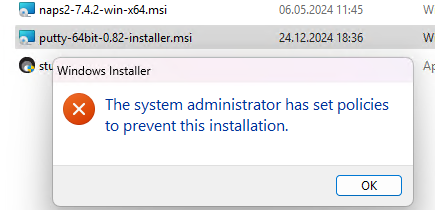
При попытке установить программу с помощью установочного MSI пакета на рабочей станции (права локального администратора имеются) возникает ошибка «Данная установка запрещена политикой, заданной системным администратором». Пытался запускать другие MSI файлы, они также не устанавливаются. Что делать?
Ответ
Сообщение Данная установка запрещена политикой, заданной системным администратором (The system administrator has set policies to prevent this installation) при установке (обновлении) программ из MSI пакетов или exe-инсталляторов указывает на то, что на компьютере включены политики, ограничивающие установку программ.
Если ваш пользователь обладает правами локального администратора, то вместо модификации локальных политик безопасности предлагаем простое обходное решение.
- Если это установщик, упакованный в EXE, щелкните по нему и выберите Запуск от имени администратора.
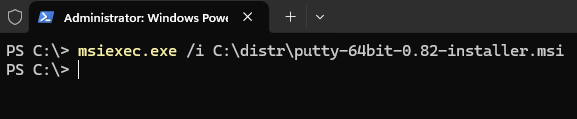
- Если это MSI пакет, откройте командную строку с правами администратора и запустите установку командой:
msiexec.exe /i C:\Install\MyApp-Installer.msi
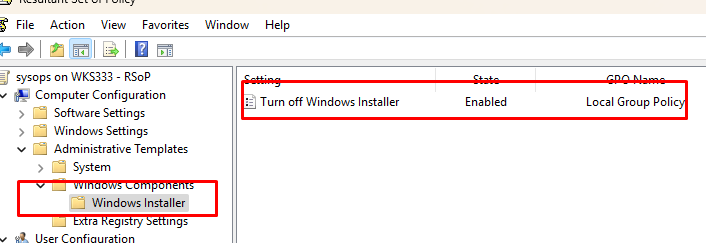
Если программа не устанавливается даже с повышенными привилегиями, проверьте настройки групповых политик на компьютере. Можно получить настройки результирующих GPO на компьютере с помощью графической оснастки
rsop.msc
или с помощью команды gpresult. Проверьте, есть ли настроенные параметры политик в разделе Конфигурация компьютера -> Административные шаблоны -> Компоненты Windows -> Установщик Windows (Computer Configuration -> Administrative Templates -> Windows Components -> Windows Installer). Параметры GPO, которые могут отграничивать права установки программ через службу
msiserver
:
- Отключение установщика Windows (Turn off Windows Installer)
- Запретить пользователям, не являющимися администраторами, устанавливать обновления, подписанные изготовителем программы (Prohibit non-administrators from applying vendor signed updates)
- Запретить пользователям устанавливать обновления через Windows Installer (Prevent users from using to install updates and upgrades)
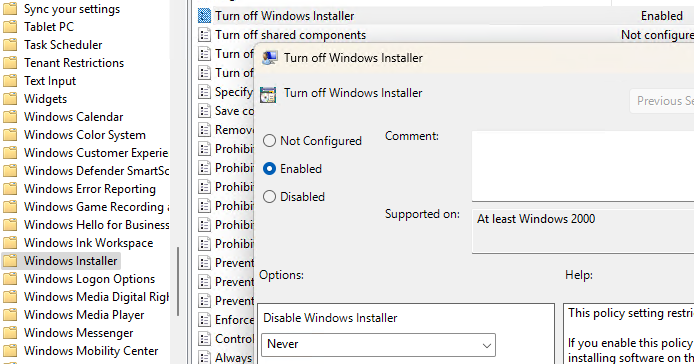
Если хотя бы одна из политик настроена, откройте редактор локальной GPO (
gpedit.msc
), перейдите в указанную выше ветку GPO, и измените настройку политики:
- Turn off Windows Installer:
Enabled
со значением
Never - Prohibit non-administrators from applying vendor signed update:
Disabled - Prevent users from using to install updates and upgrades:
Disabled
Политика позволяет запретить или разрешить пользователям (без прав администратора) выполнять обновление уже установленной программ (по умолчанию политика отключена). Если установленная программа запущена в привилегированном режиме (с правами SYSTEM), дополнительно нужно включить параметр GPO:
- Allow user to patch elevated products:
Enabled
После внесения изменений, примените настройки локальной GPO, выполнив команду:
gpupdate /force
Если на компьютере отсутствует редактор локальной GPO (например, в случае Home редакции Windows), или ограничивающие настройки применены непосредсвенно через реестр, нужно отредактировать значения в реестре. Перейдите в ветку
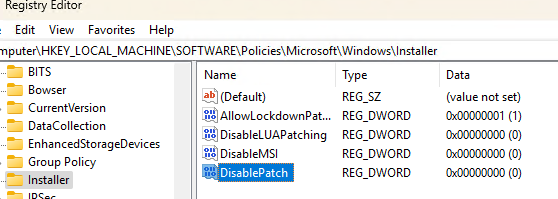
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Installer
и измените значение параметров следующим образом:
DisableMSI = 0 DisablePatch = 0 DisableLUAPatching=0 AllowLockdownPatch=1
Если параметры отсутствуют, можно создать их вручную.
