The rise of wireless networks has been tremendous in the past decade with every building fitted with several connections. Moreover, people are more concerned about their network connection than ever before. Infamous for its security consequences, hacking is an advanced technical skill that can give a user access to any secured device. However, learning the skill requires the right equipment, this is where some of the best Wi-Fi hacking tools come into the picture. But every new tech comes with its repercussions as these same tools can be used to exploit other Wi-Fi networks.

Wi-Fi hacking can be easy or very hard based on several system settings. It is dependent on two main factors:
1. Weak passwords: One of the most common ways for hackers to gain access to a Wi-Fi network is by using a weak password. Many people use default passwords for their routers, which are easy for hackers to guess. Others use weak passwords that are easy to remember, such as password 123456.
2. Unencrypted networks: Wi-Fi networks can be encrypted to protect them from hackers. However, some people choose to leave their networks unencrypted, either because they don’t know how to encrypt them or because they think it’s not necessary. Unencrypted networks are easy for hackers to access.
Top and Popular Wireless Hacking Tools
For a Wi-Fi hacking tool to be effective, it should have a few key attributes. This includes the capability of sniffing network packets and analyzing, and locating wireless network security gaps such as the WEP and WPA vulnerabilities, dictionary attacks, password guessing, and creating fake access points for tricking users. Some of the tools with all these features are listed below.
Note: Hacking into a device can cause privacy and security threats to a PC, which can result in legal consequences for the practitioner. Therefore, it is important that the use of the following tools is done in a responsible manner. The user descition is advised
1. Aircrack-ng

Aircrack-ng is one of the prominent and free WiFi password hacking tools and is written in C-language to evaluate the efficiency of network security. This tool works via a sequential process involving monitoring, attacking, testing, and cracking WI-FI passwords. While its primary emphasis is on the Linux operating system; however, it also supports Windows OS X, FreeBSD, NetBSD, OpenBSD, Solaris, and eComStation 2.
- Supports a wide range of operating systems, including Linux, Windows, OS X, and more.
- Utilizes various attacks, including FMS, Korek, and PTW attacks, to optimize the speed and efficiency of password cracking.
- Capable of cracking WEP keys using FMS, PTW, and dictionary attacks.
- Can crack WPA2-PSK through dictionary attacks.
- Focuses on Replay attacks, de-authentication, and creating fake access points for network assessment.
2. Wireshark

Wireshark is an open source WiFi hacking tool that provides best-in-class data packet analysis and network protocol examination solutions. It is one of the most popular among Windows users’ software for network troubleshooting, software development, and educational functions. With its ability to capture even the smallest details of network activity, Wireshark allows the examination and analysis of diverse protocols on a microscopic scale.
- Live packet captures and offline analysis, providing real-time insight into network activities.
- Cross-platform compatibility, supporting Windows, Linux, Mac OS, Solaris, FreeBSD, NetBSD, and more.
- Allows the application of color-coded rules to packet lists, facilitating quick and easy analysis.
- Rich Voice over Internet Protocol (VoIP) analysis for assessing phone services over the internet.
- Can decompress gzip files on-the-fly without disrupting running programs.
- Decrypts various protocols including IPsec, ISAKMP, SSL/TLS, and more.
Also Read: What is Ethical Hacking?
3. Kismet

Kismet is one of the most popular Wi-Fi hacking tools for PC, intended for ethical hackers and security specialists. Kismet is a versatile wireless network sniffer and intrusion detection tool, named after Arabic word division. It collects packets passively to recognize networks and even unveil hidden ones as a valuable resource for network analysis and security assessment.
- Supports Wi-Fi, Bluetooth, software-defined Radio (SDR), and various wireless protocols.
- Capable of identifying hidden Wi-Fi networks by analyzing broadcasted packets.
- Works with any Wi-Fi card that supports raw monitoring mode.
- Supports 802.11 standards including 802.11a, 802.11b, 802.11g, and 802.11n traffic.
- Operates on various operating systems, including Linux (e.g., Ubuntu, Backtrack), FreeBSD, NetBSD, OpenBSD, Mac OS X, and can be used on Windows through WSL (Windows Subsystem for Linux).
4. CoWPAtty

CoWPAtty is, in fact, one of the most successful tools for Wi-Fi hacking. It is meant, among other things, for conducting offline dictionary-based attacks on wireless networks but has such an extraordinary name as this. This tool authored by Joshua Wright is a way by which attackers, hackers, and network managers crack into the WPA/WPA2 protected networks relying on PreShared Key (PSK) authentication method. While Cowpatty runs on Linux and has a command-line interface, it operates using a wordlist containing potential passwords for the attack.
- Automated dictionary attack tool specifically designed for WPA-PSK networks.
- Compatible with Linux operating systems, making it an ideal choice for Linux users.
- Utilizes offline attacks, exploiting authentication based on the PSK model.
- Employs PBKDF2 with 4096 iterations for passphrase generation, slowing down brute force attacks.
5. Airjack

Airjack is a powerful Wi-Fi 802.11 packet injection tool and forms a critical part of network manipulation activities. It is a tool that has been widely used in various operations such as injecting forged packets, facilitating denial of service attacks to disrupt networks, and enabling man-in-the-middle attacks on wireless networks. Airjack is a necessary tool for ethical hackers and security professionals who want to test, evaluate, and secure their wireless networks.
- Specialized tool for Wi-Fi 802.11 packet injection.
- Enables the injection of forged packets into wireless networks.
- Capable of initiating denial of service attacks to disrupt network services.
- Facilitates man-in-the-middle attacks for intercepting and manipulating network traffic.
- A valuable asset for network penetration testing and security assessment.
Also Read: 17 Best App for WhatsApp Hacking
6. AirSnort

AirSnort, a widely known Wi-Fi password hacking software, is a must tool for decrypting WEP Keys specifically in Wi-Fi 802.11b Networks. This software was developed by Blake Hegerle and Jeremy Bruestle, it is freely available for Linux as well as Windows operating systems. Its main purpose is to intercept and analyze packets that belong to the network it targets in order to recover its password or encryption key.
- Designed for cracking WEP passwords in 802.11b wireless networks.
- Free to use and available for both Linux and Windows operating systems.
- Downloads are available via Sourceforge, ensuring easy access for users.
- Utilizes a passive attack approach, monitoring network transmissions to gather data packets.
- Computes the encryption key once a sufficient quantity of data packets has been captured.
- Operates by observing and identifying data patterns to recover encryption or password keys.
7. Wifite 2

One of the best tools for simplifying the complexities of wireless hacking is Wifite, a Python script for wireless security auditing. The tool is invaluable for security professionals and ethical hackers as it speeds up the wireless auditing process by automatically running available hacking tools for you. Whether you’re auditing WEP or WPA-encrypted wireless networks, Wifite leverages tools like aircrack-ng, pyrite, reaver, and shark to execute various attacks. The author has made a full-fledged rewrite of the original tool to be fully compatible with Kali Linux and ParrotSec.
- Simplifies wireless security auditing by automating the execution of various hacking tools.
- Supports auditing of WEP and WPA encrypted wireless networks.
- Customizable and can be automated with minimal arguments, reducing the need for user supervision.
- Compatible with popular Linux pentesting distributions like Kali Linux, Pentoo, BackBox, and others.
8. inSSIDer

inSSIDer is a highly regarded Wi-Fi scanner designed for Microsoft Windows and OS X operating systems. This versatile tool is ideal for various Wi-Fi auditing tasks, making it an invaluable resource for both professionals and enthusiasts.
- Effortlessly locates open Wi-Fi access points, aiding in the discovery of available networks.
- Provides detailed signal strength measurements, allowing users to assess signal quality and coverage.
- Logs data with GPS records, making it convenient for analyzing and mapping the location of Wi-Fi networks.
- Offers a freemium model, with basic functionality available for free, while advanced features require a paid membership.
Also Read: 20 Best WiFi Hacking Tools for PC
9. NetStumbler

NetStumbler, also known as Network Stumbler, is a widely recognized and free wireless LAN detection tool specifically designed for Windows operating systems. It is good at detecting WiFi, 802.11b, 802.11g, and 802.11a network types. NetStumbler is one of the top war-driving tools and is used in mapping wireless networks in the local area as well as in various network assessment activities.
- Detects and identifies 802.11a, 802.11b, and 802.11g wireless networks.
- Utilized in wardriving, which involves mapping open wireless access points while on the move.
- Provides information on network configurations, signal strength, network congestion, and potential rogue access points.
- Effective in pinpointing areas of poor network coverage, aiding in network optimization.
- Helps uncover unauthorized access points based on signal strength variations.
- Runs on Windows operating systems from Windows 2000 to Windows XP.
10. Wifiphisher

WiFiphisher is an advanced tool that enables man-in-the-middle (MITM) attack, utilizing Wi-Fi associations for intercepting, monitoring and possibly modifying wireless traffic. The attack works by attempting to convince wireless users to connect into an unauthorized access point which eventually allows attackers to compromise data security.
- Conducts man-in-the-middle attacks by luring wireless users to connect to a rogue access point.
- Enables attackers to intercept, monitor, and potentially modify wireless traffic.
- Supports web phishing attacks to collect user credentials for third-party websites or Wi-Fi network access.
- Modular design allows advanced users to develop custom code, extending its functionalities.
- Disrupts existing connections to target access points using de-authenticate or Disassociate packets.
- Sniffs and replicates the settings of the target access point.
11. Airgeddon

