During a recent engagement, I successfully deployed a
wildcard Domain Name System (DNS) record in conjunction with Responder. Within
minutes, a misconfigured host made a query for a non-existent DNS record and
was poisoned into connecting to our Responder instance. Unfortunately, the
account was privileged enough that domain compromise was achieved. The
techniques and tools used to achieve this attack can be found here, here, and here.
Kevin’s blog post, in the first link, also spells out what a company can do to
help protect against the attack. Essentially, the post recommends adding your
own static wildcard and ‘wpad’ DNS record pointing to a host you control or
loop back.
After working with the client, the necessary changes were
successfully implemented. However, they did ask an excellent follow-up question
— ‘How can we identify what DNS record these hosts were looking for in the
first place?’ By pointing a wild card record to our Responder instance, we can
see what hosts are poisoned, but ONLY if the host attempts a connection. In
other words, if a host is configured to use a mapped drive but has a typo in
the host name, we’d catch it. But what if there’s a process on the host to
connect to a Redis server? Responder wouldn’t know what to do with that and would
drop the traffic. Furthermore, there could be instances wherein a DNS query is
made, but no follow-up connection is attempted.
Thankfully, starting with Windows Server 2012, Microsoft
introduced a debugging/tracing feature into Windows DNS server service. This
blog post will walk you through how to enable and track down hosts performing
DNS queries for non-existent records.

Step 1: Configure the Wildcard DNS Record
This should be done regardless, as it tends to mitigate the
above wildcard and LLMNR/NBNS based poisonings. In our case, however, we’re
going to set it to an IP that we’ll remember. In our example, we’ll resolve any
queries that hit the wildcard DNS record to point to 127.0.0.2. We could pick
anything, but we don’t want any server or service to accidentally reach out to
a legitimate IP.


Step 2: Enable Advanced Logging
Once the wildcard record has been created, we will enable
Debug Logging. Please note, this will generate a large and verbose text file. Disk IO, Disk Space, and CPU load could be
heavily impacted depending on your environment. I highly recommend testing in
your dev/stage environment first.


To reduce the load, I’ve selected only the boxes that need
to be enabled. You can always expand the logging to include more functions, but
for now, use the above. Another note, I’m saving this to the desktop because
I’m in a lab. You might want to choose a better place if running in a production
environment. If you’d like to rotate these logs out, see the following
instructions on how to do so here.
Once all of the settings are correct, you can go ahead and
click OK.
Next, I’ll go ahead and generate some DNS queries to
simulate a host attempting to resolve a non-existent record.

As you can see, the address for our second query resolves to
our static value, 127.0.0.2.
Step 3: Reviewing the Log
In testing, I found that the DNS Server does not append to
the log in real time. I believe this is due to caching with the DNS service. To
force the log to write out immediately, you can stop/pause the DNS service
itself, but be aware, this also stops the resolution service for any incoming
DNS requests.
If we open the log, here is what we’ll see.


Because we enabled ‘details’ with our logging, we get the
full content of the DNS response packet. While this information is great, it’s
a bit of a pain to deal with. There are several free tools out there already to
parse DNS logs (Windows
DNS Log Analyzer, Microsoft
Log Parser, DNSModule.psm1).
However, from what I can tell, they only parse the high-level logs, not the
detailed contents. If you find one that does both, please let me know!
Step 4: Parsing With PowerShell
To aid in the parsing of these logs, I created a very basic PowerShell script that you
can feed the log through. Essentially, the script will scour through the log
file and pull four values: source IP connection, port, name being resolved, and
the IP address included in the response. The script then filters on any record
where the address resolved was 127.0.0.2. Therefore, it is important to pick a
unique IP for our wildcard. If we picked a common IP, we’d have a hard time
distinguishing between legit queries and wildcard-based queries.

Code (TraceDetailedDNSLogs.ps1) can be found here.
That’s it! The next steps would be to grab a copy of Sysmon10
with DNS query logging to trace down what process initiated the DNS query and
clean it up. Hopefully this post will help in tracking down hosts/users that
are attempting to resolve addresses for DNS records that do not exist. One
additional benefit to enabling DNS logging is that, if you uncheck the details
option, the log file will continue single line entries of log debug data which
then can be fed into a Security Information and Event Management (SIEM) system,
like Splunk. This could be a great asset for monitoring and tracking DNS
queries made to known malicious domains.

