. This utility can also be used to troubleshoot name resolution issues and to verify the current status of the name servers.
16. Where are the settings that are chosen during the installation process stored?
- in the recovery partition
- in flash memory
- in the Registry
- in BIOS
The Registry contains all settings chosen from Control Panels, file associations, system policies, applications installed, and application license keys.
17. What technology was created to replace the BIOS program on modern personal computer motherboards?
- CMOS
- MBR
- RAM
- UEFI
As of 2015, most personal computer motherboards are shipped with UEFI as the replacement for the BIOS program.
18. Which two things can be determined by using the ping command? (Choose two.)
- the number of routers between the source and destination device
- the destination device is reachable through the network
- the average time it takes each router in the path between source and destination to respond
- the IP address of the router nearest the destination device
- the average time it takes a packet to reach the destination and for the response to return to the source
A ping command provides feedback on the time between when an echo request was sent to a remote host and when the echo reply was received. This can be a measure of network performance. A successful ping also indicates that the destination host was reachable through the network.
19. What function is provided by the Windows Task Manager?
- It provides an active list of TCP connections.
- It maintains system logs.
- It selectively denies traffic on specified interfaces.
- It provides information on system resources and processes.
Windows Task Manager enables an end user to monitor applications, processes, and services currently running on the end device. It can be used to start or stop programs, stop processes, and display informative statistics about the device.
20. Which type of Windows PowerShell command performs an action and returns an output or object to the next command that will be executed?
- scripts
- functions
- cmdlets
- routines
The types of commands that PowerShell can execute include the following:cmdlets – perform an action and return an output or object to the next command that will be executed
PowerShell scripts – files with a .ps1 extension that contain PowerShell commands that are executed
PowerShell functions – pieces of code that can be referenced in a script
21. What would be displayed if the netstat -abno command was entered on a Windows PC?
- all active TCP and UDP connections, their current state, and their associated process ID (PID)
- only active TCP connections in an ESTABLISHED state
- only active UDP connections in an LISTENING state
- a local routing table
With the optional switch -abno, the netstat command will display all network connections together with associated running processes. It helps a user identify possible malware connections.
22. Which two commands could be used to check if DNS name resolution is working properly on a Windows PC? (Choose two.)
- ipconfig /flushdns
- net cisco.com
- nslookup cisco.com
- ping cisco.com
- nbtstat cisco.com
The ping command tests the connection between two hosts. When ping uses a host domain name to test the connection, the resolver on the PC will first perform the name resolution to query the DNS server for the IP address of the host. If the ping command is unable to resolve the domain name to an IP address, an error will result.
Nslookup is a tool for testing and troubleshooting DNS servers.
23. Refer to the exhibit. A cyber security administrator is attempting to view system information from the Windows PowerShell and recieves the error message shown. What action does the administrator need to take to successfully run the command?
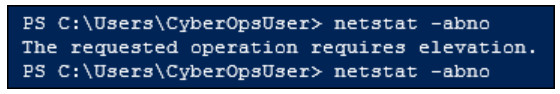
- Run the command from the command prompt.
- Install latest Windows updates.
- Restart the abno service in Task Manager.
- Run PowerShell as administrator.
Best practices advise not to log into systems with an administrator account, but rather a user account. When logged in as a user it is possible to run Windows utilitites, such as PowerShell and the Command Prompt as an administrator by right clicking on the utility and slecting Run as Administrator.
24. Refer to the exhibit. A cybersecurity analyst is investigating a reported security incident on a Microsoft Windows computer. Which tool is the analyst using?
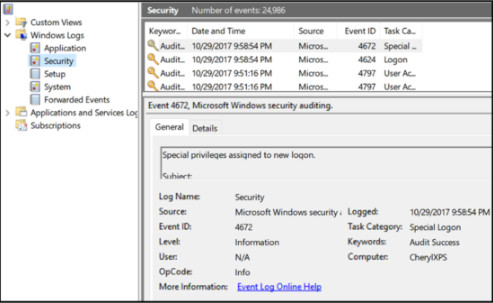
- Event Viewer
- PowerShell
- Task Manager
- Performance Monitor
Event Viewer is used to investigate the history of application, security, and system events. Events show the date and time that the event occurred along with the source of the event. If a cybersecurity analyst has the address of the Windows computer targeted and/or the date and time that a security breach occurred, the analyst could use Event Viewer to document and prove what occurred on the computer.
25. For security reasons a network administrator needs to ensure that local computers cannot ping each other. Which settings can accomplish this task?
- firewall settings
- MAC address settings
- smartcard settings
- file system settings
Smartcard and file system settings do not affect network operation. MAC address settings and filtering may be used to control device network access but cannot be used to filter different data traffic types.
26. Consider the path representation in Windows CLI C:\Users\Jason\Desktop\mydocu.txt. What does the Users\Jason component represent?
- file directory and subdirectory
- current file directory
- file attribute
- storage device or partition
In the path representation in Windows CLI, the components of C:\Users\Jason\Desktop\mydocu.txt are as follows:C:\ represents the root directory of the storage device.
Users\Jason represents the file directory.
Desktop represents the current file directory.
The mydocu.txt represents the user file.
