Written on . Posted in Windows Server 2008
Страница 8 из 15
Теперь, когда роль RRAS установлена, нам нужно активировать сервисы RRAS, также как мы делали это в предыдущих версиях Windows. Нам нужно активировать функцию VPN сервера и сервисы NAT. С активацией компонента VPN сервера все понятно, но вы можете поинтересоваться, зачем нужно активировать NAT сервер. Причина активации сервера NAT кроется в том, что внешние клиенты могут получать доступ к серверу сертификации (Certificate Server), чтобы соединяться с CRL. Если клиент SSTP VPN не сможет загрузить CRL, SSTP VPN соединение работать не будет.
Для того, чтобы открыть доступ к CRL, мы настроим VPN сервер в качестве NAT сервера и опубликуем CRL, используя обратимый NAT. В сетевом окружении компаний у вас, скорее всего, будут брандмауэры, например ISA Firewall, перед сервером сертификации, поэтому вы сможете публиковать CRL с помощью брандмауэров. Однако в этом примере единственный брандмауэр, которым будем пользоваться, это брандмауэр Windows Firewall на сервере VPN, поэтому в этом примере нам нужно настроить VPN сервер в качестве NAT сервера.
Для активации сервисов RRAS выполните следующие шаги:
- В Server Manager разверните вкладку Роли в левой панели консоли. Разверните вкладку Политика сети и Службы доступа и кликните по вкладке Маршрутизация и Удаленный доступ. Правой клавишей кликните по вкладке Маршрутизация и Удаленный доступ и нажмите Настроить и активировать маршрутизацию и удаленный доступ.

Рисунок 14
- Нажмите Далее в окне Welcome to the Routing and Remote Access Server Setup Wizard.
- На странице Конфигурация выберите опцию Доступ к виртуальным частным сетям и NAT и нажмите Далее.

Рисунок 15
- На странице VPN соединение выберите NIC в секции Интерфейсы сети, которая представляет внешний интерфейс VPN сервера. Затем нажмите Далее.

Рисунок 16
- На странице Назначение IP адресов выберите опцию Автоматически. Мы можем выбрать эту опцию, потому что у нас установлен DHCP сервер на контроллере домена за VPN сервером. Если у вас нет DHCP сервера, тогда вам нужно будет выбрать опцию Из определенного списка адресов, а затем внести список адресов, которые VPN клиенты смогут использовать при подключении к сети через шлюз VPN. Жмем Далее.

Рисунок 17
- На странице Управление удаленным доступом нескольких серверов выбираем Нет, использовать маршрутизацию и удаленный доступ для аутентификации запросов соединения. Эту опцию мы используем, когда недоступны NPS или RADIUS серверы. Поскольку VPN сервер является членом домена, можно аутентифицировать пользователей, используя учетные записи домена. Если VPN сервер не входит в домен, тогда только локальные учетные записи VPN сервера можно использовать, если только вы не решите использовать NPS сервер. Я напишу статью об использовании NPS сервера в будущем. Жмем Далее.

Рисунок 18
- Прочтите общую информацию на странице Завершение работы мастера настройки маршрутизации и удаленного доступа и нажмите Закончить.
- Нажмите OK в диалоговом окне Маршрутизация и удаленный доступ, которое говорит вам о том, что распределение DHCP сообщений требует агента распределения DHCP.
- В левой панели консоли разверните вкладку Маршрутизация и удаленный доступ и затем нажмите на вкладке Порты. В средней панели вы увидите, что WAN Miniport соединения для SSTP теперь доступны.

