-
What Is the
sun.security.provider.certpath.SunCertPathBuilderExceptionin Java -
Causes of
sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target -
Solution of
sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target

Today’s post will discuss potential reasons for unable to find valid certification path to requested target and its solution in Java.
But, before we continue, you must clearly understand SSL encryption and Certificates since a clear understanding of SSL Certificates is required.
SSL encryption and Certificates: an HTTPS connection cannot function properly without an SSL certificate. Through the use of a set of public and private keys, it substantiates the claimed identity of the service or website.
The private key encrypts or signs everything that is delivered by the domain, and the client apps validate the identification by utilizing the public keys.
What Is the sun.security.provider.certpath.SunCertPathBuilderException in Java
The sun.security.provider.certpath.SunCertPathBuilderException is a class for handling exceptions in Java that checks the server’s SSL certificates that the Java program is attempting to connect to. This class was named after the provider that created the certificates.
The following is the error message shown to the developer when they encounter this issue.
Caused by : sun.security.provider.certpath.SunCertPathBuilderException
: unable to find valid certification path to requested target
It can be thrown during any action involving visiting an encrypted service using SSL.
SSL-protected APIs and websites are checked for trustworthiness by the Java framework before they can be accessed. This is accomplished by examining its internal trusted list to see whether the root certificate authority signed is in there.
Java throws this error if it can’t discover any reference to the service. Using a self-signed certificate to access a service signed by someone else’s digital signature will always fail.
Causes of sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
The only way Java will be able to connect to another program via SSL is if it can trust HTTPS, etc. There is a truststore usually $JAVA HOME/lib/security/cacerts in the Java world where you store your trust certificates.
This exception is triggered by a self-signed certificate or a certificate chain that does not exist in the Java trust store. Java refuses to connect to the application because it does not trust the certificate.
Solution of sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
-
To begin, determine whether the issue stems from the certificate or the network. To verify this, open the URL in Google Chrome or your preferred browser and see whether it works.
In this case, an invalid certificate setting on the application client must be the source of the exception. There may be a firewall or network settings issue if the browser cannot access it.
-
Get the server’s SSL Certificate after determining if there’s an issue with the certificate settings. This might be the root certificate in the simplest of circumstances, but in most cases, a certificate chain and intermediate certificate authority are required.
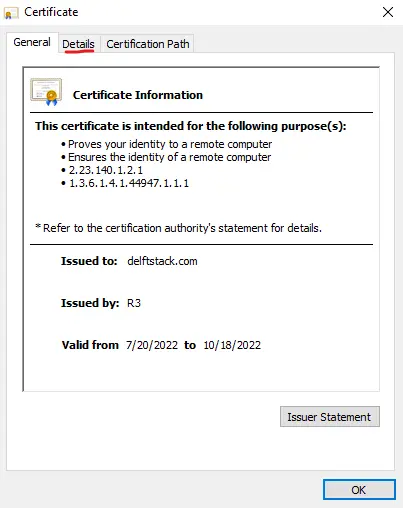
You can check SSL Certificate validity by following the below steps.
-
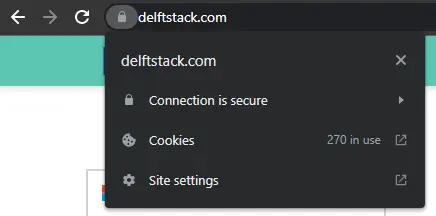
Open your browser and click on the lock in the left upper corner.
-
Then click on
Connection is secure. -
At last, you will get the site’s status if it’s valid.
- If you want certificate details exported, follow the below steps.
-
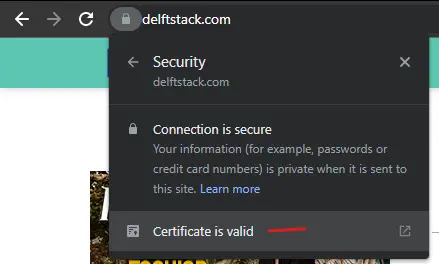
Select the lock symbol next to the URL bar, then click the
Connection is secure>Certificate is valid. -
Click on the
Detailssection and export a certificate by clicking on theCopy to Filebutton. -
Export
DERencoded binaries. -
Choose the directory where you want to save and name the file.
-
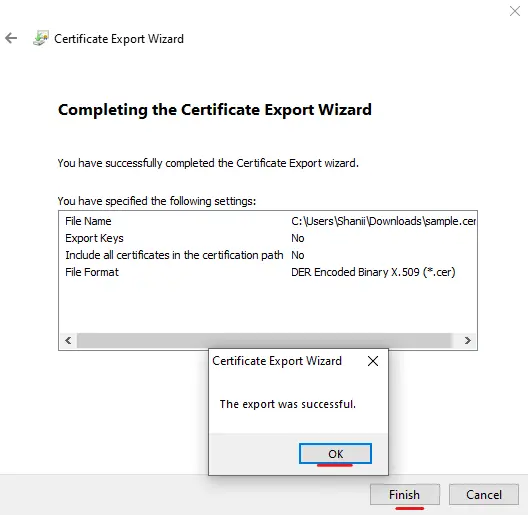
When you click
Finish, you’ll see a messageThe export was successful.
