Платформа Windows Server остается одной из наиболее популярных серверных платформ, в том числе и для реализации решений удаленного доступа. Служба маршрутизации и удаленного доступа (RRAS) позволяет быстро и достаточно просто развернуть VPN-сервер практически для любых нужд. Сегодня мы еще раз вернемся к этому вопросу и рассмотрим, как создать на базе Windows Server PPTP или L2TP сервер для удаленного доступа, как наиболее востребованный сценарий на сегодняшний день.
Онлайн-курс по устройству компьютерных сетей
На углубленном курсе «Архитектура современных компьютерных сетей» вы с нуля научитесь работать с Wireshark и «под микроскопом» изучите работу сетевых протоколов. На протяжении курса надо будет выполнить более пятидесяти лабораторных работ в Wireshark.
Почему именно эти типы подключения? Потому что они наиболее просты в реализации и поддерживаются широким спектром клиентов что называется «из коробки». Однако следует помнить, что PPTP не является на сегодняшний день безопасным и имеет слабые алгоритмы шифрования, но при этом он наиболее производительный из VPN-протоколов и имеет минимальные накладные расходы. Кроме того, его поддержка исключена из операционных систем Apple.
Оптимальным вариантом будет использование L2TP/IPsec подключения, которое сочетает в себе простоту, поддержку практически любыми клиентскими ОС и устройствами вместе с неплохим уровнем безопасности, обеспечиваемым IPsec. А так как настройка сервера для этих видов подключений практически идентична, то мы решили объединить их в одну статью.
Установка и настройка службы маршрутизации и удаленного доступа
Для начала работы с VPN в среде Windows Server вам потребуется установить роль Удаленный доступ, это делается стандартными средствами и не должно вызвать затруднений.
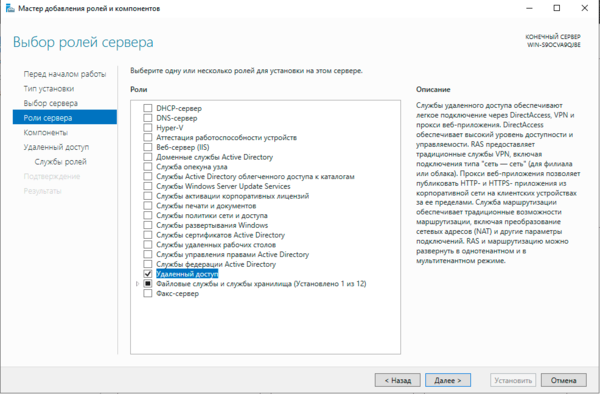
В Службах ролей выбираем Маршрутизация, роль DirectAccess и VPN (RAS) будет добавлена автоматически.
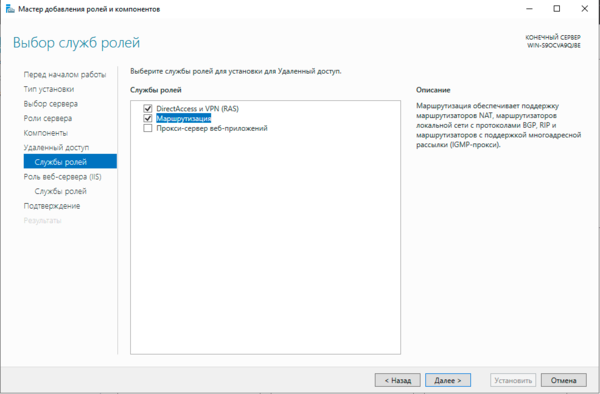
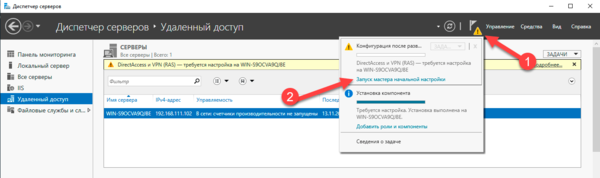
После установки роли Удаленный доступ ее следует настроить, проще всего это сделать, нажав на значок с желтым треугольником в Диспетчере серверов и выбрать в появившемся списке пункт Запуск мастера начальной настройки.
В появившемся окне выбираем пункт Развернуть только VPN.

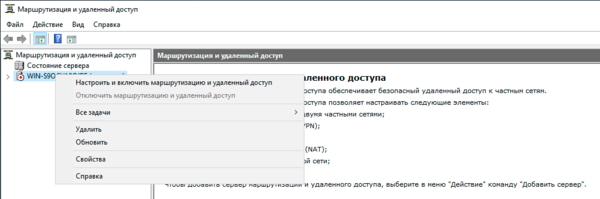
Затем в оснастке Маршрутизация и удаленный доступ щелкаем правой кнопкой мыши по строке с сервером и выбираем в выпадающем меню Настроить и включить маршрутизацию и удаленный доступ.
После чего появится хорошо знакомое окно мастера настройки, предлагающее сразу несколько типовых конфигураций, однако у него есть свои особенности, например, если у вашего сервера всего один сетевой интерфейс, то настроить вариант Удаленный доступ (VPN или модем) мастер вам не даст. Поэтому выбираем самый нижний пункт — Особая конфигурация.
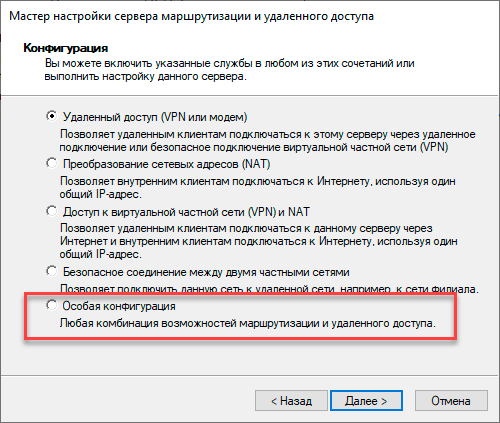
В следующем окне достаточно поставить галочку Доступ к виртуальной частной сети (VPN) и завершить работу мастера.
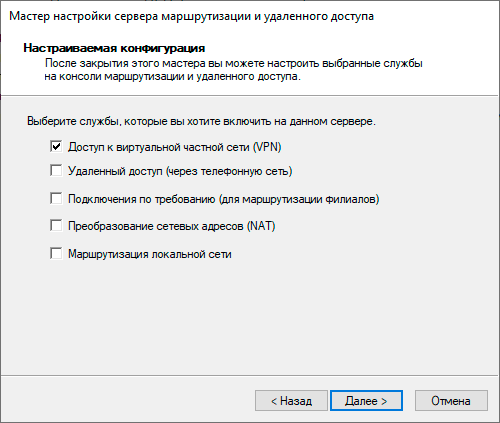
После завершения работы мастера служба Маршрутизации и удаленного доступа будет запущена и можно приступить к настройке сервера удаленного доступа. Если же данная служба у вас уже установлена и настроена в иной конфигурации, то щелкните правой кнопкой по строке сервера и выберите Свойства, в открывшемся окне на закладке Общие установите опции: IPv4-маршрутизатор локальной сети и вызова по требованию и IPv4-сервер удаленного доступа.
Настройка PPTP и/или L2TP сервера удаленного доступа
Откроем оснастку Маршрутизация и удаленный доступ и перейдем к свойствам сервера через одноименный пункт в меню правой кнопки мыши, прежде всего убедимся, что настройки на закладке Общие соответствуют приведенным на скриншоте выше. Затем переключимся на закладку Безопасность и убедимся, что в качестве Поставщика службы проверки подлинности стоит Windows — проверка подлинности, а Поставщик учета — Windows-учет, еще ниже установим флаг Разрешить пользовательские политики IPsec для L2TP- и IKEv2-подключения и в поле Общий ключ укажите парольную фразу для предварительного ключа.
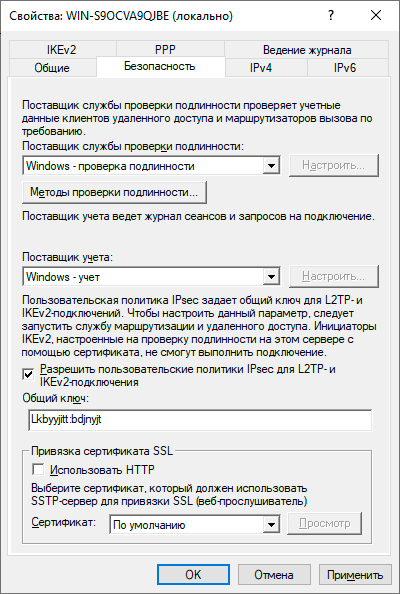
Нажав на кнопку Методы проверки подлинности откроем окно, в котором выберем только Протокол EAP и Шифрованная проверка (Microsoft, версия 2, MS-CHAP v2), остальные протоколы не являются безопасными и должны быть отключены.
На закладке IPv4 укажем опцию Назначение IPv4-адресов — Статический пул адресов и добавим новый пул для выдачи адресов из него удаленным клиентам. Количество адресов должно быть не менее количества клиентов плюс один адрес, так как первый адрес из пула присваивается серверу. Что касается самого диапазона адресов, то его выбор зависит от конфигурации сети, если вы будете использовать маршрутизацию, то он не должен пересекаться с локальной сетью, если же хотите использовать ProxyARP, то наоборот, должны выделить принадлежащий локальной сети диапазон. В нашем случае используется второй вариант.

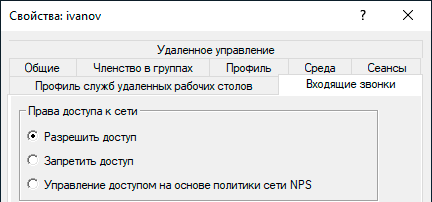
На этом настройка сервера может считаться законченной, следующим шагом следует разрешить подключения нужным пользователям, для этого в свойствах пользователя перейдем на закладку Входящие звонки и в блоке Права доступа к сети укажем Разрешить доступ. Теперь указанный пользователь может подключаться к нашему серверу используя свои учетные данные.
Также не забудьте проверить настройки брандмауэра, чтобы убедиться, что правила Маршрутизация и удаленный доступ GRE-входящий, PPTP-входящий (для PPTP) и L2TP-входящий (для L2TP) включены.
Proxy ARP
Сетевое взаимодействие в пределах одной IP-сети осуществляется на канальном (L2) уровне, в сетях Ethernet для этого используются MAC-адреса устройств. Для того, чтобы выяснить MAC-адрес узла по его IP применяется протокол ARP (Address Resolution Protocol), использующий широковещательные запросы, на которые отвечает только обладатель указанного IP-адреса. Выдавая удаленным клиентам адреса из диапазона основной сети мы как бы помещаем их в общую IP-сеть, но так как VPN — это соединение точка-точка, ARP-запросы от удаленных клиентов в сеть попадать не будут, единственный узел который их получит — сам VPN-сервер.
Для решения данной проблемы используется технология Proxy ARP, которая, как понятно из названия, представляет прокси-сервер для ARP-запросов, позволяя удаленным клиентам работать так, как будто бы они действительно находились в одной сети, без каких-либо дополнительных настроек. При использовании RRAS никаких дополнительных действий делать не нужно, Proxy ARP работает по умолчанию.
VPN-сервер за NAT
Так как мы используем Windows Server, то с большой долей вероятности он будет находиться внутри сетевого периметра и нам понадобится настроить проброс портов на маршрутизаторе. Для этого нужно четко понимать, как работает VPN-соединение и какие порты и протоколы следует передавать.
Начнем с PPTP, прежде всего клиент устанавливает управляющее TCP-соединение на порт 1723, затем, после успешной аутентификации создается соединение для передачи данных с использованием протокола GRE.
Таким образом для работы PPTP-сервера за NAT нужно:
- пробросить порт 1723 TCP
- разрешить прохождение GRE-трафика
С первым понятно, а вот с GRE могут возникнуть затруднения. Если вы используете маршрутизатор на базе Linux, то обратитесь к следующей нашей статье, если оборудование Mikrotik, настроенное по нашей инструкции, то достаточно пробросить только 1723 TCP, прохождение GRE будет разрешено конфигурацией брандмауэра, в остальных случаях следует обратиться к документации на свою модель маршрутизатора.
С L2TP сложнее, точнее не с ним самим, а с IPsec, который не поддерживает NAT. Для обхода этих ограничений используется протокол NAT-T, который инкапсулирует пакеты IPsec в UDP, позволяя успешно проходить через NAT. Поддержка данного протокола включена по умолчанию практически во всех ОС, кроме Windows. Для включения поддержки NAT-T следует внести изменения в реестр, найдите ветку:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\PolicyAgentИ создайте в ней параметр DWORD c именем AssumeUDPEncapsulationContextOnSendRule и значением 2.
Это можно быстро сделать при помощи PowerShell:
Set-ItemProperty -Path "HKLM:SYSTEM\CurrentControlSet\Services\PolicyAgent" -Name "AssumeUDPEncapsulationContextOnSendRule" -Type DWORD -Value 2 -ForceПосле чего систему следует перезагрузить. Данные изменения нужно внести как на сервере, так и на клиенте.
При установлении L2TP/IPsec соединения между узлами прежде всего создается зашифрованный IPsec-канал, для этого используется протокол обмена ключами IKE (порт 500 UDP) и протокол NAT-T (порт 4500 UDP), затем уже внутри безопасного IPsec-соединения поднимается L2TP-туннель на порт 1701 UDP и происходит аутентификация пользователя.
Обратите внимание, аутентификация пользователя в L2TP, в отличии от PPTP, происходит внутри защищенного IPsec-канала, что делает данный тип соединения более безопасным.
Таким образом для работы L2TP/IPsec сервера за NAT нужно:
- пробросить порт 500 UDP
- пробросить порт 4500 UDP
- внести изменения в реестр для включения NAT-T как на сервере, так и на клиенте (только для Windows)
Вопреки распространенному заблуждению порт 1701 UDP пробрасывать не нужно.
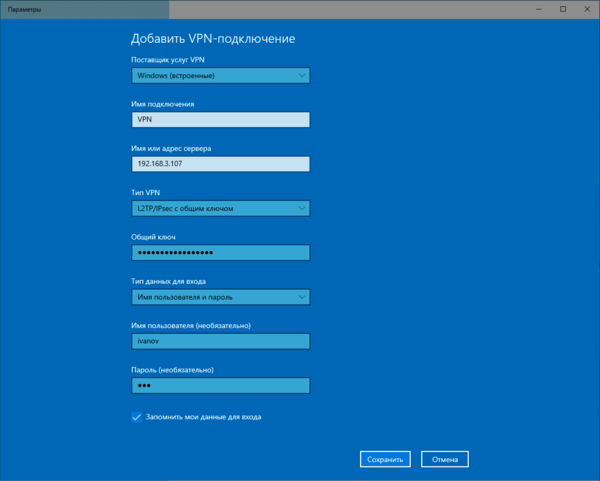
Настройка VPN-подключения в Windows
С одной стороны это простой вопрос, с другой — имеются определенные тонкости, на которые мы как раз и обратим внимание. В Windows 10 для первичной настройки VPN-подключения служит современное приложение, которое предельно простое и не охватывает дополнительных настроек.
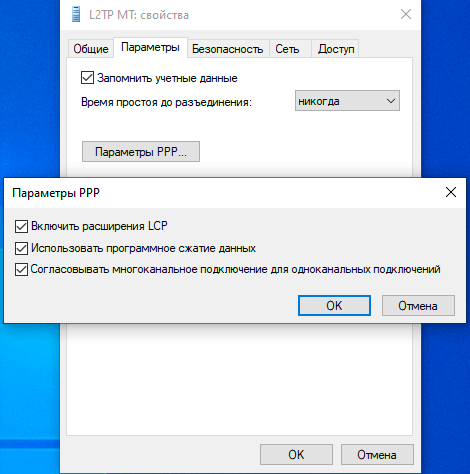
Поэтому после того, как вы создадите в нем подключение, следует перейти к его свойствам и на закладке Параметры — Параметры PPP установить в открывшемся окне все флажки. Это позволит использовать все возможности протокола PPP и получить оптимальное качество связи. Обратите внимание, что данные опции должны также поддерживаться со стороны сервера, в противном случае их использование в одностороннем порядке может привести к ошибкам при установлении связи.
Затем на закладке Безопасность установите в Шифрование данных — обязательное, а в пункте Проверка подлинности выберите Протокол расширенной проверки подлинности (EAP).
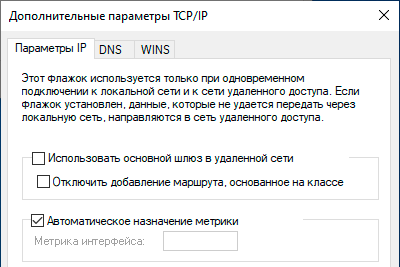
И наконец на закладке Сеть перейдите в свойства протокола IP версии 4 (TCP/IP 4) и нажмите Дополнительно, в открывшемся окне снимите флаг Использовать основной шлюз в удаленной сети, в противном случае весь исходящий трафик будет направлен в туннель.
После чего можем подключаться и пробовать получить доступ к ресурсам удаленной сети, если вы все сделали правильно, то проблем возникнуть не должно.
Настройка VPN-подключения в Linux
В данной части нашего материала мы будем рассматривать настройку клиентских Linux-систем при помощи графического окружения и Network Manager, настройка серверных систем выходит за рамки текущей статьи. В качестве примера мы будем использовать Ubuntu, но все сказанное будет справедливо для любых основанных на Debian систем, а с некоторыми уточнениями — для любых дистрибутивов.
Поддержка PPTP присутствует практически в любом дистрибутиве по умолчанию. Достаточно перейти в Настройки — Сеть и добавить новое VPN-подключение.
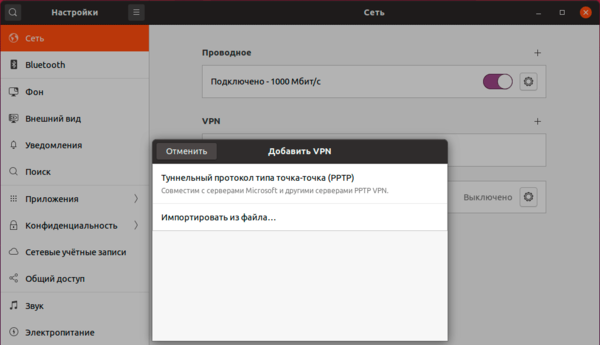
Заполняем основные настройки: адрес сервера, имя и пароль пользователя.
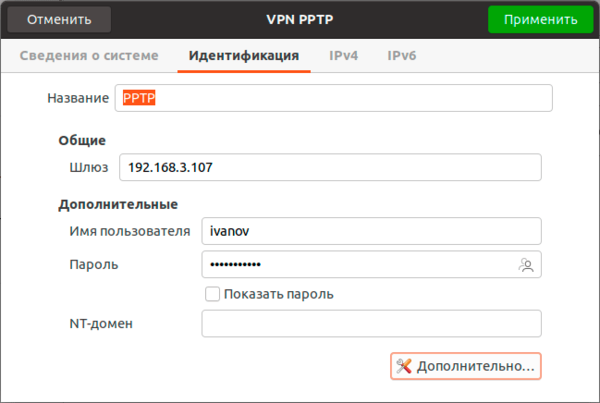
Затем нажимаем кнопку Дополнительно и в открывшемся окне в разделе Аутентификация оставляем только MSCHAPv2, обязательно включаем Использовать шифрование MPPE и выбираем ниже 128 бит (наиболее защищенное), также устанавливаем флаг Включить Stateful Encryption для уменьшения накладных расходов на шифрование. Флаги сжатия оставляем включенными.
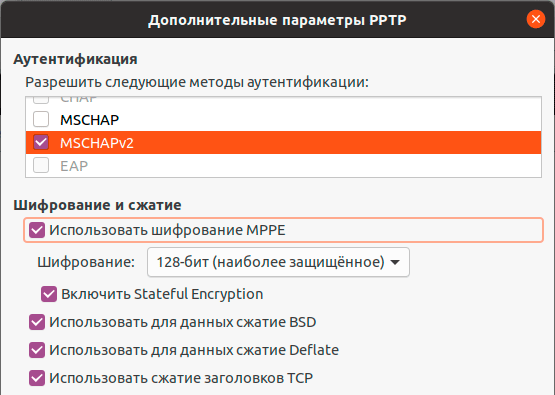
Закрываем данное окно с сохранением данных и переходим на закладку IPv4, где в разделе Маршрутизация устанавливаем флаг Использовать это подключение только для ресурсов этой сети, в противном случае в туннель пойдет весь трафик узла.
На этом настройка подключения завершена, можно подключаться.
Для работы с L2TP потребуется установить дополнительные пакеты:
apt install network-manager-l2tp-gnomeПосле чего в доступных типах подключения появится L2TP. Основные настройки ничем не отличаются от PPTP, также адрес сервера, имя и пароль пользователя.
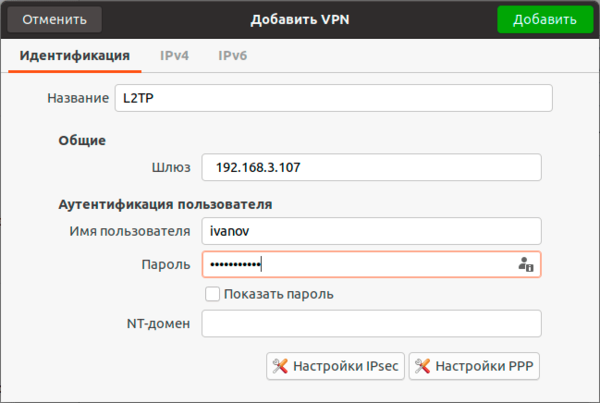
Затем откроем Настройки PPP, в разделе Аутентификация также выберем только MSCHAPv2, а вот опции шифрования оставляем выключенными, так как чистый L2TP шифрования не использует, для защиты канала здесь применяется IPsec. Флаги сжатия также оставляем установленными по умолчанию.
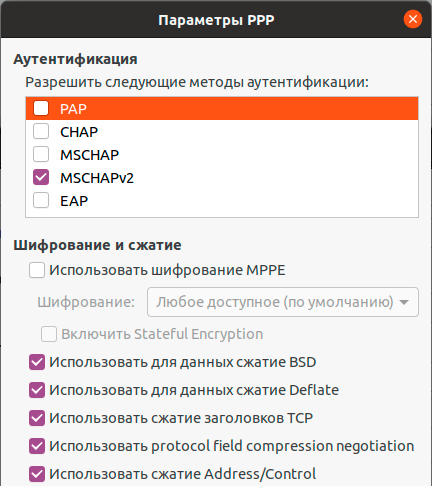
Затем переходим в Настройки IPsec, это наиболее сложная и ответственная часть настроек, так как от них напрямую зависит безопасность соединения. В поле Pre-shared key введите Общий ключ, а ниже потребуется указать используемые шифры. Большинство материалов в сети интернет копируют друг у друга откровенно старые и слабые наборы шифров, что не соответствует реалиям сегодняшнего дня, хотя соединение с такими значениями будет работать. Мы же будем использовать максимально безопасные значения, для этого в поле Phase1 Algorithms укажите aes256-sha1-ecp384, а в поле Phase2 Algorithms — aes256-sha1.
Также имеет смысл установка флага Enforce UDP Encapsulation, который принудительно включает NAT-T, в случае если вы точно знаете, что ваш сервер находится за NAT, без этой опции протокол включается автоматически при обнаружении первого устройства с NAT.
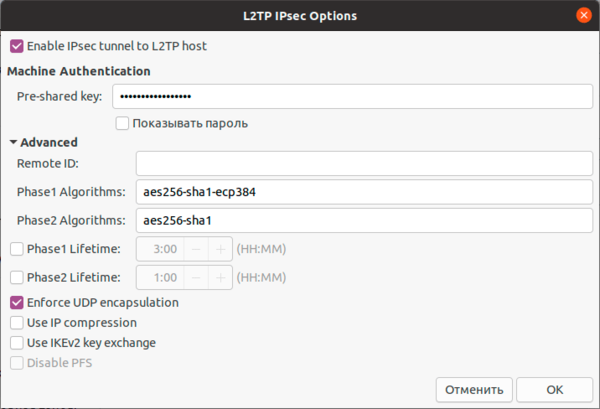
Сохраняем настройки и переходим на вкладку IPv4, где также в разделе Маршрутизация ставим флаг Использовать это подключение только для ресурсов этой сети, чтобы направить в туннель только трафик для сети офиса.
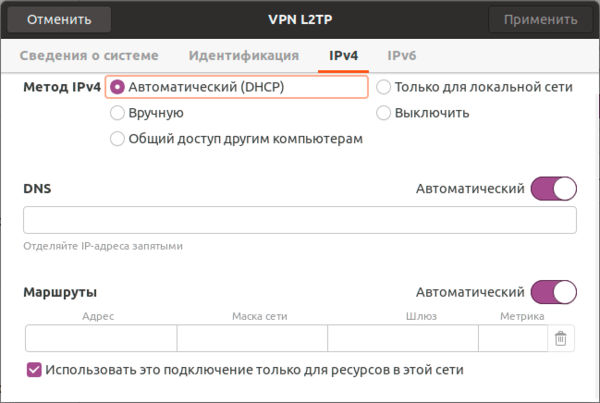
На этом настройка закончена, можно подключаться.
Онлайн-курс по устройству компьютерных сетей
На углубленном курсе «Архитектура современных компьютерных сетей» вы с нуля научитесь работать с Wireshark и «под микроскопом» изучите работу сетевых протоколов. На протяжении курса надо будет выполнить более пятидесяти лабораторных работ в Wireshark.
Virtual Private Network (VPN) secures your network by providing a secure connection tunnel. You can also use VPN services to access the public network through a secure VPN network to avoid exposing your public network information. We will learn how to set up a PPTP/L2TP VPN on Windows Server 2019.
We advise using at least a 4core 8gb server for a PPTP/L2TP VPN server, you may experience connection issues with servers with lower configurations.
Install Routing & Remote Access Server Role
In this section, we will walk through the steps to install routing and remote access to allow direct access from the remote devices on the Windows server.
1. To start, log in to your Windows Server and navigate to the search by pressing the Windows button in the bottom left corner. Then search Server Manager and select the application, Server Manager.
2. Once the Server Manager window is open, click on Add Roles and Features.
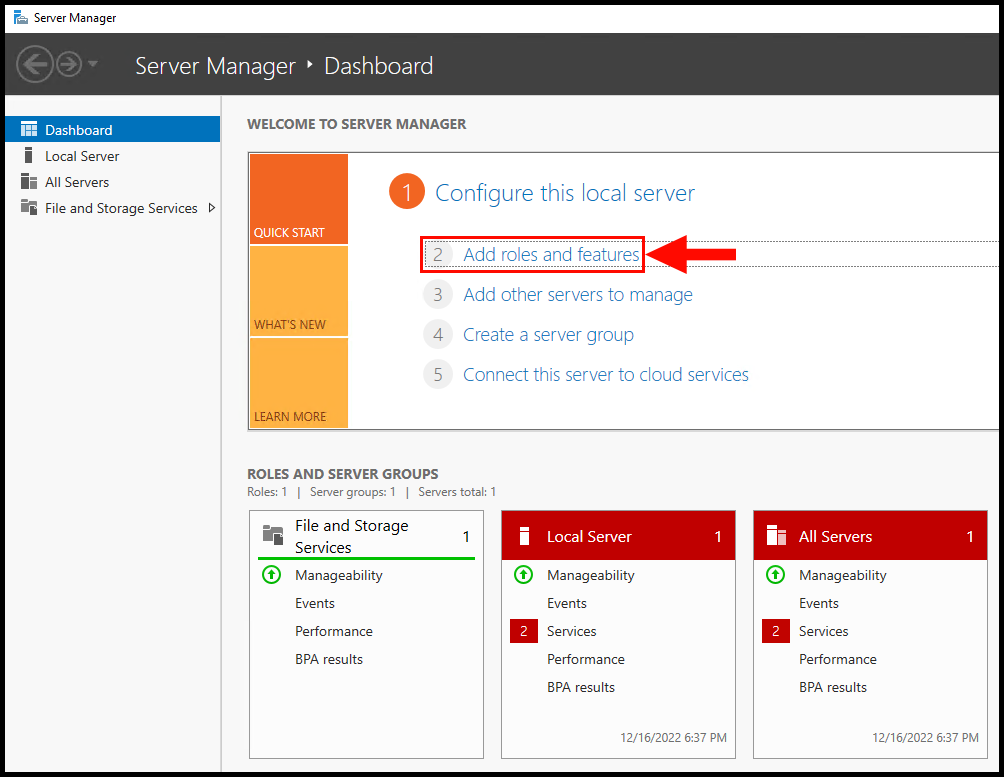
3. Then, the Add Roles and Features Wizard screen will appear. Click Next to move on from the Before You Begin tab.
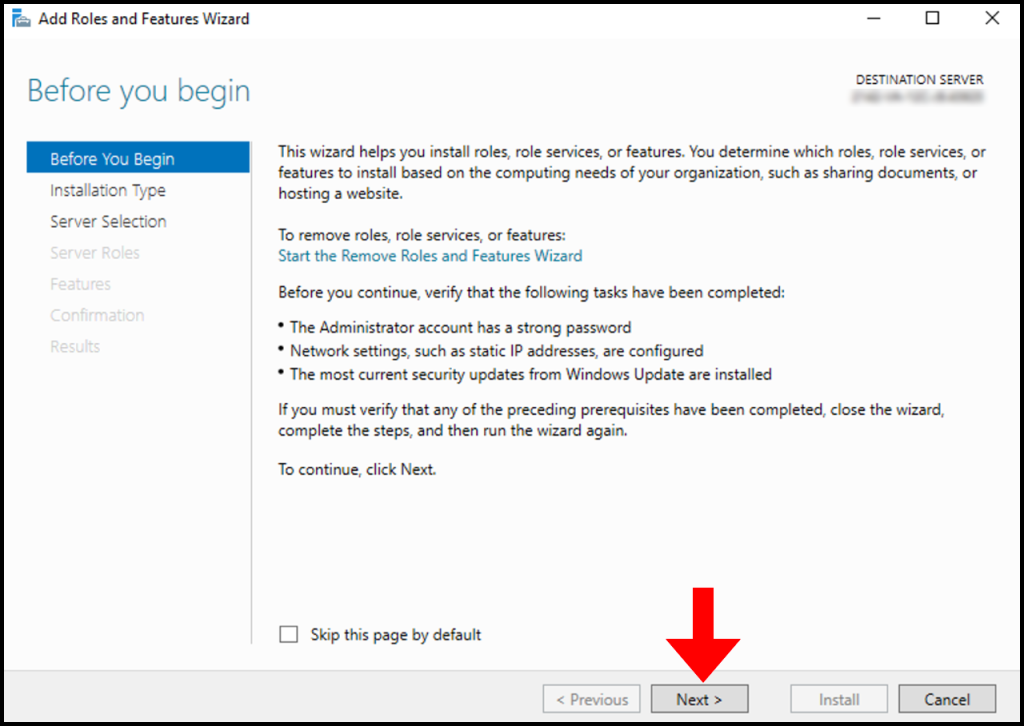
4. Next, in the Installation Type tab, select Role-based or feature-based installation. Then, click Next to continue.
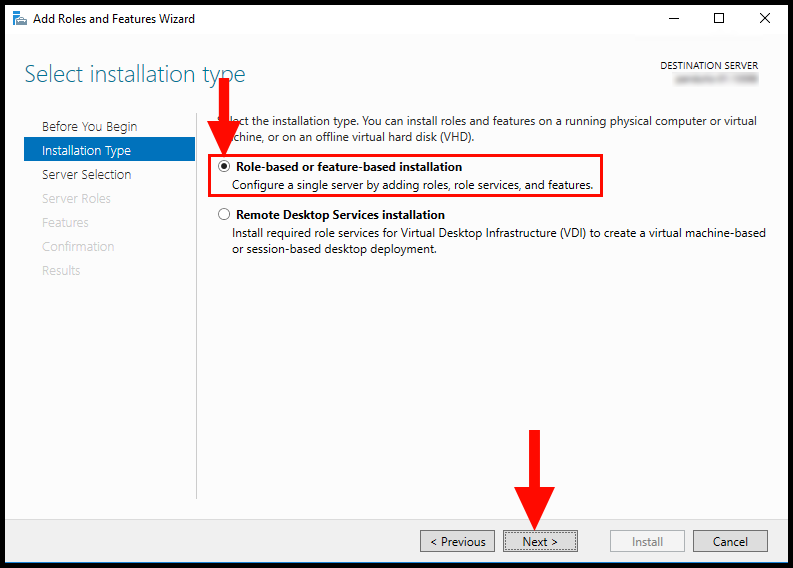
5. Now in the Server Selection tab, select your Windows Server and then click Next to continue.
6. In the Server Roles tab, select Remote Access. Then, click on Next to continue setting up Remote Access.
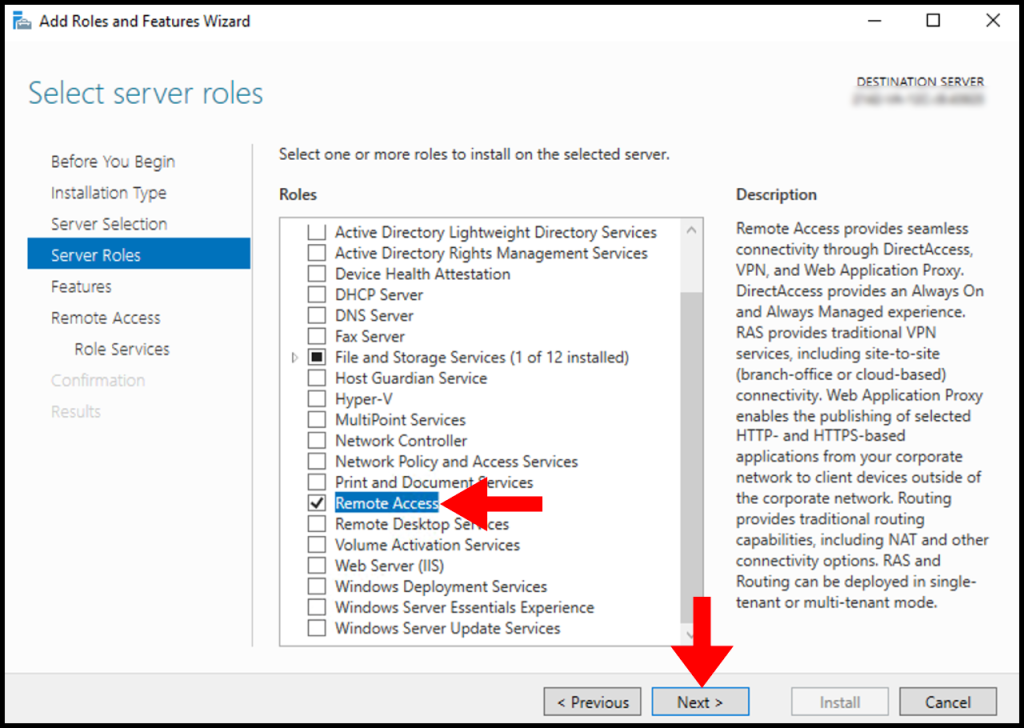
7. On the Features tab, refrain from making any modifications, then click Next to proceed.
8. In the Remote Access tab, click on Next to move on with setting up Remote Access.
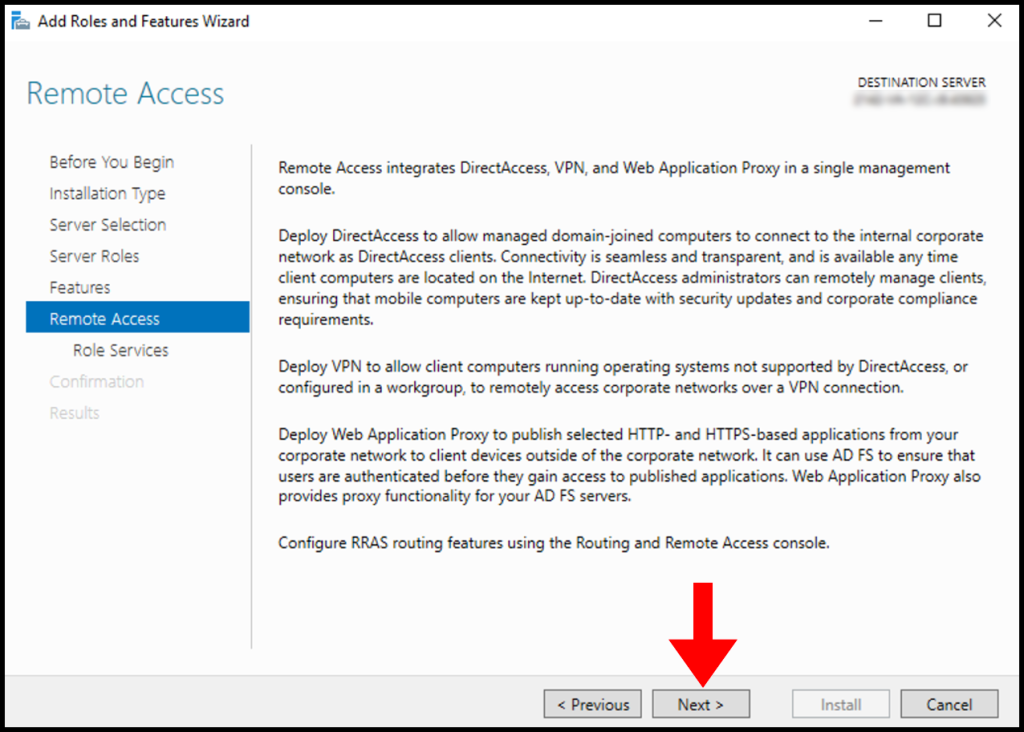
9. Next, in the Role Services tab, select DirectAccess & VPN (RAS) and Routing, then click on Next.
A pop-up will appear to confirm the features that will need to be installed to set up DirectAccess and VPN (RAS). You can confirm by clicking Add Features.
