Продолжаем знакомиться с новыми возможностями ОС Windows Server 2012 R2. Ранее мы рассказывали о корпоративном аналоге DropBox в Windows Server 2012 R2 под названием Work Folders. Сегодня речь пойдет о еще одном новшестве новой серверной платформы – функции Web Application Proxy. Web Application Proxy – это новая функция роли Remote Access в Windows 2012 R2, позволяющая публиковать HTTP/ HTTPS приложения, расположенные в периметре корпоративной сети на клиентских устройствах (в первую очередь подразумеваются мобильные устройства) за ее периметром. Благодаря возможности интеграции c AD FS (служба может выступать в качестве ADFS-прокси), возможно обеспечить аутентификацию внешних пользователей, пытающихся получить доступ к опубликованным приложениям.
Web Application Proxy предоставляет такие же возможности публикации приложений, как и Forefront Unified Access Gateway (UAG), однако данная служба также позволяет взаимодействовать с другими серверами и сервисами, обеспечивая тем самым более гибкую и рациональную конфигурацию.
Web Application Proxy по сути выполняет функцию обратного прокси сервера (HTTP reverse proxy), организуя ретрансляцию запросов клиентов из внешней сети на внутренний сервер, и является межсетевым экраном на прикладном уровне.
Сервер со службой Web Application Proxy получает внешний HTTP/HTTPS трафик и терминирует его, после чего от своего имени инициирует новое подключение ко внутреннему приложению (веб-серверу). Т.е. внешние пользователи прямого доступа к внутреннему приложению реально не получают. Любой другой трафик, получаемый Web Application Proxy, отклоняется (в том числе отклоняются HTTP/HTTPS запросы, которые могут быть использованы при DoS, SSL и 0-day атаках).
Требования к организации Web Application Proxy и ключевые особенности:
- Систему можно развернуть на серверах с ОС Windows Server 2012 R2, включенных в домен Active Directory, с ролями AD FS и Web Application Proxy. Эти роли должны быть установлены на разных серверах.
- Необходимо обновить схему Active Directory до Windows Server 2012 R2 (обновлять контроллеры домена до Windows Server 2012 R2 не нужно)
- В качестве клиентских устройств поддерживаются устройства с ОС Windows, IOS (iPad и iPhone). Работы над клиентами для Android и Windows Phone пока еще не окончены
- Аутентификация клиентов осуществляется службой Active Directory Federation Services (ADFS), которая также выполняет функции ADFS – проксирования.
- Типовая схема размещения сервера с ролью Web Application Proxy представлена на рисунке. Данный сервер располагается в выделенной DMZ зоне и отделен от внешней (Интернет) и внутренней сети (Интранет) межсетевыми экранами. В этой конфигурации для работы Web Application Proxy требует наличия двух интерфейсов – внутреннего (Intranet) и внешнего (DMZ)

