Skip to content
Windows Server 2016 SMB 3.1.1 Features and Hyper-V Enhancements
There are many powerful features related to storage in Windows Server 2016. The storage spaces direct and storage replica greatly extend the capabilities of what can be done in the world of Hyper-V, using Windows Server 2016. A less mentioned upgraded functionality contained in Windows Server 2016 is the SMB or Server Message Block protocol.
SMB 3.1.1 is the SMB version contained in Windows Server 2016 takes the advancements in SMB usage and storage to the next level in terms of performance and security.
Protect Your Data with BDRSuite
In this post, we will look at Windows Server 2016 SMB 3.1.1 Features and Hyper-V Enhancements to see how this protocol version extends Windows Server 2016 in terms of security and performance and also the capabilities that SMB 3 opens up in general for enterprise datacenters running Hyper-V.
Windows Server 2016 SMB 3.1.1 Features and Improvements
There are many new featured improvements when it comes to what the SMB 3.1.1 protocol allows Windows Server 2016 to do in terms of security and performance.
First of all, let’s look at the security benefits to SMB 3.1.1.

With SMB 3.1.1, there is a new Pre-Authentication Integrity mechanism that provides improved protection from any sort of man-in-the-middle attacks that may try to alter an SMB connection establishment or authentication. The way this works is Pre-Authentication Integrity verifies all negotiations and session setup exchanges used by SMB with a strong cryptographic hash (SHA-512). The SMB signing mechanism that is used on top of SMB 3.1.1 protects users from attackers eavesdropping on packets.
There are also various encryption improvements contained in SMB 3.1.1 including the use of AES-128-GCM which performs better on today’s modern processors. The encryption algorithm negotiated is chosen with each SMB connection with options for the CCM and GCM variants of AES-128. This change in encryption algorithm can produce a 2X performance improvement when copying large files over encrypted SMB connections.
The SMB 3.1.1 also provides support for cluster rolling upgrade for Scale-Out File Servers or SOFS. This feature is known as Cluster Dialect Fencing. With this capability a single SMB server presents support for different maximum variants of SMB, depending on whether the SMB client is accessing clustered or non-clustered file shares.
Windows Server 2016 and Windows 10 can communicate with the older version of the Windows operating system. When it does, SMB version 3.0.2 or earlier versions are leveraged to maintain the legacy connectivity.
Technologies Made Possible by SMB 3
SMB 3 as mentioned was released with Windows Server 2012 and represented a major leap forward for the SMB protocol including the following features:
- SMB Transparent Failover
- SMB Scale-Out
- SMB Multichannel
- SMB Direct
- SMB Encryption
- VSS for SMB file shares
- SMB Directory Leasing
- SMB PowerShell
Let’s look at a select few of the above list that has been a game changer with being able to utilize the SMB protocol as a true enterprise ready file protocol.
SMB Transparent Failover
The SMB Transparent Failover mechanism allows bringing back the state of an SMB connection to an alternate node in the event of a node failure. This can lead to only brief pauses in I/O while another node assumes the I/O.
SMB Scale-Out
This may be one of the single most important SMB developments as it has led to the ability to have multiple nodes in a Failover Cluster configuration to access the same LUN at the same time. This technology was introduced as Cluster Shared Volumes in Windows Server 2008 R2 and effectively allows multiple hosts to read and write to the same volume at the same time. This was a game changer for Hyper-V in that it allows all the hosts in the Failover Cluster to be able to read and write to virtual machines on the same LUN.
Cluster Shared Volumes has led to another advancement called the Scale-Out File Server. This allows efficient scaling in large environments of the backend storage for applications such as SQL Server and Hyper-V. The Scale-Out File Server is a portion of what is known as the “Converged” configuration in Storage Spaces Direct configurations.
SMB Multichannel
The SMB Multichannel feature of SMB 3 allows for having no single point of failure by establishing multiple connections for a single SMB session. This is a feature that is configured automatically. The SMB 3 client automatically looks for additional paths to the SMB server.