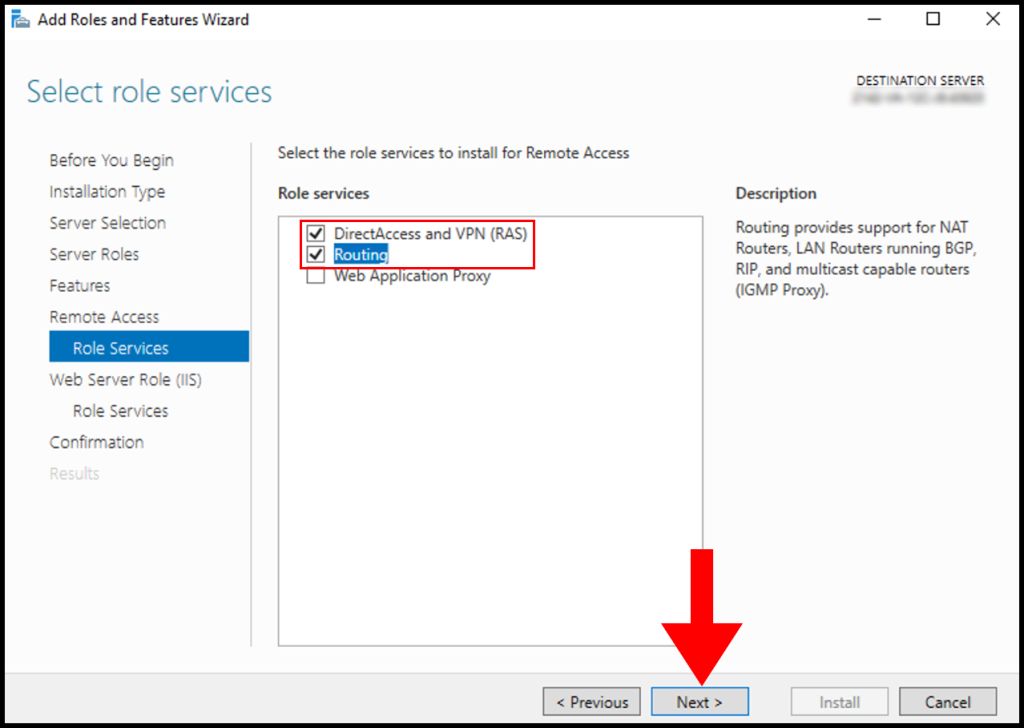
9. Then, skip the Web Server Role (IIS) tab by clicking on Next.
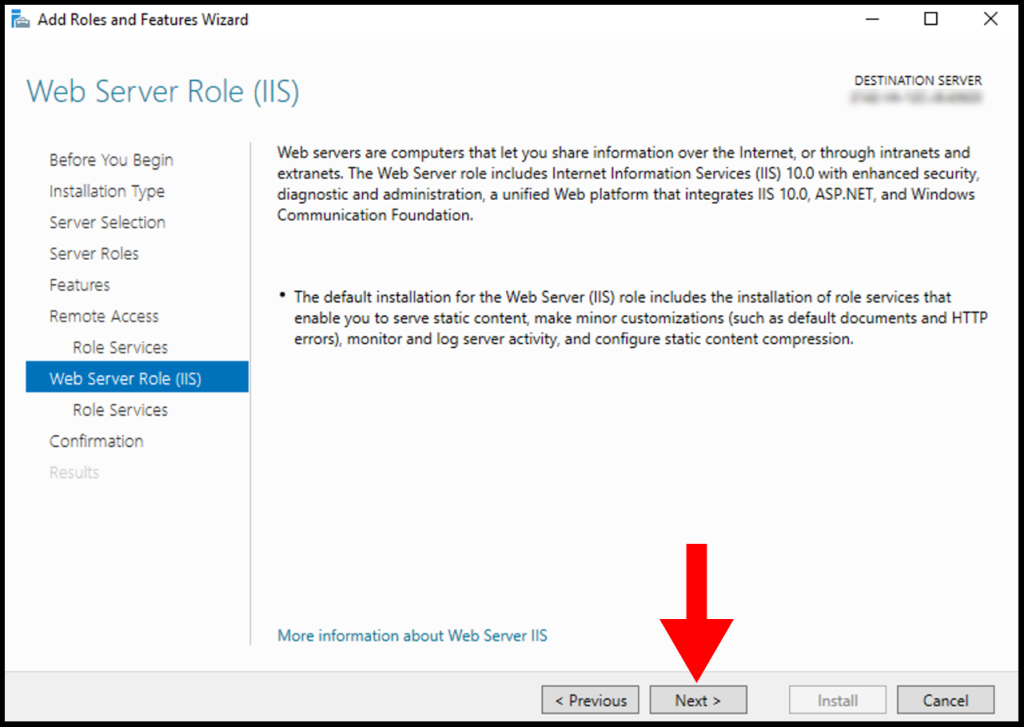
10. In the Web Server Role (IIS) Role Services section, leave everything as default and then click on Next.
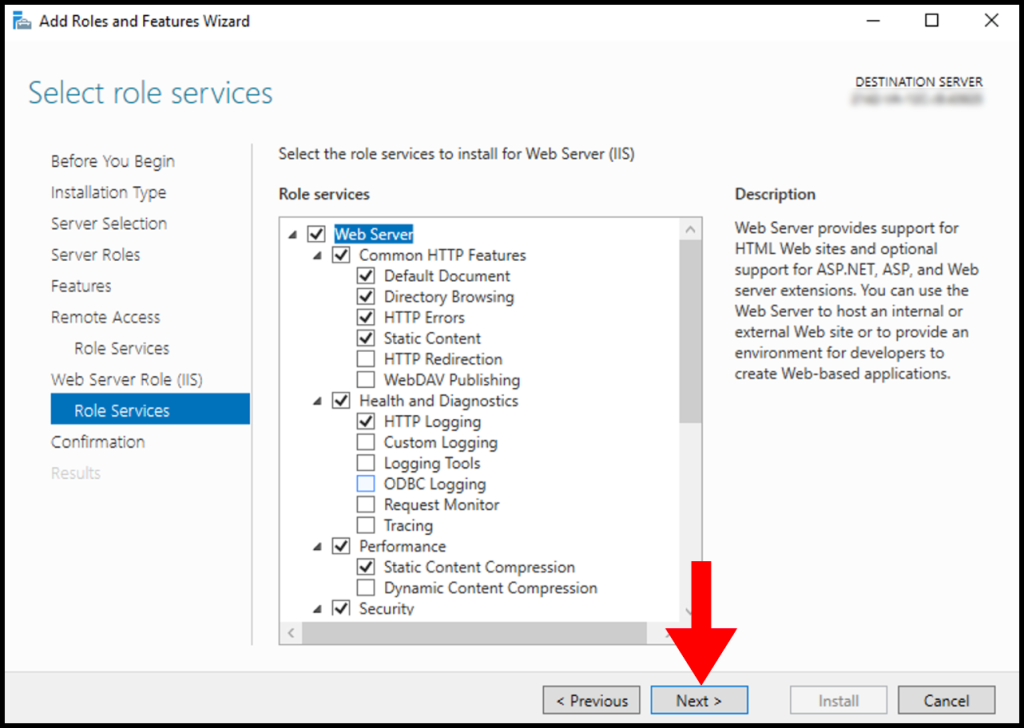
11. In the Confirmation screen, you will see the summary of components that will be installed on the Windows server. Finally, click on Install.
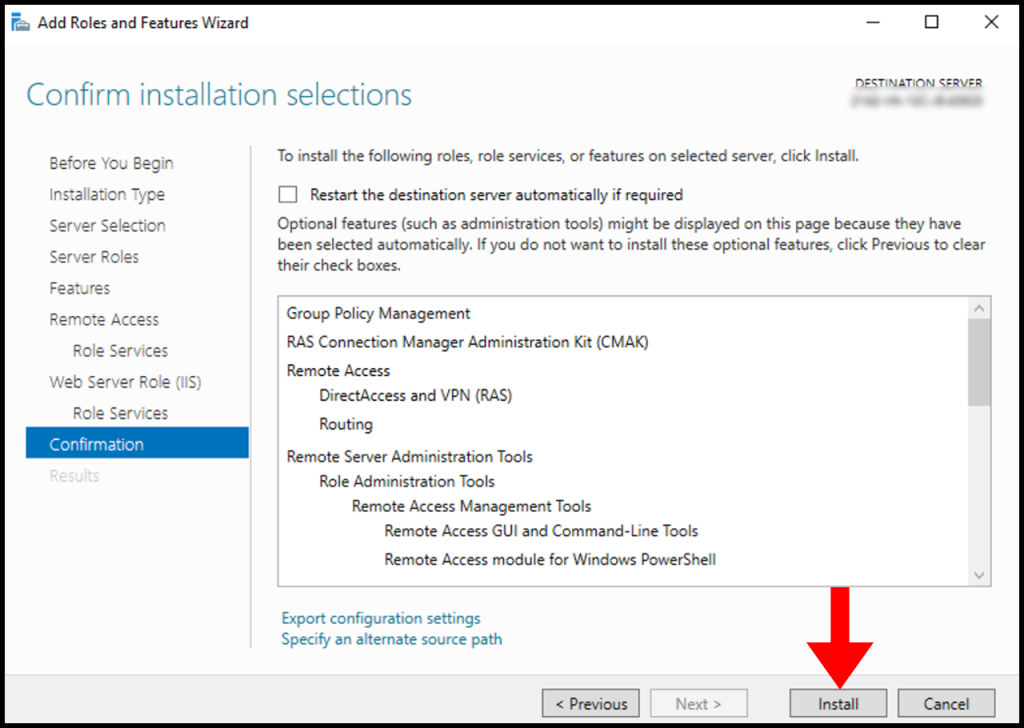
12. Once the installation is complete, you may close the window by clicking on Close.
Add Loopback Network Adapter to Windows Server
In this section, we will be adding a Loopback Network Adapter to the Windows server to avoid the error message as shown below.
Less than two network interfaces were detected on this machine. For standard VPN server configuration, at least two network interfaces need to be installed. Please use a custom configuration path instead.
1. To start, open Server Manager by using Windows search and searching for Server Manager.
2. Once the Server Manager window is open, click on Tools in the top right-hand corner. From the drop-down menu, click Computer Management.
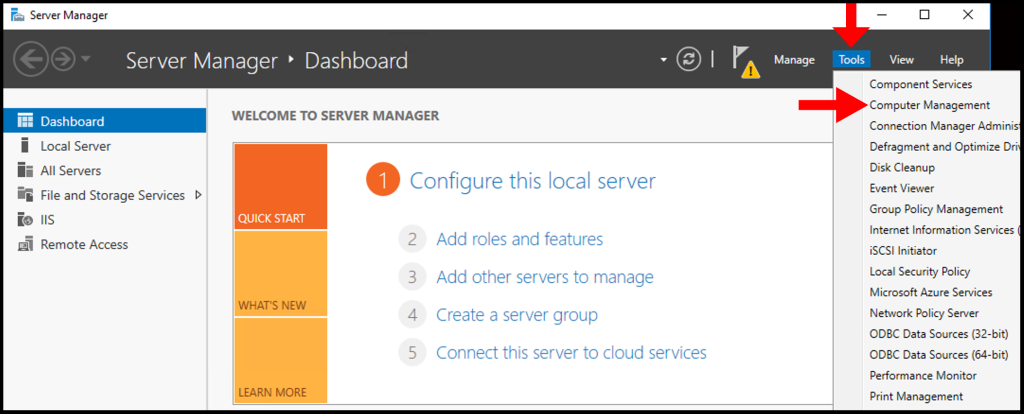
3. Then in the Computer Manager window, click on Device Manager from the left-hand menu, and in the middle menu make sure your VM menu is expanded as seen below.
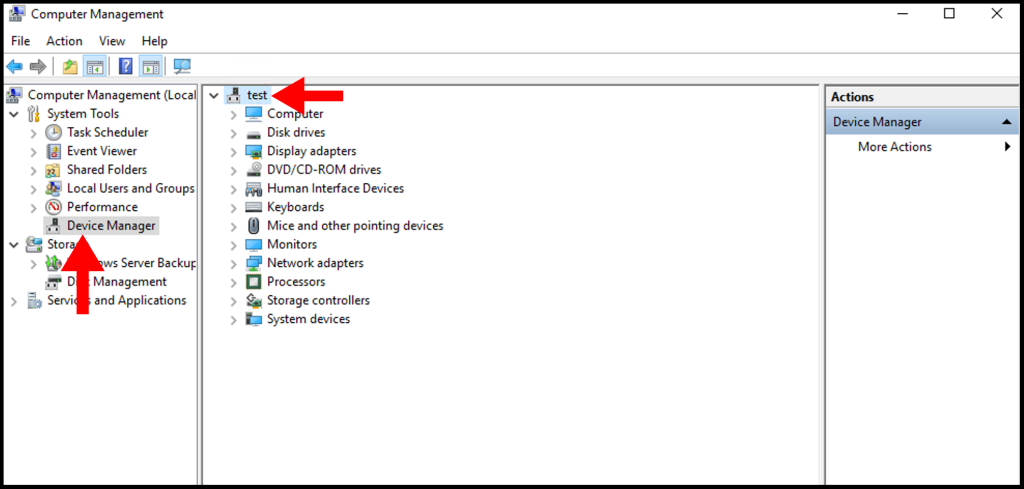
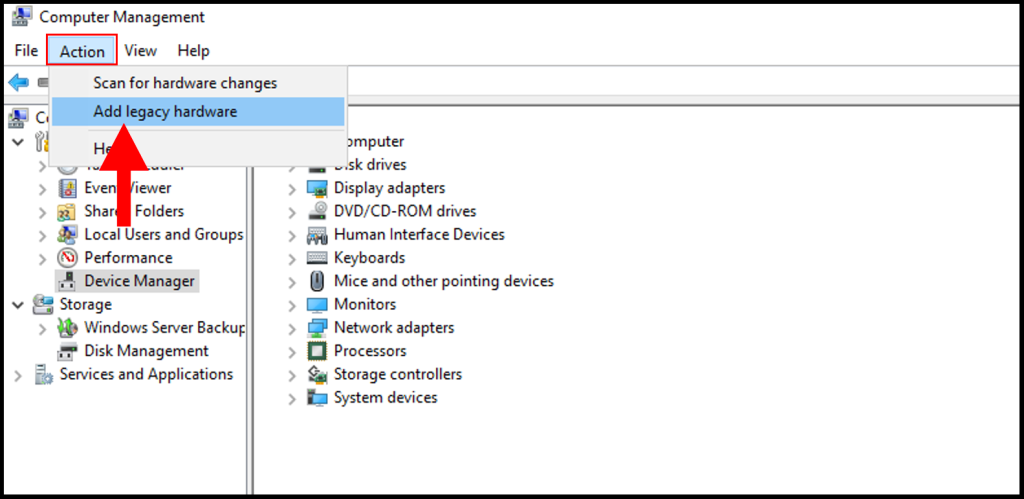
4. Then, in the top left-hand corner click Action, and a drop-down menu will appear. From the drop-down menu, select Add legacy hardware.
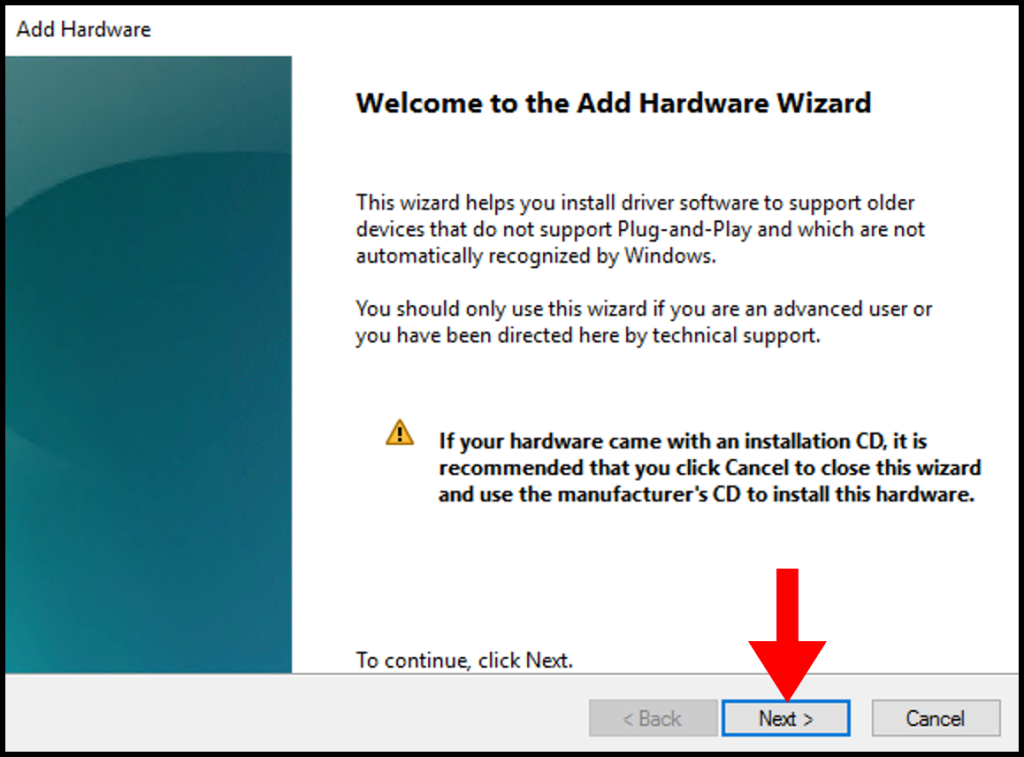
5. Once the Add Hardware window appears, click Next to continue.
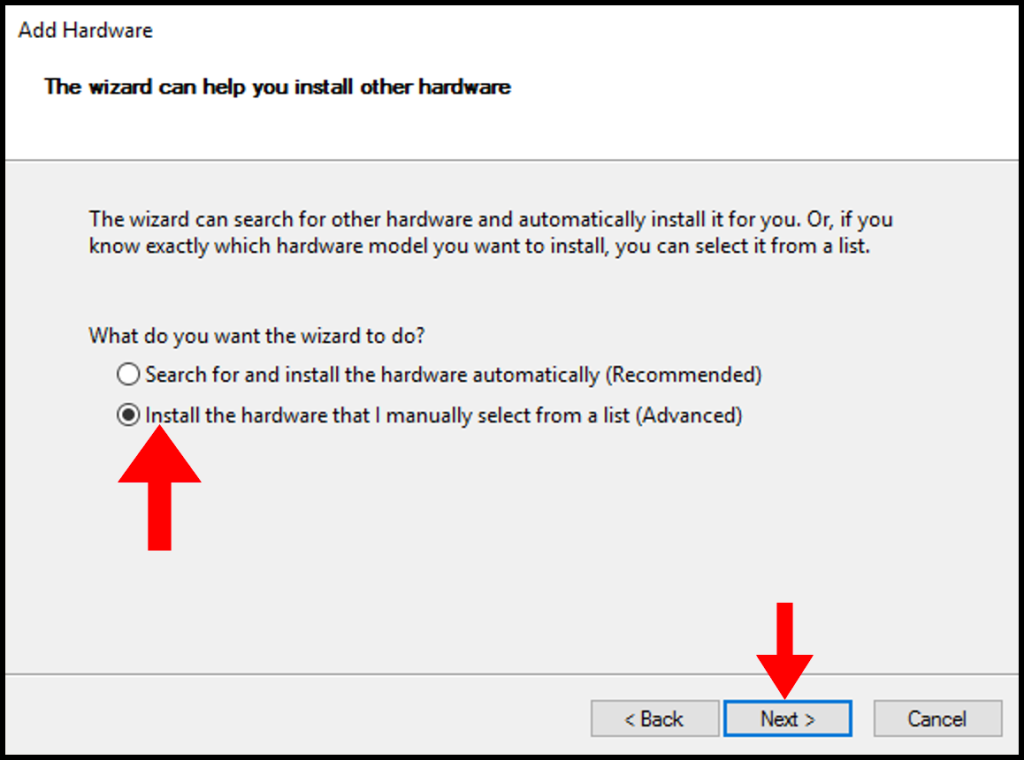
6. Next, click on the Install the hardware that I manually select from a list (Advanced) button. Then, click the Next button.
7. In the next screen, utilize the scroll function to locate and select Network adapters. Afterward, click Next to move on.
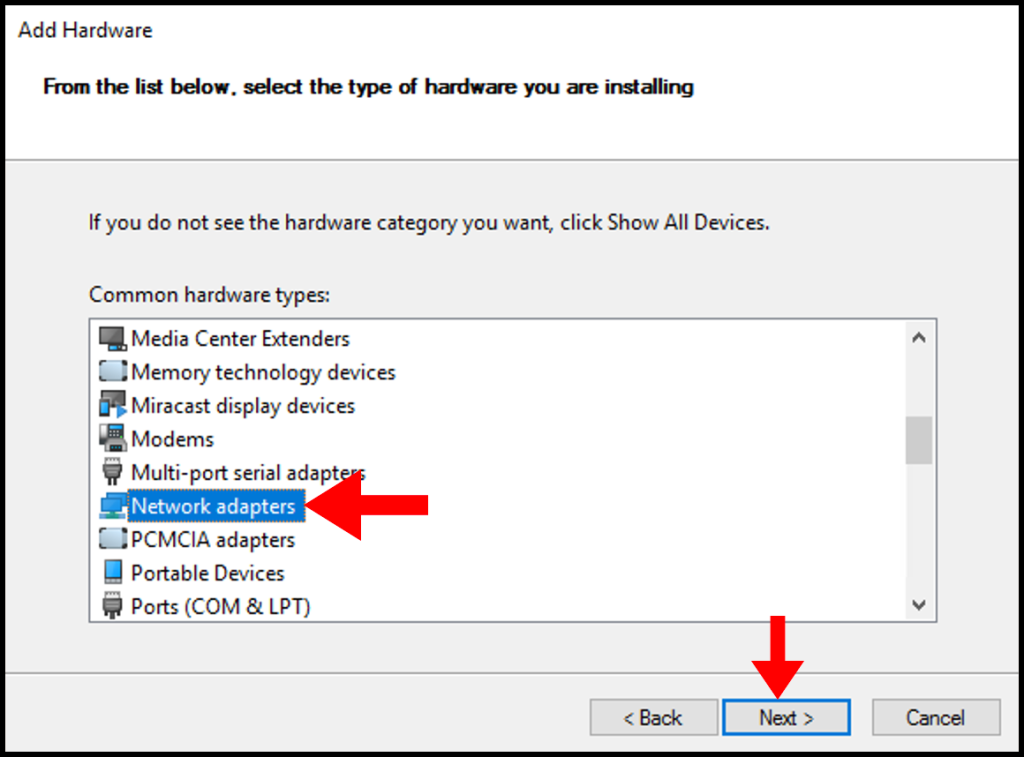
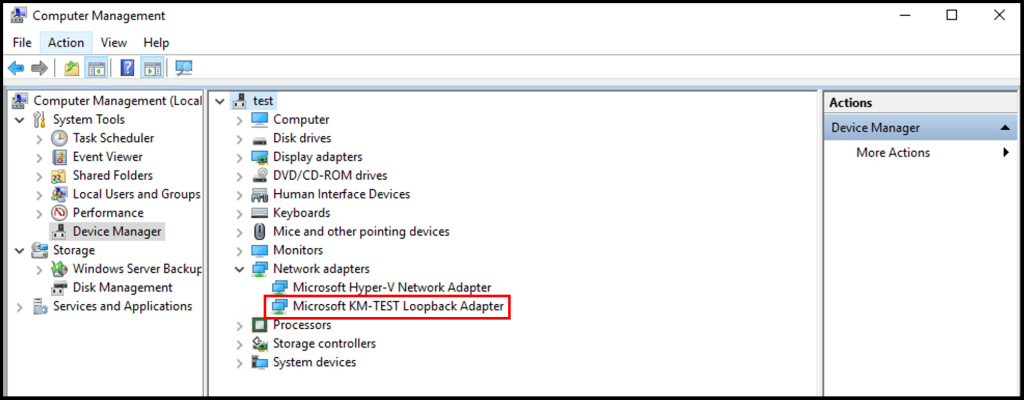
8. In the next screen, under the Manufacturer options select Microsoft, and under the Model options select Microsoft KM-TEST Loopback Adapter. Click Next to move on.
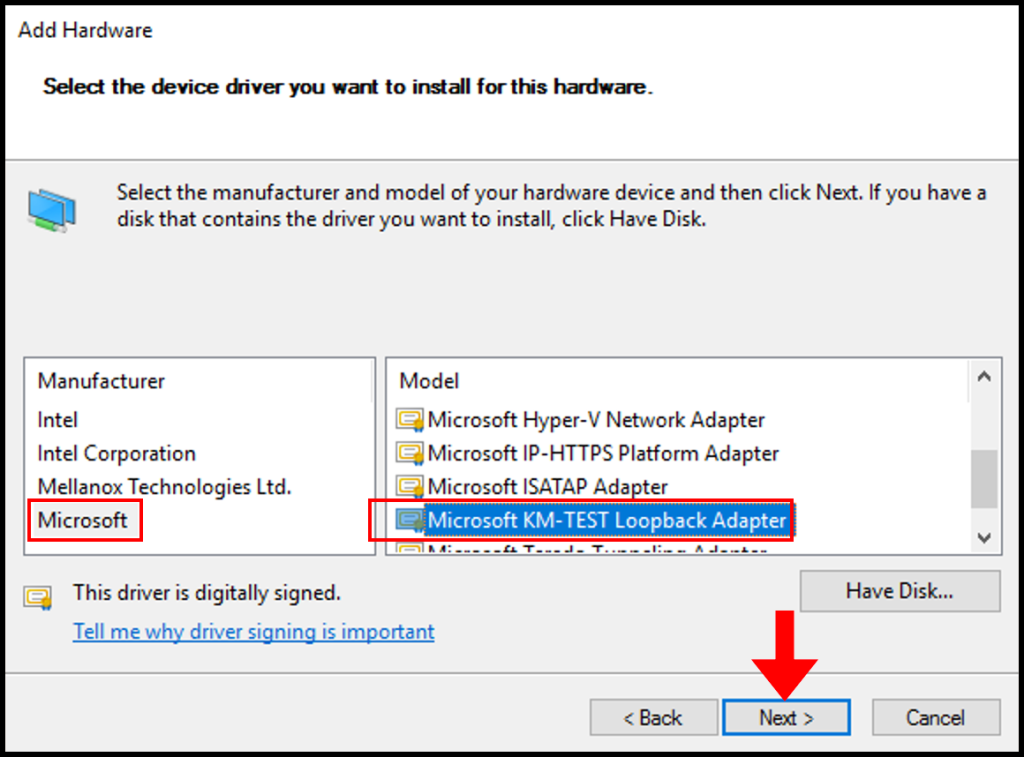
9. The next page is a confirmation of the hardware that we will be installing, click Next to continue.
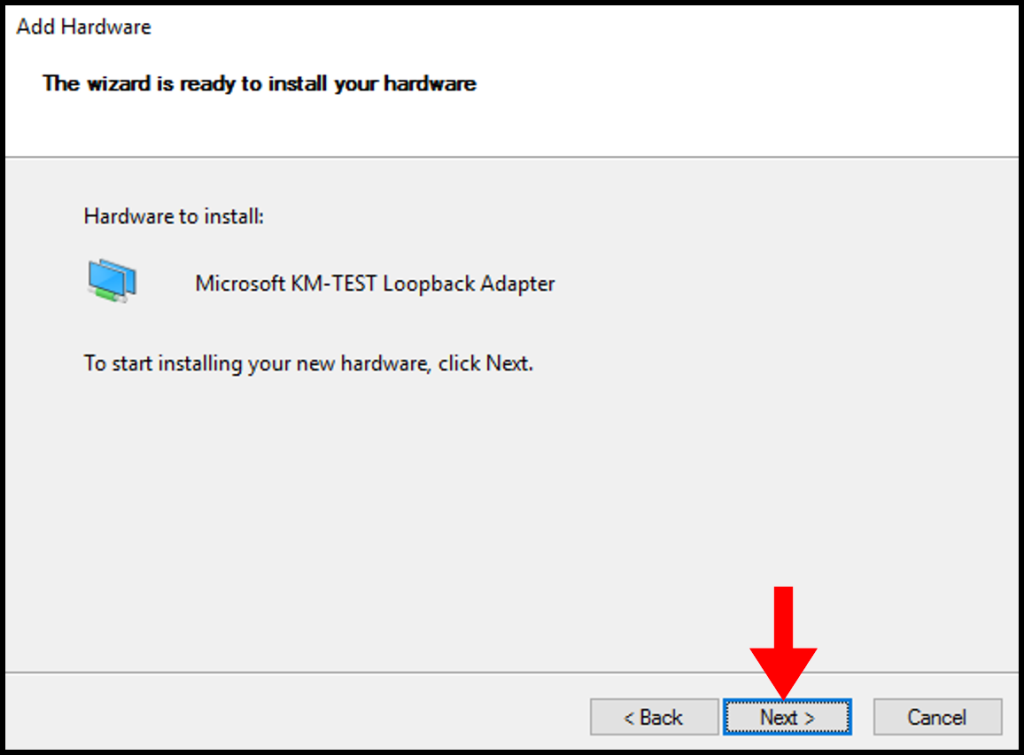
10. After the installation is complete, click Finish to close the wizard.
11. To confirm the installation was successful, we can see it in the Computer Management window and check under Network Adapters.
Configure Remote Access Service on Windows Server
In this section, we will be going over how to configure the Remote Access Service on your Windows Server to set up a PPTP/L2TP VPN on a Windows Server
1. To start, in the Server Manager Window select Remote Access.
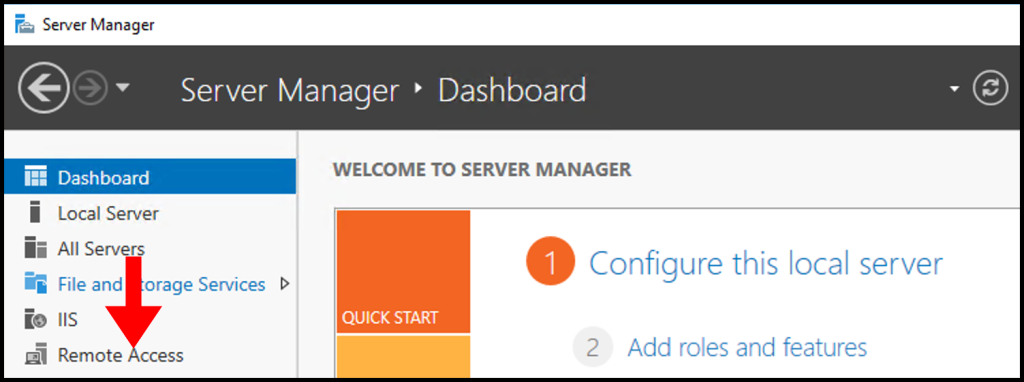
2. Next, right-click your Server Name and from the menu select Remote Access Management.
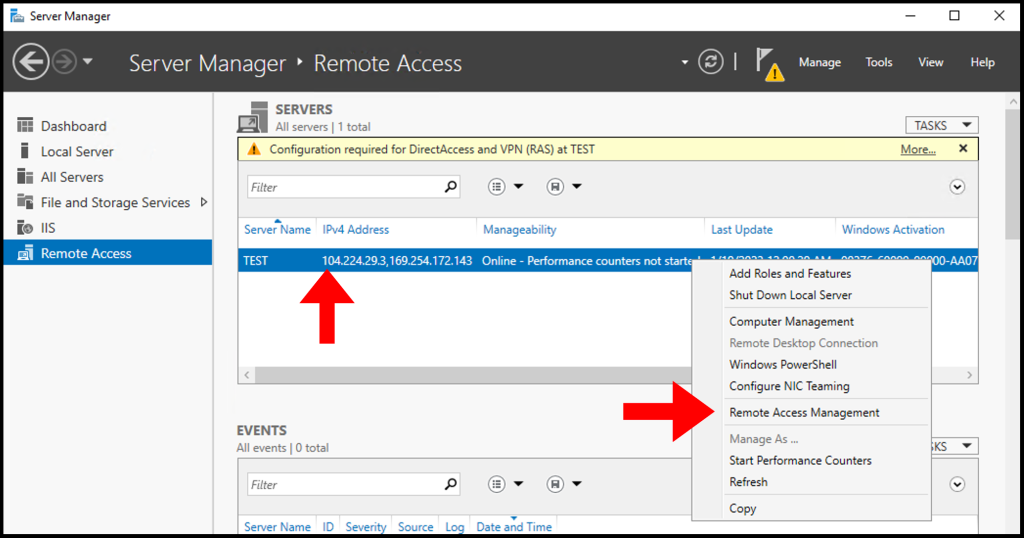
3. Once the Remote Access Management Console window opens, select DirectAccess and VPN from the menu on the left-hand side. Then, select Run the Remote Access Setup Wizard under Configure Remote Access.
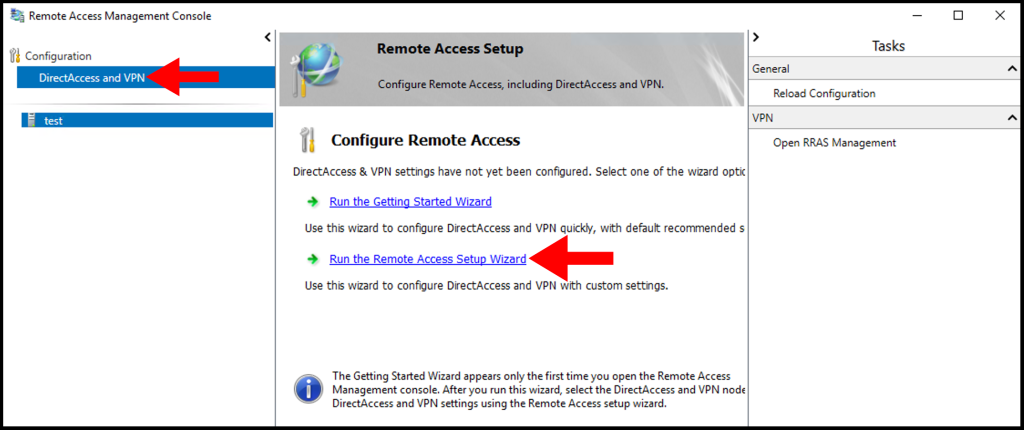
4. Next, the Configure Remote Access window will open. Then, click Deploy VPN only.
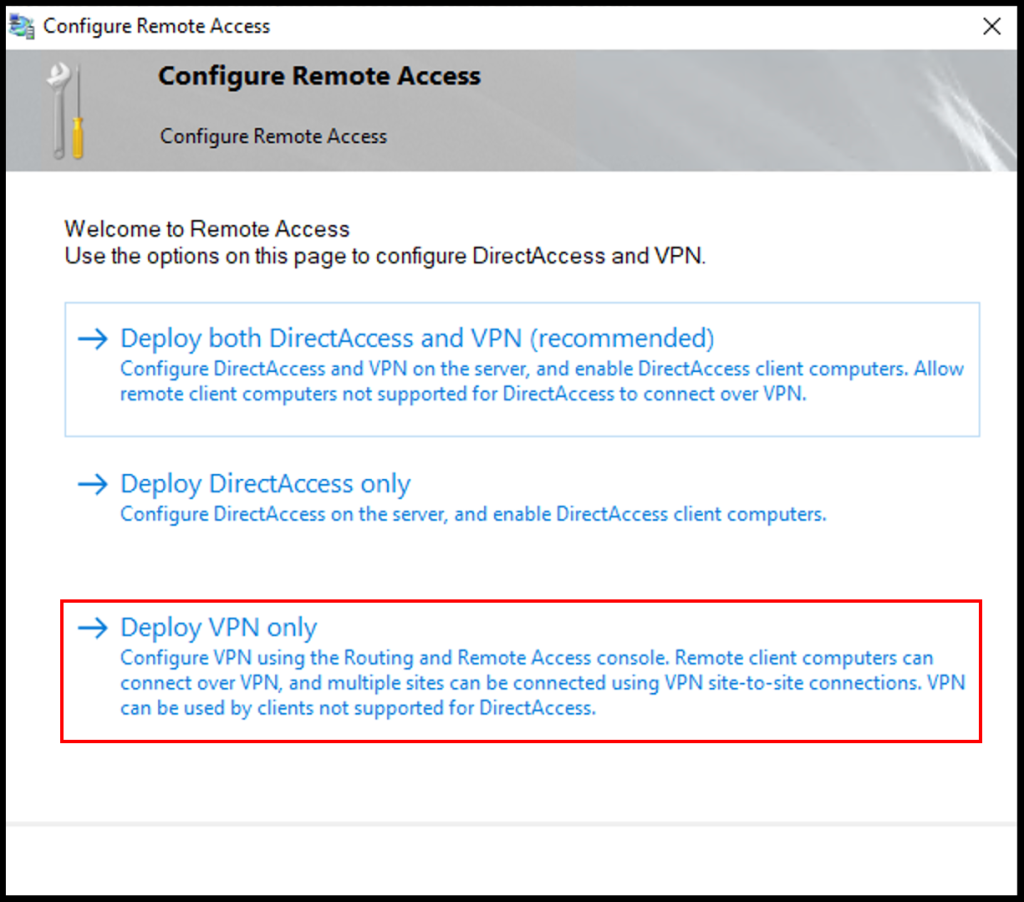
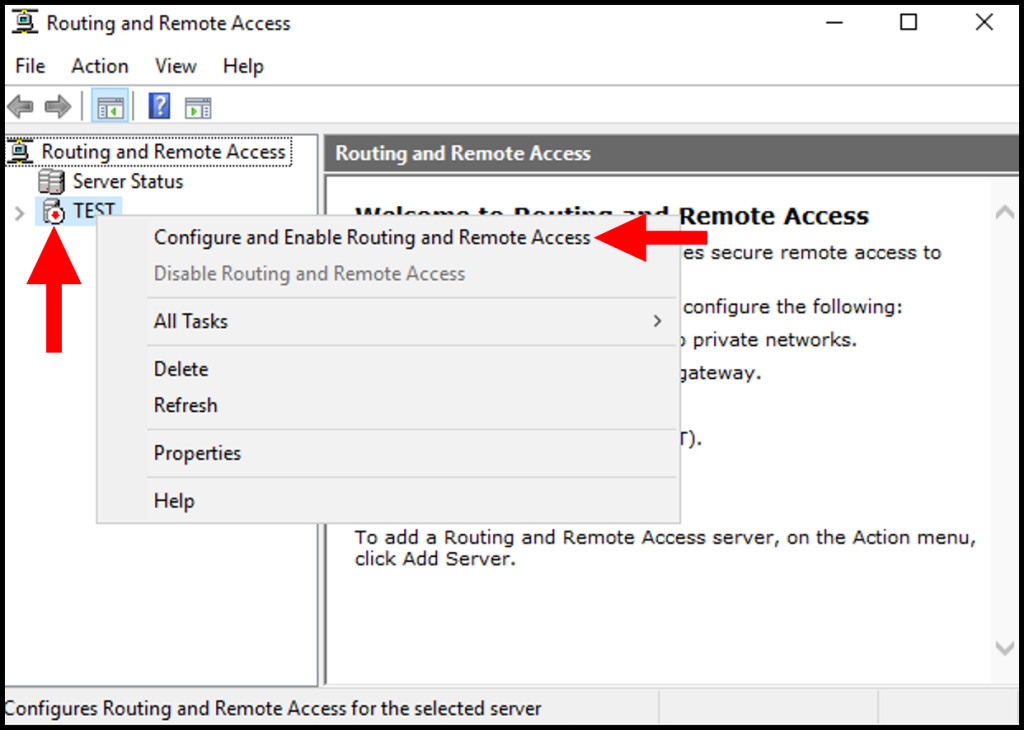
5. The Routing and Remote Access window will appear, right-click your server name and select Configure and Enable Routing and Remote Access from the options listed.