Airgeddon is a comprehensive tool designed for wireless network security analysis, streamlining the complexity of Wi-Fi security audits by integrating multiple existing tools into a single, user-friendly command-line interface.
- Interface mode switcher for Monitor and Managed modes, maintaining selections even when the interface name changes.
- Multiple Denial of Service (DoS) methods for disrupting wireless networks (mdk3, mdk4, airplay-ng), including DoS Pursuit mode to counter AP channel hopping during Evil Twin attacks.
- Full support for both 2.4GHz and 5GHz frequency bands.
- Assisted WPA/WPA2 handshake file and PMKID capturing for personal networks.
- Offline password decryption for WPA/WPA2 captured files, utilizing dictionary, brute-force, and rule-based attacks with tools like aircrack, crunch, and hashcat. Enterprise network password decryption based on John the ripper, crunch, asleap, and hashcat tools.
Also Read: 15 Best WiFi Hacking Apps For Android (2023)
12. CommView for WiFi

CommView for WiFi is a robust and user-friendly wireless network monitoring and packet analysis tool compatible with a wide range of Wi-Fi networks. Here are key features of CommView for WiFi:
- Comprehensive support for 802.11 a/b/g/n/ac/ax networks.
- Captures and analyzes every packet in the air, providing essential information such as access points, stations, signal strength, protocol distribution, and network connections.
- Enables user-defined decryption of captured packets using WEP or WPA/WPA2-PSK keys.
- Ideal for Wi-Fi network administrators, security professionals, home users monitoring their Wi-Fi traffic, and software programmers working on wireless network applications.
- Offers in-depth analysis, recording, and playback of SIP and H.323 voice communications with a dedicated VoIP module.
13. OmniPeek

OmniPeek stands as a robust and comprehensive packet sniffer and network analysis tool, primarily designed for Windows OS. It is a commercial tool, recognized for its extensive feature set, which makes it invaluable for various networking tasks. Here are its key features:
- Commercial network analysis tool for Windows, known for its comprehensive capabilities.
- An all-in-one Wi-Fi network management solution that covers packet capture, protocol decoding, network diagnostics, and troubleshooting.
- Allows for playback and analysis of voice and video traffic, aiding in diagnostic processes.
- Provides intuitive visualizations of packet data, aiding in the quick resolution of network and application performance issues.
- Supports real-time visibility and expert analysis of various network aspects, including Ethernet, Gigabit, 10 Gigabit, 802.11a/b/g/n/ac wireless, VoIP, and video.
14. Kali Linux NetHunter

Kali Linux NetHunter is an exceptional mobile penetration testing platform that extends the power of Kali Linux to Android devices. It is fully open-source and designed to run on various Android smartphones, including popular brands like OnePlus, Samsung, and Google Nexus. Here are the key features of Kali NetHunter:
- Compatible with a wide range of Android devices, offering flexibility and accessibility.
- Developed and maintained by a community of volunteers, with project funding from Offensive Security.
- Available in multiple editions, including NetHunter Rootless for un-rooted devices, NetHunter Lite for rooted devices with custom recovery, and NetHunter for rooted devices with NetHunter-specific kernels.
- Core features include a Kali Linux container with a comprehensive set of security tools and applications, a dedicated Kali NetHunter App Store, an Android client for easy access to the App Store, and the Kali NetHunter Desktop Experience (KeX) for running full Kali Linux desktop sessions and supporting screen mirroring via HDMI or wireless casting.
Also Read: 16 Best Game Hacking Apps for Android
15. Maltego

Maltego is a powerful hacking tool for data mining and link analysis, making it one of the best WiFi hacking tools for PCs. It offers a range of versions to cater to different needs, from the free Community Edition to the more powerful paid options. Here are some key features and pricing details:
- Available in free and paid versions.
- Node-based graphical representation of data.
- Supports Windows, Linux, and Mac operating systems.
- Real-time data mining and information gathering capabilities.
- Utilizes node-based graphical patterns for data representation.
- Maltego XL excels in handling large graphs and highlights network vulnerabilities.
- Online training courses with a three-month access period and a certificate upon completion.
16. Cain & Abel

Cain & Abel is a renowned WiFi hacking tool, named after the biblical children of Adam and Eve. While it’s popular for its WiFi password recovery capabilities, it uses a variety of techniques to investigate and analyze data packets individually, decrypt scrambled passwords, and recover wireless network keys. This tool supports various versions of Microsoft OS and employs methods like brute force, dictionary attacks, and cryptanalysis attacks. Additionally, it offers features like Address Resolution Protocol (ARP) support for detection on switched LANs and MITM (Man-in-the-Middle) attacks, making it a versatile choice for network security enthusiasts.
- Network packet sniffing for capturing and analyzing data traffic.
- Password cracking through methods such as dictionary attacks and cryptanalysis.
- Keylogger functionality for recording keystrokes.
- Port scanner to identify open ports on a network.
- ARP poisoning and DNS spoofing for network security assessments.
- MAC address spoofing to manipulate network access.
17. Cloud Cracker
Cloud Cracker is a valuable online password cracking service tailored for penetration testers and network auditors, serving their needs for evaluating the security of protected wireless networks, breaking password hashes, and decrypting document encryption. This tool simplifies and accelerates the process of assessing network and document security, making it a valuable resource for security professionals.
- Specialized in checking the security of WPA-protected wireless networks, ideal for testing network vulnerabilities.
- Capable of cracking password hashes, providing essential support for security assessments.
- Offers document encryption decryption, making it a versatile tool for security audits.
- Streamlines the process of assessing network and document security, saving time and effort for security professionals.
Also Read: 7 Best Websites To Learn Ethical Hacking
One thing you must know is that operating some of these best Wi-Fi hacking tools might be a little tricky. Also, you are advised to use caution and only indulge in legal activities. If you have any queries or suggestions, do let us know in the comments section below.
Уровень сложностиСредний
Время на прочтение6 мин
Количество просмотров32K
Помните, что использование полученных знаний и навыков должно быть ограничено законными и этическими рамками, и вмешательство в чужие сети без разрешения является неприемлемым и незаконным действием.
Это дополнение к основной статье «Как стать гуру или Wi-Fi Cheat Sheet». Я увидел много откликов по данной теме как положительных, так и отрицательных. Кому-то не нравится подача (да, есть свои минусы, но перенести материал из обычной заметки Markdown достаточно сложно), кому-то инструменты, но кто Я такой, чтобы останавливаться. Сегодня я приложу максимально полный список инструментов с кратким описанием.

Прошу не оценивать это, как полноценную статью (пока не могу понять общее отношение к статьям на habr), это лишь дополнение к прошлой. Давайте начинать, но с оглавления.

