What is Trojan:Win32/Tiggre!rfn ? Trojan:Win32/Tiggre!rfn is a malicious software. It can change Windows OS and browsers settings, download and install other malware, adware and PUPs. Moreover, this trojan can give a remote malicious hacker access to your computer and use your computer’s resources to generate crypto money. It will make your PC run very slow. On current date, the Trojan:Win32/Tiggre!rfn virus continues to increase the number of personal computers which have been infected.
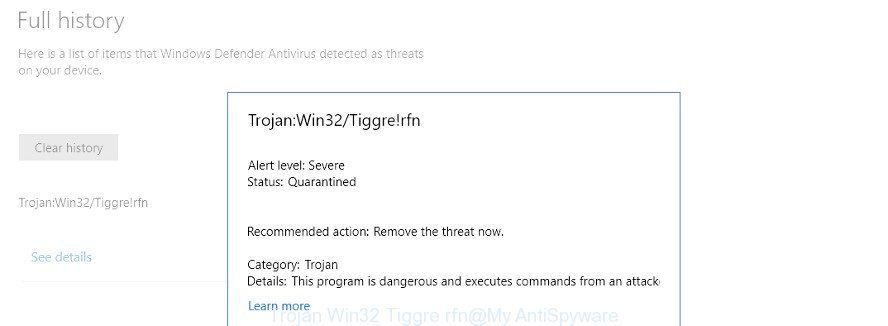
Windows Defender detects Trojan:Win32/Tiggre!rfn security threat
What is more, the Trojan:Win32/Tiggre!rfn can steal your privacy data such as: your ip address, what is a webpage you are viewing now, what you are looking for on the World Wide Web, which links you are clicking, and much, much more. Even worse, the trojan may monetize its functionality by collecting confidential information from your browsing sessions. This confidential information, afterwards, can be easily used for marketing purposes. This puts your personal information at a security risk.
The Trojan:Win32/Tiggre!rfn malware is automatically installed, without notification or user consent. Therefore, many users aren’t even aware that their machine has been infected by malicious software. Please follow the easy rules in order to protect your PC from any malicious software: don’t install suspicious programs, read the user agreement and choose only the Custom, Manual or Advanced installation option, don’t rush to press the Next button. Also, always try to find a review of the application on the Web. Be careful and attentive!
If Trojan:Win32/Tiggre!rfn has already come into your system, then you need to scan your computer for malware. Follow the steps presented below to remove Trojan:Win32/Tiggre!rfn virus from Windows 10 and other modern versions of Microsoft OS.
Remove Trojan:Win32/Tiggre!rfn trojan (removal tutorial)
In the steps below, we will try to cover the Windows 10, Windows 8, Windows 7 and Windows XP and provide general advice to delete Trojan:Win32/Tiggre!rfn malware. You may find some minor differences in your Windows install. No matter, you should be okay if you follow the steps outlined below: remove all suspicious and unknown applications, remove malicious scheduled tasks, run free malware removal tools. Some of the steps below will require you to exit this web site. So, please read the few simple steps carefully, after that bookmark or print it for later reference.
To remove Trojan:Win32/Tiggre!rfn, complete the following steps:
- Check the list of installed software
- Remove malicious Scheduled Tasks
- How to delete Trojan:Win32/Tiggre!rfn malware with Zemana Anti-malware
- Remove Trojan:Win32/Tiggre!rfn virus with HitmanPro
- Use Malwarebytes to delete Trojan:Win32/Tiggre!rfn trojan
- How to stay safe online
- Finish words
Check the list of installed software
It is of primary importance to first identify and delete all PUPs, malicious programs and hijacker infections through ‘Add/Remove Programs’ (Windows XP) or ‘Uninstall a program’ (Windows 10, 8, 7) section of your Windows Control Panel.
Make sure you have closed all browsers and other applications. Press CTRL, ALT, DEL keys together to open the Windows Task Manager.
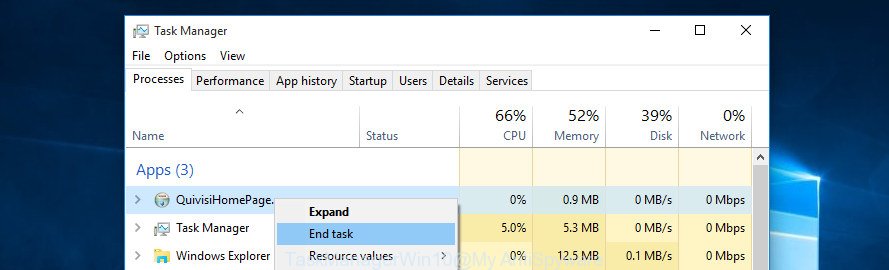
Click on the “Processes” tab, look for something suspicious that is the Trojan:Win32/Tiggre!rfn trojan then right-click it and select “End Task” or “End Process” option. In many cases, malware masks itself to avoid detection by imitating legitimate Microsoft Windows processes. A process is particularly suspicious: it is taking up a lot of memory (despite the fact that you closed all of your applications), its name is not familiar to you (if you’re in doubt, you can always check the application by doing a search for its name in Google, Yahoo or Bing).
Next, uninstall any undesired and suspicious software from your Control panel.
Windows 10, 8.1, 8
Now, click the Windows button, type “Control panel” in search and press Enter. Choose “Programs and Features”, then “Uninstall a program”.
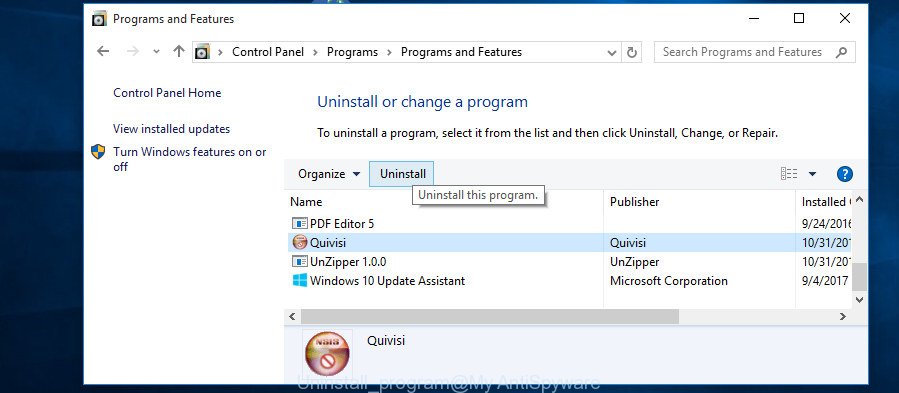
Look around the entire list of applications installed on your machine. Most probably, one of them is a malware. Choose the questionable program or the program that name is not familiar to you and delete it.