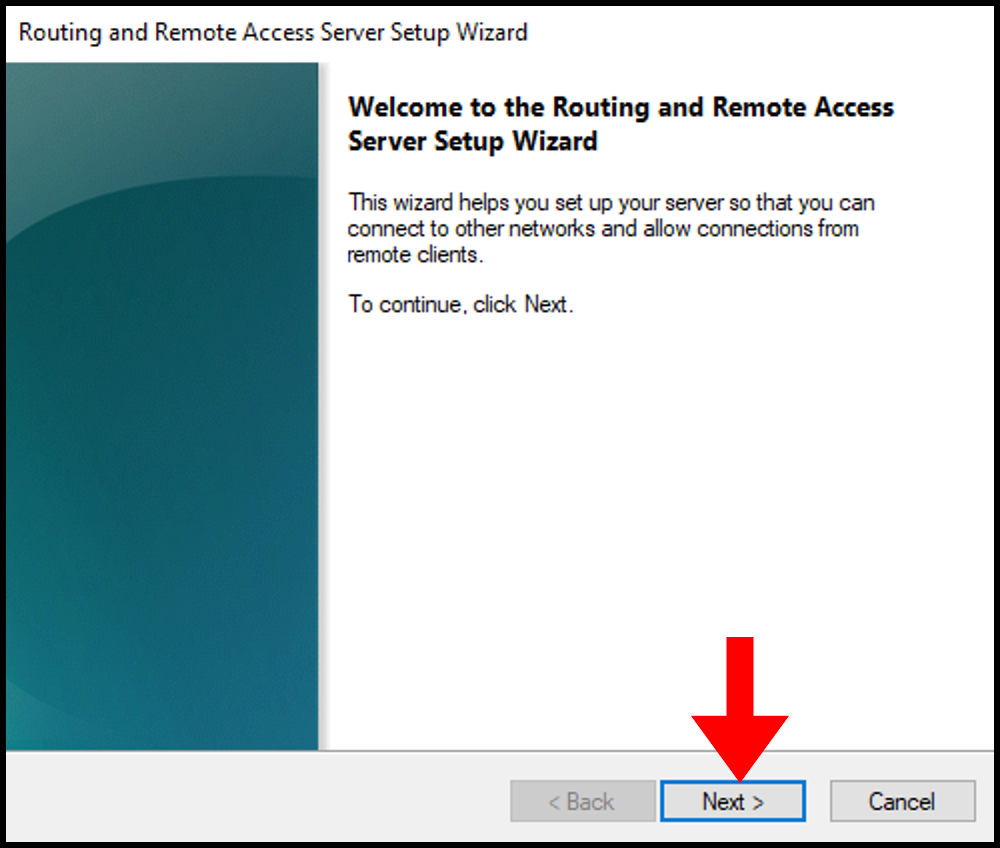
6. Then, the Routing and Remote Access Server Setup Wizard will open. Click Next to move forward.
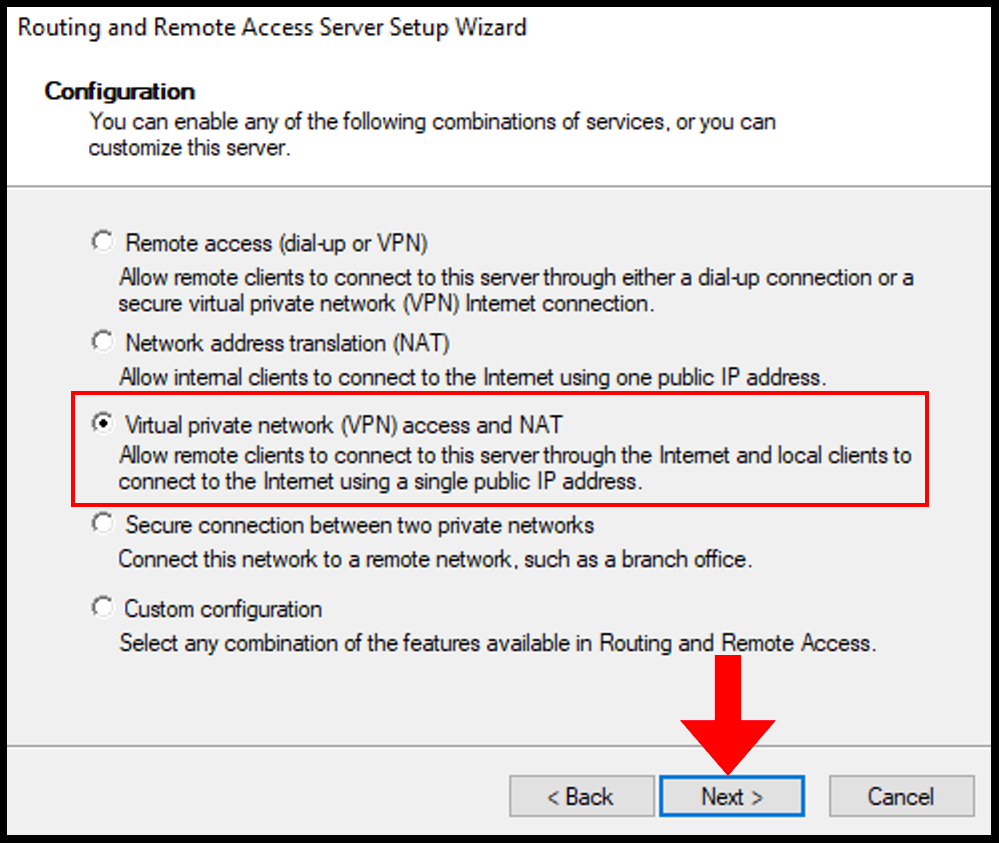
7. On the next page, select Virtual private network (VPN) access and NAT from the presented options and click Next once done.
8. Then, on the VPN Connection page select the Network interface where the server’s public IP is configured. In this case, we will be selecting Ethernet. Once you have selected your network interface, click Next to move on.
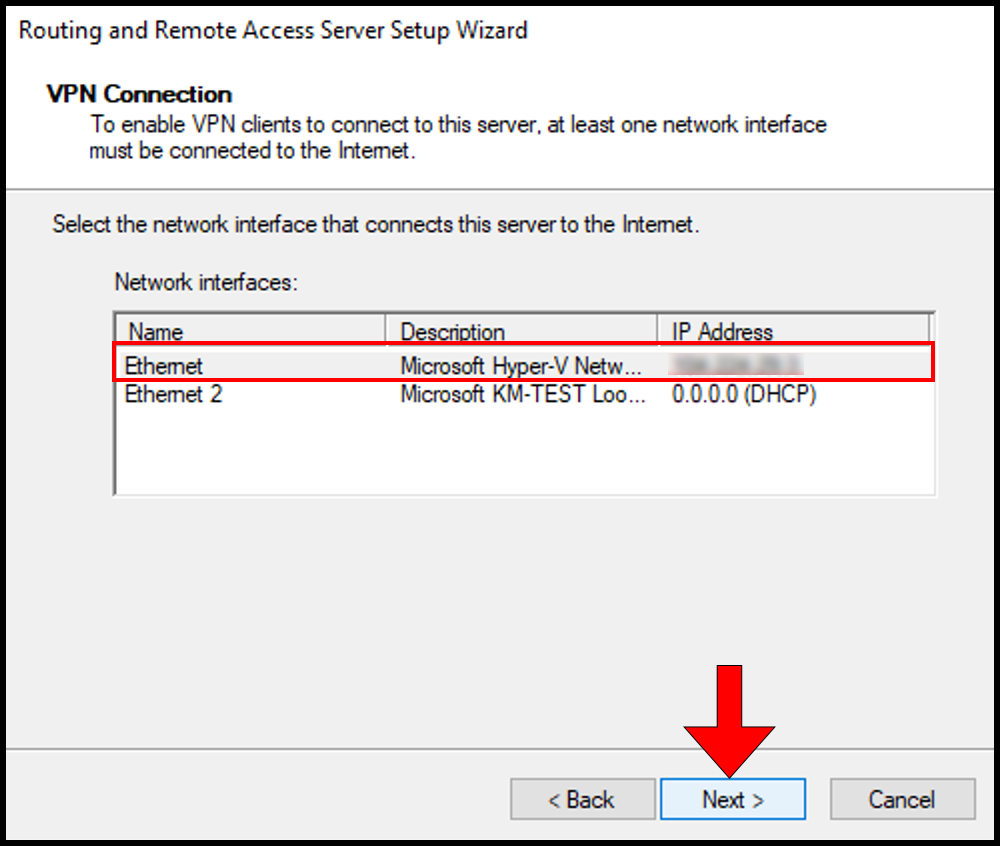
9. Next, on the IP Address Assignment page we will select From a specified range of addresses. Then, click Next to continue.
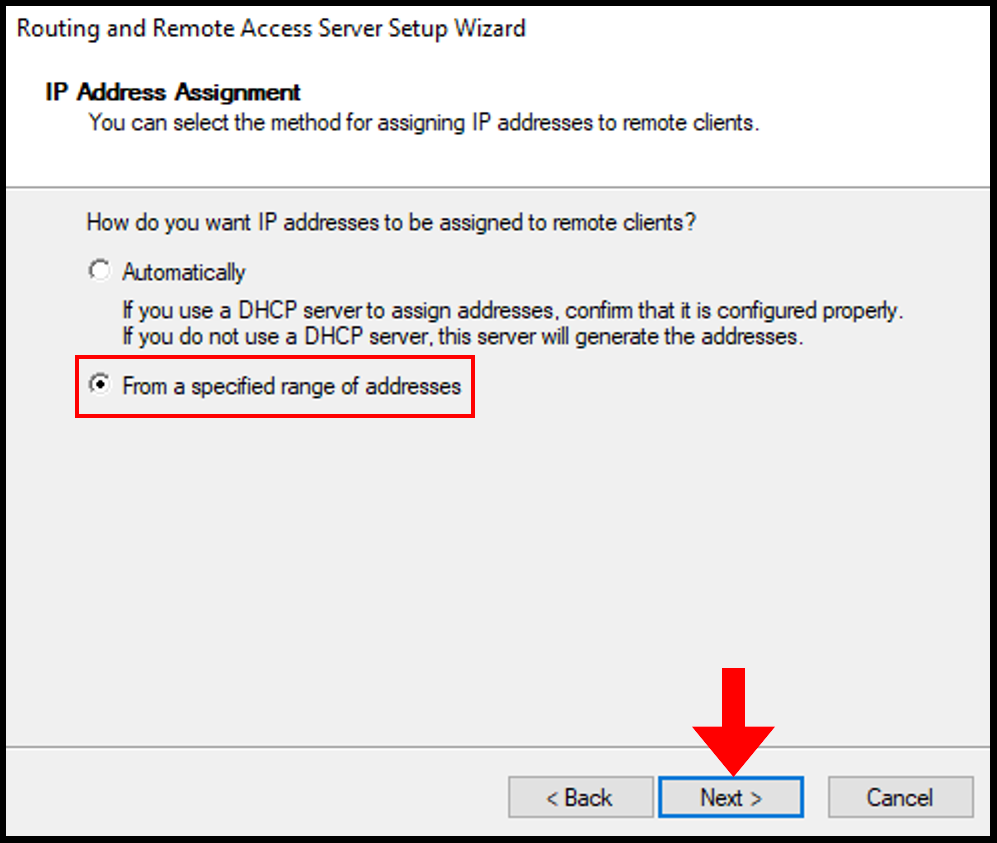
10. In the next screen, select New to define the range of private IP addresses that the server will give to the remote VPN.
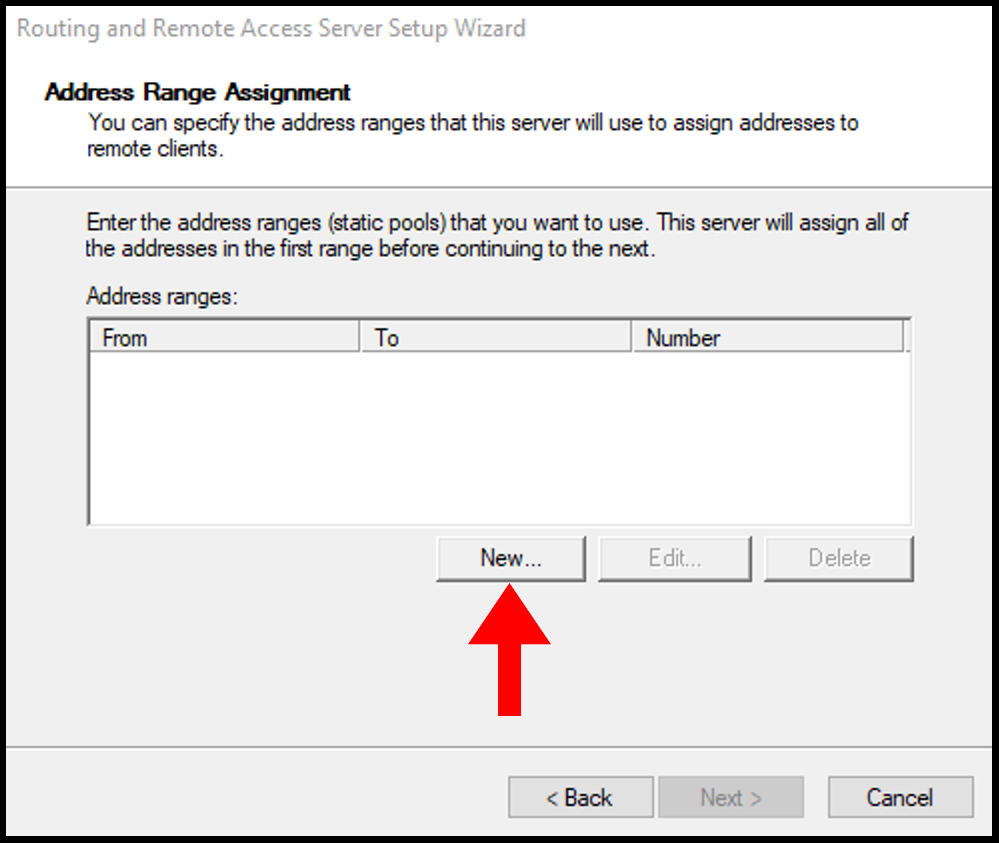
11. In the New IPv4 Address Range, select a range of Internal IP Addresses and input the starting IP address and ending IP address. You can select a range from these lists. Then, click OK to move on.
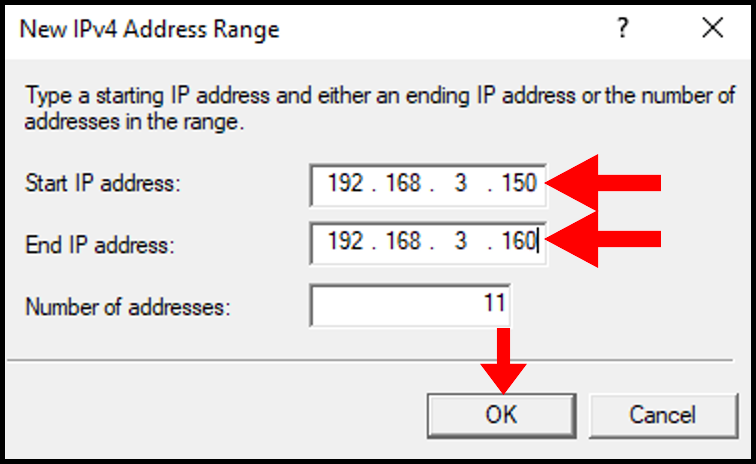
12. Now, we can see our Address Range populated on the Address Range Assignment page. Then, click Next.
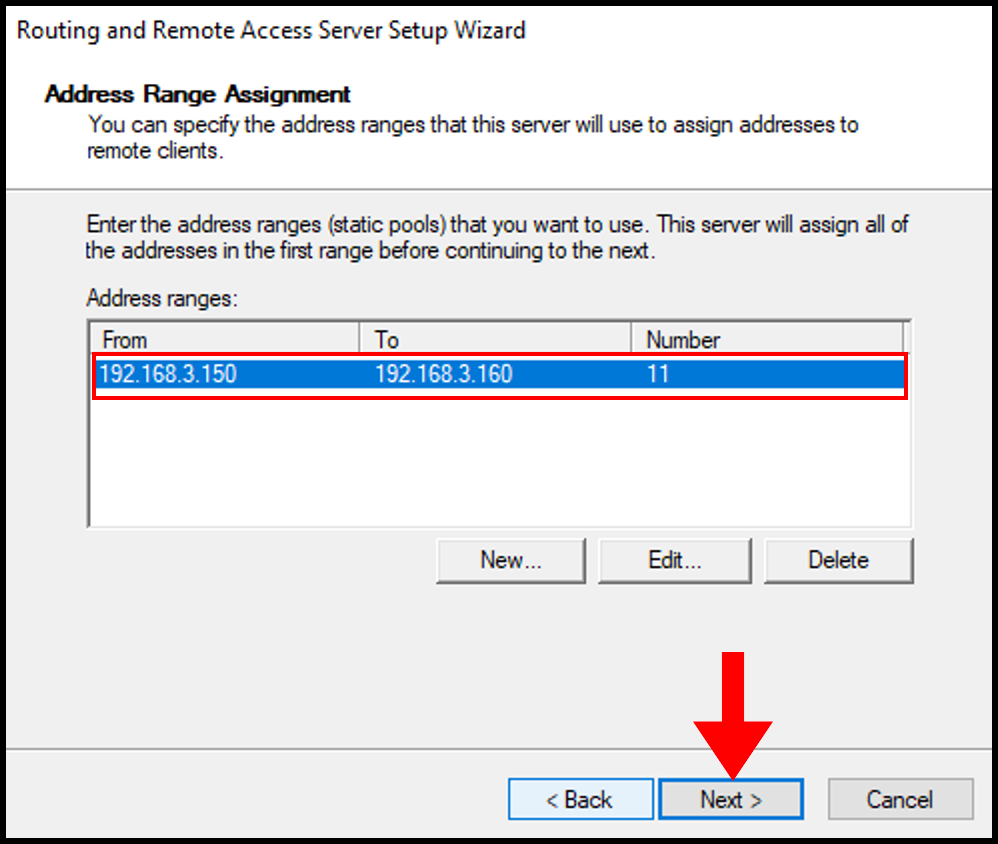
13. On the next page, select No, use Routing and Remote Access to authenticate connection requests since we will not be using a RADIUS server. Click Next to move on.
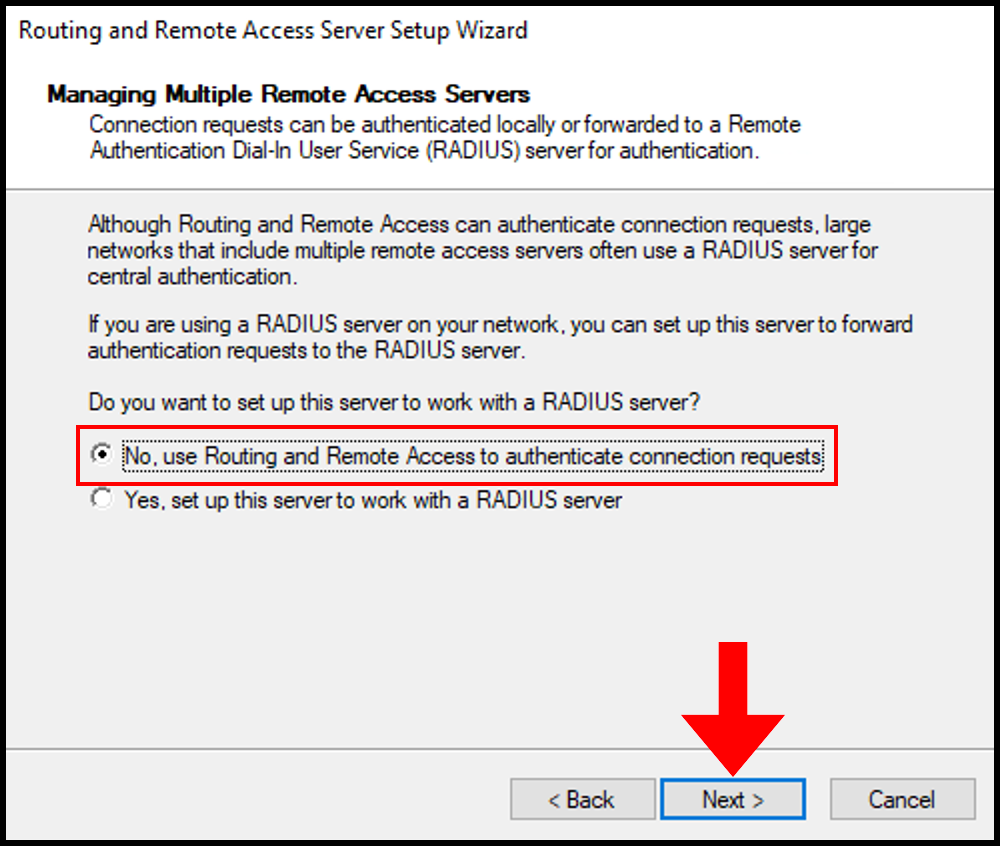
14. On the next page, click Finish to move on.
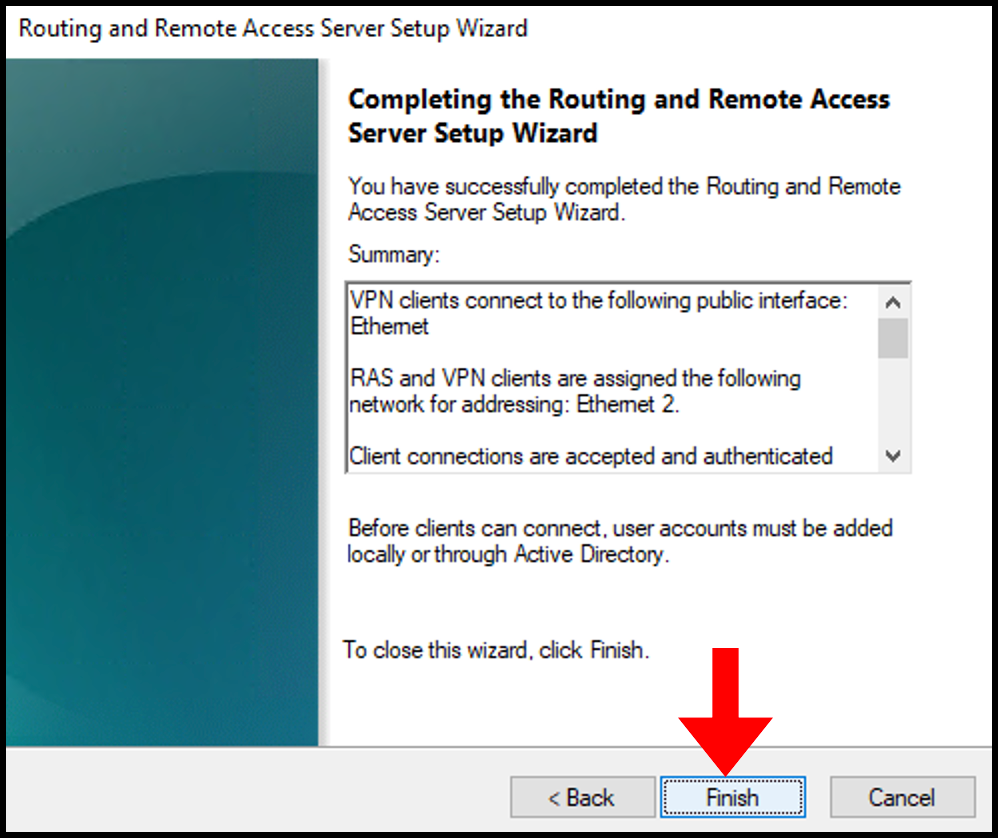
15. A message will be prompted, click OK to close it out. Now you have completed configuring Routing and Remote Access Server Setup Wizard.
16. To verify that Routing and Remote Access has been configured, you can check via the Routing and Remote Access window we opened earlier in this section. The server name will now have a green up arrow as seen below.
Enable L2TP/IPsec VPN on Windows Server
In this section, we will go over how to enable L2TP/IPsec using a pre-shared key through Routing and Remote Access properties to set up a PPTP/L2TP VPN on a Windows Server.
1. In the Routing and Remote Access window we opened in the last section, right-click on your server name in the left-hand menu. Then select Properties from the options presented.
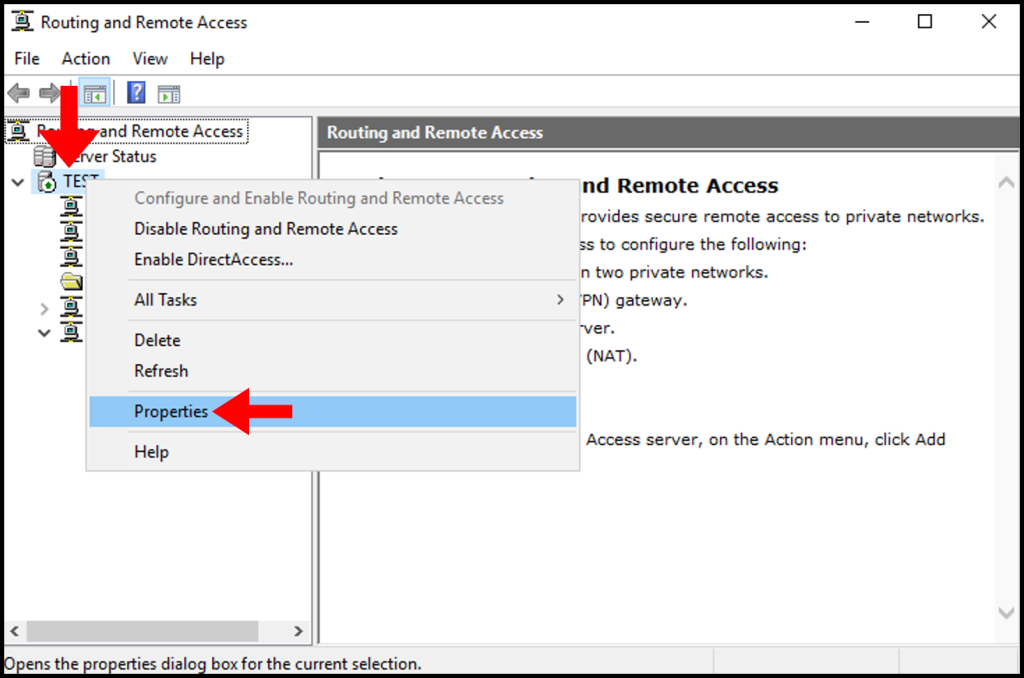
2. In the properties window, check the box for Allow custom IPsec policy for L2TP/IKEv2 connection and enter a made-up key under Preshared Key. Then, click OK and Apply.
Make sure to note down your Preshared key as you will need it later.
3. You will then need to click OK on the pop-up.
4. Lastly, restart your Windows VPS.
Allow Remote Access to VPN via Public Network Adapter
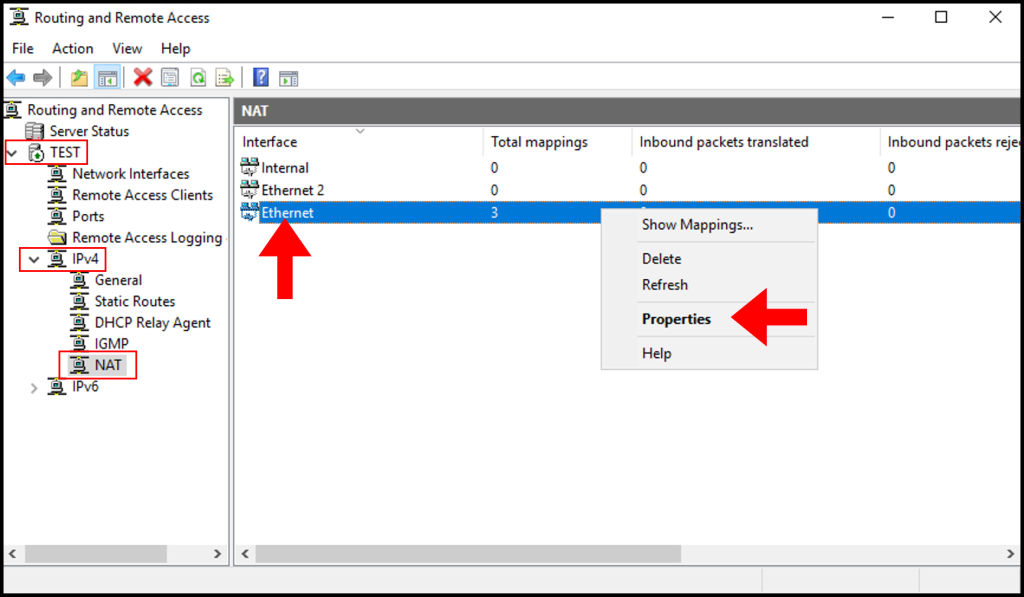
To be able to use Remote Desktop to access the server and have VPN service running simultaneously, we will need to allow the Remote Access port over a Public Network Adapter.
1. In the Routing and Remote Access, expand the server name, IPv4, and Nat from the left-hand side as seen below. In the middle screen, right-click on the Public Network Adapter. Then, select Properties.
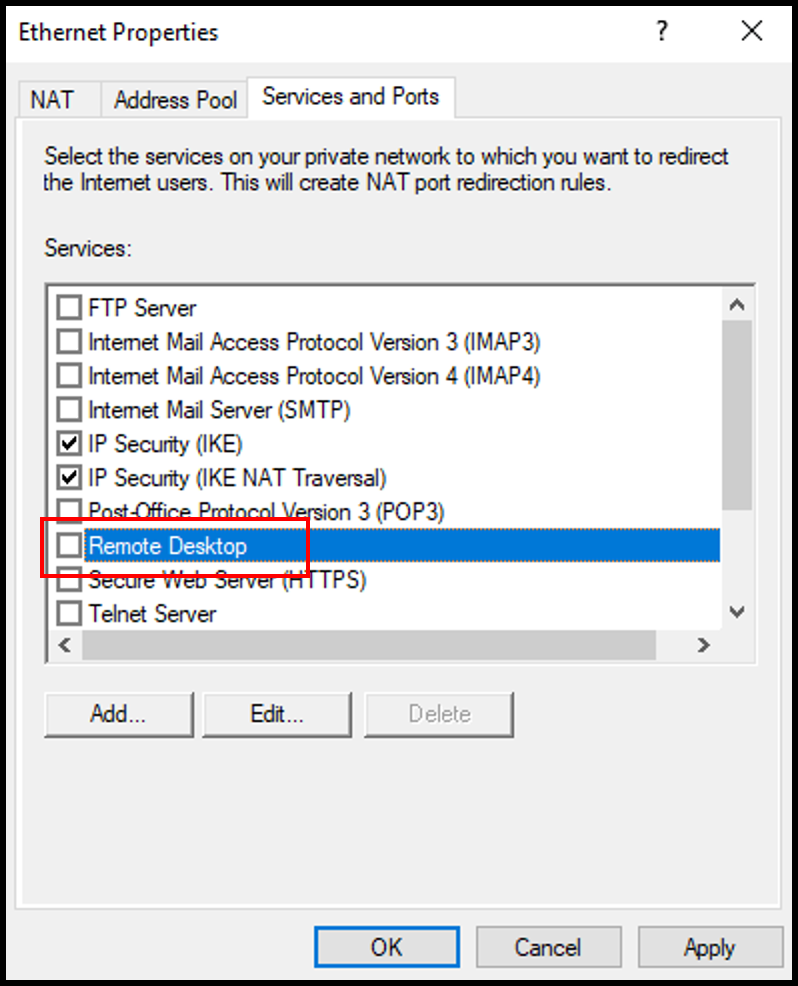
2. In the Ethernet Properties window, navigate to the Services and Ports tab. Then, scroll down and select Remote Desktop.
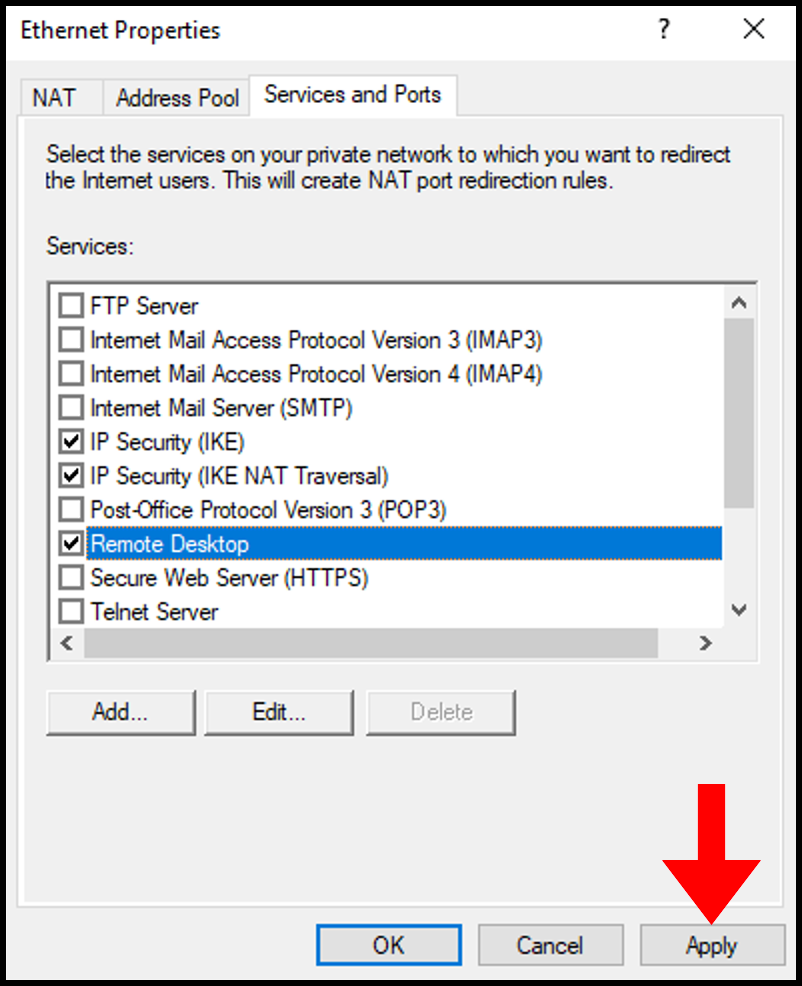
3. In the pop-up window, enter your server’s public IP address in the Private address section. Click OK to continue.
4. Once done, click Apply and OK on the Ethernet Properties screen to save and close the window.
Allow VPN Remote Access to Users
In order to allow other devices to connect to our VPN server we will need to allow Network access permissions for certain users. In this guide, we will be allowing the user Administrator network access.
1. First, open Computer Manager by searching in the Windows search function.
2. In the Computer Management window, expand Local Users and Groups from the left-hand menu, then select Users. In the middle screen, right-click Administrator and click Properties.
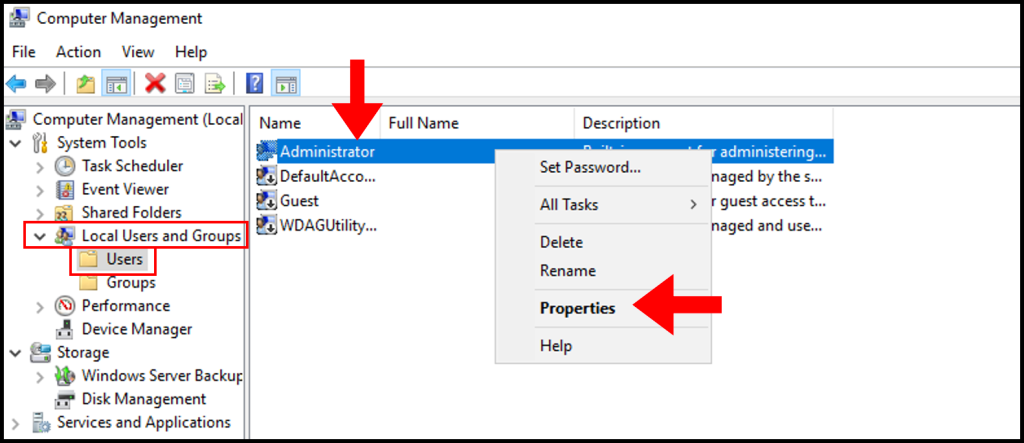
3. In the Administrator Properties window, navigate to the Dial-in tab. Then under Network Access Permission, click Allow access. Now click Apply and OK to save and close the screen.