Рисунок 19
- Click Start, point to Administrative Tools, and then click Routing and Remote Access.
- In the left pane of the console, click the server that matches the local server name. …
- Right-click the server, and then click Configure and Enable Routing and Remote Access to start the Routing and Remote Access Server Setup Wizard. Click Next.
- Click Remote access (dial-up or VPN) to permit remote computers to dial in or connect to this network through the Internet. Click Next.
- Click VPN for virtual private access, or click Dial-up for dial-up access, depending on the role you want to assign to this server.
- On the VPN Connection page, click the network interface that is connected to the Internet, and then click Next.
- On the IP Address Assignment page, do one of the following: If a DHCP server will be used to assign addresses to remote clients, click Automatically, and then click Next. …
- Accept the default setting of No, use Routing and Remote Access to authenticate connection requests, and then click Next.
- Click Finish to enable the Routing and Remote Access service and to configure the remote access server. …
To enable Remote Access, open the Routing and Remote Access console from the Administrative Tools menu, right-click the computer running Windows Server 2008 R2
Windows Server 2008 R2
Seven editions of Windows Server 2008 R2 were released: Foundation, Standard, Enterprise, Datacenter, Web, HPC Server and Itanium, as well as Windows Storage Server 2008 R2. A home server variant called Windows Home Server 2011 was also released.
that you want to host this role, and then click Configure And Enable Routing And Remote Access.Jul 15, 2011
Full
Answer
How do I configure routing and remote access (RRAS) in Windows Server 2008?
The first step is to install the Routing and Remote Access (RRAS) role in Windows 2008 Server. If you go into the Add Roles Wizard, the RRAS role can be difficult to find because what you really need to add is the Network Policy and Access Services role then the Routing and Remote Access Services Role (as you see in Figure 4 and Figure 5).
How do I enable the routing and remote access service?
To Enable the Routing and Remote Access Service Click Start, point to Administrative Tools, and then click Routing and Remote Access. In the left pane of the console, click the server that matches the local server name. If the icon has a red arrow in the lower-right corner, the Routing and Remote Access service isn’t enabled. Go to step 3.
How do I enable remote access to a Windows Server?
Right-click the server, and then click Configure and Enable Routing and Remote Accessto start the Routing and Remote Access Server Setup Wizard. Click Next. Click Remote access (dial-up or VPN)to permit remote computers to dial in or connect to this network through the Internet.
How many routing options are there in Windows Server 2008?
Windows Server 2008 has one solid static routing option and one scalable dynamic routing option – RIPV2. I discussed how OSPF has been removed from Windows 2008 (and how I feel about that).
How do I set up Remote Access and routing?
Click Start, point to Administrative Tools, and then click Routing and Remote Access. In the console tree, expand Routing and Remote Access, expand the server name, and then click Remote Access Policies. Right-click the right pane, point to New, and then click Remote Access Policy.
How do I setup Remote Desktop on Windows Server 2008?
How to configure Remote Desktop in Windows Server 2008 R2 step by…Step 1: Begin the installation. … Step 2: Select Remote Desktop Services roles you want to install. … Step 3: Pick the license mode. … Step 4: Allow access to Remote Desktop Session Host (not required) … Step 5: Configure the client experience.More items…•
What is the use of routing and remote access service?
RRAS is a software router and an open platform for routing and networking. It offers routing services to businesses in local area network (LAN) and wide area network (WAN) environments or over the Internet by using secure VPN connections.
How do I set up RRAS?
Right-click the VPN server, then select Configure and Enable Routing and Remote Access. The Routing and Remote Access Server Setup Wizard opens. In the Welcome to the Routing and Remote Access Server Setup Wizard, select Next. In Configuration, select Custom Configuration, and then select Next.
How do I enable Remote Desktop Services?
Set up the PC you want to connect to so it allows remote connections:Make sure you have Windows 10 Pro. … When you’re ready, select Start > Settings > System > Remote Desktop, and turn on Enable Remote Desktop.Make note of the name of this PC under How to connect to this PC.
What is port for RDP?
Overview. Remote Desktop Protocol (RDP) is a Microsoft proprietary protocol that enables remote connections to other computers, typically over TCP port 3389.
What is the main purpose of a RAS server?
A remote access server (RAS) is a type of server that provides a suite of services to remotely connected users over a network or the Internet. It operates as a remote gateway or central server that connects remote users with an organization’s internal local area network (LAN).
What is the difference between RAS and RRAS?
Microsoft Remote Access Server (RAS) is the predecessor to Microsoft Routing and Remote Access Server (RRAS). RRAS is a Microsoft Windows Server feature that allows Microsoft Windows clients to remotely access a Microsoft Windows network.
How can you install enable and configure Remote Access services on server?
Install the Remote Access roleOn the DirectAccess server, in the Server Manager console, in the Dashboard, click Add roles and features.Click Next three times to get to the server role selection screen.On the Select Server Roles dialog, select Remote Access, and then click Next.Click Next three times.More items…•