Обратите внимание, что в Windows Server, в отличии от дестопных версий Windows, значение политики
Turn off Windows Installer
по умолчанию For managed application only. Поэтому в Windows Server под пользователем нельзя обновить установленное приложение.
В частности, это вызывает ошибку при обновлении компонентов 1C под пользователем, не являющимся локальным администратором:
Установка запрещена на основании системной политики. Обратитесь к системному администратору.
Чтобы разрешить установку обновлений 1С под пользователем, нужно отключить политику. Либо выполнять обновлений с правами администратора.
Также ограничения на установку программ (запуск определённых типов файлов) может быть внедрены с помощью политик ограниченного использования программ ( Software Restriction Policies) или AppLocker. Проверьте результирующие настройки политик в разделах:
- Computer Configuration -> Windows Settings -> Security Settings -> Software Restriction Policies
- Computer Configuration -> Windows Settings -> Security Settings -> Application Control Policies -> Applocker
Если ошибка возникает при установке или обновлении браузера Google Chrome под пользователем, сбросьте настройки политик браузера, удалив ветку
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Google\
.
Подробнее о сбросе локальных политик в Windows.
Windows includes a Registry-activated logging service to help diagnose Windows Installer issues. In today’s post, we will describe the steps on how to enable this Windows Installer logging service on Windows 11/10. Windows Installer is the standard Microsoft technology for deploying applications. It offers a format for packaging an application and an engine to unpack and install an application. MSI packages are used instead of proprietary installation systems, allowing your installer to run on any Windows platform from Windows 95 to Windows 11/10.
The Windows Installer, also known as Microsoft Installer, is a software component of the Windows operating system, that is used for the installation, maintenance, and removal of software. Sometimes installations fail because the Windows Installer is not able to do its job. Such Windows Installer issues can typically be caused by data corruption, corrupt installations, and so on. While Windows may roll back the installation, the issue would remain unresolved.
In case you face problems while installing programs on your Windows machine, you can refer to the logs which are maintained by Windows Installer. But for that, you have to enable logging first. After you have enabled Microsoft Installer logging, you can try to install the application again. Windows Installer will then track the progress and record all the data in a log file. These log files and events can help you troubleshoot installation issues and you can even share them with support professionals.
Verbose logging records more information in the logs generated by the Microsoft Installer. It tracks all changes and settings applied using Group Policy and its extension to the local computer and to users who log on to the computer. They are usually enabled if you need additional data. Such log files are usually found in C:\Debug and are typically large in size.
Windows Installer can use logging to help assist in troubleshooting issues with installing software packages. This logging is enabled by adding keys and values to the registry. After the entries have been added and enabled, you can retry the problem installation and Windows Installer will track the progress and post it to the Temp folder. The new log’s file name is random. However, the first letters are “Msi” and the file name has a “.log: extension. To locate the Temp folder, type the following line at a command prompt:
cd %temp%
When you enable Microsoft Installer logging, the error codes generated by Windows Installer are captured and stored in the log files. You can also contact Microsoft Support and pass on the error codes or log files to them.
These Windows Installer log names start with ‘msi’, followed by a bunch of alphanumeric characters, and are saved in the .log file format. They are normally stored in the following location, which is hidden:
C:\Documents and Settings\UserName\Local Settings\Temp\
Once you are done, you may disable Microsoft Installer logging
You can enable Windows Installer logging and Verbose logging manually, using any of these methods:
- Via Registry Editor
- Via Local Group Policy Editor
- Use Microsoft Fix-It
Now let’s take a look at both the procedures.