SMB Direct
SMB Direct greatly enhances performance by bypassing the host processing resources to perform file copy operations. An RDMA network adapter is utilized which allows the SMB communication to bypass the host processing capabilities, access a special area in memory and perform the SMB operation. This is at almost no cost to the server in terms of processing resources.
Windows Server 2016 SOFS, Storage Spaces, and Hyper-V over SMB Storage
Windows Server 2016 which includes SMB 3.1.1 builds on the SMB 3 protocol that was introduced in Windows Server 2012. SMB 3, in general, makes many different types of technologies possible from a storage perspective.
Let’s look at the following:
- Scale-Out File Server
- Storage Spaces
- Hyper-V over SMB storage
Scale-out File Server
We have already mentioned SMB Scale-Out and the “Converged” configuration for Hyper-V Storage Spaces Direct made possible by SMB 3. The Scale-Out File Server or SOFS can also allow you to make better use of SAN or other storage in your environment. By placing a scale-out file server cluster in front of the SAN and using SMB3, the SoFS cluster nodes broker access to the SAN. This allows a much more cost-effective use of SAN storage since it allows all desired servers to have access to SAN storage without having a direct SAN connection to the storage array itself.
Storage Spaces
Storage spaces can be used in conjunction with a Scale-Out File Server cluster for backend storage if a SAN is not being utilized. You can have a cluster of file servers with cluster storage provisioned that by using SMB 3 storage provisioned, if you have a failure, you will have resiliency by default to the backend storage spaces storage.
Hyper-V Over SMB Storage
Another option when considering SMB3 storage as relates specifically to Hyper-V is using SMB 3 shares as the storage for your Hyper-V virtual machines. This allows organizations to have another storage option without having a SAN provisioned for Hyper-V storage. It is easy to configure as well. Instead of managing storage fabric and LUNS, you simply manage file share. For the configuration to work, it simply needs the correct permissions for the Hyper-V host’s computer account and the cluster account. You have to grant Full Control permissions at the share and NTFS permission level for the accounts mentioned to have the appropriate access for use as Hyper-V storage.
The permissions can easily be granted using the Failover Cluster Manager or by utilizing PowerShell. Once the share and NTFS permissions are configured correctly, you can simply point to the UNC path for storing virtual machine files. The share can store the virtual disks, configuration files, checkpoint files, and page files.
Concluding Thoughts
The SMB Protocol has been around for quite some time and has been the backbone of Windows Server communication since the outset. In the last few Windows Server releases, there have been major improvements to the SMB protocol. Starting in SMB 3, many capabilities were added to the protocol that formed the groundwork for many advanced storage features that are available with Windows Server 2016. As relates to Hyper-V, storage spaces direct, scale-out file server and storage replicas are all made possible by the enhancements starting with SMB3. Hyper-V environments are directly benefited by these and other technologies such as RDMA used by SMB Direct which is utilized in Storage Spaces Direct.
Follow our Twitter and Facebook feeds for new releases, updates, insightful posts and more.
Try BDRSuite for Free!
Schedule a live demo with one of our product experts
Start your full-featured 30-day free trial
Explore detailed pricing, editions & features
Lead Image © Pete Saloutos, 123RF.com
SMB 3.1.1 in Windows Server 2016
Sharing
We look at the new performance and security features of SMB 3.1.1 with Windows Server 2016 and Windows 10.
In each version of Windows, Microsoft provides an updated version of the Server Message Block (SMB) protocol. Windows Server 2016 and Windows 10 communicate via the new SMB 3.1.1, offering some new features in terms of performance and security. Of course, Windows Server 2016 and Windows 10 can still use SMB to talk to older Windows versions and to Linux without problem (see the «Linux and SMB 3.1.1» box), although you must use an SMB version from the oldest system present. In this article, I introduce the use of SMB 3.1.1 and examine its compatibility issues.
