Microsoft has released cumulative updates for all supported operating systems. The updates primarily focus on fixing discovered bugs and vulnerabilities, but may also include new features. The updates are now available in Windows Update.
Here are the updates and their changes.

- Windows 11 (version 24H2) — KB5058411 (OS Build 26100.4061). ⬇️ Microsoft Update Catalog.
- Windows 11 (version 23H2) — KB5058405 (OS Build 22631.5335). ⬇️ Microsoft Update Catalog.
- Windows 11 (version 22H2) — KB5055528 (OS Build 22621.5335). ⬇️ Microsoft Update Catalog.
Here are the key highlights.
Gradual roll-out
Recall (Preview)
Do you work with a lot of apps, websites, and documents, and sometimes it’s hard to remember where you saw something when you need it again? Recall offers a completely new way to safely find what you saw or did on your PC. With the AI capabilities of Copilot+ PCs, you can quickly find information and return to any app, website, image, or document simply by describing its content.
To use Recall, you’ll need to agree to save screenshots (snapshots of your activity) and set up Windows Hello to verify your presence so that only you can access the screenshots. You also have control over which screenshots are saved and can pause saving at any time.
As you use your Copilot+ PC, whether you’re working on documents or presentations, participating in a video conference, or switching between tasks, Recall will regularly take screenshots to help you find what you need in the future. When you need to find something you saw or did before, open Recall and authenticate with Windows Hello.
Once you find the data you want, you can reopen the app, website, or document, and use Click to Do to perform an action on any image or text in the photo you find.
You can read more about Recall in Microsoft’s documentation.
Click to Do (Preview)
-
- Click to Do lets you take quick actions on any content on your Copilot+ PC screen. It helps you complete tasks in real time and quickly takes you to the app that can do the job best.
For example, you can select an image in Click to Do to do things like delete objects in the Photos app or remove the background in Paint. - To use Click to Do, simply use WIN + <mouse click>, WIN + Q, use the Snipping Tool app menu, or the Print Screen key. You can also search for Click to Do in the search box on the Windows taskbar.
More information about Click to Do can be found on the Microsoft website. - On Snapdragon-powered Copilot+ PCs, Click to Do includes intelligent text actions. Use WIN + <mouse click> or WIN + Q to highlight a block of text, then select the text you want. You’ll then see options to create a summary or rewrite the text to make it more informal or more formal.
- These text actions take advantage of Phi Silica , the small language model (SLM) native to Windows.
- You can open the Click to Do feature by swiping left from the right edge of the screen.
- There are policies available to help manage Click to Do in an enterprise environment. You can learn more about them on the Microsoft website.
- Click to Do lets you take quick actions on any content on your Copilot+ PC screen. It helps you complete tasks in real time and quickly takes you to the app that can do the job best.
Improved Windows Search
- On devices with the Copilot+ PC label and AMD and Intel processors, finding documents, photos, and settings is easier thanks to the introduction of Enhanced Windows Search, which is based on semantic models in addition to traditional lexical indexing.
- Whether you are searching in File Explorer, the search box on the taskbar, or Settings, simply type what you think to find it on your PC. You no longer need to remember file names, exact words in document content, or the names of settings.
- Thanks to the neural processing unit (NPU) with a performance of over 40 TOPS built into Copilot+ PC devices, improved search is available even without an Internet connection. For detailed information on how semantic search works on Copilot+ PCs, please refer to the documentation at this link.
- In addition, photos from the cloud will now appear in search results along with images saved on your local computer. The results will also show exact matches for your keywords in the text of your cloud files.
- The feature only works with personal OneDrive cloud storage. To try out the improved search, you must be signed in to a Microsoft account and have an active Internet connection.
Narrator
- Speech Recap lets you monitor what Narrator has said and quickly access that information. With simple keyboard shortcuts, you can follow the transcription in real time and copy what Narrator last said.
Phone link
- The Windows 11 Start menu has a new sidebar, which offers a quick and easy way to interact with your connected smartphone. You can use it to make phone calls, send text messages, access your photos, and share content between your PC and smartphone.