Установка роли ADFS в Windows Server 2012 R2
Для обеспечения дополнительной безопасности преаутентифкация внешних клиентов выполняется на сервере ADFS, в противном случае используется pass-through аутентификация на конечном сервере приложения (что менее секьюрно). Поэтому первый шаг при настройке Web Application Proxy – установка на отдельном сервере роли Active Directory Federation Services.
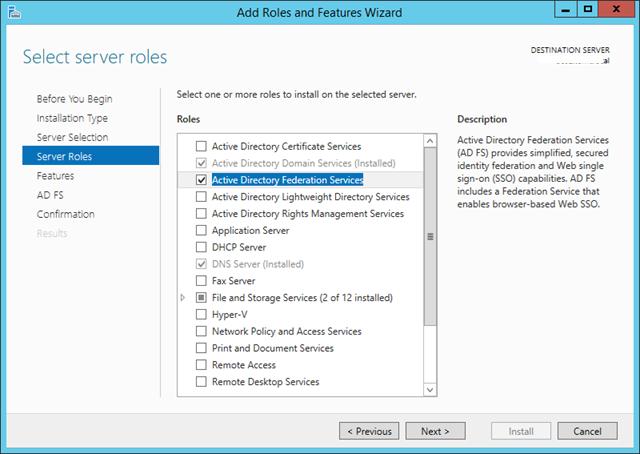
При установке ADFS нужно выбрать SSL сертификат, который будет использоваться для шифрования, а также DNS имена, которые будут использоваться клиентами при подключении (соответствующие записи в DNS зоне придется создать самостоятельно).
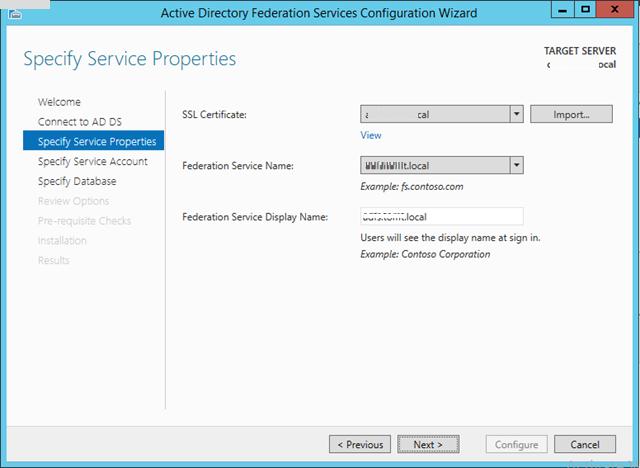
Затем нужно указать сервисную учетную запись для службы ADFS. Необходимо учесть, что имя ADFS должно быть указано в атрибут Service Principal Name аккаунта. Сделать это можно командой:
setspn –F –S host/adfs.winitpro.ru adfssvc
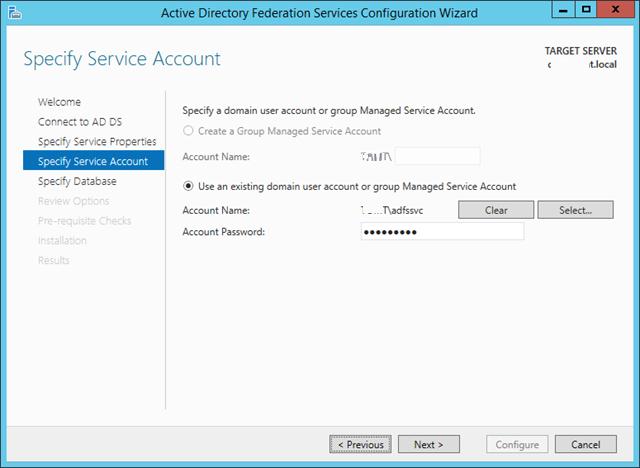
И, наконец, указать базу данных, в которой будет хранится информация: это может быть встроенная база на этом же сервере (WID — Windows Internal Database) или отдельная база на выделенном SQL-сервере.
Установка службы Web Application Proxy
Следующий этап, настройка самой службы Web Application Proxy. Напомним, что служба Web Application Proxy в Windows Server 2012 R2 является частью роли “Remote Access”. Установите службу Web Application Proxy и запустите мастер ее настройки.
На первом этапе мастер предложит Вам указать имя ADFS сервера и параметры учетной записи, имеющей доступ к данной службе.
Далее нужно указать сертификат (убедитесь, что в альтернативных именах сертификата содержится имя сервера ADFS).
Совет. Проверьте, что ваши DNSзоны настроены корректно: сервер с ролью WAP должен иметь возможность отрезолвить имя сервера ADFS, а он в свою очередь может разрешить имя прокси сервера. Сертификаты на обоих серверах должны включать имя службы федерации.
Публикация приложения через Web Application Proxy