Linux and SMB 3.1.1
Samba version 4.3 or newer supports SMB 3.1.1; you should update the Samba server to the new version 4.x for Windows 10. Moreover, domain controllers that are compatible with Windows 10 can be installed with Samba.
The new version of the SMB protocol can prevent man-in-the-middle attacks by extending SMB encryption. SMB 3.0 in Windows 7 and Windows Server 2012 already did its best to restrict access to data transmitted by attackers. In SMB 3.1.1, the cipher is exchanged during the connection establishment process, the aim being to ensure that security is in place even before the client and server have mutually authenticated. Microsoft designates this new feature «pre-authentication integrity.» The authentication data is encrypted with SHA-512.
Because the older Secure Negotiate function is rarely used and has caused some problems – especially with third-party software – you can now disable this feature, which can improve communication performance, especially if you are not using the function anyway.
More Secure
In SMB 3.1.1, Secure Negotiate is replaced by pre-authentication integrity. In connections with older versions of SMB, you cannot bypass
…
Use Express-Checkout link below to read the full article (PDF).
Buy this article as PDF
Express-Checkout as PDF
Price $2.95
(incl. VAT)
TABLET & SMARTPHONE APPS
US / Canada
UK / Australia
Related content
-
Software-defined networking with Windows Server 2016
Windows Server 2016 takes a big step toward software-defined networking, with the Network Controller server role handling the centralized management, monitoring, and configuration of network devices and virtual networks. This service can also be controlled with PowerShell and is particularly interesting for Hyper-V infrastructures.
-
Connecting Windows Server 2016 with Azure
Microsoft continues to integrate Windows Server with the Azure cloud. With Cloud Witness and the RDS Connection Broker, you can operate distributed environments more reliably and efficiently, and SQL databases migrate sensibly into the cloud.
-
Windows Server 2016 for small servers
Small businesses often do not need the full-blown version of Windows Server 2016. If the application scenarios are manageable, the cheaper Essentials version is the ideal solution; however, it does come with a number of restrictions.
-
Hyper-V with the SMB 3 protocol
Microsoft has introduced several improvements to Windows Server 2012 and Windows Server 2012 R2 with its Server Message Block 3. Hyper-V mainly benefits from faster and more stable access to network storage. In this article, we look at the innovations.
-
Virtual networks with Hyper-V in Windows Server 2016
Microsoft provides some interesting virtualization features in current and future versions of Windows Server. You can connect or isolate virtual machines, and Windows Server 2016 even supports virtual switches.
comments powered by
Subscribe to our ADMIN Newsletters
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Support Our Work
ADMIN content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.
Introduction
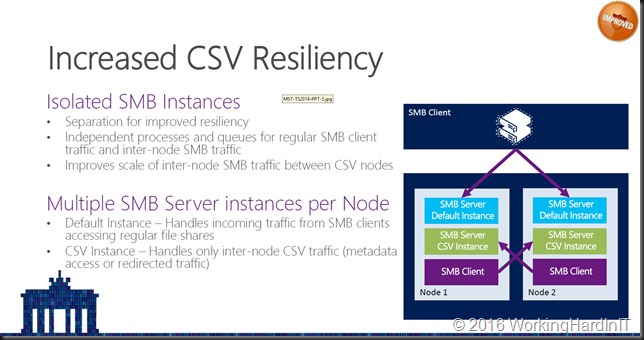
I’m pretty sure you all know / remember that in Windows Server 2012 R2 one of the improvements we got for SMB 3 was the default and the CSV instance. You can take a peak here at my slide deck from a presentation I gave at the Microsoft Technical Summit in Berlin 2014 Failover Clustering- What’s new in Windows Server 2012 R2
You can also read more on TechNet here.
We have New SMB Instances in Windows Server 2016
I’m happy to see this concept being expanded in the new SMB workloads. When playing with Windows Server 2016 TPv5 I you’ll notice that we now have gotten extra SMB instances:
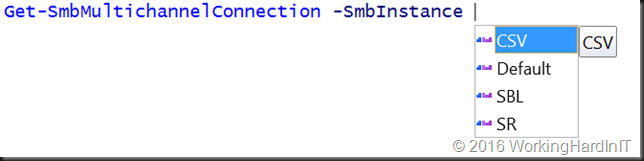
So what are these New SMB Instances in Windows Server 2016 about?