Widgets
- Web developers can now use existing web content to create dynamic and interactive widgets that can be added to the Widgets panel in Windows 11. You can read more about this in Microsoft’s documentation.
- For insiders in the European Economic Area (EEA)
- You can now customize how the Weather widget works on your lock screen. To do this, go to Settings > Personalization > Lock Screen and tap the Customize widget option in the weather widget’s advanced settings menu. More widgets will be customizable in the future.
File Explorer
- The Home page in File Explorer now shows personalized elements to help you easily access your Microsoft 365 content on Windows.
- Extended support for text scaling has been implemented in Explorer, the Open and Save dialog boxes, and the file copy window. Text scaling is configured in Options > Accessibility > Text Size.
- The performance of extracting archived files in Explorer has been improved. This will be especially noticeable when unpacking a large number of small files.
- Fixed an issue where the address bar in File Explorer might not display the path after opening a directory.
Settings
- On Copilot+ PCs, you can now control which apps Windows can recommend actions from. The settings can be found under Settings > Apps > Actions.
Windows Studio Effects
- The auto crop feature in Windows Studio Effects will be enabled the first time you use the camera if your PC supports Windows Studio Effects.
- Fixed an issue where you couldn’t switch between pinned app pages in the Start menu using touch.
- Fixed an issue where, when using a larger text size, the Sign Out and More options buttons might not appear in the Account Manager in the Start menu.
Taskbar
- Fixed an issue where underlines under app icons on the taskbar could remain visible even if the app was closed.
- Fixed an issue where the arrow keys would work in the wrong direction after using the WIN + T shortcut on an Arabic or Hebrew system.
Desktop icons
-
- Updated logic for app icons on the desktop. Packaged apps will no longer have an accent color background (for example, if you drag the Snipping Tool icon from the Start app list to the desktop). Icons should also be larger to make them easier to distinguish.
Display
- Fixed an issue where sometimes you had to use WIN + P twice to switch projection mode.
ExtFloodFill
- Fixed a rare issue with ExtFloodFill that could cause a horizontal line to appear in the wrong location in Win32 applications.
Graphics
- Fixed an issue where the system would sometimes fail to detect external graphics cards connected via Thunderbolt.
Hyper-V
- Fixed an issue where Hyper-V Manager might sometimes report no CPU usage (0%) for virtual machines.
Available to all users
BSOD
- Fixed an issue that occurred after installing the April 2025 security update and rebooting the device. Some computers may experience a BSOD with error code 0x18B, indicating SECURE_KERNEL_ERROR.
Dynamic Host Configuration Protocol (DHCP Client)
- Fixed an issue that affected the ability to connect to the Internet after waking the device from sleep mode. Users would occasionally lose their Internet connection.
File systems
-
- Fixed an issue for users with profiles redirected to a network virtual hard disk (VHD or VHDX) where a certain failure could cause the operating system to crash.
Image processing
-
- Fixed an issue where some pages that included JPEG images were not displayed.
Windows Hello
-
- Fixed a rare issue with Windows Hello that affected devices with certain security features enabled. After performing a system reset (Reset this PC in Settings > System > Recovery with the Keep my files and Remove everything options selected), some users may have experienced an inability to sign in to Windows services using Windows Hello facial recognition or a PIN.
Settings
-
- Fixed an issue where installing Windows 11 version 24H2 using Windows Setup and then running System Preparation (Sysprep) would not update the boot configuration correctly, preventing the system recovery options from System > Recovery from working.
Windows Update
-
- The system now tells you the estimated time your computer will be unusable while Windows updates are installed. This estimated time will be displayed on the Windows Update page and in the power button menu in Start.
Audio
-
- Fixed an issue where microphone audio capture could unexpectedly turn off.
Eye control
-
- Fixed an issue where the eye control app would not launch.
Updates for Windows 10
- Windows 10 version 22H2, 2022 Update — KB5058379 (OS Build 19045.5854). ⬇️ Microsoft Update Catalog.
- Windows 10 version 21H2, November 2021 Update — KB5058379 (OS Build 19044.5854). ⬇️ Microsoft Update Catalog.