Windows Vista, 7
From the “Start” menu in MS Windows, choose “Control Panel”. Under the “Programs” icon, choose “Uninstall a program”.
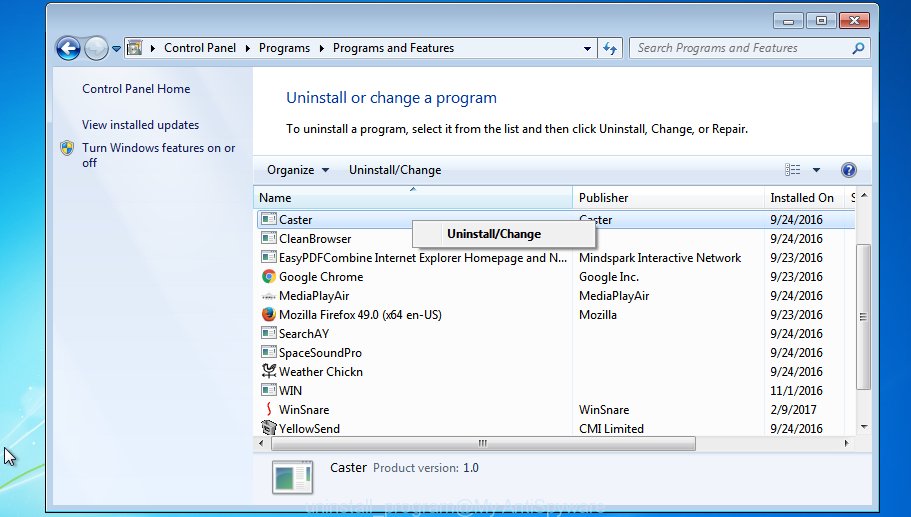
Select the questionable or any unknown programs, then click “Uninstall/Change” button to remove this undesired application from your PC.
Windows XP
Click the “Start” button, select “Control Panel” option. Click on “Add/Remove Programs”.
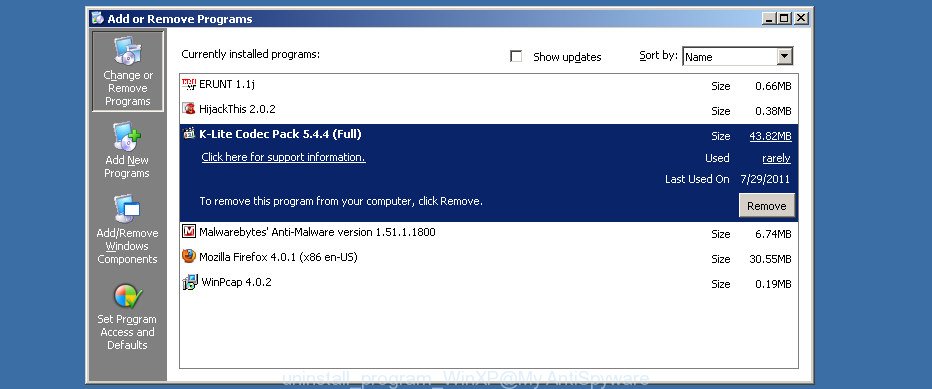
Choose an unwanted application, then click “Change/Remove” button. Follow the prompts.
Remove malicious Scheduled Tasks
Once installed, the Trojan:Win32/Tiggre!rfn virus can add a task in to the Windows Task Scheduler Library. Due to this, every time when you start your computer, it will start itself automatically. So, you need to check the Task Scheduler Library and remove all malicious tasks which have been created by malware.
Press Windows and R keys on the keyboard simultaneously. This shows a prompt that titled as Run. In the text field, type “taskschd.msc” (without the quotes) and click OK. Task Scheduler window opens. In the left-hand side, click “Task Scheduler Library”, as shown below.
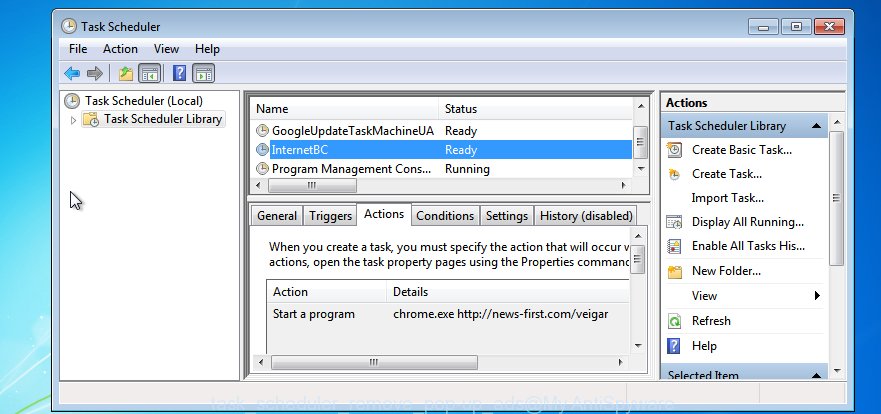
Task scheduler
In the middle part you will see a list of installed tasks. Please select the first task, its properties will be show just below automatically. Next, click the Actions tab. Pay attention to that it launches on your system. Found something suspicious, then remove this malicious task. If you are not sure that executes the task, check it through a search engine. If it is a component of the malicious apps, then this task also should be removed.
Having defined the task that you want to delete, then press on it with the right mouse button and select Delete as on the image below.
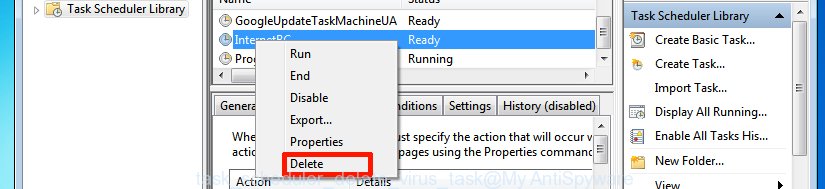
Delete a task
Repeat this step, if you have found a few tasks which have been created by the Trojan:Win32/Tiggre!rfn. Once is finished, close the Task Scheduler window.
How to delete Trojan:Win32/Tiggre!rfn malware with Zemana Anti-malware
You can remove Trojan:Win32/Tiggre!rfn automatically with a help of Zemana Anti-malware. We suggest this malicious software removal utility because it may easily remove malware, browser hijackers, potentially unwanted programs, ad-supported software with all their components such as folders, files and registry entries.