Default: This is what we had before, it’s nonspecific default SMB traffic, such as file shares
CSV: Also already known since Windows Server 2012 R2. This is the CSV traffic. This got isolated for better resiliency and isolation of issues. The goal was not to let CSV SMB issues affect default SMB traffic.
SR: This stands for Storage Replica. The purpose of this instance is the same as for CSV, isolate and make SMB on the whole more resilient.
SBL: This stands for “Storage Bus Layer”, which is related to Storage Spaces Direct replication traffic. The Storage Bus Layer is now called the Software Storage Bus (SSB). Again, isolated in its own instance for better resilience and isolation of issues. You can find more on the Software Storage Bus in Storage Spaces Direct and its use of SMB here Storage Spaces Direct – Under the hood with the Software Storage Bus

Picture by Microsoft®
“SSB uses SMB3 and SMB Direct as the transport for communication between the servers in the cluster. SSB uses a separate named instance of SMB in each server, which separates it from other consumers of SMB, such as CSVFS, to provide additional resiliency. Using SMB3 enables SSB to take advantage of the innovation we have done in SMB3, including SMB Multichannel and SMB Direct. SMB Multichannel can aggregate bandwidth across multiple network interfaces for higher throughput and provide resiliency to a failed network interface. SMB Direct enables use of RDMA enabled network adapters, including iWARP and RoCE, which can dramatically lower the CPU overhead of doing IO over the network and reduce the latency to disk devices”
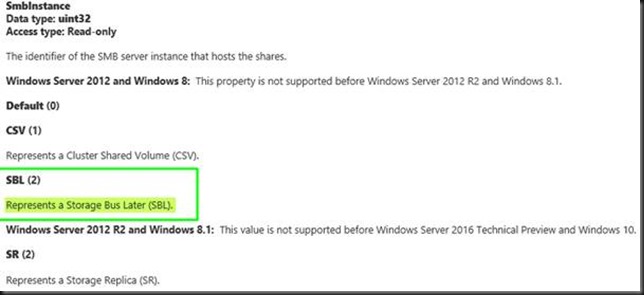
Funny anecdote: while doing some research I stumbled upon the MSDN article MSFT_SmbShare class. As you can see in the screenshot below the name was mistakenly put at “Storage Bus Later” but it should be Storage Bus Layer or as it’s now called the Software Storage Bus:
Now that will be fixed soon or by the time you read this blog post. All fun aside, if you want to see what that Software Storage Bus is capable of look at this blog post and video by Ned Pyle on what Claus Joergenson achieved already in 2015 with this technology. Amazing results!
Сетевой протокол SMB (Server Message Block) используется для предоставления совместного удаленного доступа к файлам, принтерам и другим устройствам через порт TCP 445. В этой статье мы рассмотрим: какие версии (диалекты) протокола SMB доступны в различных версиях Windows (и как они соотносятся с версиями samba в Linux); как определить версию SMB на вашем компьютере; и как включить/отключить клиент и сервер SMBv1, SMBv2 и SMBv3.
Содержание:
- Версии протокола SMB в Windows
- Как проверить поддерживаемые версии SMB в Windows?
- Вывести используемые версии SMB с помощью Get-SMBConnection
- Об опасности использования SMBv1
- Включение и отключение SMBv1, SMBv2 и SMBv3 в Windows
Версии протокола SMB в Windows
Есть несколько версии протокола SMB (диалектов), которые последовательно появлялись в новых версиях Windows:
Для реализации протокола SMB в Linux/Unix системах используется samba. В скобках мы указали в каких версиях samba поддерживается каждый диалект SMB.
