Автор: Андрей Бирюков.
Специально для Академии Кодебай
Обратная разработка или реверсивный инжиниринг это исследование программного обеспечения (в том числе вредоносного), с целью изучения принципов его работы. Этой статьей мы начинаем цикл, посвященный основам реверсинга приложений под ОС WIndows. Повествование начнется с рассмотрения необходимых для исследования программного обеспечения инструментов, далее мы начнем погружаться в саму специфику обратной разработки, решая CrackMe – небольшие приложения, мы рассмотрим основы языка Ассемблер, а также посмотрим реверсинг приложений на .NET.
Конечно, в рамках четырех статей невозможно рассмотреть все аспекты обратной разработки, поэтому тем, кого заинтересует данная тема я предлагаю пройти обучение на нашем курсе “Реверсивный инжиниринг ПО под Windows”.
Зачем нужен реверсинг
Код практически любого приложения может содержать ошибки. Самый простой способ исправить эти ошибки, это найти в исходном коде проблемную команду или функцию и внести соответствующие исправления в код. Но что делать, когда по тем или иным причинам исходный код нам не доступен? Например, если у нас имеется только откомпилированный выполнимый файл – артефакт. Например, для выявления уязвимостей, недокументированных возможностей и т.д. В таком случае на и потребуется обратная разработка. Результатом обратной разработки является построение детального алгоритма работы программы, а также выявление уязвимостей и других интересующих исследователя аспектов работы программного обеспечения.
Как правило, обратная разработка применяется в тех случаях, когда на программное обеспечение отсутствует какая-либо документация и исходный код, и имеются только откомпилированные исполняемые файлы.
Конечно, реверсить программы можно не только с благими целями. Злоумышленники тоже могут искать уязвимости в коде, для того, чтобы затем осуществлять атаки с помощью эксплуатации этих уязвимостей. Но если рассматривать представителей “светлой” стороны, то реверсивный инжиниринг требуется программистам, работающим с низкоуровневыми языками программирования (например, разработчикам драйверов).
Также обратная разработка нужна тем, кто занимается поиском уязвимостей с целью улучшения защищенности программного обеспечения – багхантерам.
Не стоит забывать, что вредоносный код это тоже программное обеспечение и его тоже необходимо реверсить для выявления принципов заражения и для того, чтобы понять как от них можно защищиться. Этим задачами занимаются вирусные аналитики
А кроме того, читателю должно быть известно, что с 2025 года на объектах критической инфраструктуры не должно использоваться иностранное ПО, то есть в том числе и ОС Windows. В связи с этим есть острая необходимость по созданию аналогов различных решений под российские версии ОС Linux. И здесь технологии обратной разработки также очень востребованы, например для понимания работы различных промышленных протоколов, используемых в автоматизированных системах управления технологическими процессами.
Ну что ж, надеюсь мне удалось наглядно обосновать необходимость реверсивного инжиниринга для решения задач ИТ и ИБ, и теперь мы можем перейти к практической части, а именно к рассмотрению тех инструментов, которые необходимы исследователю.
Ассемблер и компиляторы
Прежде чем перейти непосредственно к рассмотрению самих инструментов добавлю небольшое пояснение. В рамках наших четырех статей нам потребуются не все представленные далее инструменты, однако тем, кто собирается глубже погрузиться в тему обратной разработки все данные решения (и не только они) будут необходимы.
Итак, откомпилированное приложение представляет собой машинных кодов, которые понимает процессор. Однако для того, чтобы программистам было удобнее понимать машинные инструкции разработали язык ассемблера, который позволяет использовать более удобные для человека мнемонические (символьные) обозначения команд. Язык ассемблера — язык программирования «низкого уровня». Также существуют языки высокого уровня, такие как Си или Python. Эти языки гораздо удобнее для программирования, так как не требуют для выполнения той или иной команды написания большого количества кода. Однако, для выполнения программы на языке высокого уровня необходимо сначала перевести на язык ассемблера, чтобы компьютер их понял и смог исполнить. Таким образом, для того, чтобы понимать, как работает программа, реверсеру необходимо знать язык ассемблера.
Для написания программ на языке ассемблера нам потребуются компиляторы. Совершенно очевидно, что для того, чтобы научиться реверсингу необходимо уметь программировать на языке ассемблера. Кроме того, зачастую при анализе приложений возникает необходимость написания собственного кода. Так при исследовании приложений на переполнение буфера нам необходимо “скормить” уязвимому приложению произвольный код, который затем оно должно выполнить. Поэтому навык программирования на ассемблере реверсеру необходим.
Наиболее распространенным и что немаловажно бесплатным компилятором для 32 и 64 битной архитектуры является FASM (Flat Assembler). Скачать его можно со страницы проекта: https://flatassembler.net/.
Загружаем архив с последней версией. Никакая установка не требуется, просто распаковываем архив и запускаем файл fasmw.exe. Для проверки корректности работы компилятора откроем в папке, куда был распакован FASM каталог Examples, далее Hello и файл hello.asm.
; example of simplified Windows programming using complex macro featuresinclude 'win32ax.inc' ; you can simply switch between win32ax, win32wx, win64ax and win64wx here.code start: invoke MessageBox,HWND_DESKTOP,"May I introduce myself?",invoke GetCommandLine,MB_YESNO .if eax = IDYES invoke MessageBox,HWND_DESKTOP,"Hi! I'm the example program!","Hello!",MB_OK .endif invoke ExitProcess,0.end start
Далее жмем Run и общаемся с диалоговыми окнами. Строго говоря, тот пример кода, который мы выполнили это не совсем чистый Ассемблер, здесь используются так называемые макросы – шаблоны для генерации кода. Один раз создав макрос, мы можем использовать его во многих местах в коде программы. Макросы существенно упрощают жизнь разработчикам, делая процесс программирования на ассемблере более приятным и простым, а код программы получается понятнее, более схожим с кодом на языках высокого уровня.
Однако, как мы увидим дальше, при реверсинге макросы не видны, поэтому представленный выше пример используется лишь для того, чтобы быстро и просто проверить корректность работы компилятора.
Помимо FASM существуют также другие компиляторы, такие как NASM, MASM и другие. Некоторые из них не поддерживают 64-битную архитектуру и давно не используются. На практике синтаксис написания кода может отличаться в зависимости используемого компилятора, однако при необходимости использование другого компилятора.
Отладчики и дизассемблеры
Основными инструментами реверс-инженера являются отладчик и дизассемблер. Разберемся чем эти инструменты отличаются друг от друга.
Отладчик запускает целевую программу в контролируемых условиях, которые позволяют программисту отслеживать ее текущие операции и отслеживать изменения в компьютерных ресурсах (чаще всего областях памяти, используемых целевой программой или операционной системой компьютера), которые могут указывать на неисправность кода.
Дизассемблер — это транслятор, преобразующий машинный код, объектный файл или библиотечные модули в текст программы на языке ассемблера.
Таким образом, отладчик является мощным инструментом, который позволяет отслеживать и исправлять ошибки на всех этапах разработки. Также он может быть использован для отладки программы на разных уровнях — от отдельных функций до целого приложения.
Дизассемблер транслирует машинный код обратно в инструкции ассемблера. Машинный код — это бинарное представление исполняемого кода, который использует процессор для выполнения задач внутри компьютера.
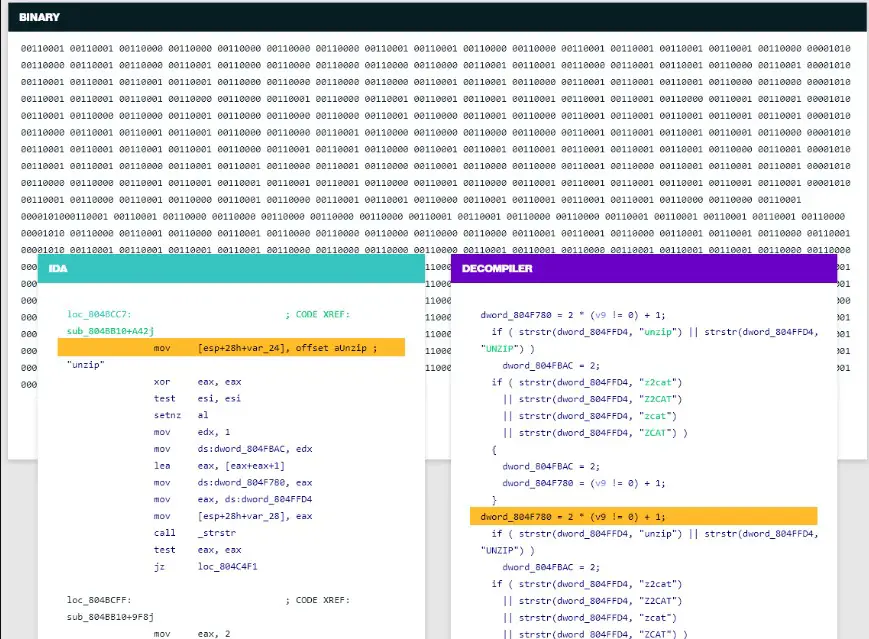
Самым известным дизассемблером является IDA – Interactive Disassembler. IDA Pro Disassembler — отличается исключительной гибкостью, наличием встроенного командного языка, поддерживает множество форматов исполняемых файлов для большого числа процессоров и операционных систем.
Для начала можно воспользоваться бесплатной редакцией IDA Free, которую можно загрузить по адресу https://hex-rays.com/ida-free/.
После установки запустим IDA Free, в появившемся окне выберем New и укажем наш файл hello.exe, который был получен в результате компиляции в FASM.
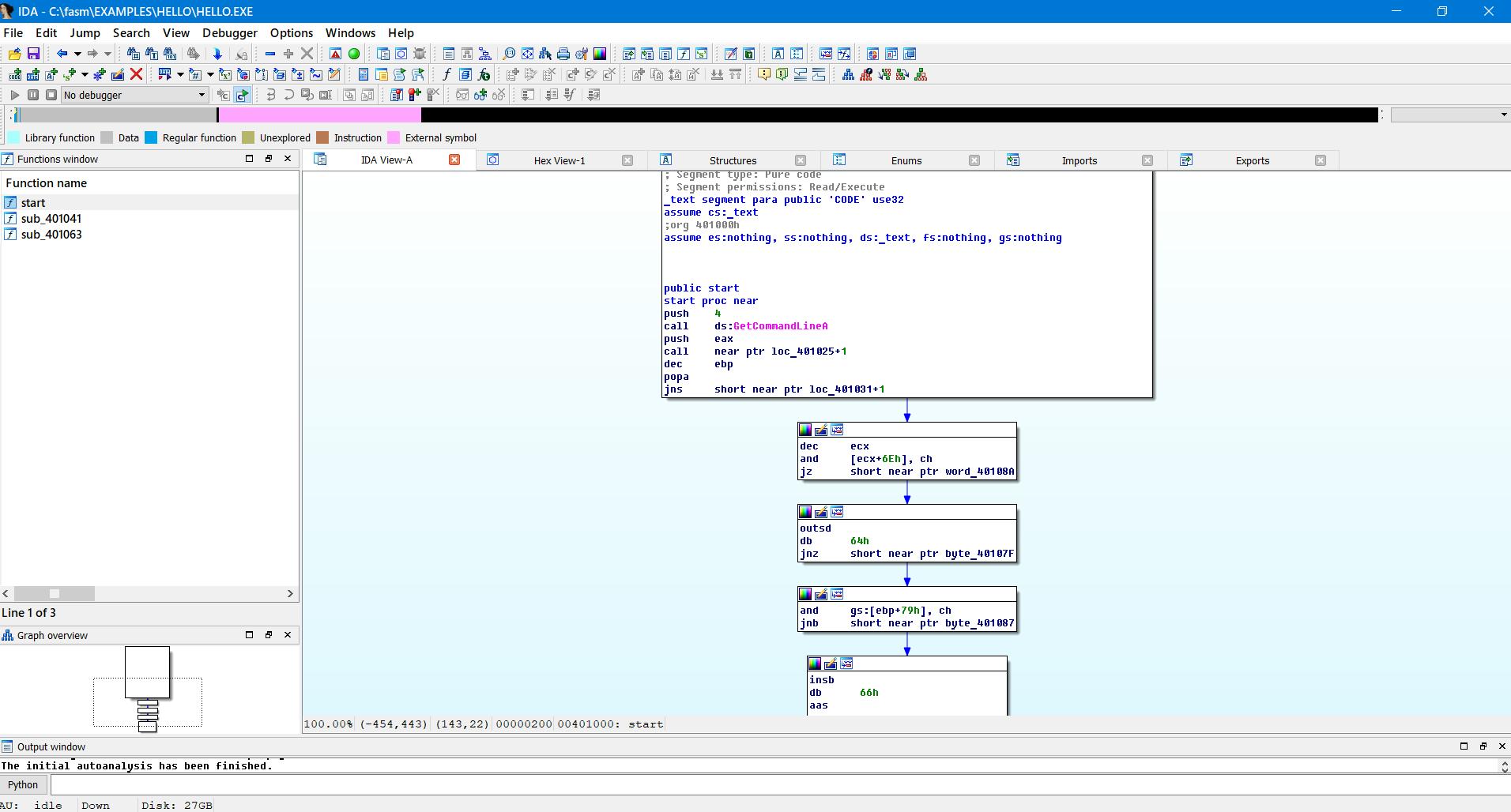
В результате мы получили дизассемлированный вид нашего выполняемого файла.
Теперь поговорим об отладчике. В принципы в IDA тоже есть свой отладчик, но я предлагаю использовать x64dbg в качестве основного средства отладки. Этот отладчик является также бесплатным и работает как в 32 битной, так и в 64 битной архитектуре. Загрузить его можно со страницы https://x64dbg.com/.
После установки отладчик становится доступным при нажатии правой кнопки мыши на любом выполнимом файле. Выберем наш выполнимый файл hello.exe и после нажатия правой кнопки мыши выберем x64dbg.
В открывшемся окне с кодом необходимо один раз нажать Выполнить . Далее мы увидим как код программы разместился в памяти.
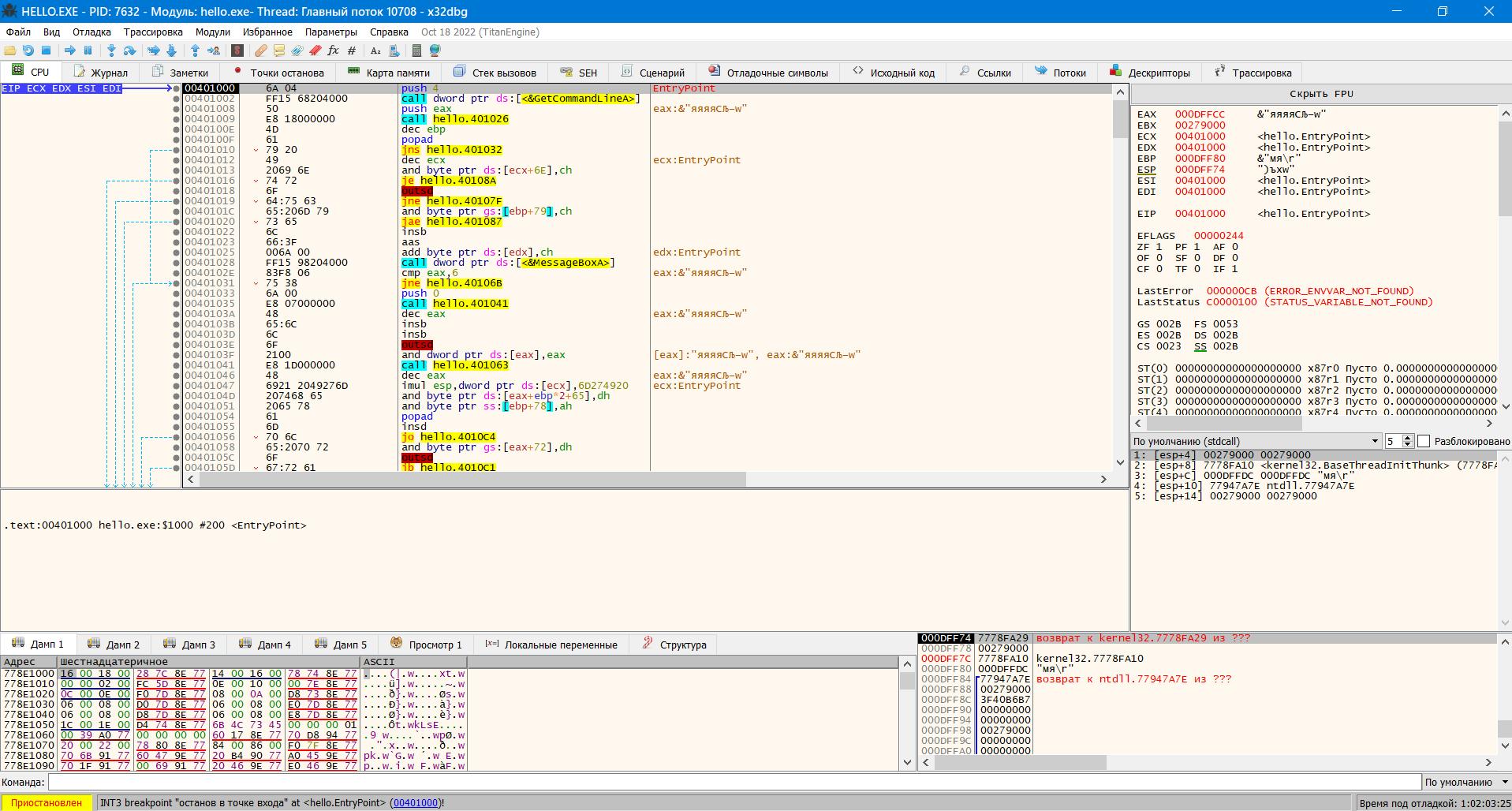
Пока нам этого достаточно для того, чтобы анализировать крякмиксы. Однако, для более серьезного реверсинга необходимы также еще некоторые средства.
Только виртуализация
Для решения крякмиксов можно использовать хостовую машину, так как они не представляют какой-либо угрозы. Однако для анализа различных подозрительных файлов, хакерских инструментов и вредоносов обязательно нужно использовать изолированную среду. Лучше всего использовать виртуальные машины, например Virtual Box или бесплатные редакции VMWare Workstation. При большом желании можно, конечно использовать контейнеры, но тогда необходимо позаботиться о сохранении данных.
В качестве рабочей ОС я обычно использую Windows 7. С одной стороны эта устаревшая ОС поддерживается большинством приложений, включая и вредоносные. С другой стороны, в ней нет “новейших механизмов защиты от Майкрософт” которые по факту только мешают отладке.
REMnux – швейцарский нож реверсера
Можно было бы еще довольно долго рассказывать о различных утилитах для анализа заголовков, энтропии, расшифровки обфусцированных файлов, а можно просто рекомендовать использовать готовый дистрибутив REMnux. Это дистрибутив ОС Linux на основе Ubuntu в котором уже установлено множество различных утилит для реверсинга. Да, приложения под Windows можно анализировать с помощью Linux.
Проще всего, загрузить готовую виртуальную машину в виде виртуального устройства (OVA) с сайта REMnux.org. При разборе крякми в следующих статьях мы будем использовать некоторые из утилит входящих в данный дистрибутив.
Заключение
Полагаю, мы подготовились к началу разбора крякмиксов. У нас есть основные инструменты для отладки, дизассемблирования и анализа артефактов. В четвертой статье, когда мы будем говорить про .NET, потребуются еще несколько средств специфичных для данной среды, но для классического реверсинга нам этого хватит.
В следующей статье мы разберем несколько crackme, двигаясь от простого к сложному, попутно рассмотрев основы программирования на ассемблере.
Have you ever felt a desire to take some mechanism apart to find out how it works? That desire is the leading force in reverse engineering. This skill is useful for analyzing product security, finding out the purpose of a suspicious .exe file without running it, recovering lost documentation, developing a new solution based on legacy software, etc.
Reverse engineering is critical in cybersecurity, software development, and legacy system modernization. By analyzing software at a low level, businesses can identify security vulnerabilities, ensure software compatibility, recover lost documentation, or even develop new solutions based on existing technologies.
However, performing reverse engineering efficiently requires deep expertise, specialized tools, and adherence to legal and ethical standards.
In this article, you’ll learn how to use reverse engineering to enhance system security, migrate your software, or optimize your app’s performance. We’ll explore key methodologies for reverse engineering Windows software and demonstrate them with a practical step-by-step example of analyzing a Windows application.
Contents:
- What is Windows reverse engineering?
- What do you need for Windows reverse engineering?
- How to analyze executables: disassembly and decompiling techniques
- How to reverse engineer a Windows app: A practical example
- How to reverse engineer a Windows driver
- How Apriorit can help
- Conclusion
What is Windows reverse engineering?
Reverse engineering Windows applications is a complex and highly specialized task that uncovers the internal structure of a piece of hardware or software.
Businesses usually turn to reverse engineers when they don’t have proper documentation of their own software or can’t access the source code of third-party software. Reverse engineers can take compiled code and dissect it to help complete the following tasks:
- Enhance security – Reverse engineering your Windows software can help you identify vulnerabilities and check if your software is prone to breaches or malicious reverse engineering. Additionally, reverse engineering malware like viruses, trojans, and ransomware is a good way to learn how it works and develop effective countermeasures.
- Ensure software compatibility – Reverse engineering allows you to analyze software dependencies, internal structures, and undocumented platform features to make sure your Windows application is compatible with new operating system versions or third-party integrations. By dissecting communication protocols and file formats, you can modernize legacy applications without full redevelopment.
- Maintain regulatory compliance – In finance, the public sector, the healthcare sector, and many other spheres, businesses are required to maintain a deep understanding of how their software operates to meet security and compliance requirements. Reverse engineering can help to uncover hidden security issues, validate security measures, and analyze encryption methods, all of which are critical for complying with laws, regulations, and standards like HIPAA, the GDPR, and PCI DSS.
- Protect intellectual property – Reverse engineering allows businesses to detect unauthorized modifications to their software and verify the integrity of proprietary code. This can help to prevent copyright infringement or find out if such infringement has occured.
- Extend software lifespans – Understanding the internal architecture of legacy applications can help you maintain, upgrade, or migrate software without full redevelopment. Reverse engineering helps you extract logic from undocumented systems, research file formats storing critical data (such as email databases or disk images), and recover lost functionality in order to continue business operations.
- Optimize performance – Reverse engineering provides deep insights into software execution and allows your team to identify performance bottlenecks. By analyzing binary code, your team can optimize resource use and improve system reliability without rewriting the entire application.
While reverse engineering can help your business tackle all these tasks, your team may face some challenges along the way.
First, you must pay attention to the legal boundaries of reverse engineering to make sure that you are not breaking any laws. Many end-user license agreements (EULAs) restrict reverse engineering, but laws such as the US Digital Millennium Copyright Act permit it for improving compatibility with other products. Legal requirements vary across jurisdictions, so your reverse engineering team must ensure compliance before initiating any reverse engineering project.
Second, Windows applications can be difficult to analyze. Reverse engineering Windows software requires extensive knowledge of Windows OS internals, including system calls, memory management, and APIs.
Additionally, software protection mechanisms like obfuscation, anti-debugging, and virtualization can make reverse engineering more difficult and time-consuming if a specialist doesn’t know how to bypass them.
In the next section, we explore the specific knowledge needed to perform reverse engineering tasks effectively and the tools that make this process possible. We also overview the most important techniques used for analyzing and modifying Windows applications at the binary level.
What do you need for Windows reverse engineering?
Imagine you’re examining a watch to determine whether it’s mechanical, quartz, or automatic. Understanding the field means knowing these watch types, recognizing that a quartz watch has a battery, and being familiar with a watch’s internal structure. Applying this knowledge requires the right tools (such as a screwdriver) to open the watch and inspect its components.
Similarly, reverse engineering a piece of software requires specialized knowledge and tools. Your team should not only have expertise in application structures, programming languages, and compilers but also know how to solve specific reverse engineering tasks using specific tools. This often demands practical experience with various tools, as well as a deep theoretical understanding of areas like malware analysis, network protocols, and file formats.
To illustrate the depth of knowledge required for reverse engineering, let’s look at some key tasks and the expertise they demand:
Table 1. Reverse engineering tasks and knowledge required
| Task | Required expertise | Business impact |
|---|---|---|
| Reverse engineering network applications | Advanced knowledge in inter-process communication, network protocols, packet analysis, and data exchange patterns | Uncovers vulnerabilities in communication channelsEnsures software adheres to industry-standard protocols |
| Decrypting cryptographic algorithms | Expertise in cryptography and algorithms such as RSA, AES, and hashing techniques | Ensures data securityIdentifies weaknesses in encrypted systems |
| Researching and analyzing file structures | Deep insight into file systems and understanding of how software interacts with stored data | Helps identify malwareUncovers the internal structure of files |
Special techniques can save a lot of time when reversing special types of software. For example, if your team deals with file interactions, making a test that writes unique type values to a file while logging the offsets and data size to the actual storage file may help them find common patterns in offsets. This will hint at the internal structures of these files.
But specialized knowledge and techniques are not enough. When starting the process of reverse engineering, software developers often use dedicated tools, such as a disassembler, to reveal the underlying algorithms and program logic embedded within the software. Disassembly allows your team to examine the assembly instructions of a compiled executable, offering insights into how the software functions at the lowest level. This foundational knowledge is essential for understanding the behavior of the software in greater detail.
In the next section, we explore why disassembling and decompiling are the key skills for reverse engineering.
How to analyze executables: disassembly and decompiling techniques
The first thing a reverse engineer usually does with a piece of software is reconstruct the code that has been compiled. This helps them better understand the program’s internals and identify potential vulnerabilities and behaviors.
There are many different executable file formats, operating systems, and compilers that give different outputs. This diversity of technologies requires reverse engineers to have expertise in various techniques and know when to use them depending on the type of software.
To understand decompiled code, a reverse engineer needs knowledge of assembly language, function calling conventions, how the call stack works, and the concept of stack frames.
Knowing the assembler output for different code samples may help your reversing team in uncovering the original functionality. Let’s consider some reverse engineering examples for the Windows x86 platform.
Let’s say we have the following code:
C++
int count = 0;
for (int i = 0; i < 10; ++i)
{
count++;
}
std::cout << count;If we compile this code to an executable file, we’ll see this in the disassembler:
ShellScript
004113DE loc_4113DE:
004113DE mov eax, [ebp-14h]
004113E1 add eax, 1
004113E4 mov [ebp-14h], eax
004113E7 loc_4113E7:
004113E7 cmp [ebp-14h], 0Ah
004113EB jge short loc_4113F8
004113ED mov eax, [ebp-8]
004113F0 add eax, 1
004113F3 mov [ebp-8], eax
004113F6 jmp short loc_4113DE
004113F8 loc_4113F8:
004113F8 mov ecx, ds:?cout@std
004113FE push eax
00411400 call ds:basic_ostream@operator<<(int)
00411404 xor eax, eax
00411406 retnAs we can see, the regular cycle has turned into assembly code with comparisons and jumps. Notice that the assembly code doesn’t use the regular assembly loop with the counter in the ecx register. In addition, local variables here are referred to as [ebp-14h] and [ebp-8], respectively.
Let’s see what happens if we compile this code using the release build:
ShellScript
00401000 main proc near
00401000 mov ecx, ds:?cout@std
00401006 push 0Ah
00401008 call ds:basic_ostream@operator<<(int)
0040100E xor eax, eax
00401010 retn
00401010 main endpThis compiled code doesn’t look anything like the assembly code. That’s because of how the code was optimized. Technically, the loop was removed, since it’s not doing anything valuable other than incrementing the count variable to 10. So the optimizer decided just to keep the final value of the count variable and place that value directly as an argument for the count output operator.
The compilers that we use nowadays are very good at optimizing code. That’s why when reverse engineering it’s better to understand the idea behind the code (the principles of the code) rather than to try getting the original code itself. If you understand the idea behind the code, you can write your own version that fits the original task.
In most cases, a reverse engineer needs to understand how compilers work to be able to analyze and reconstruct code written for any type of processor architecture. This is because disassemblers typically only show the assembly instructions, which can be difficult to understand and analyze directly.
However, advancements in tools like IDA, Ghidra, and Radare allow for decompilation into a pseudo-C representation. Pseudo-C code resembles C code, but it might not be compilable due to architecture-specific details or optimizations made by the compiler. However, it offers a much clearer understanding of the program’s logic compared to raw assembly instructions. This simplifies decompilation by providing a higher-level view of the original source code.
Consider the following code snippet written for Windows:
C
#include <windows.h>
#include <stdio.h>
struct MyDate
{
WORD wYear;
WORD wMonth;
WORD wDay;
};
__declspec(noinline) void CheckTheDate(MyDate & date)
{
if (date.wYear >= 2024 && date.wMonth == 1 && date.wDay == 1)
printf("It's a new year, let's celebrate");
}
int main()
{
SYSTEMTIME sysTime = {0};
GetSystemTime(&sysTime);
MyDate date = {sysTime.wYear, sysTime.wMonth, sysTime.wDay};
CheckTheDate(date);
return 0;
}Compiling this code in release mode and loading the executable into a decompiler like IDA results in pseudo-C code that partially resembles the original source. IDA will represent it like this:
C
int __fastcall main(int argc, const char **argv, const char **envp)
{
__int16 v4[4]; // [rsp+20h] [rbp-28h] BYREF
struct _SYSTEMTIME SystemTime; // [rsp+28h] [rbp-20h] BYREF
SystemTime = 0i64;
GetSystemTime(&SystemTime);
v4[0] = SystemTime.wYear;
v4[1] = SystemTime.wMonth;
v4[2] = SystemTime.wDay;
sub_140001070(v4);
return 0;
}The decompiler can recognize the _SYSTEMTIME structure defined in the Windows header file. However, for programmer-defined structures like MyDate, it might misinterpret the data as an array. In this case, IDA sees v4 in the main function as an integer array (__int16 v4) instead of the intended MyDate structure.
In order to fix this, IDA allows you to create user-defined structures. Let’s add the following definition:
C
struct MyDate
{
WORD year;
WORD month;
WORD day;
};After that, we will change the type of v4 from array of int to MyDate. The pseudo-code of main() will start looking like this:
C
int __fastcall main(int argc, const char **argv, const char **envp)
{
MyDate v4; // [rsp+20h] [rbp-28h] BYREF
struct _SYSTEMTIME SystemTime; // [rsp+28h] [rbp-20h] BYREF
SystemTime = 0i64;
GetSystemTime(&SystemTime);
v4.year = SystemTime.wYear;
v4.month = SystemTime.wMonth;
v4.day = SystemTime.wDay;
sub_140001070(&v4);
return 0;
}v4 is not an array anymore, so we can continue into sub_140001070.
C
__int64 __fastcall sub_140001070(_WORD *a1)
{
__int64 result; // rax
result = 2024i64;
if ( *a1 >= 0x7E8u && a1[1] == 1 && a1[2] == 1 )
return sub_140001010("It's a new year, let's celebrate");
return result;
}This demonstrates how decompiler output relies on the underlying assembly instructions. The decompiler analyzes instructions like cmp word ptr [rcx+2], 1. It also has no information about the type of date, so it decides that there’s some work being done with the WORD array.
But after we change the definition of the function from __int64 __fastcall sub_140001070(_WORD *a1) to __int64 __fastcall sub_140001070(MyDate *date), the code will start looking like this:
C
__int64 __fastcall sub_140001070(MyDate *date)
{
__int64 result; // rax
result = 2024i64;
if ( date->year >= 0x7E8u && date->month == 1 && date->day == 1 )
return sub_140001010("It's a new year, let's celebrate");
return result;
}By providing additional information like structure definitions, the reverse engineer guides the decompiler towards a more accurate representation of the initial source code.
Modern reverse engineering is less about working over the assembly code and more about reconstructing pseudo-C into real source code. Yet, to accurately reverse engineer software, your team still needs to understand how exactly the decompiler decides to generate pseudo-C from the specific assembly instructions and what these instructions could have been in the initial source code.
It will be very useful to know what assembly code you’ll get if you compile different operators, structures, and other language constructions. Understanding the resultant assembly code is a good way to start the C++ reverse engineering process, but we won’t get into the technical details here.
How to reverse engineer a Windows app: A practical example
Now, we’ll see an example of how to reverse engineer a piece of software. Let’s imagine you have a suspicious executable file. You need to find out what this program does and if it’s safe for users.
Considering the risks, it’s best not to run this executable directly on your main operating system. Instead, use a virtual machine, which provides an isolated environment that helps limit potential damage. Let’s start the application in our virtual machine.
As we can see, this executable file creates a Windows service named TestDriver. It has the kernel type, so we know it’s a driver. But where does it take the driver file from in order to run? We can use ProcessMonitor from Sysinternals Suite to find out. When we open ProcessMonitor, we can set up filters to show us only the file activity from the process we’re interested in. Its activity log looks like this:
The driver file is created by the process that we’re reversing, and this process puts this file in the user’s temp directory. There’s no need to look for the file in the temp folder, since we see that the process deletes it right after use.
So what does the process do with this file? If it unpacks it, we may try to find it in the process’s resource section, since this is a common place to store such data. Let’s look there.
We’ll use another tool — Resource Hacker — to examine the resources. Let’s run it:
Bingo! As we can see from the found resource content, this is probably a Windows executable file, since it starts with an MZ signature and has the string “This program cannot be run in DOS mode.” Let’s check if it’s our driver file. For that purpose, we extract the resource using Resource Hacker, store it as a file, and open it in the disassembler.
INIT: 0001403E ; NTSTATUS _stdcall DriverEntry(PDRIVER_OBJECT DriverObject, PUNICODE_STRING RegistryPath)
INIT: 0001403E public DriverEntry
INIT: 0001403E DriverEntry proc near
INIT: 0001403E DriverObject = dword ptr 8
INIT: 0001403E RegistryPath = dword ptr 0Ch
INIT: 0001403E
INIT: 0001403E mov edi, edi
INIT: 00014040 push ebp
INIT: 00014041 mov ebp, esp
INIT: 00014043 call sub_14005
INIT: 00014048 pop ebp
INIT: 00014049 jap sub_110F0
INIT: 00014049 DriverEntry endp As we know, DriverEntry is the entry point for kernel-mode drivers in Windows systems, and IDA identified that the file we extracted from the resources section is indeed an executable and has the DriverEntry function. We can continue our research, as it looks like we’ve found the driver used by the application.
To begin reverse engineering the driver, we examine functions that are called from DriverEntry one by one. If we go to sub_14005, we find nothing interesting, since it just sets up the security cookie variable, so we continue to sub_110F0 and find this code:
0001102C push offset SourceString; "\\DosDevices\\C:\\hello.txt"
00011031 lea ecx, [ebp+DestinationString]
00011034 push есх ; DestinationString
00011035 call ds:RtlInitUnicodeString
0001103B mov [ebp+ObjectAttributes.Length], 18h
06011042 mov [ebp+ObjectAttributes.RootDirectory], 0
00011049 mov [ebp+ObjectAttributes.Attributes], 240h
6601185S lea edx, [ebp+DestinationString]
00911053 mov [ebp+ObjectAttributes.ObjectNane], edx
00011056 mov [ebp+ObjectAttributes.SecurityDescriptor], 0
6601185D mov [ebp+ObjectAttributes.SecurityQualityOfService], 0 0001109C push eax ; FileHandle
0001109D call ds:ZwCreateFile000110B4 push offset aHelloFromDrive ; "Hello from driver\r\n"
000110B9 push 1Eh ; int
000110BB lea ecx, [ebp+Buffer]
000110BE push ecx ; char *
000110BF call sub_1115000011120 call ds:ZwWriteFile
80011126 mov [ebp+var_2C], eax
90011129 mov ecx, [ebp+Handle]
8001112C push ecx ; Handle
0001112D call ds:ZwCloseSome lines are omitted here for the sake of simplicity, but after the ZwClose call, the driver code just exits without registering any callbacks. This means it doesn’t have any logic besides what we see in the DriverEntry function.
In the first code snippet, a unicode string is created that points to the path C:\hello.txt. After that, the OBJECT_ATTRIBUTES structure is filled with regular values. We know that this structure is often needed when calling functions like ZwCreateFile.
In the second listing, we see that ZwCreateFile is indeed called, which makes us pretty sure that the driver creates the file — and we know where this file is located after it’s created.
From the third and fourth listings, we can see that the driver takes the unicode string and writes it to the buffer (this happens in the sub_11150 function) and that the buffer is written to the file using the ZwWriteFile function. At the end, the driver closes the file using the ZwClose API.
Let’s summarize. We found out that the original program extracts the driver file from its resources, puts it in the temp folder of the current user, creates the Windows service for this driver, and runs it. After that, the program stops and deletes the service and the original driver file from the temp directory.
From this behavior and from analyzing the disassembly, it appears that the driver doesn’t do anything except create a file on the C drive named hello.txt and write the string “Hello from driver”.
Now we need to check if we’re correct. Let’s run the program and check the C drive:
Wonderful! We’ve reverse engineered this simple computer program, and now we know that it’s safe to use.
As you can see, to successfully reverse engineer Windows software, your team needs to know where to look and also have experience with various tools. In the next section, we explore how our experienced reverse engineers can help you dissect your own software for your own business purposes.
How Apriorit can help
At Apriorit, we bring over 20 years of experience in reverse engineering various types of software, including Windows applications. Our team of reverse engineers can help you uncover vulnerabilities, optimize your legacy Windows systems, restore documentation, get access to lost source code, and give you a roadmap to making your app compatible with modern operating system versions. We provide a comprehensive range of reverse engineering-related services that include:
- Static and dynamic code analysis. We can disassemble and decompile Windows executable files (EXE, DLL) to analyze assembly code or reconstructed high-level code. This helps to uncover hidden algorithms, program logic, and potential vulnerabilities, providing you with a detailed understanding of how software works.
- Malware reverse engineering. If you suspect your software has been compromised, our reverse engineers can help you identify malicious code, trace the origins of the attack, and dissect the malware to recommend an effective strategy for protecting your software in the future.
- Vulnerability assessment. Our team specializes in identifying and analyzing security vulnerabilities within Windows applications. By reverse engineering your software, we can uncover potential exploits, malware entry points, and weaknesses. As a result, you’ll get a report with recommendations for eliminating these vulnerabilities.
- Software debugging and patching. If you need to modify or repair a Windows application, our experts can debug compiled code and implement necessary patches. We can fix bugs, resolve incompatibilities, and enhance functionality without requiring access to the original source code.
- Anti-reverse engineering analysis. We can help you protect your application from malicious reverse engineering. Our team will assess whether your code uses appropriate anti-reversing mechanisms like encryption and obfuscation. If it doesn’t, we can implement them.
- Legacy system integration. If you are dealing with legacy systems, we can reverse engineer outdated Windows applications to ensure compatibility with modern platforms, new operating system versions, and third-party integrations.
If you don’t know where to start, our experts can help you define your goals and choose relevant approaches. We’ll also give you a detailed breakdown of the timeline, costs, and resources required for reverse engineering.
Conclusion
Reverse engineering Windows software requires solid technical background and reverse programming experience. In order to perform reverse engineering, your team needs to combine skills in disassembling, network monitoring, debugging, API integration, programming in several languages, working with compilers, and more.
Each of these activities requires specific tools, so your team needs to know when and how to use them to get the optimal results. Reverse engineers also have to be very careful when reversing software in order not to break copyright laws or harm your system. Gaining this kind of expertise in your in-house team can take years, which is why outsourcing reverse engineering tasks can save you much time and many resources.
At Apriorit, we have an experienced team of reverse engineers. Whether you’re looking to improve your program’s security, ensure compatibility, or simply analyze your code structure, our reversing team is prepared to meet the challenge.
Время на прочтение4 мин
Количество просмотров1.7K
Некоторое время назад я написал статью, посвященную использованию дистрибутива Remnux для задач реверс инжиниринга. В этой статье мы посмотрим еще несколько инструментов, которые входят в состав данного дистрибутива.
Для того, чтобы затруднить анализ вредоносных файлов злоумышленники часто используют различные алгоритмы шифрования. При этом могут использовать как достаточно сложные (промышленные) алгоритмы шифрования, так и простые побитовые операции, такие как циклические сдвиги ROL/ROR и XOR по однобайтовому ключу. Вскрыть сложное шифрование с помощью инструментов автоматизации вряд ли возможно, а вот попробовать подобрать ключ для однобайтовой операции вполне возможно.
И в этом нам поможет REMnux. В состав дистрибутива входит утилита XORSearch. Эта программа предназначена для поиска заданной строки в двоичном файле с кодировкой XOR, ROL, ROT или SHIFT. Двоичный файл с кодировкой XOR — это файл, в котором некоторые (или все) байты были преобразованы в XOR с постоянным значением (ключом). Файл, закодированный ROL (или ROR), имеет свои байты, повернутые на определенное количество бит (ключ).
В файле, закодированном ROT, буквенные символы (A-Z и a-z) повернуты на определенное количество позиций.