- Click the following link to download the latest version of Zemana AntiMalware for Microsoft Windows. Save it on your Desktop.
Zemana AntiMalware
164873 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019 - At the download page, click on the Download button. Your web browser will display the “Save as” dialog box. Please save it onto your Windows desktop.
- When downloading is complete, please close all software and open windows on your computer. Next, start a file named Zemana.AntiMalware.Setup.
- This will open the “Setup wizard” of Zemana onto your system. Follow the prompts and don’t make any changes to default settings.
- When the Setup wizard has finished installing, the Zemana AntiMalware (ZAM) will launch and open the main window.
- Further, click the “Scan” button . Zemana Anti Malware (ZAM) program will scan through the whole computer for the Trojan:Win32/Tiggre!rfn malware. A system scan can take anywhere from 5 to 30 minutes, depending on your PC system. While the Zemana Anti Malware (ZAM) is checking, you may see how many objects it has identified either as being malicious software.
- When the system scan is finished, Zemana Anti-Malware (ZAM) will display you the results.
- Review the results once the tool has finished the system scan. If you think an entry should not be quarantined, then uncheck it. Otherwise, simply click the “Next” button. The utility will remove Trojan:Win32/Tiggre!rfn virus and move items to the program’s quarantine. Once that process is finished, you may be prompted to reboot the system.
- Close the Zemana Anti-Malware (ZAM) and continue with the next step.
Remove Trojan:Win32/Tiggre!rfn with HitmanPro
If Zemana cannot remove this virus, then we advises to use the HitmanPro. HitmanPro is a free removal utility for hijackers, potentially unwanted apps, toolbars and malware. It’s specially developed to work as a second scanner for your machine.
Download Hitman Pro from the following link.
HitmanPro
12222 downloads
Author: Sophos
Category: Security tools
Update: June 28, 2018
Download and use HitmanPro on your PC. Once started, click “Next” button to start checking your personal computer for the Trojan:Win32/Tiggre!rfn virus. This process may take some time, so please be patient. While the Hitman Pro is checking, you can see how many objects it has identified either as being malware..
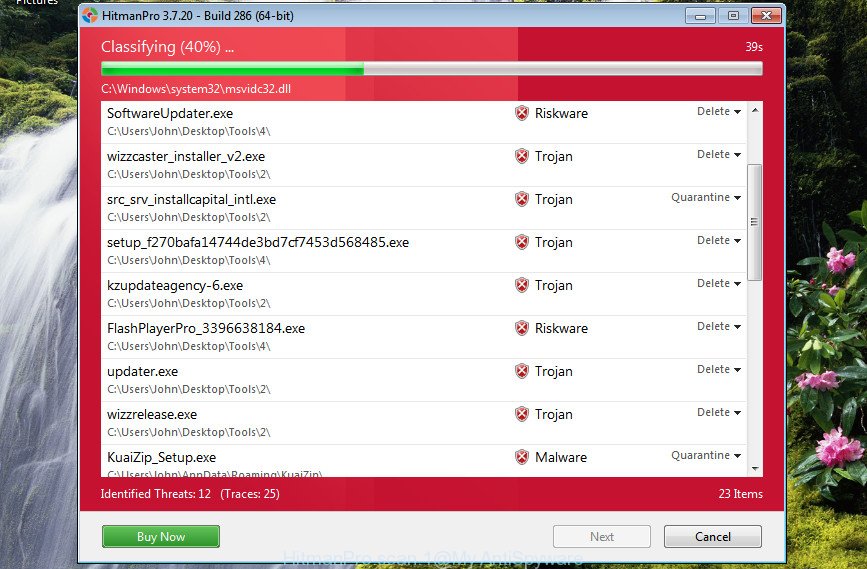
After HitmanPro completes the scan, a list of all items found is produced.
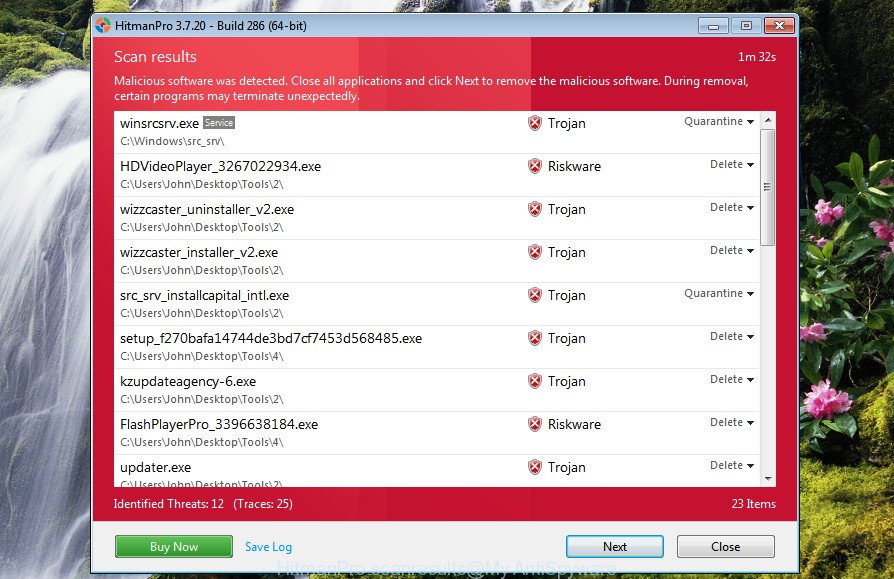
Once you have selected what you wish to get rid of from your personal computer click Next button.
It will display a prompt, press the “Activate free license” button to start the free 30 days trial to remove all malware found.
Use Malwarebytes to delete Trojan:Win32/Tiggre!rfn trojan
You can remove Trojan:Win32/Tiggre!rfn trojan automatically with a help of Malwarebytes Free. We recommend this free malicious software removal tool because it can easily remove browser hijacker infections, adware, PUPs and toolbars with all their components such as files, folders and registry entries.
- Download MalwareBytes Free on your computer from the link below.
- At the download page, click on the Download button. Your internet browser will open the “Save as” prompt. Please save it onto your Windows desktop.
- After the download is complete, please close all apps and open windows on your PC. Double-click on the icon that’s named mb3-setup.
- This will launch the “Setup wizard” of MalwareBytes onto your system. Follow the prompts and don’t make any changes to default settings.
- When the Setup wizard has finished installing, the MalwareBytes Free will start and open the main window.
- Further, click the “Scan Now” button for scanning your machine for the Trojan:Win32/Tiggre!rfn trojan. A scan can take anywhere from 10 to 30 minutes, depending on the number of files on your computer and the speed of your computer. While the utility is checking, you can see count of objects and files has already scanned.