1] Enable Windows Installer logging via Registry Editor
Since this is a registry operation, it’s recommended you back up the registry or create a system restore point as a precautionary measure in case the procedure goes wrong.
Once you have done any of the above actions, you can now proceed as follows.
- Launch Registry Editor (press Windows key and type regedit, then hit Enter).
- Navigate to the following registry key:
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Installer
If you don’t see a Installer key (folder) below the Windows folder, right-click the Windows folder and select New > Key. Name it Installer.
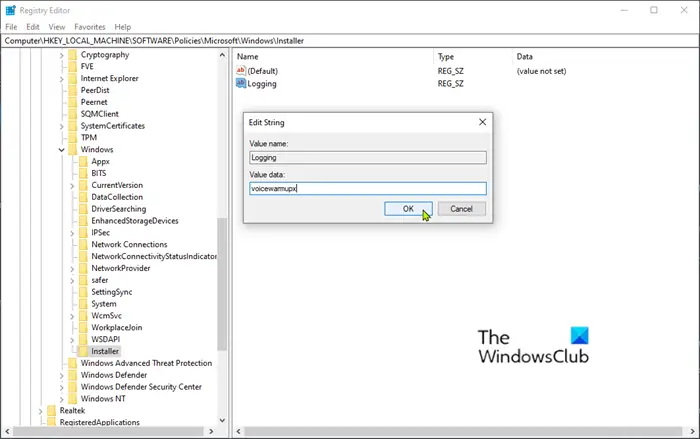
You can then create the following subkey and keys:
Type: Reg_SZ
Value: Logging
Data: voicewarmupx
Right-click the Installer key (folder) in the left pane and select New > String Value.
Name the value Logging.
Double-click the entry to edit it’s properties and set the Value data as voicewarmupx.
The letters in the value field can be in any order. Each letter turns on a different logging mode. Each letter’s actual function is as follows for MSI version 1.1:
- v – Verbose output
- o – Out-of-disk-space messages
- i – Status messages
- c – Initial UI parameters
- e – All error messages
- w – Non-fatal warnings
- a – Start up of actions
- r – Action-specific records
- m – Out-of-memory or fatal exit information
- u – User requests
- p – Terminal properties
- + – Append to existing file
- ! – Flush each line to the log
- x – Extra debugging information. The “x” flag is available only on Windows Server 2003 and later operating systems, and on the MSI redistributable version 3.0, and on later versions of the MSI redistributable.
- “*” – Wildcard: Log all information except the v and the x option. To include the v and the x option, specify “/l*vx”.
Click OK.
You can now exit Registry Editor and restart PC for changes to take effect.
Note: This change should be used only for troubleshooting and should not be left on because it will have adverse effects on system performance and disk space. Each time that you use the Add or Remove Programs item in Control Panel, a new Msi*.log file is created. To disable the logging, remove the Logging registry value.
Read: Enable Verbose or Highly Detailed Status Messages,
2] Enable Windows Installer logging via Group Policy Editor
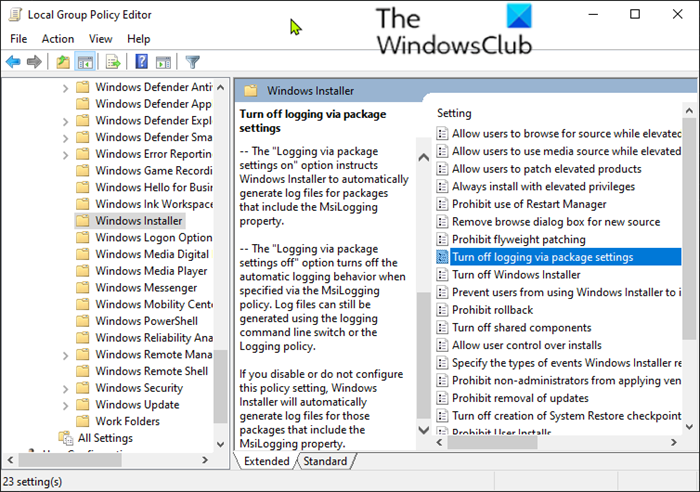
To enable Windows Installer logging on Windows 10 using Local Group Policy Editor (gpedit.msc), do the following;
- Launch the Local Group Policy Editor.