После того, как установлены роли ADFS и Web Application Proxy (которая работает еще и как ADFS Proxy), можно перейти непосредственно к публикации наружу конкретного приложения. Сделать это можно с помощью консоли Remote Access Management Console.
Запустите мастер публикации и укажите, хотите ли вы использовать для преаутентификации службу ADFS (это именно наш вариант).
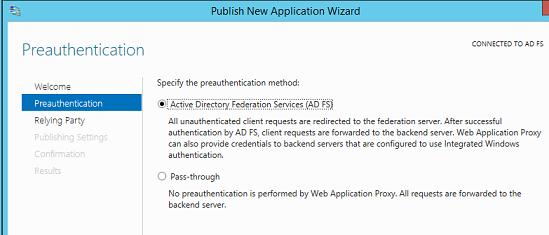
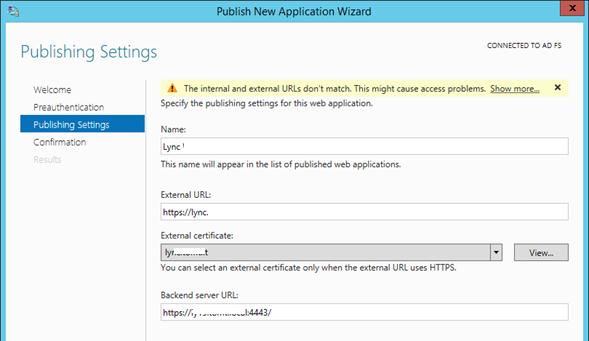
Затем нужно задать имя публикуемого приложения, используемый сертификат, внешний URL (имеенно его для подключения будут использовать внешние пользователи) и внутрений URL-адрес сервера, на который будут пересылаться запросы.
Совет. Если необходимо перенаправить внешнее приложение на альтернативный порт, необходимо задать его в URL, указаывающем на внутренний сервер. Например, если необходимо перенаправить внешние https запросы (443 порт) на 4443 порт, нужно указать:
Backend server URL: lync.winitpro.local:4443
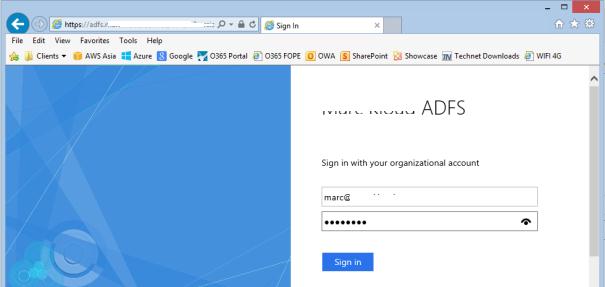
Завершите работу мастера, и на этом публикация приложений окончена. Теперь, если попытаться с помощью браузера зайти на опубликованный внешний URL-адрес, то браузер сначала будет перенаправлен на службу аутентификации (ADFS Proxy), а после успешной аутентификации пользователь будет отправлен непосредственно на внутренний сайт (веб приложение).
Благодаря новой службе Web Application Proxy в Windows Server 2012 R2 возможно реализовать функционал обратного прокси сервера с целью публикации внутренних служб предприятия наружу без необходимости использования задействовать сторонние файерволы и продукты, в том числе такие, как Forefront и пр.
Setup Microsoft Web Application Proxy (WAP) on Windows Server 2019/2022. In this post, we introduce Web application proxy, its advantages and working principles. After that, we move onto how to set up Microsoft Web Application Proxy on Windows Server running 2019 or 2022.
What is Microsoft Web Application Proxy (WAP)