- CIFS — Windows NT 4.0;
- SMB 1.0 — Windows 2000;
- SMB 2.0 — Windows Server 2008 и Windows Vista SP1 (поддерживается в Samba 3.6);
- SMB 2.1 — Windows Server 2008 R2 и Windows 7 (поддерживается в Samba 4.0);
- SMB 3.0 — Windows Server 2012 и Windows 8 (поддерживается в Samba 4.2);
- SMB 3.02 — Windows Server 2012 R2 и Windows 8. 1 (не поддерживается в Samba);
- SMB 3.1.1 – Windows Server 2016 и Windows 10 (не поддерживается в Samba).
Начиная с версии Samba 4.14, по умолчанию используется SMB2.1.
При сетевом взаимодействии по протоколу SMB между клиентом и сервером используется максимальная версия протокола, поддерживаемая одновременно и клиентом, и сервером.
Ниже представлена сводная таблица, по которой можно определить версию протокола SMB, которая выбирается при взаимодействии разных версий Windows:
| Операционная система | Win 10, Server 2016 | Windows 8.1, Server 2012 R2 |
Windows 8, Server 2012 |
Windows 7, Server 2008 R2 |
Windows Vista, Server 2008 |
Windows XP, Server 2003 и ниже |
| Windows 10 ,
Windows Server 2016 |
SMB 3.1.1 | SMB 3.02 | SMB 3.0 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows 8.1 , Server 2012 R2 |
SMB 3.02 | SMB 3.02 | SMB 3.0 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows 8 , Server 2012 |
SMB 3.0 | SMB 3.0 | SMB 3.0 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows 7, Server 2008 R2 |
SMB 2.1 | SMB 2.1 | SMB 2.1 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows Vista, Server 2008 |
SMB 2.0 | SMB 2.0 | SMB 2.0 | SMB 2.0 | SMB 2.0 | SMB 1.0 |
| Windows XP, 2003 и ниже | SMB 1.0 | SMB 1.0 | SMB 1.0 | SMB 1.0 | SMB 1.0 | SMB 1.0 |
К примеру, при подключении клиентского компьютера с Windows 8.1 к файловому серверу с Windows Server 2016 будет использоваться протокол SMB 3.0.2.
Согласно таблице Windows XP, Windows Server 2003 для доступа к общим файлам и папкам на сервере могут использовать только SMB 1.0, который в новых версиях Windows Server (2012 R2 / 2016) может быть отключен. Таким образом, если в вашей инфраструктуре одновременно используются компьютеры с Windows XP (снятой с поддержки), Windows Server 2003/R2 и сервера с Windows Server 2012 R2/2016/2019, устаревшие клиенты не смогут получить доступ к файлам и папкам на файловом сервере с новой ОС.
Если Windows Server 2016/2012 R2 с отключенным SMB v1.0 используется в качестве контроллера домена, значить клиенты на Windows XP/Server 2003 не смогут получить доступ к каталогам SYSVOL и NETLOGON на контроллерах домена и авторизоваться в AD.
На старых клиентах при попытке подключиться к ресурсу на файловом сервере с отключенным SMB v1 появляется ошибка:
The specified network name is no longer available
Как проверить поддерживаемые версии SMB в Windows?
Рассмотрим, как определить, какие версии протокола SMB поддерживаются на вашем компьютере Windows.
В Windows 10, 8.1 и Windows Server 2019/2016/2012R2 вы можете проверить состояние различных диалектов SMB протокола с помощью PowerShell:
Get-SmbServerConfiguration | select EnableSMB1Protocol,EnableSMB2Protocol
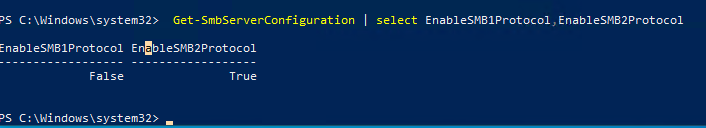
Данная команда вернула, что протокол SMB1 отключен (
EnableSMB1Protocol=False
), а протоколы SMB2 и SMB3 включены (
EnableSMB1Protocol=True
).
