- Updated on February 25, 2024
- Windows Server
The monitoring software triggers you with the error Event ID 36871: A fatal error occurred while creating a TLS client credential. The internal error state is 10013. In this article, you will learn why this is happening, and the solution for a fatal error occurred while creating a TLS client credential.
Table of contents
- A fatal error occurred while creating a TLS client credential
- Check Transport Layer Security protocols
- Transport Layer Security protocols status
- Solution for a fatal error occurred while creating a TLS client credential
- Conclusion
Sign in to the Windows Server and start Event Viewer. Navigate to Windows Logs > System. You will see error Event ID 36871. A fatal error occurred while creating a TLS client credential. The internal error state is 10013.
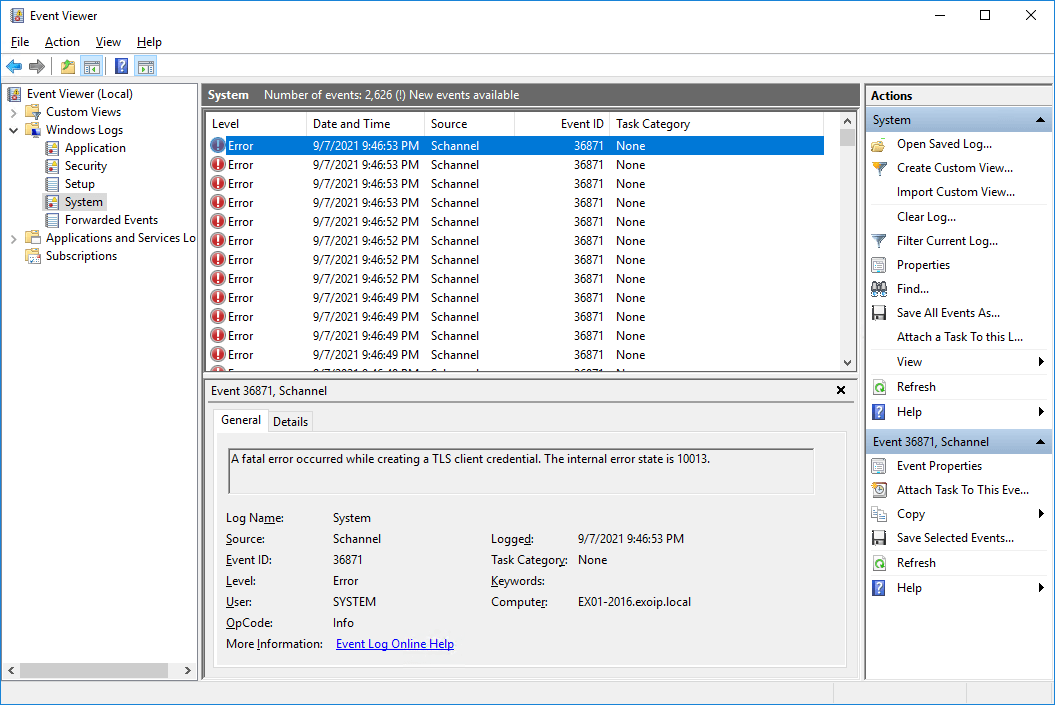
Why do we get this error, and what is the solution for a fatal error occurred while creating a TLS client credential. The internal error state is 10013?
Check Transport Layer Security protocols
Schannel is a Security Support Provider (SSP) that implements the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) Internet standard authentication protocols.
Download IIS Crypto GUI by Nartac Software. After the application is downloaded, start the application.
We see that Server Protocols and Client Protocols TLS 1.0 and TLS 1.1 are unchecked.
