Protecting your devices from malicious software helps prevent data breaches and minimizes business disruptions. Protection that’s built into your device, like tamper protection for Windows 10, provides an additional layer of security to safeguard your endpoints.
What is tamper protection in Windows 10?
Part of Windows Security, tamper protection for Windows 10 helps protect your system against unauthorized changes and modifications by preventing malicious software or users from tampering with critical system settings, files and processes. Enabling tamper protection adds extra security to your Windows 10 system, making it more resistant to attacks and unauthorized access.
Enforce and mandate tamper protection for your Windows endpoints with NinjaOne, a comprehensive RMM solution that streamlines security management.
Learn more about NinjaOne Endpoint Management
The importance of tamper protection for Windows 10 system security
An important security feature in Windows 10, tamper protection prevents critical system files and settings from being changed without your permission. This helps keep your computer safe from viruses, hackers and other cyber threats. It also protects your privacy by reducing the risk of your sensitive information being stolen or misused.
The program also makes it harder for harmful programs to mess with critical system components like your antivirus software, firewall and user account settings. By keeping them working properly, tamper protection creates a safer environment for your Windows 10 computer.
Tamper protection also prevents unauthorized access to your private information by stopping malicious software from changing settings and files that could expose your personal data. It locks down core security components of your Windows 10 system and blocks unauthorized changes that could open vulnerabilities and expose your computer to security threats or privacy breaches.
How to enable tamper protection: step-by-step
Tamper protection for Windows 10 is enabled by default but may be turned off at some point by an administrator. If you need to enable tamper protection in Windows 10, it’s a straightforward process with these step-by-step instructions:
- Open the Windows Security app by clicking on the Start menu and typing “Windows Security.”
- Select “Windows Security” from the search results to open the app.
- In the Windows Security app, click on the “Virus & threat protection” tab.
- Under the “Virus & threat protection settings,” click on “Manage settings.”
- Scroll down to the “Tamper Protection” section and toggle the switch to enable it.
- Once enabled, tamper protection will provide an additional layer of security.
Enabling tamper protection and leaving it on enhances the security of your Windows 10 system.
Should I turn off tamper protection in Windows 10?
While tamper protection is an important security feature, there are times when you need to disable it temporarily. For example, you’ll need to disable tamper protection for Windows 10 when installing or updating third-party security software, troubleshooting or changing security settings or uninstalling security components.
Although you should turn off tamper protection in Windows 10 for certain operations, remember that leaving it disabled can make your system vulnerable to attacks. If you need to temporarily disable tamper protection, make sure to enable it again as soon as you finish.
How to disable tamper protection
If you want to disable tamper protection on your Windows 10 system, there are multiple methods you can use. Here are three ways to disable tamper protection:
Through Windows Security
One way to disable tamper protection in Windows 10 is through the Windows Security app:
- Open the Windows Security app by clicking on the Start menu and typing “Windows Security.”
- Select “Windows Security” from the search results to open the app.
- In the Windows Security app, click on the “Virus & threat protection” tab.
- Under the “Virus & threat protection settings,” click on “Manage settings.”
- Scroll down to the “Tamper Protection” section and toggle the switch to disable it.
Remember to enable tamper protection again once you have finished the tasks that require it to be turned off.
Re-enabling tamper protection
When you no longer need tamper protection disabled, re-enable it promptly by following the same steps outlined in the section on how to enable tamper protection step-by-step. Turning tamper protection on helps keep your Windows 10 system secure and protected against unauthorized changes or modifications.
Managing tamper protection for your company with Microsoft InTune
If you’re changing tamper protection, you probably need to manage it across several devices in your organization. To manage several devices at once, rather than touching each device, you can use Microsoft Intune. Microsoft InTune is a cloud-based endpoint management platform that allows you to manage and secure devices, applications and data across many devices from a central console. Microsoft InTune lets you enforce tamper protection policies, ensuring that all devices adhere to the organization’s security standards and improving your overall security posture.
NinjaOne integrates with robust endpoint security tools. This, along with tamper protection helps strengthen your endpoints’ security posture.
See how NinjaOne keeps your endpoints secure
Manage all of your endpoints with ease
Tamper protection in Windows 10 protects not only your Windows Security features and settings but also helps you maintain consistent security configurations in a large IT environment. The most efficient way to manage tamper protection across all your devices is with an endpoint management tool that allows you to monitor and secure all devices in your organization, including desktop computers, laptops, smartphones and tablets.
A comprehensive endpoint management solution like NinjaOne provides advanced endpoint management capabilities, allowing you to centrally manage, secure and monitor all your devices from a single platform.
With NinjaOne, you can ensure that all your endpoints are up-to-date with the latest security patches, have the necessary antivirus protection and adhere to your organization’s security policies. NinjaOne also helps you manage your antivirus solution, with granular control over schedules and scans, encrypt your endpoint drives, back up device data and prevent remote attacks by identifying and removing rogue endpoints.
NinjaOne’s endpoint management solution helps increase security and efficiency in managing your organization’s endpoints. Ready to take your endpoint management to the next level? Experience increased security and efficiency with NinjaOne’s comprehensive endpoint management solution. Learn more about how you can increase security with NinjaOne’s endpoint management today.
One of the greatest threats to enterprise PCs is malware — or even innocuous applications — that tamper with system configuration settings and potentially create new vulnerabilities and weaken the system against future attacks.
With the Windows 10 1903 release, Microsoft introduced Tamper Protection to the Windows Security application, which enables IT admins to make it more difficult for other applications to alter sensitive security settings on the PC. There are some caveats to using Tamper Protection in Windows 10, however, so IT admins should understand how it works.
What is Tamper Protection in Windows 10?
When enabled, Tamper Protection prevents changes to important system security configuration settings — especially changes that are not made directly through the Windows Security application. The goal is to prevent malicious software — or even third-party applications — from changing important security settings in Windows Defender Antivirus and other tools. Tamper Protection is available for both Home and Enterprise versions of Windows 10.
When Tamper Protection is enabled, outside applications will no longer be able to change settings for real-time protection, which is part of the antimalware scanning feature of Microsoft Defender ATP; settings for Microsoft’s Windows Defender Antivirus cloud-based malware protection services; settings for IOfficeAntiVirus, which affects how suspicious files such as internet downloads are handled; settings for behavior monitoring in real-time protection, which can stop suspicious or malicious system processes; and it prevents deleting security intelligence updates or turning off Windows Defender antimalware protection entirely.