Как по мне, больше похож на Ёлку _)
Оглавление
-
Личный топ инструментов
-
Denial of Service (DoS) \ Deauthentication
-
Атаки на шифрование
-
WEP/WPA/WPA2
-
WPS
-
Атаки на Enterprise
-
-
Инъекции
-
Evil twin / Fake AP / MITM
-
Wardriving
-
Различные иные инструменты
-
Сбор информации
-
Защита / Обнаружение
-
Мониторинг
-
Заключение
Личный топ инструментов
Начнем с моих любимых инструментов, которые мне помогали в работе или косвенно использовались более нескольких раз.
-
Aircrack-ng — Набор средств аудита безопасности WiFi
-
airgeddon — Это многофункциональный bash-скрипт для Linux-систем, предназначенный для аудита беспроводных сетей
-
eaphammer- СЕРДЕЧКО Фреймворк для атак на WPA2-Enterprise
-
kismet — Детектор беспроводных сетей, сниффер и система обнаружения вторжений
-
pyrit — Известный взломщик WPA с предварительными вычислениями. Pyrit позволяет создавать массивные базы данных предварительно вычисленных фаз аутентификации WPA/WPA2-PSK в режиме «пространство-время-торможение». Используя вычислительную мощь многоядерных процессоров и других платформ через ATI-Stream, Nvidia CUDA и OpenCL, он на сегодняшний день является самой мощной атакой на один из самых используемых в мире протоколов безопасности.
-
wifiphisher — Инструмент для автоматизированных атак фишинга на клиентов Wi-Fi.
-
Scapy — Интерактивная программа и библиотека для работы с пакетами на языке Python
-
WiFi-Pumpkin — Фреймворк для атак на неавторизованные точки доступа
-
Wireless-ids — обследует окружающий эфир на предмет подозрительных действий, таких как атаки на пакеты WEP/WPA/WPS
Denial of Service (DoS) \ Deauthentication
Проведение DoS или дуатентификации — один из важнейших этапов тестирования Wi-Fi точки или для проведдения атак на рукопожатия.
-
80211mgmtDoS — Инструмент для проведения атак типа «Denial of Service» (DoS) в сетях 802.11 на основе не защищенных управляющих фреймов.
-
airodump_mod — Улучшенная версия airodump-ng с возможностью деаутентификации с точек доступа.
-
apflood — Переполняет область фальшивыми идентификаторами сетей (ESSID).
-
dw — Маленький инструмент для отправки пакетов с отключением и деаутентификацией 802.11 на конкретных клиентах.
-
hwk — Сборник инструментов для создания и флуда пакетов в сетях.
-
Mass-deauth — Скрипт для массовой деаутентификации в сетях 802.11.
-
modwifi — Инструмент для проведения продвинутых атак на Wi-Fi с использованием стандартного оборудования.
-
netattack — Скрипт на Python для сканирования локальной сети на наличие Wi-Fi-сетей и проведения атак деаутентификации.
-
ska — Фреймворк для перехвата пакетов IEEE802.11 и создания пакетов деаутентификации.
-
zizzania — Автоматизированная атака деаутентификации.
Атаки на шифрование
WEP/WPA/WPA2
-
Aircrack-ng — Набор инструментов для аудита безопасности Wi-Fi;
-
asleap — Восстановление слабых паролей LEAP (сокращение от «asleep»);
-
Fern-wifi-cracker — Инструмент для взлома и восстановления ключей WEP/WPA/WPS и проведения других сетевых атак на беспроводные или проводные сети;
-
hcxtools — Решение для захвата сетевого трафика WLAN и преобразования в форматы hashcat и John the Ripper;
-
kismet-deauth-wpa2-handshake-plugin — Плагин Python для Kismet, выполняющий деаутентификацию для сбора рукопожатий WPA2.
-
pyrcrack — Python-реализация Aircrack-ng.
-
pyrit — Известный крекер WPA, перенесенный из Google.
WPS
Да, wps мало где используется по-умолчанию, но не исключено, что Вы когда-нибудь встретите точку с ним.
-
Rever — Предназначен для подборки пина WPS (Wifi Protected Setup) методом перебора (обновляемый форк).
-
pixiewps — Утилита для оффлайн брутфорса WPS-PIN.
-
HT-WPS-Breaker — Инструмент для взлома WPS с поддержкой высоких скоростей (High Touch WPS Breaker).
Атаки на Enterprise
-
eaphammer- ❤️ Фреймворк для атак на WPA2-Enterprise
-
wpa_sycophant — «Злой» клиент, часть атаки ретрансляции EAP
-
extract_EAP — Простой экстрактор сертификатов WiFi EAP
-
crEAP — скрипт для определения типа EAP режима WPA Enterprise и сбора имен пользователей и/или подтверждения связи, если используются небезопасные протоколы.
-
apbleed — Позволяет использовать существующие инструменты для атаки Heartbleed для тестирования сервера RADIUS.
-
IKECrack — Инструмент для брутфорса или словарной атаки на ключ/пароль, используемый в аутентификации IKE/IPSec с предварительно установленным ключом (PSK).
Инъекции
-
Airpwn-ng — Новая и улучшенная версия инструмента airpwn.
Evil twin / Fake AP / MITM
-
fluxion — Инструмент для атак MITM на WPA.
-
wifiphisher — Инструмент для автоматизированных атак фишинга на клиентов Wi-Fi.
-
rogue — Расширяемый набор инструментов, предоставляющий тестировщикам на проникновение простую в использовании платформу для развертывания точек доступа во время тестирования на проникновение и взаимодействия с красной командой.
-
WiFi-Pumpkin3 — Фреймворк для атак с Rogue Wi-Fi Access Point.
Wardriving
-
ESP8266-Wardriving — Скрипты управления ESP8266 и инструменты визуализации данных Jupyter Notebook
Различные иные инструменты
-
airgeddon — Многофункциональный bash-скрипт для аудита беспроводных сетей в Linux.
-
AtEar — Инструмент для анализа беспроводных сетей и аудита их безопасности. (Давно заброшен, но история этого инструмента действительно вдохновляет. Сейчас, это большая компания, а начиналась всё с одного скрипта)
-
Crippled — Генератор ключей по умолчанию для роутеров Belkin.
-
eapeak — Анализ сетей, использующих EAP-аутентификацию, включая беспроводные сети.
-
FruityWiFi — Инструмент для аудита беспроводных сетей.
-
zarp — Инструмент для атак на сети в локальной сети.
Сбор информации
-
3WiFi Database — Собирает данные из отчетов о сканировании маршрутизатора, ищет точки доступа, получает их координаты геолокации и отображает их на мировой карте.
-
access_points — Сканирует беспроводные сети Wi-Fi и предоставляет информацию о точках доступа и качестве сигнала.
-
WIG — Набор инструментов для сбора информации о сетях 802.11 (Wi-Fi).
Защита / Обнаружение
-
badkarma — Простой сценарий Python, используемый для обнаружения и блокировки злонамеренных точек доступа и ловушек с использованием атаки Karma, таких как Wi-Fi Pineapple.
-
EvilAP_Defender — Защита беспроводной сети от фальшивых точек доступа.
-
huntpineapples — Инструмент для поиска и обнаружения Wi-Fi Pineapple в сети.
-
kismetclient — Python-клиент для взаимодействия с сервером Kismet.
-
kismet — Обнаружитель беспроводных сетей, сниффер и система обнаружения вторжений.
-
Openwips-ng — Открытая и модульная система предотвращения вторжений (IPS) для беспроводных сетей.
-
RogueDetection — Обнаружение фальшивых точек доступа и беспроводных систем обнаружения вторжений (WIDS).
-
waidps — Система аудита беспроводных сетей, обнаружения и предотвращения вторжений.
-
Wave — Платформа для обнаружения и анализа беспроводных сетей 802.11 в интерфейсе веб-приложения.
-
Wireless-forensics-framework — Автоматизированный инструмент для проведения аудита безопасности беспроводных сетей и беспроводных форензических исследований с использованием Python.
-
Wireless-ids — Способ обнаружения подозрительной активности, такой как атаки на WEP/WPA/WPS, путем сниффинга беспроводных пакетов.
-
wmd — Простое решение для обнаружения и определения местоположения фальшивых точек доступа.
-
wraith — Инструмент для беспроводной разведки и интеллектуальной сборки информации о целях.
-
wspy — Инструмент на Python для создания системы обнаружения идентификации беспроводных сетей. Позволяет определить, какие клиенты подключены к сети для создания паттернов использования сети.
Мониторинг
-
horst — Легковесный анализатор беспроводных локальных сетей IEEE 802.11 с текстовым интерфейсом. По своим базовым функциям аналогичен инструментам типа tcpdump, Wireshark или Kismet, но имеет небольшой размер и выводит агрегированную информацию, которая не всегда доступна в других инструментах.
Заключение
Список вышел достаточно объемным, но тут далеко не все интсрументы для работы или пентеста Wi-Fi. Это лишь дополнение и удобная структура для использования с основной статьей и я хочу, чтобы вы указали свои инструменты, которые не указаны в списке. Хочу сделать данный пост неким местом, куда пентестер сможет зайти и выбрать то, что ему нужно.
Спасибо за внимание, скоро увидемся в новой статье.
As a cyber security expert, grasping the intricacies of WiFi password hacking softwares opens the door to secured networks and empowers you to navigate the complex realm of cybersecurity with skill and confidence.
In fact, these tools are designed to help you identify vulnerabilities in WiFi networks and exploit them to gain access and should be part of your arsenal.
If you’re interested in learning more about WiFi hacking, this article is for you. We’ll begin by discussing it and then show you different tools to help you accomplish your goal.
We’ve also created a list of 12 tools, each with a description, their benefits, and whether or not they’re included in Kali Linux.
If you’re ready to jump in, let’s begin.
Table Of Contents
- About WiFi Hacking
- Top Free WiFi Password Hacking Softwares
- Aircrack-NG
- CoWPAtty
- Reaver
- Fern WiFi Cracker
- Wifite
- Kismet
- Airgeddon
- Fluxion
- Wifiphisher
- WiFipumpkin
- Bettercap
- Hashcat
- Conclusion
- Frequently Asked Questions
About WiFi Hacking
Before we start looking into the available WiFi hacking tools, let’s quickly discuss what WiFi hacking is.
WiFi hacking includes technical attacks like “Man-in-the-Middle,” where an attacker captures traffic to obtain the pre-shared key and then crack the password, and social engineering attacks like the “Evil Twin” attack.
In an Evil Twin attack, hackers create a rogue WiFi access point that mimics a legitimate one, tricking users into connecting by exploiting their trust in the familiar network name.
While technical attacks require specific tools and knowledge of secure network protocols, social engineering attacks exploit human psychology and negligence.
You’ll also need hardware to perform these types of attacks.
Essential hardware includes a wireless network adapter that supports monitor mode and packet injection, and a hacking OS like Kali Linux will make things easier.
Please note that WiFi hacking without explicit permission, including setting up rogue access points, is illegal under laws like the Computer Fraud and Abuse Act in the U.S., with penalties including fines and imprisonment. See Is Hacking Illegal? The Law and Ethical Perspectives for more information.
Now that we’ve discussed WiFi hacking, let’s look at some WiFi hacking tools.
Aircrack-NG