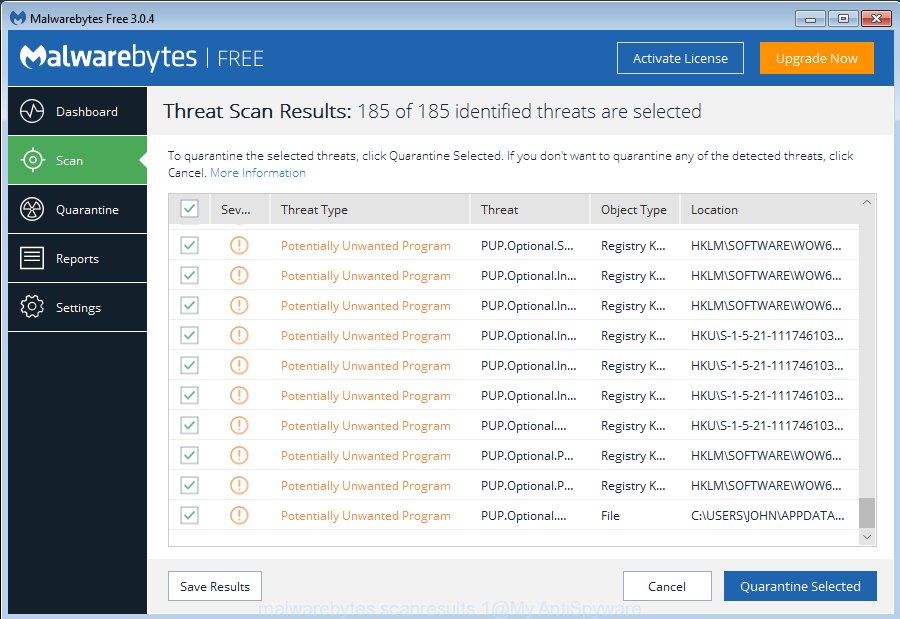
- Once the checking is finished, MalwareBytes will display a screen which contains a list of malware that has been detected.
- Review the results once the tool has finished the system scan. If you think an entry should not be quarantined, then uncheck it. Otherwise, simply press the “Quarantine Selected” button. After that process is complete, you may be prompted to reboot the personal computer.
- Close the Anti Malware and continue with the next step.
Video instruction, which reveals in detail the steps above.
How to stay safe online
If you browse the Web, you cannot avoid malicious advertising. But you can protect your internet browser against it. Download and run an ad-blocking program. AdGuard is an ad blocker that can filter out lots of of the malvertising, stoping dynamic scripts from loading malicious content.
Download AdGuard from the link below. Save it directly to your MS Windows Desktop.
Adguard download
26855 downloads
Version: 6.4
Author: © Adguard
Category: Security tools
Update: November 15, 2018
After downloading it, run the downloaded file. You will see the “Setup Wizard” screen as shown in the following example.
Follow the prompts. After the install is complete, you will see a window as displayed in the following example.

You can press “Skip” to close the installation program and use the default settings, or click “Get Started” button to see an quick tutorial that will assist you get to know AdGuard better.
In most cases, the default settings are enough and you do not need to change anything. Each time, when you launch your personal computer, AdGuard will launch automatically and block pop-up ads, browser redirects, as well as other malicious or misleading web-sites. For an overview of all the features of the application, or to change its settings you can simply double-click on the AdGuard icon, that can be found on your desktop.
Finish words
After completing the instructions above, your computer should be clean from the Trojan:Win32/Tiggre!rfn trojan and other malware. Unfortunately, if the few simple steps does not help you, then you have caught a new malware, and then the best way – ask for help.
Please start a new thread by using the “New Topic” button in the Spyware Removal forum. When posting your HJT log, try to give us some details about your problems, so we can try to help you more accurately. Wait for one of our trained “Security Team” or Site Administrator to provide you with knowledgeable assistance tailored to your problem with the Trojan:Win32/Tiggre!rfn malware.
What kind of malware is Trojan Win32/Tiggre!rfn?
Trojan Win32/Tiggre!rfn is high-risk malware designed to perform a number of malicious tasks on victims’ computers. It is also known as «Trojan.GenericKD.12694003» (by BitDefender) and «W32/Autoit.CGO!tr» (by Fortinet).
Trojan Win32/Tiggre!rfn is distributed in various ways, including spam emails (malicious attachments), fake Adobe Flash Player updaters, malicious websites, chain infections, and even Facebook messages.
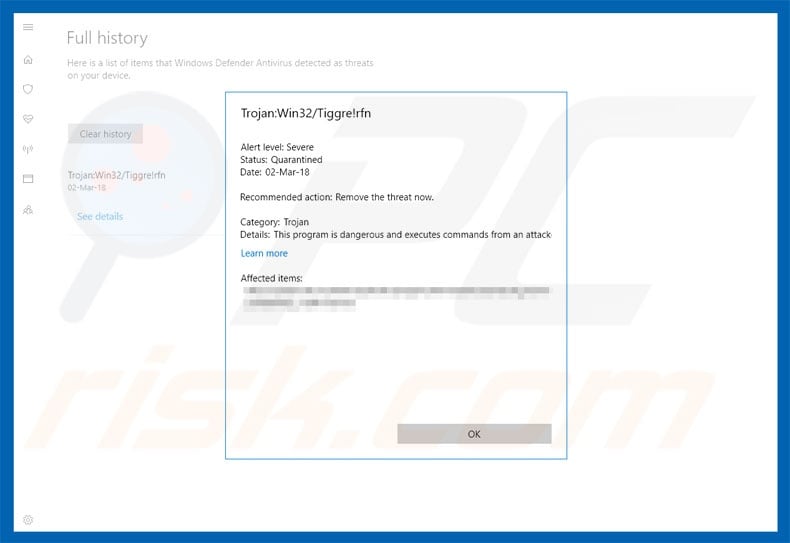
Trojan Win32/Tiggre!rfn malware in detail
Trojan Win32/Tiggre!rfn is versatile malware, since it performs various functions depending on developers’ choices. For example, it can misuse system resources to mine cryptocurrency. The entire crypto-mining process essentially based on solving various «mathematical equations». Mining tools employ system resources to perform calculations.
Each time an «equation» is solved, a single unit of currency (e.g., 1 Bitcoin) is mined. Since an identical «equation» is solved by a number of computers simultaneously, the reward is split between each device depending on the power of the device and how much work is performed. All revenue is received by cyber criminals (crypto wallet), whilst users receive nothing in return.