Is IIS required for RRAS?
RRAS: Features are managed in the Routing and Remote Access console. The Remote Access server role is dependent on the following features: — Web Server (IIS): Required to configure the network location server and default web probe.
How do I configure Windows Server Routing?
Right-click the server, and select Configure and Enable Routing and Remote Access.When the wizard opens, click Next.Select Network address translation (NAT) and click Next.Select the network interface that your users will use to connect to the internet, and then click Next.More items…
Can DHCP support Remote Access?
When you enable Dynamic Host Configuration Protocol (DHCP) to assign a static IP address to an onboard network interface during first-time setup, you can complete the configuration remotely by using an SSH client. If your system includes an e0M interface, the system broadcasts a DHCP request through it.
What is RD Session Host?
The Remote Desktop Session Host (RD Session Host) holds the session-based apps and desktops you share with users. Users get to these desktops and apps through one of the Remote Desktop clients that run on Windows, MacOS, iOS, and Android. Users can also connect through a supported browser by using the web client.
What is the new name of terminal server?
Remote Desktop ServicesTerminal Services has been renamed to Remote Desktop Services.
What is the importance of Remote Desktop Services?
The major benefit of a remote desktop connection is being able to connect to your data from anywhere in the world. Your data is in one place that is easy to see and you no longer have to have software installed on your own computer.
How to access CRL distribution points?
Click the Details tab of the certificate and scroll down to the CRL Distribution Points entry and click on that entry. In the lower pane you will see the various distribution points based on the protocol used to access those points. In the certificate seen in the figure below, you can see that we need to allow the SSL VPN client access to the CRL via the URL:
How do you know what URL the SSL VPN client needs to connect to in order to download the CRL?
How do you know what URL the SSL VPN client needs to connect to in order to download the CRL? That information is contained within certificate itself. If you go to the VPN server again and double click on the certificate in the IIS console, as you did earlier, you will be able to find this information.
How to install IIS Web Server 2008?
Perform the following steps on the VPN server to install the IIS Web server role: Open the Windows 2008 Server Manager. In the left pane of the console, click the Roles node. Figure 1. Click the Add Roles link on the right side of the right pane. Click Next on the Before You Begin page.
How to add a role in a server?
In the Server Manager, click the Roles node in the left pane of the console. In the Roles Summary section, click the Add Roles link. Click Next on the Before You Begin page. On the Select Server Roles page, put a checkmark in the Network Policy and Access Services checkbox.
What certificate is needed for VPN?
The VPN server needs a machine certificate to create the SSL VPN connection with the SSL VPN client computer. The common name on the certificate must match the name that the VPN client will use to connect to the SSL VPN gateway computer.
Where is the certificate icon in IIS?
In this example, the name of the server is W2008RC0-VPNGW. Click on the Server Certificates icon in the right pane of the IIS console.
Does VPN reverse NAT?
When the connection reaches the external interface of the VPN server, the VPN server will reverse NAT the connection to the Certificate Server. If you are using an advanced firewall, such as an ISA Firewall, you could make publishing the CRL site more secure, by allowing access only to the CRL, and not the entire site.
Introduction
With Windows Server 2008, there are a number of changes to networking and Routing and Remote Access. In fact, I wrote about some of these changes in my WindowsNetworking.com article: Which Windows Server 2008 Networking Services were removed and which should you use instead?In that article, I covered how OS…
See more on techgenix.com
Should You Use Static Or Dynamic Routing?
-
The question of whether you should use static or dynamic routing is really a question of administrative overhead. In the end, the result of your network traffic being routed to the correct network should be the same, no matter what method you choose. With static routing, you must make an entry on your Windows Server for every network that will be routed by that server. Thus…
See more on techgenix.com
Static Routing in Windows Server 2008
-
Static routing in Windows Server is nothing new. We have been using the route command for years. You can configure static routing in Windows 2008 Server using either the route command or using the GUI. However, if you use the Windows GUI interface, those routes will not be listed in the CLI interface, when you type route print. Thus, I highly recommend that if you are going to us…
See more on techgenix.com
Summary
-
Windows Server 2008 has one solid static routing option and one scalable dynamic routing option – RIPV2. I discussed how OSPF has been removed from Windows 2008 (and how I feel about that). We talked about why you would use static routing versus dynamic routing. Finally, I showed you how to configure static routing with the route command and dynamic routing by installing RI…
See more on techgenix.com
Popular Posts:
One colleague ask me to help him with detailed steps how to configure VPN on server 2008 R2 and how to configure Windows XP and Windows 7 clients. So here it is.
Configuring VPN start with adding server role for RRAS.
Just follow next two pictures what to choose