Файл, закодированный ROL, имеет свои байты, сдвинутые влево на определенное количество битов (ключ): все биты первого байта сдвигаются влево.
XOR и кодировка ROL/ROR используется разработчиками вредоносных программ как для сокрытия всего кода, так и для запутывания анализа отдельных строк, таких как URL-адреса. Представим ситуацию, когда нам известны несколько URL, к которым обращается анализируемый вредонос. Допустим, мы перехватили запросы к этим ресурсам с помощью Wireshark.
XORSearch
Если эти URL неизменны, то можно предположить, что в коде вредоноса жестко зашиты строки с этими URL. С помощью XORSearch мы можем попробовать подобрать ключ шифрования, указав ему искать заданную текстовую строку.
В процессе перебора утилита XORSearch будет подставлять все байты для операции XOR (от 0 до 255), ROL (от 1 до 7), ROT (от 1 до 25) и SHIFT (от 1 до 7) при поиске. Также она проверит добавление констант к ASCII кодам искомых символов (операция ADD).
Однако, XORSearch выполняет атаку грубой силы не только с использованием 8-битных ключей и ключей меньшего размера. Атака перебора с использованием 32-битного ключа заняла бы слишком много времени. Параметр -k предписывает XORSearch выполнить 32-битную атаку по словарю вместо 8-битной атаки грубой силой. Словарь извлекается из самого файла: предполагается, что 32-разрядный ключ находится внутри файла в виде последовательности из 4 последовательных байт (пробуются как MSB, так и LSB). Ключ 0x00000000 исключен.
Если строка поиска найдена, XORSearch будет печатать ее до тех пор, пока не встретится 0 (нулевой байт) или пока не будут напечатаны 50 символов, которые всегда будут первыми. 50 — это значение по умолчанию, его можно изменить с помощью опции -l. Непечатаемые символы заменяются точкой.
В качестве примера мы продолжим мучать артефакт вредоноса SpyEye и поищем строку, содержащую cmd.

