16.11.2022
Разберемся, как в доменной среде Active Directory по журналам контроллеров домена определить, кто из администраторов сбросил пароль учетной записи определенного пользователя.
В первую очередь, в политиках домена нужно включить аудит событий управления учётными записями. Для этого:
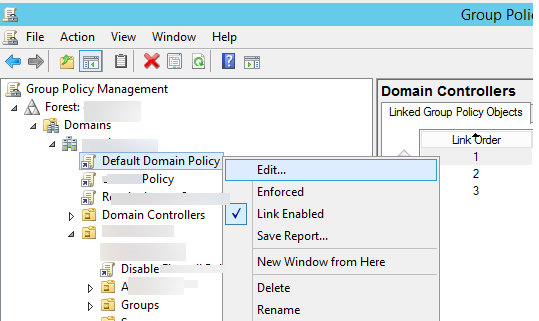
- Откройте консоль управления групповыми политиками Group Policy Management (gpmc.msc) и отредактирует политику домена Default Domain Policy.
- Затем в консоли редактора групповых политик, перейдите в раздел Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Audit Policy
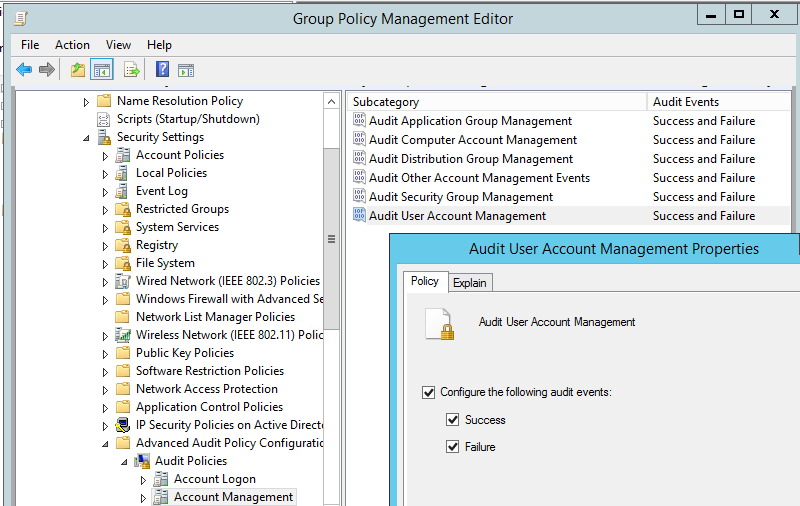
- Найдите и включите политику Audit User Account Management (если нужно фиксировать в журнале как успешные, та и неудачные попытки смены пароля, выберите опции Success и Failure).
Примечание. Эту же политику можно включить и в разделе расширенных политик аудита (Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Configuration)
- После прохождения цикла обновления групповых политик на клиентах можно попробовать изменить пароль любого пользователя в AD.
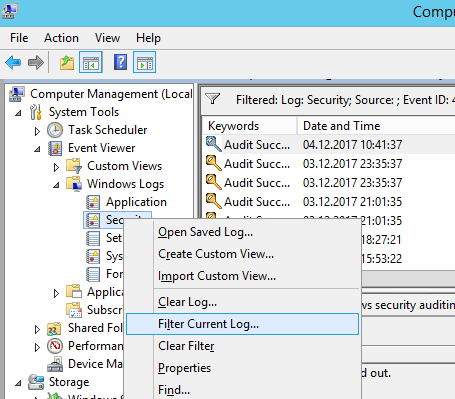
- После этого, откройте консоль просмотра событий на контроллере домена и перейдите в раздел Event Viewer -> Windows Logs -> Security. Щелкните ПКМ по журналу и выберите пункт Filter Current Log.
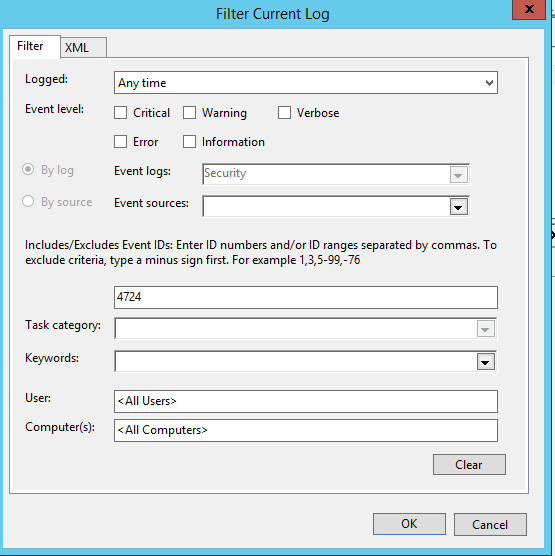
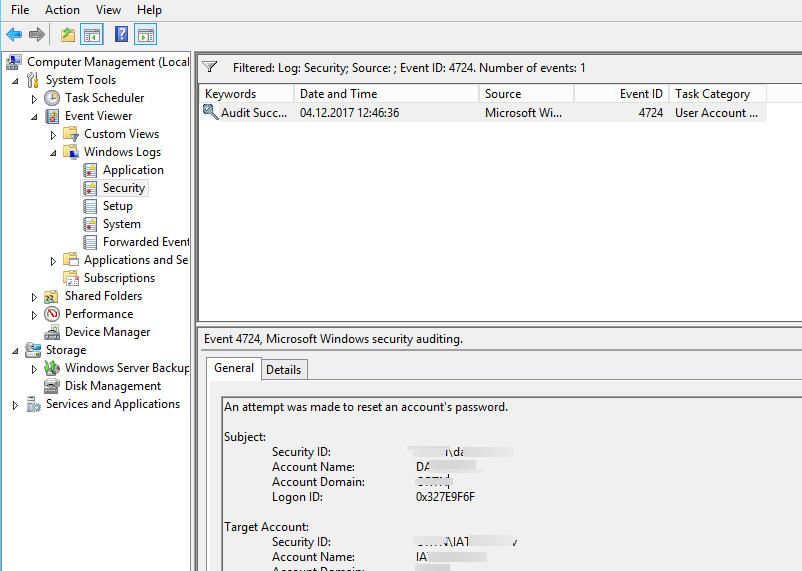
- В параметрах фильтра укажите, что нужно вывести только события с кодом EventID 4724.
- В списке событий останутся только события успешной смены пароля (An attempt was made to reset an account’s password.). При этом в расширенном представлении события можно увидеть имя учётной записи администратора, которая выполнила смену пароля (Subject:) и, собственно, учетную запись пользователя, чей пароль был сброшен (Target Account:).
Совет. В контексте получения полной информации о событиях смены пароля пользователя, в фильтр можно добавить следующие идентификаторы событий:
- 4724 (628 — в старых версиях Windows Server) – An attempt was made to reset an account’s password (сброс пароля пользователя администратором)
- 4723 (627 — в старых версиях Windows Server) – An attempt was made to change an account’s password (смена пароля самим пользователем)
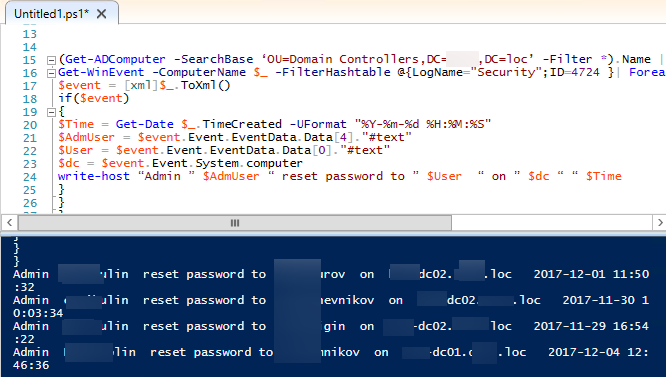
Информацию о данном событии из журналов всех контроллеров домена Active Directory с помощью PowerShell командлетов Get-ADComputer и Get-WinEvent, можно получить таким образом:
(Get-ADComputer -SearchBase ‘OU=Domain Controllers,DC=winitpro,DC=loc’ -Filter *).Name | foreach {
Get-WinEvent -ComputerName $_ -FilterHashtable @{LogName="Security";ID=4724 }| Foreach {
$event = [xml]$_.ToXml()
if($event)
{
$Time = Get-Date $_.TimeCreated -UFormat "%Y-%m-%d %H:%M:%S"
$AdmUser = $event.Event.EventData.Data[4]."#text"
$User = $event.Event.EventData.Data[0]."#text"
$dc = $event.Event.System.computer
write-host “Admin ” $AdmUser “ reset password to ” $User “ on ” $dc “ “ $Time
}
}
}
При необходимости эти данные можно записывать прямо из PowerShell во внешнюю mysql базу данных, через специальный коннектор MySQL .NET Connector по аналогии со сценарием, описанным в статье Узнаем кто удалил файл на файловом сервере.
To check the password change history in Active Directory (AD), it’s crucial to understand that AD doesn’t natively store a comprehensive historical log of all password changes indefinitely. However, there are ways to track recent password changes using Event Logs, PowerShell, and by enabling auditing.
Method 1: Using Event Logs
When users change their passwords, Event Logs in Windows Server capture these events, assuming password change auditing is enabled.