In fact, all this is done without their consent, and since mining takes up to 100% of computer resources, systems often become unstable and virtually unusable. Furthermore, within certain circumstances (high room temperatures, poor cooling systems, etc.) hardware can be damaged (components might overheat).
Trojan Win32/Tiggre!rfn also gathers various data, including saved logins/passwords, keystrokes, banking information, and so on.
Collected data is often misused to generate revenue. Therefore, the presence of malware such as Trojan Win32/Tiggre!rfn might lead to serious financial and privacy issues (e.g., cyber criminals can transfer funds to their accounts, purchase illegal items under your name, and so on).
In some cases, Trojan Win32/Tiggre!rfn infiltrates systems along with a number of adware-type applications. These programs are not as harmful as Trojan Win32/Tiggre!rfn, but can be frustrating and problematic. Adware-type programs typically deliver intrusive advertisements and gather sensitive data.
Intrusive ads conceal underlying website content (thereby significantly diminishing the browsing experience), and also redirect to malicious sites and even run scripts that stealthily download and install malware. Clicking these ads can lead to malicious sites.
Furthermore, adware gathers IP addresses, URLs visited, search queries, pages viewed, and other data relating to browsing activity. Collected information is shared with third parties (potentially, cyber criminals). Therefore, adware poses a threat to your privacy and Internet browsing safety. For these reasons, all adware-type apps must be eliminated immediately.
Threat Summary:
| Name | Trojan Win32/Tiggre!rfn malware |
| Threat Type | Trojan, Password stealing virus, Banking malware, Spyware |
| Detection Names | Avast (Win32:TrojanX-gen [Trj]), BitDefender (Trojan.GenericKD.41401183), ESET-NOD32 (A Variant Of Win32/Kryptik.GUFO), Kaspersky (Backdoor.Win32.Androm.srmx), Full List (VirusTotal) |
| Symptoms | Trojans are designed to stealthily infiltrate victim’s computer and remain silent thus no particular symptoms are clearly visible on an infected machine. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software cracks. |
| Damage | Stolen banking information, passwords, identity theft, victim’s computer added to a botnet. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo Cleaner To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Similarities with other malware
Trojan Win32/Tiggre!rfn is very similar to Pony, TrickBot, and FormBook. In fact, there are dozens of viruses that also gather information, mine cryptocurrencies, and perform other malicious tasks. Adware-type apps share many similarities.
By offering ‘useful features’, unwanted programs attempt to give the impression of legitimacy, however, rather than enabling the functions promised, adware poses a direct threat to your privacy and Internet browsing safety. The only purpose of this software is to help developers generate passive revenue.
How did Trojan Win32/Tiggre!rfn infect my computer?
As mentioned above, Trojan Win32/Tiggre!rfn is promoted using spam emails, fake Flash Player updaters, and Facebook. Spam emails contain malicious attachments (e.g., MS Office documents, JavaScript files, etc.) that, once opened, stealthily download and install malware. Fake updaters claim that the player is outdated (although it is not) and encourage users to renew it.
Rather than updating the player, however, these tools download and install Trojan Win32/Tiggre!rfn. Criminals also proliferate this malware via malicious sites that, once opened, execute scripts designed to download and install Trojan Win32/Tiggre!rfn without consent.
Another method is «chain-infecting»: a computer is infected with malware that proliferates other viruses (in this case, Trojan Win32/Tiggre!rfn). Developers also use scripts that send spam messages on Facebook. The message simply contains a video file, however, this is a disguise — rather than opening the video, the user will open a AutoIt script that will infect the system.
How to avoid installation of malware?
The main reasons for computer infections are poor knowledge and careless behavior. The key to safety is caution. Therefore, pay close attention when browsing the Internet. Think twice before opening files/links received via email, Facebook accounts, Skype, and so on.
If files/links seem irrelevant or have been sent from suspicious/unrecognizable names/email addresses, delete these messages immediately and certainly do not open attached files/links. Furthermore, keep installed applications up-to-date and remember that criminals proliferate malware via fake updaters.
Therefore, apps should be renewed using implemented update features or tools provided by the official developers only. Having a reputable anti-virus/anti-spyware suite installed and running is also paramount.
If you believe that your computer is infected with Trojan Win32/Tiggre!rfn, we recommend running a scan with
Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo Cleaner
By downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Trojan Win32/Tiggre!rfn?
- STEP 1. Manual removal of Trojan Win32/Tiggre!rfn malware.
- STEP 2. Check if your computer is clean.
How to remove malware manually?
Manual malware removal is a complicated task, usually it’s better to let antivirus or anti-malware programs do it automatically. To remove this malware we recommend using
Combo Cleaner Antivirus for Windows.