Для найденных значений XORSearch указал нам алгоритм, ключ и собственно найденную строку. При этом, для результатов, представленных на рисунке, часть строк будет ложными срабатываниями и найденный ключ тоже будет неправильным. Но для дальнейшего анализа уже надо прибегать к помощи отладчика.
Кстати, эту утилиту можно использовать не только для анализа выполнимых файлов, но к примеру, для анализа дампов сетевого трафика.
Bbcrack
Еще одна интересная утилита для перебора из состава REMnux это bbcrack. Она использует новый алгоритм перебора, основанный на шаблонах, представляющих интерес для обфускации типичных вредоносных программ, таких как XOR, ROL, ADD и различные комбинации, чтобы угадать, какие алгоритмы / ключи были использованы.
Здесь мы уже не ищем какие-либо текстовые строки в зашифрованном виде. Вместо этого утилита просто перебирает все однобайтовые ключи для определенного артефакта и в случае, если при расшифровке получается что-то похожее на выполнимый код, сохраняет его в выполнимом файле. Для того, чтобы определить, является ли полученный файл выполнимым, утилита использует скоринговую систему. Найденные слова больше определенной длины и их последовательности набирают определенное количество баллов.

В именах получившихся файлов также отражается алгоритм шифрования и ключ. Дальнейший анализ здесь также необходимо проводить с помощью других инструментов.
Bbharvest
Продолжим тему переборщиков из состава Remnux. Мы можем столкнуться с ситуацией, когда для обфускации файла используется несколько различных ключей или алгоритмов. В таком случае нам может помочь утилита BBharvest. Она извлекает все интересующие шаблоны, обнаруженные при применении типичных преобразований обфускации вредоносных программ, таких как XOR, ROL и различные комбинации, пробуя все возможные ключи. Это особенно полезно, когда в одном файле используется несколько ключей или несколько преобразований.
Перед началом анализа нас честно предупреждают о возможном большом количестве ложных срабатываний.

Анализ файла с помощью подобных механизмов перебора занимает значительное время, однако дает довольно интересный результат. Полученный отчет показывает какие интересные слова или фразы удалось найти.
При необходимости предложенные ключи расшифровки уже можно использовать в собственных скриптах и дополнительных инструментах для анализа файлов по другим критериям.

Помимо приведенных выше интересных фраз, утилита BBharvest по окончании анализа предлагает нам несколько вариантов распакованных файлов, где в качестве ключа указаны соответствующие алгоритмы и байты.