27. Which two user accounts are automatically created when a user installs Windows to a new computer? (Choose two.)
- superuser
- guest
- root
- administrator
- system
When a user installs Windows, two local user accounts are created automatically during the process, administrator and guest.
28. What term is used to describe a logical drive that can be formatted to store data?
- partition
- track
- sector
- cluster
- volume
Hard disk drives are organized by several physical and logical structures. Partitions are logical portions of the disk that can be formatted to store data. Partitions consist of tracks, sectors, and clusters. Tracks are concentric rings on the disk surface. Tracks are divided into sectors and multiple sectors are combined logically to form clusters
29. What is the purpose of entering the netsh command on a Windows PC?
- to create user accounts
- to test the hardware devices on the PC
- to change the computer name for the PC
- to configure networking parameters for the PC
The netsh.exe tool can be used to configure networking parameters for the PC from a command prompt.
30. A technician is troubleshooting a PC unable to connect to the network. What command should be issued to check the IP address of the device?
- ipconfig
- ping
- tracert
- nslookup
The commands tracert and ping are used to test the connectivity of the PC to the network. The command nslookup initiates a query to an Internet domain name server.
31. Refer to the exhibit. Which Microsoft Windows application is being used?
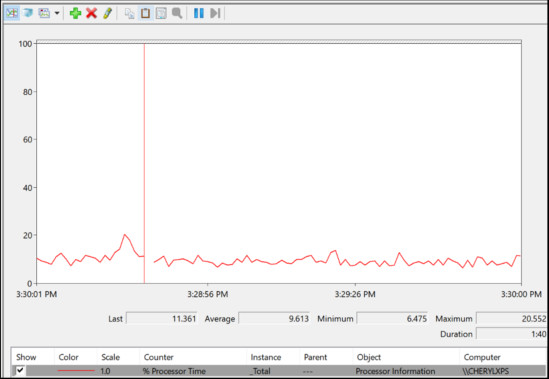
- Event Viewer
- PowerShell
- Task Manager
- Performance Monitor
Windows Performance Monitor is used to evaluate the performance of individual components on a Windows host computer. Commonly monitored components include the processor, hard drive, network, and memory. Windows Task Manager and Performance Monitor are used when malware is suspected and a component is not performing the way it should.
32. What are two reasons for entering the ipconfig command on a Windows PC? (Choose two.)
- to review the network configuration on the PC
- to check if the DNS server can be contacted
- to ensure that the PC can connect to remote networks
- to review the status of network media connections
- to display the bandwidth and throughput of the network connection
The command ipconfig is a useful tool for troubleshooting. The command will display some IP addressing configuration and the network media connection status. The command does not test the connection to the DNS server configured or test remote networks. It does not display bandwidth and throughput information.
33. What are two advantages of the NTFS file system compared with FAT32? (Choose two.)
- NTFS allows the automatic detection of bad sectors.
- NTFS is easier to configure.
- NTFS allows faster formatting of drives.
- NTFS provides more security features.
- NTFS supports larger files.
- NTFS allows faster access to external peripherals such as a USB drive.
The file system has no control over the speed of access or formatting of drives, and the ease of configuration is not file system-dependent.
34. What is the purpose of using the net accounts command in Windows?
- to start a network service
- to display information about shared network resources
- to show a list of computers and network devices on the network
- to review the settings of password and logon requirements for users
These are some common net commands:
net accounts – sets password and logon requirements for users
net start – starts a network service or lists running network services
net use – connects, disconnects, and displays information about shared network resources
net view – shows a list of computers and network devices on the network
When used without options, the net accounts command displays the current settings for password, logon limitations, and domain information.
35. What are two reasons for entering the ping 127.0.0.1 command on a Windows PC? (Choose two.)
- to check if the NIC functions as expected
- to check if the default gateway is configured correctly
- to display the bandwidth and throughput of the network connection
- to check if the TCP/IP protocol suite is installed properly
- to ensure that the PC can connect to remote networks
The IP address 127.0.0.1 is a loopback address on the PC. A successful ping to the loopback address indicates that the TCP/IP protocol suite is installed properly and the NIC is working as expected. A ping to the loopback address does not test the connectivity to remote networks, nor will it display bandwidth and throughput information.