Wait for wizard to finish, and then you will get this picture
Now you have role installed. You must configure and enable RRAS
When you click on option Configure and Enable RRAS new wizard will start. Just follow the wizard in next 5 pictures.



NOTE: You MUST have two NIC configured, one for internal use (LAN) and one for external use (WWW)


I prefer to choose IP address range and number of possible connecting clients son next picture will shown how to do that


If you have AD infrastructure configure your RRAS like this

After this you will get this picture and click Finish

Now your Server have successfully configured RRAS.

Configuring client on Windows 7 for VPN access
Go to network and sharing center and choose option set up a new connection or network

Choose option Connect to a workplace

For previously described configuration of RRAS option Use my Internet connection (VPN) will be right choice.

Type your DNS name of RRAS server or public IP address, and follow steps in next three pictures.



Additional option as authentication protocols can be founded in properties of your VPN connection. Most commonly used is already checked.
Configuring client on Windows XP for VPN access
On Windows XP go to Network Connections and click Create a new connection

A wizard will start. Follow next three pictures.



Choose name for your VPN connection

Type DNS name or public IP address of your previously configured RRAS (VPN) server

Well done you are configure client for VPN access. Now you need to type your username and password before connect.

Steps for configuring additional authentication protocols (if needed) is described in next two pictures. At first you must click Properties.