- Navigate to the following setting:
- Computer Configuration > Administrative Templates > Windows Components > Windows Installer
- Locate the Logging setting in the right pane and double-click on it to edit its properties.
- Click Enabled.
- In the Logging box, enter the options you want to log.
- The log file, Msi.log, appears in the Temp folder of the system volume.
- Click OK to save your changes.
Read: How to fix Microsoft Office installation errors
3] Use Microsoft Fix-It
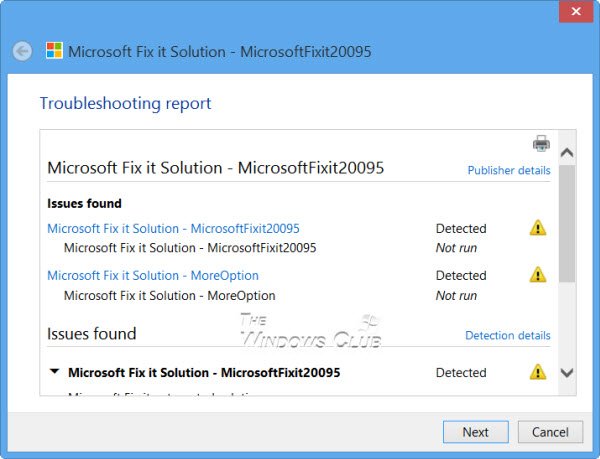
To enable and collect the Windows Installer logs, download Microsoft Fix it 20095 and run it.
Once you are done, you may disable Microsoft Installer logging using Microsoft Fix it 20096.
This Fix it is for Windows 8 and Windows 7 users only.
[Update: This Fix-It has been taken down]
That’s it!
Read: Error opening Installation Log File in Windows.
KnowledgeBase Archive
An Archive of Early Microsoft KnowledgeBase Articles
View on GitHub
Article: Q227181
Product(s): Microsoft Windows NT
Version(s): WINDOWS:
Operating System(s):
Keyword(s): kbnetwork kbtool kbOSWin2000 kbMSI kbDSupport
Last Modified: 11-JUN-2002
-------------------------------------------------------------------------------
The information in this article applies to:
- Microsoft Windows 2000 Advanced Server
- Microsoft Windows 2000 Server
- Microsoft Windows 2000 Professional
-------------------------------------------------------------------------------
SUMMARY
=======
The installation behavior of the Microsoft Windows Installer can be configured
by an administrator using the Group Policy Editor (GPE) and the Active
Directory.
There are also several user and machine policies that can be configured on a
local computer. This article describes user polices and then the machine
policies.
MORE INFORMATION
================
WARNING: If you use Registry Editor incorrectly, you may cause serious problems
that may require you to reinstall your operating system. Microsoft cannot
guarantee that you can solve problems that result from using Registry Editor
incorrectly. Use Registry Editor at your own risk.
User polices can be configured in the local registry and are located under the
following registry key:
HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\Installer
The following list contains values for these entries:
Value Name: AlwaysInstallElevated
Value Data Types: REG_DWORD
Description: If this value is set to "1" and the corresponding machine value is
also set, the Installer always installs with elevated privileges. Otherwise, the
Installer uses elevated privileges to install managed applications and uses the
current user's privilege level for non-managed applications.
Value Name: SearchOrder
Value Data Types: REG_SZ
Description: Order in which the Installer searches the three different types of
sources:
"n" - network
"m" - media (CD-ROM or DVD)
"u" - URL (Uniform Resource Locator)
For example, a value of "nmu" instructs the Installer to search network sources
first, media sources second, and URL sources last. Leaving out a letter removes
the corresponding volume type from the search. Default order in absence of this
value is network first, then media followed by URL.
Value Name: DisableBrowse
Value Data Types: REG_DWORD
Description: If this value exists and is set to "1", users are forbidden from
browsing to locate installer sources. Also, the "Use feature from:" combo box
for direct input is locked the "Browse..." button is disabled. See the source
resiliency topic in the Windows Installer SDK for more details on source
browsing.
Value Name: TransformsAtSource
Value Data Types: REG_DWORD
Description: If this value exists and is set to "1"; the Installer searches for
transform files in the root of any network sources in the source list for the
product. By default, transforms are stored in the Application Data folder of a
user's profile.