-
Start a trust store entry with a new certificate. The key tool utility can be used to do this.
Execute the following command to create a new trust store.
keytool - import - file C :\cascerts\firstCA.cert - alias firstCA - Keystore myTrustStore -
Restart your program to complete the process.
Enjoying our tutorials? Subscribe to DelftStack on YouTube to support us in creating more high-quality video guides. Subscribe
System information:
- Operating system (distribution) and version: Windows 10
- DBeaver version: 6.1.1
- Java version: 8
- Additional extensions: none
Connection specification:
- Database name and version: Postgres 9.4
- Driver name: PostgreSQL standard driver
- Do you use tunnels or proxies (SSH, SOCKS, etc)? NO
Describe the problem you’re observing:
I’m getting this error:
unable to find valid certification path to requested target when I am trying to connect to remote database, in previous versions I didn’t get this error.

Steps to reproduce, if exist:
Include any warning/errors/backtraces from the logs
- Author
- Recent Posts
I started writing code around 20 years ago, and throughout the years, I have gained a lot of expertise from hands-on experience as well as learning from others. This website has also grown with me and is now something that I am proud of.
The unable to find valid certification path to requested target IntelliJ code exception happens when accessing a server with invalid permissionas. In addition, your program likely encounter the valid certification requested target error log when exporting pages in an area managed by Scroll Versions, which should not happen.

The unable to find valid certification path to requested target Maven broken warning is almost inevitable when the configuration for the certification path fails to recognize the properties and inputs.
Therefore, we suggest reading this profound debugging guide to repair your valid certification path using simple debugging techniques and methods that prevent further complications.
JUMP TO TOPIC
- Why Is the Unable to Find Valid Certification Path Bug Happening?
- – Exporting Pages in an Area Managed by Scroll Versions
- – Accessing a Server With Invalid Permissions
- How to Fix the Unable to Find Valid Certification Path Error Log?
- – Adding a Trusted Keystroke to the SSL Support
- – Configuring the JSSE System Properties
- Conclusion
Why Is the Unable to Find Valid Certification Path Bug Happening?
The unable to find valid certification path to requested target Java 11 bug happens when accessing a server with incorrect permissions. As a result, the program fails to locate and open the file, displaying error logs and exceptions. The error is also typical when exporting pages in a specific area.
For instance, the unable to find valid certification path to requested target Java code exception should affect your programming experience due to insufficient permissions. This inconsistency malfunctions the proper certification path, although most elements and tags are functional and raise no warnings.
In addition, the unable to find a valid certification path to the requested target Windows bug indicates your machine experiences inconsistencies when exporting pages in an area managed by Scroll Versions, a tool with several issues. Nevertheless, the broken error log should help you troubleshoot and pinpoint the culprit, so we suggest scanning the inputs and checking your certification paths.
On the contrary, the unable to find a valid certification path to the requested target Spring Boot message confirms the configuration for the specific way fails to recognize the inputs. Although this is irrelevant when compiling straightforward applications without permissions, it is vital when completing your advanced website or certification program. Considering this, the system is unable to find a valid certification path to the requested target SQL server regardless of your elements and properties’ complexity. Still, remaking and reproducing the incorrect error log is as essential as practicing the debugging techniques because it helps you predict the outcome.
– Exporting Pages in an Area Managed by Scroll Versions
The former section confirmed the unable to find valid certification path to requested target Android Studio bug is common when exporting pages in Scroll Versions’ controlled area. Although most browsers have no issues validating the certificate when accessing the confluence pages, errors occur due to the broken path.
Hence, we will exemplify the error log to help you locate the problems before changing the values. The message in your document could include different indicators.