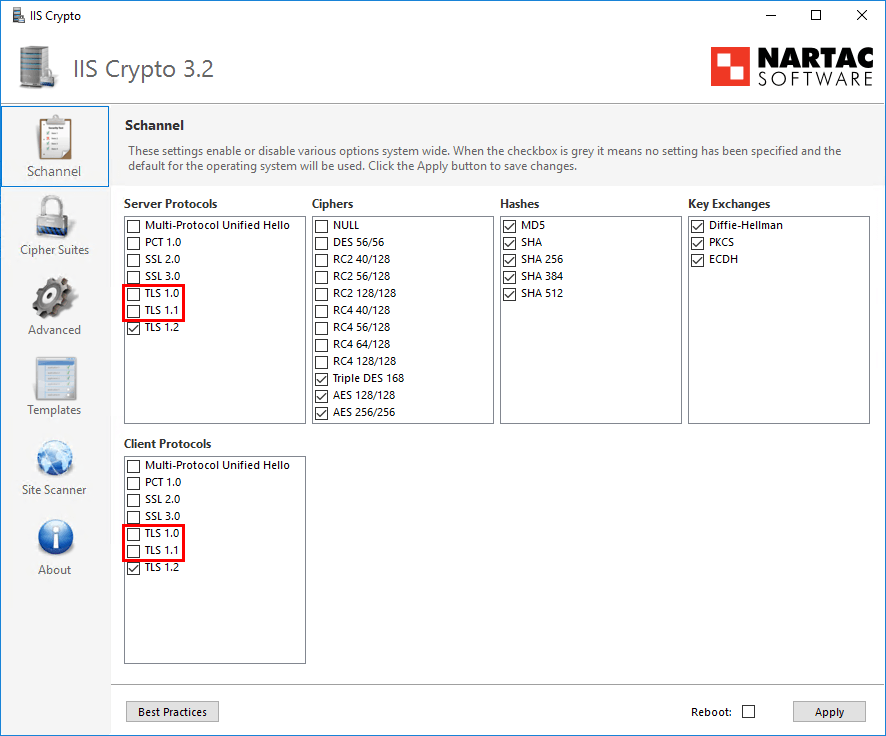
If we click on Best Practices, it will enable Server Protocols and Client Protocols TLS 1.0 and TLS 1.1. After a reboot, the event error will not show up. When doing that, we fix the problem, but we enable the deprecated protocols. That’s what we do not want.
So how do we keep TLS 1.0 and TLS 1.1 unchecked (disabled) without a fatal error TLS client credential 10013 from showing up?
Transport Layer Security protocols status
See a list of the security protocols and when they are published, including the current status.
Note: Only TLS 1.3 and TLS 1.2 are approved. The protocol TLS 1.3 is only available to enable in Windows Server 2022 or newer.
| Protocol | Published | Status |
|---|---|---|
| SSL 2.0 | 1995 | Deprecated in 2011 |
| SSL 3.0 | 1996 | Deprecated in 2015 |
| TLS 1.0 | 1999 | Deprecated in 2020 |
| TLS 1.1 | 2006 | Deprecated in 2020 |
| TLS 1.2 | 2008 | Approved |
| TLS 1.3 | 2018 | Approved |
Solution for a fatal error occurred while creating a TLS client credential
Now that we gathered all the information, we are going to enable TLS 1.2 on the system by running the script. After a reboot, we will check the Event Viewer. It should not show any errors.
- Download Enable-TLS1.2.ps1 PowerShell script if you have Windows Server 2019 or lower / Download Enable-TLS1.3.ps1 PowerShell script if you have Windows Server 2022 or higher
- Save the script in the C:\scripts folder
- Run the script from PowerShell
C:\scripts\.\Enable-TLS1.2.ps1- Reboot the Windows Server
Start Event Viewer. Expand Windows Logs and click System. The error “Event ID 36871: A fatal error occurred while creating a TLS client credential. The internal error state is 10013.” doesn’t show up anymore.
Did it work for you?
Conclusion
You learned why you get a fatal error occurred while creating a TLS client credential. The internal error state is 10013. The solution to this problem is configuring TLS 1.2 on the Windows Server. After that, you don’t see the Event ID 36871 errors in Event Viewer.
Did you enjoy this article? You may also like How to Enable TLS 1.2/TLS 1.3 on Windows Server. Don’t forget to follow us and share this article.
ALI TAJRAN is a passionate IT Architect, IT Consultant, and Microsoft MVP. He started Information Technology at a very young age, and his goal is to teach and inspire others. Read more »
A fatal error occurred while creating a TLS client credential. The internal error state is 10013″. The Windows tool prompts this message repeatedly and disturbs continuing ongoing tasks.