- Primarily, WAP is intended to offer highly secure access to online services like Exchange and SharePoint without a VPN connection. By functioning as a reverse proxy, it accomplishes this by taking inbound requests from the internet and then forwarding them to the proper internal server.
- Secondly, WAP is also an effective application for organizations that must offer protected access to web applications from external networks. Equally, it contributes to the security of internal networks by serving as a reverse proxy and offering secure authentication, authorization, encryption, and load balancing.
How Microsoft Web Application Proxy (WAP) Works

Mainly, Web Application Proxy (WAP) functions by providing web applications with reverse proxy functionality. In turn, this indicates that it serves as a gatekeeper for receiving requests and stands between the web and an internal network. Therefore, the following steps are used to break down how WAP operates:
- Processing a request: An external user attempts to access a web application hosted on the internal network.
- Authentication: WAP eliminates the requirement for each application to design its own authentication process by providing a safe, central location for user authentication.
- Authorization: Following user authentication, WAP determines whether the user is permitted access to the requested resource. In more detail, it ensures that only users with authorized device access the business applications.
- Encryption: Sensitive data is secured while being transmitted due to WAP’s ability to encrypt communication between the client and the internal network.
- Balanced loading: Incoming requests get split among several internal servers using WAP, which boosts performance and helps to guarantee high availability.
- Request transmission: The inbound request is forwarded by WAP to the proper internal server.
- Response: The client receives the response through WAP once the internal server has processed the request and returned it.
Advantages of Microsoft Web Application Proxy (WAP)
For businesses that must enable secure remote access to web applications, Web Application Proxy (WAP) offers several advantages, such as:
- Enhanced efficiency: Incoming requests are split among several internal servers using WAP, which boosts performance and helps to guarantee high availability. This makes it possible to maintain the responsiveness and accessibility of web applications for users even during periods of high traffic.
- Data protection: WAP assists in the security of internal resources and the protection of sensitive data by serving as an intermediary between the internal network and the internet. To guarantee that only authenticated and authorized users access the internal network, WAP provides security authentication, authorization, and encryption.
- Cost efficient: WAP assists enterprises in saving on the expense of building and maintaining VPN infrastructure by minimising the requirement for a VPN connection.
Setup Microsoft Web Application Proxy (WAP) on Windows Server 2019/2022
Follow these next steps to navigate how to set up Microsoft Web Application Proxy on a Windows server 2019 / 2022.
Prerequisites
- A server running Windows 2019 or 2022
- An administrator password is set up on your server.
Install Web Application Proxy
First, you need to install the Web Application Proxy server roles on your server. Follow the below guide:
Step 1 – Log in to your Windows server and open the server manager. You should see the server manager dashboard on the following screen.

Step 2 – Click on the Add roles and features. You should see the Before your begin screen.
Step 3 – Press the Next button. Select installation type screen appears.
Step 4 – Select Role-based or feature-based installation and click on the Next button. This should bring the option to Select destination server screen.
Step 5 – Choose Select a server from the server pool and click on the Next button. Next screen you see is to Select server roles screen.
Step 6 – Select Remote Access and click on the Next button.
Step 7 – Click on the Next button.
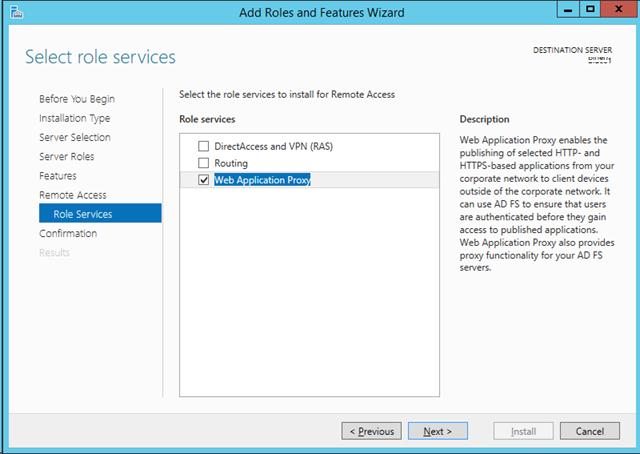
Step 8 – Now, click on the Next button. Roles service screen should appear next.
Step 9 – Select Web Application Proxy and click on the Next button. Confirm installation screen next.
Step 10 – Install button appears, which you click to start the installation. Installation progress screen appears next.
Step 11 – Click on the Close button to exit the installation windows. Your web application proxy is now installed on your server. Please proceed to the next step.
Import the ADFS Certificate
Now, you need to copy the ADFS certificate from your ADFS server to your web application proxy server and then import it to your server.
Furthermore, follow the below steps to import the ADFS certificate.
Step 1 – Type mmc.exe in the search bar and open the Microsoft Management Console as shown below.

Step 2 – Next, right click on Personal -> Certificates then go to All Tasks -> Import. This opens the Certificate Import Wizard as shown below.


Step 3 – Click on the Next button. See Certificate Window Wizard next step window.

Step 4 – Browse the ADFS certificate file that you exported from your AD FS server and click on the Next button. Likewise, you will be asked to provide password for the private key as shown below.

Step 5 – Provide your private key password, check the box to make the key exportable then click on the Next button.

Step 6 – Select “Place all certificates in the following store” and then click on the Next button.

Step 7 – Click on the Finish button. Given that, you should see your imported certificate on the following screen.

Configure Web Application Proxy
At this point, the Web Application Proxy is installed on your server. However, you need to perform post deployment configuration. Similarly, follow the below steps to configure Web Application Proxy.
Step 1 – Open the Server Manager and click Notifications.

Step 2 – Click on the Open the Web Application Proxy Wizard to start the configuration.