There are several important considerations with Tamper Protection. First, Tamper Protection does not prevent administrators from making changes to important security settings directly through the Windows Security application; Tamper Protection simply prevents third-party applications from changing those Windows settings. Second, Tamper Protection does not prevent or control how third-party antivirus or antimalware applications interoperate with the Windows Security application.
Enabling and disabling Tamper Protection on an individual machine
Users with Windows 10 computers not managed by the organization»s IT staff can use the Windows Security application to turn Tamper Protection on or off as needed. This is a common scenario in remote or BYOD (bring your own device) environments.
Users will still need admin-level permissions on the system to change security settings, but computer owners usually possess admin-level access. Once logged into the computer, users can quickly access Tamper Protection with the following steps:
- Access the Taskbar and type defender into the search bar on the Taskbar.
- Select the Windows Security app from the search results.
- Select Virus and threat protection.
- Choose Virus and threat protection settings.
- Locate the Tamper Protection toggle and choose On or Off as desired.
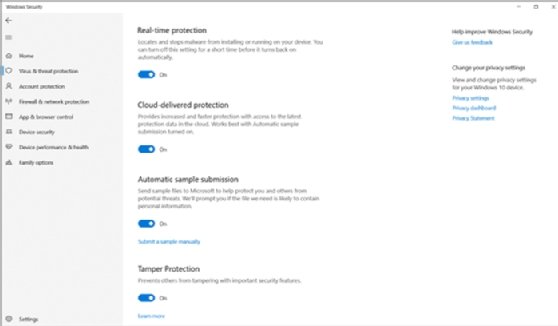
The Tamper Protection toggle should be visible, and administrators should be able to click on the toggle to turn it off or on. If the toggle is not visible, IT may need to update Windows 10. If Tamper Protection is turned off, users will see a small yellow warning symbol in the Windows Security application by the Virus & Threat Protection entry.
Enabling and disabling Tamper Protection for your whole organization
There is generally no need to disable Tamper Protection in Windows 10 unless it affects other validated tools.
When an IT organization is responsible for managing a fleet of Windows 10 user endpoints, IT admins can use Microsoft Intune to turn Tamper Protection on or off for all those managed computers through the Microsoft Endpoint Manager admin center portal. Administrators will need the correct permissions, such as global or security admin, to make changes to Tamper Protection.
Before accessing Tamper Protection, the organization must meet the following requirements:
- It must have the appropriate Intune licenses, such as Microsoft 365 E5.
- Windows 10 computers must be running versions 1709, 1803, 1809 or later.
- Organizations must use Windows security with security intelligence updated to version 1.287.60.0 or later.
- All machines must be using antimalware platform version 4.18.1906.3 and antimalware engine version 1.1.15500.X (or later).
With all requirements met, the actual process of accessing Tamper Protection is similar to accessing it for individual users:
- Access the Microsoft Endpoint Manager admin center and sign in with the appropriate credentials.
- Select Devices and choose Configuration Profiles.
- Create a profile with the following characteristics:
Platform: Windows 10 and later
Profile type: Endpoint protection
Category: Microsoft Defender Security Center
Tamper Protection: Enabled (or Disabled)

There is generally no need to disable Tamper Protection in Windows 10 unless it affects other validated tools. For example, Tamper Protection might block a known third-party tool such as ConfigureDefender from making changes to Windows Defender. Similarly, enterprise PCs that IT manages with comprehensive software installation policies may not require Tamper Protection.
Using PowerShell to check Tamper Protection
Windows PowerShell isn’t just a powerful and versatile scripting platform; it’s also a management console capable of changing and checking vital settings within a system or environment. PowerShell uses a vast array of command scripts (called cmdlets) to execute commands and retrieve details. PowerShell can quickly report on the status of Tamper Protection with these steps:
- Launch the PowerShell application.
- Enter the Get-MpComputerStatus PowerShell cmdlet.
- Review the list of results. If the value for IsTamperProtected is true, then Tamper Protection is enabled. If the result is false, Tamper Protection is disabled.
Viewing tampering attempts
Security has little value if tamper attempts or other attacks are left unseen and unreported. Administrators must have some means of monitoring or reviewing the presence of potential attacks such as tampering.
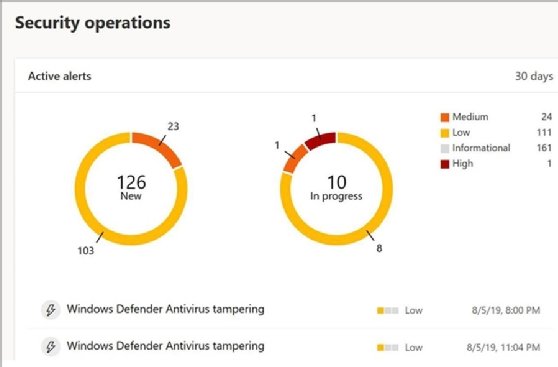
The Microsoft Defender Security Center offers protection though a cloud subscription service called Microsoft Defender for Endpoint. It’s a dashboard that displays security issues that include tamper attempts that are flagged with details logged for further investigation. Organizations will need to subscribe to the Microsoft Defender for Endpoint service.
Does Tamper Protection work with third-party security tools?
Tamper Protection prevents unauthorized changes to Windows Defender Antivirus settings through the system Registry. For example, when Tamper Protection is on, the DisableAntiSpyware group policy key in the Registry cannot disable Windows Defender Antivirus.
Some third-party security products, however, can make valid changes to security settings. Tamper Protection does work with third-party security products, and should ideally allow those validated third-party products to modify the settings guarded by Tamper Protection.
Tamper Protection uses real-time threat information to determine the potential risks of software and suspicious activities. IT can prevent «false positives» from Tamper Protection by accessing the Windows Security dialog and updating security intelligence to version 1.287.60.0 or later. Once IT admins update the system, Tamper Protection should continue to protect the system security settings in the Registry and log any attempts to modify those settings without generating errors.
Does Tamper Protection work with endpoint management tools?
Tamper Protection does work with endpoint management tools, but there are limits. The entire point of Tamper Protection is to prevent outside tools from changing Windows Security protection settings. With Tamper Protection on, administrators can potentially establish a centralized setting for Tamper Protection using management tools, but those other tools and platforms cannot change settings protected by Tamper Protection. Admins would need to manage those protection settings through Windows Security.
Unified endpoint management platforms such as Microsoft Intune, enterprise configuration management applications such as System Center Configuration Manager, command-line instructions or scripts, the Windows System Image Manager configuration, Group Policy, and any other Windows Management Instrumentation tools and administrative roles cannot override Tamper Protection.
