The rise of wireless networks has been tremendous in the past decade with every building fitted with several connections. Moreover, people are more concerned about their network connection than ever before. Infamous for its security consequences, hacking is an advanced technical skill that can give a user access to any secured device. However, learning the skill requires the right equipment, this is where some of the best Wi-Fi hacking tools come into the picture. But every new tech comes with its repercussions as these same tools can be used to exploit other Wi-Fi networks.

Wi-Fi hacking can be easy or very hard based on several system settings. It is dependent on two main factors:
1. Weak passwords: One of the most common ways for hackers to gain access to a Wi-Fi network is by using a weak password. Many people use default passwords for their routers, which are easy for hackers to guess. Others use weak passwords that are easy to remember, such as password 123456.
2. Unencrypted networks: Wi-Fi networks can be encrypted to protect them from hackers. However, some people choose to leave their networks unencrypted, either because they don’t know how to encrypt them or because they think it’s not necessary. Unencrypted networks are easy for hackers to access.
Top and Popular Wireless Hacking Tools
For a Wi-Fi hacking tool to be effective, it should have a few key attributes. This includes the capability of sniffing network packets and analyzing, and locating wireless network security gaps such as the WEP and WPA vulnerabilities, dictionary attacks, password guessing, and creating fake access points for tricking users. Some of the tools with all these features are listed below.
Note: Hacking into a device can cause privacy and security threats to a PC, which can result in legal consequences for the practitioner. Therefore, it is important that the use of the following tools is done in a responsible manner. The user descition is advised
1. Aircrack-ng

Aircrack-ng is one of the prominent and free WiFi password hacking tools and is written in C-language to evaluate the efficiency of network security. This tool works via a sequential process involving monitoring, attacking, testing, and cracking WI-FI passwords. While its primary emphasis is on the Linux operating system; however, it also supports Windows OS X, FreeBSD, NetBSD, OpenBSD, Solaris, and eComStation 2.
- Supports a wide range of operating systems, including Linux, Windows, OS X, and more.
- Utilizes various attacks, including FMS, Korek, and PTW attacks, to optimize the speed and efficiency of password cracking.
- Capable of cracking WEP keys using FMS, PTW, and dictionary attacks.
- Can crack WPA2-PSK through dictionary attacks.
- Focuses on Replay attacks, de-authentication, and creating fake access points for network assessment.
2. Wireshark

Wireshark is an open source WiFi hacking tool that provides best-in-class data packet analysis and network protocol examination solutions. It is one of the most popular among Windows users’ software for network troubleshooting, software development, and educational functions. With its ability to capture even the smallest details of network activity, Wireshark allows the examination and analysis of diverse protocols on a microscopic scale.
- Live packet captures and offline analysis, providing real-time insight into network activities.
- Cross-platform compatibility, supporting Windows, Linux, Mac OS, Solaris, FreeBSD, NetBSD, and more.
- Allows the application of color-coded rules to packet lists, facilitating quick and easy analysis.
- Rich Voice over Internet Protocol (VoIP) analysis for assessing phone services over the internet.
- Can decompress gzip files on-the-fly without disrupting running programs.
- Decrypts various protocols including IPsec, ISAKMP, SSL/TLS, and more.
Also Read: What is Ethical Hacking?
3. Kismet

Kismet is one of the most popular Wi-Fi hacking tools for PC, intended for ethical hackers and security specialists. Kismet is a versatile wireless network sniffer and intrusion detection tool, named after Arabic word division. It collects packets passively to recognize networks and even unveil hidden ones as a valuable resource for network analysis and security assessment.
- Supports Wi-Fi, Bluetooth, software-defined Radio (SDR), and various wireless protocols.
- Capable of identifying hidden Wi-Fi networks by analyzing broadcasted packets.
- Works with any Wi-Fi card that supports raw monitoring mode.
- Supports 802.11 standards including 802.11a, 802.11b, 802.11g, and 802.11n traffic.
- Operates on various operating systems, including Linux (e.g., Ubuntu, Backtrack), FreeBSD, NetBSD, OpenBSD, Mac OS X, and can be used on Windows through WSL (Windows Subsystem for Linux).
4. CoWPAtty

CoWPAtty is, in fact, one of the most successful tools for Wi-Fi hacking. It is meant, among other things, for conducting offline dictionary-based attacks on wireless networks but has such an extraordinary name as this. This tool authored by Joshua Wright is a way by which attackers, hackers, and network managers crack into the WPA/WPA2 protected networks relying on PreShared Key (PSK) authentication method. While Cowpatty runs on Linux and has a command-line interface, it operates using a wordlist containing potential passwords for the attack.
- Automated dictionary attack tool specifically designed for WPA-PSK networks.
- Compatible with Linux operating systems, making it an ideal choice for Linux users.
- Utilizes offline attacks, exploiting authentication based on the PSK model.
- Employs PBKDF2 with 4096 iterations for passphrase generation, slowing down brute force attacks.
5. Airjack

Airjack is a powerful Wi-Fi 802.11 packet injection tool and forms a critical part of network manipulation activities. It is a tool that has been widely used in various operations such as injecting forged packets, facilitating denial of service attacks to disrupt networks, and enabling man-in-the-middle attacks on wireless networks. Airjack is a necessary tool for ethical hackers and security professionals who want to test, evaluate, and secure their wireless networks.
- Specialized tool for Wi-Fi 802.11 packet injection.
- Enables the injection of forged packets into wireless networks.
- Capable of initiating denial of service attacks to disrupt network services.
- Facilitates man-in-the-middle attacks for intercepting and manipulating network traffic.
- A valuable asset for network penetration testing and security assessment.
Also Read: 17 Best App for WhatsApp Hacking
6. AirSnort

AirSnort, a widely known Wi-Fi password hacking software, is a must tool for decrypting WEP Keys specifically in Wi-Fi 802.11b Networks. This software was developed by Blake Hegerle and Jeremy Bruestle, it is freely available for Linux as well as Windows operating systems. Its main purpose is to intercept and analyze packets that belong to the network it targets in order to recover its password or encryption key.
- Designed for cracking WEP passwords in 802.11b wireless networks.
- Free to use and available for both Linux and Windows operating systems.
- Downloads are available via Sourceforge, ensuring easy access for users.
- Utilizes a passive attack approach, monitoring network transmissions to gather data packets.
- Computes the encryption key once a sufficient quantity of data packets has been captured.
- Operates by observing and identifying data patterns to recover encryption or password keys.
7. Wifite 2