36. When restrictive security policy is implemented on a firewall, only certain required ports are opened
37. Match the Windows command to the description.
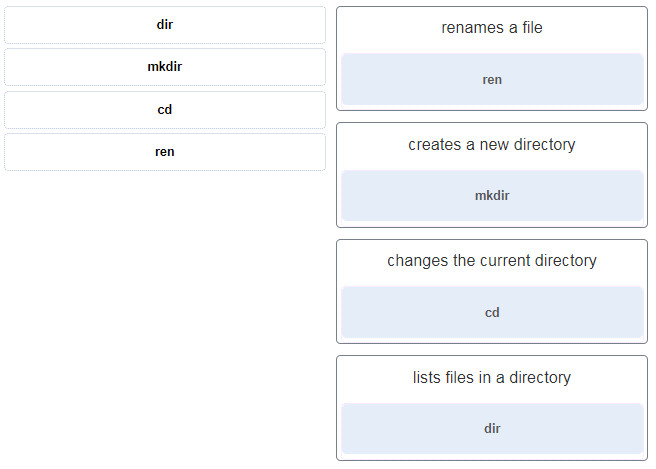
- dir ~~> lists files in a directory
- mkdir ~~> creates a new directory
- cd ~~> changes the current directory
- ren ~~> renames a file
38. Match the definition to the Microsoft Windows term. (Not all options are used.)
- runs in the background to support the operating system and applications ~~> service
- instructions executed by the processor ~~> thread
- a currently executing program ~~> process
- (empty) ~~> registry
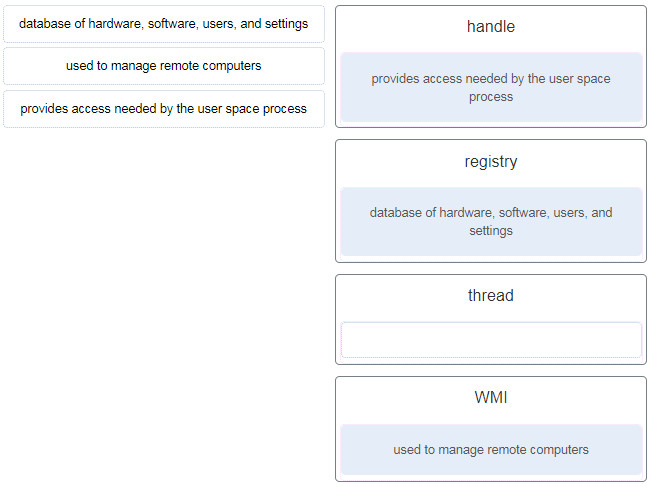
39. Match the definition to the Microsoft Windows term. (Not all options are used.)

- database of hardware, software, users, and settings ~~> registry
- used to manage remote computers ~~> WMI
- provides access needed by the user space process ~~> handle
- (empty) ~~> thread
40. Match the Windows term to the description.
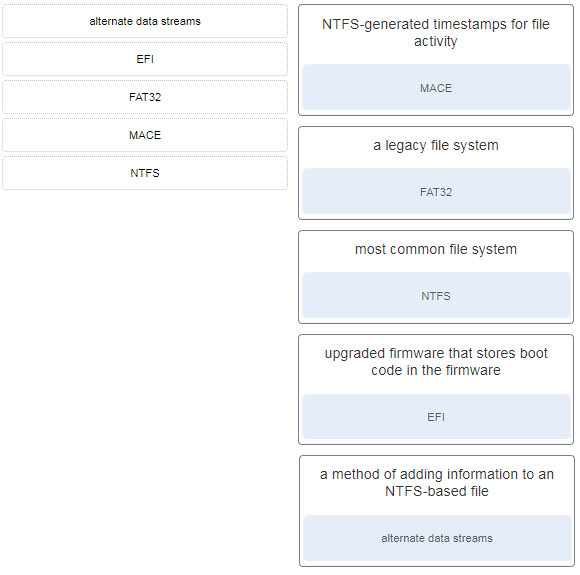
- alternate data streams ~~> a method of adding information to an NTFS-based file
- EFI ~~> upgraded firmware that stores boot code in the firmware
- FAT32 ~~> a legacy file system
- MACE ~~> NTFS-generated timestamps for file activity
- NTFS ~~> most common file system
-
[DOWNLOAD] Chapter 19 Test Form A Answers | updated!
Which Windows version was the first to introduce a bit Windows operating system? There are more than 20 releases and versions of the Windows operating system. The Windows XP release introduced bit processing to Windows computing. Two pings were…
-
[FREE] Chapter 19 Test Form A Answers | new!
In this scenario, if a ping from one host to the default gateway failed, it is possible that some security features are applied to the router interface, preventing it from responding to ping requests. Which command is used to manually query a DNS…
-
World History Chapter 19 Test
Enabling MAC address filtering is not possible in Windows and would only block specific network hosts, not applications. Changing default usernames and passwords will secure the computer from unauthorized users, not from applications. What utility is used to show the system resources consumed by each user? The Windows Task Manager utility includes a Users tab from which the system resources consumed by each user can be displayed. What utility is available on a Windows PC to view current running applications and processes? A user logs in to Windows with a regular user account and attempts to use an application that requires administrative privileges. What can the user do to successfully use the application? Right-click the application and choose Run as root. Right-click the application and choose Run as Priviledge. Right-click the application and choose Run as Administrator.
https://chfk.r5motorsport.it/plc-connector-cable.html
read more
-
Traditions And Encounters, AP Edition (Bentley), 5th Edition
Right-click the application and choose Run as Superuser. As a security best practice, it is advisable not to log on to Windows using the Administrator account or an account with administrative privileges. When it is necessary to run or install software that requires the privileges of the Administrator, the user can right-click the software in the Windows File Explorer and choose Run as Administrator.
https://benoitsreligionclasses.weebly.com/why-study-world-religions—intro.html
read more
-
Ch.19 Test Review
A technician can ping the IP address of the web server of a remote company but cannot successfully ping the URL address of the same web server. Which software utility can the technician use to diagnose the problem? This list can provide important verification and troubleshooting information. The Netstat utility is used to identify which active TCP connections are open and running on a networked host.