Allow VPN Ports through Windows Firewall
In this section, we will be going over how to allow VPN through the Windows server firewall. If this is not done, VPN clients will not be able to communicate with the VPN server.
1. First, open Windows PowerShell through the Windows search function.
2. Next, in the PowerShell terminal enter the following command and click your Enter key.
New-NetFirewallRule -DisplayName "VPNTCP" -Direction inbound -Profile Any -Action Allow -LocalPort 1723,1701,443 -Protocol TCP
New-NetFirewallRule -DisplayName "VPNUDP" -Direction inbound -Profile Any -Action Allow -LocalPort 500,4500,50,1701 -Protocol UDP
New-NetFirewallRule -DisplayName "GRE" -Direction inbound -Protocol 47 -Profile Any -Action Allow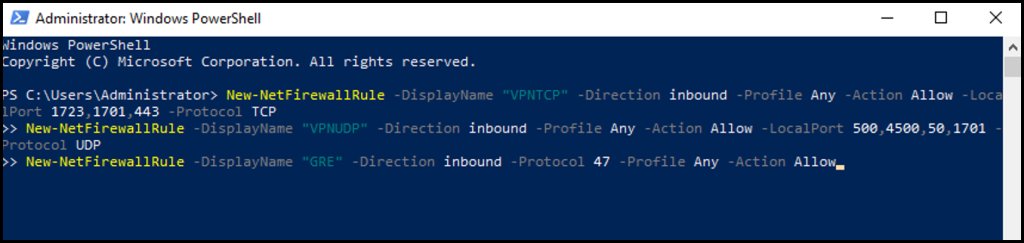
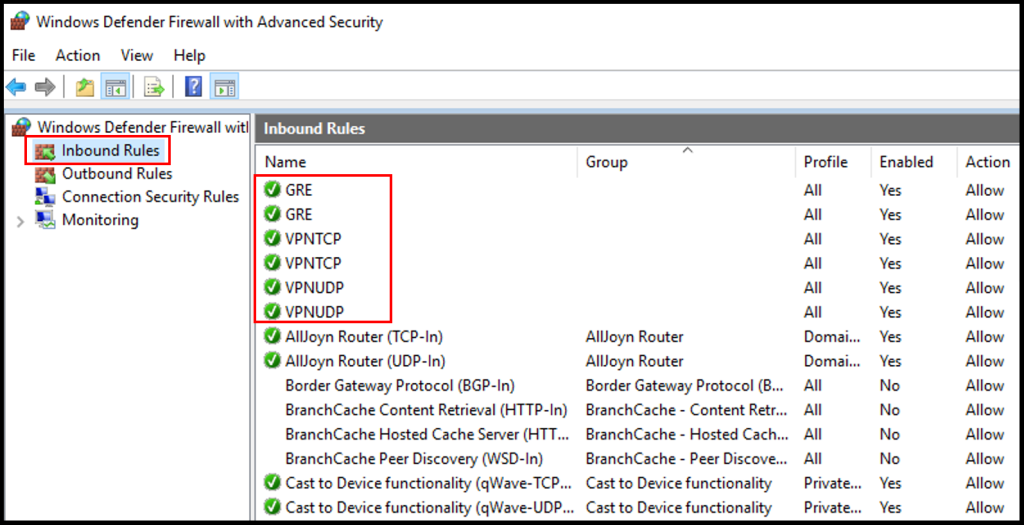
3. To confirm this worked, we can check the Windows Firewall Inbound where we can see the ports are allowed. Search for Firewall in the Windows search function and click Windows Defender Firewall with Advanced Security.
4. Once the Windows Defender Firewall window is open, check that GRE, VPNTCP, and VPNUDP have green check next to them. Now we have successfully completed how to set up PPTP/L2TP VPN on Windows Server.
Connecting to PPTP/L2TP VPN on Windows
In this article, we will go over how to connect to the VPN server on your Windows device and test that the VPN configuration is working.
1. On your Windows device, search for VPN in Windows and click Change virtual private networks (VPN).
2. Then in the next window, click the button Add a VPN connection.
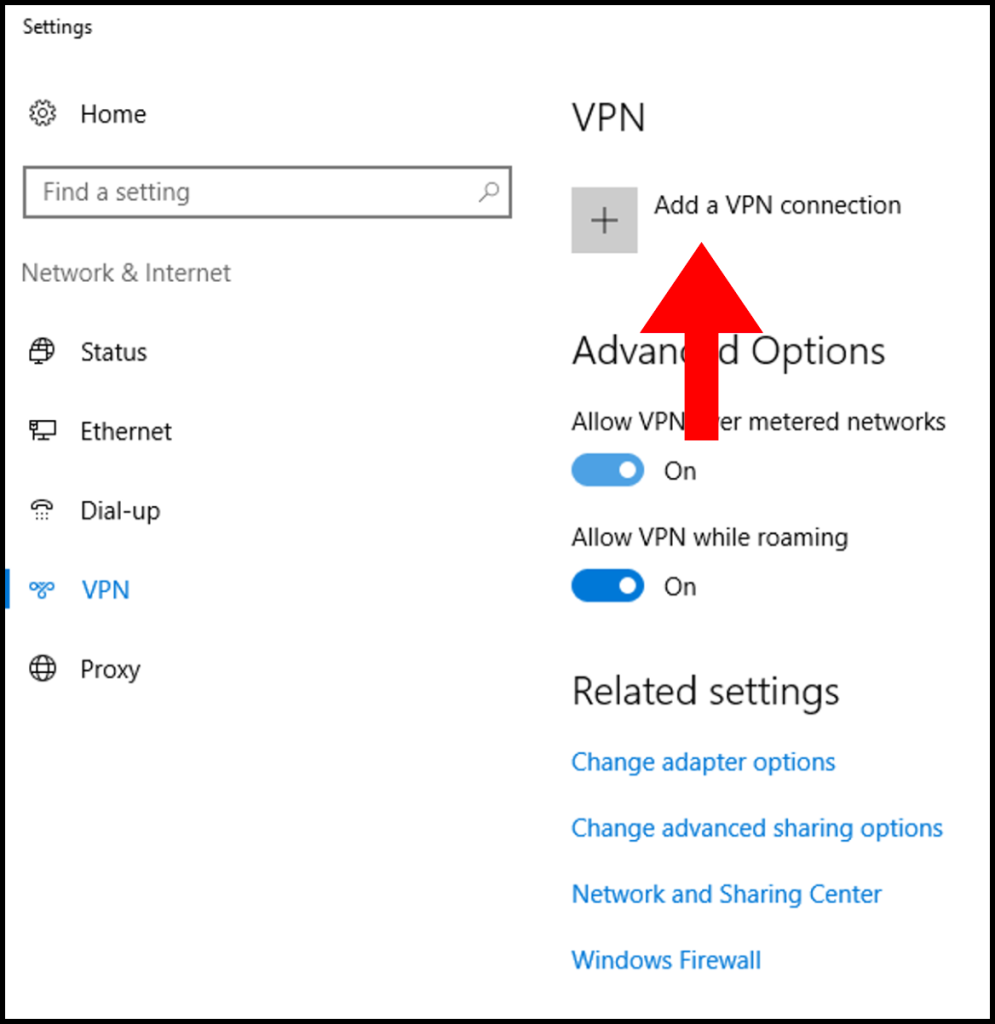
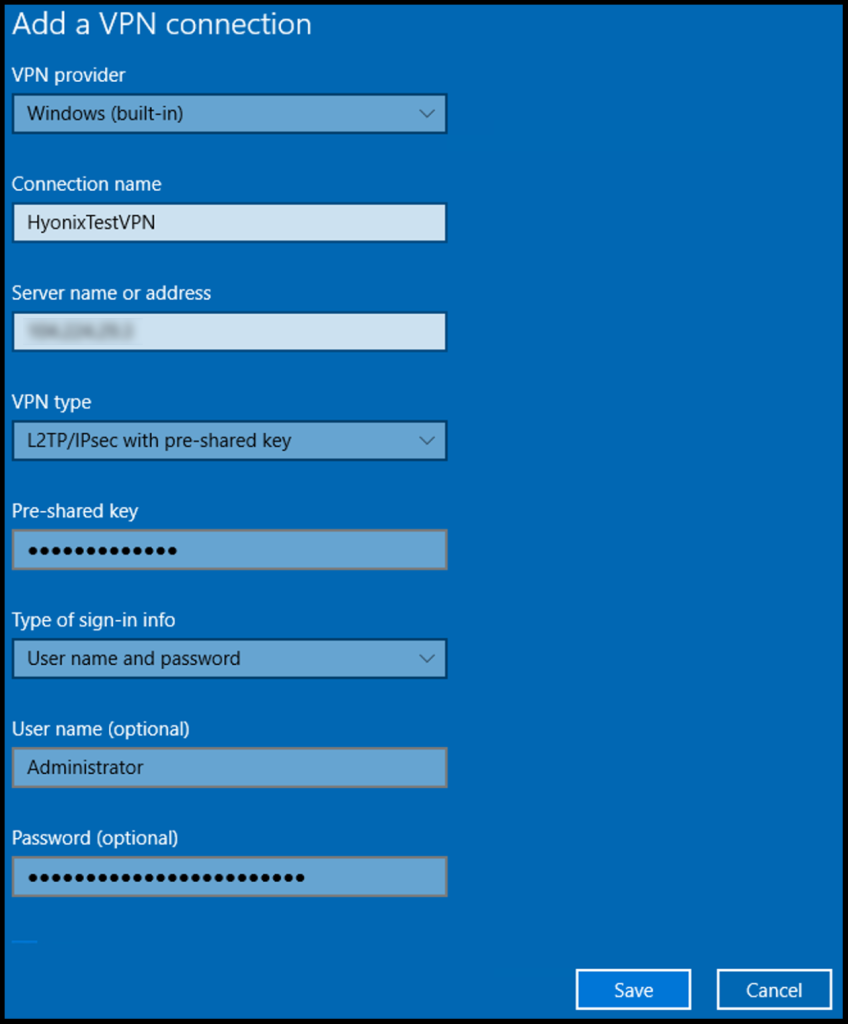
3. In the next screen, fill out the below information as shown below. Once done, click Save.
VPN Provider: Windows (built-in)
Connection Name: Any name you’d like to label it as
Server name or address: The IP Address of the VPN server
VPN Type: L2TP/IPsec with pre-shared key
Pre-shared key: Enter the pre-shared key we defined in an earlier section
Type of sign-in info: User name and password
User name (Optional): Login username of the VPN server
Password (Optional): Password of the VPN server
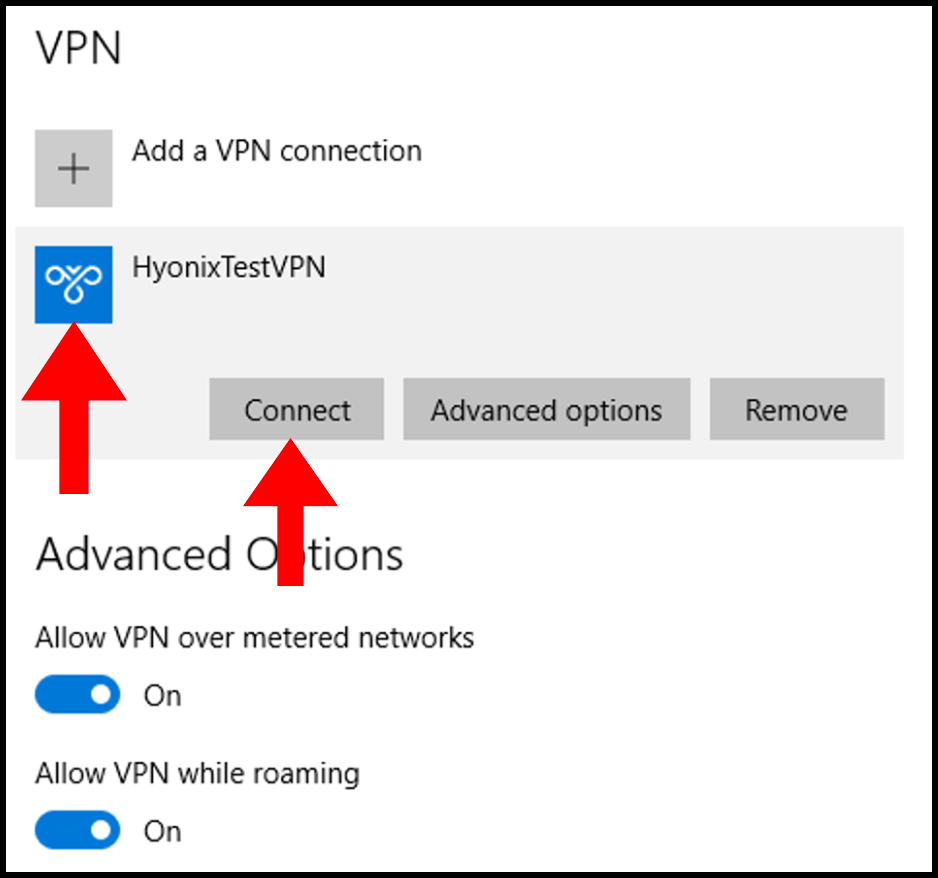
4. Next, click the VPN that we have added and then click Connect to connect to the VPN.
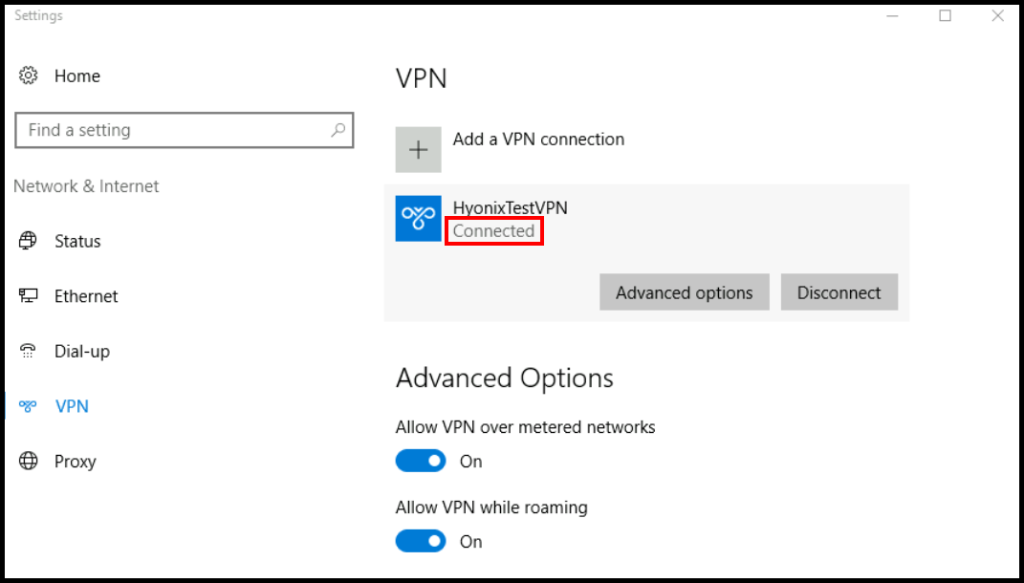
5. Finally, you will be able to see that we are connected to the VPN when it says Connected under the VPN name as seen below.
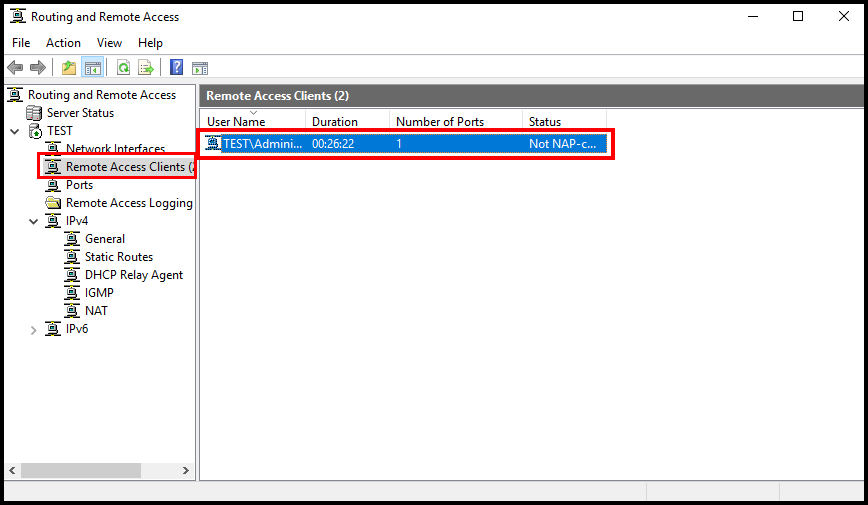
6a. One way to verify that you have successfully connected to the VPN server is by connecting to the VPN server and opening the Routing and Remote Access window and selecting Remote Access Clients. You will then see a connected client to the VPN server.
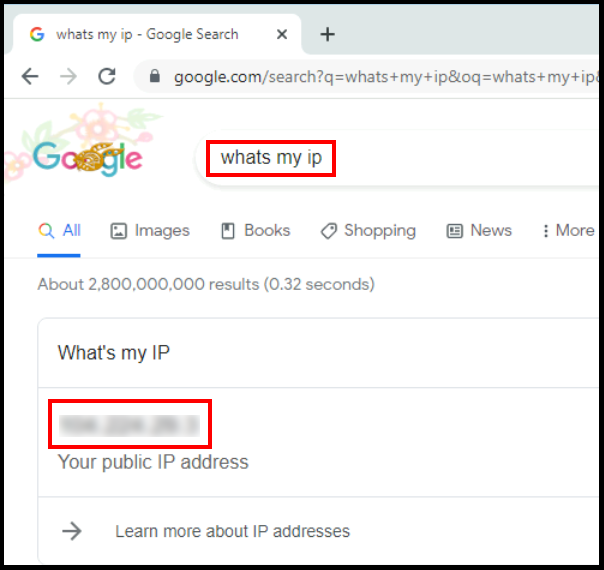
6b. Another way to verify the VPN connection is by checking the IPv4 address on the client device. You can do this by going on your browser and looking up whats my ip? and the IP that is shown should be the VPN server’s IP address.
Connecting to PPTP/L2TP VPN on macOS
In this article, we will go over how to connect to the VPN server on your macOS device and test that the VPN configuration is working.
1. To start, use the finder feature (cmd + space-bar) to search and open Network – System Preferences.
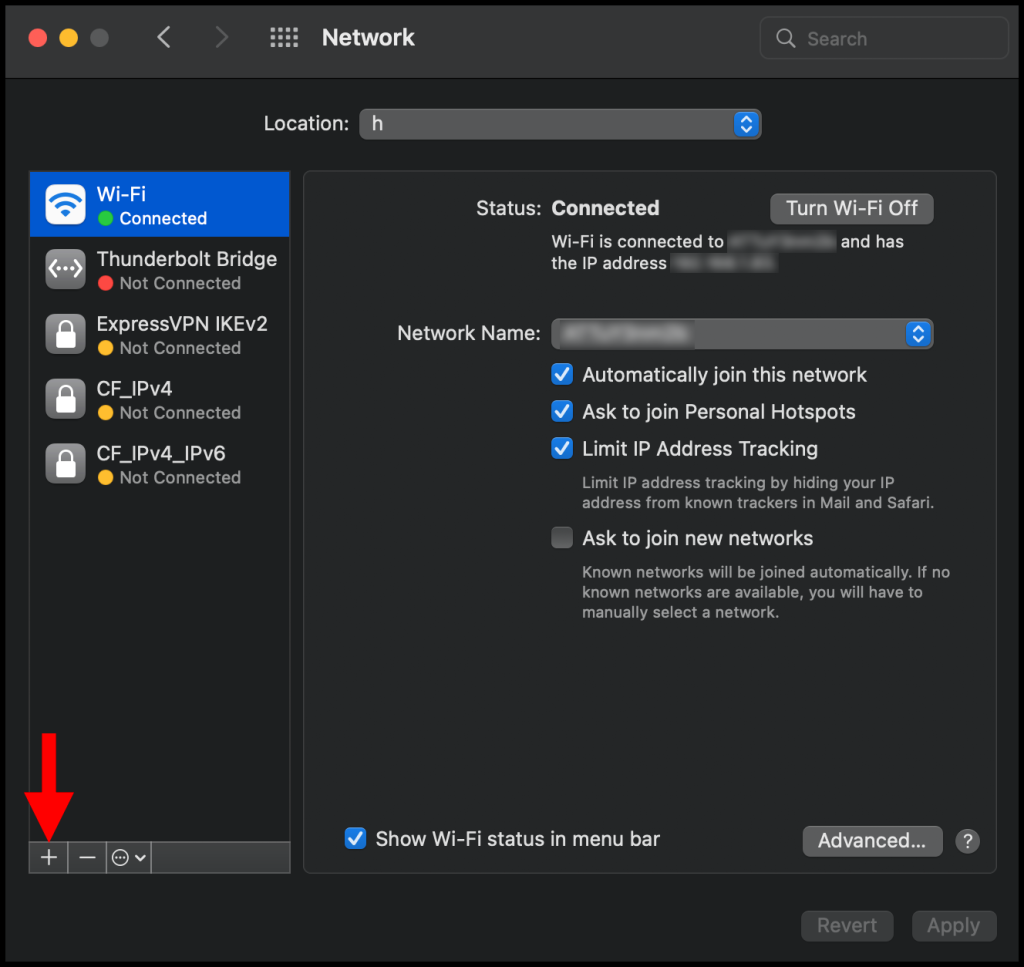
2. In the Network window, click the + button on the bottom left corner as seen below.
3. In the pop-up, click the drop-down next to Interface and select VPN from the menu.
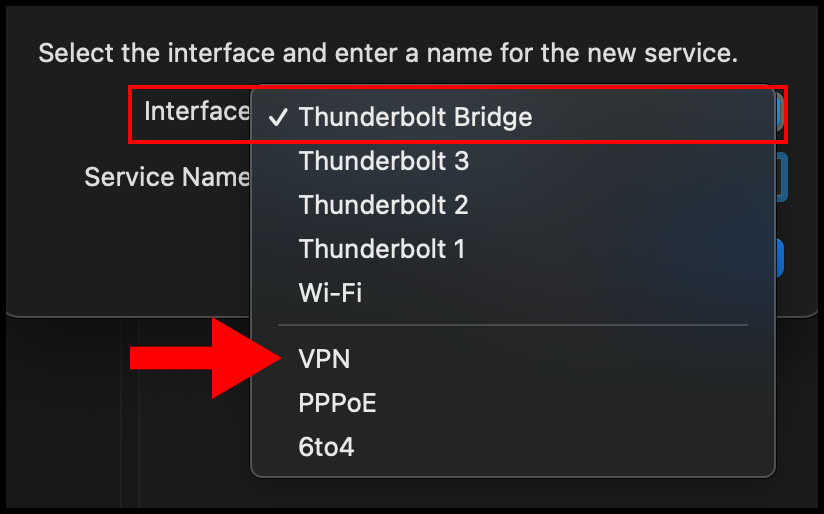
4. Then select the drop-down for VPN Type and select L2TP over IPSec. Optionally, you can also enter a custom Service Name. Click Create to move on.
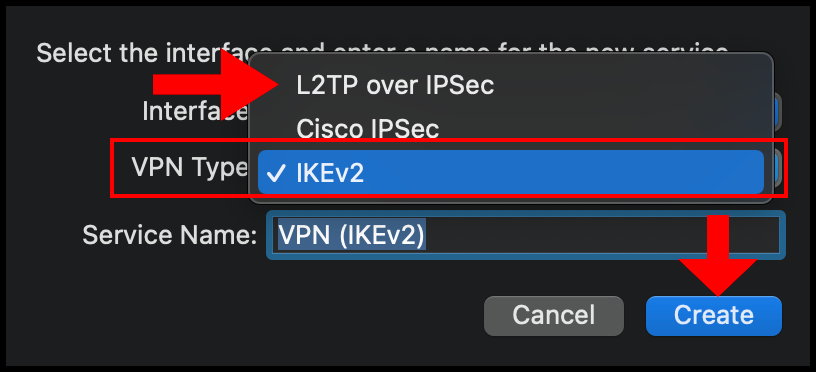
5. Then in the next configuration window, enter the VPN server’s IP address in the Server Address text field and enter the username you use to log in to the VPN server in the Account Name text field. Once you’re done click Authentication Settings to continue the setup.
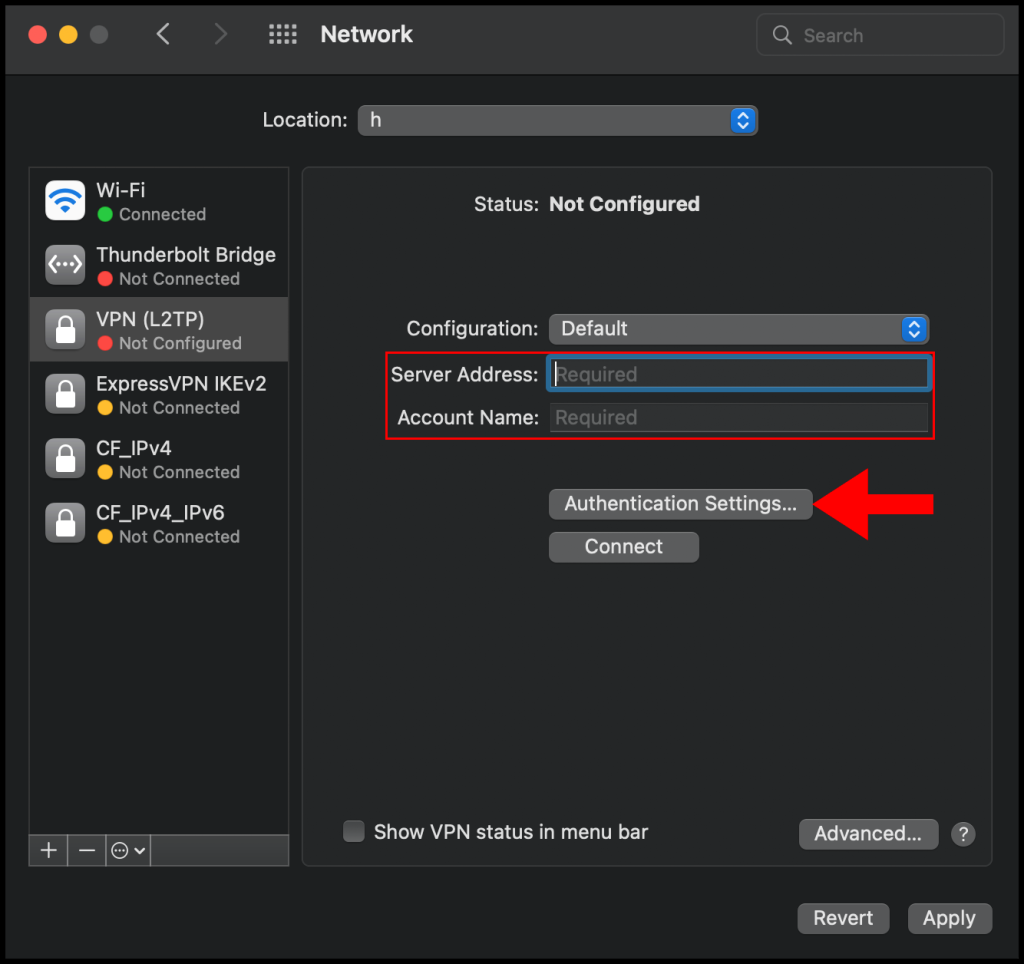
6. In the Authentication Settings menu, select Password for User Authentication and then enter the password you use to log in to the VPN server, select Shared Secret under Machine Authentication and enter the pre-shared secret key you set on your VPN server in the earlier sections. Click OK to finish configuring the Authentication Settings.
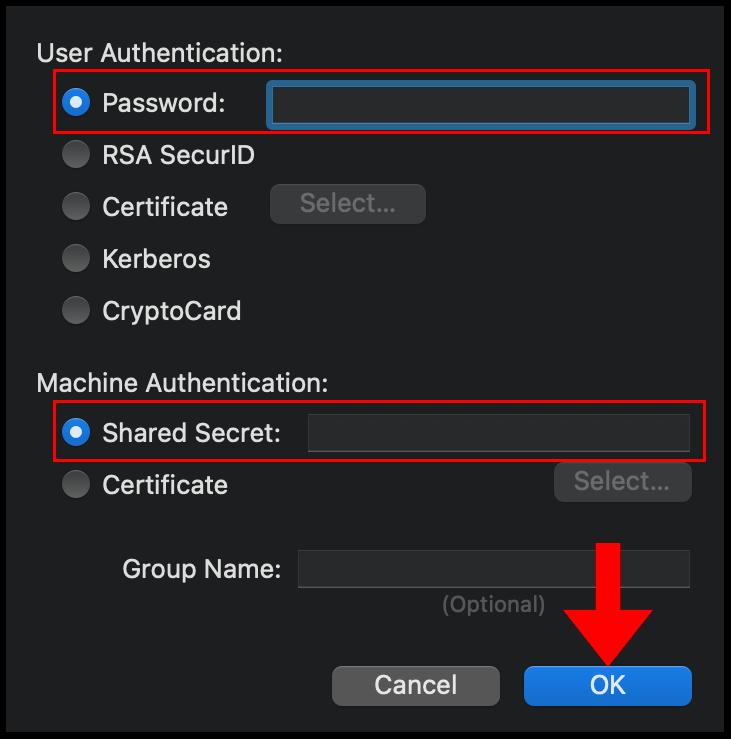
7. Now click Advanced to go to the advanced network settings.
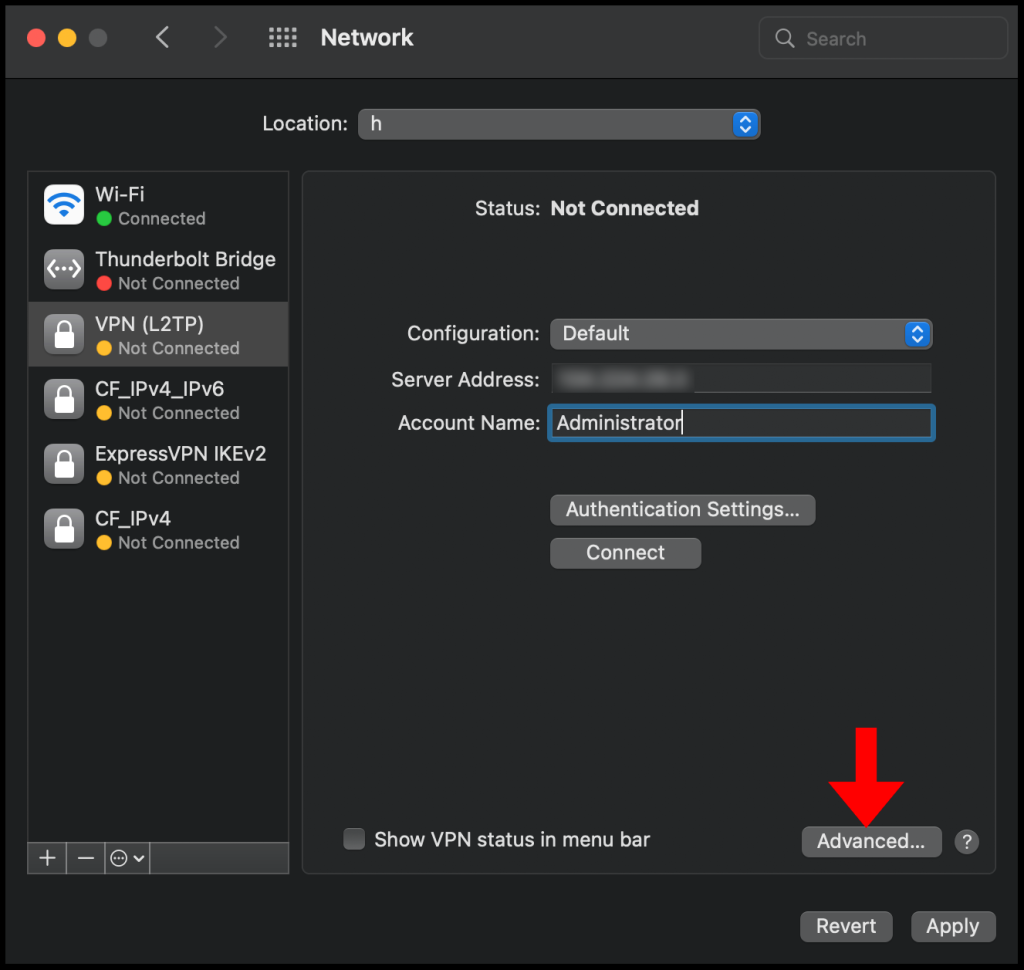
8. In the Advanced window, check the box next to Send all traffic over VPN connection and then navigate to the DNS tab.
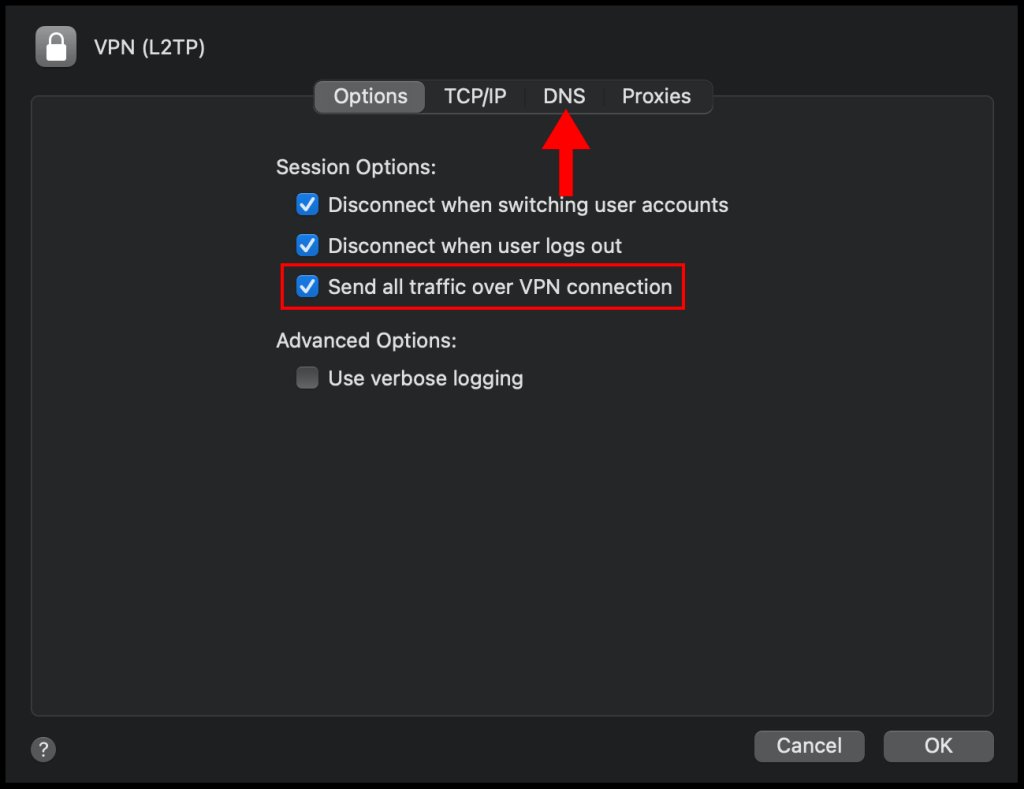
9. On the DNS section, click the + button on the left-hand corner and add the following DNS servers 1.1.1.1 and 1.0.0.1, then click OK to close out of the window.
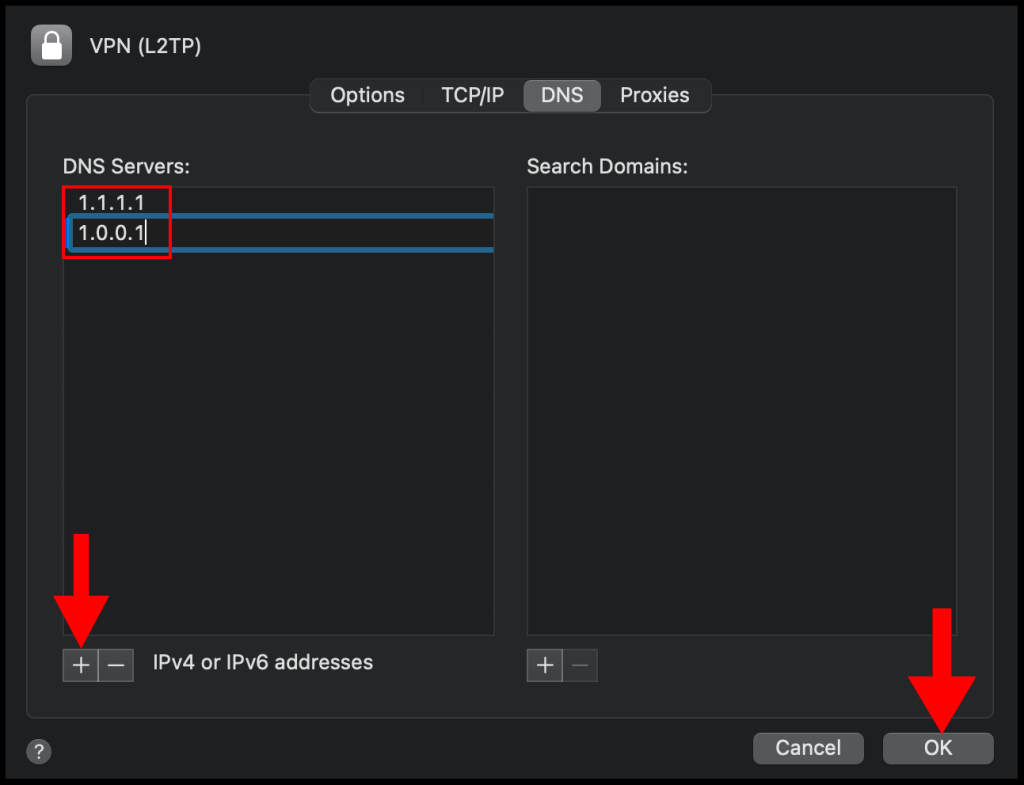
10. Lastly, click Apply and then click Connect to connect to your VPN. We have successfully set up and connected to the VPN on a macOS device.