Заключение
Конечно, представленные в статье инструменты из состава Remnux не позволяют со 100-процентной вероятностью сказать, с помощью какого алгоритма и ключа зашифрован тот или иной файл. Но они предлагают свои вариант расшифровки, тем самым существенно облегчая жизнь вирусным аналитикам, так как если файл зашифрован слабым алгоритмом, то вполне возможно данные средства смогут подобрать нужный ключ для расшифровки.
В статье использовались материалы книги “Реверсивный инжиниринг приложений под Windows” Бирюков А. А., ДМК Пресс.
Больше практических навыков по обеспечению информационной безопасности вы можете получить в рамках практических онлайн-курсов от экспертов отрасли.
ReVens: Reverse Engineering Toolkit AIO

ReVens is a Windows-based Reverse Engineering Toolkit «All-In-One», Built for Security (Malware analysis, Penetration testing) & Educational purposes only. -V2 Under development-
Note
I made ReVens AIO software to share personal experience in RE since 2008.
RE tools are priceless, especially the legacy ones. They deserve a nice place where they can live in peace.
Watch online preview.
🔧 Features
- Cross-platform & Modern UI software launcher «Blackhat style»
- 100% clean: All detections are false positives, No malware injected
- 90% portable (Resolved/Included dependencies)
- Original assets (e.g. BRD — Teleport Pro.mx, CORE — Power ISO.xm)
- Packages Auto-updater (JSON based source file)
- Boilerplate of
Electron.jsBun + React.js
💡 Notices
Important
Respecting the rights of software developers is paramount. Engaging in activities such as bypassing software protections or reverse engineering software without explicit permission is not only generally illegal, but also unethical. It’s essential to utilize software in the manner intended by its creators and in compliance with the stipulated terms of service or license agreement.
- Reverse Engineering tools are denied by Antivirus (Due to binary patching algorithms, debugging …etc).
- You should make an Antivirus exception to avoid detection, or use a secured virtual machine.
- ReVens Packages ARE
NOTautomatically downloaded from GitHub. - Many of the included tools are outdated and provided solely for legacy purposes!
- Packages includes basic docs & tutorials about RE.
- Packages primary architecture is x64, but other architectures (x86, ARM) can also be supported.
- -Use it on your own responsibility-
🔧 Requirements
To run ReVens, Windows 10/11 (x64) is required.
🔧 Download
- Download ReVens GUI from: Releases.
- Download packages manually (~8Go) from:
| Part 1 | Part 2 | Part 3 | Part 4 | Part 5 | Part 6 | Part 7 |
|---|---|---|---|---|---|---|
| Analysing | Assembling | Bypassing | Calculating | Comparing | Converting | Debugging |
| Part 8 | Part 9 | Part 10 | Part 11 | Part 12 | Part 13 |
|---|---|---|---|---|---|
| Decoding | Decompiling | Dependencies | Disassembling | Documentation | Unpacking |
| Part 14 | Part 15 | Part 16 | Part 17 | Part 18 | Part 19 | Part 20 | Part 21 | Part 22 |
|---|---|---|---|---|---|---|---|---|
| Editing | Encoding | Extracting | Hexing | Mobile | Packing | Patching | Programming | Testing |
Downloads should be extracted into ReVens /bin folder.
🔧 Screenshot
This is how it looks, Made with {heart} using Electron.js Bun + React.js.
The App background is the WebView DevTools itself.
🔧 Install, Run & Build
To build ReVens:
Electron.js ^29.4.0 (Node 20.9.0)Bun ^1.2.0- MinGW-w64
ReVens command-line:
bash init.sh bash dev.sh bash run.sh bash build.sh
🔧 TODO
- Upload legacy packages (.iso) on GitHub.
- Use Rust WebView & Bun instead of Electron.js (Performance).
- Migrate to TypeScript.
- Add AI-powered Reverse Engineering Agent.
- Add Browser-level Reverse Engineering Resources (WASM).
- Add Search feature to find tools by name. (By @MOAHSA).
🔧 Packages
ReVens packages includes:
⚡ Analyzing
Analyse binary executable files (EXE, DLL, OCX, SYS…).
Binary
Analyse binary.
- FileAlyzer — Understand files by analyzing their structure. (⭐)
- Capa (CLI) — Identify capabilities in executables. (⭐)
- Alternate DLL Analyzer — Display function names in DLLs.
- ExeInfo — Universal binary analyzer.
- Yara — Malware pattern matching tool.
- Spyre — Simple YARA-based scanner.
- PE-bear — PE reversing tool.
- ClamAV — Open-source antivirus engine.
- Malzilla — Detect malicious scripts.
- Manalyze — Another malware analyzer.
- Sysinspector — Rootkits scanner.
- Windows Kernel Explorer — Another rootkits scanner.
Compilation
Analyse PE compilation.
- Detect It Easy (DiE) — File type identifier. (⭐)
- Nauz File Detector — Detects compiler tools.
- Language 2000 — Comprehensive compiler detector.
- PE Detective — Identifies PE files.
- Signature Explorer — Manage advanced signatures.
Bytecode (p-code)
Object code converted by interpreter into binary machine code to be read by CPU.
- Bytecode Viewer — View, decompile Java/Android bytecode & more.
Packaging
Analyse PE packaging / protection.
- Exeinfo PE — Detects packers and compressors. (⭐)
- PEiD — Identifies packed executables. (⭐)
- ARiD — Identifies archive formats.
- UPX-Analyser — Analyzes UPX-packed files.
System
Analyse system (API, Process, Memory, Network, File).
- HijackThis — Malware analyser. (⭐)
- Process Monitor — Advansed monitoring tool for Windows. (⭐)
- API Monitor — Monitor Windows API calls. (⭐)
- Fiddler — Web debugging proxy. (⭐)
- SearchMyFiles — Advansed files finder.
- RegDLLView — Display the list of all registered DLL/OCX/EXE.
- WinObj — Windows object manager.
- WinID — Window information tool.
- HeapMemView — Inspect heap memory.
- CPU Stress — CPU stress testing tool.
- DeviceIOView — Monitor device I/O.
- Autoruns — Manage startup programs.
- Wireshark — Network packet analyzer.
- DLL Function Viewer — View DLL functions.
- Dependency Walker — 32-bit/64-bit Windows module scanner.
- Exif Data View — Exif data Viewer.
- SQLite Tools — SQLite database tools.
- SQLite Browser — SQLite database browser.
- Process Explorer — Detailed process viewer.
- Process Hacker — Advanced process manager.
- Zero Dump — Create memory dumps.
- GDIView — Inspect GDI handles.
- grepWin — Search tool for Windows.
- PE Network Manager — Network Manager.
- NetworkMiner — Network forensics tool.
- SmartSniff — TCP/IP packets monitoring.
- TCPView — TCP/UDP viewer.
- Aircrack-ng — WiFi network security.
- SniffPass — Network passwords monitoring.
- WhoIs This Domain — Domain registration lookup utility.
- WhoIs Connected Sniffer — Network packets discovery tool.
- DNS Lookup View — DNS tracing tool.
⚡ Calculating
Mathematical & reverse calculating.
- Alternate Math Solver — Mathematical helper.
- Reverser Calculator — Calculator for reverse engineering.
- Hex-Dec — Hexadecimal to Decimal converter.
- JMP Calculator — Calculates JMP instructions.
- XOpcodeCalc — Opcode calculator tool.
- Jump to Hex — Jump instruction to hexadecimal.
- Hash Calculator — Calculates cryptographic hashes.
- Base Calculator — Calculates in different bases.
- Base Converter — Converts between bases.
⚡ Converting
Convert binary files.
- BAT to EXE
- PS1 to EXE
- VBS to EXE
- JAR to EXE
- DLL to EXE
- EXE to DLL
- PNG to ICO
- Audio Video to EXE
- RapidEXE (PHP — EXE) (CLI)
- RegConvert (REG — EXE)
- vbstoexe (CLI)
⚡ Decompiling
Revert the process of compilation. Transforming binary program file into a structured higher-level language.
- BinaryNinja — Advanced binary analysis platform. (⭐)
- .NET Reflector — .NET assembly browser and decompiler. (⭐)
- Dis# Net Decompiler — .NET decompiler for C#. (⭐)
- ILSpy — Open-source .NET assembly browser.
- dotPeek — .NET decompiler and assembly browser.
- Java Decompiler — Decompile Java class files.
- JByteMod — Java bytecode editor and decompiler.
- VB Decompiler — Decompile Visual Basic executables.
- DJ Java Decompiler — Java decompiler and disassembler.
- Exe2Aut — AutoIt3 decompiler.
- FFDec — Flash Decompiler.
⚡ Disassembling
Transforming machine code into a human readable mnemonic representation (Assembly language).
- Ghidra — Open-source software reverse engineering suite. (⭐)
- IDA — Interactive Disassembler for binary analysis. (⭐)
- RadASM — Rapid Application Development IDE. (⭐)
- Capstone (CLI) — Lightweight multi-architecture disassembly framework.
- Delphi Disassembler — Disassembler for Delphi executables.
- bddisasm (CLI) — Binary Ninja’s disassembly library.
- Disasm — Generic disassembler for various architectures.
- Refractor — .NET decompiler and assembly browser.
- Win32Dasm — Windows 32-bit disassembler.
⚡ Debugging
View and change the running state of a program. (Disassembling, Decompiling, Hexing).
- x64dbg — Graphical debugger for x86 and x86-64 executables. (⭐)
- Immunity Debugger — Powerful and flexible debugger for Windows. (⭐)
- OllyDbg — Dynamic, 32-bit assembler level debugger for Windows. (⭐)
- dnSpy — .NET assembly editor, decompiler, and debugger.
- Cutter — Free and open-source reverse engineering platform.
- Radare2 (CLI) — A portable and multi-architecture reverse engineering framework.
- RenderDoc — Stand-alone graphics debugger.
⚡ Hexing
Edit binary hexadecimal values.
- ImHex — A fast and powerful hex editor. (⭐)
- Hiew — A hex viewer and editor for Windows. (⭐)
- HEX Editor — A tool for viewing and editing hexadecimal files.
⚡ Rebuilding
Rebuild PE import table (Imports Reconstructor).
- Scylla — A powerful and advanced x86/x86-64 executable unpacker. (⭐)
- LordPE — Another PE editor including imports reconstructing. (⭐)
- DLL Packager — A tool for bundling DLLs with executables.
- ImpREC — Import reconstructor for reconstructing imports in PE files.
⚡ Decoding
Decode hash.
- Ophcrack — Windows password cracker based on rainbow tables. (⭐)
- CyberChef — A web app for analyzing and decoding data. (⭐)
- Hashcat — Advanced password recovery.
- Armadillo KeyTool — Tool for working with Armadillo software protection.
- Keygener Assistant — Assists in generating keys for software.
- SND Reverse Tool — Reverse engineering tool for Windows binaries.
- Hash Identifier — Identifies the type of hash used in a string.
- RSA-Tool 2 — Tool for generating and analyzing RSA keys.
- RSATool — Generate, convert and analyze RSA keys.
- RSABox — Toolkit for working with RSA encryption.
- MD5 Toolbox — Toolbox for working with MD5 hashes.
⚡ Comparing
Binary compare.
- WinMerge — Open-source tool for visual file comparison and merging. (⭐)
- REPT file compare — Tool for comparing binary files. (⭐)
- File CompareR — Utility for comparing files and directories.
- Table Text Compare — Simple CSV/Tab files compare.
- ReloX — Tool for comparing and analyzing binary files.
- SideBySide — Utility for side-by-side file comparison.
- SignMan — Utility for managing digital signatures.
⚡ Editing
Binary edit (EXE, RES, DLL).
- Resource Hacker — Resource editor for Windows executables. (⭐)
- PPEE — Powerful PE file viewer and editor.
- PE Lab — Interactive PE file (executable) analysis tool.
- Exiftool — Meta data editor.
- ReClassEx — Structure class reverser.
- ReClass.NET — .Net structure class reverser.
- XPEViewer — Executable file viewer and editor.
- XELFViewer — Viewer for ELF (Executable and Linkable Format) files.
- Robber — DLL hijacker.
- Xenos — DLL injector.
- DLL Injector Slait — Tool for injecting DLLs into processes.
- DLL Addr&Func Converter — Converts DLL addresses to function names.
- DLL Injector — Tool for injecting DLLs into processes.
- DLL Loader — Utility for loading DLL files into processes.
- DLL Rebaser — Utility for rebasing DLLs.
- ResEdit — Resource editor for Windows programs.
- CFF Explorer — PE editor, hex editor, and more for Windows files.
- Resource Builder — Resource file editor and compiler.
- Splash Injector — Tool for injecting splash screens into programs.
- Far Manager — Text-based file and archive manager for Windows.
- KDiff3 — File and directory diff and merge tool.
- IID King — Interface identifier lookup tool.
- Cheat Engine — Memory scanner/debugger for games and applications.
- EasyHook — Windows API Hooking.
- Notepad++ — Free source code editor and Notepad replacement.
- Codejock Skin Builder — Tool for building custom UI skins.
- Codejock Resource Editor — Resource editor for Codejock software.
- Codejock MarkupPad — Editor for creating Codejock markup files.
- Codejock Command Bars Designer — Designer tool for command bars.
- Inno Setup — Installer for Windows programs.
- Inno Script Studio — Inno Setup script manager GUI.
- DMcsvEditor — Simple CSV/Tab file editor.
- XMLTreeEdit — Simple XML file editor.
⚡ Extracting
Binary extracting (EXE, RES, DLL).
- UniExtract2 — Universal extractor for various archive formats. (⭐)
- DLL Export Viewer — View exported functions of a DLL file.
- Bintext — Fast and powerful text extractor.
- RegFileExport — Extract registry entries to a .reg file.
- RegScanner — Registry scanner.
- ResourcesExtract — Extract resources from executable files.
- DotNetResExtract — Extract .NET assembly resources.
- RegFromApp — Extracts registry entries created by an application.
- RegRipper — Another registry extractor.
- Inno Extractor — Tool for extracting Inno Setup installers.
- Innoextract (CLI) — Command-line Inno Setup unpacker.
- Innounp (CLI) — Inno Setup unpacker, a command-line version.
- MSI Unpacker — Extract files from MSI installers.
- Fearless MSI Unpacker — Tool for unpacking MSI installers.
- LessMSI (CLI) — Command-line tool to extract data from MSI files.
- Mmextract (CLI) — Command-line MSI and CAB extractor.
- ExeDumper — Utility to dump executable files.
- Table Extractor — Extract tables from executables or libraries.
- UEFITool — UEFI firmware image viewer and editor.
- Firmware Tables View — Firmware tables (ACPI, SMBIOS) viewer.
- ChromePass — Google chrome password recovery tool.
- PasswordFox — Mozilla firefox password recovery tool.
- WebBrowserPassView — Web password recovery tool.
- Password Scanner — Windows password recovery tool.
- Product Key Scanner — Windows product key Scanner.
- ProduKey — Another Windows product key Scanner.
Games
- Dragon UnPACKer — Tool for opening and extracting game resource files.
- Unity Assets Bundle Extractor — Utility for extracting Unity assets.
- Ninja Ripper — Tool for extracting 3D models from games.
- 3D Ripper DX — Capture 3D models from DirectX 9 games.
- QuickBMS — File extraction and reimporting script engine.
- Unity Asset Editor — Tool for modifying Unity game assets.
- DevX Unity Unpacker — Utility for unpacking Unity game files.
- Unity Studio — Viewer and editor for Unity assets and bundles.
- UnityEx — Utility for extracting assets from Unity games.
- uTinyRipper — Unity asset extractor and exporter.
⚡ Unpacking
Unpack & remove binary protection (EXE, DLL).
- XVolkolak — Unpacker emulator.
- .NET Reactor Slayer — Deobfuscator and unpacker for .NET Reactor.
- ConfuserEx Unpacker (CLI) — Confuserex unpacker.
- ILProtector Unpacker — ILProtector unpacker.
- de4dot — .NET deobfuscator and unpacker.
- RL!deUPX — UPX unpacker.
- RL!deASPack — ASPack unpacker.
- RL!dePacker — Generic unpacker.
- GUnPacker — Universal unpacker.
- ASPack Unpacker — Another ASPack unpacker.
- IsXunpack — InstallShield installer extractor.
- Unpacker ExeCryptor — ExeCryptor unpacker.
- Universal Unprotector — Another universal unpacker.
⚡ Patching
Patcher
Generate patching program using binary compare.
- dUP 2 — Utility for creating patches for software. (⭐)
- AT4RE Patcher — Patch creator for software modification.
- CodeFusion — Patch creator and modifier for software.
- uPPP — Patch creation tool for software modification.
- Apatch — Tool for creating patches for software.
- Inno Setup XDELTA Patch Maker — Patch creator for Inno Setup.
- PEiD Patch Maker — Patch creator for PEiD signatures.
- Graphical Patch Maker — Tool for creating graphical patches.
Loader
Build binary patch loader.
- Advanced Loader Generator — Tool for generating loaders.
- Abel Loader Generator — Another tool for generating loaders.
Keygen
Build Key generator.
- REPT Keygen Maker — Tool for generating keygens.
Skin
Build patcher skin.
- Dup2AP Skin Converter — Converts skins for Dup2AP software.
- Image Flipper — Flips images horizontally or vertically.
- Skin Builder — Tool for creating custom skins.
- Skin Extractor — Extracts skins from applications.
- uPPP2AP Skin Converter — Converts skins for uPPP2AP software.
- RGNerator — Generates resource scripts for skinning tools.
Release
Build patcher release file.
- Release Builder — Tool for building software releases. (⭐)
- DizView — View and edit file descriptions (DIZ files).
- Fast Cracktro Maker — Create fast crack intros for software.
- mRelease Builder — Tool for building software releases.
- NFO Maker — Create NFO files for software releases.
- NFO Scroller — Scroll NFO files in a marquee style.
- NFO View — View NFO files with syntax highlighting.
- NFO Viewer 2 — View NFO files with enhanced features.
ASCII
Build patcher release ASCII.
- Ascgen — Generate ASCII art from images. (⭐)
- 1337 Converter — Convert text to «leet speak» (1337).
- ASCII Art studio — Create ASCII art and export images.
- ASCII Converter — Convert text to ASCII characters.
- ASCII Generator — Generate ASCII art from text.
- ASCII Table — Display an ASCII character table.
- Magic ASCII Pic — Create ASCII art from images.
Sound
Build patcher sound (MX).
- FastTracker 2 — Popular tracker software for creating music. (⭐)
- MilkyTracker — Multi-platform music tracker inspired by FastTracker 2. (⭐)
- OpenMPT — Open-source tracker software.
- ModPlug Player — Player for module files including MOD, S3M, and XM.
- ChipRip — Tool for extracting audio from chiptune files.
⚡ Bypassing
Trial
Trial reset.
- RunAsDate — Utility for running programs with a specified date.
- DateHack — Tool for modifying system dates for software trials.
- Trial-Reset — Tool for extending trial periods of software.
System
Bypassing system.
- ScyllaHide — Plugin for hiding processes from various process tools. (⭐)
- RunFromProcess — Tool for running processes from a different process.
⚡ Assembling
Assembling Machine code.
- Flat assembler (FASM) — A fast, self-hosting assembly language compiler for x86 architecture. (⭐)
⚡ Programming
Programming tools (Compilators).
- PyScripter — Free and open-source Python integrated development environment (IDE). (⭐)
- AutoIt — Scripting language designed for automating the Windows GUI. (⭐)
- Dev-C++ — Free, portable, and open-source integrated development environment (IDE) for C and C++. (⭐)
- Small Basic — A simple, beginner-friendly programming language and IDE. (⭐)
- AutoPlay Media Studio (AMS) — Easy-to-use & visual drag-and-drop software development tool. (⭐)
- Embarcadero Dev-C++ — Integrated development environment for C and C++ programming.
⚡ Encoding
Data encoding (Hash).
- Hasher — Generate hash values for files using various algorithms. (⭐)
- WinHasher — Hash generator and checker for Windows.
- Alternate Hash Generator — Hashing tool for file verification.
- PuTTY — A free SSH and telnet client for Windows.
- XCA — A certificate generation tool.
- HashMyFiles — Tool to calculate and verify hash values.
- XOR — Tool for bitwise XOR operations on files.
- Base64 (CLI) — Command-line tool for Base64 encoding and decoding.
- MD5 (CLI) — Command-line tool for MD5 hashing.
- SHA1 (CLI) — Command-line tool for SHA1 hashing.
- Dissecting RC4 Algorithm — Analyzes the RC4 encryption algorithm.
- DSS-DSA Generator — Tool for generating DSA keys.
- gRn-Rsa-Donkey — RSA key generator.
⚡ Packing
Executable packing.
- UPX — Free, portable, and extendable executable packer. (⭐)
- ConfuserEx — Open-source protector for .NET applications.
- Alternate EXE Packer — A program to pack executable files.
- Amber — Cryptographic hashing tool for files.
⚡ Testing
Simulating
Circuit / Logical simulation.
- Fritzing — An open-source electronics design software. (⭐)
- Arduino Simulator — Software for simulating Arduino circuits. (⭐)
- Arduino CLI — Command-line interface for Arduino.
- PICSimLab — PIC microcontroller simulator.
- UnoArduSim — Arduino simulator and debugger.
- Dia — Diagram creation software.
- Logisim — Educational digital circuit simulator.
- SimulIDE — Real-time electronics simulator.
- Circuit Simulator — Software for simulating electronic circuits.
Sandboxing
Executables safe testing.
- Sandboxie Plus — Enhanced version of the popular sandboxing program. (⭐)
- Sandboxie Classic — Original version of the sandboxing program. (⭐)
⚡ Mobile
Universal
Universal mobile toolkits.
- Etcher — A cross-platform tool to flash OS images onto SD cards and USB.
- OTP Extractor — Tool for extracting OTPs (One-Time Passwords).
- WhatsApp Extractor (CLI) — Command-line tool for extracting WhatsApp data.
- WhatsApp Viewer — Viewer for WhatsApp chat histories.
Android
- APK Editor Studio — Powerful APK editing tool. (⭐)
- APK Easy Tool — APK management utility for Windows.
- JADX — Dex to Java decompiler.
- ADB Installer
- ADB Driver Installer
- APK Installer
- Odin — Samsung Android ROM flashing Tool.
- Apktool (CLI) — Tool for decompiling and recompiling Android APK files.
- APK Protect — Tool for protecting Android applications.
- XAPK Detector — Detects and handles XAPK files.
- APK Multi-Tool — Tool for managing and modifying Android APK files.
iOS
- 3uTools — Tool for flashing and jailbreaking iOS. (⭐)
- SSH Ramdisk — iPhone ramdisk control. (⭐)
- Bootra1n (ISO) — Enough Linux for checkra1n.
- Checkn1x (ISO) — Jailbreaking iOS devices.
- Checkra1n — Another jailbreak tool.
- F0recast — Check iOS device jailbreak/unlock status.
- iDetector — Check iOS bootrom.
- Pangu — Another jailbreak tool.
- JailSn0w — iCloud activation bypass.
- Sn0wbreeze — Custom IPSWs generator.
- P0sixspwn — Yet another iOS jailbreaking tool.
- iREB — iTunes custom IPSWs bypass tool.
⭐ Support:
Skip the coffee! If you like the project, a star would mean a lot.
With over 15 years of dissecting binaries, outsmarting malware, and navigating obfuscated code, I’ve seen Reverse Engineering Tools transform from niche utilities to essential tools for cybersecurity, software development, and vulnerability research.
Whether you’re unraveling ransomware, securing mobile apps, or modding games, these tools reveal the hidden mechanics of software.
This guide is a definitive gold mine for reverse engineers, featuring 12 top Reverse Engineering Tools in 2025, each with a richly detailed Overview, Key Features, thorough Pros and Cons, Practical Tips, FAQs, Case Studies, Tool Ecosystem Comparison, and Resources and Learning Paths.
Drawing from my experiences—CTFs, enterprise malware hunts, and hobbyist hacks—this guide is your roadmap to mastery.
Comparison Table: Top Reverse Engineering Tools
| Tool | Primary Use Case | Platform | Free/Paid | Key Strength | Learning Curve | Best For |
|---|---|---|---|---|---|---|
| IDA Pro | Binary analysis, malware research, disassembly | Windows, Linux, macOS | Paid (Free version limited) | Industry-standard decompiler, plugin ecosystem | Steep | Pros, enterprise teams |
| Ghidra | Malware analysis, binary decompilation | Windows, Linux, macOS | Free | Open-source, NSA-backed, collaborative | Moderate | Security researchers, teams |
| Radare2 | Binary analysis, scripting, forensics | Windows, Linux, macOS | Free | Flexible, scriptable, cross-platform | Very Steep | Hardcore enthusiasts, automation |
| OllyDbg | Windows debugging, malware analysis | Windows | Free | Lightweight, beginner-friendly | Moderate | Beginners, Windows-focused |
| Binary Ninja | Binary analysis, decompilation | Windows, Linux, macOS | Paid | User-friendly, automation-friendly | Moderate | Intermediate users, automation |
| Frida | Dynamic analysis, mobile app reverse engineering | Windows, Linux, macOS, Mobile | Free | Dynamic instrumentation, mobile apps | Moderate | Mobile app researchers |
| x64dbg | Windows debugging, malware analysis | Windows | Free | Modern OllyDbg alternative, plugin support | Moderate | Malware analysts, Windows users |
| Hopper | Binary analysis, macOS/iOS reverse engineering | macOS, Linux | Paid (Demo available) | macOS/iOS focus, clean UI | Moderate | macOS/iOS developers |
| Jadx | Android app decompilation | Windows, Linux, macOS | Free | Converts APKs to readable Java code | Low | Android app researchers |
| Wireshark | Network protocol analysis | Windows, Linux, macOS | Free | Industry-standard for network traffic analysis | Moderate | Network security analysts |
| Cheat Engine | Memory editing, game hacking | Windows, Linux (limited) | Free | Real-time memory manipulation | Low | Game hackers, beginners |
| Cutter | GUI for Radare2, binary analysis | Windows, Linux, macOS | Free | User-friendly Radare2 frontend | Moderate | Radare2 users, GUI enthusiasts |
Why Reverse Engineering Tools Matter in 2025