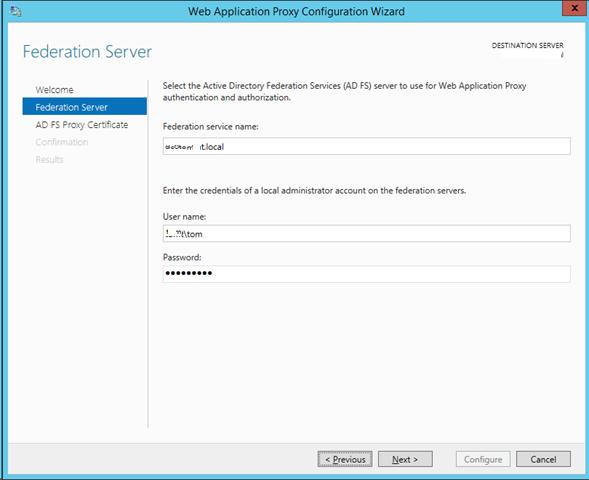
Step 3 – Click on the Next button. Then, ADFS server configuration screen appears.

Step 4 – Provide your ADFS server name, username, password, and click on the Next button. Server certificate selection screen appears next.

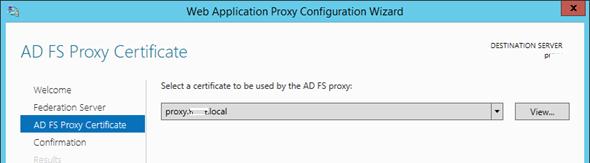
Step 5 – Select your server certificate and click on the Next button.

Step 6 – Click on the Configure button. Once the WAP is configured successfully, you should see the following screen.

Step 7 – Click on the Close button. Remote Access Management Console on the following screen appears next

Publish Web Application
In effect, you need to publish the web application from the Remote Access Management Console dashboard.
Step 1 – Click on the Web Application Proxy in the Remote Access Management Console.

Step 2 – Click on the Publish button.

Step 3 – Click on the Next button. Pre authentication screen apeears next.

Step 4 – Select Pass-through method and click on the Next button. Publishing settings screen appears next.

Step 5 – Provide the name, external URL, external certificate, and backend server URL then click on the Next button. Confirmation screen appears next.

Step 6 – Click on the Publish button. Once the Web Application has been published, you should see the following screen.

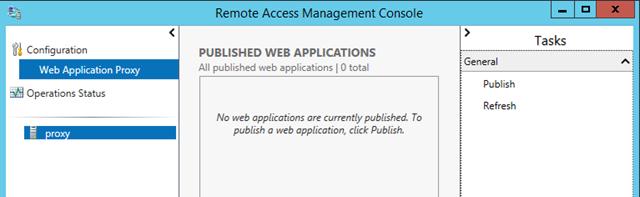
Step 7 – Click on the Close button. In essence, you should see your newly published web application on the following screen.

Thank you for reading Setup Microsoft Web Application Proxy (WAP) on Windows Server 2019/2022. We will conclude this article now.
Setup Microsoft Web Application Proxy (WAP) on Windows Server 2019/2022 Conclusion
In summary, this post explained how to set up Microsoft Web Application Proxy on Windows Server 2019 or 2022. Organizations provide secure and effective remote access to web applications via WAP. Lastly, WAP enables businesses to satisfy their demands while safeguarding sensitive data by enhancing security, performance, and remote access, as well as streamlining implementation and cutting expenses.
This Windows Server 2012 R2 feature allows online users to securely access internal resources.
With Windows Server 2012 R2, Microsoft has built in a reverse-proxy feature. The Web Application Proxy securely publishes internal resources out to the Internet for access by both corporate-owned devices and untrusted machines alike. Indeed, most deployments of, say, Work Folders or workplace join — key “work anywhere” features that Microsoft put into Windows Server 2012 R2 — demand a reverse proxy of some sort, so this requirement is likely to come up for you sooner or later.
As you may have heard, Microsoft killed its flagship reverse proxy product, Forefront Unified Access Gateway, back in December. Many organizations have used UAG to create DirectAccess tunnels as well as portals where applications could be securely accessed from all sorts of clients.
While UAG’s capabilities were vast, it may have represented overkill for many applications, so Microsoft has built a capable, if less full-featured, successor into Windows Server 2012 R2. That’s what this article is about.
Configuring the Web Application Proxy (WAP) role, however, involves a lot of moving parts, and in this piece I will walk through how to set up the WAP role in your lab with either an application of your choosing or a freely available sample claims application that Microsoft publishes as part of one of its software development kits. Let’s begin.
Installing and configuring Active Directory Federation Services
Follow these steps to get started on the ADFS server.
1. On the machine that will host the ADFS role, open Server Manager and go to Add Roles and Features, and then check the box for Active Directory Federation Services.
2. Click through the rest of the wizard — the screens are just descriptions of the service; there is no action required other than to read the text and click Next. Then press the Finish button to get the role installed.