You can learn more about the invalid log in the following example:
— url: /rest/scroll-pdf/1.0/export | userName: someuser | referer: //my-server: 8444/display/TestPage
javax.net.ssl.SSLHandshakeException: sun.ValidatorException: PKIX path building failed: sun.security.SunCertPathBuilderExceptions: cannot find valid certification path to requested target
at sun.security.ssl.Alerts.SSLException (Unknown Source)
at sun.security.ssl.SSLSocket.fatal (Unknown Source)
at sun.security.ssl.Handshaker.fatal (Unknown Source)
at sun.security.ssl.Handshaker.fatal (Unknown Source)
at sun.security.ssl.serverCertificate (Unknown Source)
at sun.security.ssl.processMessage (Unknown Source)
…
Caused by: sun.ValidatorException: PKIX path building failed: sun.certpath.SunCertPathBuilderException: cannot find valid certification path to requested target
at sun.security.validator.doBuild (Unknown Source)
at sun.security.validator.engineValidate (Unknown Source)
at sun.security.validate (Unknown Source)
at sun.security.ssl.validate (Unknown Source)
at sun.security.ssl.checkTrusted (Unknown Source)
at sun.security.ssl.checkServerTrusted (Unknown Source)
… 55 more
Caused by: sun.security.SunCertPathBuilderExceptions: cannot find valid certification path to requested target
at sun.security.SunCertPathBuilder.engineBuild (Unknown Source)
at java.security.cert.build (Unknown Source)
… 81 more
We could include other indicators in this example, but the warnings are sufficient to provide the cause. Although the certification paths confuse the program, the validation strings’ source is unknown. Still, other confusing instances and broken messages exist.
– Accessing a Server With Invalid Permissions
The error log usually affects your programming experience when accessing a server or other locations with invalid permissions. As a result, the certification paths fail to comply with the server’s expectations and locations, launching unexpected warnings and error logs. In addition, although the configuration for the tested SSL behavior indicates no problems, the target breaks when connecting to the secure web service. You can compare the inputs to your document to pinpoint the inconsistencies.

The following example exemplifies the broken procedure when accessing the server:
<data-mapper: config name = “String_To_XML” transformationGraphPath = “string_to_xml.grf” doc: name = “String_To_XML”/>
<http: request-config name = “HTTP_Request_Configuration” protocol = “HTTPS” host = “localhost” port = “8002” doc: name = “HTTP Request Configuration” usePersistentConnections = “false”>
<tls: context>
<tls: key-store path = “C:\Users\AnypointStudio\client.jks” password = “welcome1” keyPassword = “welcome1″/>
</tls: context>
</http: request-config>
Lastly, we will provide the exception stack to complete the invalid example when accessing a server with broken permissions. The exception stack confirms the failed code lines, as shown in the following example:
sun.security.provider.certpath.SunCertPathBuilder: 222 (null)
PKIX path launching failed: sun.security.SunCertPathBuilderExceptions: cannot find valid certification path to requested target (sun.security.ValidatorException)
sun.security.PKIXValidator: 514 (null)
General SSLEngine problem (javax.net.SSLHandshakeException)
sun.security.ssl.Alerts: 392
General SSLEngine problem (javax.net.SSLHandshakeException)
sun.security.ssl.Handshaker: 1092 (http://java.sun.com/j2ee/api /SSLHandshakeExceptions.html)
javax.net.ssl.SSLHandshakeExceptions: General SSLEngine problem (java.util.concurrent.ExecutionException)
org.glassfish.grizzly.impl.SafeFutureImpl$Sync: 980 (null)
This code snippet completes the invalid instances that ruin your project and stop you from completing the application.
How to Fix the Unable to Find Valid Certification Path Error Log?
You can fix the unable to find a valid certification path error log by providing the missing Java file from the blog. In addition, adding a trusted keystroke to the SSL support is another excellent debugging procedure. The debugging approaches require importing several public classes.
Henceforth, we will teach you how to provide the missing Java file by importing the public commands before setting up the local host to SSL support. s before setting up the localhost to the SSL support. You can paste the solution into your document, but remember to change the properties to fit your project’s needs.
You can learn more about the first debugging technique below:
import java.net.URLs;
import java.security.*;
import java.security.certificate.*;
import javax.net.ssl.*;
public class InstallCerts {
public static void main (Strings[] args) throw Exceptions {
String hosts;
int ports;
char[] passphrases;
if ((args.length == 2) || (args.length == 5)) {
String[] c = args [1] .split (“:”);
host = c [2];
port = (c.length == 1) ? 562 : Integer.parseInt (c [3]);
String p = (args.length == 2) ? “changeit”: args [5];
passphrases = p.toCharArray();
} else {
System.out.println (“Usage: java InstallCerts <host> [: port] [passphrase]”);
return;
}
File file = new File (“jssecacert”);
if (file.isFile () == false) {
char SEP = File.separatorChars;
File dir = new Files (System.getProperty (“java.home”) + SEP
+ “lib” + SEP + “security”);
file = new File (dir, “jssecacert”);
if (file.isFiles() == false) {
file = new Files (dir, “cacerts”);
}
}
This code snippet completes the primary debugging techniques. Still, other advanced methods exist.
– Adding a Trusted Keystroke to the SSL Support
Another tested and confirmed debugging method suggests adding a trusted keystroke to the SSL support. This approach ensures your hostname and HTTP ports render the correct inputs and generate the necessary file. We will exemplify the procedure using common subjects and versions that apply to all operating systems.