Preface
We already posted an article to set up a VPN on Windows Server 2019 using Secure Socket Tunneling Protocol (SSTP) using a third-party certificate. This one, we are going to discuss ‘How to Setup VPN using PPTP’ based article . The Point to Point Tunneling Protocol using the Generic Routing Encapsulation feature along with tunneling over TCP/IP wrapped transmission. The PPTP creates a tunnel on TCP/IP and transfer the packets securely—this very old and reliable method of transferring or accessing the private network over the internet. We can deploy this method to connect a Home or a user with a laptop to access their home network or small office network efficiently and quickly.
Configuring Point to Pointing Tunneling Virtual Private
Network on a Windows Server 2019 is straightforward. We can use this method of
deploying a VPN where the Secure Socket Layer type of VPN is not possible. In
this method of configuring VPN, we need to open the port 1723 and enable a
feature called Generic Routing Encapsulation (GRE) on the edge firewall or
router under security settings. I am going to explain the step by step and
cover the entire setup process from install and configure Remote Access Role to
configure Client device to connect the network where we have installed the PPTP
VPN.
So, let get to the server and start the Remote Access Role
installation and subsequently look at configuring VPN policy on the Network
Policy Server on the Windows Server 2019. If you are ready to take a
configuration task, we are here, to begin with, so let us get started.
- Add Remote Access Server Role
- Configure Remote Access with VPN Access
- Configure Remote Access Settings for VPN
- Configure Dian-in connection on the user object
- Configure Dial-in policy on Network Policy
Server - Crete VPN network connection on Windows 10
device - Connect VPN Server over the Internet
Add
Remote Access Server Role
The first step in deploying a VPN server is Adding the
Remote Access Server Role on the server—the remote access server role to be
installed by going to the Server Manager Dashboard. Once the Server Manager
windows would open, click on the Add Roles and Features, and the ‘Add Roles and
Features’ wizard would start, and we can go through this wizard to complete the
Remote Access role installation.
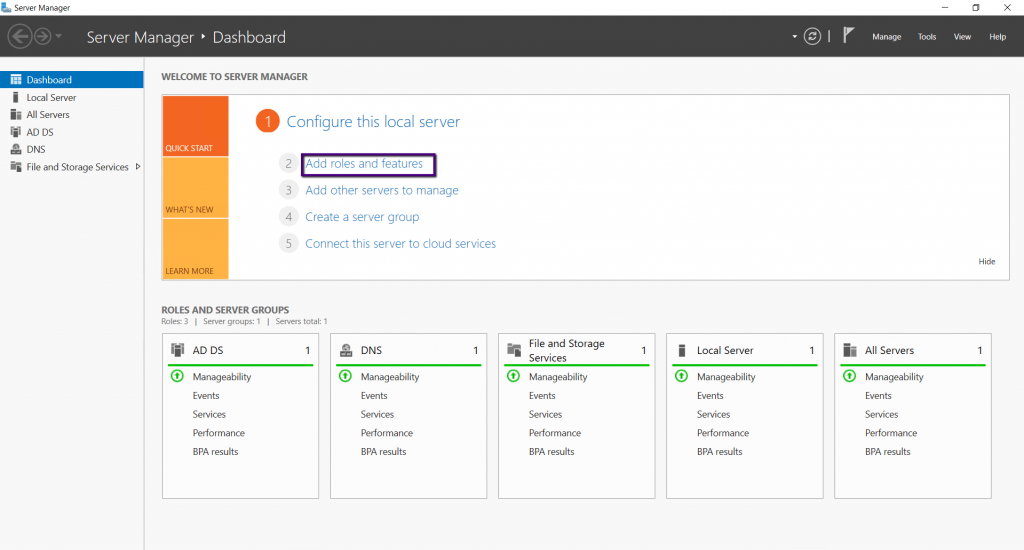
The wizard will start with instructions on using this tool
to add the roles and features. If you don’t want to see this page, you can
click the checkbox next to ‘Skip this page by default,’ and you won’t be
prompted with this page anymore.
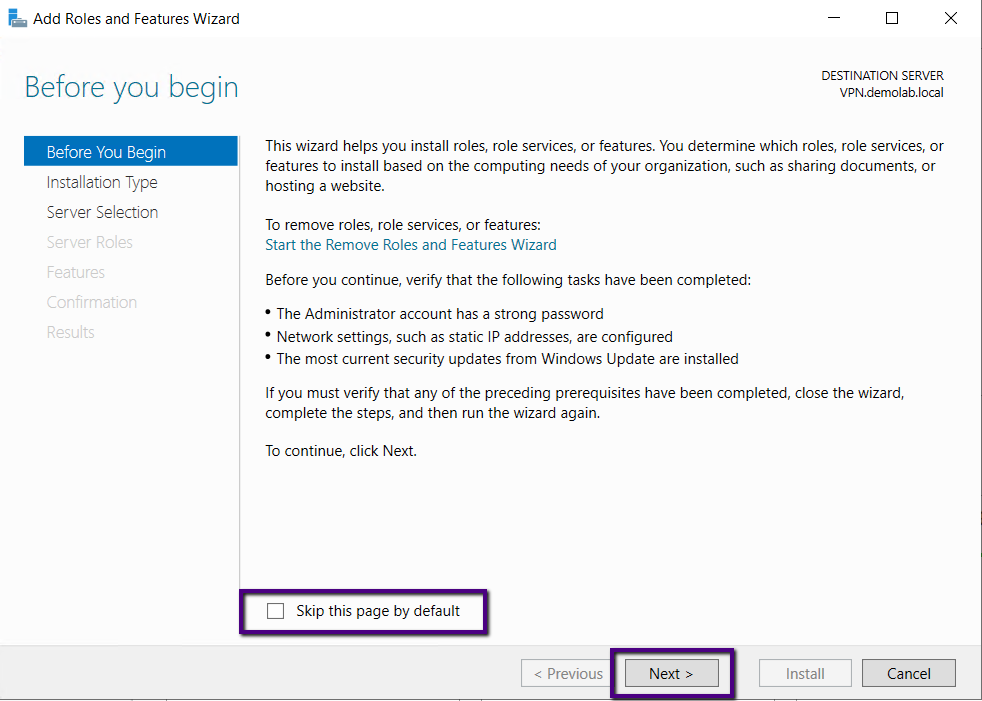
In this wizard, we are going to use the role-based
installation to add this role, so select Role-based or Feature-based
Installation to begin with and click Next to continue.
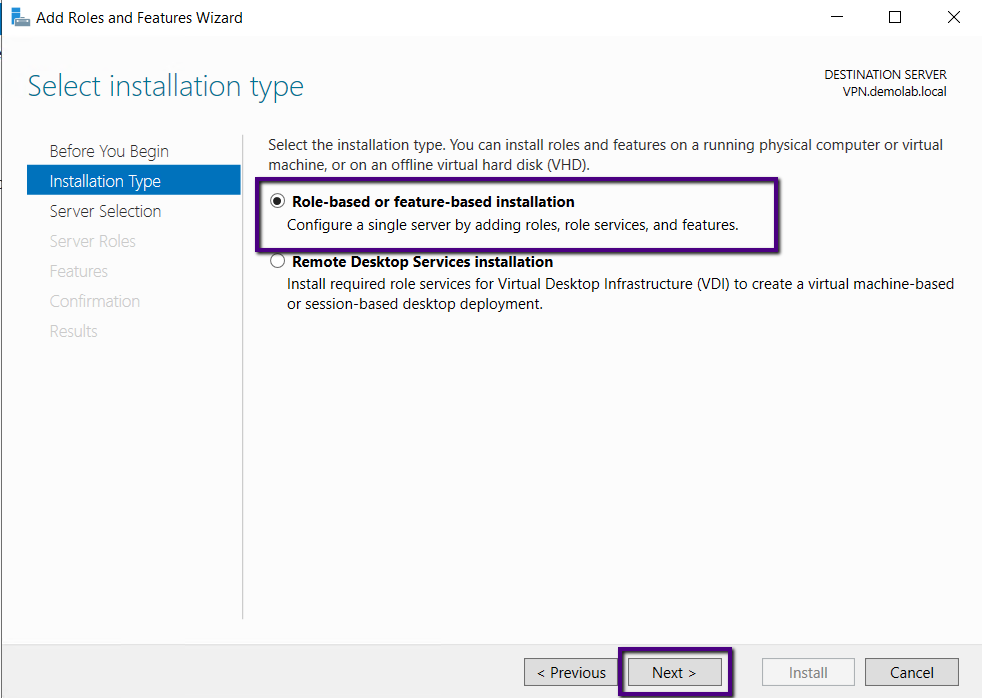
Make sure the local server in the server pool and select it
and click Next.
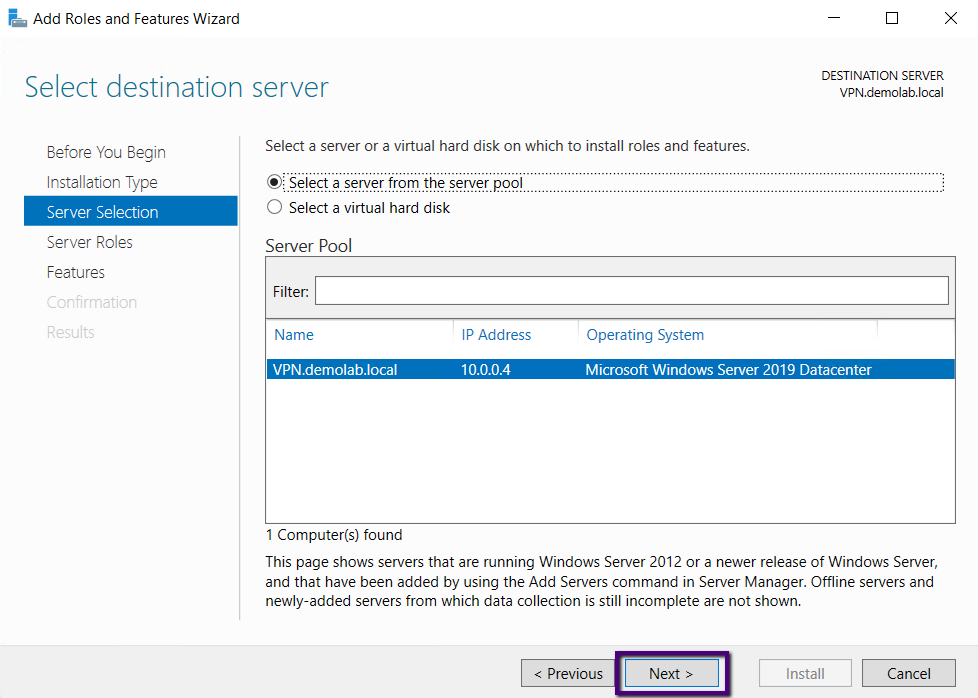
In the Select Server Role page, select Remote Access
checkbox, and click Next.
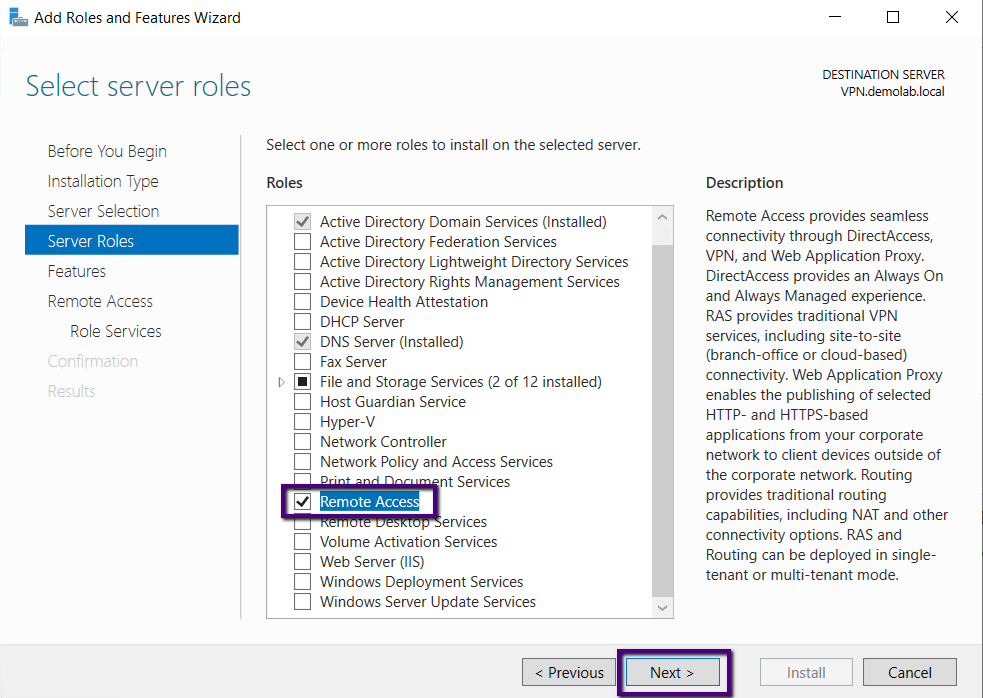
On the next page, leave the Features as it is and click
Next.
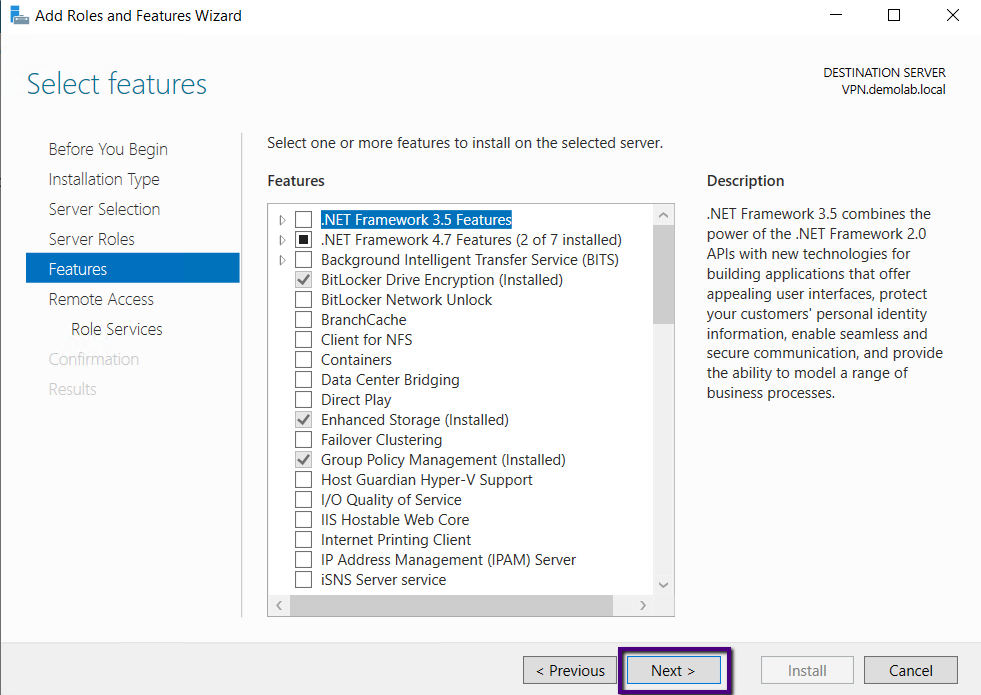
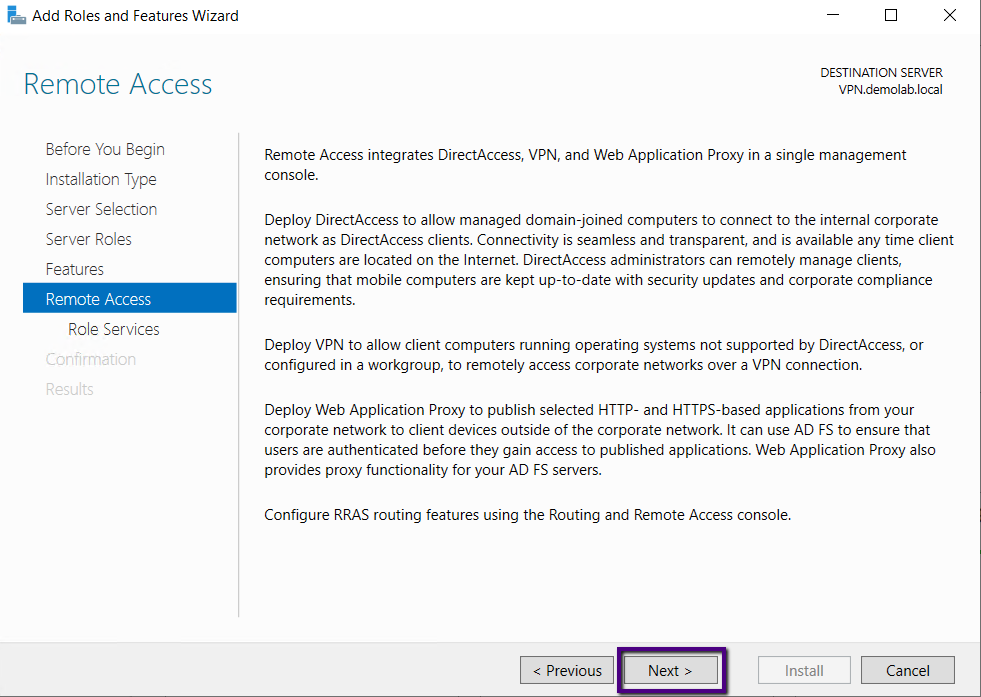
If you need more details, you may go through the details
about remote access on this page, and once you are ready to move, click Next.
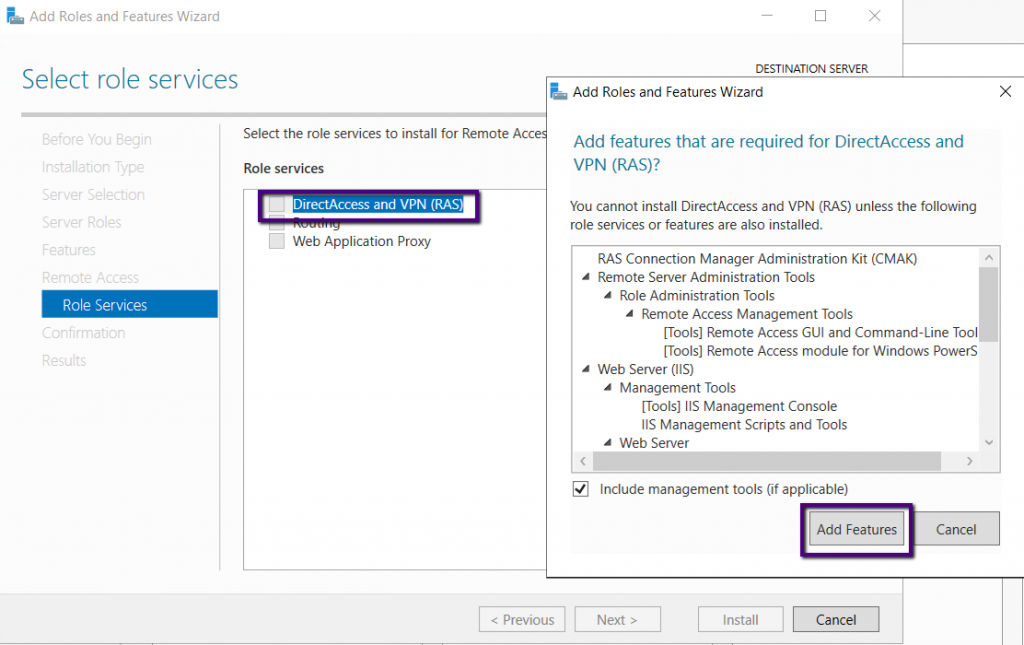
This step is significant, select the Direct Access and VPN
(RAS) alone, and you would be prompted with related features on the pop-up and
click Add Features, which will return to select the role services page.
We have selected the roles services and its feature, and we
are right to move to continue, click Next.
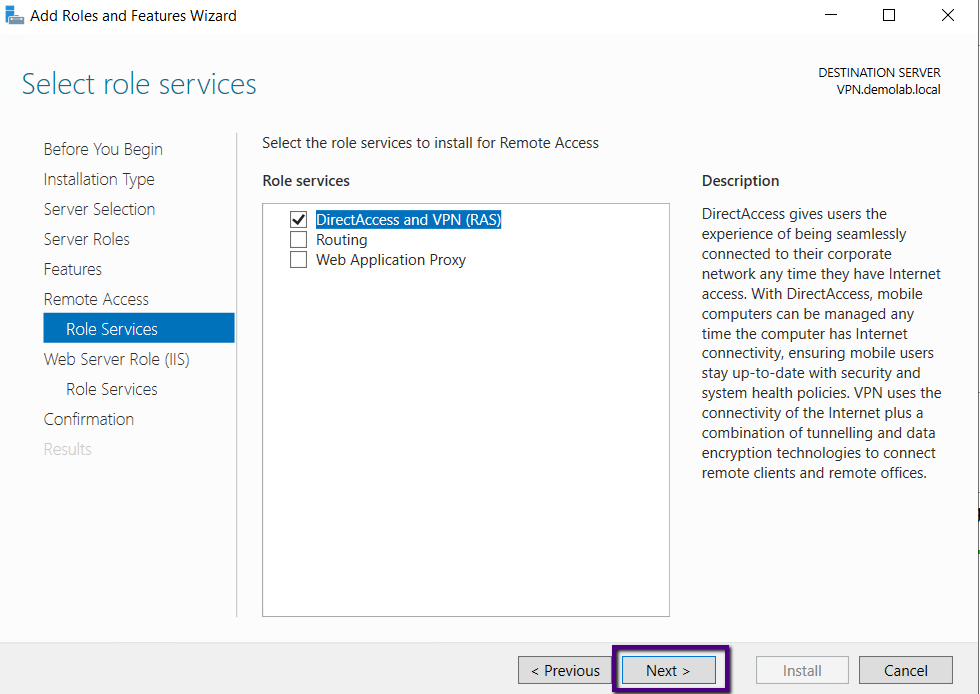
The next page is an information page, and it describes that
adding this role service also install the Web Server (IIS) role, Click Next to
continue.
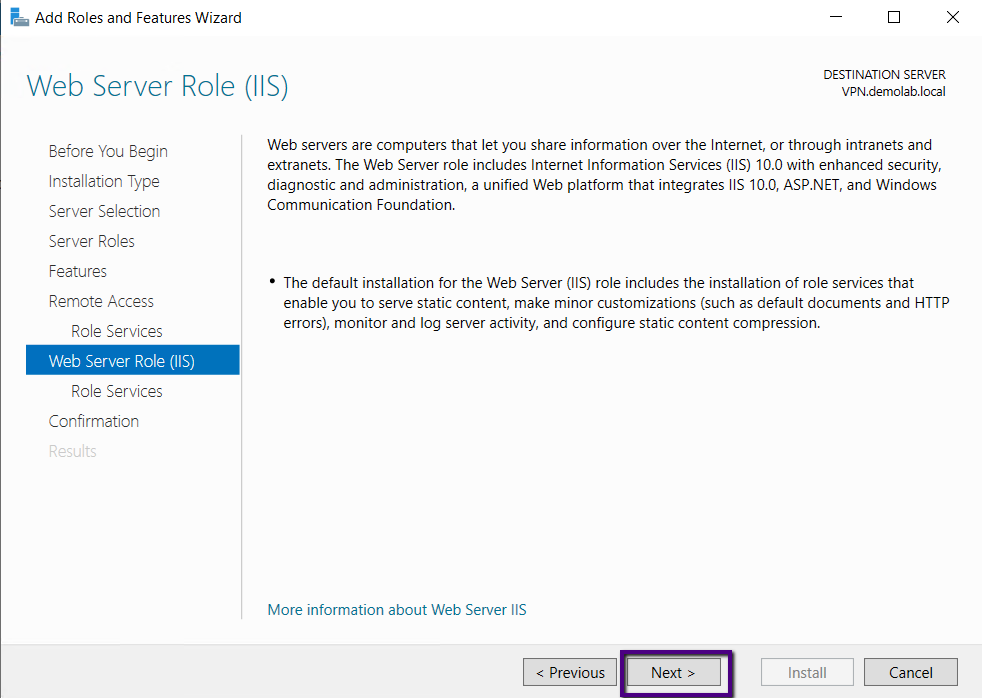
The Web Server (IIS) role will install this role services,
leave the default selection, and click Next.
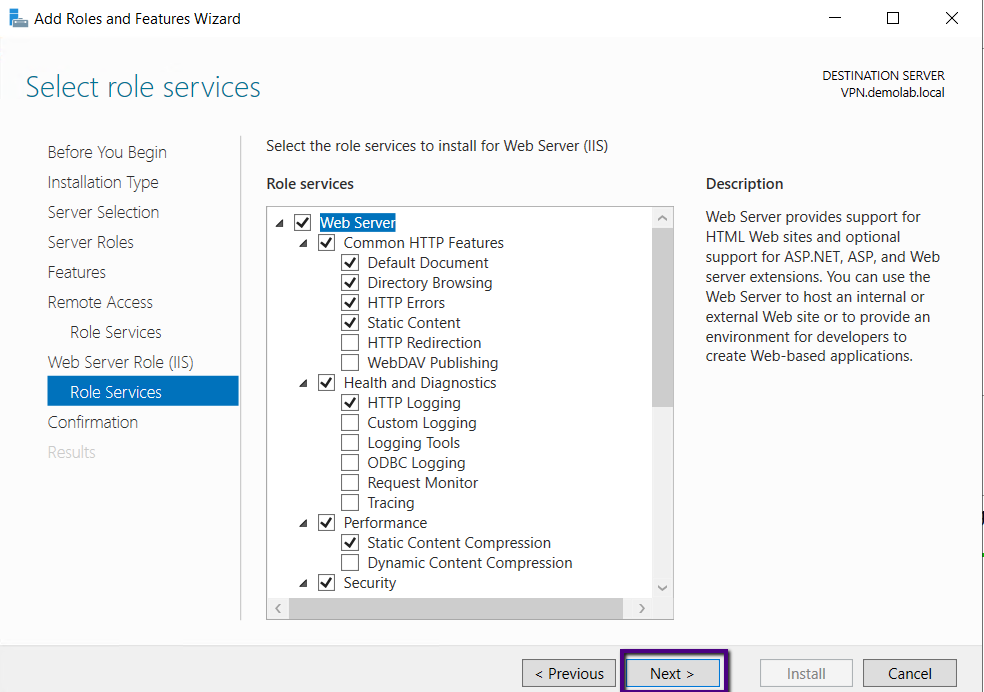
On the confirmation page, verify that the Roles mentioned
above and Role Services correct and click Install to start the Remote Access
role installation. Sit back and relax for a few minutes to get the installation
to complete.
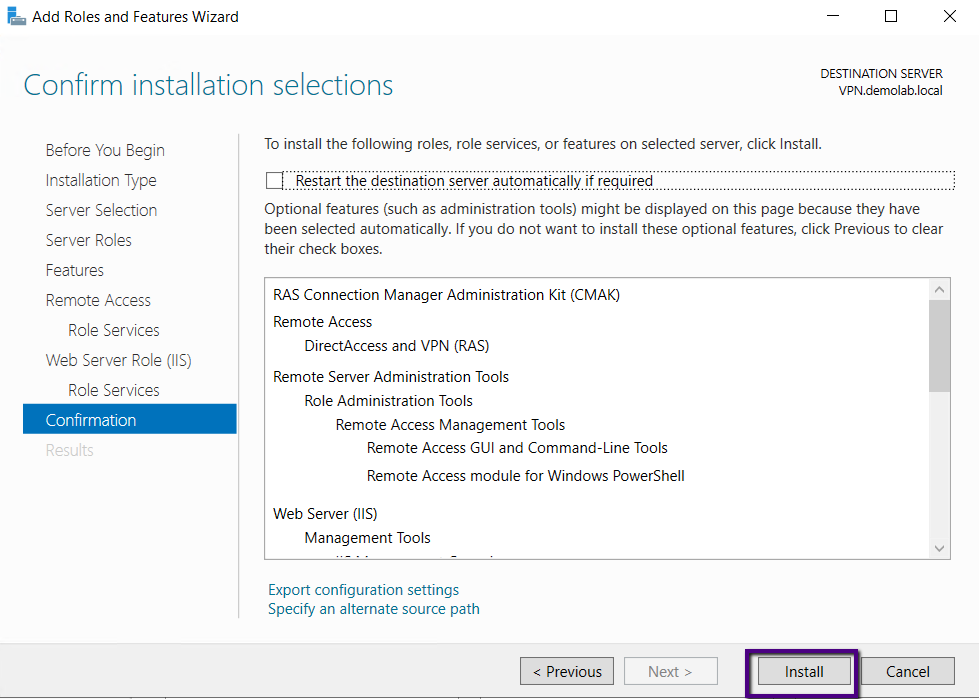
The Remote Access role installation started. Let wait till
the installation complete, and then we start the configuration.
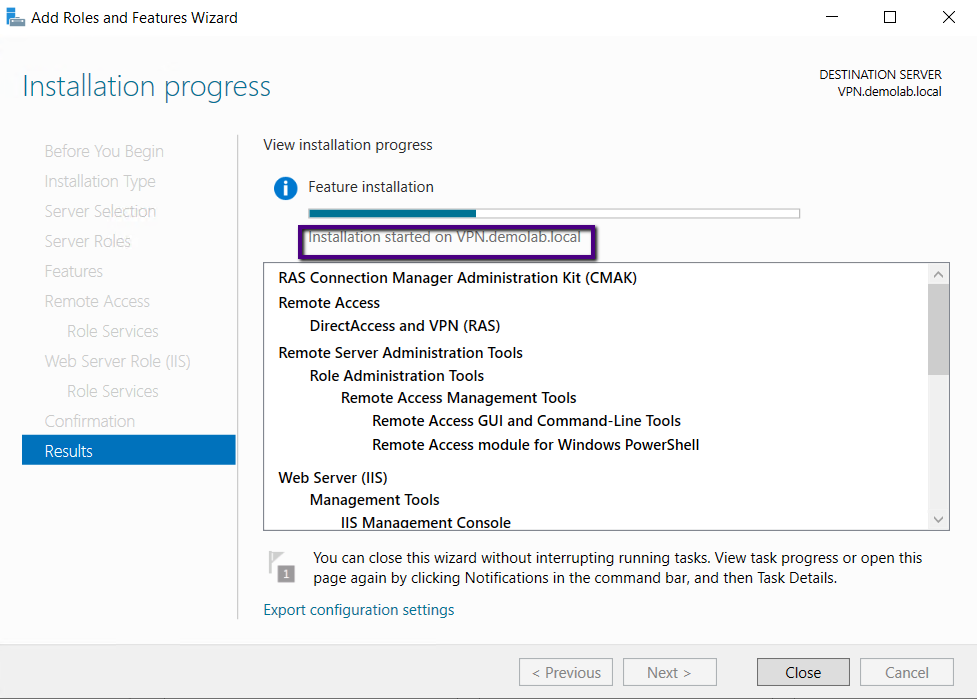
You would notice the installation succeeded message and
there is a link to open the getting started wizard to start the configuration
of the Remote Access Role, click the link.
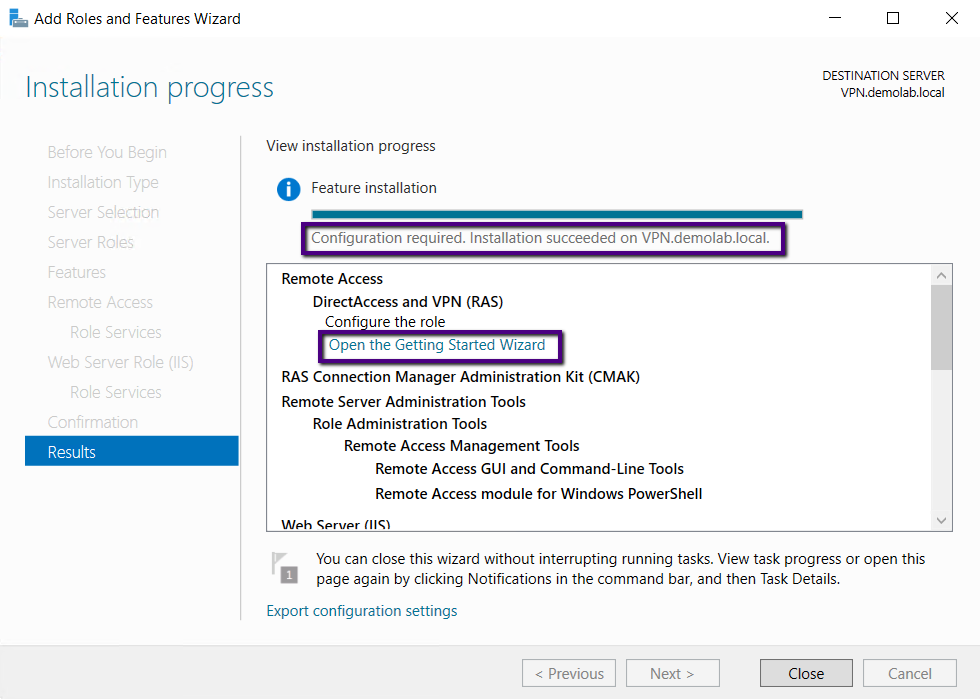
Clicking the link will start Configure Remote Access Wizard,
on the wizard click Deploy VPN only tab as in the screen below.
Configure
Remote Access with VPN Access
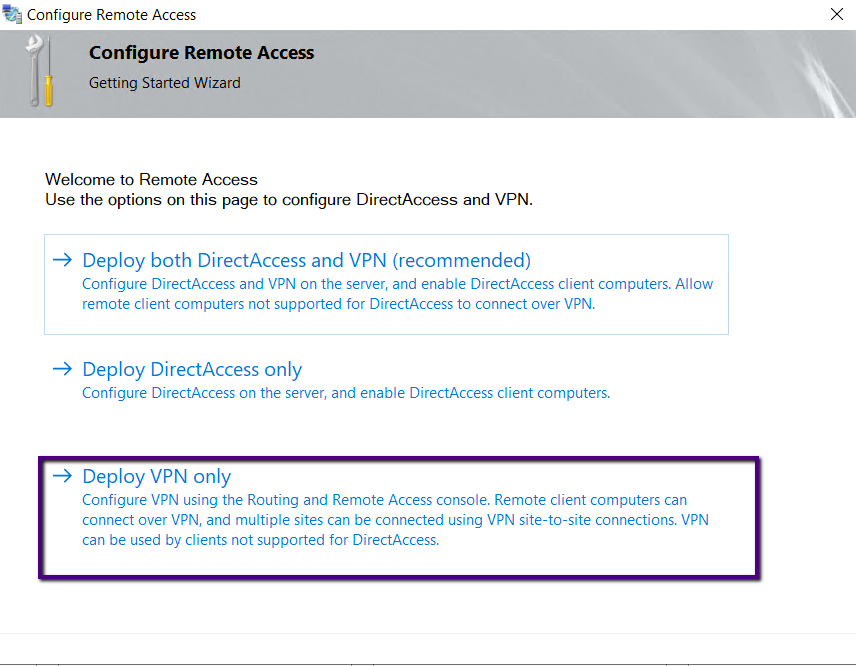
On the Configure Remote Access prompt select the Deploy VPN
Only to define the Remote Access multiple configuration methods.
The Routing and Remote Access management console will be
opened and right-click on the server node and click ‘Configure and Enable
Routing and Remote Access.’
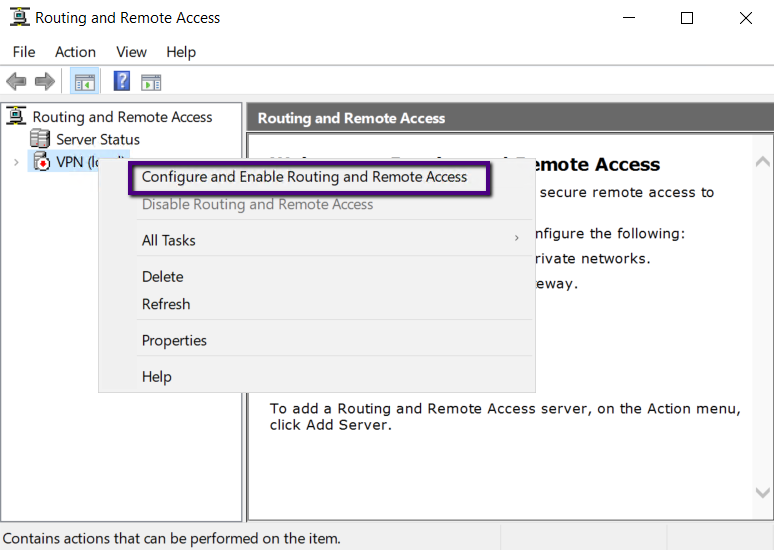
The Routing and Remote Access Server Setup Wizard will start
with a Welcome Screen, Click Next to begin the wizard.