The fatal error occurred while creating a TLS client credential commonly appears when you launch a program, browse the web, or connect to a network. The reason is a disagreement between client and server on a mutual cipher to use to establish a secure connection. However, you can fix the internal error state is 10013 in Windows 11 or 10 simply using the methods in the upcoming parts of this post –
A fatal error occurred while creating a TLS client credential. The internal error state is 10013
Here is how to Fix A fatal error occurred while creating a TLS client credential. The internal error state is 10013 Windows 11/10 –
For Windows 10 or 11 –
Way-1: Enable TLS 1.0 and 1.1 Protocols
- Press – Windows+R.
- Type – ncpa.cpl.
- Click OK or hit Enter.
- Once the Internet properties window opens up, click on the Advanced tab.
- Scroll down and check both Use TLS 1.0 and Use TLS 1.1.
- Click Apply and then OK.
- Reboot the device and check if the error A fatal error occurred while creating a TLS client credential still appears.
Way-2: Registry tweak to fix The internal error state is 10013
- Click – Search.
- Type – regedit. See – 9 Ways to Open Registry Editor in Windows 10.
- Hit – Enter.
- On User Account Control prompt, select – Yes.
- On the Registry Editor, navigate to the location –
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client
- Go to right pane, right click and select New => DWORD (32-bit) Value.
- Name the value DisabledByDefault.
- Double click on this value and enter Value data 0.
- Click – OK.
- Similarly, create one more value named, Enabled. and put value data 1 for this.
- Close the registry editor and restart the PC.
For Windows Server
Way-3: Enable deprecated Transport Layer Security protocols
- Click on IIS Crypto GUI and download the tool.
- Double click on IISCrypto.exe and launch the app.
- By default, it opens with the Schannel tab.
- Check TLS 1.0 and TLS 1.1 in both the Server protocols and Client protocols sections.
- Click on – Apply. These are the deprecated protocols.
Way-4: Solve A fatal error occurred while creating a TLS client credential by running a PowerShell Script
You can also enable TLS 1.2 using a script. Simply follow the steps –
- Download TLS1.2_enable.
- Unpack the file by extracting the file.
- Right-click on the TLS1.2_enable.ps1 and select Run with PowerShell.
- Alternatively, launch PowerShell ISE.
- Copy the following script –
New-Item 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -Force | Out-Null New-ItemProperty -path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -name 'SystemDefaultTlsVersions' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319' -name 'SchUseStrongCrypto' -value '1' -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -Force | Out-Null New-ItemProperty -path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -name 'SystemDefaultTlsVersions' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319' -name 'SchUseStrongCrypto' -value '1' -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null Write-Host 'TLS 1.2 has been enabled.'
- Paste the script in PowerShell ISE.
- Press – Enter.
- Restart the Windows Server.
- Now open Start Event Viewer. Go to Windows Logs and click – System.
- You will no longer find The error “Event ID 36871: A fatal error occurred while creating a TLS client credential. The internal error state is 10013.”
Methods list:
Way-1: Enable TLS 1.0 and 1.1 Protocols
Way-2: Registry tweak to fix The internal error state is 10013
Way-3: Enable deprecated Transport Layer Security protocols
Way-4: Run a PowerShell Script
That’s all!!
I’ve often seen Windows Server administrators puzzled by recurring Schannel errors that disrupt daily operations. Let’s explore these error messages and clarify how to successfully troubleshoot them.
TOC
Understanding Schannel Errors on Windows Server
Schannel errors, specifically Event ID 36871 and 36874, appear when there are problems with Windows’ TLS/SSL handshake processes. Schannel (Secure Channel) is a Windows security package responsible for secure communications using protocols like TLS 1.2. When a mismatch or misconfiguration arises, the server struggles to establish a secure channel, triggering error messages that can fill your Event Viewer logs.
Breaking Down the Error Messages
Event ID 36871
This error generally reads:
“A fatal error occurred while creating a TLS client credential. The internal error state is 10013 (or 10010).”
When you see these internal error codes, it usually indicates:
- A mismatch between the server’s and client’s configured TLS versions.
- An issue with the server’s cipher suites.
- A certificate-related error, such as missing or invalid certificates.