При доступе к веб-сайту ваш компьютер запрашивает DNS-сервер, чтобы преобразовать доменное имя сайта в соответствующий IP-адрес. Как правило, ваша сеть использует DNS-серверы, предоставленные вашим интернет-провайдером (ISP). Чтобы определить, является ли DNS-сервер причиной проблем с доступом, вы можете попытаться получить доступ к веб-сайту напрямую через его IP-адрес. В случае успеха это указывает на потенциальную проблему с DNS-сервером, например, устаревшие записи. В таких случаях использование инструмента DNS traceroute может помочь определить источник проблемы, сопоставив путь, по которому ваш запрос проходит через иерархию DNS.
Отчет DNS Traceroute
Трассировка DNS является отличным инструментом для выявления проблем с DNS-серверами. Он показывает, как DNS-запросы проходят через все этапы иерархии DNS, от серверов ROOT до локального DNS-сервера. Если трассировка DNS к одному из DNS-серверов не отвечает или отвечает неправильно, вы можете найти ее в результатах отчета о трассировке DNS.
-
Поддерживаемые типы записей DNS
Чтобы получить доступ к отчету о трассировке DNS, выполните следующие действия:
- Войдите в свою учетную запись. На странице «Диспетчер устройств» выберите «Онлайн-отчеты» в меню «Отчеты» на левой боковой панели.
- На странице «Онлайн-отчеты» вам будет предложено выбрать цель или устройство. Вы также можете щелкнуть имя устройства в списке «Диспетчер устройств», чтобы получить доступ к онлайн-отчету.
- На странице Онлайн-отчет выберитесоответствующее место мониторинга, в котором произошла ошибка или ошибки произошло, а затем сверлитьвниз дальше в шаг,
где ошибка была я помят. Перейдите на и нажмите DnsTrace.
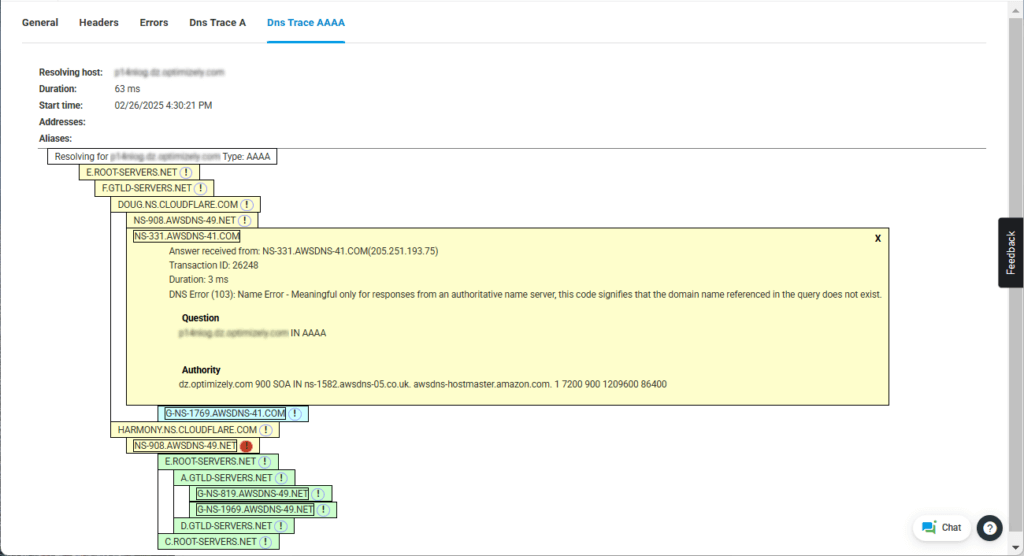
Визуализации DNS Trace A и AAAA выделяют все неотвечающие DNS-серверы, отмечая проблемные ветви красным значком и восклицательным знаком. В качестве примера обратитесь к изображению ниже.
In the vast universe of network management and IT troubleshooting, issues related to the Domain Name System (DNS) often crop up. DNS is a crucial part of online existence, responsible for translating human-friendly domain names into numerical IP addresses that computers use to communicate with one another. So, when DNS issues emerge, they can cause significant problems.
However, like every other IT problem, DNS issues can be resolved. You just have to know the right tools and commands. In this blog post, we’ll delve into some of these essential DNS troubleshooting tools and commands that every network administrator ought to arm themselves with.
Table of Contents
What is DNS Troubleshooting?