- Windows 10 version 1809, October 2018 Update — KB5058392 (OS Build 17763.7314). ⬇️ Microsoft Update Catalog.
- Windows 10 version 1607, Anniversary Update — KB5058383 (OS Build 14393.8066). ⬇️ Microsoft Update Catalog.
- Windows 10 version 1507 — KB5058387 (OS Build 10240.21012). ⬇️ Microsoft Update Catalog.
The changes are as follows:
[Secure Boot Advanced Targeting (SBAT) and Linux Extensible Firmware Interface (EFI)] This update applies improvements to SBAT for the detection of Linux systems.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:
If you like this article, please share it using the buttons below. It won’t take a lot from you, but it will help us grow. Thanks for your support!
У нас новый пакет обновлений безопасности от Microsoft. В этот раз корпорация устранила 72 уязвимости, включая пять, которые уже использовались злоумышленниками, и две 0-day, ставшие достоянием общественности до выхода патча.
Из них шесть критических, причём пять связаны с RCE, а одна — с утечкой данных. Важно: набор не включает баги в Azure, Edge и других продуктах, которые Microsoft уже патчила ранее в этом месяце.
Microsoft пока не делится деталями кибератак, но факт эксплуатации подтверждён.
Две уязвимости были раскрыты публично до выхода патча, но пока атак не зафиксировано:
| Затронутый компонент | CVE-идентификатор | CVE-наименование | Степень риска |
| .NET, Visual Studio, and Build Tools for Visual Studio | CVE-2025-26646 | .NET, Visual Studio, and Build Tools for Visual Studio Spoofing Vulnerability | Важная |
| Active Directory Certificate Services (AD CS) | CVE-2025-29968 | Active Directory Certificate Services (AD CS) Denial of Service Vulnerability | Важная |
| Azure | CVE-2025-33072 | Microsoft msagsfeedback.azurewebsites.net Information Disclosure Vulnerability | Критическая |
| Azure | CVE-2025-30387 | Document Intelligence Studio On-Prem Elevation of Privilege Vulnerability | Важная |
| Azure Automation | CVE-2025-29827 | Azure Automation Elevation of Privilege Vulnerability | Критическая |
| Azure DevOps | CVE-2025-29813 | Azure DevOps Server Elevation of Privilege Vulnerability | Критическая |
| Azure File Sync | CVE-2025-29973 | Microsoft Azure File Sync Elevation of Privilege Vulnerability | Важная |
| Azure Storage Resource Provider | CVE-2025-29972 | Azure Storage Resource Provider Spoofing Vulnerability | Критическая |
| Microsoft Brokering File System | CVE-2025-29970 | Microsoft Brokering File System Elevation of Privilege Vulnerability | Важная |
| Microsoft Dataverse | CVE-2025-47732 | Microsoft Dataverse Remote Code Execution Vulnerability | Критическая |
| Microsoft Dataverse | CVE-2025-29826 | Microsoft Dataverse Elevation of Privilege Vulnerability | Важная |
| Microsoft Defender for Endpoint | CVE-2025-26684 | Microsoft Defender Elevation of Privilege Vulnerability | Важная |
| Microsoft Defender for Identity | CVE-2025-26685 | Microsoft Defender for Identity Spoofing Vulnerability | Важная |
| Microsoft Edge (Chromium-based) | CVE-2025-4050 | Chromium: CVE-2025-4050 Out of bounds memory access in DevTools | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2025-4096 | Chromium: CVE-2025-4096 Heap buffer overflow in HTML | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2025-29825 | Microsoft Edge (Chromium-based) Spoofing Vulnerability | Критическая |
| Microsoft Edge (Chromium-based) | CVE-2025-4052 | Chromium: CVE-2025-4052 Inappropriate implementation in DevTools | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2025-4051 | Chromium: CVE-2025-4051 Insufficient data validation in DevTools | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2025-4372 | Chromium: CVE-2025-4372 Use after free in WebAudio | Unknown |
| Microsoft Office | CVE-2025-30377 | Microsoft Office Remote Code Execution Vulnerability | Критическая |
| Microsoft Office | CVE-2025-30386 | Microsoft Office Remote Code Execution Vulnerability | Критическая |
| Microsoft Office Excel | CVE-2025-29977 | Microsoft Excel Remote Code Execution Vulnerability | Важная |