Aircrack-ng is a popular collection of tools known for its efficiency in cracking WEP and WPA/WPA2 protocols. These tools are designed to assess the security of various wireless environments. They enable you to easily capture data packets, monitor networks, and crack weak passwords, making them an important toolkit for ethical hackers and penetration testers. See How to Use Aircrack-ng: A Guide to Network Compromise.
Benefits of Aircrack-NG
Includes everything from packet sniffers to encryption key crackers.
Runs on various operating systems, including Linux, Windows, and macOS.
It’s relatively easy to use with good documentation.
- Included with Kali.
CoWPAtty

CoWPAtty is a tool designed primarily for cracking WPA-PSK (pre-shared key) and WPA2-PSK passwords using dictionary attacks. It leverages the captured network traffic to perform an offline attack, testing each entry in the wordlist against the hash.
Benefits of CoWPAtty
Its command-line nature makes deploying and running it from any system easy.
It supports the use of a precomputed hash file.
CoWPAtty is optimized for conducting dictionary attacks.
- Install with the command:
sudo apt install cowpatty
Reaver

Reaver is a powerful tool for recovering WPA/WPA2 passphrases by targeting Wi-Fi Protected Setup (WPS) protocol vulnerabilities. It exploits a flaw in the WPS PIN feature, an eight-digit number used to add new devices to a wireless network without entering the passphrase.
Benefits of Reaver
Despite its powerful capabilities, Reaver is easy to use.
It can recover the WPS PIN and the WPA/WPA2 passphrase in hours.
Reaver is exceptionally effective at exploiting the WPS PIN vulnerability.
- Included with Kali
Fern WiFi Cracker

Fern Wifi Cracker is a wireless auditing and attack tool designed to analyze and crack Wi-Fi passwords. It provides a user-friendly graphical user interface (GUI). It’s mainly employed to discover vulnerabilities in wireless networks and can handle WEP, WPA, and WPA2 protocols.
Benefits of Fern WiFi Cracker
The GUI is intuitive, making it accessible for beginners and experienced users.
It integrates various third-party tools and scripts, enhancing its functionality.
It includes session hijacking features, allowing you to capture and use session cookies.
You can monitor and audit networks in real time.
- Included with Kali
Wifite

Wifite is a popular tool for automating wireless network security testing among penetration testers. It’s designed to simplify the execution of numerous wireless attacks. Read our How to Use Wifite: Best WiFi Hacking Tutorial to learn more.
Benefits of Wifite
Wifite automates several steps in the attack process, such as capturing handshakes and cracking passwords.
It supports a variety of attacks against WEP, WPA, and WPA2.
Wifite is designed to be easy to use.
Wifite combines features from multiple well-known tools under a single interface.
- Included with Kali
Kismet

Kismet supports many technologies beyond Wi-Fi, including Bluetooth, Zigbee, RF, and more. It functions as a sniffer, a wireless intrusion detection system (WIDS), and even a tool for wardriving. It runs on multiple platforms, including Linux and macOS.
Benefits of Kismet
Can monitor a wide array of devices and frequencies.
Active community engagement.
A REST API for advanced scripting.
Captures data not just on Wi-Fi with the right hardware.
- Included with Kali
Airgeddon

Airgeddon is a multi-use toolkit for auditing wireless networks. It’s a bash-scripted utility that provides an all-in-one platform for WiFi hacking. It integrates with several third-party tools, such as Aircrack-ng. Read our tutorial Evil Twin WiFi Attack: A Step-By-Step Guide to see Airgeddon in use.
Benefits of Airgeddon
Combines a variety of network auditing tools into a single framework.
Intuitive menu system that guides you through various tasks.
It works with a wide range of wireless network adapters.
Supports plugins, allowing you to extend its functionality.
- Included with Kali
Fluxion

Fluxion is a tool designed to audit the security of wireless networks through social engineering. It’s a remake of Linset with improvements in stability and functionality. The tool sets up a series of attacks to deceive users into providing their WiFi passwords on a captive portal.
Benefits of Fluxion
You can customize the phishing pages to resemble the login page of the target network.
By leveraging social engineering, Fluxion gathers credentials without the need for brute-forcing.
Combines several techniques to provide a realistic test of how actual attackers could exploit the network.
- Needs to be installed. See official GitHub for instructions.
Wifiphisher

Wifiphisher is a rogue access point framework for conducting sophisticated WiFi attacks and red team engagements. By setting up fake access points it enables the interception and manipulation of wireless communications. It’s particularly effective in simulating phishing attacks to capture sensitive information like WiFi passwords and credentials or even deploy malware.
Benefits of Wifiphisher
Its intuitive textual user interface guides you through setting up and executing attacks.
Easily gains MITM position using techniques such as Evil Twin, KARMA, and Known Beacons.
Comes with a variety of phishing templates that can be tailored for specific scenarios.
Incorporates the latest research in WiFi phishing and is constantly updated by developers.
- Install with the command:
sudo apt install wifiphisher
WiFipumpkin

Wifipumpkin3 is an interactive command line interface framework for red teamers and reverse engineers. It allows you to establish rogue access points to facilitate man-in-the-middle (MITM) attacks. Written in Python, it offers features that support versatile wireless attacks.
Benefits of WiFipumpkin
It supports various attacks, including rogue access points, MITM attacks, credential harvesting, and even multifactor authentication (MFA) phishing.
Includes modules for de-authentication attacks, a rogue DNS server, and tools like EvilQR3 for QR code phishing.
Offers tools to intercept, inspect, modify, and replay web traffic.
- Install with the command:
sudo apt install wifipumpkin3
Bettercap

Bettercap is a powerful network attack and monitoring framework that can be used for WiFi hacking. It provides a comprehensive suite of tools and capabilities tailored to perform deauth attacks to capture the four-way handshake or create rogue access points. See our Bettercap Tutorial & Top Commands.
Benefits of Bettercap
Ability to harvest credentials transmitted over WiFi networks.
Supports man-in-the-middle (MITM) attacks.
Can create rogue access points.
- Install with the command:
sudo apt install bettercap
Hashcat

Hashcat is a powerful password-cracking tool that can crack hashed passwords, including those used in WiFi networks. It leverages the computational power of modern GPUs to perform high-speed password cracking, making it a great tool for WiFi hacking.
Benefits of Hashcat
Uses the parallel processing of GPUs to speed up password cracking.
Supports a wide range of hashing algorithms commonly used in WiFi encryption, including WPA/WPA2-PSK (pre-shared key), WPA-Enterprise, and WPA2-Enterprise.
Offers various attack modes, such as dictionary attacks, brute-force attacks, and rule-based attacks.
- Installed with Kali
Conclusion
With our list of WiFi password hacking softwares, you have the necessary tools to test the security of your network and protect it from potential threats.
We recommend you test out these tools in a practice lab where you can become familiar with how they work and the various features they offer.
If you’re eager to learn more about WiFi hacking or hacking in general, join the StationX Accelerator program. We offer you courses, labs, mentorships, and much more.
Frequently Asked Questions
Do I need special hardware to hack WiFi?
Yes, you need specialized hardware and software. These include a wireless network adapter capable of packet injection and monitor mode and an operating system that can run the necessary tools for performing wireless attacks, such as Kali Linux or Parrot OS.
Is hacking WiFi illegal?
Yes, hacking WiFi networks is generally illegal if you don’t have explicit permission from the network owner or administrator. Illegally accessing wireless networks can be considered a form of computer fraud or abuse, a crime punishable by law in most jurisdictions. Only hack WiFi networks as part of an authorized pentest with permission from the owner. See Is Hacking Illegal? The Law and Ethical Perspectives for more information.
What is an evil twin attack?
An evil twin attack is when an attacker sets up a wireless access point that mimics a legitimate wireless network’s name (SSID) and configuration. They do this to lure users to connect to the fake access point instead of the real one. Once a victim connects to the evil twin network, the attacker can intercept (sniff) and potentially manipulate the victim’s network traffic. For a more detailed look at this, see Evil Twin WiFi Attack: A Step-By-Step Guide.
Can Kali Linux crack WiFi?
Kali cannot crack WiFi by itself, although it does include tools capable of cracking the WiFi handshake, including Aircrack-ng, Wifite, Hashcat, and others.
-
Richard is a cyber security enthusiast, eJPT, and ICCA who loves discovering new topics and never stops learning. In his home lab, he’s always working on sharpening his offensive cyber security skills. He shares helpful advice through easy-to-understand blog posts that offer practical support for everyone. Additionally, Richard is dedicated to raising awareness for mental health. You can find Richard on LinkedIn, or to see his other projects, visit his Linktree.
In today’s world, Wi-Fi or internet connectivity has become an essential part of our lives. It is almost impossible to survive without it. But, what if you are in a place where Wi-Fi is not accessible? In such cases, you might be tempted to crack Wi-Fi passwords, but that’s not the right way to go about it. Windows operating systems are not designed for hacking purposes, unlike Linux, which is open source and provides a wide variety of tools for hackers and penetration testers.