- Enable Auditing (if not already enabled):
- Open Group Policy Management (
gpmc.msc). - Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Logon/Logoff.
- Enable Audit Logon Events and Audit Account Logon Events.
- Ensure that Audit Directory Service Access is enabled in Security Settings > Advanced Audit Policy.
- Open Group Policy Management (
- View the Event Logs:
- Open Event Viewer (
eventvwr.msc). - Go to Windows Logs > Security.
- Look for Event ID 4723 (Password change attempt), Event ID 4724 (Password reset), and Event ID 628 (Password change).
- Filter the logs for these events to track password change history.
- Open Event Viewer (
- Event Details:
- In the Event Details, you’ll find information about the user account and the timestamp of the password change.
Method 2: Using PowerShell (with Auditing Enabled)
PowerShell can help you query password-related events if auditing is enabled.
-
Search Event Logs for Password Changes: Run the following command to search for password change events:
Get-WinEvent -LogName Security | Where-Object { $_.Id -eq 4723 -or $_.Id -eq 4724 -or $_.Id -eq 628 } | Format-Table TimeCreated, Id, Message -AutoSize -
Interpret the Results: This command will display the time of the password change and associated user details for each relevant event.
The output will show something like this:
| TimeCreated | Id | Message |
|---|---|---|
| 2/3/2025 10:15:45 AM | 4723 | An attempt was made to change the password of user ‘john.doe’ |
| 2/3/2025 10:20:30 AM | 4724 | The password of user ‘admin’ was reset by user ‘jane.doe’ |
- TimeCreated shows the time when the event occurred.
- Id represents the Event ID (4723, 4724, 628).
- Message provides additional details like the user who performed the action or the target user account.
Method 3: Using a Third-Party Tool (Optional)
If you need more detailed history and reporting capabilities, you can consider third-party tools like Netwrix Auditor, Lepide Auditor, or Specops that can provide more granular tracking of password changes, including change history over time and additional reporting features.
Limitations and Considerations:
- Default retention: Event logs are not retained indefinitely by default; old events may be overwritten after a period depending on your server’s log settings (log size, retention period). If you need to keep a long history, consider increasing log retention or exporting logs to a central logging solution.
- PowerShell speed: On large networks, querying logs using PowerShell might take time depending on the number of events. In such cases, filtering logs to a specific time range could improve performance.
Tracking password changes in Active Directory requires enabling auditing, then reviewing Event Logs or using PowerShell to query those logs. The main events to look for are Event IDs 4723, 4724, and 628. By ensuring auditing is set up correctly, you can capture and track password change attempts and resets efficiently.
Powershell — Who changed the user password in Active Directory
Powershell — Who changed the user password in Active Directory
Would you like to learn how to filter Windows event logs using Powershell to find who changed the user’s password on the domain? In this tutorial, we are going to show you how to find who changed the password of an account on the Active Directory.
• Windows 2012 R2
• Windows 2016
• Windows 2019
• Windows 2022
• Windows 10
• Windows 11
Equipment list
Here you can find the list of equipment used to create this tutorial.
This link will also show the software list used to create this tutorial.