DNS troubleshooting is the process of diagnosing and resolving issues related to the Domain Name System (DNS). Since DNS is responsible for translating domain names into IP addresses, any misconfiguration, downtime, or cache errors can lead to connectivity problems. Troubleshooting involves checking DNS settings, testing DNS resolution, clearing caches, and using diagnostic commands like nslookup, dig, and traceroute. The goal is to identify the root cause, whether a DNS server failure, a network issue, or something else. By using the right tools and techniques, administrators can quickly identify and fix DNS-related problems, ensuring seamless access to websites and online services.
Common DNS Issues
Before we dive into the tools and commands, let’s understand the most common DNS issues that most administrators often encounter:
- DNS Downtime: This occurs when DNS servers that translate domain names are temporarily unavailable.
- Incorrect DNS Configuration: This involves errors in the setup of DNS settings which may lead to problems accessing certain websites or the internet.
- DNS Cache Poisoning: Also known as DNS Spoofing, it refers to fraudulent entries in the DNS cache, causing traffic to be directed to the wrong place.
- DNS Propagation Delays: This happens when you make changes to your DNS records and they are not immediately effective due to the time taken to update network servers around the globe.
Now that we have a basic understanding of common DNS issues, let’s explore the essential DNS troubleshooting commands that can help you diagnose and resolve these problems.
DNS Troubleshooting Tools
There are plenty of tools that you can use. The
tools can be specific for Linux, Windows, or Mac OS, or they can be
browser-based. Most of the tools that we will show you overlaps in
functionality, and it will be your decision which one you would use in the
future.
Before you start with the DNS troubleshooting, check if the problem is only local. If you are trying to access your website, but you are getting this message “DNS_PROBE_FINISHED_NXDOMAIN” the problem might be in your device. We recently wrote a way to fix it. Go and read the article.
Dig command
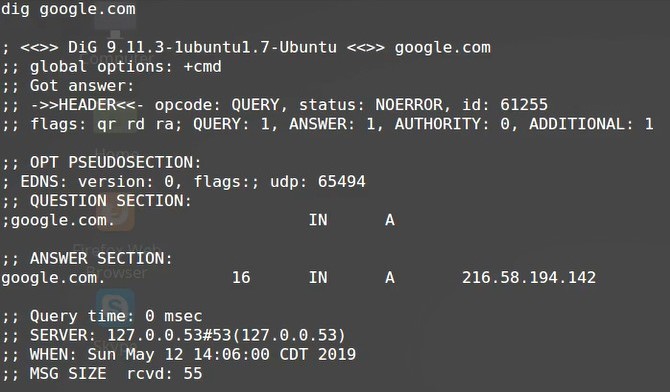
The ‘dig’ command, which stands for ‘Domain Information Groper,’ is a handy command-line tool used in the DNS name resolution process. It sends a DNS query to a specified DNS server and gets a response. It’s a useful tool for finding DNS-related issues.
With this command you can see all the DNS records. You can use it on Linux and Mac OS, but you can search for a port for Windows too. A typical dig command will show you an Authority Section. You can see if the DNS is pointing correctly.
Use it with +trace in dig +trace combination “dig +trace YOURDOMAIN” to see the whole route of your query. This way you can locate the exact problem.
ClouDNS Free DNS tool
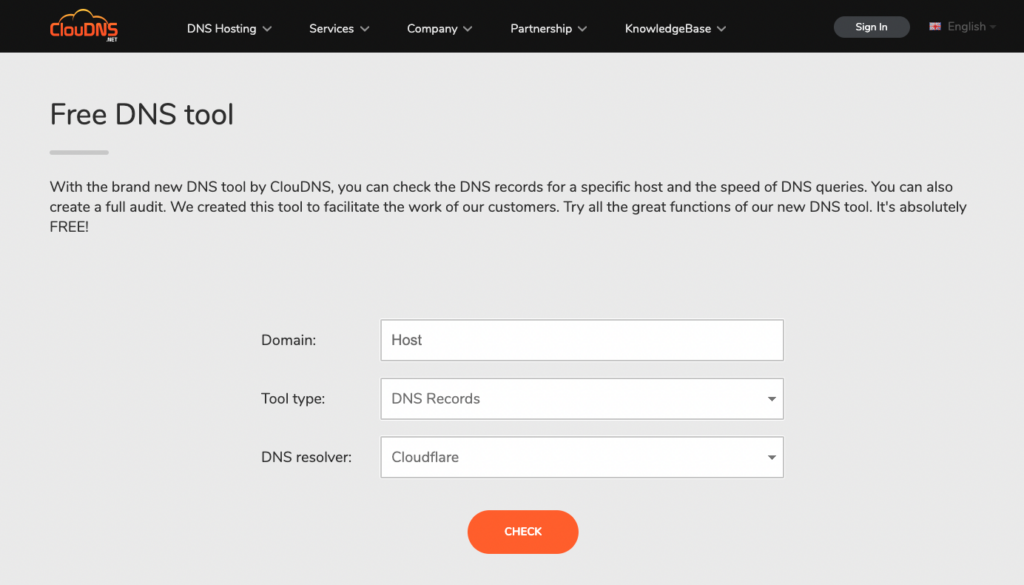
ClouDNS brings to you a valuable Free DNS tool that has transformative capabilities to enhance your DNS troubleshooting tactics. With this tool, you can inspect the DNS records for a specific host and assess the speed of DNS queries. Aside from these, you can also create a comprehensive audit, a feature that helps in in-depth analysis and identification of problematic areas.