Event ID 36874
The text often looks like:
“A TLS 1.2 connection request was received from a remote client application, but none of the cipher suites supported by the client application are supported by the server. The TLS connection request has failed.”
In this case, the client and server cannot agree on a mutual cipher suite, leading to a dropped connection. While Event ID 36874 is specifically about TLS 1.2, the core issue remains cipher suite mismatch or a lack of alignment in cryptographic settings.
Why These Errors Occur
There are several causes for Schannel issues on Windows Server:
- Cipher Suite Conflicts
- If the server only allows newer, more secure cipher suites and the client attempts older or disabled suites, the handshake will fail. Conversely, if the server lacks robust cipher suites and the client requires something more modern, the same issue arises.
- Disabled TLS Versions
- If the server registry settings disable TLS 1.2 or only partially enable it, Schannel can’t form a stable TLS 1.2 connection.
- Misconfigured .NET Settings
- Certain applications that rely on the .NET Framework may require registry-based changes to enable strong cryptography, especially for TLS 1.2.
- Certificate Problems
- Expired or invalid certificates, missing certificate chain intermediates, or using a certificate that doesn’t match the server’s fully qualified domain name (FQDN) can lead to these Schannel events.
- Inconsistent Patch Levels
- Missing Windows updates or partial installation of security patches can cause cryptographic components to misbehave.
Symptoms and Potential Impact
Schannel errors don’t just clutter your Event Viewer logs; they can also cause:
- Application Downtime: Web applications or services that require TLS-secured communication might fail to connect.
- Remote Desktop Issues: If RDP relies on TLS for encryption, Schannel errors could potentially disrupt remote sessions.
- Email Services & Authentication Failures: Exchange or third-party mail servers that need encrypted channels could fail to send or receive messages properly.
- Performance Degradation: Repeated handshake attempts that fail can consume resources, leading to overall reduced server performance.
Common Observations
Many administrators have reported that enabling TLS 1.2 via registry and applying the latest Windows patches does not immediately clear these errors. In some instances, older protocols like SSL 3.0 or TLS 1.0 had been disabled, but certain clients or applications still depended on them. This mismatch can keep the errors occurring even with the best intentions to use only modern protocols.
Step-by-Step Solutions
Below are detailed methods to align your Windows Server settings, .NET configurations, and certificates to eliminate Schannel errors.
1. Verify and Align Cipher Suites
Start by confirming what cipher suites your Windows Server offers and ensuring they match at least one of the client-supported suites.
Using IIS Crypto or PowerShell
- IIS Crypto: A straightforward GUI tool from Nartac Software that lists protocols, ciphers, and hashes.
- PowerShell: On Windows Server 2019 and later, you can inspect cipher suite configuration using PowerShell cmdlets. For example:
Get-TlsCipherSuite | Format-Table Name, Enabled, Priority
This reveals which cipher suites are enabled and their priority order.
Recommended Cipher Suites
Modern cipher suites typically include AES-based encryption with GCM mode. Examples:
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
Ensure that older cipher suites using RC4, 3DES, or MD5 hashing are disabled to maintain stronger security. You can reorder them or remove insecure suites using IIS Crypto or through registry edits.
2. Configure Strong Cryptography in .NET
Many enterprise applications built on the .NET Framework rely on .NET’s cryptographic settings rather than just the OS-level Schannel configuration. To ensure .NET apps can use TLS 1.2, set the following registry keys:
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v2.0.50727]
"SystemDefaultTlsVersions" = dword:00000001
"SchUseStrongCrypto" = dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319]
"SystemDefaultTlsVersions" = dword:00000001
"SchUseStrongCrypto" = dword:00000001Double-Check .NET Version Compatibility
- Applications running on older .NET Framework versions (e.g., 3.5) might not inherently support TLS 1.2.
- Confirm that your .NET environment supports TLS 1.2 or plan an upgrade if needed.
3. Enable TLS 1.2 in the Registry
Even though you might have TLS 1.2 enabled, it’s worth validating these registry paths:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\ClientMake sure the following values are in place:
| Value Name | Type | Value Data |
|---|---|---|
| Enabled | DWORD | 1 |
| DisabledByDefault | DWORD | 0 |
Why This Matters
Some hotfixes or group policy changes might reset these keys, causing the server or client side to revert to less secure defaults. If these keys are missing, create them with the appropriate values. Always back up your registry before modifications.