Related tutorial — PowerShell
On this page, we offer quick access to a list of tutorials related to PowerShell.
Tutorial Powershell — Who changed the user password in Active Directory
On the domain controller, start an elevated Powershell command line.
List events related to the change of a user password.
Here is the command output.
Display the content of events related to the change of user passwords.
Here is the command output.
Display only the content of the event message.
Here is the command output.
Find who changed the password of users in the last 30 days.
Search for events related to the change of user passwords in a specific time interval.
List events related to the password change of a specific user account.
In our example, we filtered based on the event message content.
This Powershell script filters who changed the user password.
Here is the command output.
When a user changes his own password, the correct event ID is 4723.
Congratulations! You are able to find who changed a user password in the Active Directory using Powershell.
VirtualCoin CISSP, PMP, CCNP, MCSE, LPIC22022-08-11T01:00:13-03:00
Related Posts
Page load link
Ok
Approved By
Anuraag Singh
Published On
June 4th, 2024
Reading Time
7 Minutes Reading
Every admin wants a secure Active Directory especially if their organization is in talks regarding what is Active Directory migration. One way to ensure this is to check last password change in Active Directory periodically. As passwords form the first line of defense against an intrusion, the admin must have a report on AD user password history. However, admins may find the traditional script-based methods problematic. So they end up delaying this crucial task, which puts their AD in a vulnerable state.
Moreover, nowadays, password history viewing is not only a security check but a compliance requirement as well. Therefore, it’s even more important to have a list ready. Fret not, as we are here to help all admins with an easy-to-understand tutorial. Let us begin with the introduction to a manual auditing method that admins have at their disposal even without realizing it. And no, it is not ADUC.
Table of Content
- Password Change Date in AD with GPMC
- Scripts to Find Last Password Change History
- Problems with Scripts to Check Password
- Professionally Report Password Change in AD
- Steps to Use the Tool
- Conclusion
How to Check Last Password Change Date in Active Directory with GPME
Most organizations allow password updates at the user level. Moreover, admins can also make changes to user credentials on top of locating users in an AD. Both situations have a different event ID associated with them, viewable in the Group Policy Management Console. As this is an extra service, it may be absent from your AD installation. So admins first need to add it, otherwise, jump directly to stage 2.
Stage 1: Install GPME
- Use the Windows Search Bar to search for Server Manager and open it.
- Look for the roles and features option in the center section of Server Manager.
- Use the on-screen instructions till you are on the Features menu.
- Toggle the advanced features and choose gpme. Use the on-screen installation wizard for the next series of steps.
- Once it installs, go to the next stage.
Stage 2: Use the Group Policy Management Editor
Step 1. Setup Password Change Auditing
Step 2. Configure the Event Viewer to reflect the changes made to passwords.
Follow Step 1 till Security Settings.
- Select Event Log:
- Keep security log’s maximum size below 1 Gigabyte (1000000 kilobytes)
- Click on Apply, then OK.
Step 3. Check the security logs inside Event Viewer:

- Event ID 4724 means that it was the admin who reset the password.
- Event ID 4723 signifies a user attempt at password change.
If you feel navigating the GPMC portal is too cumbersome, don’t worry. For a more technical cursor-free code-based method, check out the following section.
Use Commands and Queries to List the Credential Update Date in the AD
PowerShell Script
This is probably the most sought-after method by technically savvy IT Admins. However, before you begin, ensure that your workstation is part of the AD environment. Once the checks are done, do the following.
Step 1. Press Windows Key + R on your keyboard.
Step 2. Type “PowerShell”.
Step 3. Use Import-Module ActiveDirectory first.
Step 4. Then run the following cmdlet and check last password change in Active Directory:
Get-ADUser -Filter * -Properties pwdLastSet | Select-Object Name, @{Name="LastPasswordSet";Expression={[DateTime]::FromFileTime($_.pwdLastSet)}} | Sort-Object Name | Format-Table

CMD Interface:
PowerShell is not the only way for admins to detect password updates in an AD. They can use the command line as well. Like the PowerShell method before admins need to fulfill a basic set of prerequisites here as well. This includes the workstation to be connected to the AD.
Step 1. Start by pushing Windows + R simultaneously.
Step 2. This time, type “cmd” in the space in front of Open:
Step 3. After that, you can use any one of the command line queries given below:
Query 1: To Get the Password change date in human-readable format.
> net user %username% | findstr “Password last set”