| Microsoft Office Excel | CVE-2025-30383 | Microsoft Excel Remote Code Execution Vulnerability | Важная |
| Microsoft Office Excel | CVE-2025-29979 | Microsoft Excel Remote Code Execution Vulnerability | Важная |
| Microsoft Office Excel | CVE-2025-30376 | Microsoft Excel Remote Code Execution Vulnerability | Важная |
| Microsoft Office Excel | CVE-2025-30393 | Microsoft Excel Remote Code Execution Vulnerability | Важная |
| Microsoft Office Excel | CVE-2025-32704 | Microsoft Excel Remote Code Execution Vulnerability | Важная |
| Microsoft Office Excel | CVE-2025-30375 | Microsoft Excel Remote Code Execution Vulnerability | Важная |
| Microsoft Office Excel | CVE-2025-30379 | Microsoft Excel Remote Code Execution Vulnerability | Важная |
| Microsoft Office Excel | CVE-2025-30381 | Microsoft Excel Remote Code Execution Vulnerability | Важная |
| Microsoft Office Outlook | CVE-2025-32705 | Microsoft Outlook Remote Code Execution Vulnerability | Важная |
| Microsoft Office PowerPoint | CVE-2025-29978 | Microsoft PowerPoint Remote Code Execution Vulnerability | Важная |
| Microsoft Office SharePoint | CVE-2025-30378 | Microsoft SharePoint Server Remote Code Execution Vulnerability | Важная |
| Microsoft Office SharePoint | CVE-2025-30382 | Microsoft SharePoint Server Remote Code Execution Vulnerability | Важная |
| Microsoft Office SharePoint | CVE-2025-30384 | Microsoft SharePoint Server Remote Code Execution Vulnerability | Важная |
| Microsoft Office SharePoint | CVE-2025-29976 | Microsoft SharePoint Server Elevation of Privilege Vulnerability | Важная |
| Microsoft PC Manager | CVE-2025-29975 | Microsoft PC Manager Elevation of Privilege Vulnerability | Важная |
| Microsoft Power Apps | CVE-2025-47733 | Microsoft Power Apps Information Disclosure Vulnerability | Критическая |
| Microsoft Scripting Engine | CVE-2025-30397 | Scripting Engine Memory Corruption Vulnerability | Важная |
| Remote Desktop Gateway Service | CVE-2025-26677 | Windows Remote Desktop Gateway (RD Gateway) Denial of Service Vulnerability | Важная |
| Remote Desktop Gateway Service | CVE-2025-29967 | Remote Desktop Client Remote Code Execution Vulnerability | Критическая |
| Remote Desktop Gateway Service | CVE-2025-29831 | Windows Remote Desktop Services Remote Code Execution Vulnerability | Важная |
| Remote Desktop Gateway Service | CVE-2025-30394 | Windows Remote Desktop Gateway (RD Gateway) Denial of Service Vulnerability | Важная |
| Role: Windows Hyper-V | CVE-2025-29955 | Windows Hyper-V Denial of Service Vulnerability | Важная |
| Universal Print Management Service | CVE-2025-29841 | Universal Print Management Service Elevation of Privilege Vulnerability | Важная |
| UrlMon | CVE-2025-29842 | UrlMon Security Feature Bypass Vulnerability | Важная |
| Visual Studio | CVE-2025-32703 | Visual Studio Information Disclosure Vulnerability | Важная |
| Visual Studio | CVE-2025-32702 | Visual Studio Remote Code Execution Vulnerability | Важная |
| Visual Studio Code | CVE-2025-21264 | Visual Studio Code Security Feature Bypass Vulnerability | Важная |
| Web Threat Defense (WTD.sys) | CVE-2025-29971 | Web Threat Defense (WTD.sys) Denial of Service Vulnerability | Важная |
| Windows Ancillary Function Driver for WinSock | CVE-2025-32709 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | Важная |
| Windows Common Log File System Driver | CVE-2025-32701 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | Важная |
| Windows Common Log File System Driver | CVE-2025-30385 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | Важная |
| Windows Common Log File System Driver | CVE-2025-32706 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | Важная |
| Windows Deployment Services | CVE-2025-29957 | Windows Deployment Services Denial of Service Vulnerability | Важная |
| Windows Drivers | CVE-2025-29838 | Windows ExecutionContext Driver Elevation of Privilege Vulnerability | Важная |