3. Once the wizard finishes, click the yellow exclamation icon in Server Manager. This icon reminds you that even though the role is installed, ADFS is not functional yet; you need to further configure the service. Click the link within the status screen that pops up from the yellow icon to go directly to the configuration interface.
4. For this walkthrough, we can assume this is our first ADFS server, so choose the default option and click Next.
5. On the account selection page, choose an account that has domain administrator permissions and then click Next.
6. On the next screen, you need to select the secure certificate that ADFS will use in its connections. You cannot use the certificates from IIS Manager here, as you will need to have previously imported the certificate into the certificate store through the Microsoft Management Console (MMC) snap-in. You can also import a new wildcard or Subject Alternative Name certificate right from this screen.
Note that the wizard will automatically link the subject name of the certificate you are importing with the Federation Service Name, which may not be, and in fact probably is not, what you want. Instead, for the Federation Service Name, type in the URL you will want to use when applications request a connection to ADFS — some folks choose adfs.domain.tld, others choose id.domain.tld, still others choose federation.domain.tld. The key here is to not simply accept the default and to make sure the Federation Service Name lines up with the URL you will be using for Web applications that require any sort of transaction with your ADFS deployment.

7. Leave the wizard where it is now and click over to whatever application or service you are using to host your domain name service (DNS) records and add a “Record for the Federation Service Name” you just made in the previous step. Once you have created and saved that new record, come back to the ADFS configuration wizard.
8. Back in the wizard, add the Federation Service Display Name — this is a friendly name, so there are no special rules for how it is formatted or what it must be addressed to — and click Next.
9. Select the account you will run the ADFS service under, and then click Next.
10. On this database screen you can either create a new Windows internal database instance for ADFS or you can point the service to an existing database running in SQL Server. Click Next.
11. Review the options you selected to configure ADFS, and click Next to validate your choices. You can also take a look at the PowerShell script the wizard will actually run to perform the configuration, as most of the wizards in Windows Server 2012 R2 these days are really just front ends to PowerShell script generators.
12. The checks should pass and now you can click Finish to actually configure the service.
Next, you will need to spin up another client or server to test connectivity to the ADFS service. You can use any machine with a Web browser that can access the network on which your ADFS server is installed, as all you are doing here is browsing to a Web page on the ADFS deployment.
On this separate machine — NOT on the ADFS server itself, as it will fail — access the following URLs:
- https://adfs.domain.tld/federationmetadata/2007-06/federationmetadata.xml
- https://adfs.domain.tld/adfs/ls/idpinitiatedsignon.htm
Of course, replace adfs.domain.tld with whatever DNS name resolves to your instance of ADFS. The point here is to make sure that when you get to the first URL, you see the metadata from the ADFS server without any SSL or certificate validity errors. For the second URL, you must see the standard default ADFS sign-on page. If both of these pages come up without errors, you have successfully installed ADFS.
Back on the ADFS server, copy the SSL certificate you used in the configuration wizard to a network share or a thumb drive, so that you can copy it again onto the server on which we will be installing the WAP role (in the next section).
Installing the Web Application Proxy role
Continuing in this process, you will need to create a second machine — as mentioned before — on which the WAP role can be installed. However, this machine should NOT be joined to any domain; it can remain a standalone server.
First, we need to install the certificate you just copied from the ADFS server. You will need to manually import this certificate into the Windows certificate store by following these steps:
1. On the Start menu, type MMC and press Enter.
2. From the File menu, choose Add/Remove Snap-in.
3. In the left pane under “available snap-ins,” choose Certificates, and click the Add button in the middle of the window.
4. A window will pop up, asking which account this snap-in should manage. From the three choices, select Computer account at the bottom and then click Next.
5. Choose the local computer option, and then click Finish.
6. Click OK in the management window, and you will be returned to the MMC console with the certificates snap-in added.
7. In the left pane, expand “Certificates (Local Computer)” and then click on the Personal node.
8. Right click on the Personal node and select Import from the All Tasks menu.
9. Follow the wizard to select the certificate that you previously used and copied down, and finish the import.