Designed to facilitate the work of their customers, the ClouDNS Free DNS tool is user-friendly and accessible, making DNS troubleshooting a breeze even for beginners in the field. All you need to do is enter your domain and host into the tool, select the tool type as “DNS Records”, and choose ‘Google’ as your DNS resolver, then hit ‘CHECK’.
What’s more, this powerhouse tool is free of cost, making it a stellar choice for efficient network management. The value it provides, particularly in terms of insight into DNS records and query speed, can go a long way in troubleshooting DNS-related problems swiftly and effectively.
Experience Industry-Leading DNS Speed with ClouDNS!
Ready for ultra-fast DNS service? Click to register and see the difference!
Traceroute
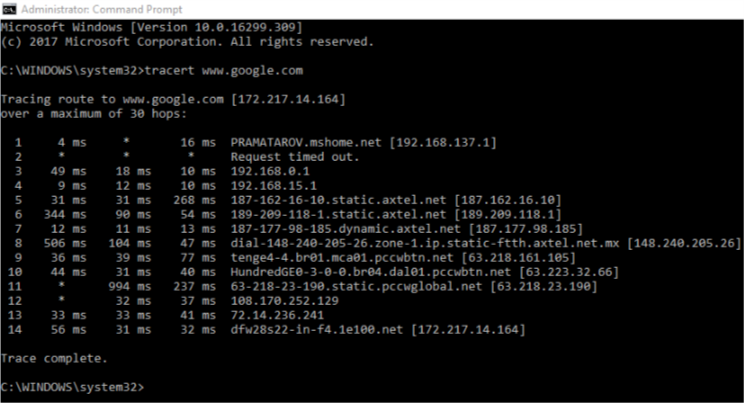
The ‘traceroute’ command enables you to track the pathway that a packet takes from the host to the destination server. As the name suggests, this will be ideal for checking the entire route of a DNS query. You can use it on Windows as Tracert, Linux and Mac OS as traceroute. You can try it with a domain or IP address, and you will see a result with all the hops and response time.
NSLookup
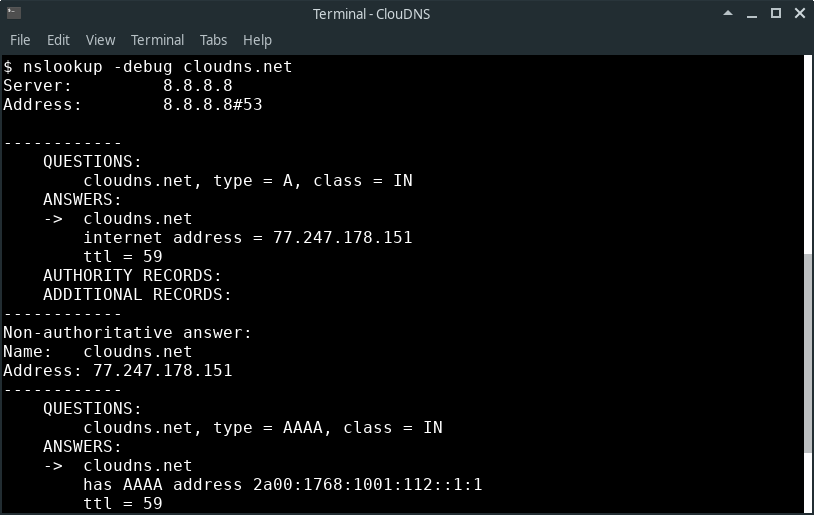
‘NSLookup‘ stands for ‘Name Server Lookup’. This command-line tool is used for obtaining information about DNS settings. It allows users to enter a host name and find out the corresponding IP address, or vice versa.