Обратите внимание, что протоколы SMBv3 и SMBv2 тесно связаны между собой. Нельзя отключить или включить отдельно SMBv3 или SMBv2. Они всегда включаются/отключаются только совместно, т.к. используют один стек.
В Windows 7, Vista, Windows Server 2008 R2/2008:
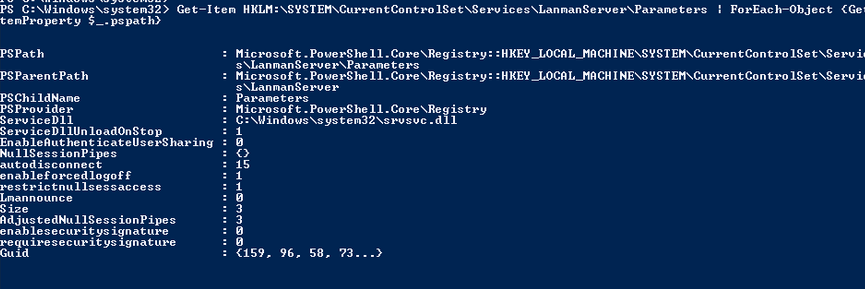
Get-Item HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters | ForEach-Object {Get-ItemProperty $_.pspath}
Если в данной ветке реестра нет параметров с именами SMB1 или SMB2, значить протоколы SMB1 и SMB2 по умолчанию включены.
Также в этих версиях Windows вы можете проверить, какие диалекты SMB разрешено использовать в качестве клиентов с помощью команд:
sc.exe query mrxsmb10
SERVICE_NAME: mrxsmb10 TYPE : 2 FILE_SYSTEM_DRIVER STATE : 4 RUNNING (STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN) WIN32_EXIT_CODE : 0 (0x0) SERVICE_EXIT_CODE : 0 (0x0) CHECKPOINT : 0x0 WAIT_HINT : 0x0
sc.exe query mrxsmb20
SERVICE_NAME: mrxsmb20 TYPE : 2 FILE_SYSTEM_DRIVER STATE : 4 RUNNING (STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN) WIN32_EXIT_CODE : 0 (0x0) SERVICE_EXIT_CODE : 0 (0x0) CHECKPOINT : 0x0 WAIT_HINT : 0x0
В обоих случаях службы запущены (
STATE=4 Running
). Значит Windows может подключаться как к SMBv1, так и к SMBv2 серверам.
Вывести используемые версии SMB с помощью Get-SMBConnection
Как мы говорили раньше, компьютеры при взаимодействии по протоколу SMB используют максимальную версию, поддерживаемую как клиентом, так и сервером. Для определения версии SMB, используемой для доступа к удаленному компьютеру можно использовать командлет PowerShell
Get-SMBConnection
:
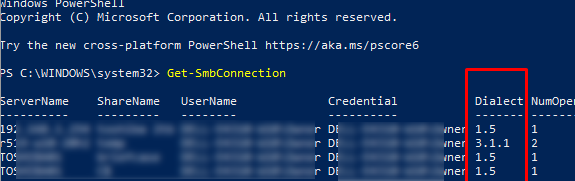
Версия SMB, используемая для подключения к удаленному серверу (ServerName) указана в столбце Dialect.
Можно вывести информацию о версиях SMB, используемых для доступа к конкретному серверу:
Get-SmbConnection -ServerName servername
Если нужно отобразить, используется ли SMB шифрование (появилось в SMB 3.0), выполните:
Get-SmbConnection | ft ServerName,ShareName,Dialect,Encrypted,UserName
В Linux вывести список SMB подключения и используемые диалекты в samba можно командой:
$ sudo smbstatus
Чтобы на стороне сервера вывести список используемых клиентами версий протокола SMB и количество клиентов, используемых ту или иную версию протокола SMB, выполните команду:
Get-SmbSession | Select-Object -ExpandProperty Dialect | Sort-Object -Unique
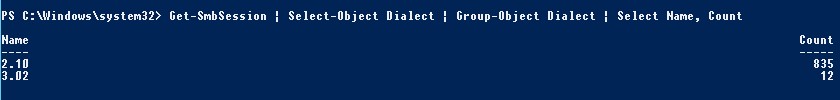
В нашем примере имеется 825 клиентов, подключенных к серверу с помощью SMB 2.1 (Windows 7/Windows Server 2008 R2) и 12 клиентов SMB 3.02.