Query 2: To get the password set date of all users.
> dsquery * -filter "(objectClass=user)" -limit 0 -attr displayName pwdLastSet
Note: Directly pasting these commands is not recommended. Check your organization’s security policy and make changes to these commands before using them. Moreover, if you are unable to get the desired result then check out the limitations discussed ahead.
Problems with Scripts to Check Password Change History in AD
- PowerShell is highly technical. Therefore, deploying any unknown external scripts may have unintended consequences that admins did not plan for. Although these can be limited by changing the scripts, admins may lack the technical know-how. Another issue is that more time is spent correcting the script than using it. So for the small task of password change date retrieval, this seems unnecessary.
- Moreover, even the relatively simple cmd queries have quite a few drawbacks. The major one being that admins have to compromise with either the password change date of a single user or deal with a format that is not human-readable.
- Apart from this admins may skip the commands as their results can’t be directly exported into a shareable format like CSV. A clumsy workaround is sending a screenshot of the command line. But let’s be real such a practice is not acceptable in a professional setting.
- Not to mention that neither PowerShell nor CMD admins have any idea what their output is going to look like. So the only way to risk running the code on a live AD environment. However, there is one simple way to do away with the script-based methods. Let us see what it is.
Script Free Way to Check Last Password Change in Active Directory for All Users
In any Windows Active Directory, the best method to list the date of a user password change is the SysTools AD Reporting Software. With its simple yet intuitive way, any admin, no matter if they have a technical background or not, can find the historical credential updates.
Download Now Purchase Now
Moreover, tracking AD password changes may be a small task, but no admin can deny its significance in securing an Active Directory. Therefore, to get accurate, readable results, go through the procedure of using the tool.
Automated Instructions to Check Last Time Password Change in Active Directory
Step 1. Launch the software on your machine and put the word “administrator” in place of Username and Password.