This command lets you check any type of DNS record. You can use it to see all the available DNS records, or you can look for a specific type like – A, AAAA, SOA, MX, PTR, NS, etc. You can use it to troubleshoot a domain using a particular port too.
Host command
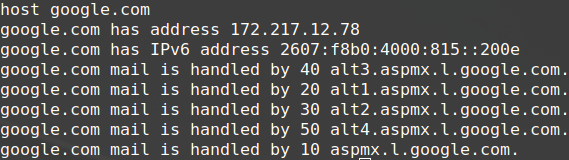
‘Host’ command is very similar to the NSLookup but available only on Linux. You have to write the commands in the Terminal, and you can see the different types of DNS records.
One thing that you can troubleshoot if you have problems with your emails are the TXT records. You can see if there is a SPF record. It is a TXT record that prevents spoofing and stops your outgoing emails from going directly into the spam folder.
Generate SPF record for free!
Why is DNS Troubleshooting So Important?
DNS is the backbone of the internet, enabling seamless access to websites, emails, and online services. When DNS issues arise, they can cause website downtime, slow browsing, failed email deliveries, and security vulnerabilities. Businesses rely on DNS for uninterrupted operations, and any failure can lead to lost revenue and customer trust. Troubleshooting DNS problems ensures fast DNS resolution, minimal downtime, and optimal performance. Additionally, identifying and fixing DNS misconfigurations helps enhance security, preventing threats like DNS spoofing. Regular DNS monitoring and troubleshooting are crucial for maintaining a smooth and secure online experience.
Conclusion
There are plenty of useful tools that you can
use for DNS troubleshooting. Try all of these and find the right one for you
and your problem. Many overlaps in functionality, but have some small
differences that can help you in a specific case.
As you saw, there are utilities for every
operating system so that you can find the problem easily. After you see where
the problem is, it is easy to fix it.
(Visited 10,286 times, 1 visits today)
Summary
Article Name
DNS Troubleshooting
Description
Your DNS is not working well, and you have no idea what is happening. It is time for DNS troubleshooting. There are plenty of options that could help you discover the DNS problem. We will show you the most popular and practical for your needs.
Author
Martin Pramatarov
Publisher Name
ClouDNS.net
Enjoy this article? Don’t forget to share.
Tags: Dig, dig command, Dig+trace, DNS, DNS computer, DNS problems, DNS tools, DNS trace, DNS troubleshooting, Host command, nslookup, nslookup cmd, nslookup commands, Ping, ping command, Traceroute, Tracert Last modified: March 19, 2025
- Can you trace DNS?
- How do I run a DNS Trace?
- What does the nslookup command reveal?
- How do I trace DNS requests in Windows?
- What is a DNS Trace?
- What my DNS is?
- How do I find my DNS resolution?
- How do I check DNS issues?
- How do I find my authoritative DNS server?
- What is netstat command?
- What is the result of nslookup?
- Can you Nslookup a IP address?
Can you trace DNS?
Using DNS trace, you can troubleshoot your DNS. You can use it on Linux OS, Mac OS and even on Windows (using Cygwin). You will trace the road of a DNS query. If there is a problem, you will see exactly where it is.
How do I run a DNS Trace?
How To Use NSLOOKUP to View Your DNS Records
- Launch Windows Command Prompt by navigating to Start > Command Prompt or via Run > CMD.
- Type NSLOOKUP and hit Enter. …
- Set the DNS Record type you wish to lookup by typing set type=## where ## is the record type, then hit Enter. …
- Now enter the domain name you wish to query then hit Enter..
What does the nslookup command reveal?
nslookup (from name server lookup) is a network administration command-line tool for querying the Domain Name System (DNS) to obtain domain name or IP address mapping, or other DNS records.
How do I trace DNS requests in Windows?
Tracing DNS Queries on Your Windows DNS Server
- Step 1: Configure the Wildcard DNS Record. This should be done regardless, as it tends to mitigate the above wildcard and LLMNR/NBNS based poisonings. …
- Step 2: Enable Advanced Logging. Once the wildcard record has been created, we will enable Debug Logging. …
- Step 3: Reviewing the Log. …
- Step 4: Parsing With PowerShell.
What is a DNS Trace?