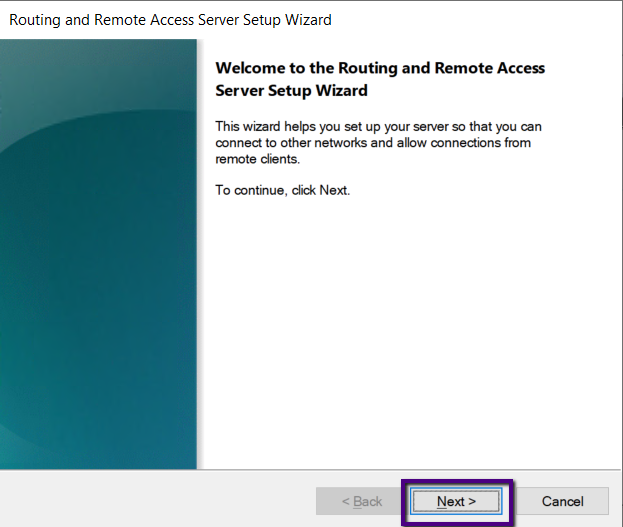
Select the Radio button next to Custom Configuration and
click Next.
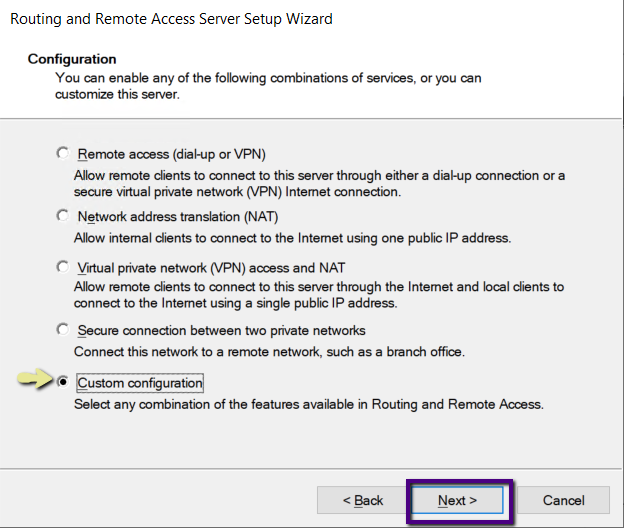
On the Custom Configuration page, select the checkbox next
to VPN Access and click Next.
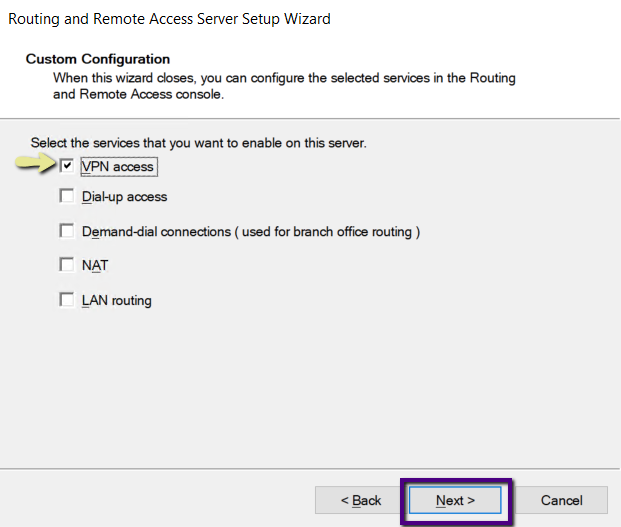
The VPN Access configuration selected on the wizard, and
that is the end of the wizard and click Finish.
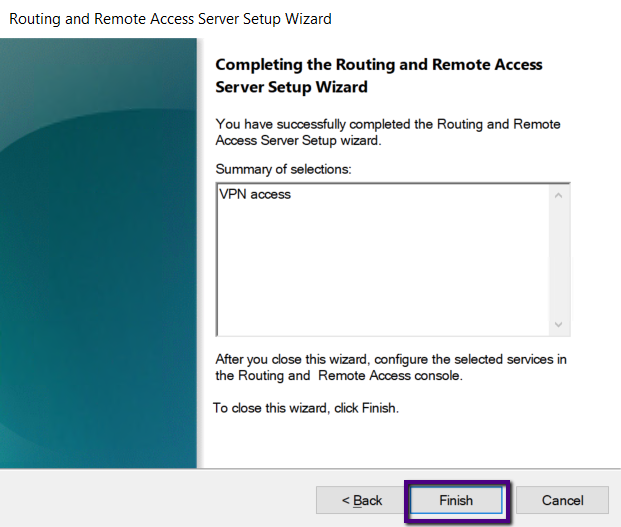
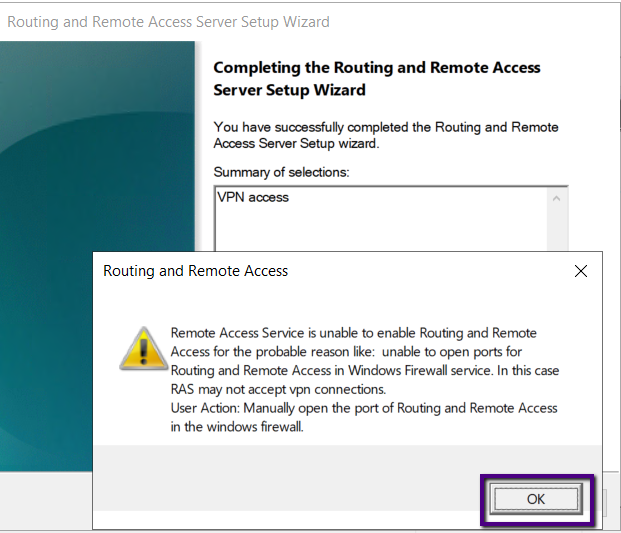
Click OK to the warning message that the Remote Access
Configuration couldn’t open the required port. We will open the port on the
Windows Firewall manually.
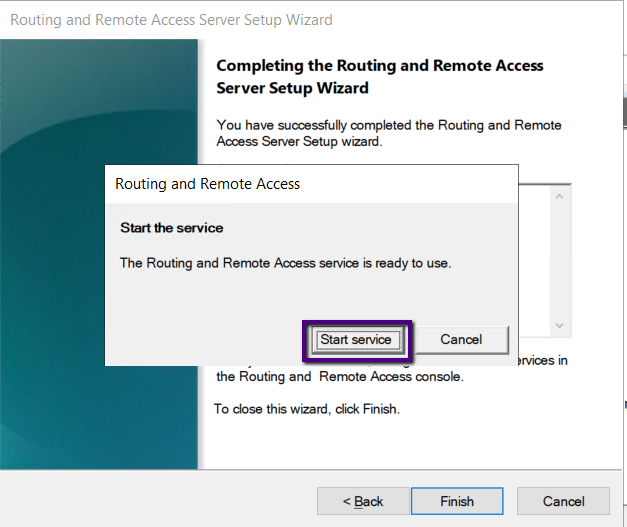
As we have configured Routing and Remote Access services
with VPN Access and the wizard will end by prompting to start service.
Once the Routing and Remote Access Service Started, you will
see a green arrow on the server node implying that the service started and
running.
Configure
Remote Access Settings for VPN
There are specific settings we need to update to set the VPN
to function securely and get the IP4 IPs to the client system.
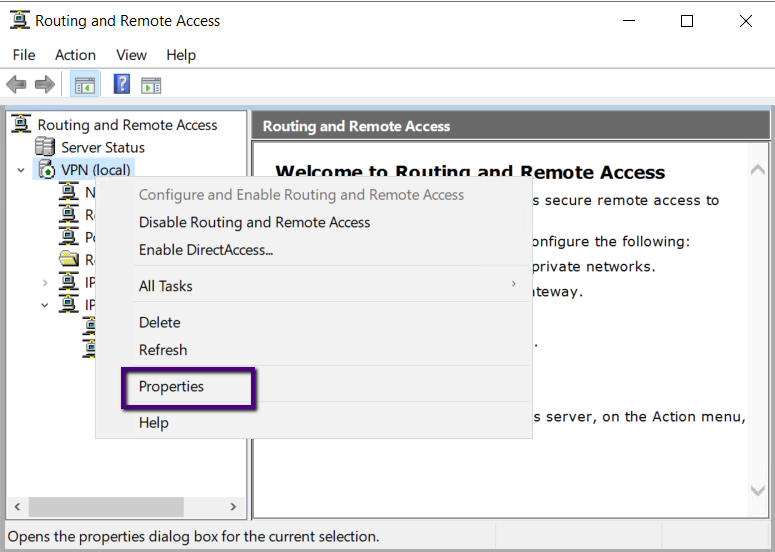
Right-click the server node and click properties as in the
screen below.
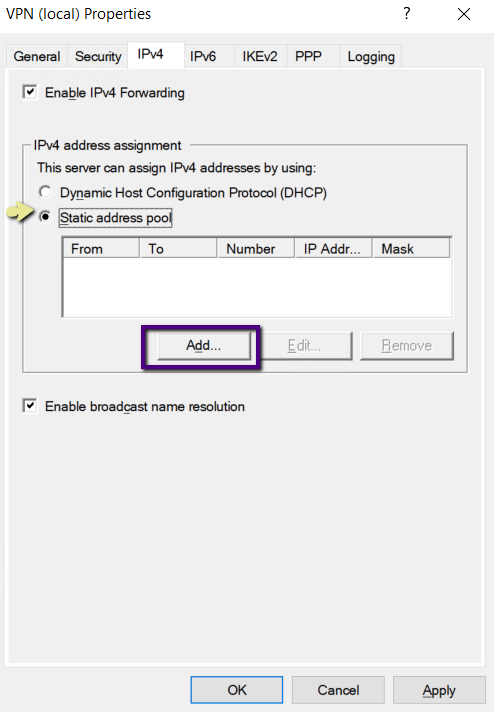
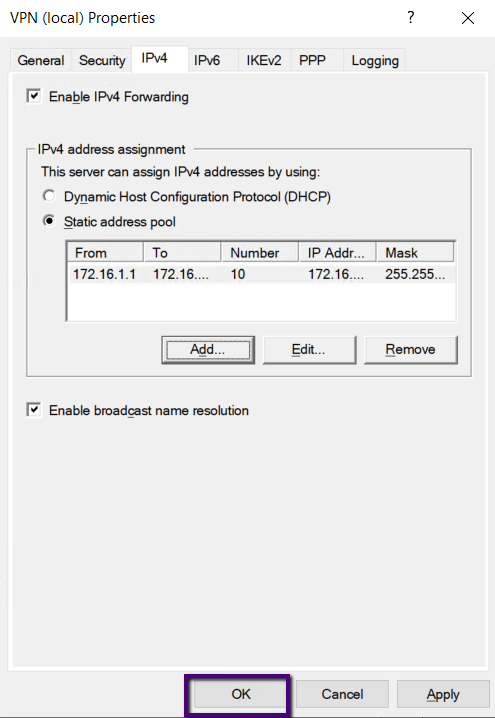
On the Remote Access, Server Properties go to the IPV4 tab
and Select the Static Address pool radio button under IPv4 Assignment and click
add to add IP address pool. Choose an IP address Pool and type start and end IP
address of the pool. The IPV4 address pool is a static one, and if you are
running the DHCP server on the server, you can leave the IP address to assign
from the DHCP server. As we are not running a DHCP service, we are creating a
static address pool in this example.
Choose IP address pool and type start and end IP address on
the Add dialog box. We have chosen 172.16.1.1 to 172.16.1.10 range to assign
the IP addresses to the VPN clients.
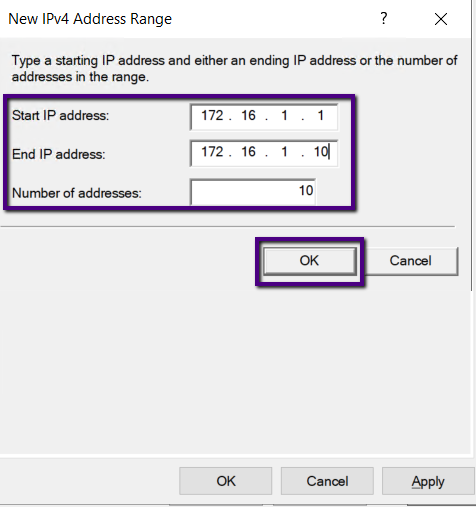
Click OK once the IP address properly typed.
How to Setup VPN using PPTP
Configure
VPN Policy on Network Policy Server
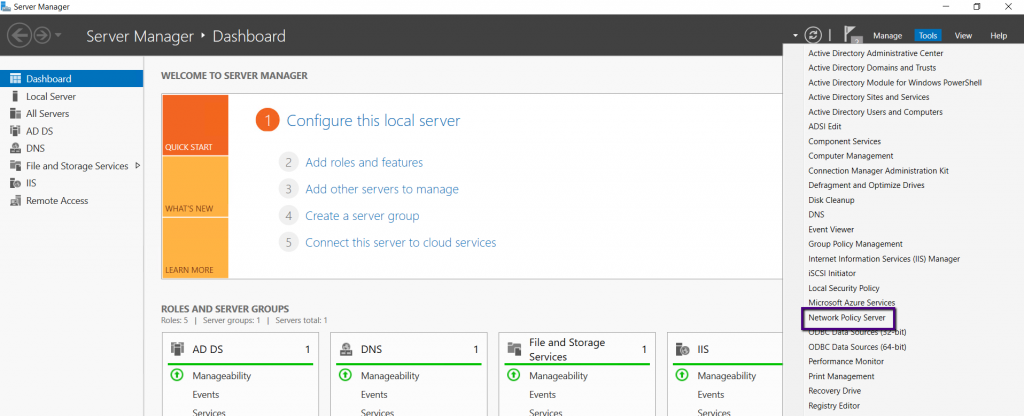
Open the
Server Manager window and on the Tools menu select Network Policy Server to
begin with configuring VPN Policy
Expand the Network Policy Server and select New to create a new
policy for VPN access.
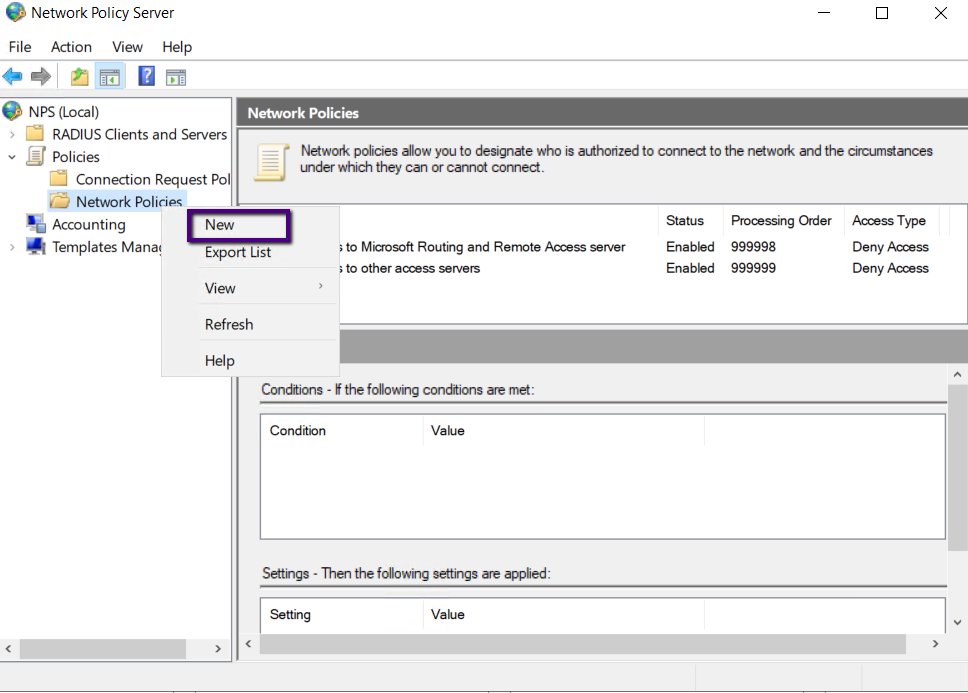
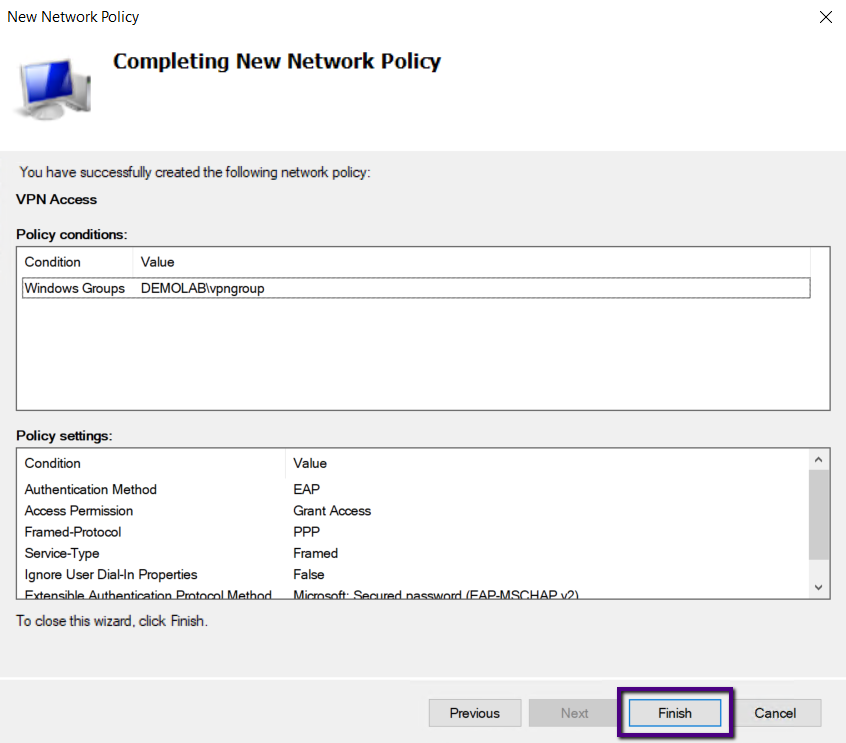
On the New Network Policy Window type VPN Access as Policy
Name and in the drop-down list of typer of network access server select Remote
Access Server (VPN-Dial Up) and Click Next.
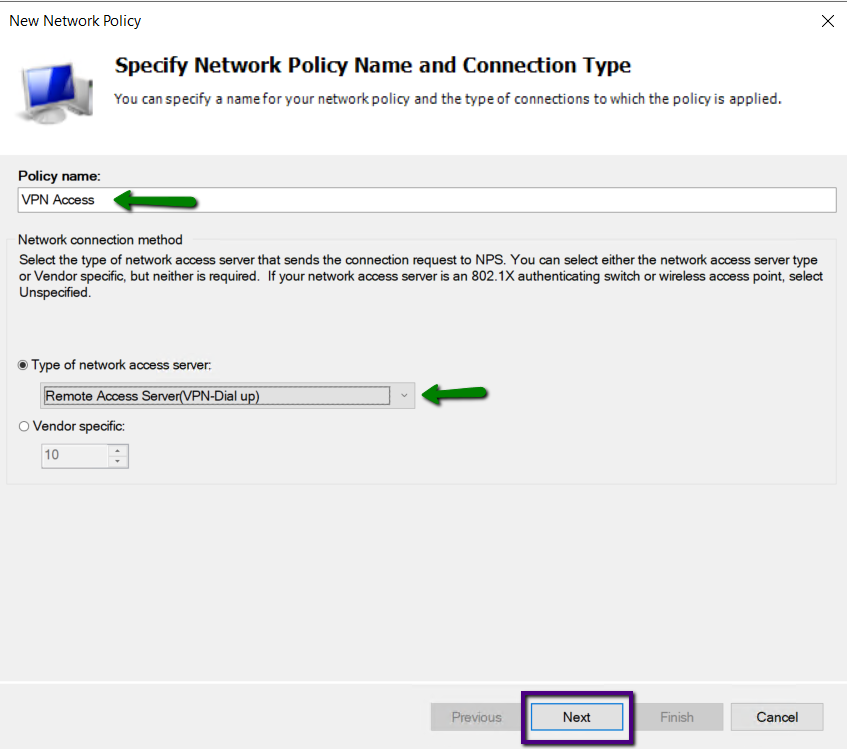
On the Specify Condition page, select Windows Group and
Click Add.
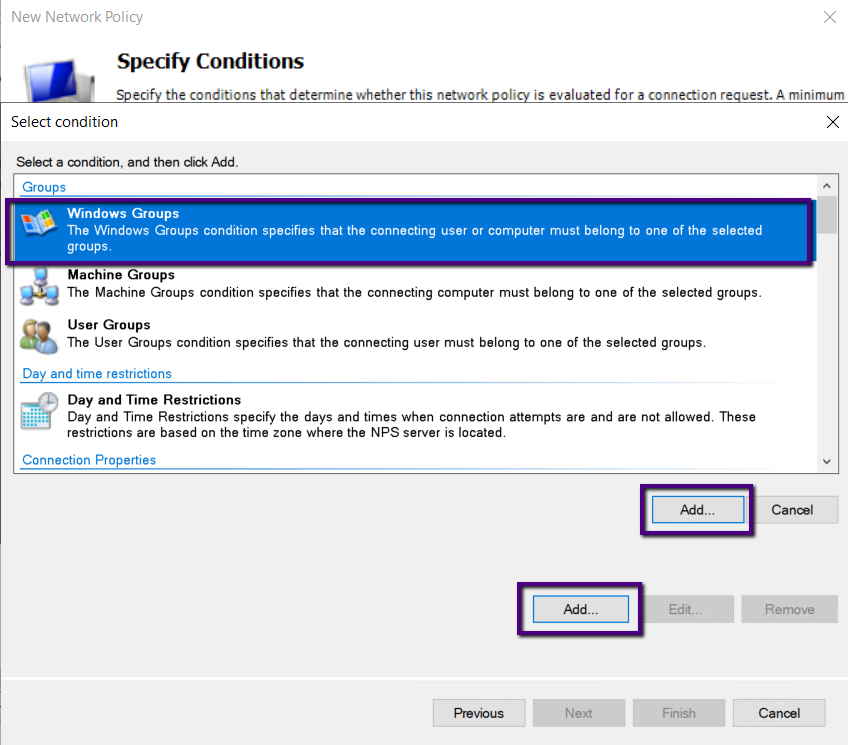
I have already created an Active Directory group called “vpngroup”
for this purpose, and we are going to add that group. Please note that we are
adding all users who need VPN access to this group.
How to Setup VPN using PPTP
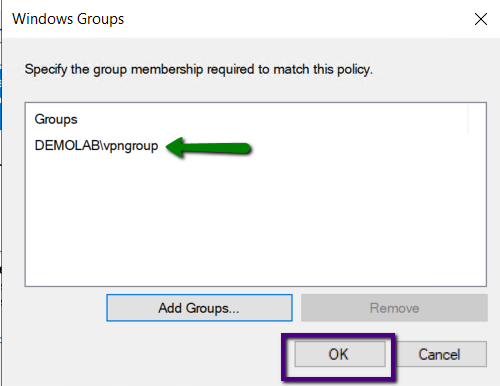
Once we confirmed the group added, click Next to continue.
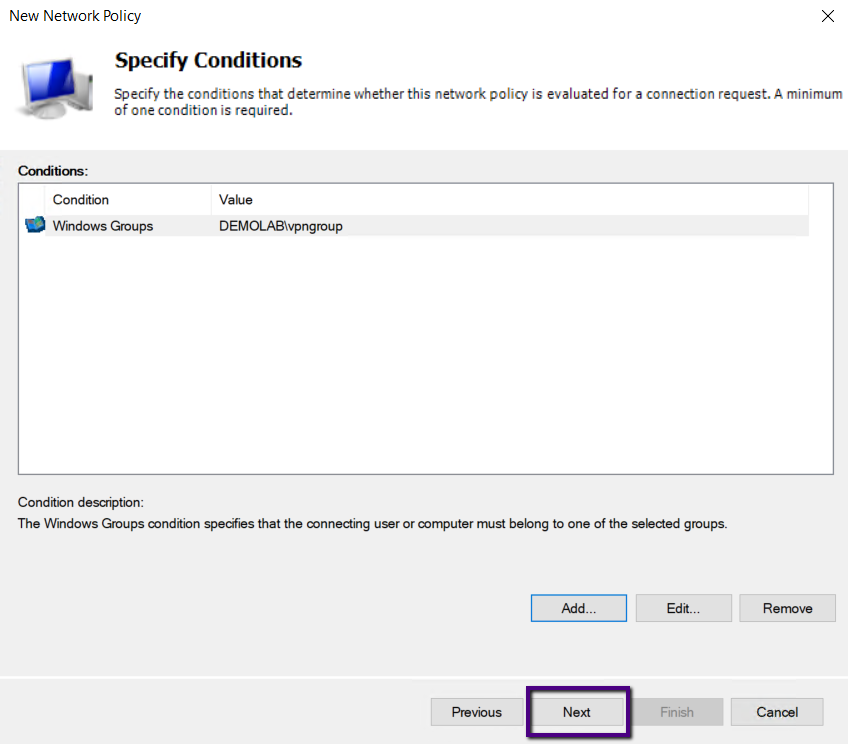
As we are granting access to this AD Group users, we are
selecting Access Granted and Clicking Next.
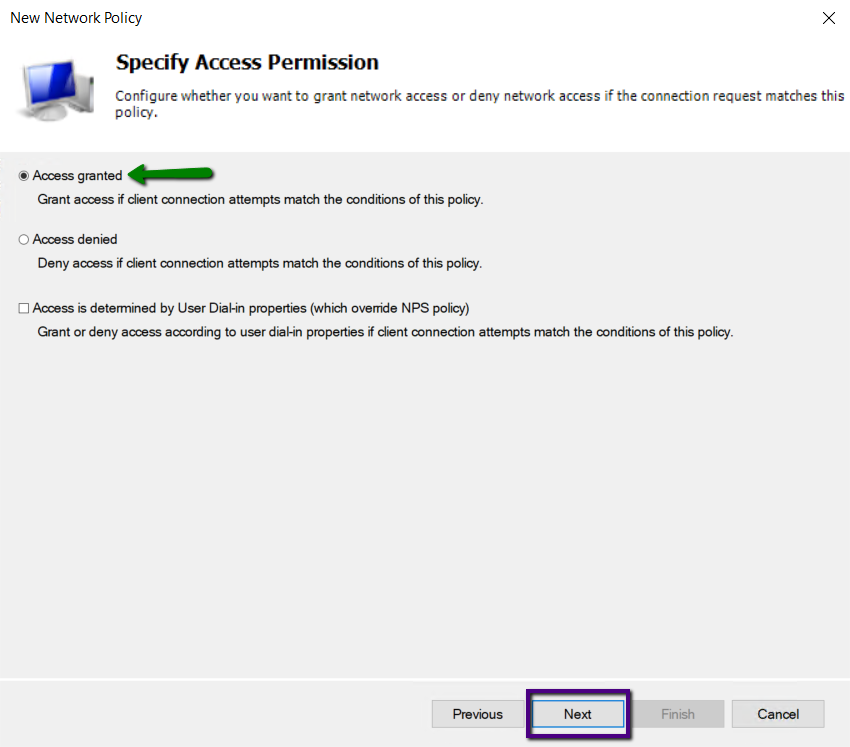
On the Configure Access methods, select Add and Microsoft
Secure Password (EAP-MSCHAP v2 as Extensible Authentication Protocol on the
list of authentication methods.
Also, uncheck the boxes near Less Secure Authentication methods.
How to Setup VPN using PPTP
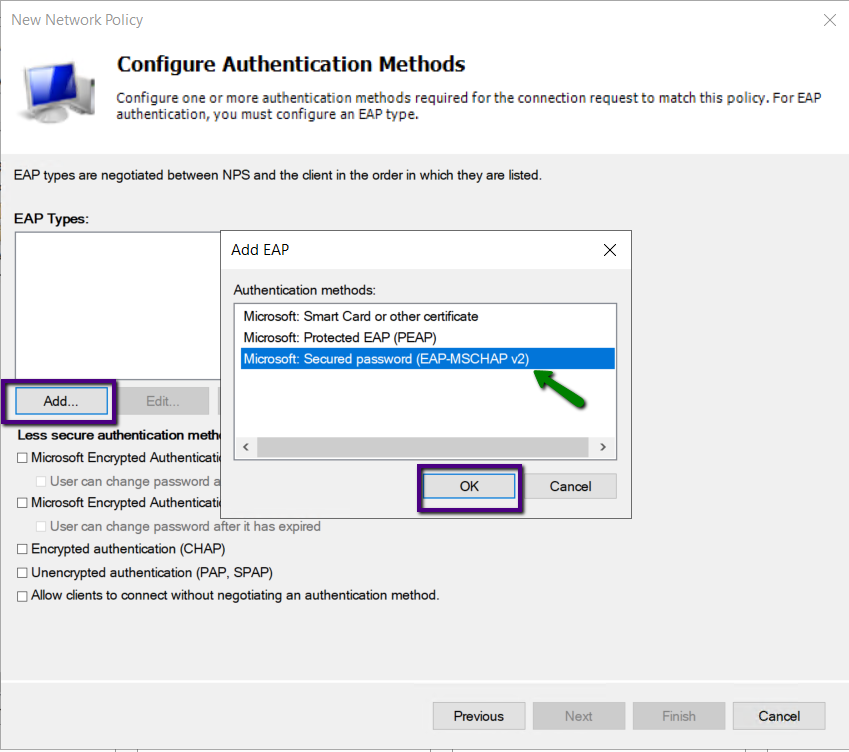
Once the Authentication method has been selected, click
Next.
On the Configure Constraints page, leave the defaults and
click Next.
Also, Configure Settings page leave the default and click
Next.
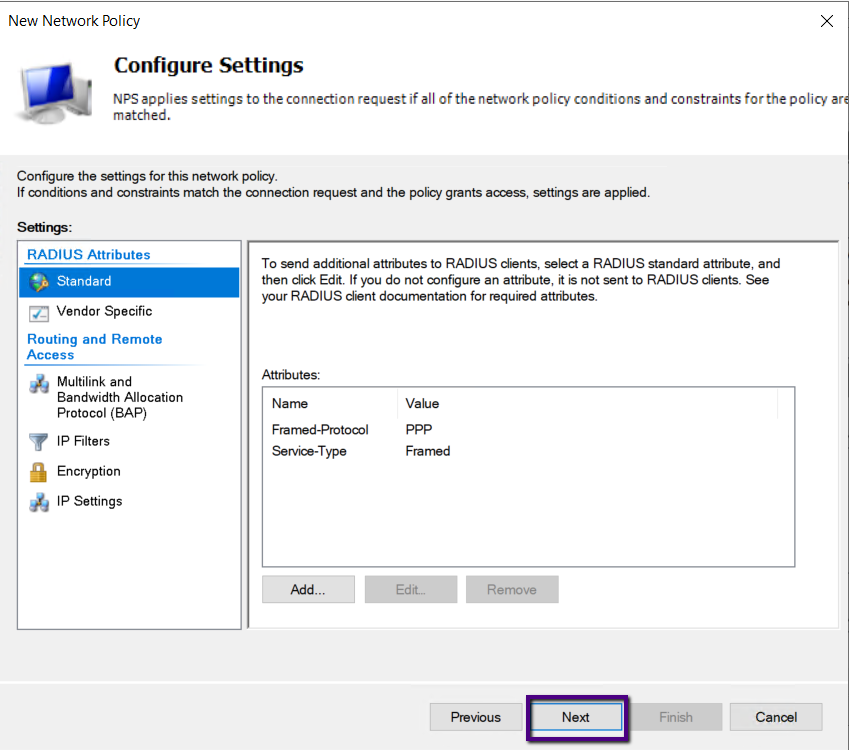
Click Finish to end the wizard.
Create a Windows
Firewall rule to open port PPTP VPN
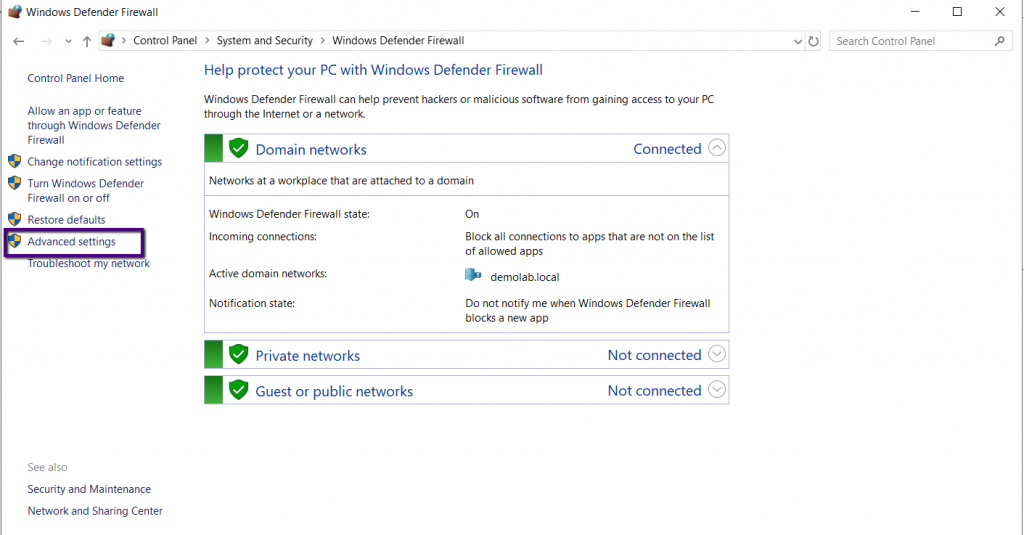
Go to
Control Panel>System and Security>Windows Defender Firewall and click
Advanced settings.
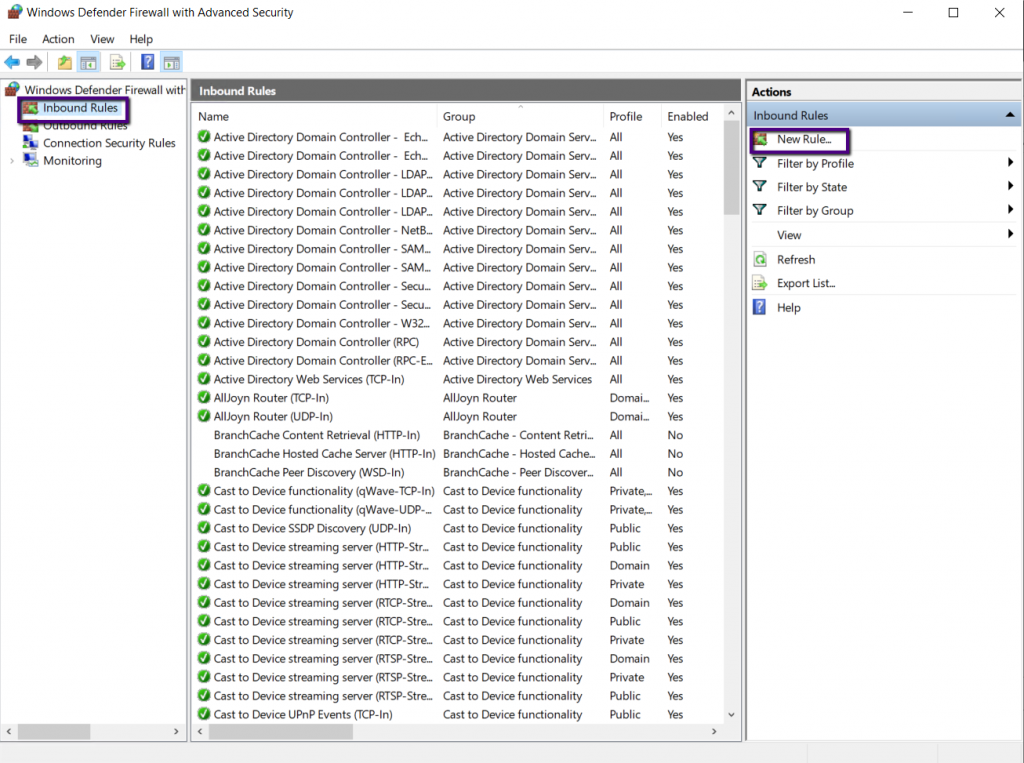
Select Inbound Rule from the left navigation and New Rule on
the Actions Menu
Select Port as Rule type and click Next
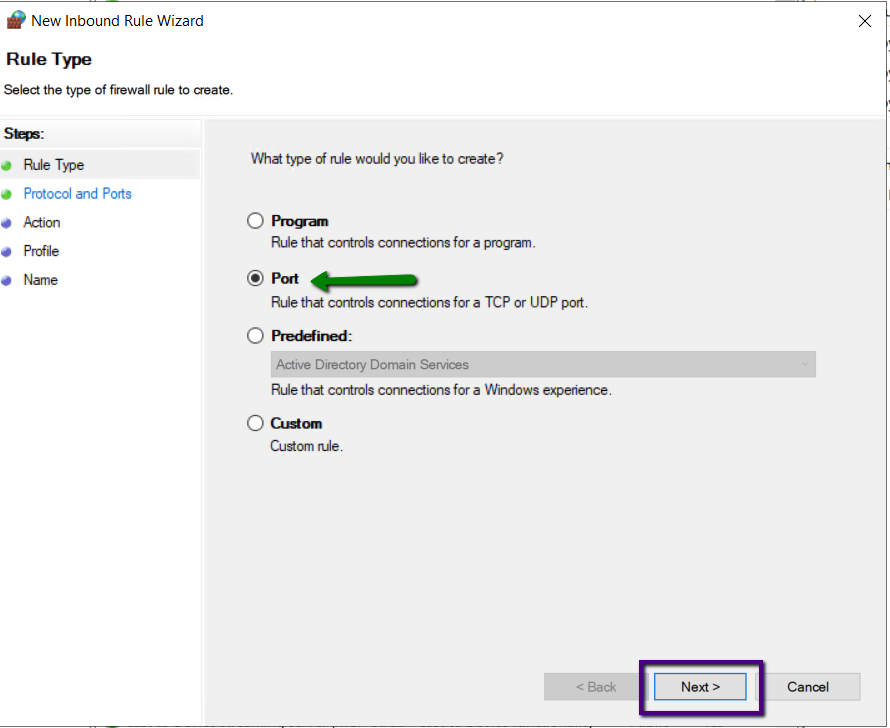
How to Setup VPN using PPTP
The PPTP port number is 1723, Select Rule “Apply to TCP” and
Specific local ports 1723 and, click Next.