Now that the certificate is safely in the certificate store, you can add the WAP role to this server. Open Server Manager, then go to Add Roles and Features and choose the Remote Access option. Follow the wizard through the confirmation screens until you are presented with a page where you are asked to select the remote access services you desire; here, check the box beside the WAP service.
Click Add Features in the screen that pops up asking you about related services that must be installed at the same time, and then click on through until you are finished. (The related services are just interdependencies; for example, to install WAP you need to install IIS, and the wizard preselects this for you. That screen just shows what other services will get installed.)

Within Server Manager, click the yellow warning icon and then follow the link to open the WAP configuration wizard. Enter the same Federation Service Name entry that you configured in the ADFS wizard and for which you set up a DNS entry, and then enter credentials for an account with local administrator privileges on the ADFS server.

Once you get to the certificate selection screen, choose the certificate that you imported earlier, review the PowerShell script that the wizard has again generated and then click the Configure button to set things into motion.
Note: If you get an SSL error relating to the failure to establish a trust relationship, make sure the root certificate authority that created the ADFS certificate that you imported into the WAP server’s certificate store is trusted by the WAP. You can look in the Certificates snap-in of the MMC to see whether the certificate is present. If it is not, import that root certificate using the previous procedure, only this time add it to the Trusted Certification Root Authority node in the MMC snap-in, and not the Personal node. See step 7.)
Setting up an application to use the WAP role
Now that you have set up ADFS on one machine and the WAP role on another machine, you can publish a new application on the WAP server. You do this by publishing rules for the specific URLs that need to pass through the WAP to some server on your network for which you are proxying transmissions.
For the purposes of this walkthrough, you can use the sample claims-based application that comes in the Windows Identity Foundation software development kit, or SDK. You can download the sample application here and get instructions here for setting up the prerequisites for this sample application. You can also use any other application you have at your disposal that works with federated identities as long as it has an external URL endpoint. You will just need to know that endpoint.
To set up a new application, follow these steps:
1. From the Start menu, open the Remote Access Management Console.
2. From the Tasks section on the right of the Remote Access Management Console, click Publish.
3. Click Next to page through the welcome screen.
4. The Preauthentication screen will appear. Select the first option, “Active Directory Federation Services (ADFS)” and click Next.
5. The Relying Party page will appear. Here, select the relying party for the application you are using and click Next. (The relying party is simply the application that needs the credentials that ADFS is federating — in other words, the application that will trust the credentials that ADFS authenticates.)
6. The Publishing Settings page appears. Enter a friendly name for your application, the URL at which external clients can access the application, the certificate that covers that name and the URL of the back-end server if different (for the purposes of this walkthrough, it is the same as the application’s external URL). Click Next.
7. Confirm these settings and click Publish.
Interestingly, you can wrap that entire seven-step sequence up into a single PowerShell command, which again is all the wizard does. (There is no PowerShell that makes sense to use for the steps given on previous pages; it would be a series of commands that is not really any more intuitive or any faster than using Server Manager and the various configuration wizards.)
Add-WebApplicationProxyApplication -BackendServerURL 'https://www.domain.tld/yourappgoeshere'
-ExternalCertificateThumbprint 'qwerty87239874923hjdf0df9'
-ExternalURL 'https://www.domain.tld/yourappgoeshere/'
-Name Test Application
-ExternalPreAuthentication ADFS
-ADFSRelyingPartyName Test Party
At this point, everything should be working, and you should be able to see your application being securely reverse-proxied using the WAP role to clients connecting from the wild Internet.
This article, How to set up Microsoft’s Web Application Proxy, was originally published at Computerworld.com.
Jonathan Hassell runs 82 Ventures LLC, a consulting firm based out of Charlotte, N.C. He’s also an editor with Apress Media LLC. Reach him at jhassell@gmail.com.
Provide feedback
Saved searches
Use saved searches to filter your results more quickly
Sign up
Microsoft Web Application Proxy [WAP] is a new service added in Windows Server 2012 R2 that allows you to access web applications from outside your network. WAP functions as a reverse proxy and an Active Directory Federation Services [AD FS] proxy to pre-authenticate user access.