I hope that this is helpful
BR
D.
A common method of securing information sent across
unsecured networks is to create a virtual private network (VPN), which
is effectively a connection between two private nodes or networks that
is secured and encrypted to prevent unauthorized snooping of the traffic
between the two connections. From the client perspective, a VPN looks
and feels just like a normal network connection between different segments on a network—hence the term virtual private network.
Data that is sent across a
VPN is encapsulated, or wrapped, in a header that indicates its
destination. The information in the packet is then encrypted to secure
its contents. The encrypted packets are then sent across the network to
the destination server, using what is known as a VPN tunnel.
The Windows Server 2008 R2
RRAS role allows for the creation of VPNs, and integrates with the NPS
role to provide for validation of client health before creating a VPN
session.
Note
Virtual private network
support in Windows Server 2008 R2 provides for simple VPN tunnels to be
created. For more complex scenarios where specific rules need to be
created and application-layer filtering of the VPN traffic is needed,
look at Microsoft’s Forefront Edge line of products, which includes the
Forefront Threat Management Gateway (previously called Internet Security
and Acceleration or ISA Server) and the Forefront Unified Access
Gateway products.
Exploring VPN Tunnels
The connection made
by VPN clients across an unsecured network is known as a VPN tunnel. It
is named as such because of the way it “tunnels” underneath the regular
traffic of the unsecured network.
VPN tunnels are logically
established on a point-to-point basis but can be used to connect two
private networks into a common network infrastructure. In many cases,
for example, a
VPN tunnel serves as a virtual wide area network (WAN) link between two
physical locations in an organization, all while sending the private
information across the Internet. VPN tunnels are also widely used by
remote users who log on to the Internet from multiple locations and
establish VPN tunnels to a centralized VPN server in the organization’s
home office. These reasons make VPN solutions a valuable asset for
organizations, and one that can be easily established with the
technologies available in Windows Server 2008 R2.
Note
VPN tunnels can either be
voluntary or compulsory. In short, voluntary VPN tunnels are created
when a client, usually out somewhere on the Internet, asks for a VPN
tunnel to be established. Compulsory VPN tunnels are automatically
created for clients from specific locations on the unsecured network,
and are less common in real-life situations than are voluntary tunnels.
Tunneling Protocols
The tunneling protocol is
the specific technology that defines how data is encapsulated,
transmitted, and unencapsulated across a VPN connection. Varying
implementations of tunneling protocols exist, and correspond with
different layers of the Open System Interconnection (OSI)
standards-based reference model. The OSI model is composed of seven
layers, and VPN tunneling protocols use either Layer 2 or Layer 3 as
their unit of exchange. Layer 2, a more fundamental network layer, uses a
frame as the unit of exchange, and Layer 3 protocols use a packet as a
unit of exchange.
The most common Layer 2 VPN
protocols are the Point-to-Point Tunneling Protocol (PPTP) and the Layer
2 Tunneling Protocol (L2TP), both of which are fully supported
protocols in Windows Server 2008 R2.
PPTP and L2TP Protocols
Both PPTP and L2TP are based
on the well-defined Point-to-Point Protocol (PPP) and are consequently
accepted and widely used in VPN implementations. L2TP is the preferred
protocol for use with VPNs in Windows Server 2008 R2 because it
incorporates the best of PPTP, with a technology known as Layer 2
Forwarding. L2TP allows for the encapsulation of data over multiple
network protocols, including IP, and can be used to tunnel over the
Internet. The payload, or data to be transmitted, of each L2TP frame can
be compressed, as well as encrypted, to save network bandwidth.
Both PPTP and L2TP build on a
suite of useful functionality that was introduced in PPP, such as user
authentication, data compression and encryption, and token card support.
These features, which have all been ported over to the newer
implementations, provide for a rich set of VPN functionality.
L2TP/IPSec Secure Protocol
Windows Server 2008 R2
uses an additional layer of encryption and security by utilizing IP
Security (IPSec), a Layer 3 encryption protocol, in concert with L2TP in
what is known, not surprisingly, as L2TP/IPSec. IPSec allows for the
encryption of the L2TP header and trailer
information, which is normally sent in clear text. This also has the
added advantage of dual-encrypting the payload, adding an additional
level of security into the mix.
L2TP/IPSec has some distinct advantages over standard L2TP, namely the following:
-
L2TP/IPSec
allows for data authentication on a packet level, allowing for
verification that the payload was not modified in transit, as well as
the data confidentiality that is provided by L2TP. -
Dual-authentication mechanisms stipulate that both computer-level and user-level authentication must take place with L2TP/IPSec.
-
L2TP
packets intercepted during the initial user-level authentication cannot
be copied for use in offline dictionary attacks to determine the L2TP
key because IPSec encrypts this procedure.
An L2TP/IPSec packet
contains multiple, encrypted header information and the payload itself
is deeply nested within the structure. This allows for a great deal of
transport-level security on the packet itself.
Enabling VPN Functionality on an RRAS Server
By installing the Routing and
Remote Access Service (RRAS) on the server, the ability to allow VPN
connections to and/or from the server is enabled. The following type of
VPN connections can be created:
-
VPN gateway for clients—
The most common scenario, this involves the RRAS server being the
gateway into a network for VPN clients. This scenario requires the
server to have two network cards installed. -
Site-to-site VPN—
In this scenario, the RRAS server creates a VPN tunnel between another
RRAS server in a remote site, allowing for traffic to pass unimpeded
between the networks, but in an encrypted state. -
Dial-up RAS server— In this layout, the server is installed with a modem or pool of modems and provides for dial-in capabilities.
-
NAT between networks—
On an RRAS server installed in Routing mode, this deployment option
provides for Network Address Translation (NAT) between network segments.
For example, on one network, the IP addresses might be public, such as
12.155.166.x, while on the internal network they might be 10.10.10.x.
The NAT capability translates the addresses from public to private and
vice versa. -
Routing between networks—
On an RRAS server installed in Routing mode, this deployment option
allows for direct routing of the traffic between network segments. -
Basic firewall—
The RRAS server can act as a simple Layer 3 router, blocking traffic by
port. For more secure scenarios, use of an advanced Layer 7 firewall
such as Microsoft’s Forefront Threat Management Gateway (previously
called Internet Security and Acceleration or ISA Server) is recommended.
Note
Setting
up a VPN connection requires the server to have at least two network
cards installed on the system. This is because the VPN connections must
be coming from one network and subsequently passed into a second
network, such as from the demilitarized zone (DMZ) network into the
internal network.
To set up the RRAS server for the most common scenario, VPN gateway, perform the following tasks:
|
1. |
Open the Routing and Remote Access MMC tool (Start, All Programs, Administrative Tools, Routing and Remote Access). |
|
2. |
Select |
|
3. |
Click Action, Configure and Enable Routing and Remote Access. |
|
4. |
Click Next at the Welcome page. |
|
5. |
Choose from the list of configuration settings, as shown in Figure 1. Figure 1. Enabling VPN functionality.
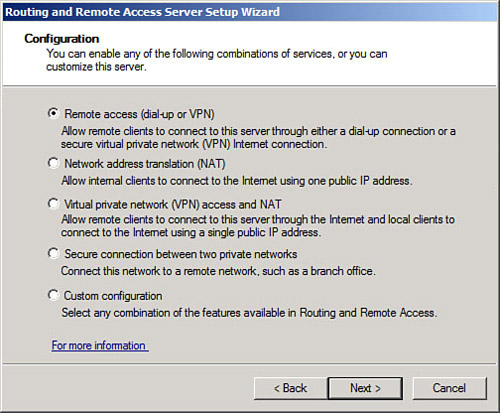
|
|
6. |
On |
|
7. |
On the VPN Connection page, shown in Figure 2, select which network card is connected to the network where VPN clients will be coming from. This might be the Internet, or it might be a secured perimeter network such as a DMZ. Click Next to continue. Figure 2. Specifying the network card for VPN clients.