An organization with a Windows enterprise-class license, such as a Microsoft Defender ATP license, or computers running Windows 10 Enterprise E5 must opt in to global Tamper Protection. IT can only manage the feature through an Intune management console, which prevents local users from overriding Tamper Protection on managed systems.
Рекомендуем: Что нового в Майском обновлении Windows 10 — 2019 года (версия 1903).
Одна из лучших особенностей Microsoft — это то, что они пытаются создать более надежную систему безопасности для своих ОС. Защита от несанкционированного доступа призвана добавить больше ключевых функций в защиту наших данных.
Защита от подделки (Tamper Protection) — это новый параметр, доступный в приложении «Безопасность Windows», он обеспечивает дополнительную защиту от изменений ключевых функций безопасности, включая ограничение изменений, которые не вносятся непосредственно через приложение, другими словами — Запрещает другим вмешиваться в важные функции безопасности системы.
«Защита от подделки» в приложении «Безопасность Windows».
Если вы являетесь домашним пользователем, вы можете включить этот параметр в области настроек защиты от вирусов и угроз в приложении «Безопасность Windows». Если вы корпоративный пользователь, вы можете использовать управление Intune для централизованного управления настройками безопасности.
Защита от несанкционированного доступа предотвращает определенные изменения во всех функциях безопасности, чтобы избежать неправильного использования. Вредоносные программы могут изменять настройки безопасности системы, но при наличии защиты эти изменения будут заблокированы.
Microsoft пока объясняет немногое: нам известен только один сценарий, когда изменения блокируются, если включена защита от несанкционированного доступа, но есть и другие.
Включить или отключить функцию «Защита от подделки».
Используйте клавиши Win + I, чтобы быстро открыть приложение «Параметры» и перейдите в раздел «Обновление и безопасность».
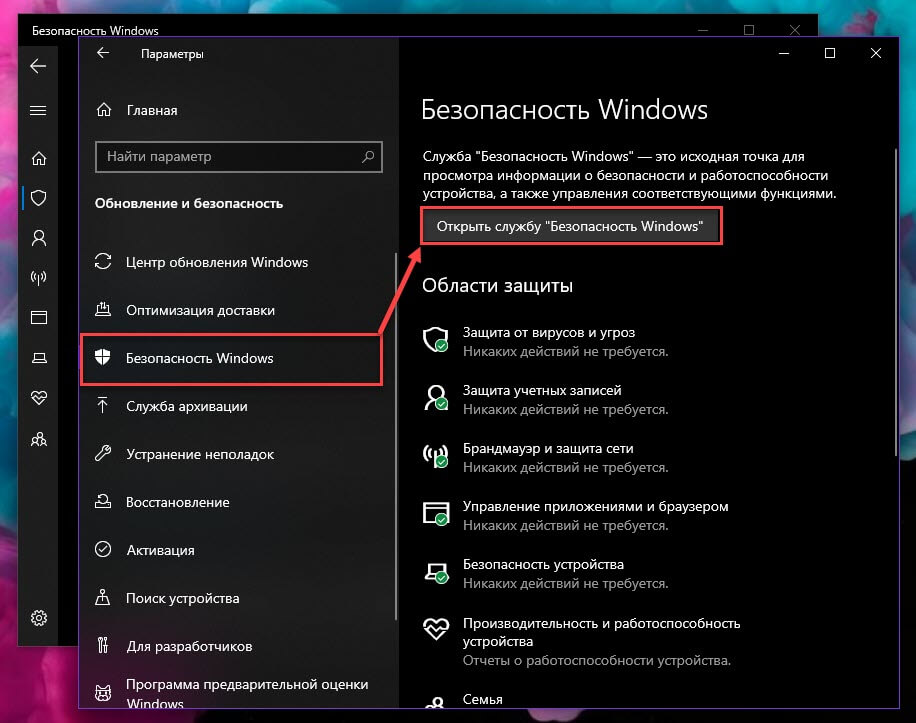
Перейдите в раздел «Безопасность Windows» → «Открыть службу безопасности Windows» → «Защита от вирусов и угроз» → «Настройки защиты от вирусов и угроз» → «Управление настройками».
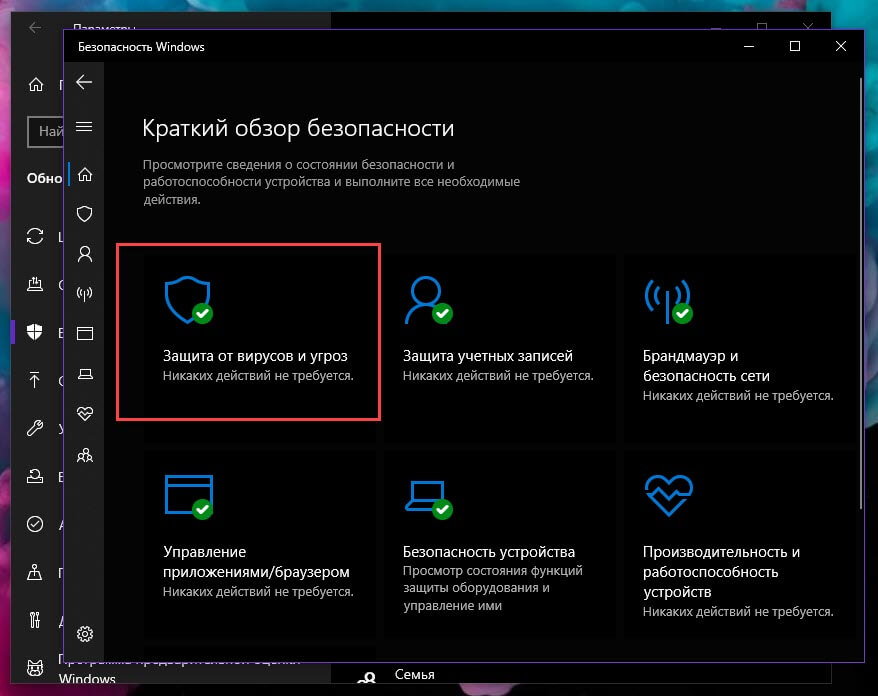
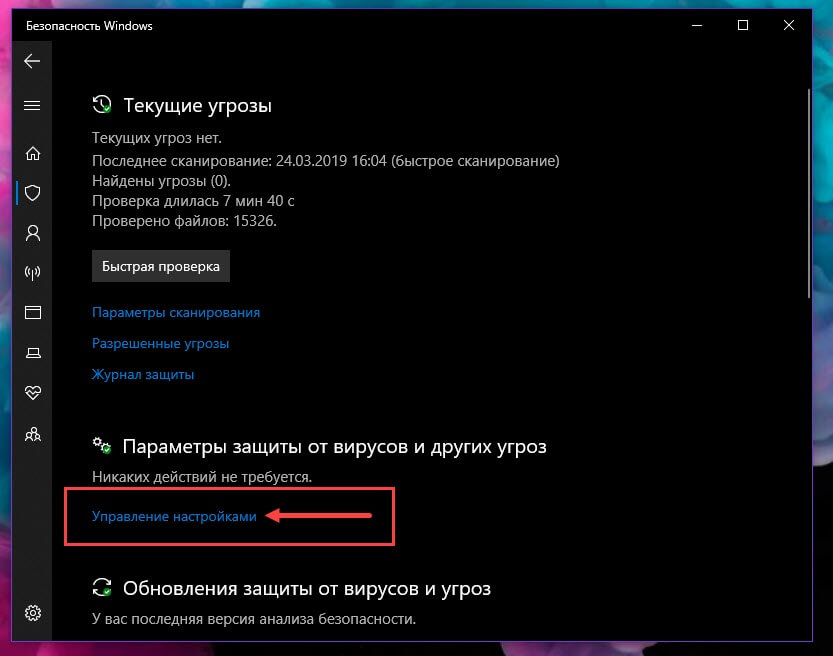
Здесь вы можете включить или отключить новую функцию Windows 10 — «Защита от подделки».