So, if you want to crack Wi-Fi passwords, which operating system should you use? Both Linux and Windows can be used, but Linux is preferred due to its flexibility and range of tools. However, many people find Linux difficult to use, and they give up quickly. If you are one of them, don’t worry! There are windows applications such as Dumpper and JumpStart that can help you crack WPA/WPA2 WPS enabled networks. These applications can crack WPS pins, allowing you to connect to any WPS enabled network easily. This is one of the easiest and best ways to crack Wi-Fi WPA/WPA2 WPS enabled routers. Additionally, if you want to try hacking through your Android mobile, there is a simple method that can help you crack Wi-Fi WPA WPS enabled networks in just 2 minutes.. Refer to Hacking Wifi using your android mobiles
easily in 2 mins
THIS IS MERELY CREATED FOR EDUCATIONAL & ETHICAL PURPOSE, AUTHOR IS NOT RESPONSIBLE FOR ANY ILLEGAL ACTIVITIES DONE BY THE VISITORS
THIS IS MERELY CREATED FOR EDUCATIONAL & ETHICAL PURPOSE, AUTHOR IS NOT RESPONSIBLE FOR ANY ILLEGAL ACTIVITIES DONE BY THE VISITORS
What is WPA/WPA2
Wi-Fi Protected
Access (WPA) and Wi-Fi Protected Access II (WPA2) are
two security protocols and security certification programs developed by
the Wi-Fi Alliance to secure wireless computer networks. The Alliance
defined these in response to serious weaknesses researchers had found in the
previous system, WEP (Wired Equivalent Privacy).
A flaw in a feature added to Wi-Fi,
called Wi-Fi Protected Setup, allows WPA and WPA2 security to be bypassed
and effectively broken in many situations. WPA and WPA2 security implemented without using the Wi-Fi
Protected Setup feature are unaffected by the security vulnerability.
WPA2 has
replaced WPA. WPA2, which requires testing and certification by the Wi-Fi
Alliance, implements the mandatory elements of IEEE 802.11i. In particular, it
includes mandatory support for CCMP, an AES-based encryption mode
with strong security. Certification began in September, 2004; from March
13, 2006, WPA2 certification is mandatory for all new devices to bear the Wi-Fi
trademark.
What Is WPS
Wi-Fi Protected
Setup (WPS; originally Wi-Fi Simple Config) is a
network security standard that attempts to allow users to easily secure a wireless home network but could fall
to brute-force attacks if one or more of the network’s access points do not guard against
the attack.
Limitations
1. This Hack works on Wpa/Wpa2 – Wps
Unlocked Networks only
2. Does not work on all Routers & all
encryption’s, so cannot hack all the wifi networks Available near you. At least
this method can’t.
3. Not all Networks or routers can be
hacked using this method.
4. While hacking some networks it says
«Wireless Configuration Failed » that means jumpstart (the software
that we are going to use to hack wifi password) cannot hack that network.
There are many people wondering about
hacking wifi networks. So, here is a simple tutorial on How to hack wifi Wpa
and Wpa2 security through Windows using dumpper and Jumpstart
Requirements:
1)
Laptop
or USB wifi Adapter
2)
Windows Operating System
7)
Wpa/Wpa2 – WPS Networks Available with at least 8% signal
Links to Download the Required Software’s
2)
Download JumpStart
4) Download Dumpper
Install all the applications in the order given above to avoid any unnecessary
errors. Download and Install all the above
given Applications one by one, even If a single software installation is missed
(Except Dumpper), lot of errors might occur which might disable the
functionality of other software that might result in failure of hack. Be careful
while downloading and installing these software’s.
Tutorial on Hacking Wifi WPA/WAP2 — WPS in Windows Using JumpStart and Dumpper
Tutorial To Hack Wifi WPA/WPA 2 — WPS Networks
1) After
Downloading and Installing all the applications — Open Dumpper (No need of
Installing Dumper, Just run Dumpper when ever you want to try out this hack)
2) Select your Network
Adapter and click ”Scan”. All the
available networks around will be shown below

3) You can see all the available Networks, Move to «WPS» tab and click «Scan»

4) Select «All Networks«

5) click on ”Scan”

6) Select your «Network» that you want to hack

7) Click on «JumpStart» after selecting the network that you want to hack



9) Jumpstart tries to «Associate with the network» and runs few command on the target router trying to get details from it.

10) In just few mins, you can see that you are already connected to the network that you are trying to hack.

11) Click on «Profiles» to see the passwords of all the networks that you connected to already at least once.

12) Click on Any Profile or network name (SSID) to view the details of the networks along with the password and the encryption which the network uses.


13) You can check the passwords of the connected networked using different ways, here is one without using any tools or applications or without running any commands.

14) Click on «Open Network and Sharing Center»
.png)
15) Click on your «Router Name» (SSID)

16) In the «General» tab click on «Wireless Properties«

17) Move to «Security» tab.