| Windows DWM | CVE-2025-30400 | Microsoft DWM Core Library Elevation of Privilege Vulnerability | Важная |
| Windows File Server | CVE-2025-29839 | Windows Multiple UNC Provider Driver Information Disclosure Vulnerability | Важная |
| Windows Fundamentals | CVE-2025-29969 | MS-EVEN RPC Remote Code Execution Vulnerability | Важная |
| Windows Hardware Lab Kit | CVE-2025-27488 | Microsoft Windows Hardware Lab Kit (HLK) Elevation of Privilege Vulnerability | Важная |
| Windows Installer | CVE-2025-29837 | Windows Installer Information Disclosure Vulnerability | Важная |
| Windows Kernel | CVE-2025-24063 | Kernel Streaming Service Driver Elevation of Privilege Vulnerability | Важная |
| Windows Kernel | CVE-2025-29974 | Windows Kernel Information Disclosure Vulnerability | Важная |
| Windows LDAP — Lightweight Directory Access Protocol | CVE-2025-29954 | Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability | Важная |
| Windows Media | CVE-2025-29962 | Windows Media Remote Code Execution Vulnerability | Важная |
| Windows Media | CVE-2025-29963 | Windows Media Remote Code Execution Vulnerability | Важная |
| Windows Media | CVE-2025-29964 | Windows Media Remote Code Execution Vulnerability | Важная |
| Windows Media | CVE-2025-29840 | Windows Media Remote Code Execution Vulnerability | Важная |
| Windows NTFS | CVE-2025-32707 | NTFS Elevation of Privilege Vulnerability | Важная |
| Windows Remote Desktop | CVE-2025-29966 | Remote Desktop Client Remote Code Execution Vulnerability | Критическая |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-29836 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | Важная |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-29959 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | Важная |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-29835 | Windows Remote Access Connection Manager Information Disclosure Vulnerability | Важная |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-29960 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | Важная |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-29832 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | Важная |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-29830 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | Важная |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-29961 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | Важная |
| Windows Routing and Remote Access Service (RRAS) | CVE-2025-29958 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | Важная |
| Windows Secure Kernel Mode | CVE-2025-27468 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability | Важная |
| Windows SMB | CVE-2025-29956 | Windows SMB Information Disclosure Vulnerability | Важная |
| Windows Trusted Runtime Interface Driver | CVE-2025-29829 | Windows Trusted Runtime Interface Driver Information Disclosure Vulnerability | Важная |
| Windows Virtual Machine Bus | CVE-2025-29833 | Microsoft Virtual Machine Bus (VMBus) Remote Code Execution Vulnerability | Критическая |
| Windows Win32K — GRFX | CVE-2025-30388 | Windows Graphics Component Remote Code Execution Vulnerability | Важная |
Апдейт доступен всем пользователям
Компания Microsoft выпустила один из самых больших апдейтов для Windows 11 в рамках традиционного ежемесячного «обновления по вторникам» (Patch Tuesday). Апдейт под номером KB5040442 доступен для версий 23H2 и 22H2, а KB5040431 – для 21H2. Обязательное обновление приносит довольно много новшеств.

Среди основных улучшений – возвращение кнопки «Показать рабочий стол», которая была скрыта по умолчанию, когда Microsoft выпустила Copilot для всех пользователей. ОС теперь также позволяет создавать файлы 7-Zip и Tape Archive (TAR) с помощью контекстного меню. Щелчок правой кнопкой мыши по файлу и выбор «Сжать в» позволяет использовать такие инструменты, как gzip и bzip2.

Новая функция менеджера учетных записей в меню «Пуск» позволяет быстро просмотреть преимущества учетной записи Microsoft и упрощает управление настройками.