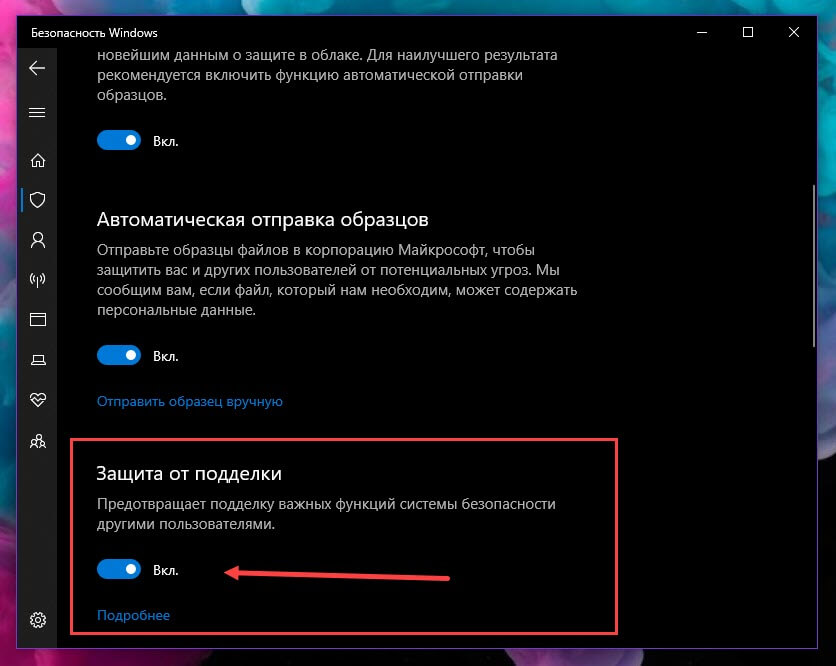
Вероятно, функция будет включена по умолчанию в будущих версиях системы.
Отключение «Защиты от подделки» может быть полезно, если вы используете стороннее программное обеспечение, такое как «Configure Defender», которое может быть заблокировано от внесения изменений в Защитник Windows после обновления Windows 10.
Помимо приложения «Параметры» настройка доступна с помощью редактора реестра.
Следующий параметр реестра определяет, включена ли эта функция:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Features\TamperProtection
- 0: Защита от подделки Отключена.
- 1: Защита от подделки Включена.
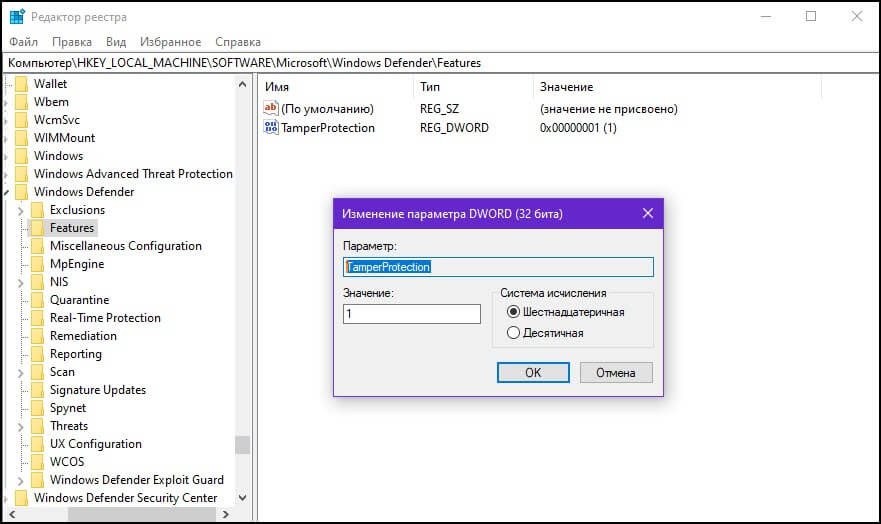
Как новая функция помогает защитить систему?
Вы получаете защиту в режиме реального времени на основе Microsoft Defender ATP — защиты следующего поколения. Это препятствует любому вмешательству в важные функции безопасности. Вы не должны отключать ее.
Возможности:
- Облачное обнаружение вредоносного ПО за считанные секунды.
- Получите IOVA — инструмент обнаружения подозрительных файлов в Интернете.
- Инструмент мониторинга поведения, который обнаруживает подозрительное поведение в активных приложениях.
- Защита от подделки также предотвращает удаление или отключение Защитника Windows.
- Для корпоративных клиентов (например, с лицензией Microsoft Defender ATP), эта функция будет включена и управляться только с помощью консоли управления Intune. Пользователи с правами локального администратора устройства не смогут изменить настройки. Это гарантирует, что даже вредоносные приложения — или злоумышленники — не смогут локально переопределить настройку.
Заключительные слова
Недостаток информации затрудняет оценку эффективности новой защитной функции. Еще неизвестно, насколько она эффективна. Полная функциональность будет доступна вместе с выпуском Windows 10 v1903 ожидаемым в мае 2019 года.