С помощью PowerShell можно включить аудит версий SMB, используемых для подключения:
Set-SmbServerConfiguration –AuditSmb1Access $true
События подключения затем можно извлечь из журналов Event Viewer с помощью PowerShell:
Get-WinEvent -LogName Microsoft-Windows-SMBServer/Audit
Об опасности использования SMBv1
Последние несколько лет Microsoft из соображений безопасности планомерно отключает устаревший протокол SMB 1.0. Связано это с большим количеством критических уязвимостей в этом протоколе (вспомните историю с эпидемиями вирусов-шифровальщиков wannacrypt и petya, которые использовали уязвимость именно в протоколе SMBv1). Microsoft и другие IT компании настоятельно рекомендуют отказаться от его использования.
Однако отключение SMBv1 может вызвать проблемы с доступом к общий файлам и папкам на новых версиях Windows 10 (Windows Server 2016/2019) с устаревших версий клиентов (Windows XP, Server 2003), сторонних ОС (Mac OSX 10.8 Mountain Lion, Snow Leopard, Mavericks, старые версии Linux), различных старых NAS устройствах.
Если в вашей сети не осталось legacy устройств с поддержкой только SMBv1, обязательно отключайте эту версию диалекта в Windows.
В том случае, если в вашей сети остались клиенты с Windows XP, Windows Server 2003 или другие устройства, которые поддерживают только SMBv1, их нужно как можно скорее обновить или тщательно изолировать.
Включение и отключение SMBv1, SMBv2 и SMBv3 в Windows
Рассмотрим способы включения, отключения различных версий SMB в Windows. Мы рассматриваем отдельно включение клиента и сервера SMB (это разные компоненты).
Windows 10, 8.1, Windows Server 2019/2016/2012R2:
Отключить клиент и сервер SMBv1:
Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol
Отключить только SMBv1 сервер:
Set-SmbServerConfiguration -EnableSMB1Protocol $false
Включить клиент и сервер SMBv1:
Enable-WindowsOptionalFeature -Online -FeatureName smb1protocol
Включить только SMBv1 сервер:
Set-SmbServerConfiguration -EnableSMB1Protocol $true
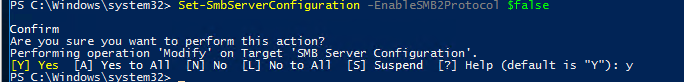
Отключить сервер SMBv2 и SMBv3:
Set-SmbServerConfiguration -EnableSMB2Protocol $false
Включить сервер SMBv2 и SMBv3:
Set-SmbServerConfiguration -EnableSMB2Protocol $true
Windows 7, Vista, Windows Server 2008 R2/2008:
Отключить SMBv1 сервер:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB1 -Type DWORD -Value 0 –Force

Включить SMBv1 сервер:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB1 -Type DWORD -Value 1 –Force
Отключить SMBv1 клиент:
sc.exe config lanmanworkstation depend= bowser/mrxsmb20/nsi
sc.exe config mrxsmb10 start= disabled
Включить SMBv1 клиент:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/mrxsmb20/nsi
sc.exe config mrxsmb10 start= auto
Отключить SMBv2 сервер:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB2 -Type DWORD -Value 0 -Force
Включить SMBv2 сервер
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB2 -Type DWORD -Value 1 –Force
Отключить SMBv2 клиент:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/nsi
sc.exe config mrxsmb20 start= disabled
Включить SMBv2 клиент:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/mrxsmb20/nsi
sc.exe config mrxsmb20 start= auto
Для отключения сервера SMBv1 на всех компьютерах независимо от версии Windows можно распространить параметр реестра типа REG_DWORD с именем SMB1 и значением 0 (HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters)на через GPO.