Step 2. Once the tool is ready press the “REGISTER DOMAIN CONTROLLER” option. If you have a previous domain registered and want to add a new domain click on the building-like icon below the cross on the top-right part of your screen.

Step 3. Fill in the required details in the prompt box i.e. Domain Friendly Name and IP Address for the domain. Then hit Save & Continue.

Step 4. In the Domain Details screen enter the Admin User ID and Admin Password after that press the Save & Continue button below.

Step 5. After validation, change the screen to the Report tab. To check the last password change in Active Directory, select the Password Changed option under the Users category.

Step 6. You can also set an optional duration for the report. Either choose the premade time frame or make a custom date filter.

Step 7. Click on the Preview button to get an idea of what your report contains.

Step 8. Press Download and pick CSV from the Dropdown.

Step 9. Choose a location to save the report.

Step 10. View it on any external visualization software.

Conclusion
In this tutorial, we helped admins check last password change in Active Directory for all users. We found how this domain-wide credential history tracking forms a core component of security management in an AD. Moreover, we discussed multiple methods to see when the password update took place. Out of these, only the professional method helps in formulating a shareable CSV-style report. So it is in the best interest of admins to use the most optimal method.
By Mohit Kumar Jha
Mohit is a writer, researcher, and editor specializing in cloud migration, cybersecurity, and digital forensics. Passionate about these fields, he strives to create well-researched, insightful content that helps readers learn and stay informed.
View all of Mohit Kumar Jha’s posts.
Understanding the Password Changed Event ID is essential for maintaining secure IT systems. This event ID, a logging occurrence within numerous computer systems, works with security software and applications to enhance security measures. It notifies administrators about any password modifications, offering transparency into adjustments within the IT infrastructure and ensuring the network’s security functions properly. Moreover, this event plays a pivotal role in safeguarding against harmful actions and offers expanded oversight over an organization’s network. Recognizing and leveraging this critical event can significantly enhance the protection of personal and business information for search engines.
1. Keeping Your Password Secure: Understanding Password Changed Event IDs
Understanding Password Changed Event IDs is one of the most important aspects of keeping your passwords secure. If you’re not aware of what an Event ID is, it’s a unique identifier assigned to a specific operation or event. All systems, including computers, smartphones, and online services, track these events and assign a unique ID to them.
In this case, the Event IDs are used when a user changes their password. When their password is changed, the system logs the event with an Event ID, allowing the system to track changes and any attempts to access the account without permission. Knowing which Event IDs indicate a password change can help you protect your accounts and keep your passwords secure. Here are a few of the most common Password Changed Event IDs:
- 4740 – Account Lockout
- 4738 – Password changed
- 4741 – Account unlocked
- 476 – Account Password Reset
- 4689 – Account Login
It’s important to keep in mind that not all password changes require an Event ID. Some systems may assign different identifiers or may not assign any identifier. If you’re unsure what system your account is using, it’s best to contact the service provider for help. Once you know which Event IDs to look for, you can make sure that your passwords and accounts remain secure.
2. What is a Password Changed Event ID?
A password change event is an alert generated by an operating system or computer network when a user changes their password. These events are triggered when the password is changed, reset, or created. It is important to monitor and audit these events as it allows an organization to keep track of user accounts and have a better understanding of their security posture.
A password-changed event contains logs that contain valuable information about the user. This includes information like the username, the timestamp, the IP address from which the change took place, and any other relevant details that could be useful in identifying who made the changes. In addition, any password reset or change that took place outside of the organization will likely be documented as well.
- Username: The username of the person who made the changes.
- Timestamp: When the password change took place.
- IP Address: The IP address of the person or system responsible for making the changes.
3. How Does It Keep Your Passwords Secure?
Password managers are equipped with a range of security features to keep passwords safe. To start, most managers deploy an extra layer of encryption, known as AES (Advanced Encryption Standard) 256-bit encryption. This is a military-grade encryption that scrambles the data stored in the password manager, making it unreadable for anyone who attempts to access it. This is a must-have feature for keeping passwords secure.
In addition to this, many password managers also offer two-factor authentication. This feature requires the user to provide two forms of authentication for access, such as a password and a one-time PIN or an authentication code sent to their smartphone. This additional step of security makes it exceedingly difficult for hackers to gain access to your stored passwords. Password managers also protect passwords with a master password that must be entered with each login. This is the password you choose when initially setting up the manager, and it serves as a key to unlock your passwords. The stronger and more unique this master password is, the more secure your passwords stay.
4. Tips for Making Password Changed Event IDs Work Best for You
It’s important to keep your passwords secure, but taking extra steps to ensure their changes are noted can further protect you from hackers and other security issues. Here are a few tips to help you make the most out of your password change event IDs:
- Keep Track Of Your Event Ids. Make sure to note your event id anytime you make a password change. Keeping track of the event IDs will allow you to easily go back and check the history of your password changes and view any notes about them.
- Look at Your Event ID history. Regularly check your event ID history to stay in the know of all of your past password changes. If you notice an unauthorized change or something that just doesn’t look right, you can follow the instructions to set up a new password.
- Make Sure Your Event Ids Are Secure. Event IDs shouldn’t be shared with anyone outside of your organization, as they contain information about any password changes you have made. Make sure your event IDs are kept private and protected from any unauthorized access.