Теперь вы: Какое решение безопасности вы используете в Windows? Нужна ли вам дополнительная функция безопасности?
Windows 10 Tamper Protection is a vital security feature designed to protect your computer from unauthorized changes and tampering. It acts as a safeguard against malware and other malicious activities that may attempt to modify critical system settings or disable security features. With Tamper Protection enabled, your Windows 10 device becomes more resilient to attacks, ensuring the integrity and stability of your system.
By enabling Tamper Protection, you can improve the security of your Windows 10 device by preventing unauthorized access and modification to important settings, including Windows Defender Antivirus and real-time protection. This feature adds an additional layer of defense, helping to keep your computer safe from malware, ransomware, and other cyber threats. With Tamper Protection in place, you can have peace of mind knowing that your system is better protected against potential vulnerabilities and attacks.
Windows 10 Tamper Protection is a security feature that helps protect your device against unauthorized changes. It prevents malicious apps and processes from modifying important system settings, files, and registry keys without your knowledge. Tamper Protection works in the background, silently safeguarding your system and ensuring that critical security features are always active. This helps to enhance the overall security of your Windows 10 device, providing you with peace of mind knowing that your system is protected against tampering attempts.

Understanding Windows 10 Tamper Protection
Windows 10 Tamper Protection is a powerful security feature that enhances the security of your Windows 10 operating system by protecting it against unauthorized changes and tampering. It is designed to safeguard critical system settings and files from being modified or tampered with by malware, unauthorized users, or even some legitimate software that may attempt to make unauthorized changes.
With the increasing sophistication and prevalence of cyber threats, it has become essential to implement robust security measures to protect sensitive data and ensure the integrity of the operating system. Tamper Protection acts as an additional layer of defense, providing enhanced security and preventing malicious actors from gaining control and compromising your system.
In this article, we will explore in detail the capabilities and benefits of Windows 10 Tamper Protection, and how it helps in preventing tampering, unauthorized access, and malicious actions on your Windows 10 device.
1. Protecting Critical System Settings and Files
One of the primary functions of Windows 10 Tamper Protection is to safeguard crucial system settings and files from unauthorized modifications. This includes protecting essential configuration files, registry keys, and critical system components that could be targeted by malware or unauthorized users to gain control over your system.
Tamper Protection ensures that even if a malicious entity gains access to your system, they will be unable to modify or tamper with these critical components. This helps to maintain the integrity of your operating system and prevents unauthorized changes that could potentially lead to system instability or compromise.
The protected system settings and files include critical security configurations, such as Windows Defender settings, Windows Firewall configurations, and other security-related components. By protecting these settings, Tamper Protection actively defends against attempts to disable or modify security features, ensuring that your system remains secure and protected.
In addition to protecting critical system files, Tamper Protection also guards against unauthorized modifications to important system-level registry keys. The registry is a central component of the Windows operating system that stores vital configuration settings for various applications and system functions. Preventing tampering with registry keys helps to maintain the stability and reliability of your system.
1.1 Enhancing System Security
By protecting critical system settings and files, Windows 10 Tamper Protection plays a vital role in enhancing the overall security of your system. It acts as a proactive defense mechanism, preventing unauthorized changes that can compromise the integrity of your operating system and put your sensitive data at risk.
Unauthorized modifications to system settings can potentially lead to the disabling of security features, such as antivirus software or firewalls, making your system vulnerable to malware attacks. Tamper Protection ensures that these essential security configurations remain intact, providing continuous protection against known and emerging threats.
Moreover, by protecting important registry keys, Tamper Protection prevents unauthorized changes that could impact system stability and performance. This helps to maintain a reliable and secure computing environment, free from potential disruptions caused by tampering or unauthorized modifications.
1.2 Preventing Unauthorized Access
Windows 10 Tamper Protection not only protects against unauthorized modifications but also prevents unauthorized access to system settings and files. It restricts changes that could potentially grant inappropriate privileges or access to sensitive data.
Even if an attacker gains administrative privileges on your system, Tamper Protection ensures that they cannot modify critical security configurations or gain additional privileges that would enable them to escalate their access or compromise the system further.
By controlling access and protecting system settings, Tamper Protection acts as a gatekeeper, ensuring that only authorized changes can be made and that unauthorized users or malicious software cannot gain control over your system.
Furthermore, it helps protect your personal and sensitive data by preventing unauthorized access to files and folders that contain private information. This adds an additional layer of security, especially for users who share their system with others or use it in a public environment.
1.3 Safeguarding System Integrity
Tamper Protection plays a crucial role in maintaining the overall integrity of your Windows 10 system. By preventing unauthorized modifications to critical system settings and files, it ensures that your system operates as intended and remains free from unauthorized changes that could result in system instability.
Unauthorized modifications to system files and settings can lead to a variety of issues, including application crashes, system errors, and even complete system failure. Tamper Protection prevents these issues by safeguarding the integrity of critical components, minimizing the risk of system instability.
Additionally, by protecting system-level registry keys, Tamper Protection helps maintain the integrity of various applications and system functions that rely on these keys for proper operation. This ensures that your system functions optimally and that authorized changes can be made without the risk of disruption or instability.
Overall, Windows 10 Tamper Protection provides robust protection against unauthorized modifications, preventing tampering, unauthorized access, and potential compromises to the security and stability of your Windows 10 system.
2. Real-time Threat Detection and Response
Another important aspect of Windows 10 Tamper Protection is its real-time threat detection and response capabilities. It continuously monitors the system for suspicious or malicious activities and takes immediate action to mitigate any potential threats.
By leveraging advanced threat intelligence and behavioral analysis, Tamper Protection can identify and neutralize emerging threats in real-time, providing a proactive defense against malware, ransomware, and other malicious activities.
When Tamper Protection detects a potential threat or suspicious activity, it takes appropriate actions to protect the system. These actions may include blocking or quarantining malicious files, terminating suspicious processes, or notifying the user about the detected threat.
This real-time threat detection and response capability enhances the overall security of your system by ensuring that any potential threats are promptly identified and neutralized, minimizing the risk of damage or compromise to your system and data.
2.1 Proactive Defense Against Emerging Threats
Windows 10 Tamper Protection employs advanced threat intelligence and behavioral analysis to detect and proactively defend against emerging threats. It constantly monitors the system for indicators of compromise, allowing it to identify and mitigate new and unknown threats.