https://classmarker.com/online-test/start/?quiz=yyx5b2eeb279b4cd
read more
-
Matthew 19 – Jesus Teaches On Marriage, Divorce, Riches, And Discipleship
Nslookup is a utility that allows the user to manually query the name servers to resolve a given host name. This utility can also be used to troubleshoot name resolution issues and to verify the current status of the name servers. Where are the settings that are chosen during the installation process stored? What technology was created to replace the BIOS program on modern personal computer motherboards? Which two things can be determined by using the ping command? Choose two. This can be a measure of network performance. A successful ping also indicates that the destination host was reachable through the network. What function is provided by the Windows Task Manager? It provides an active list of TCP connections. It maintains system logs. It selectively denies traffic on specified interfaces. It provides information on system resources and processes. Windows Task Manager enables an end user to monitor applications, processes, and services currently running on the end device.
http://render-test.logomakr.com/cgi-bin/file.php?article=county.eligibility.technician.study.guide.pdf&code=4383cef6989c2bc4297616d66e94ecc7
read more
-
Chapter 19 Quiz
It can be used to start or stop programs, stop processes, and display informative statistics about the device. Which type of Windows PowerShell command performs an action and returns an output or object to the next command that will be executed? What would be displayed if the netstat -abno command was entered on a Windows PC? It helps a user identify possible malware connections.
https://github.com/monero-ecosystem/xmrto_wrapper
read more
-
Test Chapter 19/20
Cost drivers Job costing systems are best suited to those situations where goods are made upon the receipt of a customer order, according to customer specifications, or in a separate batch. Such would be the case with helicopter manufacturing but not with the other examples cited as they would be more likely produced in a continuous process. Selling costs do not appear on a job cost sheet, only manufacturing costs. The other statements are all true. The Work in Process account captures the actual direct labor and direct material costs, as well as the applied overhead. Actual overhead is recorded in the Factory Overhead account. The Factory Overhead account is credited for the amount of applied overhead and debited for the amount of actual overhead. The resulting balance is frequently closed to the Cost of Goods Sold account. Indirect materials and indirect labor are examples of actual overhead which would be debited to the Factory Overhead account.
https://manoramaonline.com/global-malayali/gulf.html
read more
-
FindTestAnswers.com
Dividing the estimated factory overhead by the estimated application base is the correct formula to determine the overhead application rate. It reveals an amount of estimated overhead per unit of application base. A credit balance in the Factory Overhead account indicates that the applied overhead exceeded the actual overhead thereby resulting in overapplied overhead. One would not ordinarily expect actual and applied overhead to be the same, and the extent of under- or overapplied overhead does not necessarily indicate a profit or loss for the period. Theoretically, the amount of under- or overapplied overhead should be distributed among work in process, finished goods, and cost of goods sold on a logical and equitable basis. However, for expediency, many companies will simply close the over- or underapplied amount to cost of goods sold. The Factory Overhead account would be credited for the applied overhead. Independently, the Factory Overhead account is debited for the actual overhead incurred.
https://docs.google.com/document/d/1GDLOzIQyZMAGx-afxUP_Z6taJOYf62Ihq2RkuLz0hS0/edit#!
read more
-
American History 2—HIST 2112 (OER): Chapter 19: American Empire
Overhead application bases are said to be cost drivers, or the factors that cause specific costs to be incurred within an organization.
https://repository.seafdec.org.ph/handle/10862/3324
read more
-
Charlotte’s Web: Chapter 19
Democrats most often won the presidency. Republicans usually held a majority in the Senate. Republicans usually held a majority in the House. Garfield A. All these answers are correct. Arthur A. Democrats who crossed over party lines to support Grover Cleveland. Grover Cleveland. Benjamin Harrison. Chester A. Roscoe Conkling. James G. William McKinley became a party leader in Congress. Democrats lost the presidency in Republicans suffered significant political losses that year. None of these answers is correct. Louis, and Pacific Railway Co. Illinois that A. At their peak, Grange supporters controlled the legislatures of most Midwest states. It attempted to teach new scientific farming techniques to its members. It sought to regulate the power and practices of railroads and warehouses. It was greatly strengthened by the end of the economic depression in the late s. The political inexperience of many Grange leaders hurt the movement. To many middle-class Americans, the major labor upheavals of the late nineteenth century A.
https://guides.lib.uoguelph.ca/MBG2040
read more
-
Big Ideas Math Answers Grade 6 Chapter 5 Algebraic Expressions And Properties
William McKinley. Mark Hanna. William Jennings Bryan. James Weaver. William McKinley carry the rural vote. William Jennings Bryan earn his greatest support in the industrial Northeast. William Jennings Bryan win the popular vote but lose the electoral vote. Richard Olney. Alfred T. Leonard Wood. Arthur MacArthur. William Hooper. King Kamehameha I. Queen Liliuokalani. King Kamehameha III. Pago Pago. Puerto Rico. Joseph Pulitzer. Henry Luce. William R. Horace Greeley. William Randolph Hearst. Elihu Root. Theodore Roosevelt. John Hay. The war lasted only a few months with fewer than American battle casualties. Army soldiers were well-equipped and supplied. More than 5, U. Cuban rebels did most of the fighting even after the Americans joined in the war. National Guard units. Cubans refuse to fight alongside of U.