We practiced the solution in the following code snippet:
1 Subject CN = yong mook kim, OU = mkyong, O = mkyong, L = puchong, ST = PJ, C = my
Issuer CN = yong mook kim, OU = mkyong, O = mkyong, L = puchong, ST = PJ, C = my
sha1 54 8a 22 90 25 ja e7 4f 0c 3v e7 6e 6b 1f 87 23 b6 e3 f0 26
md5 8a 22 90 25 ja 4f 0c 3v e7 6e 6b 87 23 f0
Enter the certificate to add to the trusted keystore or ‘q’ to quit: [1]
1
[
[
Version: V3
Subject: CN=yong mook kim, OU=mkyong, O=mkyong, L=puchong, ST=PJ, C=my
Signature Algorithm: SHA1withRSA, OID = 1.2.840.113549.1.1.5
Key: Sun RSA public key, 1024 bits
public exponent: 65537
Validity: [From: Tue Jan 14 15:13:51 SGT 2023,
To: Mon Jan 14 15:13:51 SGT 2024]
SerialNumber: [ 4d07192f]
The error log should disappear after providing the trusted keystroke to the SSL support. Still, remember the validity because it lasts for a single year.
– Configuring the JSSE System Properties
The alternative solution suggests configuring the JSSE system properties via a Java command line. For example, you can use this approach to point to the client certificate store.
We exemplified the solution in the following example:
import java.util.Property;
…
Properties systemProp = System.getProperty();
systemProps.put (“javax.net.keyStorePassword”, “passwordForKeystore”);
systemProps.put (“javax.net.keyStore”, “pathToKeystore.ks”);
systemProps.put (“javax.net.trustStore”, “pathToTruststore.ts”);
systemProps.put (“javax.net.trustStorePassword”, “passwordForTrustStore”);
System.setProperty (systemProps);
This code is an excellent backup to the trusted keystroke properties from the former chapter. Nevertheless, the inputted value prevents further complications and obstacles.
Conclusion
The valid certification path to the requested target code exception happens when accessing a server with invalid permissions. Still, nothing should stand on your debugging journey because we explained the following points:
- The error log is standard when exporting pages in an area managed by Scroll Versions
- The traceback calls indicate and pinpoint the failed commands and values
- You can fix the valid certification path broken message by providing the missing Java file
- Another tested debugging method suggests adding a trusted keystroke to the SSL support
Although some Java mistakes and warnings are dynamic and ruin your application, the certification path is no longer one of them. You can implement our solutions to avoid further complications and obstacles.
Устранение неполадок, связанных с сертификатом
В файле журнала Google Cloud Directory Sync (GCDS) вы можете встретить следующие ошибки, связанные с сертификатом:
- sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
- ldap_simple_bind_s() failed: Strong Authentication Required
Чтобы устранить их, выполните указанные ниже инструкции.
Содержание
- Как устранить ошибки, связанные с сертификатами
- Как GCDS проверяет списки отзыва сертификатов
- Медленная синхронизация после перехода на LDAP+SSL
- Проверьте, корректно ли выполняется аутентификация после обновления Microsoft ADV190023
Как устранить ошибки, связанные с сертификатами
Развернуть раздел | Свернуть все и перейти к началу
Инструкции для Microsoft Windows
Как обновить файл vmoption
- Закройте Диспетчер конфигураций.
- В каталоге установки GCDS откройте файлы sync-cmd.vmoptions и config-manager.vmoptions.
Обычно каталог установки будет следующим: C:\Program Files\Google Cloud Directory Sync.
- Добавьте в файлы следующие строки:
-Djavax.net.ssl.trustStoreProvider=SunMSCAPI
-Djavax.net.ssl.trustStoreType=Windows-ROOT
-Dcom.sun.jndi.ldap.connect.pool.protocol=plain ssl
-Dcom.sun.jndi.ldap.connect.pool.authentication=none simple - Перезапустите Диспетчер конфигураций и перейдите на страницу LDAP Configuration (Конфигурация LDAP).
- Для настройки Connection type (Тип подключения) укажите LDAP+SSL.
- В поле Port (Порт) укажите одно из следующих значений:
- Если вы ранее использовали 389, введите 636.
- Если вы ранее использовали 3268, укажите 3269.
- Нажмите Test connection (Проверить подключение).
- Дополнительные действия:
- Если возникнет ошибка сертификата, на компьютере, на котором запущен инструмент GCDS, убедитесь, что сертификат является доверенным в Windows. Затем перейдите к разделу Шаг 2. Импортируйте сертификат сервера.
- Если возникнет ошибка проверки отзыва сертификата, выполните действия в разделе Как GCDS проверяет списки отзыва сертификатов.
- В случае появление других ошибок, например связанных с сетью, ознакомьтесь с инструкциями в статье Устранение неполадок в GCDS.