4. Check Certificates in the Server Certificate Store
Open the Certificate Manager (certlm.msc) on your Windows Server and review the Personal > Certificates section:
- Valid Dates: Ensure the certificate is current (not expired) and not close to expiration.
- Key Usage & Chain: Make sure the key usage includes server authentication, and the certificate chain is fully trusted.
- SAN (Subject Alternative Name): Confirm the FQDN or hostname matches the certificate’s SAN.
If your server is using multiple SSL certificates (e.g., for different subdomains), verify each one individually.
5. Keep Windows Updated
While you may have applied the latest monthly rollups, occasionally Microsoft releases targeted Schannel or TLS updates as part of cumulative or optional updates. Double-check Windows Update or WSUS to see if any optional security fixes address TLS handshake issues.
6. Confirm No Dependencies on Older Protocols
Modern security standards recommend disabling TLS 1.0, TLS 1.1, SSL 2.0, and SSL 3.0. However, if older applications or devices still rely on these protocols, the server might continue to log Schannel errors when they try to connect. A typical scenario is a legacy printer or scanner that only supports TLS 1.0, which fails to communicate properly with an updated Windows Server.
Advanced Troubleshooting Techniques
If none of the standard fixes solve your Schannel errors, you can delve deeper with the following:
1. Enable Schannel Event Logging
Schannel offers a debug logging feature to expose detailed handshake progress. You can enable it via registry:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\EventLoggingSet the EventLogging DWORD to 7. This will produce verbose logs in the System event log, helping you identify exactly which ciphers or protocols are attempted.
2. Use Network Monitoring Tools
- Wireshark: Capture traffic on the server to see the TLS handshake process in detail. This helps confirm which cipher suites are proposed by the client and accepted (or rejected) by the server.
- Microsoft Message Analyzer (Legacy): Although no longer actively developed, older environments might still rely on it to review Schannel connections.
3. Group Policy Overrides
In some domains, group policies might override local server registry settings. Check for any GPOs that specifically set cipher suites or TLS protocols:
- Open the Group Policy Management Console (GPMC).
- Review computer-based policies under “Administrative Templates” or “Security Settings.”
- Look for settings related to “SSL Configuration Settings” or “Schannel” within the policy tree.
Even if you set registry keys locally, these can be overridden at the next GPO refresh interval.
Practical Example: Aligning Cipher Suites Step by Step
Below is an example table showing how an administrator might align cipher suites between a Windows Server 2022 and a legacy application server that also supports TLS 1.2:
| Step | Action | Tool/Command | Outcome |
|---|---|---|---|
| 1 | List enabled cipher suites | Get-TlsCipherSuite \| Format-Table Name, Enabled |
Identify which suites are available on the Windows Server. |
| 2 | Identify client’s supported ciphers | Review client’s TLS logs or application config | See which ciphers the client expects to negotiate. |
| 3 | Match and prioritize secure suites | Use IIS Crypto or registry edits | Ensure at least one or two identical secure suites are present. |
| 4 | Test handshake | Use openssl s_client -connect [server]:443 -tls1_2 (if applicable) |
Validate the handshake works using a known TLS 1.2-compatible client. |
| 5 | Monitor Event Logs | Re-check Event Viewer for Schannel errors | Confirm that the mismatch error (Event ID 36874) no longer appears. |
When to Seek Additional Help
Some scenarios require deeper expertise:
- Custom or Legacy Applications: If you have custom-coded software that references legacy .NET frameworks or uses certain cryptography APIs, you may need developer intervention to recompile or update those applications.
- Strict Compliance Environments: If you’re managing environments subject to strict compliance standards (PCI-DSS, HIPAA, etc.), you must ensure that only authorized cipher suites and protocols are used while maintaining functionality.
- Repeated Certificate Failures: When certificates repeatedly fail or you see chain-of-trust issues, consider involving your Certificate Authority (CA) or a network security professional to re-provision your PKI (Public Key Infrastructure).