18) In Security Tab, check the «Show Character» button, then you can see «Network Security Key» which is the password of the router that you are connected to.
Note: If you are logged into the system as a Limited user; you might be prompted to enter your system password.
If you are Stuck anywhere
in the process of hacking wifi, feel free to comment below, i will try to help
you solve your problem. Before that please check Frequently asked questions.
you might find the answer you are looking for.
Frequently Asked Questions:
1) Does This method work??
Yes, it works, but not on all
kinds of networks and routers. As i mentioned in the above article using
jumpstart, you can hack only wifi routers secured with wpa/wpa2 — wps enabled
2) Jumpstart shows Wireless configuration
failed! what could be the reason for it not to be successful?
Same answer as
above, because it is not programmed to hack routers that are already patched of
this vulnerability. To put it into simple words, router is much stronger than
the attack
3) Hacking with JumpStart Failed, how should i hack this
particular network now??
Not all Hacks
on first try, you need to do a lot of digging before you are trying to hack
something, Same goes for wifi networks as well. Hacking is not easy at all.
There are many other methods to hack wifi, but there are not many methods that
work on all kinds of networks or devices. As this is the very basic way of
hacking, we need to go into a little more advanced techniques of wifi hacking
like Evil twin Attack. Refer This Article
4) Networks Found in Wifi Tab but nothing in WPS Tab, what
should i do not ?
Ans: This is neither your fault or Dumpper’s or the system’s fault. This
happened because there are no WPS enabled networks near you. Dumpper and
Jumpstart cannot hack the networks with wps disabled. so you need to go for
another method of wifi hacking, which means you need to work a little on Kali
Linux to hack the network, even though its not as easy as Dumpper. Click here To read what to do if Dumpper
doesnt work.
In case Jumpstart Failed to hack the router try the following (Hacking With Linux)
If you are not able to understand which
method to select, here is complete tutorial on Wifi Hacking, which explains the process of
choosing the method to hack any kind of router. which can be easily understood
by beginners. Follow this article, once you scroll down a little you can find
all the methods, usage and the method selection for hacking any kind of
router.
Refer To:
Internet is now a basic requirement of our daily life be it office or home. As a result, the Wi-Fi router and data connection have become a fundamental amenity for every user.
People also use wireless routers in their home network to connect all devices. However, using Wi-Fi could make your network visible to the neighborhood who may want to use it for free.
Similarly, big organizations that use Wi-Fi may want to keep a check on how the network is being utilized by its employees.
Although the wireless networks are secured with a password key, there are many Wifi hacking tools available that allow one to crack the password of any Wi-Fi protected with WAP, WAP2, and WPS protocol.
Suggested- Best Hacking Tools For Windows 10
In this article, we provide a list of top Wi-Fi hacking tools that can crack the networks to get you access.
These tools can also be used to recover the lost password of your own Wi-Fi.
Table Of Contents
- Is It Possible To Hack WiFi?
- Top 15 Wi-Fi Hacking Tools
- 1. Aircrack-ng
- 2. WiFi WPS WPA Tester
- 3. Cain & Abel
- 4. Kismet
- 5. AirSnort
- 6. NetStumbler
- 7. Airjack
- 8. inSSIDer
- 9. CoWPAtty
- 10. WepAttack
- 11. Wireshark
- 12. Wifite2
- 13. Wifiphiser
- 14. Rfa
- 15. airgeddon
- Is it Illegal to Hack WIFI?
Is It Possible To Hack WiFi?
Yes, it’s possible to hack WiFi using certain tools and software.
You can even hack WiFi using an Android smartphone, Windows or Linux PC.
However, hacking and using someone else’s WiFi connection without their consent is illegal in a wide variety of nations. Unauthorized access to a WiFi network is considered a criminal offense in different parts of the world.
Top 15 Wi-Fi Hacking Tools
- Aircrack-ng
- WiFi WPS WPA Tester
- Cain & Abel
- Kismet
- AirSnort
- NetStumbler
- Airjack
- inSSIDer
- CoWPAtty
- WepAttack
- Wireshark
- Wifnite
- Wifiphiser
- Airgeddon
- Rfa
1. Aircrack-ng
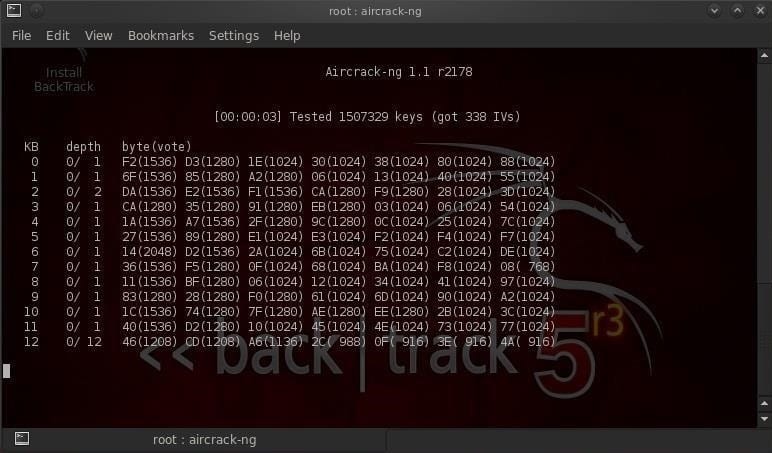
Aircrack-ng is one of the most popular wireless passwords cracking tools, which can help you crack passwords by cracking WEP Keys of Wi-Fi 802.11b network.
Aircrack uses the best algorithms to recover wireless passwords by capturing packets. Once enough packets have been gathered, it tries to recover the password. To make the attack faster, it implements a standard FMS attack with some optimizations.
The company behind the tool also offers an online tutorial where you can learn how to install and use this tool to crack wireless passwords. It comes as Linux distribution, Live CD and VMware image options. You can use any of these. It supports most of the wireless adapters and is almost guaranteed to work.
If you are using a Linux distribution, the only drawback of the tool is that it requires a deeper knowledge of Linux.
When you are not comfortable with Linux, you will find it hard to use this tool. In this case, try Live CD or VMWare image. VMWare Image needs less knowledge, but it only works with a limited set of host OS, and only USB devices are supported.
Before you start using this tool, confirm that the wireless card can inject packets. Then start WEP cracking. Read the online tutorial on the website to know more about the tool. If you will follow steps properly, you will end up getting success with this tool.
2. WiFi WPS WPA Tester
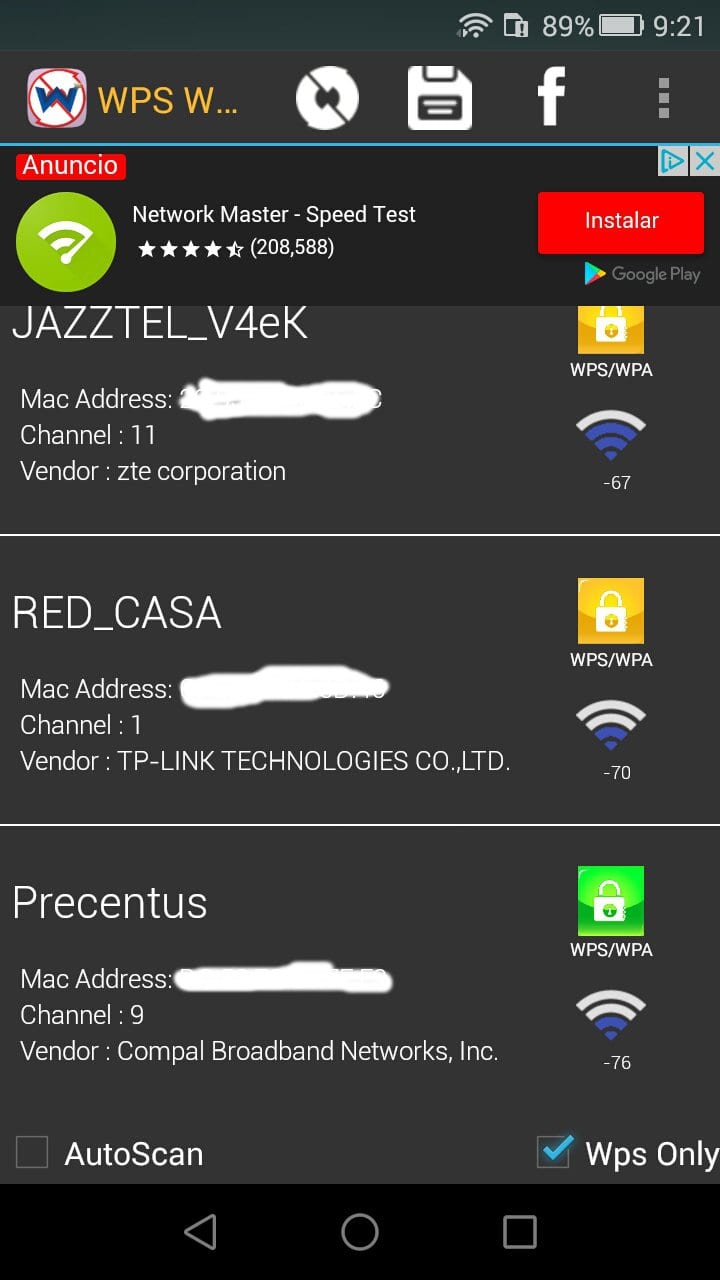
WPA WPS Tester is one of the most popular Wi-Fi password hacker tools known for breaking the security and works on both rooted and Android devices. This app tests the connection to Access Points with WPS PIN and needs Android 4.0 and up for running.
It relies on several algorithms involving MAC addresses and the inbuilt database to calculate the pins. You will need root permissions to realize its full potential.