|
|
8. |
On |
|
9. |
On the Managing Multiple Remote Access Servers page, shown in Figure 3, select whether to use RRAS to authenticate locally or to use a remote RADIUS server. Click Next to continue. Figure 3. Specifying RADIUS settings for the VPN server.
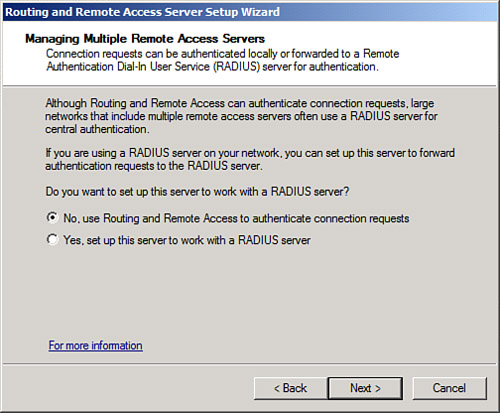
|
|
10. |
Review the wizard settings and click Finish when complete. |
|
11. |
Click |
|
12. |
Click Finish when the wizard is complete. |
The wizard will enable RRAS
on the server and allow for administration of the VPN settings and
client from the Routing and Remote Access dialog box, shown in Figure 4. Review the settings within this tool to familiarize yourself with how the system is configured.
Figure 4. Administering the server from the RRAS MMC tool.
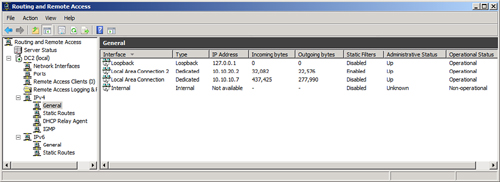
Modifying the RRAS Network Policy
After installing and
configuring RRAS, the NPS system will deny access by default to the RRAS
server for clients, unless the network policy generated is modified.
The network policy, which is labeled Connections to Microsoft Routing
and Remote Access server, can be found under the Network Policies node
of the Network Policy Server.
The policy must be set to Grant Access in the Access Permission section of the dialog box, as shown in Figure 5.
This dialog box can be invoked by right-clicking the policy and
choosing Properties. After enabling, the NPS system will allow client
connections.
Figure 5. Modifying the RRAS network policy on the NPS server.