This proactive defense mechanism ensures that your system remains protected even against the most sophisticated and evasive malware attacks. Tamper Protection leverages the latest threat intelligence and security updates from Microsoft to stay up to date with emerging threats, providing you with a robust defense against evolving cyber threats.
By using behavioral analysis, Tamper Protection can identify suspicious activities or patterns that may indicate the presence of malware or other malicious actions. This allows it to take immediate action to stop the threat and protect your system before any damage occurs.
2.2 Prompt Response to Suspicious Activities
Tamper Protection ensures a prompt response to any suspicious activities detected on your system. When it identifies a potential threat, it takes immediate action to mitigate the risk and protect your system from further harm.
These actions can include blocking or quarantining malicious files, terminating processes associated with the threat, or isolating the affected area to prevent the spread of malware or unauthorized activities.
Furthermore, Tamper Protection provides real-time notifications to users, alerting them about detected threats, and providing guidance on how to handle the situation. This ensures that users are aware of the potential risks and can take appropriate actions to protect their system and data.
3. Securing Windows Defender and Security Features
Windows 10 Tamper Protection also plays a crucial role in securing Windows Defender, the built-in antivirus and antimalware solution provided by Microsoft. Tamper Protection ensures that Windows Defender remains active and cannot be disabled or tampered with by unauthorized users or malware.
By protecting Windows Defender configurations and files, Tamper Protection prevents malware or unauthorized users from disabling or modifying critical security settings of the antivirus software.
Windows Defender is a key component of the overall security of your system, providing real-time protection against malware, ransomware, and other malicious activities. By ensuring that Windows Defender remains active and its configurations intact, Tamper Protection helps to maintain a strong defense against cyber threats.
In addition to protecting Windows Defender, Tamper Protection also secures other security features and components of the Windows operating system. This includes protecting Windows Firewall configurations, preventing unauthorized changes to firewall rules and settings that could potentially expose your system to security risks.
3.1 Protection Against Disabling Security Features
One of the primary goals of Windows 10 Tamper Protection is to prevent the disabling or modification of critical security features. This includes safeguarding antivirus software, such as Windows Defender, to ensure continuous protection against malware and other threats.
Malware often attempts to disable or tamper with antivirus software to evade detection and carry out malicious activities. Tamper Protection blocks these attempts, ensuring that the antivirus software remains active and capable of detecting and neutralizing threats.
By protecting Windows Firewall configurations, Tamper Protection also prevents unauthorized changes that could weaken the security of your system. Windows Firewall acts as a barrier between your system and the external network, controlling the incoming and outgoing network traffic to protect against unauthorized access and malware.
Ensuring the integrity of Windows Firewall settings helps to maintain the overall security of your system and prevent unauthorized access or data breaches.
3.2 Continuity of Built-in Security Features
Tamper Protection ensures the continuity of the built-in security features of Windows 10. By protecting critical security configurations, it guarantees that the security features function as intended and provide continuous protection against evolving cyber threats.
Disabling or modifying security features can leave your system vulnerable to various attacks, including malware infections, data breaches, and unauthorized access. Tamper Protection prevents these security features from being tampered with, ensuring that your system remains protected at all times.
This continuity of built-in security features is essential for maintaining the overall security of your system and protecting your sensitive data from unauthorized access or compromise.
4. Integration with Microsoft Defender Advanced Threat Protection
An important aspect of Windows 10 Tamper Protection is its integration with Microsoft Defender Advanced Threat Protection (ATP). ATP is an enterprise-level endpoint security solution offered by Microsoft that helps protect against advanced and targeted attacks.
Tamper Protection enhances the capabilities of ATP by providing additional protection against unauthorized changes and tampering on Windows 10 devices. It ensures that the security configurations and critical files protected by Tamper Protection cannot be modified or tampered with, even by advanced and persistent attackers.
The integration of Tamper Protection with ATP provides organizations with a comprehensive defense against advanced threats, helping to prevent unauthorized access, data breaches, and compromise of sensitive information.
By leveraging the collective intelligence and advanced detection capabilities of Microsoft Defender ATP, Tamper Protection can detect and respond to sophisticated attacks, even in real-time. This integration significantly enhances the security posture of organizations and helps them stay protected against emerging threats.
5. Enabling and Configuring Tamper Protection
Windows 10 Tamper Protection is an essential security feature that comes built-in with Windows 10 devices. By default, it is enabled to provide maximum protection against unauthorized changes and tampering.
If you want to verify whether Tamper Protection is enabled on your system or configure its settings, you can do so through the Windows Security app or the Windows Defender Security Center.
In the Windows Security app, navigate to the «Virus & Threat Protection» section and click on «Virus & Threat Protection Settings.» From there, you can access the Tamper Protection settings and ensure that it is enabled.
It is recommended to keep Tamper Protection enabled at all times to maximize the security of your Windows 10 device. However, if you need to temporarily disable Tamper Protection for a specific reason, you can do so from the Windows Security app by toggling the feature off.
In Conclusion
Windows 10 Tamper Protection is a critical security feature that enhances the overall security and integrity of your Windows 10 system. By protecting critical system settings and files, providing real-time threat detection and response, securing built-in security features, and integrating with Microsoft Defender ATP, Tamper Protection ensures continuous protection against unauthorized changes, tampering, and advanced threats.
Understanding Windows 10 Tamper Protection
Windows 10 Tamper Protection is a security feature included in the Windows Defender Antivirus program. Its primary purpose is to protect the system against unauthorized changes made by malicious software or individuals. This feature is especially crucial in preventing sophisticated malware from disabling or tampering with antivirus software.
When turned on, Windows 10 Tamper Protection ensures that critical system settings, such as Windows Security settings and antivirus configurations, cannot be modified without proper authorization. It effectively acts as a safeguard, preventing malware or unauthorized users from disabling your antivirus protection, modifying registry keys, or making other unauthorized changes to the system.
This feature also enhances the overall security of the system by providing real-time protection against threats, including ransomware and other malicious software that commonly try to disable or tamper with antivirus software. Windows 10 Tamper Protection is designed to work in conjunction with other security features to provide a multi-layered defense against various cyber threats.
By enabling Windows 10 Tamper Protection, users can ensure that their antivirus software remains active and effective, providing continuous protection against the ever-evolving landscape of malware and cyberattacks.
Key Takeaways — What Does Windows 10 Tamper Protection Do
- Windows 10 Tamper Protection is a security feature that helps protect your computer against unauthorized changes.
- It prevents malware and other malicious applications from tampering with critical Windows operating system files and settings.