Frequently Asked Questions
Q1: Do I need to enable TLS 1.1 if TLS 1.2 is enabled?
A1: Generally, no. TLS 1.2 is more secure and is widely supported. You can safely disable older protocols like TLS 1.1 to maintain a strong security posture unless you have applications that strictly require them.
Q2: Why do these errors persist after applying Windows updates?
A2: Sometimes, post-update reboots or finalizing certain KB patches is necessary. Furthermore, registry changes might not be recognized until a reboot. Always verify that you’ve completed all steps and confirm the correct registry settings remain in place after an update.
Q3: Are there performance implications to using only newer cipher suites?
A3: In modern server hardware with optimized AES instructions, the performance impact of using advanced suites like AES-GCM is often negligible. In fact, they can be more efficient than older ciphers. Unless you’re dealing with extremely high-volume encryption or older hardware, performance is usually improved with modern suites.
Conclusion
Resolving Schannel Event IDs 36871 and 36874 on Windows Server 2022 or 2019 involves ensuring alignment in TLS versions, cipher suites, and certificate configurations. Begin with verifying your server’s TLS registry settings, matching cipher suites between client and server, and confirming that .NET applications are configured for strong cryptography. Keep your server patched, regularly review your certificate stores, and remain alert for older protocols still in use by legacy systems. By following these steps, you can maintain a secure, modern, and fully functional environment free from repetitive Schannel warnings.
If you continue seeing persistent issues even after implementing these measures, it may be time to delve deeper into advanced diagnostics with Wireshark or Schannel debug logs. In particularly challenging cases, Microsoft Support or a dedicated security consultant can help pinpoint the missing link in your TLS configuration.
IMPORTANT NOTE: The guidance in this post will disable support for null SSL/TLS cipher suites on the DirectAccess server. This will result in reduced scalability and performance for all clients, including Windows 8.x and Windows 10. It is recommended that TLS 1.0 not be disabled on the DirectAccess server if at all possible.
When performing security hardening on the DirectAccess server it is not uncommon to disable weak cipher suites or insecure protocols such as SSL 3.0 and TLS 1.0. However, after disabling SSL 3.0 and TLS 1.0 you will find that it is no longer possible generate reports. Clicking the Generate Report link in the Remote Access Management console returns no data.

In addition, the System event log indicates Schannel errors with Event ID 36871. The error message states that “A fatal error occurred while creating a TLS client credential. The internal error state is 10013.”

To resolve this issue and restore DirectAccess reporting functionality you must enable the use of FIPS compliant encryption algorithms on the DirectAccess server. This change can be made locally or via Active Directory group policy. Open the Group Policy Management Console (gpmc.msc) for Active Directory GPO, or the Local Group Policy Editor (gpedit.msc) on the DirectAccess server and navigate to Computer Configuration > Windows Settings > Security Settings > Local Policies > Security Options. Double-click System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing and select Enabled.

If using Active Directory GPO, ensure that the GPO is applied all DirectAccess servers in the organization. A restart is not required for this setting to take effect. Once this change has been made, reporting should work as expected.
Additional Resources
DirectAccess IP-HTTPS SSL and TLS Insecure Cipher Suites
DirectAccess Video Training Courses on Pluralsight
Implementing DirectAccess with Windows Server 2016 Book on Amazon.com
Posted in DirectAccess, Encryption, IP-HTTPS, IPv6 Transition, Remote Access, Security, SSL and TLS, troubleshooting, Windows 10, Windows 7, Windows 8, Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows Server 2016
Posted by Richard M. Hicks on June 26, 2017
DirectAccess Reporting Fails and Schannel Event ID 36871 after Disabling TLS 1.0
Schannel error messages are common and can have many different causes. Here is a rather specific error message that occurred on a Windows Server 2022 after the operating system underwent standard hardening. After disabling outdated cipher suites and SSL / TLS protocols, the following error message appeared very frequently in the system event log:
Source: Schannel
Event ID: 36871
A fatal error occurred while creating a TLS client credential. The internal error state is 10013.
The SSPI client process is svchost[wlidsvc] (PID: 4828).