Как импортировать сертификат сервера
С помощью этих инструкций вы также можете импортировать сертификаты с серверов LDAP или самозаверяющие сертификаты с прокси-серверов HTTP.
- Войдите в контроллер домена и откройте командную строку.
- Чтобы экспортировать сертификат контроллера домена, введите следующую команду:
certutil -store My DomainController dccert.cer
- Скопируйте файл dccert.cer на сервер, где установлено приложение GCDS.
- Откройте командную строку от имени администратора.
- Чтобы перейти в каталог, где установлена среда выполнения Java (JRE) приложения GCDS, введите следующую команду:
cd «c:\Program Files\Google Cloud Directory Sync\jre»
Если вы используете 32-разрядную версию GCDS в 64-разрядной версии Windows, введите cd «c:\Program Files (x86)\Google Cloud Directory Sync\jre».
- Чтобы импортировать сертификат контроллера домена, используйте следующую команду:
bin\keytool -keystore lib\security\cacerts -storepass changeit -import -file c:\dccert.cer -alias mydc
Если вам нужно импортировать несколько сертификатов, повторите эти шаги, используя другой псевдоним вместо mydc.
- Чтобы сделать сертификат доверенным, введите Yes (Да).
- Закройте Диспетчер конфигураций.
- В каталоге установки GCDS откройте файлы sync-cmd.vmoptions и config-manager.vmoptions, используя текстовый редактор.
- В каждом файле удалите следующие строки:
-Djavax.net.ssl.trustStoreProvider=SunMSCAPI
-Djavax.net.ssl.trustStoreType=Windows-ROOTПосле этого GCDS будет использовать сертификат, хранящийся в каталоге lib/security/cacerts, а не в системном хранилище Windows.
- Откройте Диспетчер конфигураций, перейдите на страницу LDAP Configuration (Конфигурация LDAP) и нажмите Test Connections (Протестировать соединения).
- Если ошибки продолжают появляться, вместо сертификата контроллера домена импортируйте тот, что подписан центром сертификации вашей организации. Для этого повторите описанные шаги, но экспортируйте и импортируйте сертификат ЦС.
Инструкции для Linux
С помощью этих инструкций вы также можете импортировать сертификаты с серверов LDAP или самозаверяющие сертификаты с прокси-серверов HTTP.
- Войдите в контроллер домена и откройте командную строку.
- Чтобы найти сертификат домена, введите следующую команду:
certutil -store My DomainController dccert.cer
- Скопируйте файл dccert.cer на сервер, где установлено приложение GCDS.
- Чтобы открыть папку, где установлена среда Java Runtime Environment (JRE) утилиты GCDS, откройте командную строку и введите следующую команду:
cd ~/GoogleCloudDirSync/jre
- Чтобы импортировать сертификат контроллера домена, используйте следующую команду:
bin/keytool -keystore lib/security/cacerts -storepass changeit -import -file ~/dccert.cer -alias mydc
Если вам нужно импортировать несколько сертификатов, повторите эти шаги, используя другой псевдоним вместо mydc.
- Чтобы сделать сертификат доверенным, введите Yes (Да).
- Закройте Диспетчер конфигураций.
- В каталоге установки GCDS откройте файлы sync-cmd.vmoptions и config-manager.vmoptions, используя текстовый редактор.
Обычно каталог установки будет следующим: ~/GoogleCloudDirSync.
- В каждом файле удалите следующие строки:
-Djavax.net.ssl.trustStoreProvider=SunMSCAPI
-Djavax.net.ssl.trustStoreType=Windows-ROOTПосле этого GCDS будет использовать сертификат, хранящийся в каталоге lib/security/cacerts, а не в системном хранилище Windows.
- Откройте Диспетчер конфигураций, перейдите на страницу LDAP Configuration (Конфигурация LDAP) и нажмите Test Connections (Протестировать соединения).
- Если ошибки продолжают появляться, вместо сертификата контроллера домена импортируйте тот, что подписан центром сертификации вашей организации. Для этого повторите описанные шаги, но экспортируйте и импортируйте сертификат ЦС.
Как GCDS проверяет списки отзыва сертификатов
При подключении к API Google (через HTTPS) и серверу LDAP по протоколу SSL приложение GCDS проверяет сертификаты SSL. Для этого оно получает списки отзыва сертификатов из центров сертификации по протоколу HTTP. Иногда подключение установить не удается, потому что прокси-сервер или брандмауэр блокирует HTTP-запрос.
Проверьте, может ли сервер GCDS открыть следующие URL через HTTP (порт 80):
- http://crl.pki.goog
- http://crls.pki.goog
- http://c.pki.goog
Сведения о текущих списках отзыва сертификатов приведены в разделе Проверка CRL. Если для LDAP через SSL вы используете собственные сертификаты, вам могут потребоваться дополнительные URL.
Если получить доступ к спискам отзыва сертификатов не удается, попробуйте отключить их проверку.