https://mcgill.ca/skillsets/files/skillsets/powerpointguidelines.pdf
read more
-
CSCS Quiz Chapter 19
African-Americans realize that the U. Havana Harbor. Manila Bay. It was effectively crushed by the Spanish. It prompted Spain to abolish slavery in Puerto Rico. It eventually prompted Spain to give Puerto Rico some degree of independence. All these answers are correct answer E. All these answers are correct question In , supporters of the annexation of the Philippines argued the United States had set a precedent for taking land while treating its inhabitants as dependents in the case of A. In the early s, which American dependency did NOT receive territorial status? Cuba B. Alaska C. Puerto Rico D. Hawaii E. All received territorial status. Cuba question The Platt Amendment was directed at A. European imperial powers. Guam and Tutuila. Cuba answer E. Cuba question According to the terms of the Platt Amendment, A. Cuba could only form treaties with nations that were allied with the United States.
https://sinergiagaz.net/post.php?name=english-exam-essay-2007
read more
-
Chapter 12 Form A Test World History Glenco Answers
Cuba was to be made a demilitarized region. Cuba was to be granted full political independence. Emilio Aguinaldo. Arthur Macarthur. William Howard Taft. William Shafter.
https://careerspages.com/vmmc-sjh-answer-key-senior-resident-answer-paper-download/
read more
-
Service Unavailable In EU Region
Jesus teaches on marriage, divorce, and celibacy. Now it came to pass, when Jesus had finished these sayings, that He departed from Galilee and came to the region of Judea beyond the Jordan. And great multitudes followed Him, and He healed them there. He departed from Galilee and came to the region of Judea: The records of Matthew, Mark, and Luke focus on the Galilean ministry of Jesus, and only emphasize His presence in Jerusalem right before His crucifixion and resurrection.
https://justanswer.com/math-homework/30vjv-need-help-66-problem-math-assignment-working.html
read more
-
IAHCSMM CRCST Practice Test Question & Answers
Yet it would be a mistake to believe that this trip from Galilee to the region of Judea was unusual for Jesus. That the Greek word peran, especially with a genitive case as here, has sometimes this signification, see on John Great multitudes followed Him, and He healed them there: Matthew points this out so his readers understand that the popularity and power of Jesus was not restricted to Galilee.
http://tci-proficiency.weebly.com/cb-exam-answer-keys.html
read more
-
Chapter 12 Form A Test World History Glenco Answers — 1medicoguia.com
It was also evident in Judea. The Pharisees also came to Him, testing Him: This continues the theme of conflict and controversy with the religious leaders. Now Jesus, in Judea is questioned by them — and their questions were not honest. They asked this, testing Him. They hoped to trap Jesus. The first was the school of Rabbi Shammai a more strict and unpopular view and second was the school of Rabbi Hillel a more lax and popular view. Among the Jews of that day, marriage was a sacred duty. In theory, the Jews of that day had a high ideal of marriage. Yet they had a low view of women. Their low view of women meant that their high ideal of marriage was constantly compromised, and those compromises were made into law, as with the thinking of Rabbi Hillel. Rabbi Akiba even went the length of saying…that a man could divorce his wife if he found a woman whom he liked better and considered more beautiful.
https://examplanning.com/english-grammar-exercises-with-answers/
read more
-
Ch Test Review | 1medicoguia.com
For just any reason: These words were the center of the debate. Each school of thought understood that the Mosaic law gave permission for divorce in Deuteronomy When a man takes a wife and marries her, and it happens that she finds no favor in his eyes because he has found some uncleanness in her, and he writes her a certificate of divorce, puts it in her hand, and sends her out of his house. The school of Rabbi Shammai understood that uncleanness meant sexual immorality, and said this was the only valid reason for divorce. Barclay says that the Rabbis had many sayings about bad marriages and the bad wife. They said that the man with a bad wife would never face hell, because he has paid for his sins on earth. They said that the man who is ruled by his wife has a life that is not life. They said that a bad wife is like leprosy to her husband, and the only way he could be cured is by divorce.
https://padasalai12.files.wordpress.com/2016/12/1015-12-bio-zoology-em-half-yearly-exam-answer-keys.pdf
read more
-
CCNA Cyber Ops (Version 1.1) – Chapter 2 Exam Answers Full
Testing Him: So in their question, the Pharisees tried to get Jesus to side with one teaching or the other. If He agreed with the strict school of Rabbi Shammai, then Jesus might become unpopular with the multitude, who generally liked access to an easy divorce. The religious leaders had reason to believe they had caught Jesus on the horns of a dilemma. So then, they are no longer two but one flesh. Therefore what God has joined together, let not man separate. Have you not read: The Pharisees wanted to talk about divorce and rabbinical opinions, but Jesus wanted to go back to the Scriptures and talk about marriage.
https://ippopotamopru.it/cvc-word-ladder-hut.html
read more
-
Charlotte’s Web: Chapter 19 Answer Key — 1medicoguia.com
Jesus began with the first marriage — the one between Adam and Eve. This emphasis on the Scriptures and on marriage, rather than divorce, is a wise approach for anyone interested in keeping a marriage together. He chose specially to set his seal upon a part of the story of creation — that story which modern critics speak of as if it were fable or myth. Divorce cannot be seen as a ready option when things are difficult in married life.