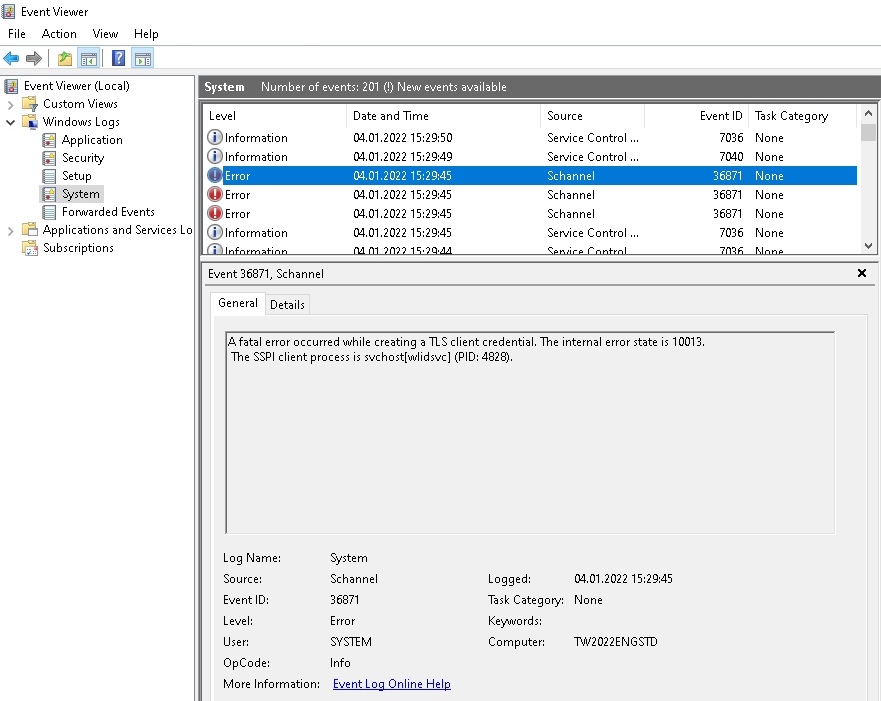
The solution to this problem was quite simple, because the error message already points in the right direction. The error message indicates that the problematic service is «wlidsvc», which is started by «svchost» (see screenshot of the error message). WLIDSVC is part of the «Microsoft Account Sign-In Assistant» service and enables logon with Microsoft accounts. However, this service is not required on Windows servers and can therefore be deactivated:
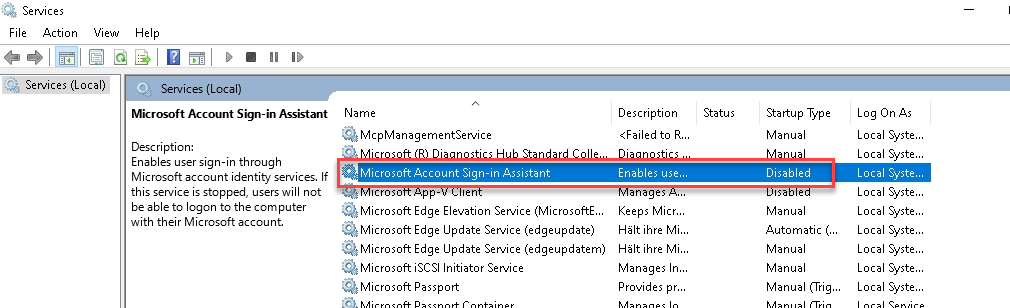
The «Microsoft Account Sign-In Assistant» service is set to the «Manual» start type by default and starts cyclically. Whenever the service is started, the above error messages appear in Eventlog. With Windows Server 2016 it was still OK to deactivate the service, so I assume that this is also the case with Windows Server 2022. See here for more information:
- https://github.com/MicrosoftDocs/windowsserverdocs/blob/master/WindowsServerDocs/security/windows-services/security-guidelines-for-disabling-system-services-in-windows-server.md#microsoft-account-sign-in-assistant
After the service was deactivated, the error messages no longer occurred.
Here you can find the Microsoft Security Baselines for Windows Server 2022 and Edge:
- https://www.microsoft.com/en-us/download/details.aspx?id=55319
There will be a separate article on the topic of «Hardening Windows Server 2022» here.