One of the best tools for simplifying the complexities of wireless hacking is Wifite, a Python script for wireless security auditing. The tool is invaluable for security professionals and ethical hackers as it speeds up the wireless auditing process by automatically running available hacking tools for you. Whether you’re auditing WEP or WPA-encrypted wireless networks, Wifite leverages tools like aircrack-ng, pyrite, reaver, and shark to execute various attacks. The author has made a full-fledged rewrite of the original tool to be fully compatible with Kali Linux and ParrotSec.
- Simplifies wireless security auditing by automating the execution of various hacking tools.
- Supports auditing of WEP and WPA encrypted wireless networks.
- Customizable and can be automated with minimal arguments, reducing the need for user supervision.
- Compatible with popular Linux pentesting distributions like Kali Linux, Pentoo, BackBox, and others.
8. inSSIDer

inSSIDer is a highly regarded Wi-Fi scanner designed for Microsoft Windows and OS X operating systems. This versatile tool is ideal for various Wi-Fi auditing tasks, making it an invaluable resource for both professionals and enthusiasts.
- Effortlessly locates open Wi-Fi access points, aiding in the discovery of available networks.
- Provides detailed signal strength measurements, allowing users to assess signal quality and coverage.
- Logs data with GPS records, making it convenient for analyzing and mapping the location of Wi-Fi networks.
- Offers a freemium model, with basic functionality available for free, while advanced features require a paid membership.
Also Read: 20 Best WiFi Hacking Tools for PC
9. NetStumbler

NetStumbler, also known as Network Stumbler, is a widely recognized and free wireless LAN detection tool specifically designed for Windows operating systems. It is good at detecting WiFi, 802.11b, 802.11g, and 802.11a network types. NetStumbler is one of the top war-driving tools and is used in mapping wireless networks in the local area as well as in various network assessment activities.
- Detects and identifies 802.11a, 802.11b, and 802.11g wireless networks.
- Utilized in wardriving, which involves mapping open wireless access points while on the move.
- Provides information on network configurations, signal strength, network congestion, and potential rogue access points.
- Effective in pinpointing areas of poor network coverage, aiding in network optimization.
- Helps uncover unauthorized access points based on signal strength variations.
- Runs on Windows operating systems from Windows 2000 to Windows XP.
10. Wifiphisher

WiFiphisher is an advanced tool that enables man-in-the-middle (MITM) attack, utilizing Wi-Fi associations for intercepting, monitoring and possibly modifying wireless traffic. The attack works by attempting to convince wireless users to connect into an unauthorized access point which eventually allows attackers to compromise data security.
- Conducts man-in-the-middle attacks by luring wireless users to connect to a rogue access point.
- Enables attackers to intercept, monitor, and potentially modify wireless traffic.
- Supports web phishing attacks to collect user credentials for third-party websites or Wi-Fi network access.
- Modular design allows advanced users to develop custom code, extending its functionalities.
- Disrupts existing connections to target access points using de-authenticate or Disassociate packets.
- Sniffs and replicates the settings of the target access point.
11. Airgeddon

Airgeddon is a comprehensive tool designed for wireless network security analysis, streamlining the complexity of Wi-Fi security audits by integrating multiple existing tools into a single, user-friendly command-line interface.
- Interface mode switcher for Monitor and Managed modes, maintaining selections even when the interface name changes.
- Multiple Denial of Service (DoS) methods for disrupting wireless networks (mdk3, mdk4, airplay-ng), including DoS Pursuit mode to counter AP channel hopping during Evil Twin attacks.
- Full support for both 2.4GHz and 5GHz frequency bands.
- Assisted WPA/WPA2 handshake file and PMKID capturing for personal networks.
- Offline password decryption for WPA/WPA2 captured files, utilizing dictionary, brute-force, and rule-based attacks with tools like aircrack, crunch, and hashcat. Enterprise network password decryption based on John the ripper, crunch, asleap, and hashcat tools.
Also Read: 15 Best WiFi Hacking Apps For Android (2023)
12. CommView for WiFi

CommView for WiFi is a robust and user-friendly wireless network monitoring and packet analysis tool compatible with a wide range of Wi-Fi networks. Here are key features of CommView for WiFi:
- Comprehensive support for 802.11 a/b/g/n/ac/ax networks.
- Captures and analyzes every packet in the air, providing essential information such as access points, stations, signal strength, protocol distribution, and network connections.
- Enables user-defined decryption of captured packets using WEP or WPA/WPA2-PSK keys.
- Ideal for Wi-Fi network administrators, security professionals, home users monitoring their Wi-Fi traffic, and software programmers working on wireless network applications.
- Offers in-depth analysis, recording, and playback of SIP and H.323 voice communications with a dedicated VoIP module.
13. OmniPeek

OmniPeek stands as a robust and comprehensive packet sniffer and network analysis tool, primarily designed for Windows OS. It is a commercial tool, recognized for its extensive feature set, which makes it invaluable for various networking tasks. Here are its key features:
- Commercial network analysis tool for Windows, known for its comprehensive capabilities.
- An all-in-one Wi-Fi network management solution that covers packet capture, protocol decoding, network diagnostics, and troubleshooting.
- Allows for playback and analysis of voice and video traffic, aiding in diagnostic processes.
- Provides intuitive visualizations of packet data, aiding in the quick resolution of network and application performance issues.
- Supports real-time visibility and expert analysis of various network aspects, including Ethernet, Gigabit, 10 Gigabit, 802.11a/b/g/n/ac wireless, VoIP, and video.
14. Kali Linux NetHunter

Kali Linux NetHunter is an exceptional mobile penetration testing platform that extends the power of Kali Linux to Android devices. It is fully open-source and designed to run on various Android smartphones, including popular brands like OnePlus, Samsung, and Google Nexus. Here are the key features of Kali NetHunter:
- Compatible with a wide range of Android devices, offering flexibility and accessibility.
- Developed and maintained by a community of volunteers, with project funding from Offensive Security.
- Available in multiple editions, including NetHunter Rootless for un-rooted devices, NetHunter Lite for rooted devices with custom recovery, and NetHunter for rooted devices with NetHunter-specific kernels.
- Core features include a Kali Linux container with a comprehensive set of security tools and applications, a dedicated Kali NetHunter App Store, an Android client for easy access to the App Store, and the Kali NetHunter Desktop Experience (KeX) for running full Kali Linux desktop sessions and supporting screen mirroring via HDMI or wireless casting.
Also Read: 16 Best Game Hacking Apps for Android
15. Maltego