vBoring Blog Series:
- How to setup Microsoft Active Directory Federation Services [AD FS]
- How to setup Microsoft Web Application Proxy
Requirements:
- The only hard requirement of WAP is having an AD FS server. Refer to step 1 for setting that up.
- WAP cannot be installed on a server that AD FS is installed on. They must be separate servers.
Installing the Web Application Proxy Server Role:
Open Server Manager and click Manage -> Add Roles and Features:
Click Next:

Role-based or feature-based installation should be selected then click Next:

Select the server you want to install this role on to and then click Next:
Note: Web Application Proxy role and AD FS cannot be installed on the same computer.

Select Remote Access then click Next:

No additional Features are needed. Click Next:

Click Next:

Select Web Application Proxy:

On the pop up click Add Features:

The Web Application Proxy role does not required a reboot. Click Install:

Once complete click Close:

Web Application Proxy is now installed but you need the AD FS certificate to continue.
Export & Import the AD FS Certificate:
You need the certificate from your AD FS server added to your Web Application Proxy server. Login to your AD FS server and open MMC.exe:
Go to File -> Add/Remove Snap-ins -> select Certificates then click Add:

When you click OK you will get the following pop up. Select Computer account then click Next:

On AD FS Server: Drill down to Personal -> Certificates then right click the SSL certificate you used during setup of AD FS. Go to All Tasks -> Export. Save to a location that your Web Application Proxy can access. Ensure you export the Private Key and certificate as a .PFX file.

On Web Application Proxy: Right click on Personal -> Certificates then go to All Tasks -> Import:

This will bring up the Certificate Import Wizard. Click Next:

Browse to the certificate that you exported from your AD FS server and select it. Click Next:

Enter the password for the private key and check the box to make the key exportable. Click Next:

Leave the default certificate store as Personal. Click Next:

Click Finish:

You should now see the certificate from your AD FS servers on your Web Application Proxy server.

Now we are ready to perform the Post Configuration.
Post-Deployment Configuration:
Back on your Web Application Server open Server Manager then click Notifications then the message Open the Web Application Proxy Wizard:
Click Next:

Enter the FQDN of your AD FS name and the Service Account you created during AD FS setup. Click Next:

On the drop down menu select the certificate you imported from your AD FS server. Click Next:

Click Configure:

Once finished click Close:

Remote Access Management Console should open when you clicked Close. On Operations Status you should see all the objects as green.

Publish Web Applications:
Now we are finally ready for the magic. In the Remote Access Management Console click Web Application Proxy then Publish:

Click Next:

Pass-through will let WAP act like a reverse proxy. I will have documentation on setting up AD FS link soon!
Select Pass-through and click Next:

Name: Enter a display name
External URL: Enter the URL that will be coming in your the WAP server externally
External Certificate: The drop down menu will show certificates that are added on the WAP server. Select the same certificate that you used while setting up your application. In my case I used my wildcard certificate.
Backend server URL: Enter the web URL of the server you want the external URL forwarded
Click Next:

Copy the PowerShell command down and with some minor edits you can easily add additional PassThrough applications with ease.
Click Publish:

Click Close to finish:

You will now see the published web application and ready for testing.

You are ready to test the application!
Configure Firewall for 443 Port Forwarding:
Before you can test you need to ensure you have port 443 (HTTPS) being sent to your WAP server. This step does not involve configuration of your WAP environment but on your firewall. Since this can vary greatly I will give you two examples of this step:
For pfSense you would create a NAT: Port Forward Rule:

For DD-WRT you would go to NAT / QOS then Port Forwarding:

Once added you are ready to test!
From outside your network (like on your phone or a PC elsewhere) try to access your web link. You should get your internal web page through your WAP externally! Success!

Coming Soon!! Setting up Microsoft RDS to use AD FS authentication through WAP!