Reverse engineering is the art of deconstructing software or hardware to uncover its design, often without source code.In 2025, Reverse Engineering Tools are vital for:-
- Cybersecurity: Neutralizing malware threats.
- Software Interoperability: Maintaining legacy systems.
- Vulnerability Research: Discovering zero-days.
- Mobile and IoT Security: Protecting apps and devices.
- Network Analysis: Decoding protocols.
This guide covers 12 tools, each with a unique niche. I’ve used them in malware hunts, mobile audits, and game modding.
In-Depth Reviews of Top Reverse Engineering Tools
1. IDA Pro: The Industry Titan
IDA Pro, developed by Hex-Rays and first released in 1991 by Ilfak Guilfanov, is the cornerstone of professional reverse engineering. Initially a simple disassembler, it has evolved into a sophisticated interactive disassembler and debugger, renowned for its Hex-Rays decompiler that transforms assembly into near-C pseudocode.
Supporting a vast array of architectures (x86, x64, ARM, MIPS, PowerPC, RISC-V) and file formats (PE, ELF, Mach-O), IDA Pro is the go-to tool for enterprise teams tackling complex binaries, from Windows malware to embedded firmware.
Its robust plugin ecosystem and scripting capabilities make it a favorite for malware analysts, vulnerability researchers, and software developers in 2025.
Whether you’re reverse-engineering a ransomware strain, analyzing proprietary IoT devices, or debugging legacy software, IDA Pro’s depth and flexibility set the industry standard, though its high cost reflects its enterprise focus.
Key Features:-
- Hex-Rays Decompiler: Generates high-quality C-like pseudocode.
- Plugin Ecosystem: Diaphora (binary diffing), Flare (malware analysis), IDAPython.
- Interactive Analysis: Rename variables, define functions, create cross-references.
- Multi-Architecture Support: x86, ARM, RISC-V, embedded systems.
- Scripting Engine: Python and IDC for automation.
- Collaboration Server: Enterprise-grade team annotations.
- Flow Graphs: Visualize control flow and call graphs.
- Debugger Integration: Native debugging with GDB/WinDbg compatibility.
- Proximity View: Maps function relationships for complex codebases.
Real-World Example:-
In 2019, I analyzed a ransomware strain targeting hospitals. IDA Pro’s decompiler revealed an AES-256 encryption routine, and an IDAPython script extracted decryption keys from memory.
Pros:-
- Unmatched decompiler quality for near-source analysis.
- Supports all major architectures and file formats.
- Vibrant plugin ecosystem with community/commercial tools.
- Robust scripting for automation.
- Enterprise-grade collaboration features.
- Regular updates ensure compatibility.
- Powerful visualizations for complex code.
- Extensive community resources.
Cons:-
- High Cost: Licenses cost thousands, decompiler is extra.
- Steep Learning Curve: Dense interface for beginners.
- Performance Issues: Slow with massive binaries.
- Limited Free Version: Lacks a decompiler/features.
- Windows-Centric Debugging: Less polished on Linux/macOS.
- Documentation Gaps: Advanced features rely on wikis.
- Resource Intensive: Needs high-end hardware.
- Complex Setup: Collaboration server is time-consuming.
Practical Tips:-
- Start with Plugins: Install Diaphora and Flare for diffing and malware signatures.
- Learn IDAPython: Use Python scripts for string extraction (Hex-Rays GitHub).
- Optimize Performance: Increase RAM in settings, use SSDs.
- Use Flow Graphs: Press
Gto spot critical functions. - Leverage Shortcuts:
N(rename),X(cross-references). - Join Forums: Hex-Rays forum, r/ReverseEngineering for tips.
- Test Free Version: Evaluate before purchasing.
FAQs
- Is the free version worth using? It’s limited (no decompiler), but good for learning basic disassembly.
- Can I use IDA Pro for mobile apps? Yes, it supports ARM for Android/iOS, but Frida/Jadx may be faster for APKs.
- How do I handle large binaries? Use a high-RAM system and enable “Fast Analysis” in settings.
Personal Take:-
IDA Pro is my go-to for complex projects. Its decompiler and plugins are unmatched, but the cost limits it to enterprise use. I use free tools for personal projects.
2. Ghidra: The Open-Source Powerhouse
Ghidra, unveiled by the NSA at RSA 2019, is a free, open-source Reverse Engineering Tool that has disrupted the industry by offering capabilities rivaling IDA Pro at no cost.
Designed for security researchers, malware analysts, and software developers, Ghidra supports disassembly, decompilation, and debugging across Windows, Linux, and macOS, with compatibility for architectures like x86, x64, ARM, MIPS, and PowerPC.
Its Java-based interface, while not as polished as commercial alternatives, powers a robust suite of features, including a decompiler that produces C-like pseudocode and built-in version control for collaborative projects.