Maltego is a powerful hacking tool for data mining and link analysis, making it one of the best WiFi hacking tools for PCs. It offers a range of versions to cater to different needs, from the free Community Edition to the more powerful paid options. Here are some key features and pricing details:
- Available in free and paid versions.
- Node-based graphical representation of data.
- Supports Windows, Linux, and Mac operating systems.
- Real-time data mining and information gathering capabilities.
- Utilizes node-based graphical patterns for data representation.
- Maltego XL excels in handling large graphs and highlights network vulnerabilities.
- Online training courses with a three-month access period and a certificate upon completion.
16. Cain & Abel

Cain & Abel is a renowned WiFi hacking tool, named after the biblical children of Adam and Eve. While it’s popular for its WiFi password recovery capabilities, it uses a variety of techniques to investigate and analyze data packets individually, decrypt scrambled passwords, and recover wireless network keys. This tool supports various versions of Microsoft OS and employs methods like brute force, dictionary attacks, and cryptanalysis attacks. Additionally, it offers features like Address Resolution Protocol (ARP) support for detection on switched LANs and MITM (Man-in-the-Middle) attacks, making it a versatile choice for network security enthusiasts.
- Network packet sniffing for capturing and analyzing data traffic.
- Password cracking through methods such as dictionary attacks and cryptanalysis.
- Keylogger functionality for recording keystrokes.
- Port scanner to identify open ports on a network.
- ARP poisoning and DNS spoofing for network security assessments.
- MAC address spoofing to manipulate network access.
17. Cloud Cracker
Cloud Cracker is a valuable online password cracking service tailored for penetration testers and network auditors, serving their needs for evaluating the security of protected wireless networks, breaking password hashes, and decrypting document encryption. This tool simplifies and accelerates the process of assessing network and document security, making it a valuable resource for security professionals.
- Specialized in checking the security of WPA-protected wireless networks, ideal for testing network vulnerabilities.
- Capable of cracking password hashes, providing essential support for security assessments.
- Offers document encryption decryption, making it a versatile tool for security audits.
- Streamlines the process of assessing network and document security, saving time and effort for security professionals.
Also Read: 7 Best Websites To Learn Ethical Hacking
One thing you must know is that operating some of these best Wi-Fi hacking tools might be a little tricky. Also, you are advised to use caution and only indulge in legal activities. If you have any queries or suggestions, do let us know in the comments section below.
Подробный мануал по взлому WiFi в Windows 10. Перехват handshake (cap-файла) авторизации.

Замечу, что эта статья написана только для образовательных целей. Мы никого ни к чему не призываем, только в целях ознакомления! Автор не несёт ответственности за ваши действия!
CommView for Wifi Windows 10
Шаг 1. Нам нужно скачать программу CommView for WiFi. Это достаточно популярная прога для мониторинга и анализа пакетов под Windows. Её интерфейс гораздо дружелюбнее, нежели у того же WireShark’а, а функций в полнофункциональной версии хватает с головой. Сейчас же, для быстрой демонстрации я воспользуюсь демкой. На офф сайте tamos.ru открываем раздел «Загрузка» и кликаем по кнопке скачать напротив названия нужного нам продукта.
Шаг 2. Откроется страница с перечислением всех адаптеров, которые поддерживаются программой. Список, мягко говоря, не велик. После того, как убедились, что сетевая карта подходит, кликаем «Скачать CommView for WiFi».
Шаг 3. И по завершению загрузки запускаем установочный EXE’шник внутри архива.
Шаг 4. Next.
Шаг 5. Принимаю.
Шаг 6. Стандартный режим. Никакой IP-телефонии нам не нужно.
Шаг 7. Путь установки по дефолту.
Шаг 8. Язык – русский. Ярлыки создать.
Шаг 9. Дальше.
Шаг 10. После завершения установки, жмём «Finish».
Шаг 11. И ждём, пока откроется главное окно. Видим, что программа нашла совместимый адаптер и предлагает нам установить собственный драйвер. Сразу предупрежу, что после его установки ваша сетевая карта перестанет работать в штатном режиме и перейдёт в режим монитора. Сети при это не будут видеться через стандартную службу Windows. Далее, я покажу, как это исправить. Но сначала завершим начатое. Жмём «Далее».
Шаг 12. Установить драйвер.
Шаг 13. После инсталляции непременно перезагружаем компьютер.
Как пользоваться CommView For Wifi
Шаг 14. Отлично. Дождавшись включения запускаем ярлычок CommView и в главном окне программы выбираем справа режим сканирования всех каналов.
Шаг 15. Видим предупреждение о том, что оценочная версия позволяет захватывать трафик не дольше 5 минут. Нам, признаться, дольше то и не нужно. Кликаем «Продолжить».
Шаг 16. Дожидаемся, пока наша сеть появится в списке и тормозим сканирование. Запоминаем, а ещё лучше записываем MAC-адрес точки, SSID и номер канала, на котором она работает в данный момент.
Шаг 17. Переводим программу в одноканальный режим и указываем уже конкретно канал нашей точки. Врубаем перехват заново.
Шаг 18. И чтобы не ждать, пока одно из устройств отключится, а затем подключится к роутеру, дабы инициировать «Рукопожатие» (handshake,cap-файл), отправим пакеты деаутентификации. Вкладка «Инструмента» — «Реассоциация узлов».
Шаг 19. Послать 100 пакетов с интервалом 10 мсек. Проверяем точку. Смотрим клиентов. Рекомендую откидывать не более 1 за раз. Послать сейчас. Всё. Ждёмс. Яблочное устройство отвалилось и вновь законнектилось, а значит можно двигаться дальше.
Шаг 20. Останавливаем перехват.
Шаг 21. И переходим на вкладку «Пакеты». На самом деле из всей этой истории нас интересуют только EAPOL паки. В момент коннекта устройство обменивается с роутером 4 пакетами этого типа. Внутри содержится пароль от точки в зашифрованном виде. Совсем скоро мы его достанем и дешифруем. Вызываем контекстное меню, «Открыть пакеты в новом окне» — «Все».
Шаг 22. Далее «Файл» — «Экспорт log-файлов» — «Формат Wireshark/Tcpdump».
Шаг 23. Указываем место для сохранения и присваиваем файлу понятное имя. «Сохранить».
CommView For Wifi не видит сети
Шаг 24. Всё. CommView можно закрывать и переходить к загрузке второй программы. Однако тут возникнет сложноcть о которой я уже упоминал ранее. Сетки не видятся. Нужно восстановить нормальный драйвер.
Шаг 25. Запускаем «Диспетчер устройств».
Шаг 26. В списке сетевых адаптеров ищем тот, что содержит приписку «CommView» и идём в «Свойства».
Шаг 27. На вкладке драйвер кликаем по заветной кнопочке «Откатить».
Шаг 28. Указываем причину. Предыдущая версия работала явно лучше. Жмём «ОК».
Шаг 29. И после завершения отката проверяем список сеток. Тэкс. Всё хорошо. Инет снова работает.
Aircrack-ng Windows 10
Шаг 30. Открываем браузер и переходим на сайт aircrack-ng.org. Тут прям на главной странице есть кнопка загрузки тулза под виндовс. Качаем.
Шаг 31. И после загрузки распаковываем всю эту историю в отдельную папку. Внутри открываем каталог «bin» и запускаем файлик «Aircrack-ng GUI».
Шаг 32. Выбираем тип – «WPA». В первой строчке указываем путь к файлу с добытым ранее хендшейком.
Шаг 33. Во второй указываем путь к словарю. Ссылку на те, что юзаю я, найдёте в описании к видео.
Шаг 34. Ставим галочку «Advanced option» и указываем имя интересующей нас точки и MAC-адрес. Помните, ранее, я специально просил вас зафиксировать эти данные. Жмём «Launch».
Шаг 35. Пошла жара. Если пароль присутствует в словаре, он обязательно дешифруется через какое-то время.
Всем спасибо за внимание!
Источник
Время на прочтение3 мин
Количество просмотров324K
Автор статьи, перевод которой мы сегодня публикуем, хочет рассказать о том, как взломать Wi-Fi-сеть, для защиты которой используются протоколы WPA и WPA2.