Note
VPN clients can be
controlled and monitored using the NPS role just like the IPSec, 802.1X,
and DHCP clients can.
Встала перед мной задача: настроить раздачу интернетов в Windows Server 2008 R2, не привлекаю внешнего софта (лицензионные и ресурсные ограничения имели место быть). Таким образом, решено было использовать стандартную службу RRAS (Routing and Remote Access) в Windows 2008 R2. Саму суть настройки рассказывать не буду, но, далее — фикс небольшой проблемы, которая возникает при попытке использования PPPoE подключения.
Мой конфиг: машина с двумя сетевыми картами, одна из которых смотрит в локальную сеть, вторая — в интернеты.
Итак, служба настроена, NAT тоже вроде как настроен, необходимые порты проброшены, PPPoE интерфейс создан и подключен, а Интернета — нету. Погуглив, более-менее вразумительного ответа я не нашел, лишь намеки; впрочем, я убедился, что проблема не в моих руках, а с ней сталкиваются многие, пытающиеся настроить такую конфигурацию.
Первый путь, который я избрал — был путь наименьшего сопротивления: раз подключение есть, интерфейс создается, а интернета нету, то надо озадачить техподдержку провайдера. Наши переговоры длились довольно таки долго, но ни к чему не привели — провайдер убедил меня в том, что проблема таки у меня так как:
- На своем оборудовании они видят мою авторизацию
- В модели OSI PPPoE находиться ниже, чем TCP/IP
Вот второй пункт как раз и подтолкнул меня к решению проблемы. Раз подключение есть, а интернета нет — значит проблема в настройках TCP/IP, вероятнее всего в маршрутизации.
Подключившись при помощи мастера из Настроек сети (то есть создав подключение ручками, а не интерфейсом в RRAS), я посмотрел табличку маршрутизации и обнаружил, что там есть один маршрут, который не создается при использовании RRAS, а именно:
Dest: 0.0.0.0; Mask: 0.0.0.0; Gateway: мой_внешний_ip
Таким образом, для решения проблемы достаточно просто добавить постоянный маршрут в таблице маршрутизации коммандой route add 0.0.0.0 mask 0.0.0.0 внешний_ip (при условии, что внешний ip статический). Если IP динамический, то точно такой маршрут нужно добавить в оснастке RRAS, указав в качестве внешнего интерфейса PPPoE.
Забавная фишка, что все эти танцы с бубном актуальны лишь для Windows Server 2008, в 2003 все работает самостоятельно.