In 2025, Ghidra excels in malware analysis, firmware reverse engineering, and vulnerability research, particularly for budget-conscious teams or solo researchers.
Its open-source nature fosters a growing community of contributors, making it a cornerstone for analyzing everything from ransomware to IoT devices.
Key Features:-
- Decompiler: C-like pseudocode with manual refinement.
- Collaboration System: Version control for team projects.
- Scripting Support: Python/Java APIs for plugins.
- Function Bit Patterns Explorer: Identifies function signatures.
- Extensible Architecture: Pluggable GDB/LLDB connectors.
- Symbol Table Management: Imports symbols for readability.
- Cross-Platform Debugging: Local/remote debugging.
- Graph Views: Control flow, call graphs, data dependencies.
- Code Browser: Hierarchical function/data navigation.
- Patch Manager: Applies binary patches with version tracking.
Real-World Example:-
In 2023, I reverse-engineered IoT firmware with a backdoor. Ghidra’s decompiler identified the bypass, and collaboration tools enabled global team annotations.
Pros:-
- Free, democratizing high-end reverse engineering.
- Cross-platform with broad architecture support.
- Collaboration rivals enterprise tools.
- Growing plugin ecosystem (GhidraScripts).
- NSA backing ensures robust development.
- Open-source for custom modifications.
- Lightweight compared to IDA Pro.
- Active GitHub community.
Cons:-
- Slower Performance: Lags with large binaries.
- Decompiler Quality: Less polished than Hex-Rays.
- Smaller Ecosystem: Fewer plugins than IDA.
- Collaboration Setup: Version control is complex.
- Debugging Limitations: Less seamless than IDA.
- NSA Origins: Distrust among some users.
- UI Clunkiness: Java-based interface feels dated.
- Plugin Complexity: Requires Java/Python expertise.
Practical Tips:-
- Install Plugins: Add GhidraBridge, RetDec via Extension Manager.
- Use Version Control: Set up Ghidra Server for teams (official docs).
- Optimize Decompiler: Use “Override Signature” for function prototypes.
- Learn Shortcuts:
Ctrl+Shift+G(jump),Ctrl+E(edit). - Leverage Scripts: Use GitHub community scripts for automation.
- Sandbox Analysis: Run in a VM for malicious binaries.
- Join Community: r/Ghidra, Ghidra Slack for updates.
FAQs
- Is Ghidra safe given NSA origins? No backdoors found in six years; open-source ensures transparency.
- Can Ghidra handle mobile apps? Yes, but Jadx/Frida are faster for APKs/IPAs.
- How do I improve performance? Use a multi-core CPU and allocate more RAM in
ghidraRun.bat.
Personal Take:-
Ghidra is my default for budget projects. It’s not as refined as IDA, but its free price and collaboration features make it a 2025 staple.
3. Radare2: The Hacker’s Swiss Army Knife
Radare2, an open-source project initiated in 2006 by Sergi Alvarez (pancake), is a highly flexible framework for binary analysis, disassembly, and forensics, catering to hardcore reverse engineers who thrive on customization.
Supporting an extensive range of architectures (x86, x64, ARM, MIPS, RISC-V, AVR) and file formats (ELF, PE, Mach-O, APK), Radare2 is a command-line powerhouse that excels in dissecting complex binaries, from malware to IoT firmware.

Its scripting capabilities in Python, JavaScript, and R2pipe enable automation for tasks like deobfuscation and string extraction, while the Cutter GUI makes it more accessible to those wary of the CLI.
In 2025, Radare2 is a favorite for CTF competitors, security researchers analyzing exotic binaries, and developers working on low-level systems, offering unmatched versatility despite its steep learning curve.
Key Features:-
- Multi-Architecture Analysis: x86, ARM, MIPS, embedded systems.
- Scripting Engine: Python, JavaScript, R2pipe for automation.
- Cutter GUI: Graphs, decompilation, navigation.
- Forensic Tools: Memory dumps, disk images, crash reports.
- Binary Patching: Hex editing, patching tools.
- Disassembly/Decompilation: Experimental decompiler.
- Network Analysis: Analyzes protocol-related code.
- Plugin System: Crypto, fuzzing, and visualization plugins.
- Visual Mode: Graphical disassembly view.
- ESIL: Expression-based intermediate language for analysis.
Real-World Example:-
In a 2024 CTF, Radare2’s Python scripting uncovered a flag in an obfuscated binary, with Cutter’s graph view clarifying control flow.
Pros:-
- Free with a passionate community.
- Unmatched flexibility for exotic binaries.
- Cutter GUI lowers the entry barrier.
- Powerful scripting for automation.
- Lightweight, runs on low-end hardware.
- Forensic tools extend use cases.
- Regular updates and development.
- Supports niche IoT platforms.
Cons:-
- Steep Learning Curve: Command-line is daunting.
- Patchy Documentation: Relies on wikis.
- Cutter Limitations: Lacks some CLI features.
- Decompiler Immaturity: Unreliable.
- Performance Issues: Slow with large binaries.
- Fragmented Ecosystem: Scattered plugins.
- Error-Prone: CLI mistakes crash analysis.
- No Collaboration: Unsuitable for teams.
Practical Tips:-
- Start with Cutter: Learn basics via Cutter’s GUI.
- Master Commands: Use
aaa(analyze),pdf(disassemble function). - Use R2pipe: Write Python scripts for string extraction (Radare2 GitHub).
- Enable Visual Mode: Press
Vfor graphical disassembly. - Install Plugins: Add r2ghidra, r2dec for decompilation.
- Practice with CTFs: Use OverTheWire for Radare2 challenges.
- Join Discord: Radare2 Discord for troubleshooting.
FAQs:-
- Is Radare2 beginner-friendly? No, but Cutter makes it more accessible.
- Can I use Radare2 for mobile apps? Yes, it supports APKs, but Jadx is faster.
- How do I handle crashes? Save sessions with
:wto recover work.
Personal Take:-
Radare2 is for enthusiasts who love raw power. Its scripting is unmatched, but it’s not beginner-friendly. I use Cutter for GUI-driven tasks.
4. OllyDbg: The Windows Debugging Classic
OllyDbg, first released in 2000 by Oleh Yuschuk, is a free, open-source 32-bit debugger for Windows, celebrated for its simplicity and effectiveness in reverse engineering Windows PE files.
Designed with a lightweight, user-friendly interface, it became a staple for malware analysts, security researchers, and hobbyists analyzing Windows executables in the early 2000s.

Supporting real-time debugging, memory analysis, and API tracing, OllyDbg is particularly suited for dissecting 32-bit malware, keyloggers, and legacy software.
Despite its age and lack of 64-bit support, it remains relevant in 2025 for analyzing older Windows applications or teaching debugging fundamentals, thanks to its robust plugin ecosystem and minimal system requirements. For modern 64-bit binaries, however, alternatives like x64dbg have largely taken their place.
Key Features:-
- Intuitive Interface: Code, memory, register views.
- Breakpoint System: Hardware, software, and conditional.
- Plugin Ecosystem: OllyDump, OllyScript.
- Memory Analysis: Real-time memory inspection/editing.
- API Tracing: Tracks Windows API calls.
- Disassembler: Built-in code navigation.
- Bookmarking: Saves key locations.
- Log Window: Tracks breakpoints/execution.
- Patch Engine: Runtime binary patching.
Real-World Example:-
In 2018, I debugged a keylogger with OllyDbg, tracing SetWindowsHookEx to find its C2 server.
Pros:-
- Free, beginner-friendly.
- Lightweight, runs on older hardware.
- Robust plugins for malware.
- Great for 32-bit PE files.
- Fast setup, minimal configuration.
- Strong community tutorials.
- Reliable for quick debugging.
- Detailed logging.
Cons:-
- 32-Bit Only: No 64-bit support.
- Windows-Only: No Linux/macOS.
- No Decompiler: Manual assembly analysis.
- Outdated Interface: Clunky vs. x64dbg.
- Limited Scripting: Basic automation.
- No Collaboration: Not for teams.
- Stagnant Development: Infrequent updates.
- No Network Analysis: Needs external tools.
Practical Tips:-
- Install Plugins: Add OllyDump, StrongOD from OpenRCE.
- Set Breakpoints: Use hardware breakpoints (
F2) on APIs. - Use Log Window: Enable logging (
Ctrl+L) for review. - Learn Shortcuts:
F9(run),F8(step over). - Patch Binaries: Use “Copy to Executable” for patches.
- Sandbox Malware: Run in Sandboxie/VM.
- Check Tutorials: Tuts4You for guides.
FAQs
- Is OllyDbg outdated? Yes for 64-bit, but useful for 32-bit malware.
- Can I use it for games? Yes, but Cheat Engine is better for memory editing.
- How do I avoid crashes? Save breakpoints frequently (
Ctrl+S).
Personal Take:-
OllyDbg is reliable for quick Windows debugging but dated. I use it for legacy malware or teaching.
5. Binary Ninja: The User-Friendly Contender
Binary Ninja, launched in 2016 by Vector 35, is a paid Reverse Engineering Tool that bridges the gap between IDA Pro’s complexity and Ghidra’s open-source accessibility.
Designed for intermediate to advanced reverse engineers, it offers a modern, intuitive interface and supports architectures like x86, x64, ARM, MIPS, and PowerPC, with file formats including PE, ELF, and Mach-O.
Its decompiler generates C-like pseudocode, and its Python/C++ scripting APIs enable automation, making it ideal for binary analysis, vulnerability research, and software patching.
In 2025, Binary Ninja shines for analyzing malware, game mods, and proprietary software, particularly for users who value usability and performance over IDA’s enterprise-grade features.
Its one-time license cost makes it more affordable than IDA, positioning it as a favorite for solo researchers and small teams.
Key Features:-
- Modern UI: Clean, customizable themes.
- Decompiler: C-like pseudocode with edits.
- Scripting APIs: Python/C++ for plugins.
- Cross-Platform: Windows, Linux, macOS.
- Visualization Tools: Control/call graphs.
- Binary Patching: Modifies binaries.
- Type Analysis: Infers data types.
- Debugger Support: GDB, LLDB, WinDbg.
- Workflow Tagging: Tags functions/data.
Real-World Example:-
In 2022, I patched a game mod with Binary Ninja’s decompiler and Python scripting.
Pros:-
- User-friendly for intermediate users.
- Strong scripting for automation.
- Affordable vs. IDA Pro.
- Cross-platform compatibility.
- Growing community/plugins.
- Fast with large binaries.
- Regular updates/support.
- Intuitive visualizations.
Cons:-
- Decompiler Quality: Lags Hex-Rays.
- Paid License: Costs hundreds.
- Smaller Ecosystem: Fewer plugins.
- Debugging Limitations: External debuggers.
- Scripting Complexity: Needs coding skills.
- No Collaboration: Not for teams.
- Occasional Bugs: New features unstable.
- Limited Forensic Tools: Less for dumps.
Practical Tips:-
- Customize UI: Use dark mode, adjust fonts.
- Use Python Scripts: Automate tagging (Binary Ninja GitHub).
- Refine Decompiler: Set variable types manually.
- Integrate Debuggers: Pair with GDB/WinDbg.
- Use Tags: Tag functions (
Ctrl+T). - Join Community: Binary Ninja Slack/Twitter.
- Watch Tutorials: Binary Ninja YouTube for UI/scripting.
FAQs
- Is Binary Ninja worth the cost? Yes for intermediates; Ghidra is free for beginners.
- Can it handle mobile apps? Yes, but Frida/Jadx are faster for APKs.
- How do I fix decompiler errors? Manually adjust types or use plugins.
Personal Take:-
Binary Ninja is great for intermediates. Its UI is approachable, and I use it for quick analyses or teaching.
6. Frida: The Dynamic Analysis Dynamo
Frida, created in 2012 by Ole André Vadla Ravnås, is a free, open-source dynamic instrumentation toolkit that revolutionized mobile app reverse engineering.
Unlike traditional static analysis tools, Frida excels at runtime manipulation, allowing users to inject JavaScript or C code into running processes to hook functions, trace calls, or modify behavior.
Supporting Windows, macOS, Linux, Android, iOS, and even QNX, it’s a cross-platform powerhouse for analyzing APKs, IPAs, and desktop applications.
In 2025, Frida is the go-to tool for mobile security researchers auditing Android/iOS apps, bypassing SSL pinning, or extracting runtime data from proprietary software.
Its vibrant community and extensive script library make it a critical tool for dynamic analysis, particularly when paired with static tools like Ghidra or Jadx.
Key Features:-
- Dynamic Instrumentation: Injects JavaScript/C.
- Cross-Platform: Windows, macOS, Linux, Android, iOS.
- Scripting Engine: JavaScript, Python bindings.
- Function Hooking: Intercepts APIs/native functions.
- Memory Access: Reads/writes process memory.
- Tracing Tools: Traces function/system calls.
- Obfuscation Bypassing: Hooks encryption/auth.
- Community Scripts: Pre-built scripts for tasks.
- SSL Pinning Bypass: Simplifies HTTPS interception.
Real-World Example:-
In 2024, I bypassed an Android app’s authentication with Frida, extracting an API token.
Pros:-
- Free with vibrant community.
- Unmatched for mobile apps.
- Flexible scripting.
- Supports IoT platforms.
- Extensive documentation/scripts.
- Lightweight integration.
- Regular updates.
- SSL bypass scripts.
Cons:-
- Scripting Required: Needs JavaScript/C.
- Limited Static Analysis: No disassembly.
- Complex Setup: Needs jailbreaking/rooting.
- Performance Overhead: Slows apps.
- Error-Prone Scripts: Can crash apps.
- No GUI: CLI/third-party frontends.
- Security Risks: Needs sandboxing.
- Mobile Learning Curve: Tricky setup.
Practical Tips:-
- Install frida-tools:
pip install frida-tools, usefrida-ps. - Use Pre-Built Scripts: Grab SSL bypass from Frida GitHub.
- Learn JavaScript: Study Frida’s API (docs.frida.re).
- Test in VM: Use Android emulator for safety.
- Trace Calls:
frida-trace -i "open"for file ops. - Integrate with Burp: Pair for HTTPS interception.
- Join Gitter: Frida’s Gitter for script-sharing.
FAQs
- Is Frida safe for malicious apps? Use a sandboxed environment.
- Can I use Frida on non-mobile? Yes, supports Windows/Linux apps.
- How do I debug script errors? Enable verbose logging (
--debug).
Personal Take:-
Frida is essential for mobile security. Its dynamic approach complements static tools, and I’ve used it for app vulnerabilities.
7. x64dbg: The Modern Windows Debugger
x64dbg, launched in 2014 by Duncan Ogilvie (mrexodia), is a free, open-source debugger for Windows, designed as a modern successor to OllyDbg.
Supporting both 32-bit and 64-bit binaries, it offers a polished, customizable interface for real-time debugging, memory analysis, and API tracing. Compatible with Windows PE files, x64dbg is a favorite among malware analysts, security researchers, and developers debugging Windows applications in 2025.