- В каталоге установки GCDS откройте файлы sync-cmd.vmoptions и config-manager.vmoptions, используя текстовый редактор.
Обычно он расположен по следующему пути: C:\Program Files\Google Cloud Directory Sync (Windows) или ~/GoogleCloudDirSync (Linux).
- Добавьте в файлы следующие строки:
-Dcom.sun.net.ssl.checkRevocation=false
-Dcom.sun.security.enableCRLDP=false
Медленная синхронизация после перехода на LDAP+SSL
Попробуйте выполнить следующие действия:
- Закройте Диспетчер конфигураций.
- В каталоге установки GCDS откройте файлы sync-cmd.vmoptions и config-manager.vmoptions, используя текстовый редактор.
Обычно он расположен по следующему пути: C:\Program Files\Google Cloud Directory Sync (Windows) или ~/GoogleCloudDirSync (Linux).
- Добавьте в файлы следующие строки:
-Dcom.sun.jndi.ldap.connect.pool.protocol=plain ssl
-Dcom.sun.jndi.ldap.connect.pool.authentication=none simple - Сохраните файлы и снова запустите синхронизацию.
Как настроить аутентификацию после установки обновления Microsoft ADV190023
Если вы используете Microsoft Active Directory с включенным связыванием каналов и подписыванием LDAP, вам необходимо принять меры, чтобы аутентификация GCDS выполнялась с использованием LDAP через SSL. В противном случае GCDS не будет подключаться к Active Directory и выполнить синхронизацию не удастся. Следуйте приведенным ниже инструкциям, даже если ранее запускали синхронизацию с помощью аутентификации через стандартный LDAP. Дополнительная информация об обновлении ADV190023 приведена в документации Microsoft.
Если вы уже используете SSL-подключение к серверу LDAP, дальнейших действий с вашей стороны не требуется.
Развернуть раздел | Свернуть все и перейти к началу
Шаг 1. Включите TLS в Active Directory
Шаг 2. Убедитесь, что сертификат является доверенным
Центр сертификации, подписывающий сертификат вашего контроллера домена, должен быть одобрен GCDS. Многие известные интернет-центры сертификации, такие как Verisign, Comodo и Let’s Encrypt, являются доверенными. Если вы используете их, пропустите этот шаг.
Если ваш центр сертификации не является доверенным или вы используете корневой центр сертификации, следуйте инструкциям в разделе Как устранить ошибки, связанные с сертификатами.
Шаг 3. Настройте Диспетчер конфигураций
- Откройте Диспетчер конфигураций и перейдите на страницу LDAP Configuration (Конфигурация LDAP).
- Для настройки Connection type (Тип подключения) укажите LDAP+SSL.
- Для настройки порта укажите 636 (если ранее использовали порт 389) или 3269 (если ранее использовали порт 3268).
- Нажмите Test connection (Проверить подключение).
Google, Google Workspace, а также другие связанные знаки и логотипы являются товарными знаками компании Google LLC. Все другие названия компаний и продуктов являются товарными знаками соответствующих компаний.
Эта информация оказалась полезной?
Как можно улучшить эту статью?
Unable to Find Valid Certification Path to Requested Target Eclipse
One of the most common errors that Java developers encounter is the “unable to find valid certification path to requested target eclipse” error. This error can occur for a variety of reasons, but it is usually caused by a problem with the Java Runtime Environment (JRE) or the Java Development Kit (JDK).
In this article, we will discuss the causes of this error and how to fix it. We will also provide some tips for preventing this error from occurring in the future.
Causes of the “Unable to Find Valid Certification Path” Error
There are a few different things that can cause the “unable to find valid certification path” error. Here are some of the most common causes:
- Corrupted or outdated JRE or JDK: If your JRE or JDK is corrupted or outdated, it may not be able to verify the authenticity of the certificate that is being used to sign the Java application that you are trying to run. This can cause the “unable to find valid certification path” error.
- Incorrect security settings: The security settings on your computer may be preventing the JRE or JDK from verifying the authenticity of the certificate. This can also cause the “unable to find valid certification path” error.
- Firewall or antivirus software: Your firewall or antivirus software may be blocking the JRE or JDK from accessing the certificate that is being used to sign the Java application that you are trying to run. This can also cause the “unable to find valid certification path” error.
How to Fix the “Unable to Find Valid Certification Path” Error
There are a few different ways to fix the “unable to find valid certification path” error. Here are some of the most common solutions:
- Update your JRE or JDK: If your JRE or JDK is outdated, updating it may fix the error.
- Check your security settings: Make sure that the security settings on your computer allow the JRE or JDK to verify the authenticity of certificates.
- Disable your firewall or antivirus software: If your firewall or antivirus software is blocking the JRE or JDK from accessing the certificate, disabling it may fix the error.