Для отключения SMBv2 нужно в этой же ветке установить параметр SMB2=0.
Для отключения SMBv1 клиента нужно распространить такой параметр реестра:
- Key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\mrxsmb10
- Name: Start
- Type: REG_DWORD
- Value: 4
При отключении SMB 1.0/CIFS File Sharing Support в Windows вы можете столкнуться с ошибкой “0x80070035, не найден сетевой путь”, ошибкой при доступе к общим папкам, и проблемами обнаружения компьютеров в сетевом окружении. В этом случае вместо служба обозревателя компьютеров (Computer Browser) нужно использовать службы обнаружения (линк).
Sharing folders makes them accessible to network users and probably you need to do. After you’ve configured disks on the server, you must share files/disks to enable network users to access files and disks. When sharing files and folders also you can enable administrators and clients to access the files, folders offline even when the server is off.
Sharing files and managing permissions with advanced settings are one of important strategy an administrator must know. Here in this article, we will discuss fully on share files and folders in Windows server 2016, no matter it’s possible to do it in Windows server 2012 and 2008 R2. So let’s get started.
Before start sharing files make sure that the advanced sharing settings is configured correctly from control panel with firewall settings then select the folder you want to share. Here we will share files with File and Storage Services, it’s already available in windows server by default.
1. Go to Server manager click File and Storage Services then click shares>tasks>New share to create a folder share on server.

2. Select a share profile for the folder you want to share then click Next.
SMB Share Quick: (SMB) is the standard file sharing used by all versions of Windows. SMB Share Quick provides basic SMB sharing with full share and NTFS permission.
SMB Share Advanced: Provides SMB sharing with full share and NTFS permission and access to services provided by File Server Resource Manager.
SMB Share Application: Provides SMB sharing with settings suitable for Hyper-V and other applications.
NFS Share Quick: (NFS) is the standard file sharing protocol used by most UNIX, Linux. NFS Share Quick provides NFS sharing with authentication permission and access to services provided by File Resource Manager.
NFS Share Advanced: Provides NFS Sharing with authentication and permission and access to services provided by File Resource Manager.

3. Now select the server and select a volume on the server or specify the folder path you want to share. To share a custom path, choose Type a custom path and browse the folder then click Next.

4. On the specify share name page, type a share name and click Next.

5. Here you have to select the sharing options you need, if you don’t know the definition read then mark them if required.
- Select any or all of the following options:
Enable Access-Based Enumeration: Prevents users from seeing files and folders
they do not have permission to access. - Allow Caching Of Share: Enables offline users to access the contents of this share.
- Enable BranchCache On The File Share: Enables BranchCache servers to cache
files accessed from this share. - Encrypt Data Access: Causes the server to encrypt remote file access to this share.

6. Now Specify the permissions to control access read or write by clicking on Customize permissions then add, remove or change users permission and click Next.

7. Confirm that the shared settings are configured properly and click Create.

The share was created successfully with its appropriate permissions, click close.

To check the folder shared go to Network>your computer then your shared files will be there.
Also you can see them by typing \\yourcomputername\ in the file explorer.
Configure file Shares using file Explorer
1. Navigate to the folder then right click and select Properties, click on sharing tab then click Advanced sharing.
2. Mark on Share this folder and enter a share name then click on permissions to add, remove or change permissions of users and click ok.
When the folder sharing is configured properly, click Apply then ok. Your folder will be shared successfully.
Also, you can manage caching of the folder by clicking on caching and select the one you want. (Caching enables offline files for the users those who have enabled offline files. You can choose if the folder should be available offline or not.

All right, this was all about configured file shares in windows server 2016, hope it would be helpful and informative.
If you have any question regarding this ask here.