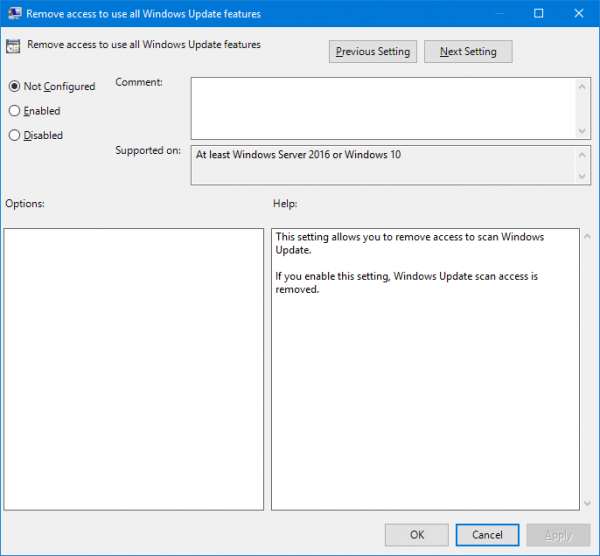
This policy setting allows you to remove access to Windows Update.If you enable this policy setting all Windows Update features are removed. This includes blocking access to the Windows Update website at http://windowsupdate.microsoft.com from the Windows Update hyperlink on the Start menu and also on the Tools menu in Internet Explorer. Windows automatic updating is also disabled; you will neither be notified about nor will you receive critical updates from Windows Update. This policy setting also prevents Device Manager from automatically installing driver updates from the Windows Update website.If you disable or do not configure this policy setting users can access the Windows Update website and enable automatic updating to receive notifications and critical updates from Windows Update.
Policy path:
System\Internet Communication Management\Internet Communication settings
Scope:
Supported on:
At least Windows Server 2003 operating systems Windows XP Professional Service Pack 1 or Windows 2000 Service Pack 3
Registry settings:
HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate!DisableWindowsUpdateAccess
Filename:
Related content
If you are running Microsoft Windows in a domain environment with WSUS configured, you may notice that you’re not able to install some FODs (Features on Demand), or use the “Turn Windows features on or off”. This will stop you from installing things like the RSAT tools, .NET Framework, Language Speech packs, etc…
You may see “failure to download files”, “cannot download”, or errors like “0x800F0954” when running DISM to install packages.
To resolve this, you need to modify your domain’s group policy settings to allow your workstations to query Windows Update servers for additional content. The workstations will still use your WSUS server for approvals, downloads, and updates, however in the event content is not found, it will query Windows Update.
Enable download of “Optional features” directly from Windows Update
- Open the group policy editor on your domain
- Create a new GPO, or modify an existing one. Make sure it applies to the computers you’d like
- Navigate to “Computer Configuration”, “Policies”, “Administrative Templates”, and then “System”.
- Double click or open “Specify settings for optional component installation and component repair”
- Make sure “Never attempt to download payload from Windows Update” is NOT checked
- Make sure “Download repair content and optional features directly from Windows Update instead of Windows Server Update Services (WSUS)” IS checked.
- Wait for your GPO to update, or run “gpupdate /force” on the workstations.
Please see an example of the configuration below:
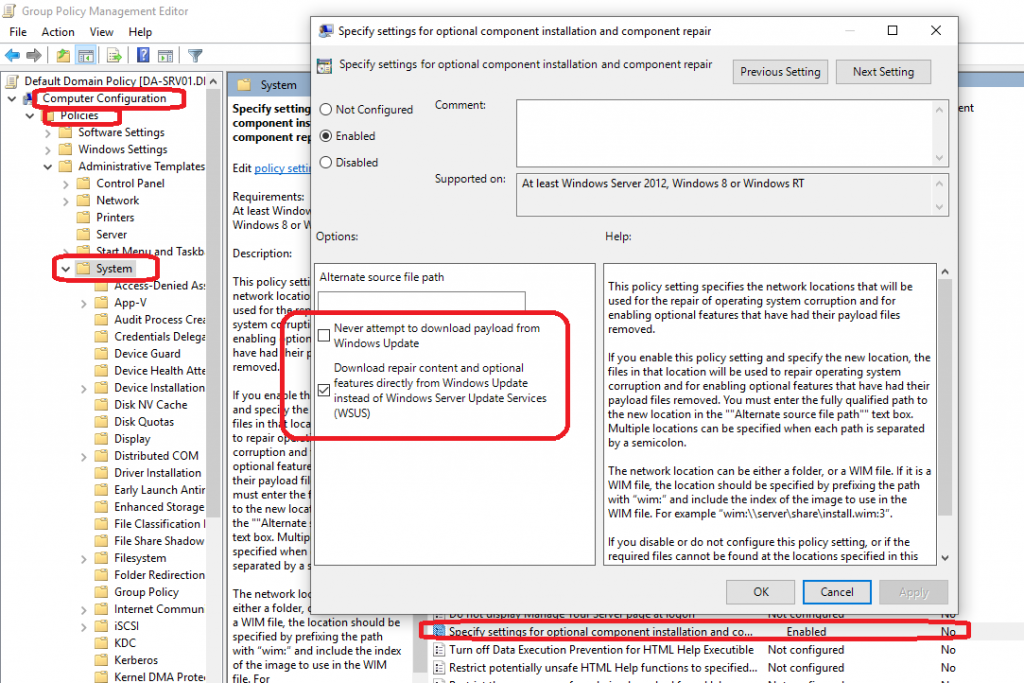
Download repair content and optional features directly from Windows Update instead of Windows Server Update Services (WSUS)
You should now be able to download/install RSAT, .NET, Speech language packs, and more!
Skip to content
Again, Microsoft has silently updated available Group Policies in Windows 10. Earlier, the Redmond giant was removing a number of policies from Windows 10 Anniversay Update. With the recently released Windows 10 build 14931, Microsoft has added a new policy setting to the operating system related to Windows Update.
The new policy is called Remove access to all Windows Update features and is located under Computer Configuration -> Administrative Templates -> Windows Components -> Windows Update.
To try out it in action, you need to do the following.
- Press Win + R keys together on your keyboard and type:
gpedit.msc
Press Enter.
- Group Policy Editor will open. Go to Local Computer Policy -> Computer Configuration -> Administrative Templates -> Windows Components -> Windows Update.
- There, double click and enable the option Remove access to all Windows Update features.
- Restart Windows 10.
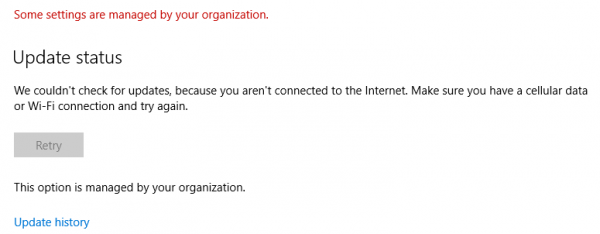
Once enabled, the policy prevents users from manually searching for updates, as shown below.
So, you can use it to apply additional restrictions to your PC or workstation. As of this writing, Windows 10 build 14931 is available for Fast Ring insiders. You can get more details about this build from the following articles:
- Download MUI language packs for Windows 10 build 14931 – direct links
- Windows 10 build 14931 is out for Fast Ring insiders
Thanks to Inside Windows for this finding.
Support us
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:
If you like this article, please share it using the buttons below. It won’t take a lot from you, but it will help us grow. Thanks for your support!
This article explains how you can disable Check for Updates using Group Policy. To prevent users from manually downloading updates from Microsoft, you can disable the check for updates button.
Most organizations today use Configuration Manager to deploy software updates to computers. Why? Because SCCM makes it easy to deploy and manage the updates.
With Configuration Manager deploying the software updates, you ensure the client computers are patched with the latest updates.