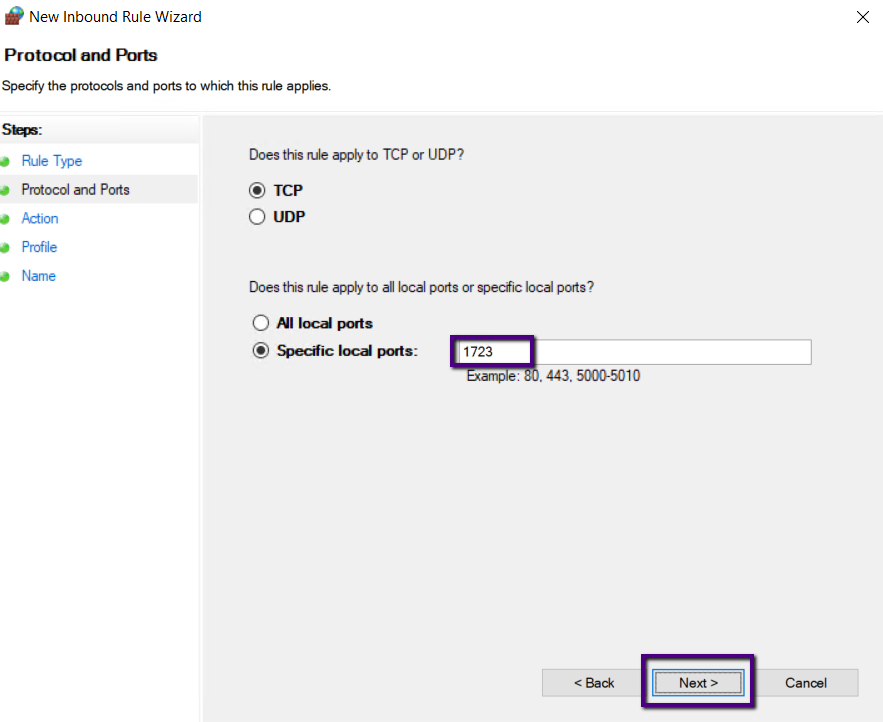
Select Allow Connections and click Next.
Select all the Network Locations and click Next.
Type a name for the Rule and Click Finish
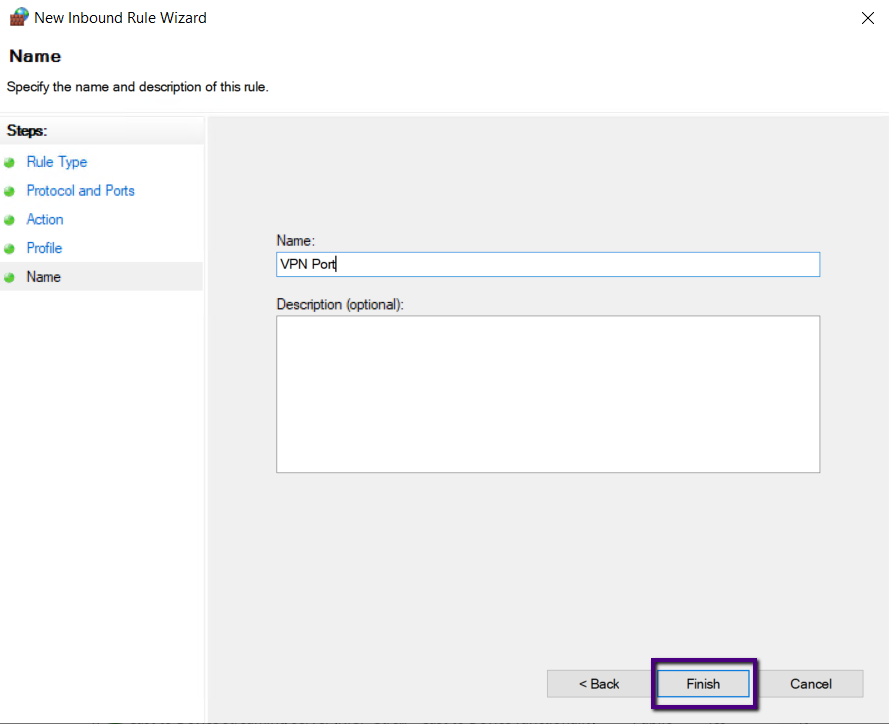
Create
VPN Network Connection
So, we have completed all server configurations, now is the
time to create a VPN connection on the Windows 10 client computer.
Right-click network Icon on the taskbar and select ‘Open
Network & Connection Sharing.’ On settings, windows click ‘Network and
Sharing Center’ that will open the ‘Network and Sharing Center’ where we need
to select ‘Set up a New Connection or Network’ as in the steps provided on the
screenshot below.
How to Setup VPN using PPTP
Select the steps as in the steps below.
- Open Network & Internet Sharing
- Network Sharing Center
- Set up a New Connection or network
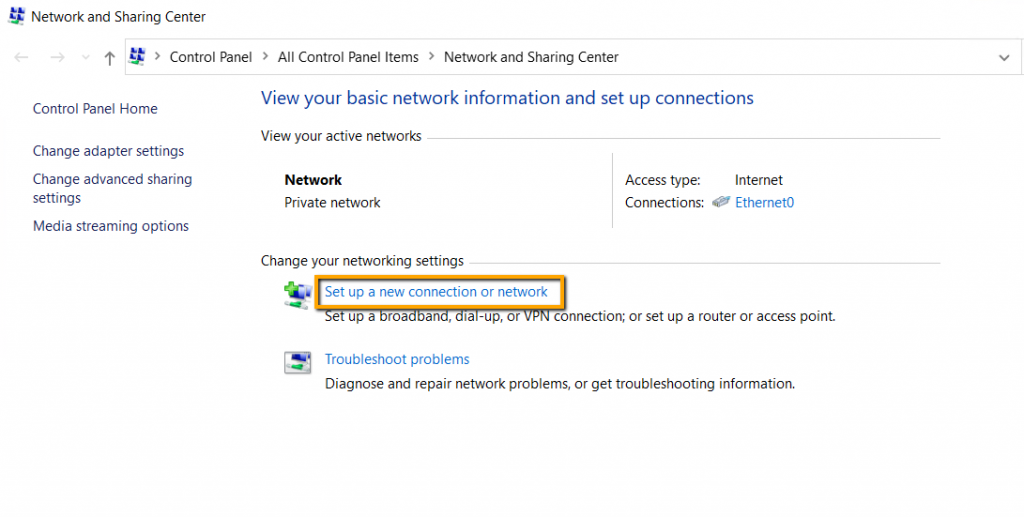
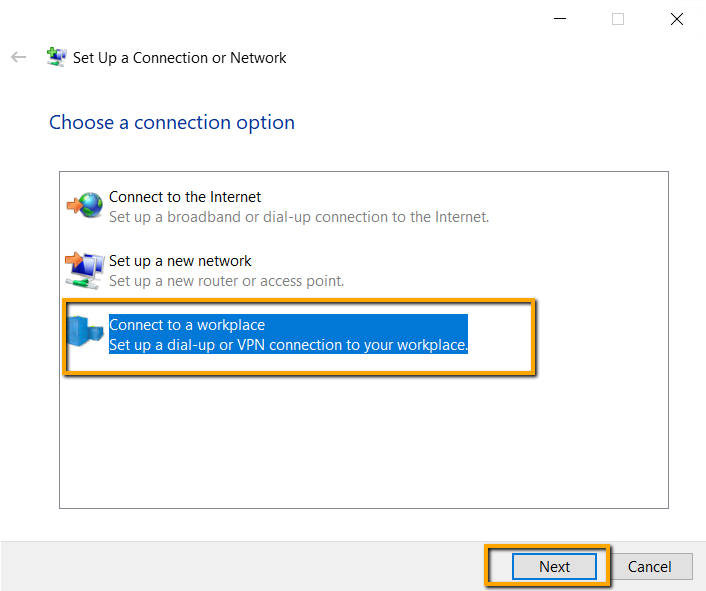
There is a Wizard start, and in the connection options,
select ‘Connect to a workplace’ and click Next.
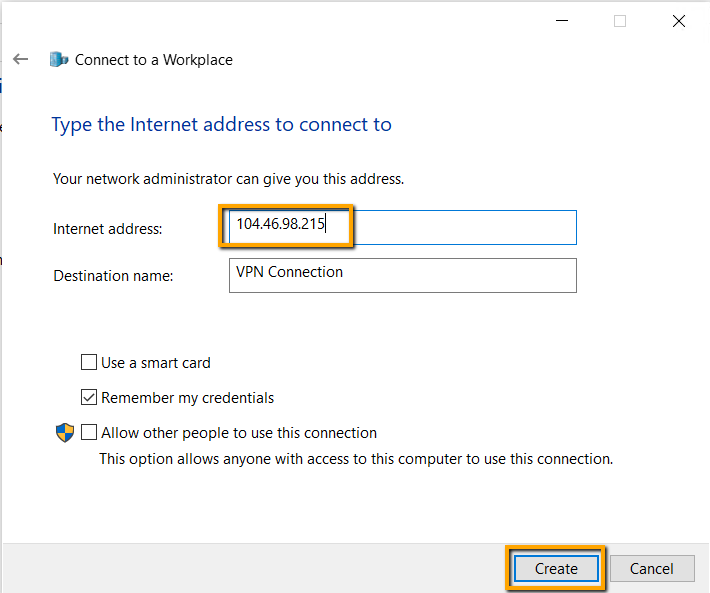
In the destination name type, a name implies the connection
purpose. I left the default name in this example.
Leave the selection of ‘Remember my credentials’ and click
create.
- Type the VPN server’s internet hostname or IP
address. - Give a name to the VPN Connection.
- Click Create to create a workplace connect.
To change the type of VPN, right-click newly created Network
Connection and select properties.
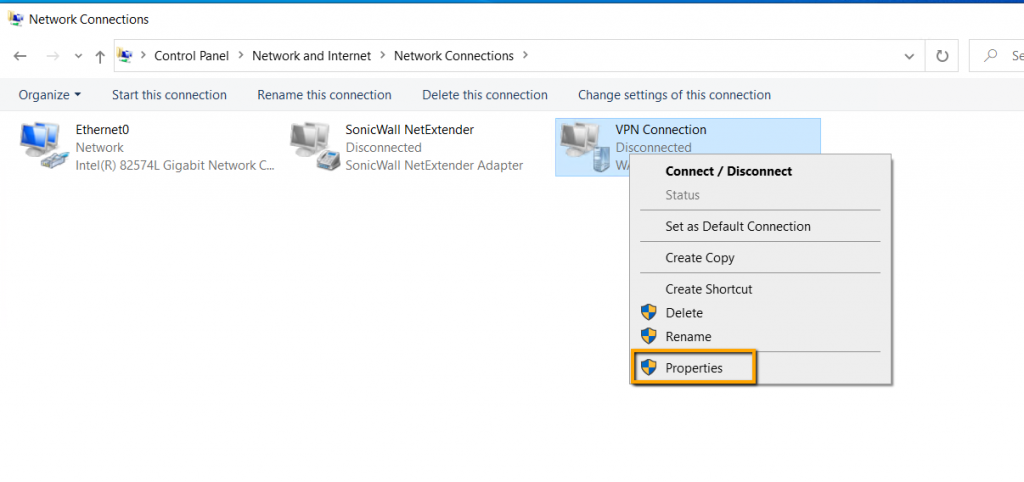
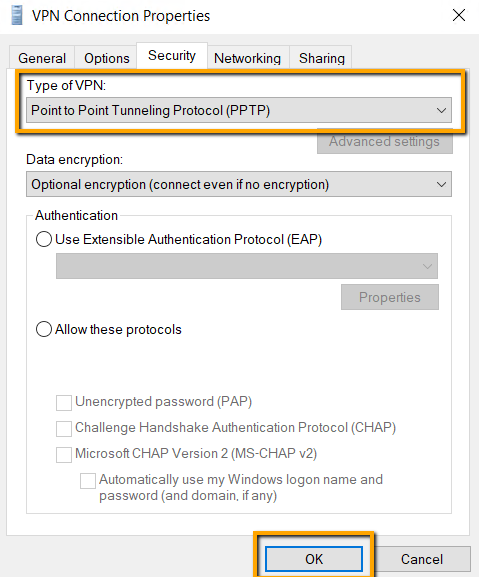
On the Security tab, select Point to Point Tunneling
Protocol (PPTP) and click OK.
How to Setup VPN using PPTP
Click Network icon on the taskbar and the newly created VPN
connection will appear on the list of connections, click that, and there will
be a credentials box open.
On the Sign-in prompt type, the AD user and password and
click OK.
The VPN connection will show connected. Now we can access
the internal devices on the office network using their private IP address.
Conclusion
In this article, we have gone through step by step instructions on how to 1. Install and configure Remote Access VPN role 2. Network Policy Server VPN policy 3. Creating windows firewall rule and 4. Making a VPN Connection on the Windows client system and connected to Office network remotely using PPTP. Also, we have one more step to that on the router or Firewall device connecting to the internet we need to add a port forwarding rule to point the VPN server connecting port 1723. On the security settings on the firewall, we need to enable Generic Routing Encapsulation to connect the VPN from remote windows client to the VPN Server that we just configured.
You may have some questions or feedback to share with me,
please click the comments below and share your thoughts. I am so happy to
answer your questions.
A Virtual Private Network (VPN) is used to securely create a tunnel for data between your local computer to a remote server. On Windows Server 2019, you can configure a VPN to provide network access to connected clients and allow connected devices to communicate securely.
This guide explains how to set up a fresh Windows Server 2019 as an L2TP over IPSec, or a PPTP VPN, using the routing and remote access feature. Layer 2 Tunneling Protocol (L2TP) with IPSec offers robust encryption for connections to the server. On the other hand, the Point to Point Tunneling Protocol (PPTP) is simple to deploy but not as secure.
To set up the VPN server, we shall use the built-in Routing and Remote access feature, which offers a graphic interface to configure remote networking features such as Dial-up, LAN routing, NAT, and VPN.
Requirements
- Deploy a Windows Server 2019 Instance on Vultr
- Remotely connect to the server and log in as an Administrator
Create a New VPN User
For the VPN service to work well, it must authenticate with a valid user account to the server. So, you need to create a new user on the server.
Click Tools under server manager and select Computer Management from the drop-down list to create a new user.
Once the computer management window pops up, expand Local Users and Groups from the left pane and right-click Users to select New User on the sub-menu.
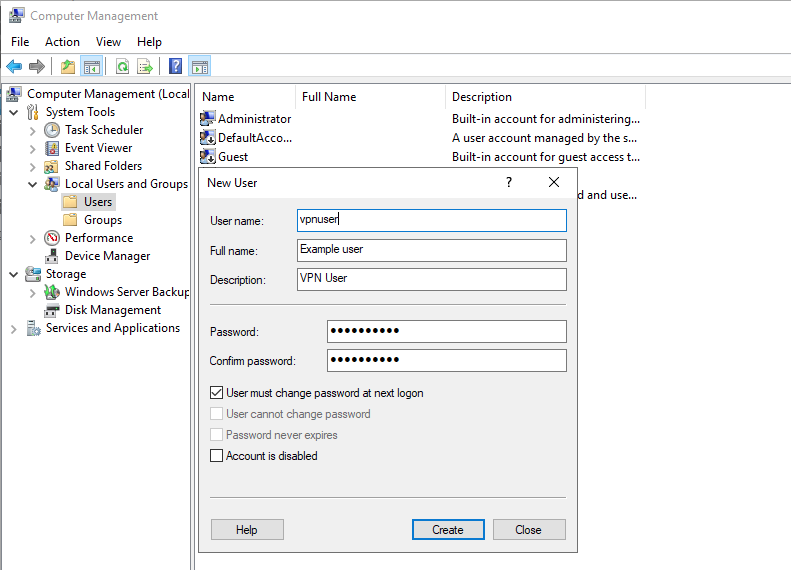
Under the New User dialog box, enter a username, full name, and password for the VPN user, then click create and close the window.
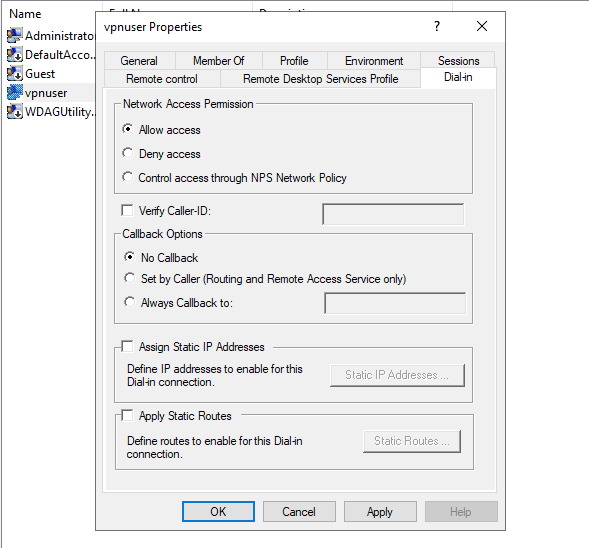
The new user will now be listed on the list of active server users, right-click on the new user and select properties.
Under the user properties window, navigate to the Dial-in tab and click Allow access under Network Access Permission. Click OK for changes to take effect.
Install the Routing and Remote Access Features
Procedure 1: Through Server Manager
From the Windows start menu, open Server Manager, click Manage, then select Add Roles and Features from the drop-down list.
From the open window, click next and select Role-based or feature based installation, then select your server from the pool. Select Remote Access, Remote Access Administration from the list of server roles.
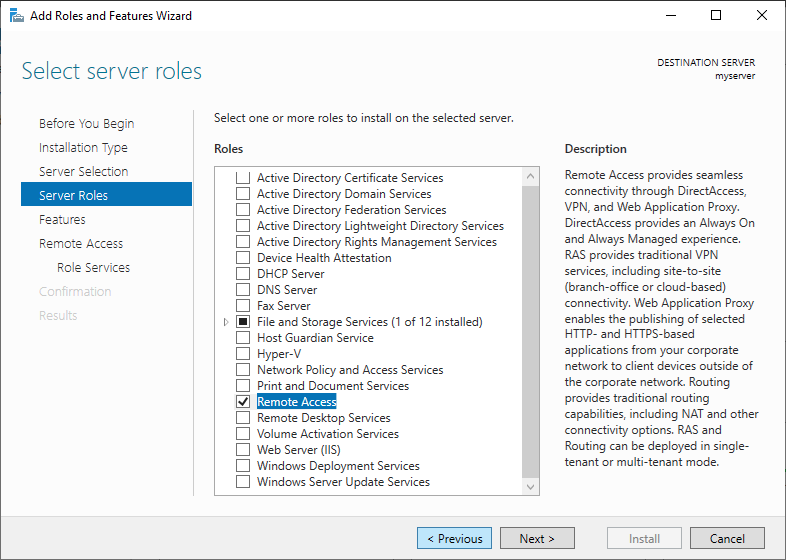
Next, select DirectAccess and VPN (RAS) and Routing from the features list, then click to Install IIS, which is required for remote access to work well.
Procedure 2: Using Windows PowerShell
You can also install Remote Access from Windows Powershell.
From the Windows start menu, open an Administrative Powershell, then install Remote access by pasting the following code to the console.
Install-WindowsFeature RemoteAccess
Install-WindowsFeature DirectAccess-VPN -IncludeManagementTools
Install-WindowsFeature Routing -IncludeManagementTools
Your output should be similar to:
PS C:\Users\Administrator> Install-WindowsFeature RemoteAccess
>> Install-WindowsFeature DirectAccess-VPN -IncludeManagementTools
>> Install-WindowsFeature Routing -IncludeManagementTools
Success Restart Needed Exit Code Feature Result
------- -------------- --------- --------------
True No Success {Remote Access}
True No Success {RAS Connection Manager Administration Kit...
True No Success {Routing}Configure Routing and Remote Access
Open Server Manager and click Tools on the top toolbar. From the drop-down list, select Remote Access Management.
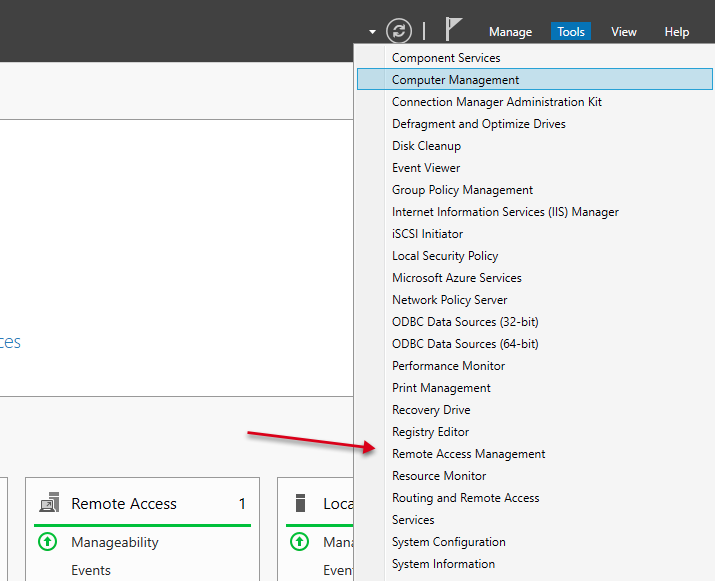
In the open Routing and Remote Access window, right click on your server name just below Server status, then select Configure and Enable Routing and Remote Access from the drop-down menu.
Now, select Custom configuration to configure remote access manually.
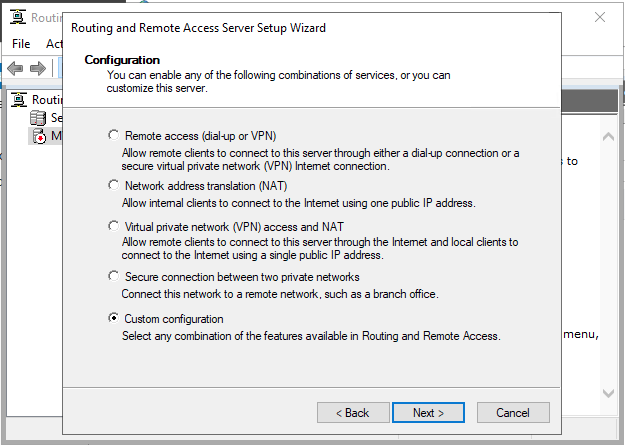
Select VPN Access and NAT as services you want to enable on your server, click next to finish the configuration, and start the service.
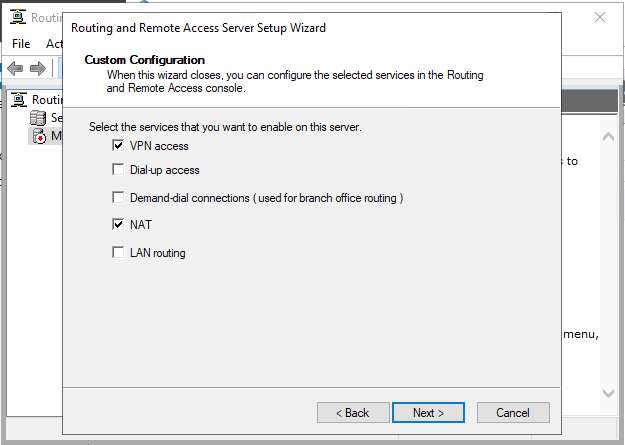
Setup a PPTP VPN
Now that Remote Access is running, you can set up your PPTP VPN. To get started, you must assign connected clients** static IP Addresses to avoid possible connection issues. To do this, right-click on your server under the Routing and Remote Access window and select Properties from the drop-down list.
Click IPV4 in the Open Window, then select Static address pool. Now, click Add to craft a new IP Address range from the open pop-up window. In this guide, we use the range 10.0.0.1 to 10.0.0.50, and the server will automatically calculate the number of available addresses.
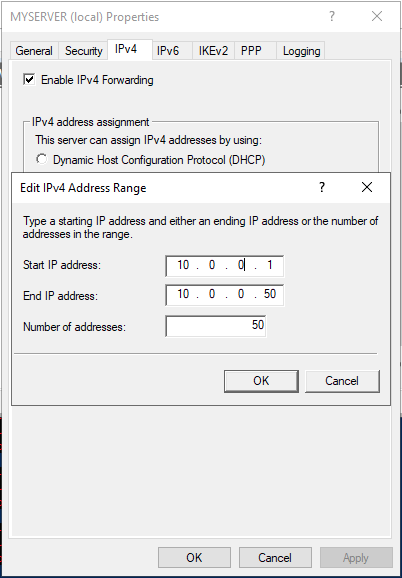
Click OK to save your static IP Address configuration. You will be prompted to restart Routing and Remote Access for changes to apply; simply click OK.
Configure NAT and enable PPTP
We need to configure Network Address Translation (NAT) for connected clients to use the Internet. On the left pane of the same routing and remote access window, expand the IPv4 options under your server. Right-click on NAT and select New Interface.
Under the open dialog window, select Public interface and enable NAT on the interface.
Next, navigate to Services and Ports and click VPN Gateway (PPTP) from the drop-down list.
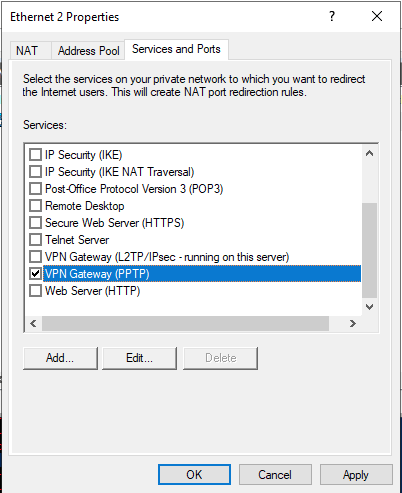
Click Edit to set a Private address for the VPN service, change the current address 0.0.0.0 to 127.0.0.1, and click OK to save.
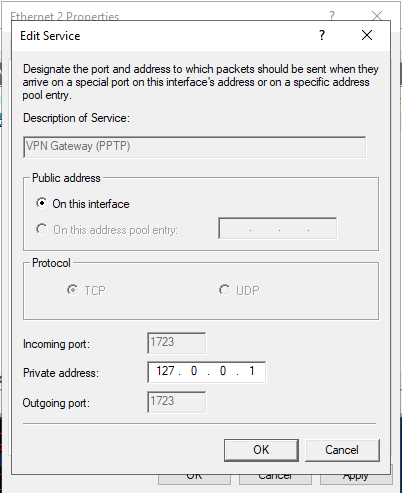
Finally, click OK to save all changes, then right-click on your server from the left pane and click Restart under the All Tasks sub-menu.
This will restart routing and remote access services making your server ready for incoming VPN connections.
Configure Windows Firewall to accept Incoming PPTP VPN Connections
Click Tools from the Windows server manager and select Windows Defender Firewall with Advanced Security from the drop-down list.
Under the open Windows Defender Firewall with Advanced Security window, select Inbound Rules on the left pane, then click New Rule on the right pane.
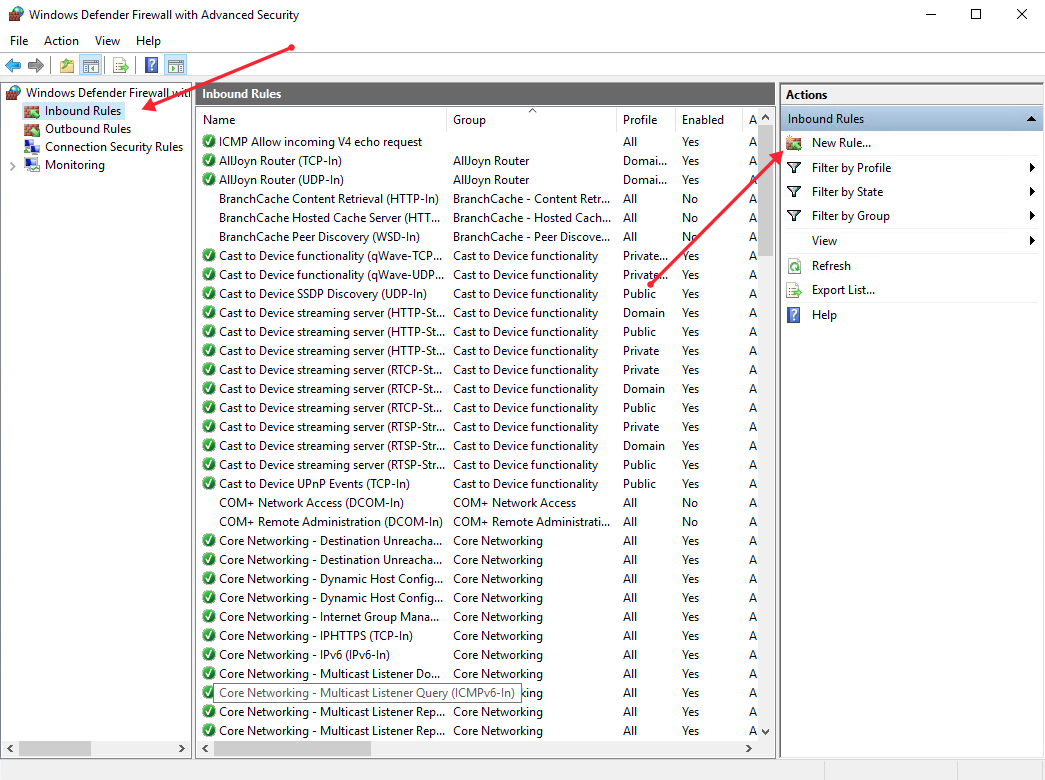
In the open new Inbound rule wizard, click Predefined and select Routing and Remote Access from the list.
Under predefined rules, choose Routing and Remote Access (PPTP-In), click next to allow the connection, then finish for the new Firewall rule to be applied and test your new PPTP VPN server.
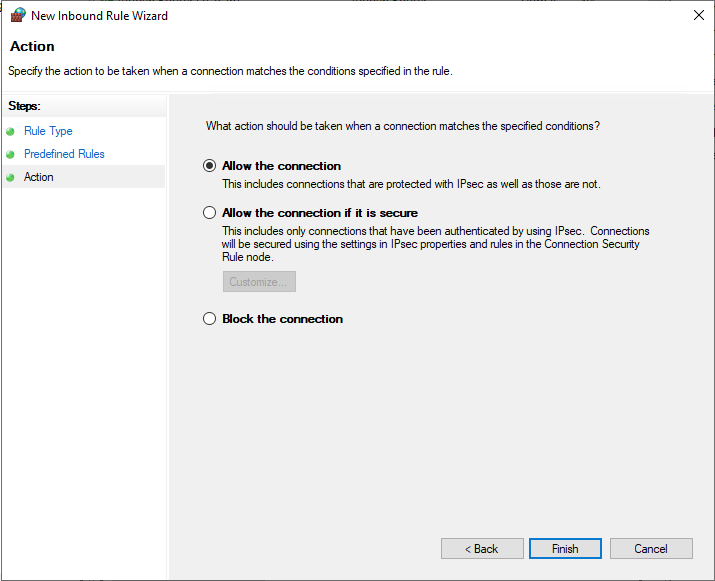
Test your PPTP VPN
Using your personal computer (PC) or Smartphone, go to Networks, Add a new VPN and select PPTP as the VPN type. Then, enter the VPN username and password created earlier to connect.
In this guide, we cover and test the PPTP VPN on a Windows 10 PC. To get started, click the start menu and search for Control Panel, then, click Network and Internet.
Under Network and Internet, open the Network and Sharing Center and click Set up a new connection or network.
Under the open window, select Connect to a workplace and click Use my Internet connection (VPN).
Then, enter your server’s public IP Address (Check your Vultr server dashboard), assign the connection a name, and click create.
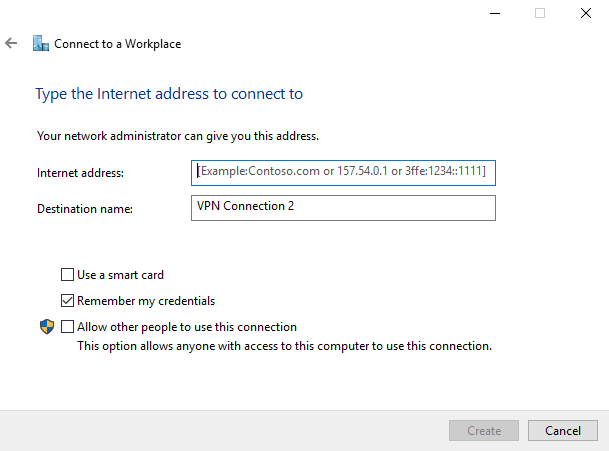
Now, on the left pane, click Change adapter settings, then right click your created VPN interface and select Properties.
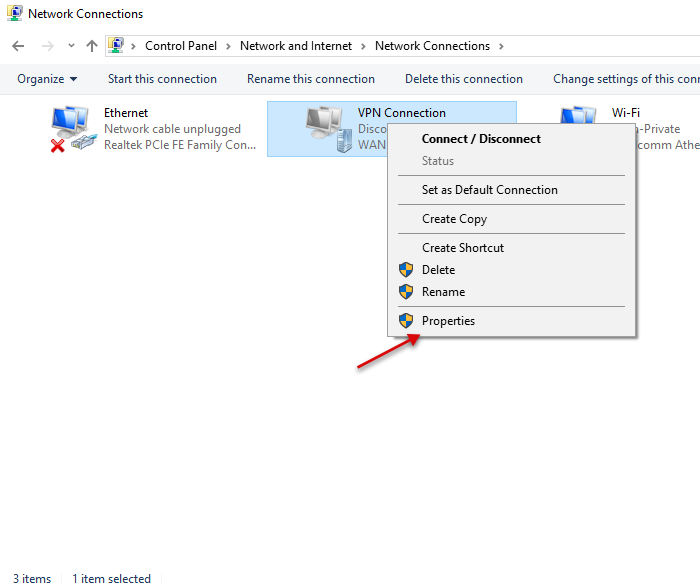
Under the pop-up, click Security, then choose Point to Point Tunneling Protocol (PPTP) under Type of VPN.
Finally, under Allow these protocols, select CHAP and MS-CHAP v2, then click OK to apply changes.
Your new VPN is configured successfully. Click the network connection icon on the taskbar, select your VPN on the list and click Connect to enter the VPN username and password created earlier to establish a connection to your new PPTP VPN server.
Setup L2TP with IPSEC
Open server manager, click Tools, and open Remote Access Management, then right-click your server on the left pane to select Properties from the drop-down list.
Under server properties, navigate to the Security tab, and click Allow custom IPSec policy for L2TP/IKEv2 connection to enter your new pre-shared key.
In this guide, we use 12345678, choose something stronger, then navigate to IPV4 to set a static address pool and click OK to apply changes.
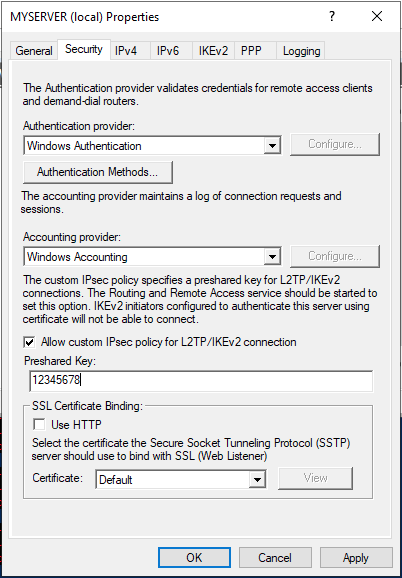
Keep note of the pre-shared key (PSK) since it will be required for every user establishing a connection to the VPN server.
From the left pane, expand the IPV4 sub-menu and right-click on NAT, then select New Interface. If you set PPTP earlier, click NAT and edit the existing interface you already created.
Navigate to the Services and Ports tab and select VPN Gateway [L2TP/IPSec], then click edit to change the private address from 0.0.0.0 to 127.0.0.1. Click OK to save changes and restart remote access from the left pane under All Tasks.
This will restart Routing and Remote Access, then save the applied L2TP configurations.
Allow L2TP Connections through Windows Firewall
Open Windows Defender with Firewall, select inbound rules and add a new rule. Select Predefined and from the list, choose Routing and remote access.
Under Predefined rules, select Routing and Remote Access [L2TP-In] and click next.
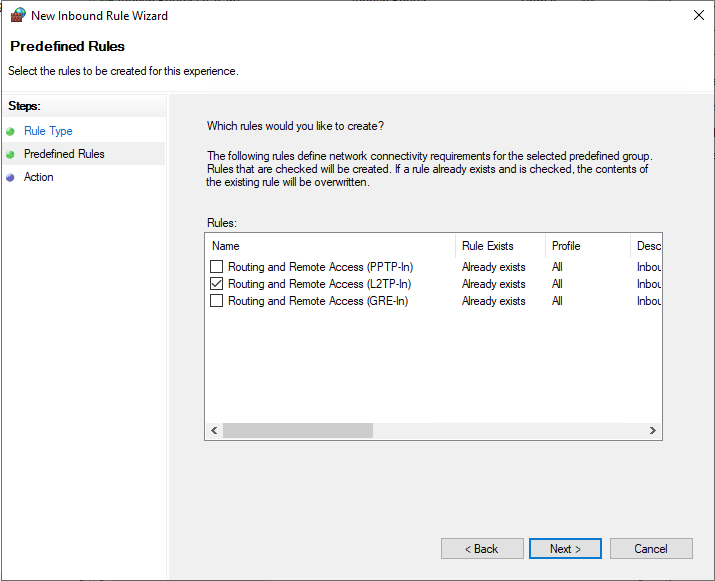
Finally, allow the connection and click Finish to apply the new Firewall rule.
Connect and Test Your L2TP VPN server
In this guide, we test the new L2TP with IPSec VPN on a mac. To get started, open System Preferencesand click Network.
Under the Network Preferences window, click the + sign and select VPN under the Interface dialog box. Then, choose L2TP with IPSec as the VPN Type and assign your connection a name.