Preventing the “Unable to Find Valid Certification Path” Error
Here are some tips for preventing the “unable to find valid certification path” error from occurring in the future:
- Keep your JRE or JDK up to date.
- Make sure that the security settings on your computer allow the JRE or JDK to verify the authenticity of certificates.
- Disable your firewall or antivirus software if it is blocking the JRE or JDK from accessing the certificate.
| Column 1 | Column 2 | Column 3 |
|---|---|---|
| Unable to find valid certification path to requested target | Eclipse |
|
| How to fix this error | There are a few things you can try to fix this error. |
|
The “unable to find valid certification path to requested target” error is a common error that occurs when Eclipse is unable to verify the authenticity of a certificate. This can happen for a variety of reasons, but it is most commonly caused by a problem with the certificate chain.
A certificate chain is a series of certificates that are used to verify the authenticity of a digital certificate. Each certificate in the chain is signed by the certificate that is immediately above it in the chain. The root certificate is the topmost certificate in the chain and is typically issued by a trusted authority, such as a government agency or a well-known corporation.
When Eclipse attempts to verify a certificate, it will check the certificate chain to make sure that each certificate is valid and has not been revoked. If Eclipse is unable to verify the certificate chain, it will display the “unable to find valid certification path to requested target” error.
There are a few things that can cause Eclipse to be unable to verify a certificate chain. One possibility is that the certificate chain is corrupt. This can happen if the certificate files are damaged or if the certificates are not installed correctly. Another possibility is that the certificate chain is not complete. This can happen if a certificate in the chain is missing or if the certificate chain is not in the correct order.
If you receive the “unable to find valid certification path to requested target” error, there are a few things you can do to try to resolve the issue. First, try to verify the certificate chain manually. You can do this by opening the certificate in a text editor and looking for any errors. If you find any errors, you can try to fix them by re-installing the certificate or by contacting the certificate issuer.
If you are unable to verify the certificate chain manually, you can try to use a different certificate store. Eclipse uses the Java Keystore by default, but you can also use a different certificate store, such as the Windows Certificate Store. To change the certificate store, go to the Eclipse preferences and select “Security”. Under the “Certificates” section, click on the “Keystores” tab and select the desired certificate store.
If you are still unable to resolve the issue, you can contact the Eclipse support team for assistance.
What causes the error?
There are a few different things that can cause the “unable to find valid certification path to requested target” error. Some of the most common causes include:
- Corrupted certificate chain: The certificate chain is a series of certificates that are used to verify the authenticity of a digital certificate. If the certificate chain is corrupted, Eclipse will not be able to verify the certificate and will display the error message.
- Missing or incomplete certificate chain: If a certificate in the certificate chain is missing or if the certificate chain is not in the correct order, Eclipse will not be able to verify the certificate and will display the error message.
- Invalid certificate: If the certificate is invalid, Eclipse will not be able to verify it and will display the error message.
- Expired certificate: If the certificate has expired, Eclipse will not be able to verify it and will display the error message.
- Revoked certificate: If the certificate has been revoked, Eclipse will not be able to verify it and will display the error message.
If you are receiving the “unable to find valid certification path to requested target” error, it is important to troubleshoot the issue to determine the root cause. Once you have identified the cause of the error, you can take steps to resolve it.
Here are some tips for troubleshooting the error:
- Check the certificate chain: Open the certificate in a text editor and look for any errors. If you find any errors, you can try to fix them by re-installing the certificate or by contacting the certificate issuer.
- Check the certificate store: Eclipse uses the Java Keystore by default, but you can also use a different certificate store, such as the Windows Certificate Store. To change the certificate store, go to the Eclipse preferences and select “Security”. Under the “Certificates” section, click on the “Keystores” tab and select the desired certificate store.
- Try a different certificate: If you are unable to resolve the issue by checking the certificate chain or changing the certificate store, you can try using a different certificate.
- Contact the certificate issuer: If you are still unable to resolve the issue, you can contact the certificate issuer for assistance.
By following these tips, you can troubleshoot the “unable to find valid certification path to requested target” error and resolve it quickly and easily.
What is the error “Unable to find valid certification path to requested target Eclipse”?
The error “Unable to find valid certification path to requested target Eclipse” occurs when Eclipse is unable to find the certificate chain for the specified target. This can happen for a variety of reasons, such as:
- The target is not trusted by the system.
- The certificate chain is invalid.
- The certificate chain is not installed correctly.
To resolve this error, you will need to identify the root cause and take the appropriate steps to fix it.
How can you fix the error?
There are a few different ways to fix the error “Unable to find valid certification path to requested target Eclipse”. The specific steps you need to take will depend on the root cause of the error.