Приложение Copilot теперь закреплено на панели задач и ведет себя как обычное приложение, позволяя изменять размер, перемещать и прикреплять окно. Эта функция внедряется постепенно и изначально будет доступна для новых ПК с Windows 11 и новых ПК Copilot+ в Европейской экономической зоне и других регионах.
Кроме того, были устранены проблемы с сенсорной клавиатурой, инструментом «Ножницы» и опцией «Безопасное извлечение устройства», а также сделано множество других доработок.
10 июля 2024 в 11:53
| Теги: Windows, Microsoft
| Источник: WindowsLatest
3DNews Новости Software Операционные системы Microsoft наконец-то ускорила «Проводник…
Самое интересное в обзорах
Microsoft выпустила обновление KB5055627 для Windows 11 24H2, которое значительно ускоряет работу «Проводника». Теперь вкладка «Главная» загружается быстрее, а задержки, связанные с запуском интерфейса, значительно сократились.
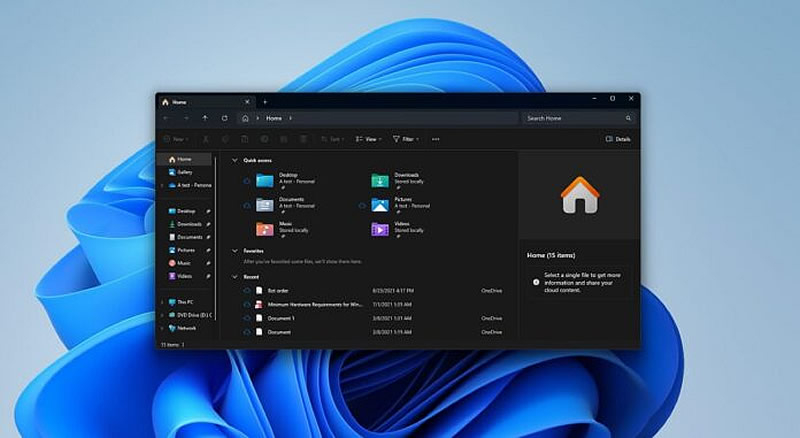
Источник изображения: windowslatest.com
Пользователи Windows 11 24H2 заметили, что «Проводник» стал работать заметно быстрее после установки обновления KB5055627 (сборка 26100.3915 или новее). Хотя официально Microsoft не анонсировала это изменение, на практике это довольно заметно, особенно при открытии вкладки «Главная» с разделами «Недавние», «Избранное» и «Общие», сообщает ресурс Windows Latest.
Ранее «Проводник» мог загружаться несколько томительных секунд, особенно при первом запуске после включения компьютера. На экране появлялась надпись «Загрузка…», а меню и лента интерфейса откликались с задержкой. Теперь эти проблемы устранены. И хотя интерфейс по-прежнему требует некоторого времени на полную загрузку, его работа значительно улучшилась.
Microsoft объясняет прошлые замедления переходом на современные фреймворки WinUI и интеграцией облачных сервисов, которых не было в Windows 10 или Windows 7. При открытии «Проводника», система инициализирует компоненты интерфейса, загружает значки синхронизации и обрабатывает расширения оболочки. Всё это создавало дополнительную нагрузку, но в KB5055627 все эти процессы удалось оптимизировать.
Помимо скорости, обновление принесло и другие изменения: шкала заполненности дисков и прогресс-бар при копировании файлов отображаются в более приятных тёмных оттенках синего и зелёного. Также Microsoft исправила баг, из-за которого контекстное меню «Проводника» раскрывалось в неправильную сторону.
Сообщается, что обновление KB5055627 пока доступно как необязательное, но 13 мая оно войдёт в обязательный набор исправлений «вторника патчей» (Patch Tuesday). Пользователи, которые уже установили его, не сообщают о серьёзных проблемах, хотя у некоторых остаются сложности с Windows Hello при отключённой инфракрасной камере.
Если вы заметили ошибку — выделите ее мышью и нажмите CTRL+ENTER.
Readers help support Windows Report. We may get a commission if you buy through our links.