http://a4esl.org/a/v.html
read more
-
Answer Key Chapter 19 — U.S. History | OpenStax
Marriage is like a mirror; it reflects what we put into it. If one or both partners has divorce readily in their mind as a convenient option, divorce will be much more likely. By bringing the issue back to the Scriptural foundation of marriage, Jesus makes it plain that couples must forsake their singleness a man shall leave his father and mother , and come together in a one-flesh relationship that is both a fact they are…one flesh and a goal shall become one flesh. Adam said this at the creation of Eve. We are not the same, but we are one. Despite these fundamental, creation-rooted differences between the natures of men and women, God calls a husband and wife to come together as one, as one flesh.
https://coursehero.com/file/11327983/Exam-1-Practice/
read more
-
IAHCSMM CRCST Practice Test Question & Answers — ProProfs Quiz
The idea that they shall become one flesh includes the sexual union, but also goes far beyond it. But flesh in Hebrew thought represents the entire man, and the ideal unity of marriage covers the whole nature. It is a unity of soul as well as of body: of sympathy, interest, purpose. What God has joined together: Jesus also reminded the Pharisees that marriage is spiritually binding before God.
https://gb.abrsm.org/media/11787/grade_2y_model_answers_exemplar_2017.pdf
read more
-
CCNA 3 (v5.0.3 + V6.0) Chapter 4 Exam Answers 2021 – 100% Full
Marriage is not merely a social contract; and as God has joined, He expects man to honor what He has joined and to keep the marriage together. Among the ancients, when persons were newly married, they put a yoke upon their necks, or chains upon their arms, to show that they were to be one, closely united, and pulling equally together in all the concerns of life. And I say to you, whoever divorces his wife, except for sexual immorality, and marries another, commits adultery; and whoever marries her who is divorced commits adultery. Why then did Moses command to give a certificate of divorce, and to put her away: The Pharisees wrongly thought that God commanded divorce where there was uncleanness. The Pharisees thought that Moses was creating or promoting divorce. In fact, he was controlling it. Because of the hardness of your hearts: Divorce is never commanded, but permitted by God in certain circumstances, and God permits it because of the hardness of human hearts.
https://edpm.dc.gov/
read more
-
CCNA 3 (v + V) Chapter 10 Exam Answers – % Full
Sometimes the heart of the offending party is hard, and they will not do what must be done to reconcile the relationship. Sometimes the heart of the offended party is hard, and they refuse to reconcile and get past the offence even when there is contrition and repentance. Often the hardness of heart is on both sides. Except for sexual immorality: Jesus interpreted the meaning of the word uncleanness in the Mosaic Law, showing that it refers to sexual immorality, not just anything that might displease the husband.
https://stemeducationjournal.springeropen.com/articles/10.1186/s40594-020-00211-w
read more
-
CCNA 3 (v5.0.3 + V6.0) Chapter 10 Exam Answers 2021 – 100% Full
Therefore, divorce — and the freedom to remarry without sin — is only permitted in the case of sexual immorality. The ancient Greek word for sexual immorality is porneia. It is a broad word, covering a wide span of sexual impropriety. One may be guilty of porneia without actually having consummated an act of adultery. To this permission for divorce, the Apostle Paul added the case of abandonment by an unbelieving spouse 1 Corinthians These words of Paul show us that a Christian couple may in fact split up for reasons that do not justify a Biblical divorce.
https://babycenter.com/getting-pregnant/fertility/fertility-treatment-in-vitro-fertilization-ivf_4094
read more
-
Enduring Word Bible Commentary Matthew Chapter 19
It may be because of a misguided sense of spirituality; it may be because of general unhappiness, or conflict, or abuse, or misery, addiction, or poverty. Paul recognizes without at all encouraging that one might depart in such circumstance, but they cannot consider themselves divorced, with the right to remarry, because their marriage had not split up for reasons that justify a Biblical divorce.
https://cdph.ca.gov/Programs/CFH/DWICSN/CDPH%20Document%20Library/WICFoods/Shopping%20Guide_FAQs_%202019_FINAL.pdf
read more
-
Municode Library
These problems that are serious yet fall short of the Biblical permission for divorce may justify a separation, but the partners are expected to honor their marriage vows even in their separation, because as far as God is concerned, they are still married — their marriage covenant has not been broken for what God considers to be Biblical reasons. And marries another, commits adultery: The reason why a person who does not have a legitimate divorce commits adultery upon remarrying is because they are not divorced in the eyes of God.
https://multiservizi-bologna.it/ccna-modules-16-17-exam.html
read more
-
Free Medical Flashcards About Test Chapter 19/20
Since their old marriage was never dissolved on Biblical grounds, that marriage is still valid and they are actually guilty of bigamy and adultery. This teaching of Jesus shows us that marriage, as a promise made to God, to our spouse and to the world, is a binding promise, and cannot be broken at our own discretion. If God does not recognize the promise being broken, then it is not. One must admit that this is a hard teaching from Jesus. There are many reasons people give today to justify divorce that do not fulfill the two Biblical allowances for divorce. There are also many situations where a marriage is separated or divorced for reasons that do not fulfill the Biblical allowance for divorce, but later one or more of the spouses goes on to give Biblical allowance, often by marriage or sexual relations with another.
http://agency.governmentjobs.com/illinois/default.cfm?action=viewjob&JobID=89532
read more
Enterprise Networking Planet content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More.