Статья написана исключительно в ознакомительных целях
Аппаратное и программное обеспечение
Я буду пользоваться дистрибутивом Kali Linux, установленным на VMware Workstation.
Кроме того, в моём распоряжении имеется Wi-Fi-адаптер Alfa AWUS036NH 2000mW 802.11b/g/n. Вот его основные характеристики:
- Стандарты: IEEE 802.11b/g/n, USB 2.0.
- Скорости передачи данных: 802.11b — 11 Мбит/с, 802.11g — 54 Мбит/с, 802.11n — 150 Мбит/с.
- Разъём для подключения антенны: 1 x RP-SMA.
- Частотные диапазоны: 2412~2462 МГц, 2412~2472 МГц, 2412~2484 МГц.
- Питание: 5В.
- Безопасность: WEP 64/128, поддержка 802.1X, WPS, WPA-PSK, WPA2.
Шаг 1
Нужно запустить Kali Linux в VMware и подключить к системе Wi-Fi-адаптер Alfa AWUS036NH, выполнив следующую последовательность действий:
VM > Removable Devices > Ralink 802.11n USB Wireless Lan Card > Connect

Подключение Wi-Fi-адаптера к ОС, работающей в VMware
Шаг 2
Теперь обратите внимание на средства управления Wi-Fi-подключениями в Kali Linux.
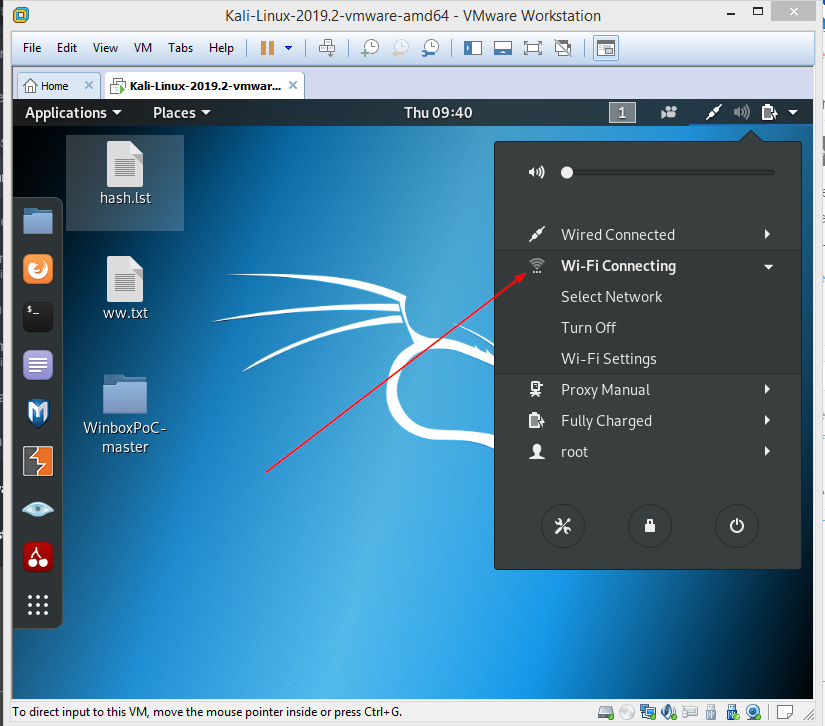
Управление Wi-Fi-подключениями в Kali Linux
Шаг 3
Откройте терминал и выполните команду airmon-ng для вывода сведений об интерфейсах беспроводных сетей.
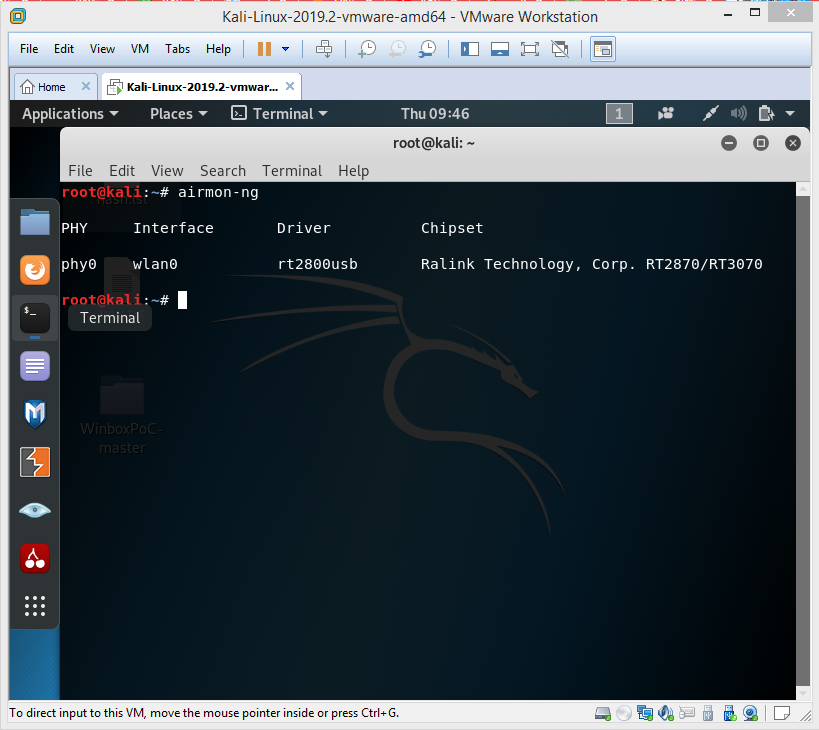
Вывод сведений об интерфейсах беспроводных сетей
Шаг 4