If you wish to remove malware manually, the first step is to identify the name of the malware that you are trying to remove. Here’s an example of a suspicious program running on user’s computer:
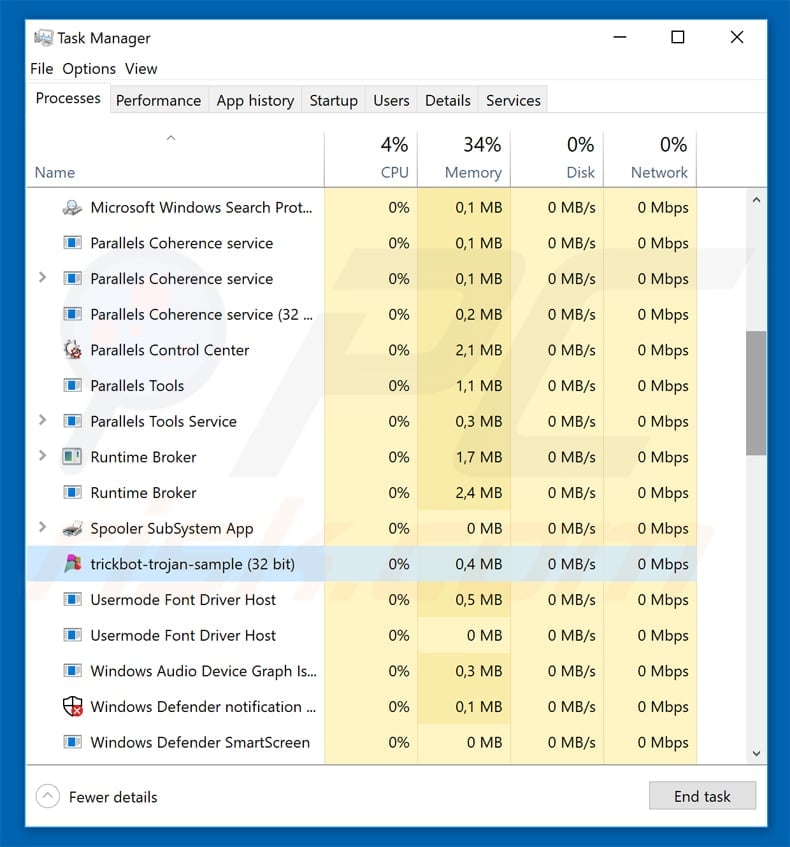
If you checked the list of programs running on your computer, for example using task manager and identified a program that looks suspicious you should continue with these steps:
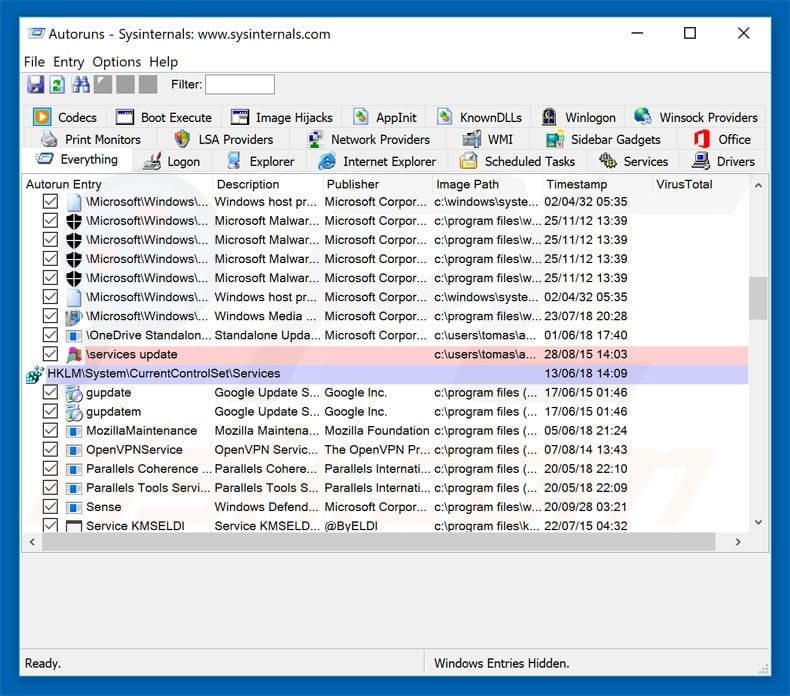
Download a program called Autoruns. This program shows auto-start applications, Registry and file system locations:
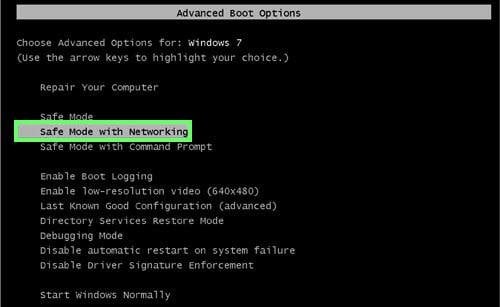
Restart your computer into Safe Mode:
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, and then select Safe Mode with Networking from the list.
Video showing how to start Windows 7 in «Safe Mode with Networking»:
Windows 8 users: Start Windows 8 is Safe Mode with Networking — Go to Windows 8 Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened «General PC Settings» window, select Advanced startup. Click the «Restart now» button. Your computer will now restart into the «Advanced Startup options menu».
Click the «Troubleshoot» button, and then click the «Advanced options» button. In the advanced option screen, click «Startup settings». Click the «Restart» button. Your PC will restart into the Startup Settings screen. Press F5 to boot in Safe Mode with Networking.
Video showing how to start Windows 8 in «Safe Mode with Networking»:
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click «Restart» while holding «Shift» button on your keyboard. In the «choose an option» window click on the «Troubleshoot», next select «Advanced options». In the advanced options menu select «Startup Settings» and click on the «Restart» button.
In the following window you should click the «F5» button on your keyboard. This will restart your operating system in safe mode with networking.
Video showing how to start Windows 10 in «Safe Mode with Networking»:
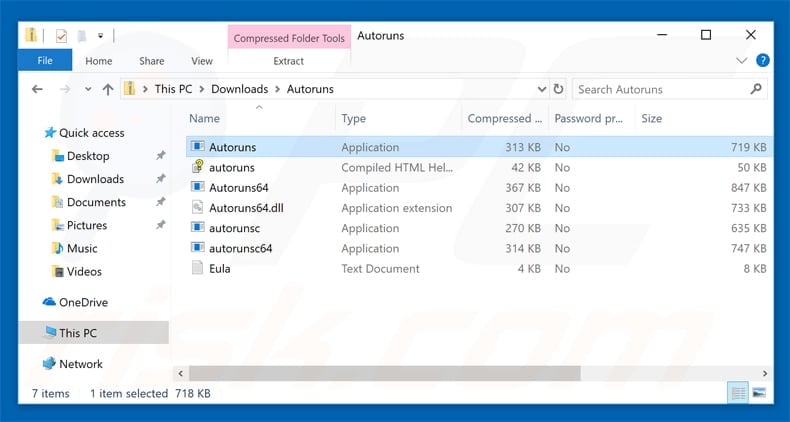
Extract the downloaded archive and run Autoruns.exe file.
In the Autoruns application click «Options» at the top and uncheck «Hide Empty Locations» and «Hide Windows Entries» options. After this procedure click the «Refresh» icon.
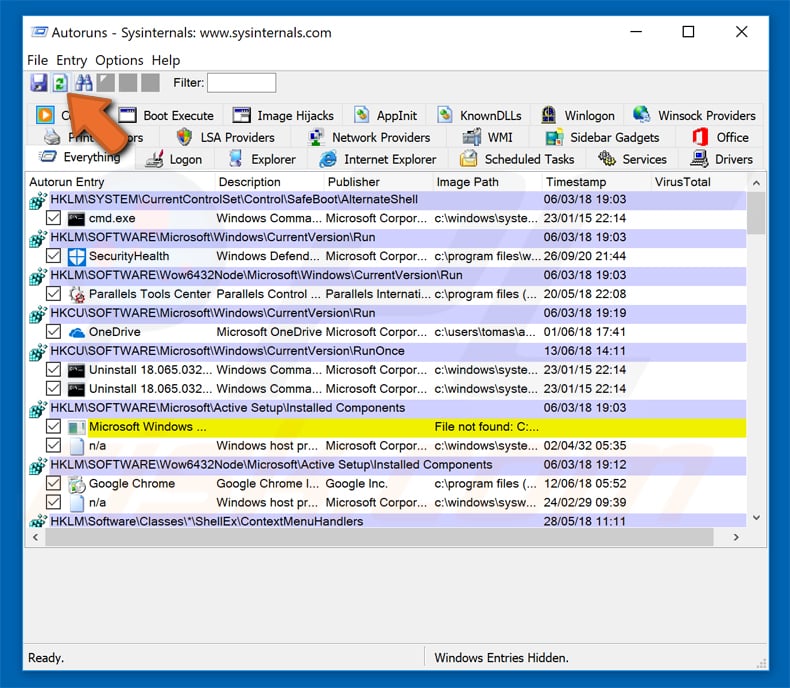
Check the list provided by Autoruns application and locate the malware file that you want to eliminate.