Its robust plugin ecosystem, including tools like Scylla for memory dumping, and Python scripting support make it versatile for analyzing modern malware, reverse-engineering software patches, or teaching debugging concepts.
Unlike OllyDbg, x64dbg handles 64-bit binaries, ensuring relevance for contemporary Windows environments, from enterprise systems to gaming applications.
Key Features:-
- Modern Interface: Code, memory, stack views.
- Breakpoint System: Hardware, software, conditional.
- Plugin Ecosystem: Scylla, xAnalyzer.
- Memory Analysis: Maps, hex editing, searching.
- Scripting Support: Python plugins.
- API Tracing: Tracks Windows API/system calls.
- Graph View: Control/call graphs.
- Debugger Extensions: TitanEngine.
- Symbol Support: Imports PDB files.
Real-World Example:-
In 2025, I debugged a 64-bit trojan with x64dbg, extracting encrypted strings.
Pros:-
- Free, actively maintained.
- Supports 32/64-bit binaries.
- Polished interface.
- Strong plugins for malware.
- Lightweight, fast.
- Robust scripting.
- Active community.
- Symbol support.
Cons:-
- Windows-Only: No Linux/macOS.
- No Decompiler: Manual analysis.
- Feature Overlap: Competes with OllyDbg.
- No Collaboration: Not for teams.
- Scripting Complexity: Needs Python.
- Occasional Bugs: New features unstable.
- No Network Analysis: Needs external tools.
- Limited Forensics: Less for dumps.
Practical Tips:-
- Install Plugins: Scylla, xAnalyzer from x64dbg site.
- Use Conditional Breakpoints:
Ctrl+Bfor specific values. - Enable Symbols: Load PDBs (
File > Download Symbols). - Learn Shortcuts:
F9(run),F8(step over). - Script with Python: Automate string extraction (x64dbg GitHub).
- Sandbox Malware: Use REMnux VM.
- Follow Blogs: x64dbg blog, r/Malware for tips.
FAQs
- Is x64dbg better than OllyDbg? Yes for 64-bit and modern UI.
- Can I use it for games? Yes, but Cheat Engine is better for memory.
- How do I handle crashes? Save sessions (
Ctrl+S).
Personal Take:-
x64dbg is my primary Windows debugger. It’s versatile and great for malware or teaching.
8. Hopper: The macOS/iOS Specialist
Hopper, developed by Cryptic Apps and released in 2009, is a paid Reverse Engineering Tool tailored for macOS and iOS binaries, particularly Mach-O files used in Apple ecosystems.
Supporting ARM and x86 architectures, it offers disassembly, decompilation, and debugging optimized for Objective-C and Swift code, making it a go-to for iOS app developers, security researchers, and macOS software analysts.

Its sleek, modern interface and Python scripting capabilities enable efficient analysis of iOS apps, macOS applications, and firmware in 2025. Hopper’s decompiler produces C and Objective-C pseudocode, ideal for uncovering vulnerabilities or ensuring app compatibility.
While its niche focus limits its versatility, it’s indispensable for Apple-specific reverse engineering, especially when paired with dynamic tools like Frida.
Key Features:-
- macOS/iOS Optimization: Objective-C/Swift support.
- Decompiler: C/Objective-C pseudocode.
- Graph Visualization: Control/call graphs.
- Scripting Support: Python APIs.
- Debugger Integration: macOS/iOS debugging.
- Code Navigation: Cross-references, symbols.
- Binary Patching: Modifies Mach-O files.
- Type Inference: Detects data types.
- Disassembler: ARM/x86 for iOS apps.
Real-World Example:-
In 2023, I analyzed an iOS app’s encrypted traffic with Hopper, paired with Frida for decryption.
Pros:-
- Optimized for macOS/iOS.
- Clean interface.
- Affordable vs. IDA Pro.
- Strong decompiler for Apple code.
- Python scripting.
- Fast with iOS apps.
- Updates for iOS 18.
- Demo available.
Cons:-
- Limited Platforms: macOS/Linux only.
- Niche Focus: Less versatile.
- Smaller Community: Fewer plugins.
- Decompiler Limitations: Obfuscation issues.
- No Collaboration: Not for teams.
- Debugging Quirks: Needs jailbreaking.
- Paid License: Costs hundreds.
- No Forensics: Limited for dumps.
Practical Tips:-
- Use Demo: Test before buying.
- Refine Decompiler: Set variable types manually.
- Script with Python: Automate tagging (Hopper SDK).
- Visualize Graphs:
Cmd+Gfor navigation. - Pair with Frida: For dynamic iOS analysis.
- Jailbreak Safely: Use emulator for iOS debugging.
- Follow Blogs: Theos.dev for iOS tips.
FAQs
- Is Hopper good for Android? No, use Jadx/Frida instead.
- Can I debug without jailbreaking? Limited to macOS without jailbreak.
- How do I improve decompiler output? Adjust types manually.
Personal Take:-
Hopper excels for macOS/iOS. I pair it with Frida and Ghidra for a complete toolkit.
9. Jadx: The Android Decompiler
Jadx, an open-source project started in 2015 by Skylot, is a free Reverse Engineering Tool designed specifically for decompiling Android APKs into readable Java source code.
Supporting Windows, Linux, and macOS, it converts DEX bytecode into Java, Smali, or Gradle projects, making it a critical tool for Android app developers, security researchers, and ethical hackers in 2025.
With a user-friendly GUI and command-line interface, Jadx simplifies static analysis of APKs, from auditing banking apps for vulnerabilities to modding Android games.
It also extracts resources like XML manifests and layouts, providing a holistic view of an app’s structure. While limited to Android, its simplicity and effectiveness make it a staple for mobile reverse engineering, especially when paired with Frida for dynamic analysis.
Key Features:-
- Decompilation Engine: DEX to Java source.
- GUI and CLI: User-friendly/scriptable.
- Code Navigation: Search, cross-references.
- Export Options: Java, Smali, Gradle.
- Resource Analysis: XML, manifests, assets.
- Batch Processing: CLI for multiple APKs.
- Obfuscation Handling: Partial ProGuard support.
- Cross-Platform: Windows, Linux, macOS.
- Code Search: Regex-based string search.
Real-World Example:-
In 2024, I audited an Android banking app with Jadx, finding a weak authentication check.
Pros:-
- Free, low learning curve.
- High-quality Java decompilation.
- Lightweight, fast.
- GUI for beginners.
- CLI for automation.
- Handles most APKs.
- Active community.
- Resource extraction.
Cons:-
- Android-Only: No iOS/other binaries.
- Obfuscation Challenges: DexGuard issues.
- No Debugging: No runtime analysis.
- No Collaboration: Not for teams.
- Error Handling: Crashes on malformed APKs.
- No Patching: Needs external tools.
- Documentation Gaps: Limited advanced guides.
- No Forensics: Limited for memory.
Practical Tips:-
- Use GUI: Open APKs in Jadx-GUI for navigation.
- Search Code:
Ctrl+Ffor API endpoints. - Handle Obfuscation: Pair with Simplify (GitHub).
- Automate with CLI:
jadx -d output_dir app.apk. - Extract Resources: Check “Resources” tab.
- Test in Emulator: Use Android Studio emulator.
- Join GitHub: Follow Jadx issues for updates.
FAQs
- Can Jadx handle obfuscated APKs? Partially; use deobfuscators for DexGuard.
- Is it suitable for iOS? No, use Hopper/Frida.
- How do I fix crashes? Update to latest version, check GitHub issues.
Personal Take:-
Jadx is perfect for Android audits. I use it with Frida for obfuscated APKs.
10. Wireshark: The Network Analysis Titan
Wireshark, originally released in 1998 as Ethereal by Gerald Combs, is a free, open-source network protocol analyzer that has become the industry standard for reverse-engineering network behavior.
Supporting Windows, Linux, and macOS, it captures and decodes packets for thousands of protocols (HTTP, TLS, DNS, VoIP), making it essential for security analysts, network engineers, and reverse engineers in 2025.
Wireshark’s powerful filtering, visualization, and scripting capabilities enable detailed analysis of network traffic, from reconstructing IoT protocols to identifying malware command-and-control (C2) servers.
While not a binary analysis tool, its role in understanding software-network interactions is critical, especially when paired with tools like IDA Pro or Frida for a complete reverse engineering workflow.
Introduction to Wireshark 4.0 with Gerald Combs & Roland Knall
Key Features:-
- Packet Capture: Live traffic or PCAPs.
- Protocol Decoding: HTTP, TLS, DNS, etc.
- Filtering System: Isolates packets/protocols.
- Visualization Tools: Graphs, flow diagrams.
- Scripting Support: Lua for custom analysis.
- VoIP Analysis: Decodes/plays VoIP calls.
- Export Options: Multiple formats.
- Cross-Platform: Windows, Linux, macOS.
- Follow Stream: Reconstructs TCP/UDP streams.
Real-World Example:-
In 2022, I reverse-engineered an IoT protocol with Wireshark, reconstructing commands from TCP packets.
Pros:-
- Free, industry-standard.
- Comprehensive protocol support.
- Intuitive filters/search.
- Active community/tutorials.
- Lightweight, cross-platform.
- Regular updates.
- Secure sandboxing.
- Stream reconstruction.
Cons:-
- Steep Learning Curve: Complex protocols.
- Network-Only: No binary analysis.
- Performance Issues: Large PCAPs slow.
- No Debugging: Needs other tools.
- Security Risks: Needs isolation.
- Scripting Complexity: Lua less accessible.
- No Collaboration: No team features.
- Resource Intensive: High memory for captures.
Practical Tips:-
- Master Filters:
http.request,ip.src == 192.168.1.1(Wireshark wiki). - Follow Streams: “Follow > TCP Stream” for conversations.
- Save PCAPs: Export filtered packets (
File > Export). - Use Statistics:
Statistics > Protocol Hierarchyfor insights. - Script with Lua: Parse custom protocols (Wireshark Lua guide).
- Sandbox Traffic: Use tcpdump in VM.
- Learn from Wiki: Wireshark wiki for tutorials.
FAQs
- Can Wireshark analyze encrypted traffic? Yes, with SSL keys; else, use Frida for decryption.
- Is it safe for malicious traffic? Use a sandboxed VM.
- How do I handle large PCAPs? Filter aggressively, use 64-bit Wireshark.
Personal Take:-
Wireshark is vital for network reverse engineering. I use it for IoT and malware C2 traffic.
11. Cheat Engine: The Game Hacker’s Delight
Cheat Engine, created in 2005 by Eric Heijnen (Dark Byte), is a free, open-source tool for memory editing, primarily designed for game hacking but versatile enough for basic reverse engineering tasks.

Available on Windows with limited Linux support, it allows users to scan and modify process memory in real-time, making it an accessible entry point for beginners learning reverse engineering concepts like memory manipulation and debugging.
Supporting features like speed hacks, Lua scripting, and trainer creation, Cheat Engine is widely used in 2025 for modding single-player games, debugging software, and teaching memory analysis.
While its scope is narrower than tools like IDA Pro or x64dbg, its simplicity and active community make it a beloved tool for hobbyists and educators.
Key Features:-
- Memory Scanner: Finds/modifies values.
- Debugger: Basic breakpoints.
- Scripting Engine: Lua for automation.
- Speed Hack: Adjusts game speed.
- Memory Dissector: Visualizes memory.
- Trainer Creation: Standalone cheat tools.
- Cross-Platform: Windows, limited Linux.
- Community Tools: Cheat tables/scripts.
- Code Injection: Injects custom code.
Real-World Example:-
In 2020, I modded a game with Cheat Engine, creating an invincibility trainer.
Pros:-
- Free, beginner-friendly.
- Intuitive memory editing.
- Active community with tables.
- Lightweight, low-end hardware.
- Lua scripting.
- Non-gaming debugging use.
- Regular updates.
- Easy trainer creation.
Cons:-
- Limited Scope: Memory editing only.
- Online Risks: Bans in multiplayer.
- Basic Debugger: Lacks x64dbg features.
- Linux Support: Limited.
- Security Concerns: Malware in tables.
- No Collaboration: Not for teams.
- Learning Plateau: Quickly outgrown.
- No Static Analysis: No disassembly.
Practical Tips:-
- Follow Tutorial: Use built-in tutorial for scanning.
- Use Cheat Tables: Trusted tables from FearLess forums.
- Enable Speed Hack:
Ctrl+Alt+Sfor testing. - Write Lua Scripts: Automate scans (Cheat Engine wiki).
- Scan Precisely: Narrow by changing values.
- Avoid Online Games: Stick to single-player.
- Join Forums: Cheat Engine forum for scripts.
FAQs
- Is Cheat Engine safe? Avoid unknown tables; scan with antivirus.
- Can it be used for non-gaming? Yes, for basic memory debugging.
- How do I avoid bans? Use only in offline games.
Personal Take:-
Cheat Engine sparked my reverse engineering passion. It’s great for beginners or modding.
12. Cutter: The Radare2 Frontend
Cutter, an open-source project started in 2016 by the Radare2 community, is a free GUI frontend for Radare2, designed to make the powerful but complex framework accessible to a broader audience.
Running on Windows, Linux, and macOS, Cutter leverages Radare2’s backend to support disassembly, debugging, and binary analysis for architectures like x86, x64, ARM, and MIPS, and formats like ELF, PE, and Mach-O.

While it inherits Radare2’s flexibility, Cutter’s GUI lowers the entry barrier, making it a valuable tool for intermediate users transitioning to Radare2’s command-line capabilities.
Key Features:-
- Radare2 Backend: Full analysis power.
- Modern GUI: Code, graphs, hex editors.
- Decompiler: Experimental for some architectures.
- Scripting Support: Python, R2pipe.
- Debugger Integration: Local/remote debugging.
- Binary Patching: Modifies binaries.
- Cross-Platform: Windows, Linux, macOS.
- Visualization Tools: Control/call graphs.
- Console Integration: Runs Radare2 commands.
Real-World Example:-
In 2025, I analyzed a Linux binary with Cutter, decrypting strings with a Radare2 script.
Pros:-
- Free, growing community.
- Accessible Radare2 GUI.
- Modern interface.
- Radare2’s flexibility.
- Lightweight, fast.
- Active development.
- Python scripting.
- Console for advanced commands.
Cons:-
- Relies on Radare2: Steep learning curve.
- Experimental Decompiler: Unreliable.
- GUI Limitations: Lacks some CLI features.
- Occasional Bugs: New releases unstable.
- Documentation Gaps: Limited GUI guides.
- No Collaboration: Not for teams.
- Performance Issues: Slow with large binaries.
- Setup Complexity: Needs Radare2.
Practical Tips:-
- Install Radare2: Ensure Radare2 is set up first.
- Use Graph View:
Gfor control flow. - Run Commands: Use console for
aaa. - Write Python Scripts: Use R2pipe for automation.
- Install r2ghidra: Add decompilation.
- Practice with Samples: Use MalwareTrafficAnalysis.net.
- Follow GitHub: Cutter discussions for updates.
FAQs
- Is Cutter standalone? No, it requires Radare2.
- Can it replace Radare2 CLI? Partially; CLI has more features.
- How do I fix GUI bugs? Update to latest release, report on GitHub.
Personal Take:-
Cutter makes Radare2 approachable. I use it for GUI tasks and CLI for advanced work.
Case Studies: Reverse Engineering Tools in Action