Как видно, интерфейсу назначено имя wlan0. Зная это, выполним в терминале команду airmon-ng start wlan0. Благодаря этой команде Wi-Fi-адаптер будет переведён в режим мониторинга.
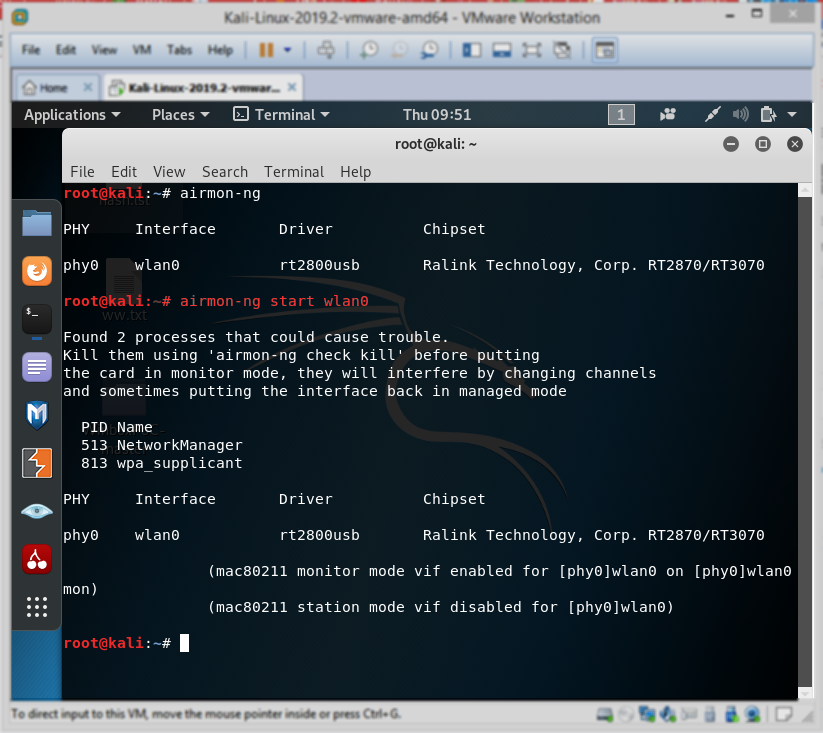
Перевод адаптера в режим мониторинга
Шаг 5
Теперь выполните такую команду: airodump-ng wlan0mon. Это позволит получить сведения о Wi-Fi-сетях, развёрнутых поблизости, о том, какие методы шифрования в них используются, а так же — о SSID.

Сведения о Wi-Fi-сетях
Шаг 6
Теперь воспользуемся такой командой:
airodump-ng -c [channel] –bssid [bssid] -w /root/Desktop/ [monitor interface]
В ней [channel] надо заменить на номер целевого канала, [bssid] — на целевой BSSID, [monitor interface] — на интерфейс мониторинга wlan0mon.
В результате моя команда будет выглядеть так:
airodump-ng -c 6 –bssid 4C:ED:FB:8A:4F:C0 -w /root/Desktop/ wlan0mon

Выполнение команды
Шаг 7
Теперь нужно подождать. Утилита airodump будет мониторить сеть, ожидая момента, когда кто-нибудь к ней подключится. Это даст нам возможность получить handshake-файлы, которые будут сохранены в папке /root/Desktop.
Вот как выглядит работа утилиты до того момента, как кто-то подключился к исследуемой сети.
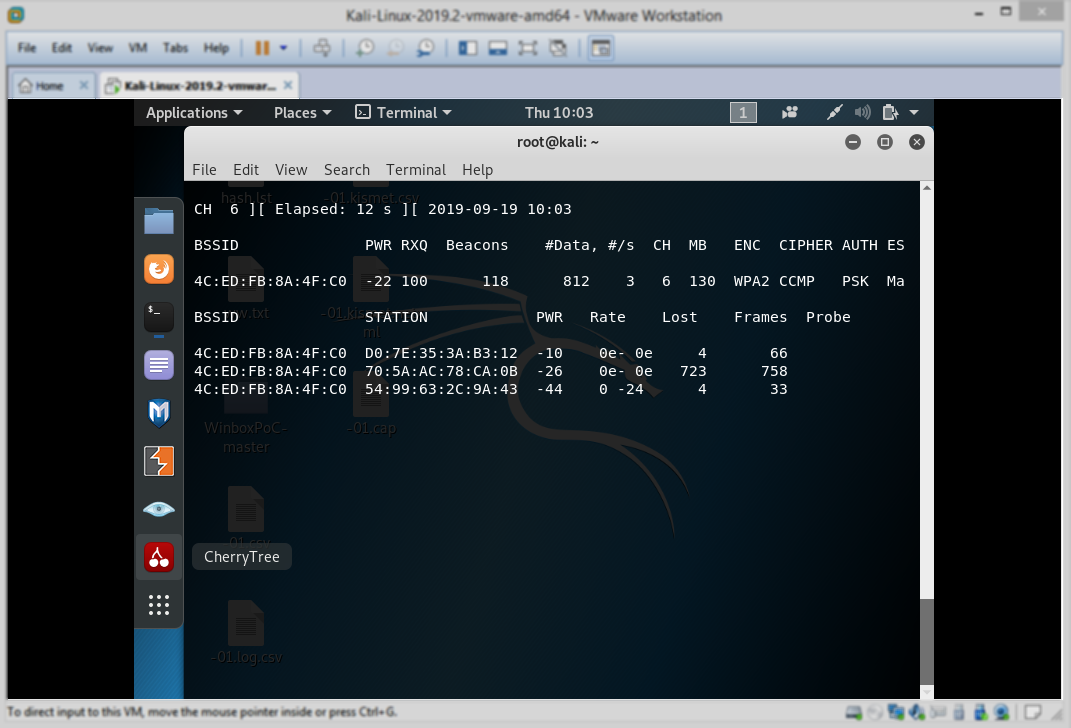
Программа наблюдает за сетью
А вот что происходит после того, как то-то к сети подключился, и программе удалось получить нужные данные.