3. Cain & Abel
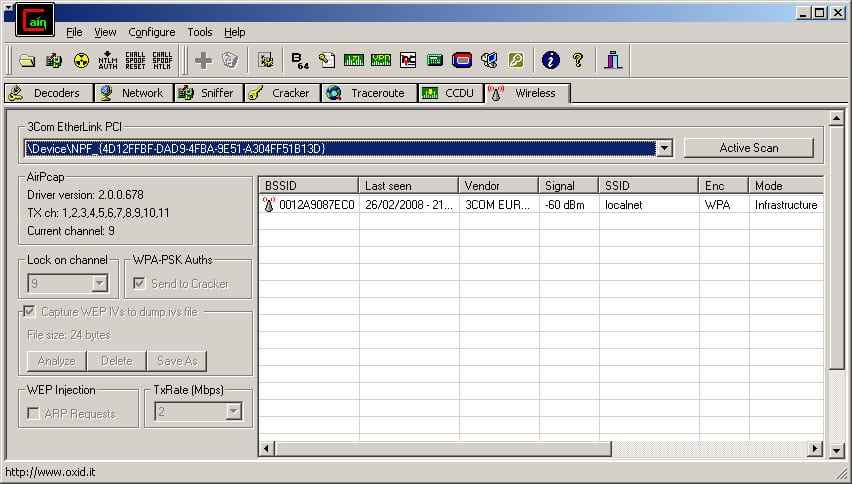
Cain & Abel is a popular password cracking tool developed to intercept network traffic and then discover passwords by brute-forcing them using cryptanalysis attack methods.
It can also recover wireless network keys by analyzing routing protocols. If you are trying to learn wireless security and password cracking, you should once try this tool.
The last official update of the hacking tool was around seven years ago. Its active development has been stopped as the developers have moved on to other things in life.
4. Kismet
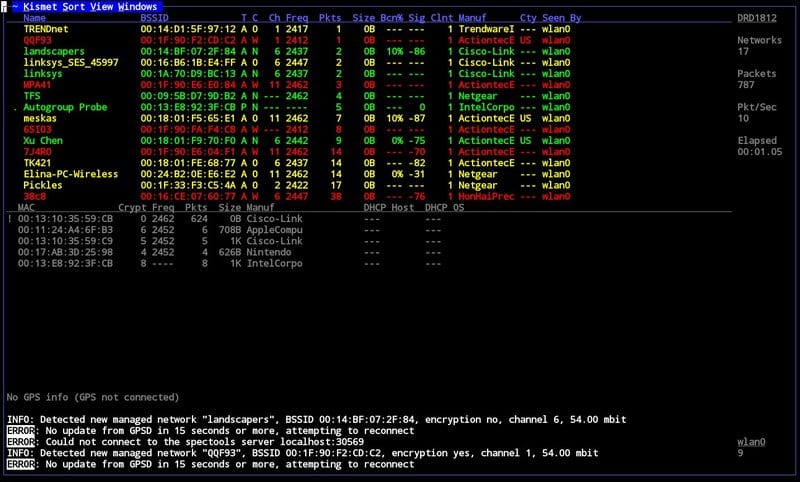
Kismet is a packet sniffer, network detector and intrusion detection system for 802.11 wireless local area networks. It works with any Wi-Fi card, which supports rfmon mode, Bluetooth interfaces, a few of the SDR(Software Defined Radio), and other hardware like RTLDSR, along with several of the capture hardware.
It passively collects packets to identify networks and detect hidden networks. It can also sniff 802.11a, 802.11b, 802.11g, and 802.11n traffic. It is built on client/server modular architecture. It is available for Linux, OSX, Windows and BSD platforms.
With their recent update, Kismet now supports plugins that can extend enhance WebUI functionalities and other accompanying features through Javascript.
They have also added “helper” tools that provide extra server functionality through Python scripting.
5. AirSnort
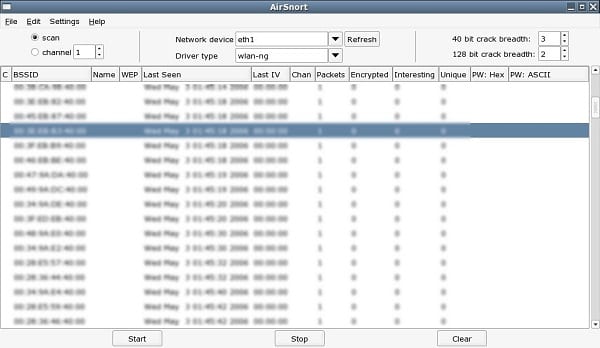
AirSnort is another popular tool for decrypting WEP encryption on a Wi-Fi 802.11b network. It is a free tool and comes with Linux and Windows platforms. This tool is no longer maintained, but it is still available to download from Sourceforge.
AirSnort works by passively monitoring transmissions and computing encryption keys once it has enough packets received. This tool is simple to use and does not require any kind of network expertise. If you are interested, you can try this tool to crack WEP passwords.
6. NetStumbler
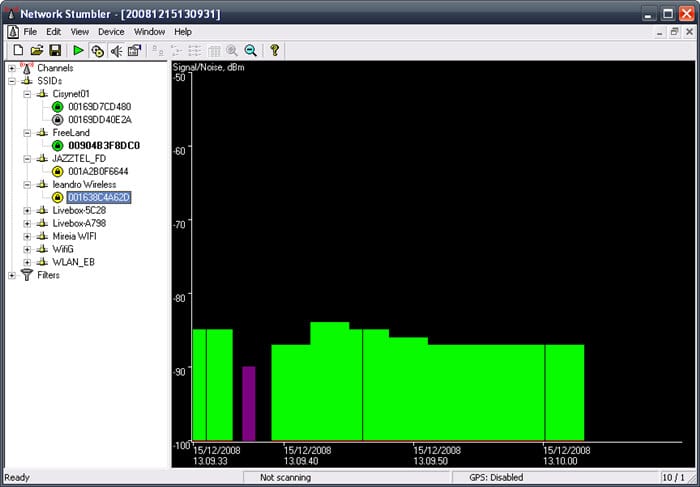
NetStumbler is one of the well-known Windows tools to find open wireless access points. This tool is free and available for Windows.
A trimmed-down version of the tool is also available known as MiniStumbler. Basically, NetStumbler is used for wardriving, verifying network configurations, finding locations with a poor network, detecting unauthorized access points, and more.
The free WIFI hacking tool is no longer being maintained but available for download from the website, whose address is updated after the last earlier one down.
7. Airjack
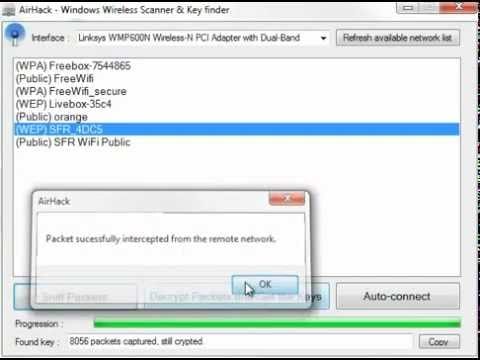
Airjack is a Wi-Fi 802.11 packet injection tool, which is very useful in injecting forged packets and making a network down by denial of service attack. This tool can also be used for a man in the middle attack in the network.
For launching the tool, you will need C installed on your computer. Then unzip the Airjack files and extract them in a folder.
After that, you need to scan for the available WIFI networks and then select the network which you want to intercept.
8. inSSIDer
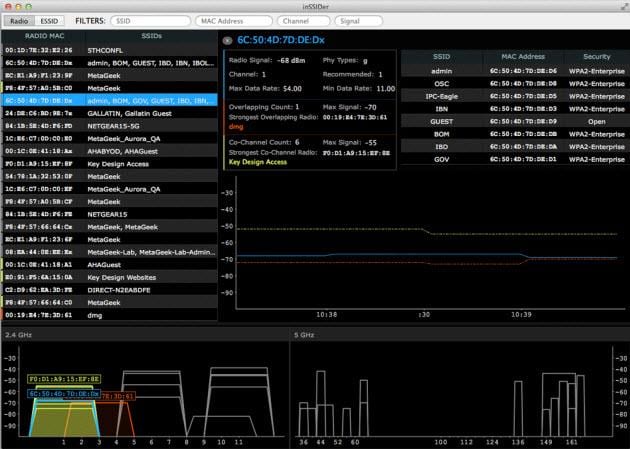
inSSIDer is a wireless network scanner designed to overcome the limitation of another tool, which is NetStumbler. Initially, the tool was open source but now its premuim costs $19.99.
The inSSIDer Wi-Fi scanner can do various tasks, including finding open Wi-Fi access points, tracking signal strength, saving logs with GPS records, collect data from wireless card and software, choose the best wireless channel available and more.
inSSIDER has been acquired by Metageek. You will need to create a free Metageek account in order to log in and use the WIFI hacking tool on your computer.
9. CoWPAtty
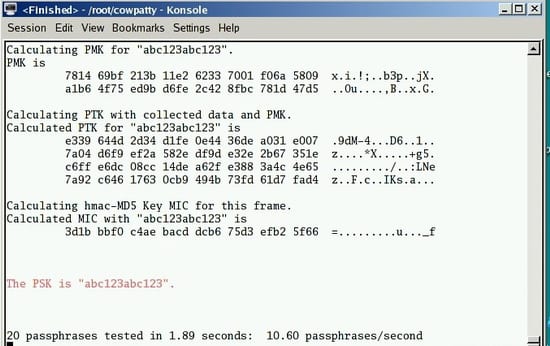
CoWPAtty is an automated dictionary attack tool for WPA-PSK that runs on Linux OS. This program has a command line interface and runs on a word-list that contains the password to use in the attack.
The tool is really simple to use, but it is slow. That’s because the hash uses SHA1 with a seed of SSID. It means the same password will have a different SSIM. So, you cannot simply use the rainbow table against all access points. So, the tool uses the password dictionary and generates the hack for each word contained in the dictionary by using the SSID.
The new version of the tool tried to improve the speed by using a pre-computed hash file. This pre-computed file contains around 172000 dictionary file for around 1000 most popular SSIs. But if your SSID is not in those 1000, you are unlucky.
10. WepAttack
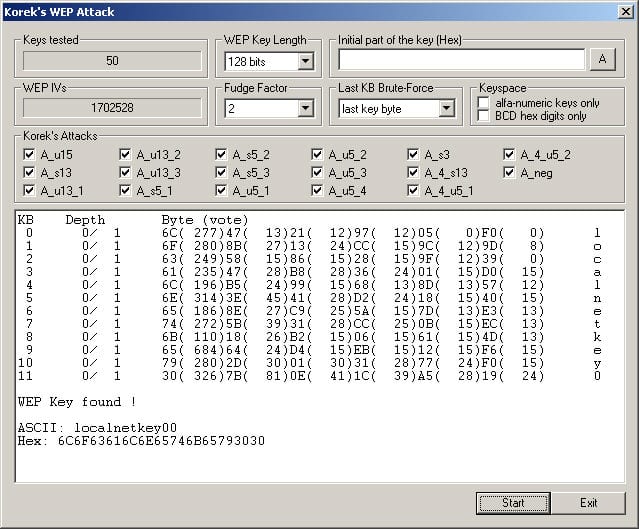
WepAttack is an open-source Linux tool for breaking 802.11 WEP keys. This tool performs an active dictionary attack by testing millions of words to find the working key. Only a working WLAN card is required to work with WepAttack which present on virtually all the computers.
Also Read: Easily Hack WiFi Password Using New WPA/WPA2 flaw
11. Wireshark
Wireshark is a very popular network analyzer that can be used as a WIFI hacking tool. You can take a microscopic look at the network connections without charging a penny like inSSIDER. The network hacking tool was developed by hundreds of volunteers for various platforms.
Often when using different tools, we tend to rely on YouTube for finding tutorials. That would not be the case here with their extension knowledgebase tutorials, which include several video guides.
You can head straight to the official YouTube channel to find full-fledged video series on using the tool on different platforms.
Coming to the features, you can deep inspect hundreds of different network protocols. We also get live capture along with offline analysis in various formats such as tcdump, Catapult DCT2000, and Pcap NG, amongst dozens of others.
You can view all the captured data using the GUI or the TTY-mode TShark utility.
12. Wifite2
Wifite2 is the complete re-write of the original Wifite in the Python script for auditing and hacking WIFI networks. It is a Linux-only network tool, available for several distros, designed explicitly for Kali Linux and ParrotSec.