Value Name: DisableRollback
Value Data Types: REG_DWORD
Description: If this value is set to "1", the Installer will not store rollback
files during installation, disabling installation rollback. By default, rollback
is enabled. Administrators are advised to not use this policy unless it is
absolutely essential.
Machine polices can be configured under the following registry key:
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Installer
Value Name: AlwaysInstallElevated
Value Data Types: REG_DWORD
Description: If this value is set to "1" and the corresponding user value is also
set, the Installer always installs with elevated privileges. Otherwise, the
Installer uses elevated privileges to install managed applications and uses the
current user's privilege level for non-managed applications
Value Name: DisableMSI
Value Data Types: REG_DWORD
Description: If this value exists and is set to "2", the Installer is always
disabled for all applications. If this value is set to "1", the Installer is
disabled for non-managed applications but is still enabled for managed
applications. If this value is set to "0', any other number, or is absent, the
Installer is always enabled.
Value Name: Logging
Value Data Types: REG_SZ
Description: This policy is used only if logging has not been enabled by the "/L"
command line option or MsiEnableLog. If policy is set in this case, a log file
is created in the temp directory with the random name: MSI*.LOG. Specify the
logging mode by setting the policy value to a string of characters. Use the same
characters to specify logging mode policy as used by the '/L' command line
option. See Command Line Options. Note that you cannot use "+" and "*" for the
policy.
Value Name: DisablePatch
Value Data Types: REG_DWORD
Description: If this value is set to "1" the Installer does not apply patches.
This policy can be used to provide security in environments where patching must
be restricted.
More information about local polices and the Windows Installer can be found in
the Windows 2000 Software Development Kit (SDK).
Additional query words: 2000
======================================================================
Keywords : kbnetwork kbtool kbOSWin2000 kbMSI kbDSupport
Technology : kbwin2000AdvServ kbwin2000AdvServSearch kbwin2000Serv kbwin2000ServSearch kbwin2000Search kbwin2000ProSearch kbwin2000Pro kbWinAdvServSearch
Version : WINDOWS:
Issue type : kbinfo
=============================================================================
THE INFORMATION PROVIDED IN THE MICROSOFT KNOWLEDGE BASE IS
PROVIDED «AS IS» WITHOUT WARRANTY OF ANY KIND. MICROSOFT DISCLAIMS
ALL WARRANTIES, EITHER EXPRESS OR IMPLIED, INCLUDING THE WARRANTIES
OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. IN NO
EVENT SHALL MICROSOFT CORPORATION OR ITS SUPPLIERS BE LIABLE FOR
ANY DAMAGES WHATSOEVER INCLUDING DIRECT, INDIRECT, INCIDENTAL,
CONSEQUENTIAL, LOSS OF BUSINESS PROFITS OR SPECIAL DAMAGES, EVEN IF
MICROSOFT CORPORATION OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE
POSSIBILITY OF SUCH DAMAGES. SOME STATES DO NOT ALLOW THE EXCLUSION
OR LIMITATION OF LIABILITY FOR CONSEQUENTIAL OR INCIDENTAL DAMAGES
SO THE FOREGOING LIMITATION MAY NOT APPLY.
Copyright Microsoft Corporation 1986-2002.
Реализация DI в PHP
Jason-Webb 13.05.2025
Когда я начинал писать свой первый крупный PHP-проект, моя архитектура напоминала запутаный клубок спагетти. Классы создавали другие классы внутри себя, зависимости жостко прописывались в коде, а о. . .
Обработка изображений в реальном времени на C# с OpenCV
stackOverflow 13.05.2025
Объединение библиотеки компьютерного зрения OpenCV с современным языком программирования C# создаёт симбиоз, который открывает доступ к впечатляющему набору возможностей. Ключевое преимущество этого. . .
POCO, ACE, Loki и другие продвинутые C++ библиотеки
NullReferenced 13.05.2025
В C++ разработки существует такое обилие библиотек, что порой кажется, будто ты заблудился в дремучем лесу. И среди этого многообразия POCO (Portable Components) – как маяк для тех, кто ищет. . .
Паттерны проектирования GoF на C#
UnmanagedCoder 13.05.2025
Вы наверняка сталкивались с ситуациями, когда код разрастается до неприличных размеров, а его поддержка становится настоящим испытанием. Именно в такие моменты на помощь приходят паттерны Gang of. . .