Read our disclosure page to find out how can you help Windows Report sustain the editorial team. Read more
Microsoft has released May 2025 Patch Tuesday updates for Windows 11 versions 24H2, 23H2, and 22H2. For version 24H2, the update comes as KB5058411, bringing the build to 26100.4061.
Versions 23H2 and 22H2 get KB5058405, bumping both to build 22631.5335 and 22621.5335, respectively. Each update includes security fixes and under-the-hood improvements as part of the monthly rollout.
What’s new for Windows 11 24H2, 23H2, and 22H2 with May 2025 Patch Tuesday
Microsoft detailed everything in its support page:
For Windows 11 24H2
Highlights
- This update addresses security issues for your Windows operating system.
Improvements
This security update includes improvements that were a part of update KB5055627 (released April 25, 2025). The following summary outlines key issues addressed by the KB update after you install it. Also, included are the available new features. The bold text within the brackets indicates the item or area of the change.
- [Audio] Fixed: This update addresses an issue where the audio form your microphone might mute unexpectedly.
- [Eye controller] Fixed: The eye controller app doesn’t launch.
If you installed earlier updates, your device downloads and installs only the new updates contained in this package.
For more information about security vulnerabilities, please refer to the Security Update Guide website and the May 2025 Security Updates.
AI Components
The following AI components have been updated with this release:
AI Component Version Image Search 1.7.824.0 Content Extraction 1.7.824.0 Semantic Analysis 1.7.824.0 Windows 11 servicing stack update (KB5058523)- 26100.4060
This update makes quality improvements to the servicing stack, which is the component that installs Windows updates. Servicing stack updates (SSU) ensure that you have a robust and reliable servicing stack so that your devices can receive and install Microsoft updates. To learn more about SSUs, see Simplifying on-premises deployment of servicing stack updates.
Known issues in this update
Microsoft is not currently aware of any issues with this update.
Microsoft has also detailed everything
For Windows 11 23H2 and 22H2
Highlights
- This update addresses security issues for your Windows operating system.
Improvements
Windows 11, version 23H2
Important: Use EKB KB5027397 to update to Windows 11, version 23H2.
This security update includes quality improvements. Key changes include:
- This build includes all the improvements in Windows 11, version 22H2.
- No additional issues are documented for this release.
Windows 11, version 22H2
This security update includes improvements that were part of update KB5055629 (released April 22, 2025). The following summary outlines key issues addressed by the KB after you install it. Also, included are available new features. The bold text within the brackets indicates the item or area of the change.
- [Secure Boot Advanced Targeting (SBAT) and Linux Extensible Firmware Interface (EFI)] This update applies improvements to SBAT for the detection of Linux systems.
- [Windows Update] Fixed: This update addresses an issue where you might be unable to update to Windows 11, version 24H2 via WSUS. The download might not start or complete, showing error code 0x80240069 and logs with “Service has unexpectedly stopped”.
If you installed earlier updates, your device downloads and installs only the new updates contained in this package.
For more information about security vulnerabilities, see the Security Update Guide and the May 2025 Security Update.
Windows 11 servicing stack update (KB5058528) – 22621.5334 and 22631.5334
This update makes quality improvements to the servicing stack, which is the component that installs Windows updates. Servicing stack updates (SSU) ensure that you have a robust and reliable servicing stack so that your devices can receive and install Microsoft updates. To learn more about SSUs, see Simplifying on-premises deployment of servicing stack updates.
Known issues in this update
Microsoft is not currently aware of any issues with this update.
These updates will roll out via Windows Update and should install automatically for most users. If you prefer to install them manually, you can download the standalone packages from the Microsoft Update Catalog:
- Download for 24H2 (KB5058411)
- Download for 23H2 and 22H2 (KB5058405)
Rishaj Upadhyay
Rishaj is a tech writer who has been writing professionally for over four years, with a passion for Android, Windows, and all things tech. He initially joined Windows Report as a tech journalist and is now taking over as a news editor. He also writes for AndroidHeadlines. In the past, he has covered features, guides, and listicles for YTECHB and TechieTechTech. When he’s not breaking the keyboard, you can find him cooking, or listening to music/podcasts.