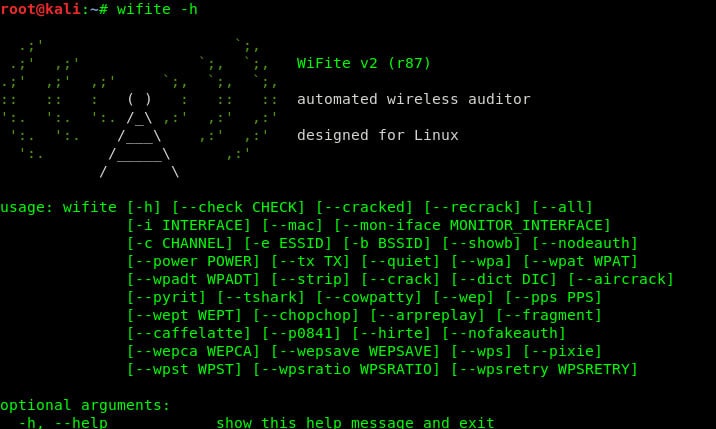
There is no graphical user interface on this network hacking tool. You get a command-line interface and a list of commands to use.
Before going forward, we need to make sure that your device’s wireless network card is capable of “monitor mode.” Aircrack has a tutorial on finding it out on your own. If it is not available, you can go with after-market wireless cards through USB.
You will need Aircrack-ng suite, ifconfig, and iwconfig for Wifite to work. There are several optional tools such as shark, reaver, amongst others, to augment the chances.
This open-source WIFI hacking tool supports 5 GHz networks on a few wireless cards. The support is in its nascent stage, but it’s seeing improvement. It supports the Brute-Force attack in WPS offline and online through Pixie-Dust and Pin Attack.
All the cracked passwords and handshakes are in the current directory.
13. Wifiphiser
Next up, we have a man-in-the-middle attack on a WIFI network. Wifiphiser is a rogue access point network framework that can conduct red team engagements and WIFI penetration testing.
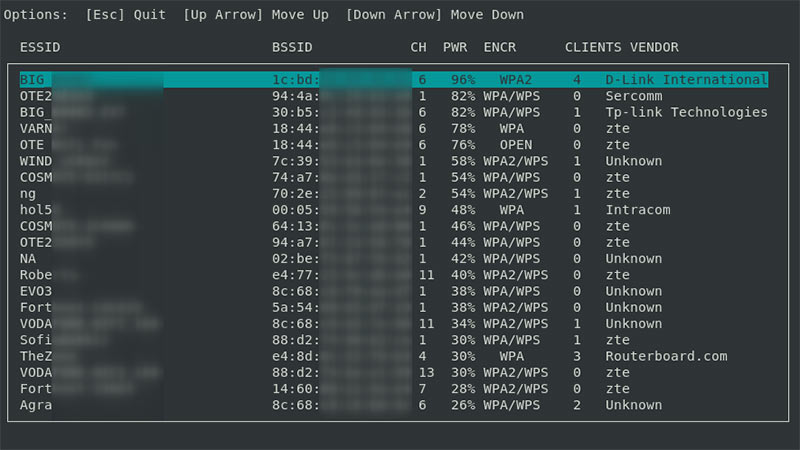
Similar to Wifite, this program is also available exclusively for Linux. You will need a working wireless adaptor with Monitor and AP mode.
Here the WIFI network hack tool can achieve a man-in-the-middle attack position with ease on wireless networks using targeted WIFI-associated attacks.
That is not all, it can run for hours on Raspberry Pi devices while executing the latest techniques such as “Evil Twin,” “KARMA,” and “Known Beacons.”
A plethora of community-driven phishing templates is available with the tool for deployment in different scenarios. Users can also write complicated Python driven scripts to create new phishing scenario templates for conducting target-oriented attacks.
There are several phishing templates of drivers and router firmware updates that are ready to use. You can take a leaf out of the booklet and modify them according to the requirements at hand.
Wifiphisher offers an interactive textual interface, a much-needed relief from the mundane command-line offered by other tools.
State-of-the-art attack methods like “Known Beacons” and “Lure10” along with other phenomenal techniques were introduced by the developers and immediately incorporated into the tool.
14. Rfa
You are out in public, often seeing tons of WIFI networks but password protected. You can use Rfa, a WIFI hacking tool for Android that can brute-force a password-protected WIFI network.
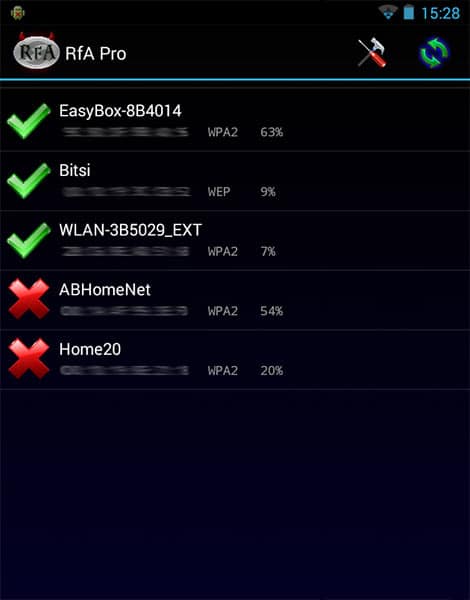
Rfa is essentially Reaver for Android, which is a GUI version of the Reaver tool for the smartphone OS. It comes with monitor mode support.
Recover WPA/WPA2 passphrases/pins and compromise the WPS implementations on any kind of router. Officially takes an average of 4 to 10 hours through the online brute-force method.
In reality, the time is significantly shorter and almost half of the official estimation to guess the WPS pin and get ahold of the passphrase.
On the other hand, using an offline attack may take seconds or a few minutes when the AP is vulnerable.
As a Reaver veteran user, you can rest assured that all the features are available through the GUI. It takes a second to activate/deactivate Monitor mode.
Wait up; it gets even better here. Rfa also supports external scripts, paving the way for additional capabilities. You are not bogged down by the tool’s limitations anymore.
Now that we are done with the features let’s talk installation. You need to install bcmon.apk before going ahead with rfa.apk. The bcmon file can also be downloaded directly when opening the rfa.apk.
15. airgeddon
After a brief pitstop at Android station, we are back to Linux with airgeddon. An actively developing WIFI hacking tool.
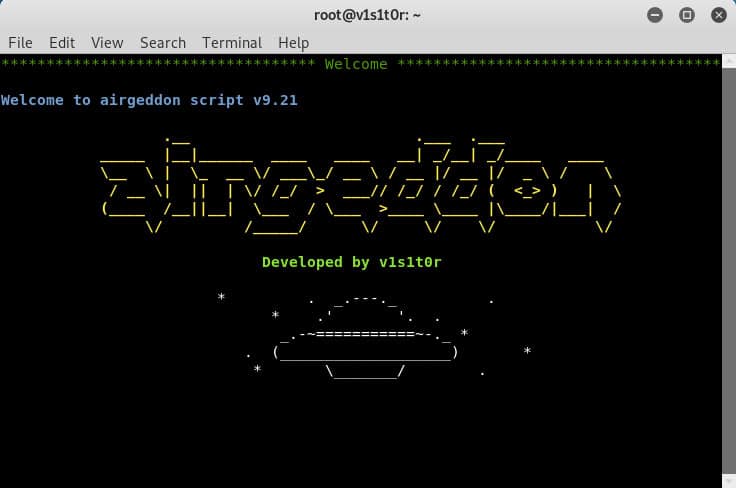
Unlike other network hacking tools, here, we get full support for 2.4 GHz and 5 GHz bands right out of the box. Make sure your device’s wireless network card supports all the required bands.
airgeddon not only captures WPA/WPA2 personal handshake network attacks but cleans the captured files. This makes things a lot easier when dealing with multiple networks.
All the offline password decryption on the captured files of WPA/WPA2 (Handshakes and PMKIDs) rely on dictionary attacks. For rule-based and brute-force attacks, the tool relies on aircrack, hashcat, and crunch tools.
You can also drag and drop files directly into the console window to make inputs and entering file paths easier. This comes with an auto-sizing console window that detects the resolution on its own and adjusts accordingly.
The WIFI hacking tool also offers quick deployments and implementation through using the docker image. You can either use the already built image on the Docker hub or create your own.
Thanks to the auto-updating, we also don’t have to worry about having the latest versions. It will upgrade to the latest available versions from the servers in the background.
Saving the best for the last, we also have access to the plugin system. Based on the hook system, users can create their custom plugins for adding new functionalities to the hacking tool.
Is it Illegal to Hack WIFI?
Hacking or accessing someone’s WIFI to use the Internet without consent is a crime in virtually every part of the world. It is treated as a misdemeanor in most cases unless you are attempting to hijack a person’s network for snooping on emails, web activity, and more.
You can check with a legal expert on the prevailing law in your region to understand the extent of criminal wrongdoing in accordance with the regulations.
Disclaimer – Techworm.net or the author of this article does not condone hacking, hijacking, or any illegal activity in any capacity. The article is intended for educational purposes for spreading the ethical usage of the tools for securing the network.
Over to You
We discussed some of the best WIFI hacking tools to hack any WIFI and use the Internet. In addition to the above mentioned apps and tools there are several other tools that can be used to hack a Wi-Fi network.