Получение необходимых данных
Шаг 8
Вы можете пропустить этот шаг в том случае, если у вас уже есть handshake-файлы. Здесь описан альтернативный способ получения соответствующих данных.
Речь идёт об использовании следующей команды:
aireplay-ng -0 2 -a [router bssid] -c [client bssid] wlan0mon
Здесь [router bssid] нужно заменить на BSSID Wi-Fi-сети, а [client bssid] — на идентификатор рабочей станции.
Эта команда позволяет получить handshake-данные в том случае, если вам не хочется ждать момента чьего-либо подключения к сети. Фактически, эта команда атакует маршрутизатор, выполняя внедрение пакетов. Параметр -0 2 можно заменить другим числом, например, указать тут число 50, или большее число, и дождаться получения handshake-данных

Использование утилиты aireplay-bg
Шаг 9
Теперь воспользуемся такой командой:
aircrack-ng -a2 -b [router bssid] -w [path to wordlist] /root/Desktop/*.cap
-a2означает WPA.-b— это BSSID сети.-w— это путь к списку паролей.*.cap— это шаблон имён файлов, содержащих пароли.
В моём случае эта команда выглядит так:
aircrack-ng -a2 -b 4C:ED:FB:8A:4F:C0 -w /root/Desktop/ww.txt /root/Desktop/*.cap
После выполнения этой команды начнётся процесс взлома пароля. Если пароль будет успешно взломан — вы увидите что-то, похожее на следующий скриншот.
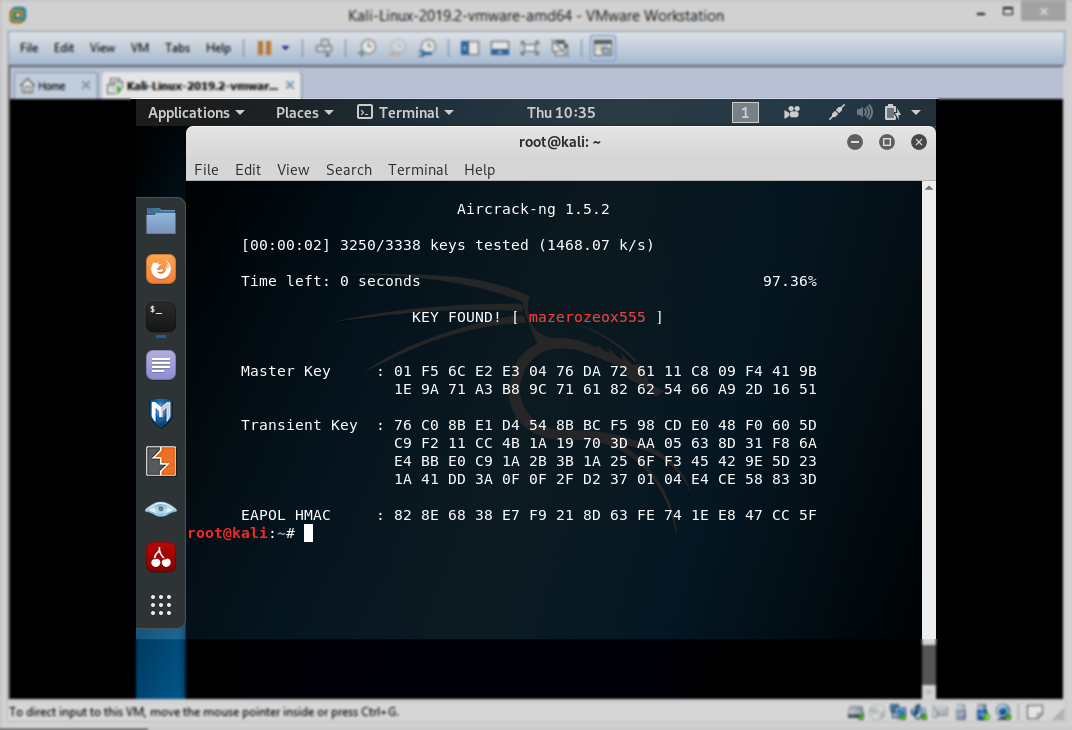
Успешный взлом пароля
Как вы контролируете безопасность своих беспроводных сетей?