Создаем CLI приложение на Python с Prompt Toolkit
py-thonny 13.05.2025
Современные командные интерфейсы давно перестали быть черно-белыми текстовыми программами, которые многие помнят по старым операционным системам. CLI сегодня – это мощные, интуитивные и даже. . .
Конвейеры ETL с Apache Airflow и Python
AI_Generated 13.05.2025
ETL-конвейеры – это набор процессов, отвечающих за извлечение данных из различных источников (Extract), их преобразование в нужный формат (Transform) и загрузку в целевое хранилище (Load). . . .
Выполнение асинхронных задач в Python с asyncio
py-thonny 12.05.2025
Современный мир программирования похож на оживлённый мегаполис – тысячи процессов одновременно требуют внимания, ресурсов и времени. В этих джунглях операций возникают ситуации, когда программа. . .
Работа с gRPC сервисами на C#
UnmanagedCoder 12.05.2025
gRPC (Google Remote Procedure Call) — открытый высокопроизводительный RPC-фреймворк, изначально разработанный компанией Google. Он отличается от традиционых REST-сервисов как минимум тем, что. . .
CQRS (Command Query Responsibility Segregation) на Java
Javaican 12.05.2025
CQRS — Command Query Responsibility Segregation, или разделение ответственности команд и запросов. Суть этого архитектурного паттерна проста: операции чтения данных (запросы) отделяются от операций. . .
Шаблоны и приёмы реализации DDD на C#
stackOverflow 12.05.2025
Когда я впервые погрузился в мир Domain-Driven Design, мне показалось, что это очередная модная методология, которая скоро канет в лету. Однако годы практики убедили меня в обратном. DDD — не просто. . .
Machine Policies
The following machine policies can be configured under:
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\Installer
| Policy | Value data type | Description |
|---|---|---|
| AlwaysInstallElevated | REG_DWORD | If this policy value is set to «1» and the corresponding user value is also set, the installer always installs with elevated privileges.
Otherwise, the installer uses elevated privileges to install managed applications and uses the current user’s privilege level for unmanaged applications. |
| AllowLockdownBrowse | REG_DWORD | If this policy value is set to «1», non-administrative users can browse for new sources while running an installation at elevated privileges. The default is that only administrators can browse for sources during an elevated installation. Setting this policy also enables non-administrative users to run programs at LocalSystem privileges during an elevated installation. |
| AllowLockdownMedia | REG_DWORD | If this policy value is set to «1», non-administrative users can use media sources, such as a CD-ROM, while running an installation at elevated privileges. The default is that only administrators can use media sources during an elevated installation. Setting this policy also enables non-administrative users to run programs at LocalSystem privileges during an elevated installation. |
| AllowLockdownPatch | REG_DWORD | If this per-machine system policy value is not set, only administrators can patch existing products that were installed at elevated privileges. If this policy value is set to «1», non-administrative users can, in some cases, apply patches to products while running an installation using elevated privileges. With the policy set, the patch can install minor upgrades while running an installation using elevated privileges; the patch cannot install major upgrades. Setting this policy also enables non-administrative users to run programs at LocalSystem privileges during an elevated installation. |
| Debug | REG_DWORD | If this policy value exists and is set to «1», the installer writes common debugging messages to the debugger using the OutputDebugString function. If this value exists and is set to «2», the installer writes all valid debugging messages to the debugger using the OutputDebugString function. This policy is for debugging purposes only and may not be supported in future versions of Windows Installer. |
| DisableAutomaticApplicationShutdown | REG_DWORD | If this policy value exists and is set to «1», Windows Installer does not interact with Restart Manager but will use the FilesInUse Dialog functionality.
|
| DisableBrowse | REG_DWORD | If this policy value exists and is set to «1», users are prevented from browsing to locate installer sources. The Use feature from combo box for direct input is locked and the Browse button is disabled. For more information about source browsing, see Source Resiliency. |
| DisableFlyWeightPatching | REG_DWORD | If this per-machine system policy value is set to «1», all Patch Optimization options are turned off during the installation.
|
| DisableLUAPatching | REG_DWORD | If this per-machine system policy value is set to «1», the installer prevents non-administrators from using least-privileged account (LUA) patching to any application installed on the computer. When this value is not set or «0», non-administrators can apply LUA patches to LUA-enabled application. |
| DisableMSI | REG_DWORD | If this policy value is set to «Null», «absent», or any number other than «1» or «2», the effect on the Windows Installer depends on the operating system. On Windows Server 2003, or when using Windows Installer 3.0 with Windows 2000 Server, Windows Installer is enabled for managed applications and disabled for unmanaged application installs. On Windows XP the Windows Installer is enabled for all applications.