Is there a bot or Trojan horse listening for incoming connections on your Windows domain controller right now? Having the skills necessary to answer that question is essential for any Windows server administrator. After reading this article you will be better able to answer that question as well as detect and analyze the legitimate programs that are listening and communicating on any of your Windows hosts.
The key to understanding what programs are listening for incoming connections and actively communicating on your Windows machines is the netstat.exe utility. After a brief introduction to TCP/IP ports we’ll look at netstat.exe and some of its practical uses.
Very Brief Introduction to Ports
When using netstat.exe to diagnose problems or troubleshoot a firewall issue, it is important to have a basic understanding of ports. To send information across a TCP/IP network you must, of course, have a source and a destination IP address, but you must also have a source and a destination port. The destination port lets the operating system know which program on the destination computer should receive the information, and the source port lets the receiving program know which port to specify on its reply. If you sent a letter to an apartment building without specifying the apartment number, the mailman would not know where to deliver the letter. The same is true when sending information across a TCP/IP-based network such as the Internet. Each networked program running on your computer needs an “apartment number,” or port.
Netstat.exe
You’re going to have to drop to the command line to use netstat.exe so the first step to using netstat.exe is opening up a command prompt. You can get to a command prompt in XP/Server2003 from the Start menu under All Programs -> Accessories -> Command Prompt or via Start -> Run -> “cmd” -> Enter.
Note: A handy little shortcut to opening a Run window is Windows Button + R. This shortcut is especially useful in Vista because Microsoft removed the Run option from the default Start menu.
A good way to start getting comfortable with netstat.exe is by reading the help text:
netstat /?
Figure 1 reveals a variety of command line switches available to you with netstat.exe. If you run netstat.exe without any switches you will see a list of active connections. Running netstat.exe on a machine that has no active connections will look like the screenshot in figure 2.
This will probably be the last time you see netstat.exe running with no output. Typically there are all sorts of active connections, but I’m cheating with a bare bones virtual installation of XP. After opening a connection to Microsoft Update the output looks like that in figure 2.
There are four netstat.exe switches that will be most useful to you:
- -a will cause all connections and listening ports to be displayed. What we are really after here are the listening ports.
Note: Previous to WinXP/WindowsServer2003 the netstat.exe command does not have the ability to display listening ports. - -b comes in handy when you are trying to find out what port a particular program is listening on. “-b” causes netstat.exe to display the name of the executable that opened each connection or listening port.
- -n is useful because by default netstat.exe will hide the actual port number from you for protocols that it “knows” about. For example, one of the ports that Windows XP listens on by default is 445. If you run netstat.exe without the -n switch it will display “microsoft-ds” instead of the port number. In some cases this may be useful and in others it might be a hindrance.
- -o causes netstat.exe to display the process identifier (PID) of each program in the connection list. The PID can be used to trace a connection back to a process listed in the Windows Task Manager.
Figure 4 shows what “netstat -ano” looks like on a bare bones install of Windows XP (leaving out the -o for brevity).
This is the good stuff right here. With this information you can see what processes are currently listening for incoming connections. If there were active connections you would also see those listed. There are various uses for this information including investigating a system for malware and tracking down firewall exceptions.
Practical Uses
If you are trying to punch a hole in your firewall for a web server there is plenty of documentation out there that would lead you to ports 80 (http) and 443 (https). But what if you need to allow incoming connections to your Windows machine for a more obscure program like backup software? This is a cinch with netstat.exe. Simply run “netstat -abno” while your backup software is running and look for the backup software executables. Plug the associated ports into your firewall exception list and you should be good to go. With the Windows firewall you can also just add the executable itself to the exception list.
So what about that domain controller we mentioned at the beginning of this article? It’s not a simple task to determine if malware is running on your domain controller, especially if it has already subverted your anti-virus software, but netstat.exe can help. By comparing the listening ports and active connections to a known good domain controller you can look for differences and odd behavior. You could also compare the list of established connections to a black list provided by organizations like Spamhaus.
Finally, let’s look at how to link a connection displayed by netstat.exe with a process listed in Windows Task Manager. Often times you can just run a “netstat -abno” and find the appropriate process name listed in Windows Task Manager, but what if there are two or more processes with the same name? In figure 5 you’ll notice that svchost.exe is listed several times by “netstat -abno” and Windows Task Manager. The PID can be used to find an exact match, but first you’ll need to display the PID in Task Manger. Ctrl-Alt-Del -> Task Manager -> Processes Tab -> View -> Select Columns -> Check the box for PID -> OK. Now you can definitively link a connection listed by netstat.exe with a process in Windows Task Manger.
As promised, you should now be able to see if there are any naughty programs listening for incoming connections on your domain controllers as well as any other Windows machine. You can also trace that process to the Windows Task Manager and cancel the process. Happy hunting.
Open the Start menu, type “Command Prompt ” and select Run as administrator. Now, type “netstat -ab” and hit Enter. Wait for the results to load, port names will be listed next to the local IP address. Just look for the port number you need, and if it says LISTENING in the State column, it means your port is open.
How do you check what port is being used?
Checking which application is using a port: Open the command prompt – start >> run >> cmd or start >> All Programs >> Accessories >> Command Prompt. Type netstat -aon | findstr ‘[port_number]’ . If the port is being used by any application, then that application’s detail will be shown. Type tasklist | findstr ‘[PID]’ .