The software update point (SUP) interacts with the WSUS services to configure the software update settings and to request synchronization of software updates metadata.
If you have set up a standalone WSUS server to deploy Windows Updates to your computers, you ensure only the approved updates are deployed to all computers.
When you are using ConfigMgr/WSUS to manage updates, you basically have a complete control over the updates that you deploy. You don’t want users to manually check updates from Microsoft update and install it.
If you are allowing users to check for updates from Microsoft update, any user can download the updates and install. You don’t want users to download unwanted updates and cause issues with the laptop.
And when WSUS or SCCM attempts to deploy the latest updates, it would detect the client computer already has the updates installed.
Why should you disable Check for Updates?
Here are some reasons why you should prevent domain users from using Check for Updates option in Windows.
- A user can manually go to Start > Settings > Windows Update and run check for updates. This option should be disabled on domain computers because a user can manually download unapproved updates. Since these updates aren’t tested by admins, it may affect the stability of the computer.
- When a user manually downloads and installs the updates from Microsoft update, an operating system upgrade could occur. This has been the case in several organizations where an OS upgrade occurred just because the user wanted newer version of operating system. After the upgrade, some applications may not work properly and some settings may change. Overall, it’s a big challenge for system admins to roll back the operating system. To prevent such things, you can restrict users checking updates from Microsoft.
- Allowing users to manually check for updates from Microsoft update defeats the purpose of having WSUS, Configuration Manager in the setup. When you have invested money in a tool that deploys updates to your domain computers, it’s of no use when users download the updates directly from Microsoft update.
The below screenshot is from a computer that is just joined to the AD domain and managed by Configuration Manager.
Notice that check for updates button is active and enabled. In addition, there is a cumulative update available for installation.
If the user clicks download and install, the quality update will download from Microsoft update and install on the computer.
The user may think that the computer requires that optional update whereas it clearly states that it’s an optional quality update.
Now, do you see a reason why you must disable check for updates on domain computers?