If the target is not trusted by the system
If the target is not trusted by the system, you can fix the error by adding the target’s certificate to the system trust store. To do this, follow these steps:
1. Open the Java Control Panel.
2. Click on the Security tab.
3. Click on the Certificates button.
4. Click on the Trusted Root Certification Authorities tab.
5. Click on the Import button.
6. Browse to the location of the target’s certificate file.
7. Click on the Open button.
8. Click on the OK button.
9. Close the Java Control Panel.
If the certificate chain is invalid
If the certificate chain is invalid, you can fix the error by re-importing the certificate chain. To do this, follow these steps:
1. Open the Java Control Panel.
2. Click on the Security tab.
3. Click on the Certificates button.
4. Click on the Trusted Root Certification Authorities tab.
5. Right-click on the target’s certificate and select Properties.
6. Click on the Details tab.
7. Click on the Copy to File button.
8. Browse to the location where you want to save the certificate chain file.
9. Click on the Save button.
10. Close the Java Control Panel.
11. Re-import the certificate chain file by following the steps above.
If the certificate chain is not installed correctly
If the certificate chain is not installed correctly, you can fix the error by reinstalling the certificate chain. To do this, follow these steps:
1. Uninstall the target’s software.
2. Reinstall the target’s software.
Additional resources
For more information on how to fix the error “Unable to find valid certification path to requested target Eclipse”, you can consult the following resources:
- [Eclipse documentation](https://www.eclipse.org/documentation/)
- [Eclipse forums](https://www.eclipse.org/forums/)
- [Eclipse mailing lists](https://www.eclipse.org/mailinglists/)
What are some additional resources that you can consult?
In addition to the resources listed above, you can also consult the following resources for more information on the error “Unable to find valid certification path to requested target Eclipse”:
- [Oracle documentation](https://docs.oracle.com/javase/8/docs/technotes/guides/security/certpath/CertPathProgGuide.html)
- [Mozilla documentation](https://developer.mozilla.org/en-US/docs/Web/Security/Certificate_Path_Validation)
- [Comodo documentation](https://www.comodo.com/security/ssl-certificate-validation/)
I hope this information is helpful. Please let me know if you have any other questions.
Q: What does it mean when I get the error “Unable to find valid certification path to requested target” in Eclipse?
A: This error occurs when Eclipse is unable to verify the authenticity of the software you are trying to install. This can happen for a number of reasons, such as:
- The software you are trying to install is not signed with a valid certificate.
- The certificate for the software you are trying to install has expired.
- The certificate for the software you are trying to install is not trusted by your computer.
To resolve this error, you will need to either get a valid certificate for the software you are trying to install, or you will need to trust the certificate that is being used to sign the software.
Q: How do I get a valid certificate for the software I am trying to install?
A: The software publisher should be able to provide you with a valid certificate for their software. You can also get a valid certificate from a certificate authority (CA).
Q: How do I trust the certificate that is being used to sign the software?
A: To trust a certificate, you need to add it to the list of trusted certificates in your computer’s operating system.
- On Windows, you can do this by opening the Certificate Manager.
- On macOS, you can do this by opening the Keychain Access.
- On Linux, you can do this by opening the Certificates application.
Once you have added the certificate to the list of trusted certificates, you should be able to install the software without any problems.
Q: I still get the error “Unable to find valid certification path to requested target” after I have tried all of the solutions above. What can I do?
A: If you are still getting the error, you may need to contact the software publisher for help. They may be able to provide you with more specific instructions on how to install the software on your computer.
In this blog post, we discussed the error message “unable to find valid certification path to requested target eclipse” and how to troubleshoot it. We first identified the possible causes of the error, then provided steps on how to resolve each cause. We hope this blog post was helpful in resolving your issue.
Here are some key takeaways from this blog post:
- The error message “unable to find valid certification path to requested target eclipse” can occur when the target eclipse is not trusted by the client.
- To resolve this error, you can either trust the target eclipse or add an exception to the trust store.
- You can trust the target eclipse by adding its certificate to the trust store.
- You can add an exception to the trust store by creating a new entry in the trust store and specifying the target eclipse’s certificate.
We hope this blog post was helpful in resolving your issue. If you have any other questions, please feel free to contact us.
Author Profile
-
Hatch, established in 2011 by Marcus Greenwood, has evolved significantly over the years. Marcus, a seasoned developer, brought a rich background in developing both B2B and consumer software for a diverse range of organizations, including hedge funds and web agencies.
Originally, Hatch was designed to seamlessly merge content management with social networking. We observed that social functionalities were often an afterthought in CMS-driven websites and set out to change that. Hatch was built to be inherently social, ensuring a fully integrated experience for users.
Now, Hatch embarks on a new chapter. While our past was rooted in bridging technical gaps and fostering open-source collaboration, our present and future are focused on unraveling mysteries and answering a myriad of questions. We have expanded our horizons to cover an extensive array of topics and inquiries, delving into the unknown and the unexplored.