- Tamper Protection is enabled by default in Windows 10, providing an additional layer of defense against threats.
- It blocks attempts by malware to disable antivirus software or modify security settings.
- Tamper Protection enhances the overall security posture of your computer and reduces the risk of infections and data breaches.
Frequently Asked Questions
Here are some common questions about Windows 10 Tamper Protection:
1. How does Windows 10 Tamper Protection protect my device?
Windows 10 Tamper Protection is a security feature that helps protect your device against unauthorized changes to critical security settings. It prevents malware or other malicious software from tampering with Windows Defender Antivirus, Windows Security Center, and other system components that are crucial for keeping your device secure. By enabling Tamper Protection, you ensure that important security features cannot be easily bypassed or modified.
Furthermore, Tamper Protection also helps protect your device against file system modifications, registry changes, and credential theft attempts, providing an additional layer of defense against sophisticated cyber threats.
2. How do I enable Windows 10 Tamper Protection?
Enabling Windows 10 Tamper Protection is a straightforward process. Here’s how you can do it:
1. Open Windows Security by clicking on the Windows Start button, then selecting Settings > Update & Security > Windows Security.
2. In the Windows Security app, click on «Virus & threat protection» in the left sidebar.
3. Scroll down to the «Virus & threat protection settings» section and click on «Manage settings.»
4. On the next screen, toggle the switch next to «Tamper Protection» to turn it on. The switch should turn blue to indicate that Tamper Protection is now enabled.
Once enabled, Windows 10 Tamper Protection starts protecting your device against unauthorized changes and provides an enhanced level of security.
3. Can I turn off Windows 10 Tamper Protection?
While it is generally recommended to keep Windows 10 Tamper Protection enabled for maximum device security, users do have the option to disable it if necessary. However, it is important to understand the potential risks associated with disabling Tamper Protection.
Disabling Tamper Protection may make your device more vulnerable to malware and other malicious software. It can also leave your critical security settings exposed to unauthorized modifications. It is advisable to consult with an IT professional or Microsoft Support before disabling Tamper Protection to assess the potential impact on your device’s security.
4. Does Windows 10 Tamper Protection work with third-party antivirus software?
Yes, Windows 10 Tamper Protection is designed to work seamlessly with third-party antivirus software. It provides an extra layer of defense to protect critical security settings, regardless of the antivirus program you have installed on your device. By enabling Tamper Protection, you ensure that even if malware attempts to disable or tamper with your antivirus software, it will be unable to do so.
It is important to note that some antivirus programs may have their own built-in tamper protection features. In such cases, it is recommended to consult the documentation or support resources provided by your antivirus software vendor to understand how their product and Windows 10 Tamper Protection work together.
5. How often does Windows 10 Tamper Protection update?
Windows 10 Tamper Protection receives regular updates through Windows Update to ensure it stays up-to-date with the latest security enhancements. The frequency of these updates may vary depending on various factors, including the release schedule of Windows updates and the severity of emerging security threats.
It is generally recommended to keep your device up to date with the latest Windows updates to ensure you have the latest features and security measures, including updates to Windows 10 Tamper Protection.
So, to summarize, Windows 10 Tamper Protection is a security feature that helps protect your computer from unauthorized changes. It prevents malicious software or users from tampering with critical system settings, files, and processes.
Tamper Protection is designed to provide an additional layer of defense against malware and other threats. By enabling it, you can ensure that your system remains secure and that important settings are not altered without your knowledge and consent. With Tamper Protection, you can have greater peace of mind knowing that your Windows 10 computer is better protected against unauthorized access and malicious activities.
,
Windows 10 comes with Windows Defender, which is a built-in antivirus and in which Microsoft has introduced a new security feature called «Tamper Protection» in Windows 10 build 1909 and later versions. When Tamper Protection is enabled in the system, a malware can’t change the settings of the Windows Defender Antivirus. As real-time protection cannot be tampered with, this adds an extra degree of security to the system.
By default, Tamper protection is enabled in Windows 10. If you want to disable tamper protection, this guide covers two different ways to do so.
How to Enable or Disable Tamper Protection on Windows 10.*
- Method 1. Manage Tamper Protection via Defender Settings.
- Method 2. Manage Tamper Protection via Registry.
* Notes:
1. The methods mentioned below can be used to turn on or off the Tamper Protection security on an individual Windows 10 system. If you are an organization using Microsoft Defender for Endpoint, you should be able to manage tamper protection in Intune similar to how you manage other endpoint protection features. For instructions read the corresponding section of the following Microsoft article:
- Manage tamper protection using Intune.
- Manage tamper protection using Configuration Manager, version 2006.
- Manage tamper protection using the Microsoft 365 Defender portal.
2. To see if the Tamper Protection is enabled on your system from PowerShell, open PowerShell as Administrator and type «Get-MpComputerStatus«. Then look if the IsTamperPrtotected status is True.

3. The below methods can be used only to enable or disable Tamper Protection within Windows Defender Firewall. For any third-party antivirus that you are using, you have to enable or disable the tamper protection separately.
Method 1: How to Turn Off/On Tamper Protection Security through Windows Defender Settings.
The first method to disable or enable the Tamper Protection security is via Defender settings.