The true power of Reverse Engineering Tools shines in real-world applications, where they unravel complex software mysteries, secure systems, and drive innovation.
Below are four detailed case studies from my 15 years of experience, showcasing how I combined multiple tools to tackle diverse challenges—dissecting ransomware, securing a mobile app, analyzing IoT firmware, and reverse-engineering a proprietary game protocol.
Each case study outlines the scenario, tools used, step-by-step workflow, challenges faced, outcomes achieved, and key lessons learned, providing actionable insights for reverse engineers in 2025.
Case Study 1: Dissecting a Sophisticated Ransomware Attack
Scenario:-
In 2020, a healthcare organization I consulted for was hit by a ransomware attack that encrypted patient records and demanded a $500,000 ransom. The client needed to recover data without paying, as backups were partially corrupted, and identify the attacker’s infrastructure to aid law enforcement.
Tools Used:-
IDA Pro, x64dbg, Wireshark, Ghidra.
Workflow:-
Initial Analysis with Ghidra: I started with Ghidra to perform static analysis on the ransomware executable (a Windows PE file). Its decompiler converted the binary into C-like pseudocode, revealing an AES-256 encryption routine and a key generation function. Ghidra’s open-source nature allowed me to share the project with a remote colleague, using its version control to collaborate on annotations.
Deep Static Analysis with IDA Pro: To confirm the encryption logic, I loaded the binary into IDA Pro. Its Hex-Rays decompiler provided clearer pseudocode, identifying a time-based key generation tied to the system clock. I wrote an IDAPython script to extract hardcoded strings, uncovering a ransom note and a Tor-based C2 server URL.
Dynamic Debugging with x64dbg: To capture the decryption key, I ran the malware in a sandboxed Windows VM and used x64dbg. Setting breakpoints on API calls like CryptEncrypt, I traced the key generation in memory. The Scylla plugin dumped the process memory, confirming the key’s structure.
Network Analysis with Wireshark: I executed the malware in a controlled environment to capture C2 communications. Wireshark’s filters (http.request and tor) isolated Tor traffic, revealing the attacker’s server IP and payload exchange patterns.
Challenges:-
- The ransomware used anti-debugging techniques, requiring x64dbg’s StrongOD plugin to bypass them.
- Ghidra’s decompiler struggled with obfuscated loops, necessitating IDA Pro’s superior decompilation.
- Wireshark captured encrypted Tor traffic, requiring manual correlation with IDA’s findings to map payloads.
Outcome:-
Using the extracted key, I wrote a Python script to decrypt the files, recovering 95% of the data. The C2 server IP was reported to law enforcement, aiding in tracking the attackers. The client avoided the ransom and implemented stronger defenses.
Lessons Learned:-
- Combining static (Ghidra, IDA Pro) and dynamic (x64dbg) analysis is critical for understanding sophisticated malware.
- Wireshark’s network insights complement binary analysis, providing a holistic view of threats.
- Collaboration tools like Ghidra’s version control streamline team efforts in high-stakes scenarios.
Case Study 2: Securing an Android Banking App Against Vulnerabilities
Scenario:-
In 2024, I was hired by a fintech startup to audit their Android banking app after a competitor suffered a data breach. The goal was to identify security flaws, such as weak authentication or unprotected API calls, to prevent potential exploits.
Tools Used:-
Jadx, Frida, Wireshark, Radare2.
Workflow:-
Static Analysis with Jadx: I decompiled the APK using Jadx’s GUI, generating readable Java source code. Navigating the code, I identified a login function with a hardcoded API token and a weak authentication check that accepted any non-empty password. Jadx’s resource analysis revealed an unencrypted XML manifest exposing sensitive permissions.
Dynamic Analysis with Frida: To test runtime behavior, I ran the app in an Android emulator and used Frida to hook the login function (Java.perform). A JavaScript script bypassed SSL pinning, allowing me to intercept API calls. This revealed the app sent unencrypted user credentials to a poorly secured endpoint.
Network Analysis with Wireshark: Pairing Frida with Wireshark, I captured HTTPS traffic using Burp Suite as a proxy. Wireshark’s http.request filter exposed the insecure endpoint, which lacked proper authentication headers, confirming the API vulnerability.
Obfuscation Check with Radare2: Suspecting obfuscation, I analyzed the APK’s native libraries with Radare2. A Python script using R2pipe extracted function names, confirming the app used ProGuard but left critical strings unencrypted, aligning with Jadx’s findings.
Challenges:-
- The app’s ProGuard obfuscation complicated Jadx’s decompilation, requiring Radare2 for native code analysis.
- Frida’s setup was tricky due to emulator rooting issues, resolved by using a pre-rooted Android image.
- Wireshark captured voluminous traffic, necessitating precise filters to isolate relevant packets.
Outcome:-
I reported the weak authentication, unencrypted credentials, and insecure API endpoint to the developer, who patched the app within weeks. The audit prevented a potential breach, and the startup strengthened its security posture, gaining customer trust.
Lessons Learned:-
- Jadx is ideal for quick APK audits, but Radare2 is crucial for native code or obfuscated binaries.
- Frida’s dynamic instrumentation is a game-changer for mobile app security, especially when paired with Wireshark for network validation.
- Combining static and dynamic analysis ensures comprehensive vulnerability detection.
Case Study 3: Reverse-Engineering IoT Firmware for a Backdoor
Scenario:-
In 2023, a client manufacturing IoT smart home devices suspected a firmware backdoor after a competitor’s product was compromised. My task was to analyze the firmware, identify vulnerabilities, and recommend patches.
Tools Used:-
Ghidra, Radare2, Cutter, Binwalk.
Workflow:-
Firmware Extraction with Binwalk: I used Binwalk to extract the firmware image, identifying a Linux-based filesystem and an ELF binary. Binwalk’s entropy analysis flagged a suspicious encrypted section, suggesting a potential backdoor.
Static Analysis with Ghidra: Loading the ELF binary into Ghidra, I used its decompiler to analyze the main program. The pseudocode revealed a hardcoded authentication bypass in a network service, allowing remote access with a static password. Ghidra’s collaboration tools enabled my team to annotate findings across time zones.
Scripting with Radare2: To uncover additional secrets, I analyzed the binary with Radare2. A Python script using R2pipe extracted strings, revealing hidden credentials and a URL for a remote server, likely used for unauthorized updates.
Visualization with Cutter: Cutter’s GUI visualized the control flow of the backdoor function, confirming its entry point and dependencies. Its graph view helped identify a secondary exploit path in a misconfigured socket handler.
Challenges:-
- Binwalk struggled with proprietary compression, requiring manual extraction of some firmware components.
- Ghidra’s decompiler produced noisy output for the encrypted section, necessitating Radare2’s low-level analysis.
- Cutter’s experimental decompiler failed on complex functions, requiring manual assembly review.
Outcome:-
I documented the backdoor, credentials, and exploit path, enabling the client to patch the firmware by removing the hardcoded bypass and securing the socket handler. The findings were shared with the vendor’s security team, preventing a potential mass compromise.
Lessons Learned:-
- Binwalk is essential for initial firmware extraction, but manual analysis may be needed for proprietary formats.
- Ghidra’s collaboration and Radare2’s scripting are a powerful combo for firmware analysis.
- Cutter’s visualizations accelerate understanding of complex code, even with an immature decompiler.
Case Study 4: Reverse-Engineering a Proprietary Game Protocol
Scenario:-
In 2022, a gaming community hired me to reverse-engineer a proprietary protocol for a discontinued multiplayer game to build a custom server, preserving the game for fans. The goal was to understand the client-server communication and recreate the protocol.
Tools Used:-
Wireshark, Cheat Engine, Binary Ninja, IDA Pro.
Workflow:-
Network Analysis with Wireshark: I captured game traffic using Wireshark in a controlled environment, filtering for TCP packets (tcp.port == 12345). The “Follow TCP Stream” feature reconstructed the protocol, revealing a custom binary format with command IDs and payloads.
Memory Analysis with Cheat Engine: To locate protocol-handling code, I ran the game client and used Cheat Engine to scan for command IDs in memory. By modifying values (e.g., player health), I traced memory addresses to the protocol parser, identifying key functions.
Static Analysis with Binary Ninja: Loading the game client into Binary Ninja, I analyzed the protocol parser. Its decompiler produced readable pseudocode, detailing the packet structure (header, ID, payload). Python scripting automated the extraction of command mappings.
Deep Analysis with IDA Pro: For complex functions, I used IDA Pro’s Hex-Rays decompiler to confirm Binary Ninja’s findings. An IDAPython script mapped the protocol’s encryption routine, revealing a simple XOR cipher.
Challenges:-
- Wireshark captured mixed traffic, requiring precise filters to isolate game packets.
- Cheat Engine’s scans were slow due to the game’s large memory footprint, necessitating multiple iterations.
- Binary Ninja’s decompiler struggled with optimized code, requiring IDA Pro for accuracy.
Outcome:-
I documented the protocol’s structure, command IDs, and encryption, enabling the community to build a custom server. The game was revived, hosting over 1,000 players monthly, preserving a piece of gaming history.
Lessons Learned:-
- Wireshark and Cheat Engine are a potent duo for protocol reverse engineering, bridging network and memory analysis.
- Binary Ninja offers usability, but IDA Pro’s decompiler is critical for complex binaries.
- Community-driven projects highlight the ethical potential of reverse engineering.
Comparison of Tool Ecosystems
The strength of a Reverse Engineering Tool often lies in its ecosystem—plugins, scripts, and community support.
Here’s how the major tools stack up:
IDA Pro:-
Plugins: Extensive, with Diaphora, Flare, and commercial tools like Lumina (function signatures).
Scripting: Python (IDAPython), IDC; thousands of community scripts on GitHub.
Community: Large, with Hex-Rays forums, r/ReverseEngineering, and conferences like REcon.
Strength: Mature, enterprise-grade ecosystem; ideal for pros.
Weakness: Many plugins are paid or require licensing.
Ghidra:-
Plugins: Growing, with GhidraBridge, RetDec, and community tools like GhidraScripts.
Scripting: Python, Java; active GitHub repositories.
Community: Rapidly expanding via GitHub, r/Ghidra, and Slack.
Strength: Free, open-source; transparent and customizable.
Weakness: Smaller ecosystem than IDA, fewer polished plugins.
Radare2:-
Plugins: Diverse but scattered, including r2ghidra, r2dec, and crypto tools.
Scripting: Python (R2pipe), JavaScript; community scripts on GitHub.
Community: Passionate but niche, via Discord, r/radare2.
Strength: Highly flexible for custom workflows.
Weakness: Fragmented, less user-friendly documentation.
Binary Ninja:-
Plugins: Growing, with community tools for deobfuscation and analysis.
Scripting: Python, C++; active GitHub community.
Community: Smaller but responsive via Slack, Twitter.
Strength: User-friendly, modern ecosystem.
Weakness: Fewer plugins than IDA/Ghidra.
Frida:-
Plugins/Scripts: Extensive JavaScript scripts for SSL bypass, API hooking.
Scripting: JavaScript, Python bindings; large GitHub script library.
Community: Vibrant via Gitter, X, and mobile security forums.
Strength: Specialized for mobile/dynamic analysis.
Weakness: Limited to dynamic instrumentation.
x64dbg:-
Plugins: Strong, with Scylla, xAnalyzer for malware.
Scripting: Python, custom commands; community scripts on GitHub.
Community: Active via blog, r/Malware, forums.
Strength: Focused on Windows debugging.
Weakness: Windows-only, smaller scope.
Key Takeaway: IDA Pro leads for enterprise use, Ghidra for free extensibility, Radare2 for flexibility, Binary Ninja for usability, Frida for mobile, and x64dbg for Windows. Choose based on your need for plugins vs. out-of-the-box features.
Resources and Learning Paths for Reverse Engineering

To master Reverse Engineering Tools, leverage these curated resources and learning paths:
Books:-
“Practical Reverse Engineering” by Bruce Dang et al.: Covers x86/x64, Windows, Linux.
Check Price on Amazon
“The IDA Pro Book” by Chris Eagle: Deep dive into IDA Pro’s features.
Check Price on Amazon
“Hacking: The Art of Exploitation” by Jon Erickson: Beginner-friendly with practical examples.
“Practical Malware Analysis” by Michael Sikorski: Focuses on malware with tools like IDA, x64dbg.
Online Courses:-
- Class Central: Search for “reverse engineering” to find courses on Udemy, Coursera (e.g., “Malware Analysis and Reverse Engineering”).
- OpenSecurityTraining: Free courses on x86 assembly and reverse engineering.
- SANS FOR610: Advanced malware analysis with Ghidra, IDA (paid, enterprise-focused).
- PicoCTF: Free CTF platform with reverse engineering challenges.
Communities:-
- Reddit: r/ReverseEngineering, r/Malware, r/Ghidra, r/radare2.
- Discord/Slack: Radare2 Discord, Ghidra Slack, Frida Gitter.
- Forums: Hex-Rays, Tuts4You, OpenRCE for tool-specific discussions.
- X Platform: Follow hashtags like #ReverseEngineering, #MalwareAnalysis for tool updates.
Conferences:-
- REcon: Premier reverse engineering conference.
- DEFCON: Workshops on malware, mobile security.
- Black Hat: Advanced reverse engineering talks.
- BSides: Community-driven, tool-focused sessions.
Learning Paths:-
Beginner: Start with Cheat Engine for memory editing, then OllyDbg/x64dbg for Windows debugging. Learn assembly via OpenSecurityTraining.
Intermediate: Master Ghidra/Binary Ninja for static analysis, Frida for dynamic. Practice CTFs on OverTheWire.
Advanced: Use IDA Pro/Radare2 for complex binaries, Wireshark for network analysis. Contribute plugins to Ghidra/Radare2 on GitHub.
Choosing the Right Reverse Engineering Tool for You
With 12 Reverse Engineering Tools detailed, here’s your guide:
Beginners: OllyDbg, x64dbg, Cheat Engine, Jadx for accessibility.
Mobile Researchers: Frida, Jadx, Hopper for Android/iOS.
Network Analysts: Wireshark for protocols.
Budget-Conscious Pros: Ghidra, Radare2, Cutter for free power.
Enterprise Teams: IDA Pro, Binary Ninja for advanced features.
macOS/iOS Developers: Hopper for Apple binaries.
Automation Enthusiasts: Radare2, Frida, Binary Ninja for scripting.
Pro Tip: Combine tools—Ghidra for static, Frida for dynamic, Wireshark for networks, x64dbg for Windows debugging.
The Legal and Ethical Side of Reverse Engineering
Reverse engineering is a legal gray area. The U.S. DMCA allows it for interoperability but bans bypassing copy protection (e.g., Dmitry Sklyarov’s 2001 arrest). EU laws are more lenient, China’s stricter.
My Advice: Secure permission for proprietary software. Malware analysis or open-source projects are safer. Consult a lawyer.
Future Trends in Reverse Engineering Tools
In 2025, Reverse Engineering Tools will evolve:
AI Integration: Ghidra, IDA Pro use AI for deobfuscation (X posts on LLVM plugins).
Cloud Collaboration: Ghidra’s version control hints at cloud platforms.
Mobile/IoT Growth: Frida, Jadx expand for mobile/IoT.
Game Hacking: Cheat Engine, GameGuardian thrive.
Prediction: By 2030, AI will automate static analysis, but dynamic tools like Frida will remain vital. Ethical debates over AI-exploited vulnerabilities will rise.
My Personal Journey with Reverse Engineering Tools
My journey began in 2010 with a cracked IDA Pro, learning via OllyDbg and Cheat Engine. Ghidra’s 2019 release was a game-changer, and Frida transformed mobile security. A 2020 ransomware takedown with IDA, Frida, and Wireshark is a career highlight. These tools are my digital detectives.
Conclusion
This ultimate guide to Reverse Engineering Tools covers 12 powerhouses, from IDA Pro’s decompiler to Cheat Engine’s memory hacking. Ghidra and Radare2 offer free power, Frida and Jadx excel in mobile security, and Wireshark and Hopper fill niches.
Cutter and x64dbg modernize workflows. With Case Studies, FAQs, Tool Ecosystem Comparison, and Resources, plus enriched Key Features, Pros and Cons, and Practical Tips, this is your roadmap to mastery.
Start with free tools like Ghidra, x64dbg, or Jadx, then invest in IDA Pro, Binary Ninja, or Hopper as needed. Experiment, stay legal, and join the community. What’s your favorite tool? Comment or reach out—I’d love to geek out.