Batch Wi-Fi Brute Forcer — By TechnicalUserX
An active attack tool against Wi-Fi networks with internal CMD commands.
This program is created to be a proof of concept that it is possible
to write a working Wi-Fi attack tool with Batchfiles since there
are countless examples on the internet that claims to be legit
hacking tools, working on CMD. While this tool does not claim
a 100% success ratio, it still works if the target Wi-Fi has
weak password. 
Usage
Interface initialization
The program automatically detects your wireless interfaces when you execute the batch file.
If it finds only one, it will select it as default. If there are multiple interfaces,
the program will ask you to choose one. If none exist, it will stay «not_defined».
You can later change the interface by typing
interfaceon the main menu.
This will bring the interface initialization screen back.
Scan
When you type scan at the main menu, the program will enumerate all Wi-Fi networks
available from the selected wireless interface. You can choose one by typing the number
associated with an SSID.
No Name could mean that the network is hidden. You cannot attack that network.
Performing a scan disconnects the interface from the network that it has connected previously.
Selecting a wordlist
A wordlist file is already provided in the repository. If you want to use a custom
wordlist, you have to specify the file you are going to use by typing wordlist on the
main menu and then typing the absolute or relative path of the wordlist file.
Attacking
Simply type attack and the program will show you a warning screen that this process is going
to delete the profile associated with the SSID if you have connected to it before.
It means you will lose the password you entered while connecting to that SSID before.
Save it before using the attack.
Counter
When a connection is attempted with netsh to a network, it takes time to establish the connection. To check whether the connection is successful,
the program repeatedly queries the connection status of the selected interface. A counter value controls how many times this query will be done.
If not changed, the counter value is 5, and counts down after each query for each password combination.
If an authentication or association is detected, this value is increased by 5 to ensure a successful connection.
Limitations
-
This program has been tested unsuccessfully on Windows 7 and tested successfully on Windows 10 and 11. Since some commands may differ in terms of output between Windows versions, it is not expected to work on previous versions.
-
ANSI escape sequences used in the terminal were added to the Windows Console in the Windows 10 version 1511, previous versions are not expected to run this program.
-
There is a strict dependency on the command line utility
netsh, meaning that it cannot understand «Unicode» characters. Only ASCII characters are supported for network names. -
Speed is significantly slow due to its nature.
-
Cannot attack hidden networks.
Result file
If an attack is successful, the result is automatically written to result.txt.
Help screen
Commands - help : Displays this page - wordlist : Provide a wordlist file - scan : Performs a WI-FI scan - interface : Open Interface Management - attack : Attacks selected WI-FI - counter : Sets the attack counter - exit : Close the program
Contributors
Huge thanks to everyone for their contributions to this project.
- TheKvc aka Batch-Man (www.batch-man.com)
- Ankitamehra93
- lioen-dev
- akshatbhatter1
Special thanks to the TheBATeam, and AACINI.
More From TechnicalUserX
Check out TechnicalUserX for more projects.
As a cyber security expert, grasping the intricacies of WiFi password hacking softwares opens the door to secured networks and empowers you to navigate the complex realm of cybersecurity with skill and confidence.
In fact, these tools are designed to help you identify vulnerabilities in WiFi networks and exploit them to gain access and should be part of your arsenal.
If you’re interested in learning more about WiFi hacking, this article is for you. We’ll begin by discussing it and then show you different tools to help you accomplish your goal.
We’ve also created a list of 12 tools, each with a description, their benefits, and whether or not they’re included in Kali Linux.
If you’re ready to jump in, let’s begin.
Table Of Contents
- About WiFi Hacking
- Top Free WiFi Password Hacking Softwares
- Aircrack-NG
- CoWPAtty
- Reaver
- Fern WiFi Cracker
- Wifite
- Kismet
- Airgeddon
- Fluxion
- Wifiphisher
- WiFipumpkin
- Bettercap
- Hashcat
- Conclusion
- Frequently Asked Questions
About WiFi Hacking
Before we start looking into the available WiFi hacking tools, let’s quickly discuss what WiFi hacking is.
WiFi hacking includes technical attacks like “Man-in-the-Middle,” where an attacker captures traffic to obtain the pre-shared key and then crack the password, and social engineering attacks like the “Evil Twin” attack.
In an Evil Twin attack, hackers create a rogue WiFi access point that mimics a legitimate one, tricking users into connecting by exploiting their trust in the familiar network name.
While technical attacks require specific tools and knowledge of secure network protocols, social engineering attacks exploit human psychology and negligence.
You’ll also need hardware to perform these types of attacks.
Essential hardware includes a wireless network adapter that supports monitor mode and packet injection, and a hacking OS like Kali Linux will make things easier.
Please note that WiFi hacking without explicit permission, including setting up rogue access points, is illegal under laws like the Computer Fraud and Abuse Act in the U.S., with penalties including fines and imprisonment. See Is Hacking Illegal? The Law and Ethical Perspectives for more information.
Now that we’ve discussed WiFi hacking, let’s look at some WiFi hacking tools.
Aircrack-NG

Aircrack-ng is a popular collection of tools known for its efficiency in cracking WEP and WPA/WPA2 protocols. These tools are designed to assess the security of various wireless environments. They enable you to easily capture data packets, monitor networks, and crack weak passwords, making them an important toolkit for ethical hackers and penetration testers. See How to Use Aircrack-ng: A Guide to Network Compromise.
Benefits of Aircrack-NG
Includes everything from packet sniffers to encryption key crackers.
Runs on various operating systems, including Linux, Windows, and macOS.
It’s relatively easy to use with good documentation.
- Included with Kali.
CoWPAtty

CoWPAtty is a tool designed primarily for cracking WPA-PSK (pre-shared key) and WPA2-PSK passwords using dictionary attacks. It leverages the captured network traffic to perform an offline attack, testing each entry in the wordlist against the hash.
Benefits of CoWPAtty
Its command-line nature makes deploying and running it from any system easy.
It supports the use of a precomputed hash file.
CoWPAtty is optimized for conducting dictionary attacks.
- Install with the command:
sudo apt install cowpatty
Reaver

Reaver is a powerful tool for recovering WPA/WPA2 passphrases by targeting Wi-Fi Protected Setup (WPS) protocol vulnerabilities. It exploits a flaw in the WPS PIN feature, an eight-digit number used to add new devices to a wireless network without entering the passphrase.
Benefits of Reaver
Despite its powerful capabilities, Reaver is easy to use.
It can recover the WPS PIN and the WPA/WPA2 passphrase in hours.
Reaver is exceptionally effective at exploiting the WPS PIN vulnerability.
- Included with Kali
Fern WiFi Cracker

Fern Wifi Cracker is a wireless auditing and attack tool designed to analyze and crack Wi-Fi passwords. It provides a user-friendly graphical user interface (GUI). It’s mainly employed to discover vulnerabilities in wireless networks and can handle WEP, WPA, and WPA2 protocols.
Benefits of Fern WiFi Cracker
The GUI is intuitive, making it accessible for beginners and experienced users.
It integrates various third-party tools and scripts, enhancing its functionality.
It includes session hijacking features, allowing you to capture and use session cookies.
You can monitor and audit networks in real time.
- Included with Kali
Wifite