1. Open the Run command box by holding the Win and R keys at the same time.
2. Type windowsdefender: and hit Enter:
3. In the windows security window, click on the Virus & threat protection tile.
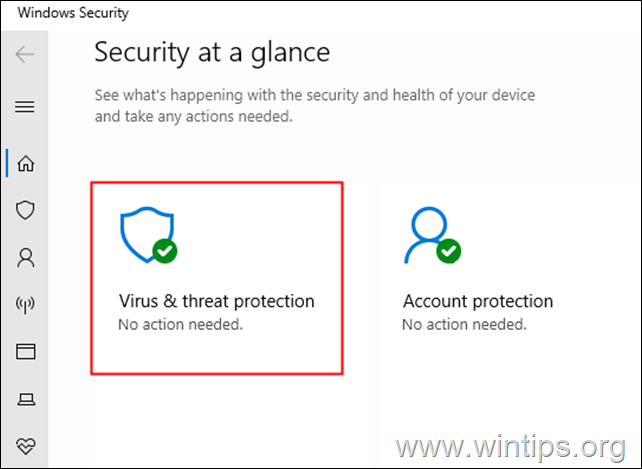
4. Scroll down and locate Virus & threat protection settings and click on Manage Settings.
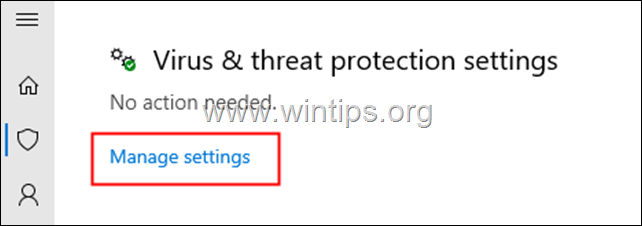
5. Scroll down and locate Tamper Protection.
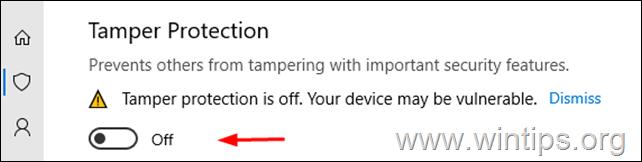
6a. In order to Enable Tamper Protection, toggle the switch to On, or…

6b. …toggle the switch to Off to Disable Tamper Protection Security.*
* Note: If you see a UAC popping up asking for permissions, click on Yes.
Method 2: How to Disable or Enable Tamper Protection using Registry Editor.
1. Open the Registry Editor: To do that:
-
- Open the Run command box by holding the Win and R keys at the same time.
- Type regedit and hit Enter: *
* Note: If you see a User Access Control (UAC) warning window asking for permission, click on Yes.
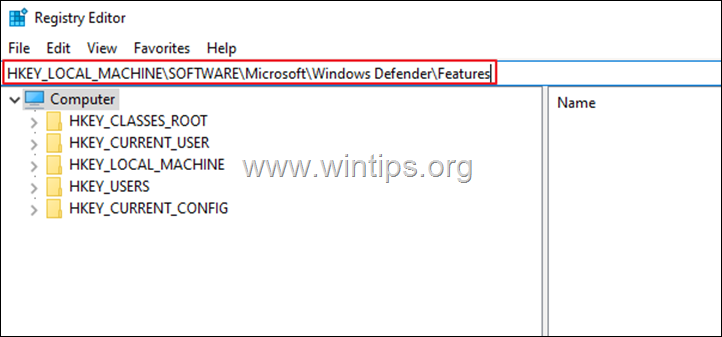
2. In the search bar at the top, delete any previous values and copy-paste the below registry location and hit Enter. *
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Features
* Note: If you are facing any issues, navigate to the above mentioned registry location from the left-hand side panel.
3. Select the Features key at the left and at the right double-click at the TamperProtection REG_DWORD value. *
* Note: If the «TamperProtection» value doesn’t exist, right-click anywhere at the right pane and select New > DWORD(32-bit) Value. Name the new value «TamperProtection» and proceed reading below.

4. In the Edit DWORD window that opens:*
- To Disable Tamper Protection, set the value data to 0 and click on the OK button.*
- To Enable Tamper Protection, set the value to 5 and click OK. *
* Note: If after pressing OK, you receive the error: «Error Editing Value. Cannot edit TamperProtection. Error writing the value’s new contents.», proceed below to take the ownership of the «Features» registry key and then repeat the above step.
To take the ownership of Features registry key:
Step 1. Backup Registry.
Since making changes to your Registry settings can be dangerous because even a minor mistake can result in system harm, it’s important to make a backup of the Registry Key you’re about to update before you start. To do that:
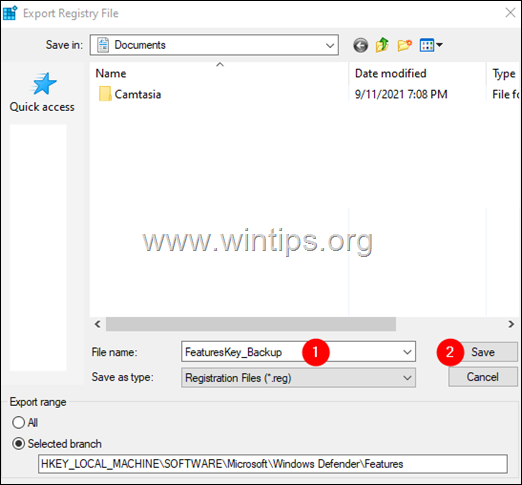
1. Right-Click on the Features key at the left-hand side panel and choose Export.
2. Give a suitable name (e.g. FeaturesKey_Backup), and save the REG file to your desktop. *
* Note: If something goes wrong after editing the registry, you can simply undo the changes by double-clicking the extracted registry key (REG file) on your desktop.
Step 2. Take Ownership of the Registry key.
1. Right-click on the Features key and choose Permissions.
2. In the ‘Permissions for Features’ window, click on the Advanced button.
3. In the ‘Advanced Security Settings for features’ window, click on Change.
4. In the ‘Select User or Group’ window, under Enter the object name to select section, type Administrators, and click on the OK button.
![clip_image004[5] clip_image004[5]](https://www.wintips.org/wp-content/uploads/2021/09/clip_image0045_thumb.png)
5. Tick the Replace owner on subcontainers or objects option, and click on the Apply button.

6. Now, double-click on the Administrators entry as shown below.
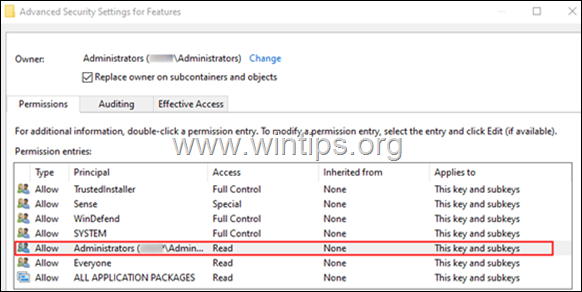
7. In the appearing window, check the Full control box and click on OK.

8. In the ‘Advanced Settings’ window, click on OK.
9. In the ‘Permissions for Features’ window, click on OK.
10. Now that you have the necessary permissions, proceed and modify the «TamperProtection» REG value as instructed in method-2 above.
That’s it! Which method worked for you?
Let me know if this guide has helped you by leaving your comment about your experience. Please like and share this guide to help others.
If this article was useful for you, please consider supporting us by making a donation. Even $1 can a make a huge difference for us in our effort to continue to help others while keeping this site free:
- Author
- Recent Posts
Konstantinos is the founder and administrator of Wintips.org. Since 1995 he works and provides IT support as a computer and network expert to individuals and large companies. He is specialized in solving problems related to Windows or other Microsoft products (Windows Server, Office, Microsoft 365, etc.).