This function will trace the DNS delegation for a domain name from the Internet DNS root servers down to the DNS servers responsible (authoritative) for the domain. Just like a DNS server resolving a domain name, this function will pick DNS servers in random order (given multiple choices). …
What my DNS is?
Your DNS server can be configured in the network settings of your Operating System. If you don’t configure DNS in your Operating System, then you can set it in the router. If you don’t set it in the router, then your ISP decides which DNS server you use.
How do I find my DNS resolution?
Released with Windows 2000 and later versions, Nslookup is a command-line tool that lets you test and troubleshoot Domain Name System (DNS) resolution. To start nslookup, open a command prompt and enter nslookup, see Figure A. Nslookup will display the machine’s default DNS server and IP address.
How do I check DNS issues?
A quick way to prove that it is a DNS issue and not a network issue is to ping the IP address of the host that you are trying to get to. If the connection to the DNS name fails but the connection to the IP address succeeds, then you know that your issue has to do with DNS.
A list of DNS servers authoritative for the domain is shown in the Name Server (NS) record. To find this record, you can use the NSLOOKUP tool. Read the Knowledge Base article on How do I use the NSLOOKUP tool provided with Windows? for more information.
What is netstat command?
The netstat command generates displays that show network status and protocol statistics. You can display the status of TCP and UDP endpoints in table format, routing table information, and interface information. The most frequently used options for determining network status are: s , r , and i .
What is the result of nslookup?
NSLookup allows you to change the nameserver you query, to ensure you query a nameserver from which you are guaranteed to get an accurate result. If you query the nameserver listed against the domain name you will receive an authoritative answer, because the nameserver has authority over the DNS for the domain name.
Can you Nslookup a IP address?
nslookup is a simple but very practical command-line tool, which is principally used to find the IP address that corresponds to a host, or the domain name that corresponds to an IP address (a process called “Reverse DNS Lookup”). … The name nslookup stands for “name server look up.”
| All Utilities |
| Password Tools |
| System Tools |
| Browser Tools |
| Programmer Tools |
| Network Tools |
| Outlook/Office |
| 64-bit Download |
| Panel |
| Forensics |
| Pre-Release Tools |
| Articles |
DescriptionDNSLookupView is a DNS tracing tool for Windows 10 and Windows 11 that allows you to view the details of every DNS query sent through the DNS Client service of Windows. 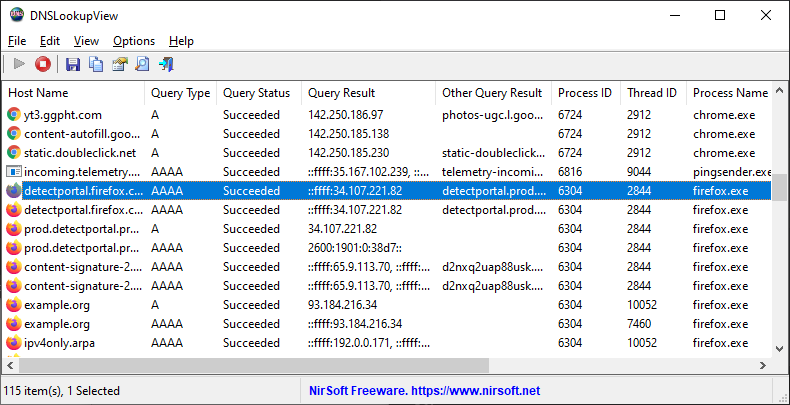
System RequirementsThis tool works only on Windows 11, Windows 10, and Windows 8.1. Both 32-bit and 64-bit systems are supported. This tool doesn’t work on older versions of Windows, because How it works ?This tool uses the event tracing of Windows operating system with the ‘Microsoft-Windows-DNS-Client’ provider ( 1C95126E-7EEA-49A9-A3FE-A378B03DDB4D ). The captured event ID is 3008, which contains the information about every DNS query Version History
Start Using DNSLookupViewDNSLookupView doesn’t require any installation process or additional DLL files. In order to start using it, simply run the executable file — DNSLookupView.exe Command-Line Options
Translating DNSLookupView to other languagesIn order to translate DNSLookupView to other language, follow the instructions below:
LicenseThis utility is released as freeware. DisclaimerThe software is provided «AS IS» without any warranty, either expressed or implied, FeedbackIf you have any problem, suggestion, comment, or you found a bug in my utility, Download DNSLookupView DNSLookupView is also available in other languages. In order to change the language of
|