If this policy value is set to «0», Windows Installer is enabled for all applications. All install operations are allowed. If this policy value is set to «1», Windows Installer is disabled for unmanaged applications but is still enabled for managed applications. Non-elevated per-user installations are blocked. Per-user elevated and per-machine installs are allowed. If this policy value is set to «2», Windows Installer is always disabled for all applications. No installs are allowed including repairs, reinstalls, or on-demand installations. |
| DisablePatch | REG_DWORD | If this policy value is set to «1» the installer does not apply patches. This policy can be used to provide security in environments where patching must be restricted. |
| DisablePatchUninstall | REG_DWORD | If this policy value is set to «1», patches cannot be removed from the computer by a user or an administrator. The Windows Installer can still remove patches that are no longer applicable to a product.
|
| DisableRollback | REG_DWORD | If this policy value is set to «1», the installer does not store rollback files during installation, disabling installation rollback. By default, rollback is enabled. Administrators are advised not to use this policy unless it is absolutely essential. |
| DisableSharedComponent | REG_DWORD | If this per-machine system policy is set to 1, no package on the system gets the shared component functionality enabled by the msidbComponentAttributesShared attribute in the Component table. |
| DisableUserInstalls | REG_DWORD | If this policy value is not set, the installer searches the registry for products in the following order: managed products that are registered as per-user, unmanaged products that are registered as per-user, and finally products that are registered as per-machine.
If this policy value is set to «1», the installer ignores all products that are registered as per-user and only searches for products that are registered as per-machine. An attempt to perform a per-user installation causes the installer to display an error message and stops the installation. |
| EnforceUpgradeComponentRules | REG_DWORD | Set this policy value to «1» to apply upgrade component rules during small updates and minor upgrades of all products on the computer.
|
| EnableAdminTSRemote | REG_DWORD | Setting this policy enables administrators to perform installations from a client session of a server running the Terminal Server role service. |
| EnableUserControl | REG_DWORD | If this policy value is set to «1», then the installer can pass all public properties to the server side during a managed installation using elevated privileges. Setting this policy has the same effect as setting the EnableUserControl property. |
| LimitSystemRestoreCheckpointing | REG_DWORD | This policy turns off the creation of checkpoints by Windows Installer.
If the policy value is set to «0» or «absent», Windows Installer does normal checkpointing for install or uninstall. If the policy value is set to «1», Windows Installer creates no checkpoints. |
| Logging | REG_SZ | This policy value is used only if logging has not been enabled by the «/L» command-line option or MsiEnableLog. If a policy is set in this case, a log file is created in the temp directory with the random name: MSI*.LOG. Specify the logging mode by setting the policy value to a string of characters. Use the same characters to specify logging mode policy as used by the ‘/L’ command-line option. For more information, see Command Line Options. Note that you cannot use «+» and «*» for the policy. |
| MaxPatchCacheSize | REG_DWORD | If this policy value is set to a value greater than «0», Windows Installer saves old versions of patched files in a cache. Set the value to the maximum percentage of disk space that can be used for the file cache. For example, a value of «15» and sets the maximum to 15%. Set to «0» to save no files. When this policy is not set, the default is 10%. |
| MsiDisableEmbeddedUI | REG_DWORD | To disable embedded UI handlers on the computer, set this policy value to 1.
|
| SafeForScripting | REG_DWORD | If this policy value is set to «1», users are not prompted when scripts use installer automation within a Web page. This may be useful for Web-based tools but can allow silent installations of applications without user knowledge or consent. |
| TransformsSecure policy | REG_DWORD | Setting the TransformsSecure policy value to «1» informs the installer that transforms are to be cached locally on the user’s computer in a location where the user does not have write access. |
| DisableLoggingFromPackage | REG_DWORD |
Set this policy value to «1» to disable the logging specified for the package by the MsiLogging property for all users of the computer.
|
Send comments about this topic to Microsoft
Build date: 8/13/2009
© 2009 Microsoft Corporation. All rights reserved.