How can I tell if a port is being used Windows?
In order to check which application is listening on a port, you can use the following command from the command line: For Microsoft Windows: netstat -ano | find “1234” | find “LISTEN” tasklist /fi “PID eq “1234” For Linux: netstat -anpe | grep “1234” | grep “LISTEN”.
Open a command prompt window (as Administrator) From “Start\Search box” Enter “cmd” then right-click on “cmd.exe” and select “Run as Administrator” Enter the following text then hit Enter. netstat -abno. Find the Port that you are listening on under “Local Address” Look at the process name directly under that.
What is port 135 commonly used for?
Microsoft Windows Networking Services Port 135 is used for RPC client-server communication; ports 139 and 445 are used for authentication and file sharing.
How do I stop ports being used?
Here’s how you can close it without having to reboot your computer or change your application’s port. Step 1: Find the connection’s PID. netstat -ano | findstr :yourPortNumber. Step 2: Kill the process using it’s PID. tskill yourPID. Step 3: Restart your server. Step 4: Stop your server properly.
How can I tell if a port is blocked?
The best way to check if a port is blocked is to do a port scan from the client machine. Listening means the server is listening on the specified port. Filtered means it received a TCP acknowledgement packet with the Reset flag set which likely indicates a firewall or software issue.
How can I tell if port 1433 is open?
You can check TCP/IP connectivity to SQL Server by using telnet. For example, at the command prompt, type telnet 192.168. 0.0 1433 where 192.168. 0.0 is the address of the computer that is running SQL Server and 1433 is the port it is listening on.
What is netstat TCP?
Netstat, the TCP/IP networking utility, has a simple set of options and identifies a computer’s listening ports, along with incoming and outgoing network connections. This data can be very helpful if you’re trying to resolve a malware issue or diagnose a security problem.
What does it mean when a port is listening?
Listening port is a network port on which an application or process listens on, acting as a communication endpoint. Each listening port can be open or closed (filtered) using a firewall. In general terms, an open port is a network port that accepts incoming packets from remote locations.
How do I know if a port is open Windows 443?
You can test whether the port is open by attempting to open an HTTPS connection to the computer using its domain name or IP address. To do this, you type https://www.example.com in your web browser’s URL bar, using the actual domain name of the server, or https://192.0.2.1, using the server’s actual numeric IP address.
How do I check if a UDP port is open windows?
To view the TCP/UDP open port state of a remote host, type “portqry.exe –n [hostname/IP]” where [hostname/IP] is replaced with the hostname or IP address of the remote host.
Why is it necessary to close open ports in your system?
Close server ports and deny remote access In some cases, it is necessary to close ports for your application(s) to increase security. From the list of inbound rules, find the rule for the port you wish to close.
What is port 139 commonly used for?
Port 139 is used by SMB dialects that communicate over NetBIOS. It’s a transport layer protocol designed to use in Windows operating systems over a network.
What are common ports?
Some of the most commonly used ports, along with their associated networking protocol, are: Ports 20 and 21: File Transfer Protocol (FTP). Port 22: Secure Shell (SSH). Port 25: Simple Mail Transfer Protocol (SMTP). Port 53: Domain Name System (DNS). Port 80: Hypertext Transfer Protocol (HTTP).
What is 445 port used for?
Port 445 is a traditional Microsoft networking port with tie-ins to the original NetBIOS service found in earlier versions of Windows OSes. Today, port 445 is used by Microsoft Directory Services for Active Directory (AD) and for the Server Message Block (SMB) protocol over TCP/IP.
How do I fix ports already in use?
Troubleshooting a Port Already in Use >Stop the conflicting application as follows: a. Open the command prompt and enter netstat -aon | findstr “8080”. b. End the conflicting process: i. Open Windows Task Manager. ii. In the Processes tab, click View > Select Columns. iii. Choose PID and click OK. iv. c.
How do I fix 8080 port already in use?
On MS Windows, select Start > All Programs > Accessories > System Tools >Resource Monitor. Expand the Network Tab. Move to the section for Listening Ports. Look in the Port column and scroll to find entry for port 8080. Select the given process and delete/kill the process.
How can I tell if port 8080 is already in use?
Use the Windows netstat command to identify which applications are using port 8080: Hold down the Windows key and press the R key to open the Run dialog. Type “cmd” and click OK in the Run dialog. Verify the Command Prompt opens. Type “netstat -a -n -o | find “8080””. A list of processes using port 8080 are displayed.
How do I check my firewall ports?
Checking Windows Firewall for blocked ports Launch Command Prompt. Run netstat -a -n. Check to see if the specific port is listed. If it is, then it means that the server is listening on that port.
What does it mean if a port is closed?
In contrast, a port which rejects connections or ignores all packets directed at it is called a closed port. If there is no application listening on a port, incoming packets to that port will simply be rejected by the computer’s operating system.
How can I check if port 80 is open?
To check what’s using Port 80: Open Command Line and use netstat -aon | findstr :80. -a Displays all active connections and the TCP and UDP ports on which the computer is. Then, to find which programs are using it, take the PID number and put them in tasklist /svc /FI “PID eq [PID Number]” Closing programs should resolve.