You should write down it full path and name. Note that some malware hides their process names under legitimate Windows process names. At this stage it’s very important to avoid removing system files. After you locate he suspicious program you want to remove right click your mouse over it’s name and choose «Delete»
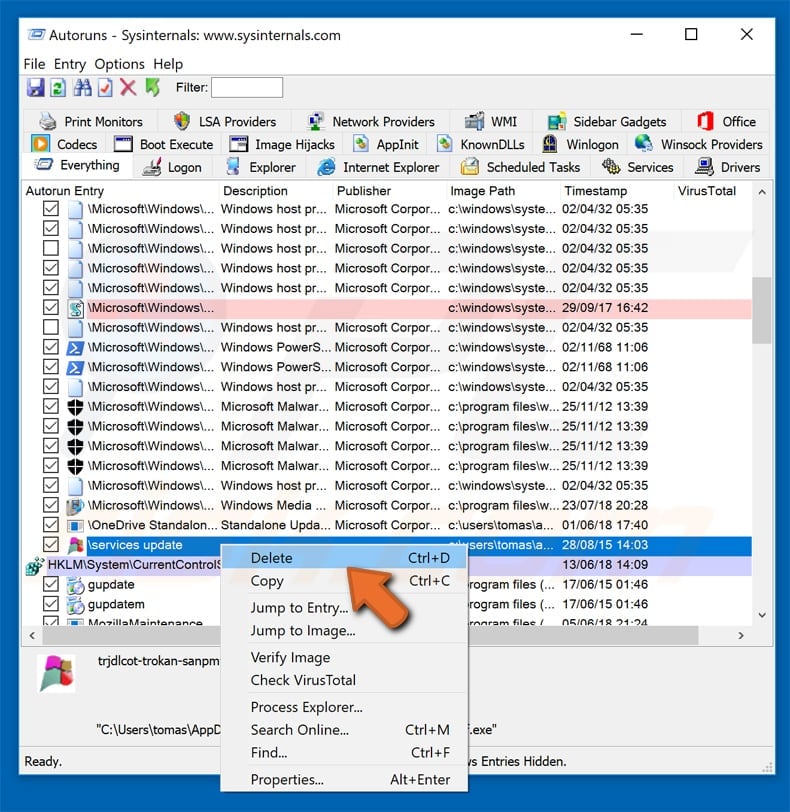
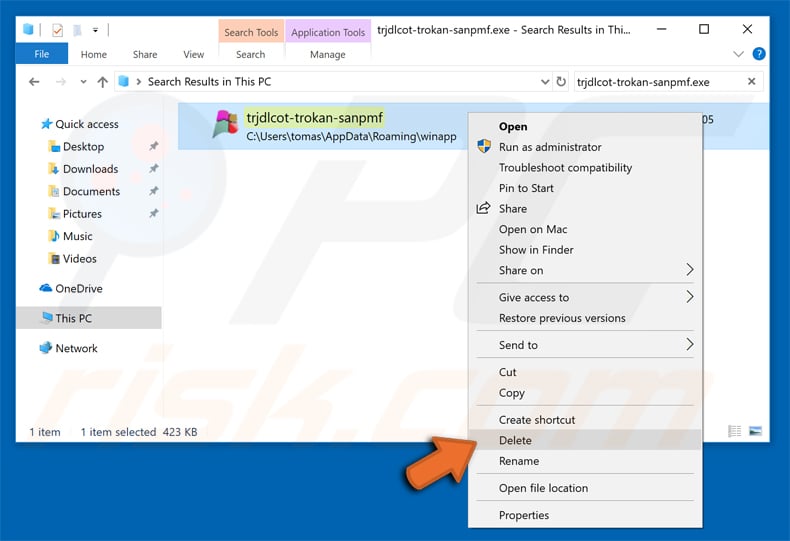
After removing the malware through Autoruns application (this ensures that the malware won’t run automatically on the next system startup) you should search for the malware name on your computer. Be sure to enable hidden files and folders before proceeding. If you find the file of the malware be sure to remove it.
Reboot your computer in normal mode. Following these steps should help remove any malware from your computer. Note that manual threat removal requires advanced computer skills, it’s recommended to leave malware removal to antivirus and anti-malware programs.
These steps might not work with advanced malware infections. As always it’s better to avoid getting infected that try to remove malware afterwards. To keep your computer safe be sure to install latest operating system updates and use antivirus software.
To be sure your computer is free of malware infections we recommend scanning it with
Combo Cleaner Antivirus for Windows.
Frequently Asked Questions (FAQ)
My computer is infected with Trojan Win32/Tiggre!rfn malware, should I format my storage device to get rid of it?
You can remove Trojan Win32/Tiggre!rfn from the operating system by following the steps provided in our removal guide. It is not necessary to format the storage device to remove it.
What are the biggest issues that malware can cause?
The biggest issues that software of this type can cause are monetary and data loss, identity theft, decreased computer performance, and further infections.
What is the purpose of Trojan Win32/Tiggre!rfn malware?
It can be used for different purposes. It is known that cybercriminals use it to mine cryptocurrency and (or) gather various data (including saved logins/passwords, keystrokes, and banking information). We also found that this malware often injects some adware.
How did Trojan Win32/Tiggre!rfn infiltrate my computer?
The Trojan Win32/Tiggre!rfn malware is distributed via spam emails (malicious attachments), fake Adobe Flash Player updaters, malicious web poages, other malicious programs, and even Facebook messages.
Will Combo Cleaner protect me from malware?
Yes, Combo Cleaner will remove malware from the operating system. It can detect almost all known malware. If a computer is infected with high-end malware, it must be scanned using a full scan. Otherwise, the antivirus program will not detect malware that hides deep in the operating system.
Чем асинхронная логика (схемотехника) лучше тактируемой, как я думаю, что помимо энергоэффективности — ещё и безопасность.