Wifite is a popular tool for automating wireless network security testing among penetration testers. It’s designed to simplify the execution of numerous wireless attacks. Read our How to Use Wifite: Best WiFi Hacking Tutorial to learn more.
Benefits of Wifite
Wifite automates several steps in the attack process, such as capturing handshakes and cracking passwords.
It supports a variety of attacks against WEP, WPA, and WPA2.
Wifite is designed to be easy to use.
Wifite combines features from multiple well-known tools under a single interface.
- Included with Kali
Kismet

Kismet supports many technologies beyond Wi-Fi, including Bluetooth, Zigbee, RF, and more. It functions as a sniffer, a wireless intrusion detection system (WIDS), and even a tool for wardriving. It runs on multiple platforms, including Linux and macOS.
Benefits of Kismet
Can monitor a wide array of devices and frequencies.
Active community engagement.
A REST API for advanced scripting.
Captures data not just on Wi-Fi with the right hardware.
- Included with Kali
Airgeddon

Airgeddon is a multi-use toolkit for auditing wireless networks. It’s a bash-scripted utility that provides an all-in-one platform for WiFi hacking. It integrates with several third-party tools, such as Aircrack-ng. Read our tutorial Evil Twin WiFi Attack: A Step-By-Step Guide to see Airgeddon in use.
Benefits of Airgeddon
Combines a variety of network auditing tools into a single framework.
Intuitive menu system that guides you through various tasks.
It works with a wide range of wireless network adapters.
Supports plugins, allowing you to extend its functionality.
- Included with Kali
Fluxion

Fluxion is a tool designed to audit the security of wireless networks through social engineering. It’s a remake of Linset with improvements in stability and functionality. The tool sets up a series of attacks to deceive users into providing their WiFi passwords on a captive portal.
Benefits of Fluxion
You can customize the phishing pages to resemble the login page of the target network.
By leveraging social engineering, Fluxion gathers credentials without the need for brute-forcing.
Combines several techniques to provide a realistic test of how actual attackers could exploit the network.
- Needs to be installed. See official GitHub for instructions.
Wifiphisher

Wifiphisher is a rogue access point framework for conducting sophisticated WiFi attacks and red team engagements. By setting up fake access points it enables the interception and manipulation of wireless communications. It’s particularly effective in simulating phishing attacks to capture sensitive information like WiFi passwords and credentials or even deploy malware.
Benefits of Wifiphisher
Its intuitive textual user interface guides you through setting up and executing attacks.
Easily gains MITM position using techniques such as Evil Twin, KARMA, and Known Beacons.
Comes with a variety of phishing templates that can be tailored for specific scenarios.
Incorporates the latest research in WiFi phishing and is constantly updated by developers.
- Install with the command:
sudo apt install wifiphisher
WiFipumpkin

Wifipumpkin3 is an interactive command line interface framework for red teamers and reverse engineers. It allows you to establish rogue access points to facilitate man-in-the-middle (MITM) attacks. Written in Python, it offers features that support versatile wireless attacks.
Benefits of WiFipumpkin
It supports various attacks, including rogue access points, MITM attacks, credential harvesting, and even multifactor authentication (MFA) phishing.
Includes modules for de-authentication attacks, a rogue DNS server, and tools like EvilQR3 for QR code phishing.
Offers tools to intercept, inspect, modify, and replay web traffic.
- Install with the command:
sudo apt install wifipumpkin3
Bettercap

Bettercap is a powerful network attack and monitoring framework that can be used for WiFi hacking. It provides a comprehensive suite of tools and capabilities tailored to perform deauth attacks to capture the four-way handshake or create rogue access points. See our Bettercap Tutorial & Top Commands.
Benefits of Bettercap
Ability to harvest credentials transmitted over WiFi networks.
Supports man-in-the-middle (MITM) attacks.
Can create rogue access points.
- Install with the command:
sudo apt install bettercap
Hashcat

Hashcat is a powerful password-cracking tool that can crack hashed passwords, including those used in WiFi networks. It leverages the computational power of modern GPUs to perform high-speed password cracking, making it a great tool for WiFi hacking.
Benefits of Hashcat
Uses the parallel processing of GPUs to speed up password cracking.
Supports a wide range of hashing algorithms commonly used in WiFi encryption, including WPA/WPA2-PSK (pre-shared key), WPA-Enterprise, and WPA2-Enterprise.
Offers various attack modes, such as dictionary attacks, brute-force attacks, and rule-based attacks.
- Installed with Kali
Conclusion
With our list of WiFi password hacking softwares, you have the necessary tools to test the security of your network and protect it from potential threats.
We recommend you test out these tools in a practice lab where you can become familiar with how they work and the various features they offer.
If you’re eager to learn more about WiFi hacking or hacking in general, join the StationX Accelerator program. We offer you courses, labs, mentorships, and much more.
Frequently Asked Questions
Do I need special hardware to hack WiFi?
Yes, you need specialized hardware and software. These include a wireless network adapter capable of packet injection and monitor mode and an operating system that can run the necessary tools for performing wireless attacks, such as Kali Linux or Parrot OS.
Is hacking WiFi illegal?
Yes, hacking WiFi networks is generally illegal if you don’t have explicit permission from the network owner or administrator. Illegally accessing wireless networks can be considered a form of computer fraud or abuse, a crime punishable by law in most jurisdictions. Only hack WiFi networks as part of an authorized pentest with permission from the owner. See Is Hacking Illegal? The Law and Ethical Perspectives for more information.
What is an evil twin attack?
An evil twin attack is when an attacker sets up a wireless access point that mimics a legitimate wireless network’s name (SSID) and configuration. They do this to lure users to connect to the fake access point instead of the real one. Once a victim connects to the evil twin network, the attacker can intercept (sniff) and potentially manipulate the victim’s network traffic. For a more detailed look at this, see Evil Twin WiFi Attack: A Step-By-Step Guide.
Can Kali Linux crack WiFi?
Kali cannot crack WiFi by itself, although it does include tools capable of cracking the WiFi handshake, including Aircrack-ng, Wifite, Hashcat, and others.
-
Richard is a cyber security enthusiast, eJPT, and ICCA who loves discovering new topics and never stops learning. In his home lab, he’s always working on sharpening his offensive cyber security skills. He shares helpful advice through easy-to-understand blog posts that offer practical support for everyone. Additionally, Richard is dedicated to raising awareness for mental health. You can find Richard on LinkedIn, or to see his other projects, visit his Linktree.