By taking these extra steps to ensure the security of your passwords, you can make sure that your accounts are as secure as possible. The effort and time you put in to make sure you understand and utilize password change event IDs will be worth it in the end!
A domain controller is a server that manages network services such as user accounts and security policies in a Windows domain. Active Directory is a centralized directory service used to manage resources and security within a network. Password policy defines the requirements and rules for creating and managing passwords for domain accounts. A password reset attempt occurs when a user tries to change their password. Security logs are records of events and activities related to security in an organization’s network. Real-time alerts notify administrators of potential security threats or issues as they occur. The Target Account\Security ID is a unique identifier for security purposes. Logon events track user access to network resources.
The Default Domain Policy is a set of default security settings for a domain. User passwords should meet the requirements of the domain password policy. Password change attempts and processes should be monitored for security purposes. User password resets should follow established procedures. Well-known security principals are commonly used security entities. Monitoring security logs and implementing security recommendations and updates are essential for network security. Windows Security features protect against malicious activities. Audit account management tracks changes to user accounts. Management for MSPs involves overseeing network security for multiple clients. Compliance reports ensure adherence to security standards. False-positive alerts can be misleading. Receiving alerts promptly is crucial for managing security incidents.
Set-ADAccountPassword cmdlet is a command-line tool for setting account passwords. Failure events indicate security breaches. Entity behavior analytics detect anomalous behavior. High-value accounts require extra security measures. User privileges should be limited to necessary functions. Event viewer provides details on security events. Built-in local administrators have administrative access to a system. Compliance standards must be met to protect sensitive data. Machine learning techniques help detect real threats. Monitoring event logs helps detect suspicious activity. Real-time monitoring is crucial for identifying security breaches.
Auditing solutions provide critical notifications for security incidents. Machine account password changes should be monitored closely. User account passwords must be secure to prevent unauthorized access. Security Monitoring Recommendations offer best practices for security. Audit policies set security standards for a network. Lepide Active Directory Auditor is a tool for managing Active Directory services. Lightweight Directory Access Protocol is a protocol for accessing directory services. Time Range specifies a period for monitoring activities. Real-time monitoring gives immediate feedback on security events. Sources: Microsoft, Lepide, TechTarget, Cybersecurity Insiders.
Critical Information for Understanding Password Changed Event IDs
| Concept | Description |
|---|---|
| Password Changed Event ID | An alert triggered when a user changes their password, providing valuable user information. |
| Password Manager Security Features | Includes AES 256-bit encryption, two-factor authentication, and a master password for secure storage. |
| Event ID Tips | Keep track of event IDs, check history regularly, and ensure their security for enhanced protection. |
| Domain Controller | Manages network services and security policies in a Windows domain. |
| Login Events | Track user access to network resources, providing critical security monitoring. |
| Default Domain Policy | Set of default security settings for a domain, ensuring standard security measures. |
| Security Monitoring Recommendations | Best practices for security, helping organizations maintain a secure network environment. |
Q&A
Q: What is a Password Changed Event ID?
A: A Password Changed Event ID is a special number that is created when a user changes their password on a computer or network. It’s used for security and recordkeeping purposes so that the user’s new password can be tracked and monitored by computer system administrators.
Q: What is a domain controller?
A: A domain controller is a server that is responsible for allowing network resources to be accessed by domain users. It stores a database of domain users, their passwords, and security information.
Q: What is Active Directory?
A: Active Directory is a directory service developed by Microsoft for Windows domain networks. It is used to manage domain accounts, security policies, and access control throughout a network.
Q: What is a password policy in Active Directory?
A: A password policy in Active Directory defines the rules and requirements for user passwords, such as length, complexity, and expiration. It helps ensure the security of domain accounts by enforcing strong password practices.
Q: How can I monitor password reset attempts in Active Directory?
A: You can monitor password reset attempts in Active Directory by enabling auditing of account management events in the security log. By monitoring events such as password changes and reset attempts, you can detect suspicious activity and take appropriate action.
Q: What are some recommended security log settings for Active Directory?
A: Recommended security log settings for Active Directory include setting a maximum security log size, enabling real-time alerts for critical events, and regularly reviewing security log entries for any suspicious activity. These measures can help detect and respond to potential security breaches.
Conclusion
If your goal is to protect and manage passwords for your online data, create a FREE LogMeOnce account for the most reliable password security and maximum data protection. LogMeOnce is a comprehensive and secure password manager that offers features such as two-factor authentication and Password Health Check to keep your data safe and secure. With Password Changed Event ID alerts, you can stay informed of any suspicious activity and immediately take action to protect your online identity. LogMeOnce provides a secure and easy way to change, track, and monitor passwords for your online accounts. Try to protect your data and passwords from online theft and keep yourself safe in this digital age.
Faye Hira, a distinguished graduate from the University of Okara, has carved a niche for herself in the field of English language education and digital marketing. With a Bachelor of Science in English, she specializes in Teaching English as a Second or Foreign Language (ESL), a skill she has honed with dedication and passion. Her expertise extends beyond the classroom and content writer, as she has also made significant strides in the world of Content and Search Engine Optimization (SEO). As an SEO Executive, Faye combines her linguistic prowess with technical acumen to enhance online visibility and engagement.