Hrethgir 14.05.2025
Помимо огромного плюса в энергоэффективности, асинхронная логика — тотальный контроль над каждым совершённым тактом, а значит — безусловная безопасность, где безконтрольно не совершится ни одного. . .
Многопоточные приложения на C++
bytestream 14.05.2025
C++ всегда был языком, тесно работающим с железом, и потому особеннно эффективным для многопоточного программирования. Стандарт C++11 произвёл революцию, добавив в язык нативную поддержку потоков,. . .
Stack, Queue и Hashtable в C#
UnmanagedCoder 14.05.2025
Каждый опытный разработчик наверняка сталкивался с ситуацией, когда невинный на первый взгляд List<T> превращался в узкое горлышко всего приложения. Причина проста: универсальность – это прекрасно,. . .
Как использовать OAuth2 со Spring Security в Java
Javaican 14.05.2025
Протокол OAuth2 часто путают с механизмами аутентификации, хотя по сути это протокол авторизации. Представьте, что вместо передачи ключей от всего дома вашему другу, который пришёл полить цветы, вы. . .
Анализ текста на Python с NLTK и Spacy
AI_Generated 14.05.2025
NLTK, старожил в мире обработки естественного языка на Python, содержит богатейшую коллекцию алгоритмов и готовых моделей. Эта библиотека отлично подходит для образовательных целей и. . .
Реализация DI в PHP
Jason-Webb 13.05.2025
Когда я начинал писать свой первый крупный PHP-проект, моя архитектура напоминала запутаный клубок спагетти. Классы создавали другие классы внутри себя, зависимости жостко прописывались в коде, а о. . .
Обработка изображений в реальном времени на C# с OpenCV
stackOverflow 13.05.2025
Объединение библиотеки компьютерного зрения OpenCV с современным языком программирования C# создаёт симбиоз, который открывает доступ к впечатляющему набору возможностей. Ключевое преимущество этого. . .
POCO, ACE, Loki и другие продвинутые C++ библиотеки
NullReferenced 13.05.2025
В C++ разработки существует такое обилие библиотек, что порой кажется, будто ты заблудился в дремучем лесу. И среди этого многообразия POCO (Portable Components) – как маяк для тех, кто ищет. . .
Паттерны проектирования GoF на C#
UnmanagedCoder 13.05.2025
Вы наверняка сталкивались с ситуациями, когда код разрастается до неприличных размеров, а его поддержка становится настоящим испытанием. Именно в такие моменты на помощь приходят паттерны Gang of. . .
Создаем CLI приложение на Python с Prompt Toolkit
py-thonny 13.05.2025
Современные командные интерфейсы давно перестали быть черно-белыми текстовыми программами, которые многие помнят по старым операционным системам. CLI сегодня – это мощные, интуитивные и даже. . .
Trojan Win32 Tiggre Rfn Virus Removal Guide To remove trojan:win32 tiggre!rfn, complete the following steps: check the list of installed software; remove malicious scheduled tasks; how to delete trojan:win32 tiggre!rfn malware with zemana anti malware; remove trojan:win32 tiggre!rfn virus with hitmanpro; use malwarebytes to delete trojan:win32 tiggre!rfn trojan; how to stay safe online. The trojan win32 tiggre!rfn malware is distributed via spam emails (malicious attachments), fake adobe flash player updaters, malicious web poages, other malicious programs, and even facebook messages.

Trojan Win32 Tiggre Rfn Virus Removal Guide Use a reputable anti virus and anti malware software to scan your system and detect and remove the trojan. if the anti virus and anti malware software cannot remove the trojan, you can try manually deleting the files and registry entries associated with the trojan. While you are waiting for the next qualified approved malware removal expert helper to weigh in on your topic, and even though you may have run the following malwarebytes utility, or its subsets, please carefully follow these instructions: download the malwarebytes support tool. This video will show you how to remove trojan:win32 tiggre!rfn. if you need more details about the removal process, please visit: easysolvemalware.co. To remove trojan win32 tiggre!rfn completely, we recommend you to use spyhunter 5. it can help you remove files, folders, and registry keys of trojan win32 tiggre!rfn and provides active protection from viruses, trojans, backdoors.
Trojan Win32 Tiggre Tiggre Trojan Removal Guide This video will show you how to remove trojan:win32 tiggre!rfn. if you need more details about the removal process, please visit: easysolvemalware.co. To remove trojan win32 tiggre!rfn completely, we recommend you to use spyhunter 5. it can help you remove files, folders, and registry keys of trojan win32 tiggre!rfn and provides active protection from viruses, trojans, backdoors. Trojan:win32 tiggre!rfn is a multi purpose malware that uses your pc resources for illegal actions; signs and symptoms of crypto mining bot presence; ways to protect yourself from harmful trojan horses and other malware; trojan win32 tiggre!rfn elimination can prevent your cpu from overheating; how to prevent from getting trojans; references. Follow the step by step removal guide below to eliminate trojan:win32 tiggre!rfn virus right now. you will regain a clean and safe computer. how to remove trojan:win32 tiggre!rfn?. Trojan:win32 tiggre detected by microsoft defender? how to remove tiggre malware by following easy step by step instructions. The instructions in removal guide and the professional tiggre removal tool on this page can both help with this task, so don’t hesitate to use them in order to get rid of the infection. summary: name.
Trojan Win32 Pomal Rfn Trojan Virus Pomal Removal Trojan:win32 tiggre!rfn is a multi purpose malware that uses your pc resources for illegal actions; signs and symptoms of crypto mining bot presence; ways to protect yourself from harmful trojan horses and other malware; trojan win32 tiggre!rfn elimination can prevent your cpu from overheating; how to prevent from getting trojans; references. Follow the step by step removal guide below to eliminate trojan:win32 tiggre!rfn virus right now. you will regain a clean and safe computer. how to remove trojan:win32 tiggre!rfn?. Trojan:win32 tiggre detected by microsoft defender? how to remove tiggre malware by following easy step by step instructions. The instructions in removal guide and the professional tiggre removal tool on this page can both help with this task, so don’t hesitate to use them in order to get rid of the infection. summary: name.

Trojan Win32 Skeeyah A Rfn Virus Removal Guide Trojan:win32 tiggre detected by microsoft defender? how to remove tiggre malware by following easy step by step instructions. The instructions in removal guide and the professional tiggre removal tool on this page can both help with this task, so don’t hesitate to use them in order to get rid of the infection. summary: name.

How To Remove Trojan Win32 Tiggre Rfn Virus Removal Guide