Therefore, in most organizations, a group policy is deployed to the client computers to disable check online for updates from Microsoft update site.
Thankfully, with “Remove access to use all Windows Update features” GPO setting, administrators can disable the “Check for updates” option for users.
The group policy setting essentially blocks the access to Windows update. If you enable this policy setting, user access to Windows Update scan, download and install is removed.
Any background update scans, downloads and installations will continue to work as configured.
How To Disable Check for Updates using Group Policy
The best way to disable check for updates on computers is by using group policy (GPO). Group Policy can be used to apply security settings to users and computers.
The Group Policy allows administrators to define security policies for users and for computers. The GPO is a vast topic, and you can start learning about Group Policy from Microsoft Documentation.
When you create a group policy, you either deploy it to the entire AD domain or select Organizational Units. Whenever you create a new GPO, ensure you test it on pilot computers and then deploy it to wider set of computers.
Let’s create a new group policy disable check for updates from Microsoft Update. Launch the Server Manager and click Tools > Group Policy Management console.
In the Group Policy Management console, expand the domain and right-click Group Policy Objects and select New.
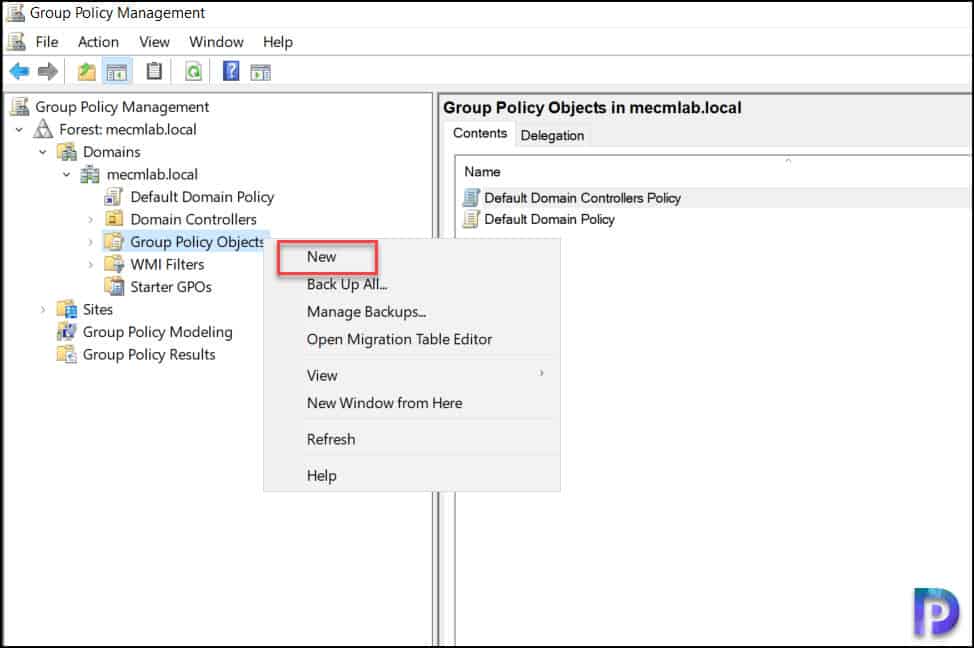
Specify the GPO name as “Disable Check for Updates from Microsoft Update” or something similar. Click OK.

After you create the GPO, right click the GPO and select Edit. Edit the GPO and specify the settings to disable check for updates.

In the Group Policy Object Editor, expand Computer Configuration > Administrative Templates > Windows Components > Windows Update.
In the right pane, from the list of settings, right click the setting Remove access to use all Windows Update features and select Edit.

The GPO setting Remove access to use all Windows Update features removes access to scan for Windows Updates. The check for updates from Microsoft update button will be disabled.

Group Policy Result – Check for Updates Disabled
After you apply the above group policy, run the command gpupdate /force on the client machines.
Read: How to Modify Group Policy Refresh Interval for Windows computers.
On the Windows 10 computer, click Start > Settings > Windows Update. Notice that Check for updates button is now disabled. The option to check online for updates from Microsoft update is also gone.
Instead, you see This option is managed by your organization.

Let’s check if the check for updates button is disabled for Windows 11 computer. On the Windows 11 computer, click Start > Settings > Windows Update. Yes, the check for updates button is disabled. The option to check online for updates from Microsoft update is not available.

Still Need Help?
If you need further assistance on the above article or want to discuss other technical issues, check out some of these options.
If you are already managing your Windows 10 systems (currently 1607 and below) with System Center Configuration Manager, then chances are you might want to prevent certain users from also being able to “Check online for updates from Microsoft Update.” before you have had a chance to fully test the latest cumulative update or feature update. Unfortunately, when users go into Settings > Update & security they will see a Check for updates button and below that, a Check online for updates from Microsoft Update link.
By clicking that link, it will bypass System Center Configuration Manager and go directly to Microsoft Update to see what the latest updates are available and start installing them once they download. One way that you can prevent this from happing is to enable the Group Policy setting: Do not connect to any Windows Update Internet locations:
If you enable this setting, you will not only disable the ability to check online for updates from Microsoft Update, but you will also disable the ability to install software from the Windows Store. Now if you have not started using the Windows Store yet, then this might not be a problem. Also, this policy is only effective if the Specify intranet Microsoft update service location policy is set (which it should be if you are using System Center Configuration Manager for Software Updates):
Once enabled, the Check online for updates from Microsoft Update link will disappear:
Hopefully we will see an option in the future that will allow for the ability to disable this link without disabling the ability to install apps from the Windows Store.
Originally posted on https://miketerrill.net/