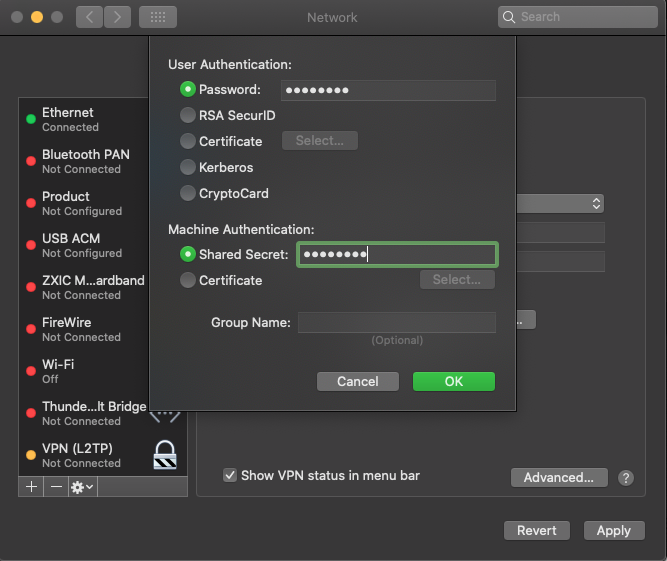
Click create, then enter your public server IP Address (server address) and username (Account name). Next, click Authentication Settings to enter your account password and Pre-shared key (Shared secret) created earlier.
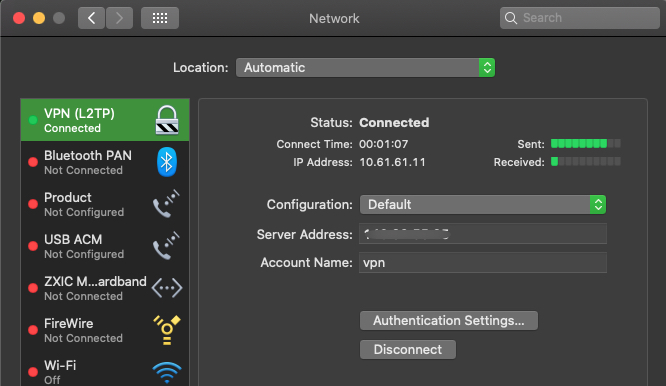
Next, click Advanced and select Send all Traffic over VPN Connection, then click Apply, and finally click Connect to establish a connection with your new L2TP VPN server.
Conclusion
You have set up a VPN on your Windows server 2019 instance; you can choose to create both PPTP and L2TP VPNs with different users connecting through your server without any limitations.
For every connected device, they will be able to access the Internet through your server and interact with other connected computers.
,
In this tutorial you will find step by instructions to setup a PPTP VPN Server 2016, in order to access your local network resources from anywhere in the world. So, if you have a Windows 2016 server with one network card and you want to setup a VPN connection in order to connect and access server or network files from everywhere, continue reading below…*
* Note: If you want to setup a more secure VPN Server for your network, then read this article: How to Setup L2TP VPN Server 2016 with a Custom Preshared Key for Authentication.
How to Install a PPTP VPN Server 2016 (With only One NIC).
To install and configure the Server 2016 to act as a PPTP VPN access server follow the steps below:
Step 1. Install the Routing and Remote Access Role on Server 2016.
Step 2. Enable the Routing and Remote Access on Server 2016.
Step 3. Configure VPN Server Settings (Security, IP Range, etc.).
Step 4. Allow Routing and Remote Access Inbound Traffic in Windows Firewall.
Step 5. Select the VPN Users.
Step 6. Configure the VPN Server to Allow the Network Access.
Step 7. Configure ISP’s Firewall to Allow the PPTP Connections.
Step 8. Setup the PPTP Connection on Clients.
.
Step 1. How to Add Remote Access (VPN Access) Role on a Server 2016.
The first step to setup a Windows Server 2016, as a VPN server is to add the Remote Access role to your Server 2016. *
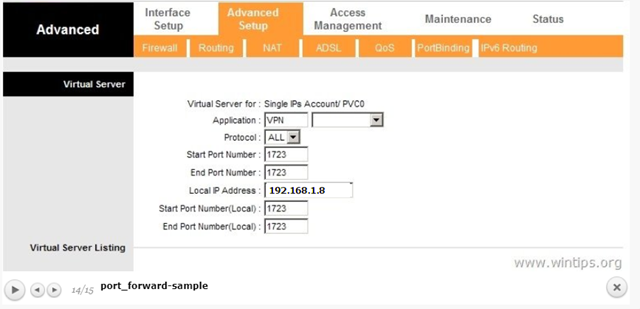
* Info: For this example we’re going to setup VPN on a Windows Server 2016 machine, named «Srv1» and with IP Address «192.168.1.8».
1. To install VPN role on Windows Server 2016, open ‘Server Manager’ and click on Add Roles and Features.
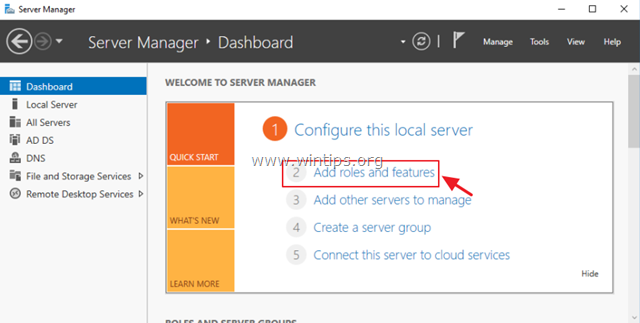
2. At the first screen of ‘Add Roles and Features wizard’, leave the Role-based or feature-based installation option and click Next.
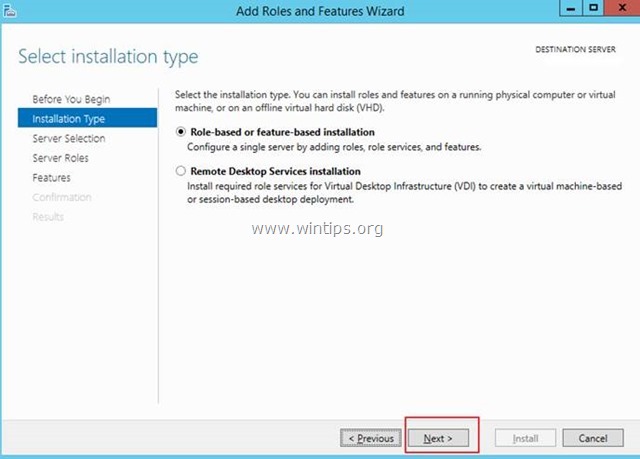
3. At the next screen, leave the default option «Select server from the server pool» and click Next.
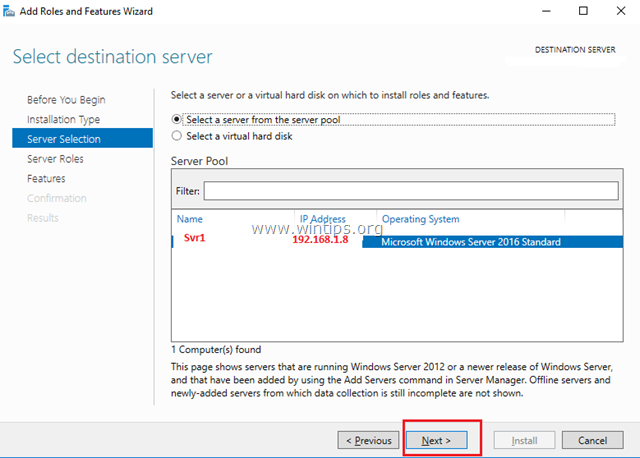
4. Then select the Remote Access role and click Next.
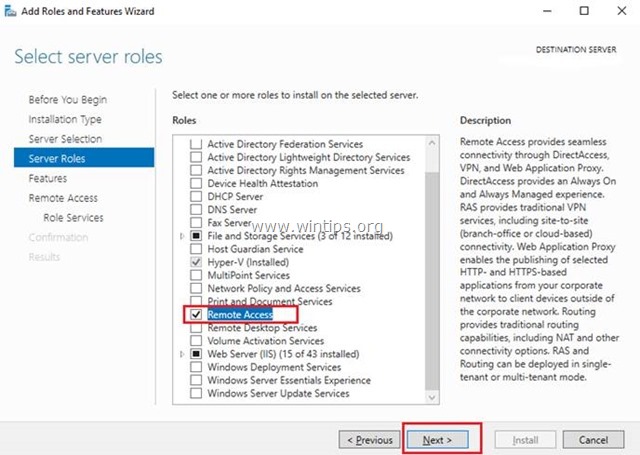
5. At ‘Features’ screen leave the default settings and click Next.
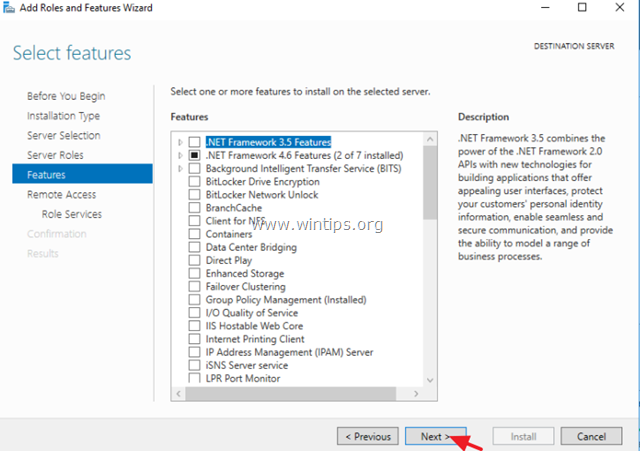
6. At ‘Remote Access’ information screen, click Next.
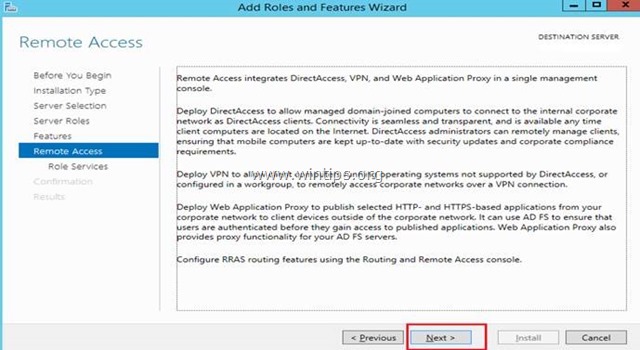
7. At ‘Remote Services’, choose the Direct Access and VPN (RAS) role services and then click Next.
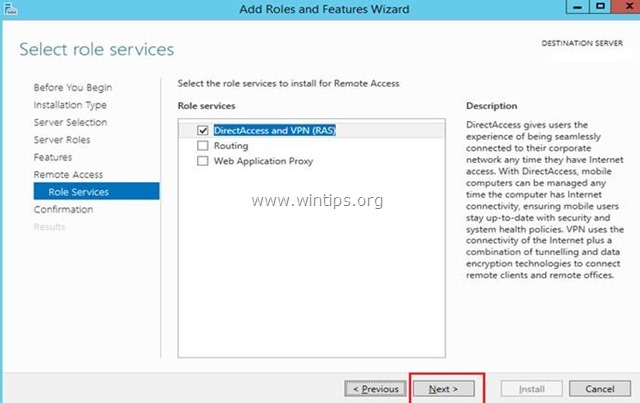
8. Then click Add Features.
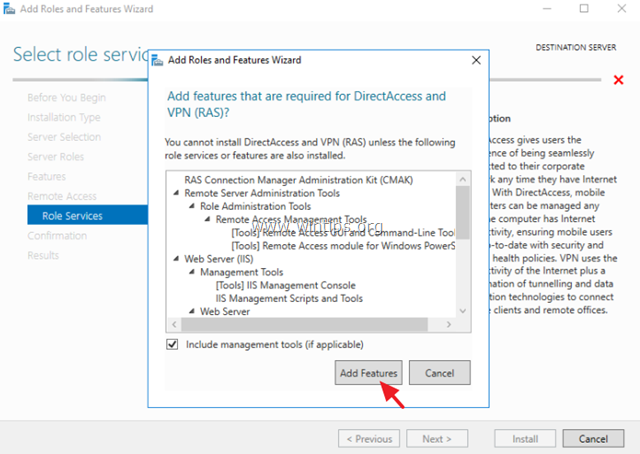
9. Click Next again.
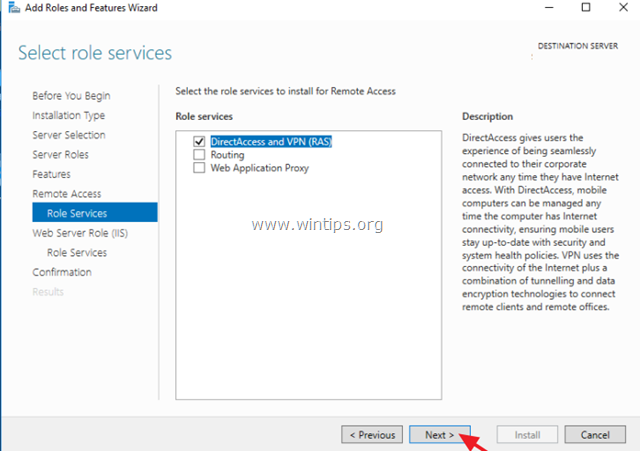
10. Leave the default settings and click Next (twice) at ‘Web Server Role (IIS)’ and ‘Role Services’ screens.
11. At ‘Confirmation’ screen, select Restart the destination server automatically (if required) and click Install.
12. At the final screen, ensure that the installation of the Remote Access role is successful and Close the wizard.
13. Then (from Server Manager) Tools menu, click on Remote Access Management.
14. Select Direct Access and VPN on the left and then click to Run the Getting Started Wizard.
15. Then click Deploy VPN only.
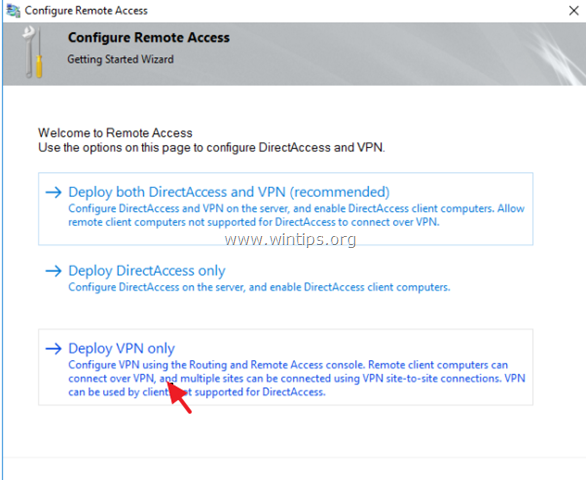
16. Continue to step-2 below to configure Routing and Remote Access.
Step 2. How to Configure and Enable Routing and Remote Access on Server 2016.
The next step is to enable and configure the VPN access on our Server 2016. To do that:
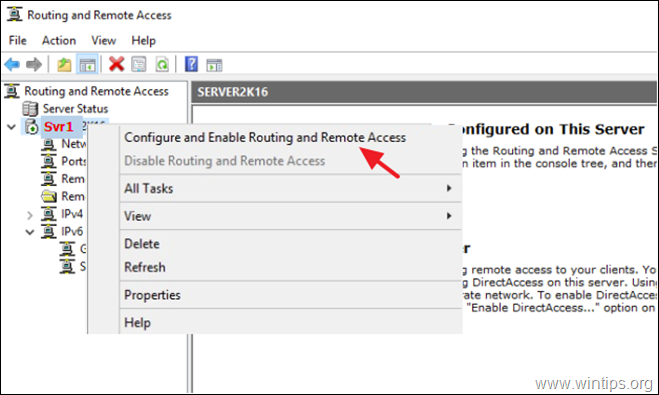
1. Right click on the Server’s name and select Configure and Enable Routing and Remote Access. *
* Note: You can also launch Routing and Remote Access settings, by using the following way:
1. Open Server Manager and from Tools menu, select Computer Management.
2. Expand Services and Applications
3. Right click on Routing and Remote Access and select Configure and Enable Routing and Remote Access.
2. Click Next at ‘Routing and Remote Access Server Setup Wizard’.
3. Choose Custom configuration and click Next.
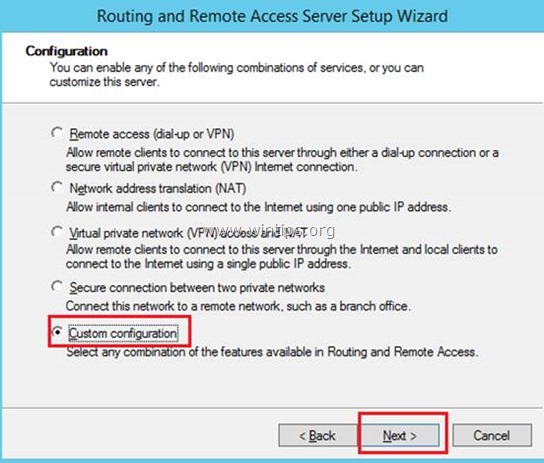
4. Select VPN access only in this case and click Next.
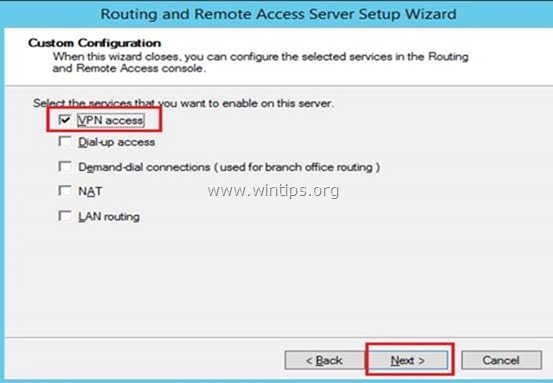
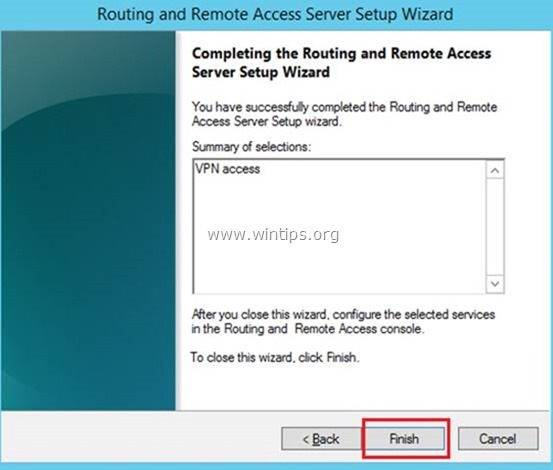
5. Finally click Finish. *
* Note: If you receive an error says » Remote Access Service in unable to enable Routing and Remote Access ports in Windows Firewall…», ignore it and click OK to continue.
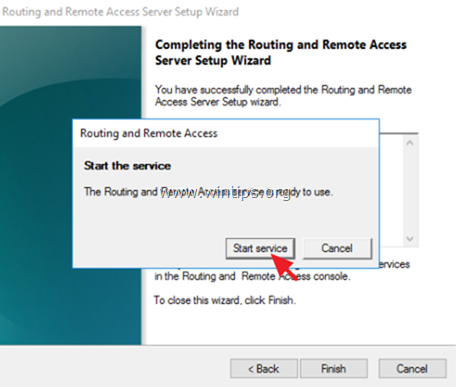
6. When prompted to Start the service click Start.
Step 3. Configure VPN Server Settings (Security, IP Range, etc.)
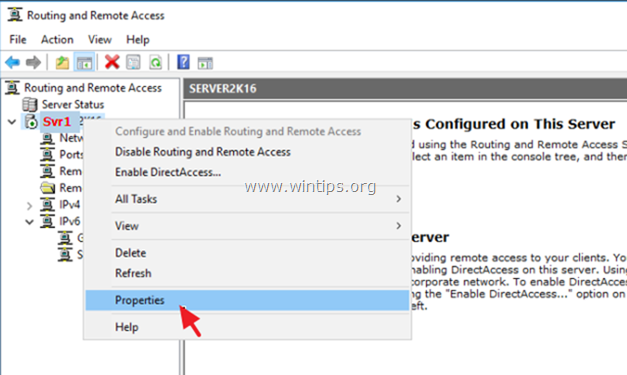
1. At Routing and Remote access panel, right click on your server’s name and select Properties.
2a. At ‘Security’ tab, select the Windows Authentication as the Authentication Provider. and then click the Authentication Methods button.
2b. Make sure that the Microsoft encrypted authentication version 2 (MS-CHAP v2) is selected and then click OK.
3a. Now select the IPv4 tab, choose the Static address pool option and click Add.
3b. Now type the IP Address Range that will be assigned to VPN clients and click OK twice to close all windows.
e.g. For this example we’re going to use the IP address range: 192.168.1.200 – 192.168.1.209.
Step 4. Allow Routing and Remote Access Inbound Traffic in Windows Firewall
1. Go To Control Panel > All Control Panel Items > Windows Firewall.
2. Click Advanced settings on the left.
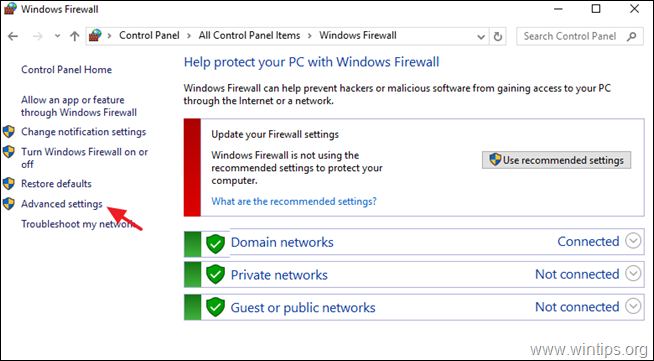
3. Select Inbound Rules on the left.
4a. At the right pane, double click at Routing and Remote Access (PPTP-In)
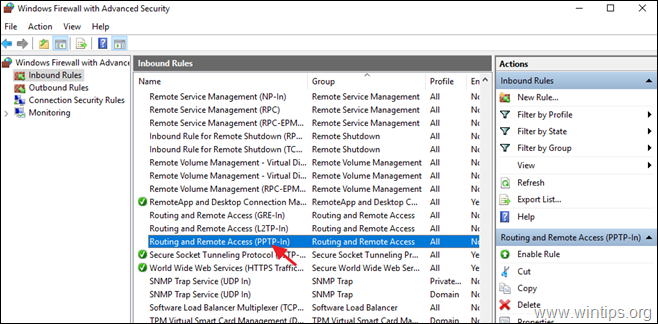
4b. At ‘General’ tab, choose Enabled, Allow the connection and click OK.
5a. Then double click at Routing and Remote Access (GRE-In).
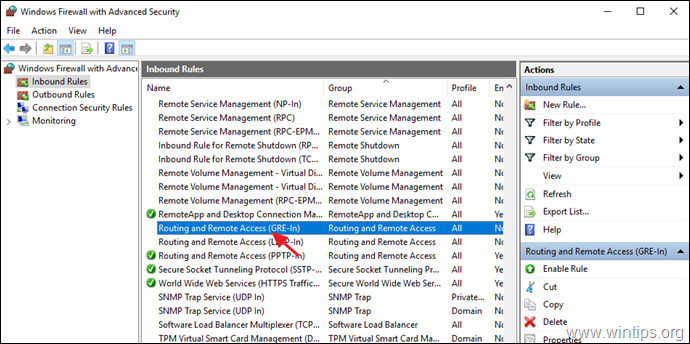
5b. At General tab, choose Enabled, Allow the connection and click OK.
6. Close the Firewall settings and restart your server.
Step 5. How to Select which users will have VPN Access.
Now it’s time to specify which users will be able to connect to the VPN server (Dial-IN permissions).
1. Open Server Manager.
2. From Tools menu, select Active Directory Users and Computers. *
* Note: If your server doesn’t belong to a domain, then go to Computer Management -> Local Users and Groups.
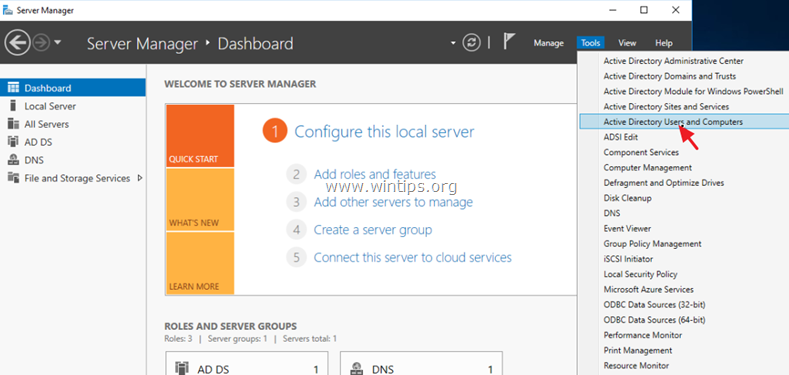
3. Select Users and double click on the user that you want to allow the VPN Access.
4. Select the Dial-in tab and select Allow access. Then click OK.
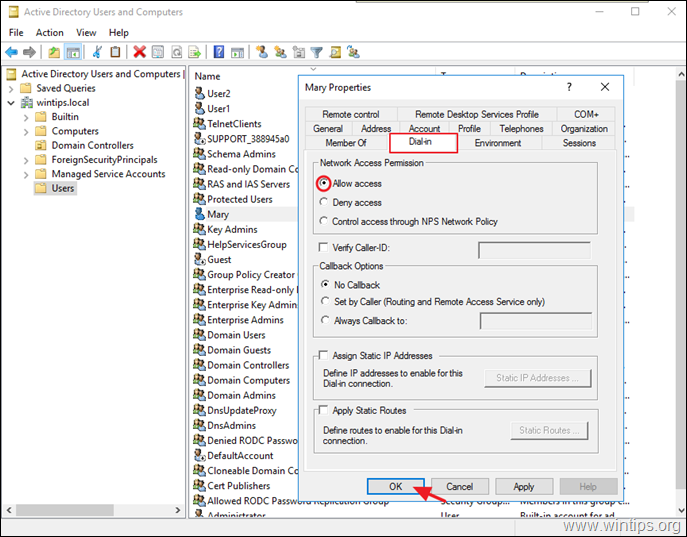
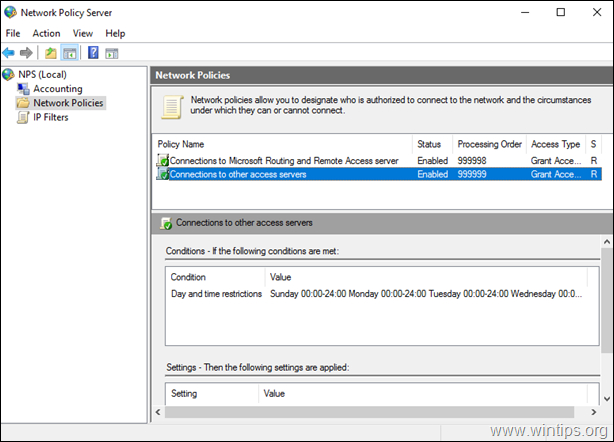
Step 6. How to Configure the Network Policy Server to Allow the Network Access.
In order to allow the VPN users to access the network through the VPN connection, proceed and modify the Network Policy Server as follows:
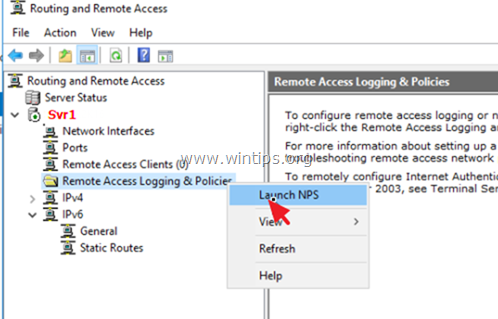
2. Under the NPS (Local) select Network Policies on the left.
3a. Double click at Connections to Microsoft Routing and Remote Access server policy.
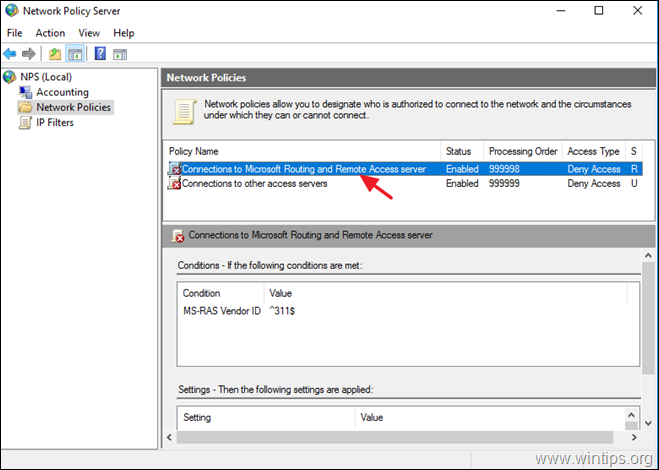
3b. At the ‘Overview’ tab, select the following settings and click OK:
-
- Grant access: If the connection request matches this policy.
- Remote Access Server (VPN-Dial up)
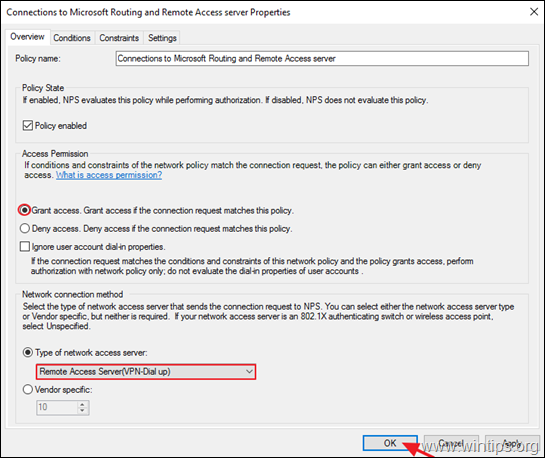
4a. Now open the Connections to other access servers policy, select the same settings and click OK.
-
- Grant access: If the connection request matches this
policy. - Remote Access Server (VPN-Dial
up)
- Grant access: If the connection request matches this
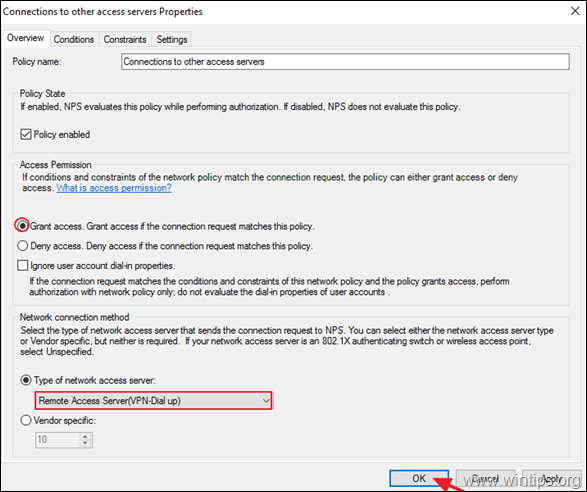
5. Close the Network Policy Server settings.
Step 7. How to Configure Firewall to Allow PPTP VPN Access (Port Forwarding).
The next step is allow the PPTP VPN connections on your ISP’s Router/Firewall.
1. At the top of our browser type your router’s IP address: (e.g. «http://192.168.1.1» in this example) and login to router’s web interface.
2. Inside the Router configuration setup, forward the port 1723 to the IP address of the VPN Server. (See your Router’s manual on how to configure Port Forward). *
- For example, if your VPN Server has the IP address «192.168.1.8» then you have to forward the port 1723 to the IP «192.168.1.8».
Step 8. How to Setup the PPTP VPN Connection on CLIENTS *
* Notes & Additional Help:
1. In order to be able to connect to your VPN server from a distance you have to know the public IP Address of the VPN server. To find the pubic IP Address navigate to this link: http://www.whatismyip.com/ (from VPN Server 2016).
2. To ensure that you can always connect to your VPN server it is better to have a Static Public IP Address. To obtain a Static Public IP Address you must contact your internet service provider. If you don’t want to pay for a static IP Address, then you can setup a free Dynamic DNS service (e.g. no-ip.) on your router’s (VPN Server) side.
To setup a PPTP VPN Connection on Windows 10:
1. From Settings click Network and Internet, OR, right click at the Network icon on the taskbar and choose Open Network & Internet settings.
2. Click VPN on the left and then click + to Add a VPN connection.
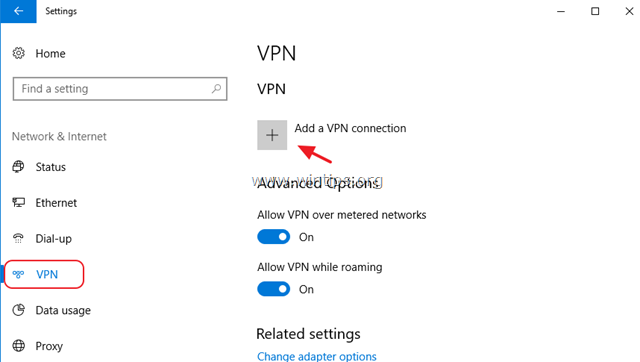
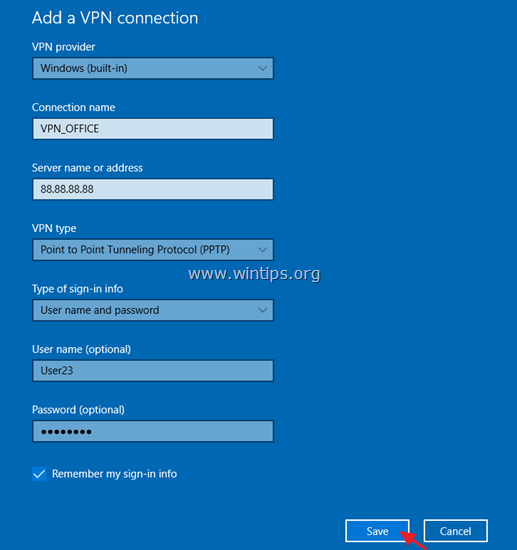
3. At the next screen, fill out the following information and click Save:
a. VPN provider: Select Windows (built-in).
b. Connection name: Type a friendly name for the VPN connection. (e.g.. «VPN_OFFICE»)
c. Server name or address: Type the VPN’s server host name or the public IP address or the VPN server.
d. VPN Type: Use the drop down arrow to select the type of the VPN connection that your company uses. {e.g. «Point to Point Tunneling Protocol (PPTP)»}.
e. Type of sign-in info: Use the drop down arrow and select the authentication type for the VPN connection. (e.g. «User name and password»).
f. User Name: Type the VPN user name.
g. Password: Type the VPN password.
h. Check the «Remember my sign-in info» checkbox, if you want to save your sign-in credentials for the VPN connection and then click Save
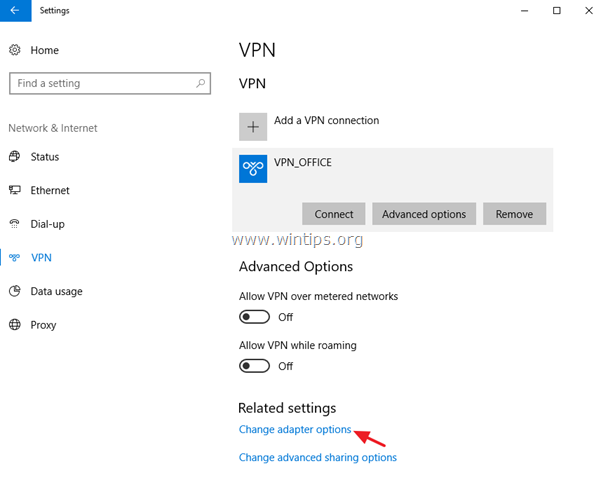
4. Under Related settings, choose Change adapter options.
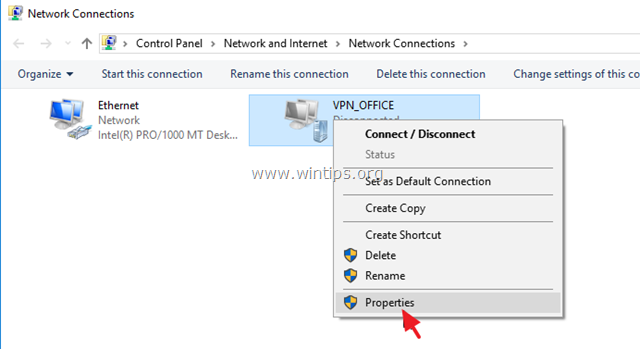
5. Right click on the VPN connection and choose Properties.
6. At Security Tab, select Allow these protocols, and check the following protocols:
-
- Challenge Handshake Authentication Protocol (CHAP)
- Microsoft CHAP Version 2 (MS-SHAP v2)
7. At Networking tab, select the Internet Protocol Version 4 (TCP/IPv4) and click Properties.
7a. Click Advanced.
7b. Uncheck the «Use default gateway on remote network» and click OK three (3) times to apply changes and close all windows.
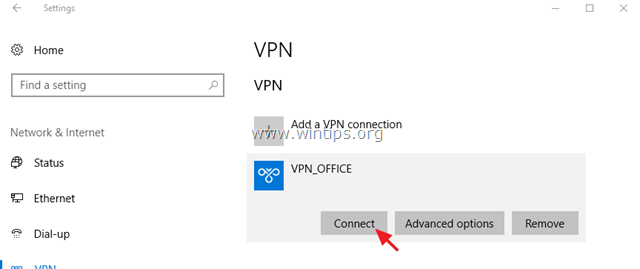
8. Now you’re ready to connect to your VPN Server 2016.
That’s it! Let me know if this guide has helped you by leaving your comment about your experience. Please like and share this guide to help others.
If this article was useful for you, please consider supporting us by making a donation. Even $1 can a make a huge difference for us in our effort to continue to help others while keeping this site free:
- Author
- Recent Posts
Konstantinos is the founder and administrator of Wintips.org. Since 1995 he works and provides IT support as a computer and network expert to individuals and large companies. He is specialized in solving problems related to Windows or other Microsoft products (Windows Server, Office, Microsoft 365, etc.).
