Understanding About Port 135
Port 135 is a Windows Remote Procedure Call (RPC) port that is used for remote management and communication between Windows devices and services. Understanding how this port functions and the risks associated with it is important for managing the security of Windows environments.
Overview of Remote Procedure Call (RPC)
RPC (Remote Procedure Call) is a protocol that allows programs on one computer to execute code and access services on other systems across a network. Microsoft extensively used RPC in Windows for file sharing, printing, naming services, and various system management tasks.
How Does Port 135 Work?
Port 135 is the main port used by RPC services in Windows operating systems. It is called the RPC endpoint mapper and facilitates communication between RPC services by directing network traffic to the correct RPC process on remote computers.
When an RPC request comes in, the endpoint mapper listens on Port 135 and determines which RPC service should handle the request based on the packet’s destination address. It then routes the traffic to the RPC server process responsible over a dynamically assigned port.
Some key RPC services in Windows that rely on Port 135 include:
Without Port 135, none of these vital management functions would work across networks. That is why it is essential for communication between Windows servers and workstations.
What are the Security Risks of Port 135
While RPC and Port 135 are critical for remote Windows administration, they also introduce significant security risks if not properly secured. Some of the main threats associated with Port 135 include:
Malware Exploitation
Many worms and viruses, such as Conficker, Sasser, and Wannacry, specifically target vulnerabilities in the Microsoft RPC services dependent on Port 135 as infection vectors. By flooding the port with malicious RPC requests, they can exploit weaknesses to execute code and spread malware.
Remote Code Execution
Port 135, combined with vulnerable RPC services, can be exploited to execute arbitrary commands on remote Windows systems. This allows attackers to gain unauthorized remote access and perform malicious actions, such as installing backdoors or stealing data.
Distributed Denial of Service (DDoS)
Attackers can abuse RPC communication via Port 135 to overwhelm systems and networks with an excessive volume of requests, which can result in a denial of service and system crashes.
Information Disclosure
Flaws in RPC services can sometimes be leveraged to pull sensitive data, such as system credentials, registry hives, and authentication information, from remote systems over Port 135.
Lateral Movement
Once an attacker gains access to one system on a network, Port 135 provides an avenue for compromising additional systems by moving laterally using RPC, allowing them to quickly infiltrate networks.
How to Secure Port 135 Against Attacks
Because malicious actors frequently target Port 135 to breach into Windows environments, proper configuration is necessary to secure it. Some tips include:
Block Access at the Firewall
Create firewall rules to block all external traffic over Port 135 by default. Only allow access from specific systems that require RPC connectivity for remote management tasks. This prevents external attacks from reaching the port.
Restrict RPC Services
Determine which RPC services, such as Server, Wmi, Netlogon, etc., are absolutely necessary and disable any others to reduce the attack surface. If possible, disable RPC functionality entirely.
Patch and Update Regularly
Apply the latest security updates for Windows and RPC services to ensure no known vulnerabilities can be exploited over Port 135. Keep systems updated against emerging threats.
Use Authentication and Encryption
Configure RPC services to require authentication and encrypt traffic to prevent unauthorized access, data disclosure, or man-in-the-middle attacks.
Monitor and Limit Access
Use tools like Sysmon to log all connection attempts to Port 135. Review regularly and limit access to only trusted sources. Be suspicious of any unknown or unauthorized activity.
Deploy Additional Security Layers
Consider using additional security solutions, such as IPsec, SMB signing, and RDP encryption, to further harden RPC communications against attacks.
Proactively securing Port 135 is one of the most important steps for protecting against damaging Windows malware and intrusions. Combining the measures above can help minimize the risks.
Final Thoughts
Port 135 is fundamentally necessary for the proper functioning of Windows RPC services that allow remote management, file sharing, and communication. However, due to many vulnerabilities, attackers also heavily target it.
By implementing a robust defense-in-depth strategy involving firewall rules, access controls, service hardening, network segmentation, and up-to-date patching, organizations can securely benefit from RPC while minimizing risks from Port 135 exploits. Striking the right balance is crucial for Windows security.
Frequently Asked Questions (FAQ) Related to Port 135
Why is Port 135 a security risk?
Port 135 is a security risk because it provides the endpoint mapper service for Windows RPC communication. Vulnerabilities in RPC services often allow remote code execution, malware spread, DDoS attacks, and other exploits over Port 135.
What is the exact purpose of Port 135?
Port 135’s main purpose is to listen for incoming RPC requests and direct them to the correct RPC server process for handling based on the packet destination address or UUID. This enables remote communication and management between Windows machines.
Should Port 135 be blocked by default?
Yes, generally, Port 135 should be blocked at perimeter firewalls and only allowed access from internal sources that require RPC connectivity for administration tasks. This helps prevent external exploits. Proper authentication and encryption can make some limited exceptions.
Can I completely disable Port 135?
You typically cannot completely disable Port 135 since core Windows functions for file sharing, printing, authentication, and management depend on the RPC services using this port. Disabling it entirely would cause system instability or failure.
Is there an alternative to RPC and Port 135?
Not directly. RPC allows unique cross-network communication between Windows systems that is not easy to replace. However, using strong network segmentation, authentication, and encryption provides additional layers of security on top of RPC to help minimize risks.
How can I detect attacks on Port 135?
Look for connection spikes or brute force activity in firewall logs indicating port scanning or exploit attempts. Use IPS to detect known RPC exploit signatures. Monitor logs from security tools and RPC services themselves for anomalies.
What’s the best way to manage RPC security?
Use a remote procedure call (RPC) firewall to manage RPC network traffic. Disable unneeded RPC services. Apply the latest security patches. Use IPsec policies to authenticate and encrypt RPC communications between hosts. Limit RPC connections only to trusted sources.
by Colin Cohen | Published on June 13, 2024

Port 135 is dedicated to the Windows Remote Procedure Call (RPC) Mapper Service.
Many crucial services, such as Windows Server Active Directory, rely on the port for remote client-server communication.
What is Port 135?
You use port 135 in Windows environments when you have clients and servers that need to remotely connect to each other. They use the RPC Mapper Service running on the port to determine what services are available to them and to learn which ports they are available at.
Definition
Devices in Windows environments will often run the RPC Mapper Service on port 135. This allows other machines that remotely connect to them to learn what services are running and on what ports they can connect to them. These services typically relate to remote access and management.
Understanding Port 135
You use port 135 for making remote procedure calls using the RPC protocol. The protocol lets you execute functions on a remote device over a network. It operates in both the application and transport layer of the Open Systems Interconnection (OSI) model used in network communication.
Protocol Association
When using port 135 for the Windows RPC Mapper Service, you are implementing the RPC protocol. It allows devices to remotely communicate with each other over a network to determine what services are available and how to connect to them.
What is Port 135 Used for?
Port 135 enables remote communication between clients and servers in Windows environments. Important services such as Windows Management Instrumentation (WMI) and AD rely on this port being open so that they can function properly.
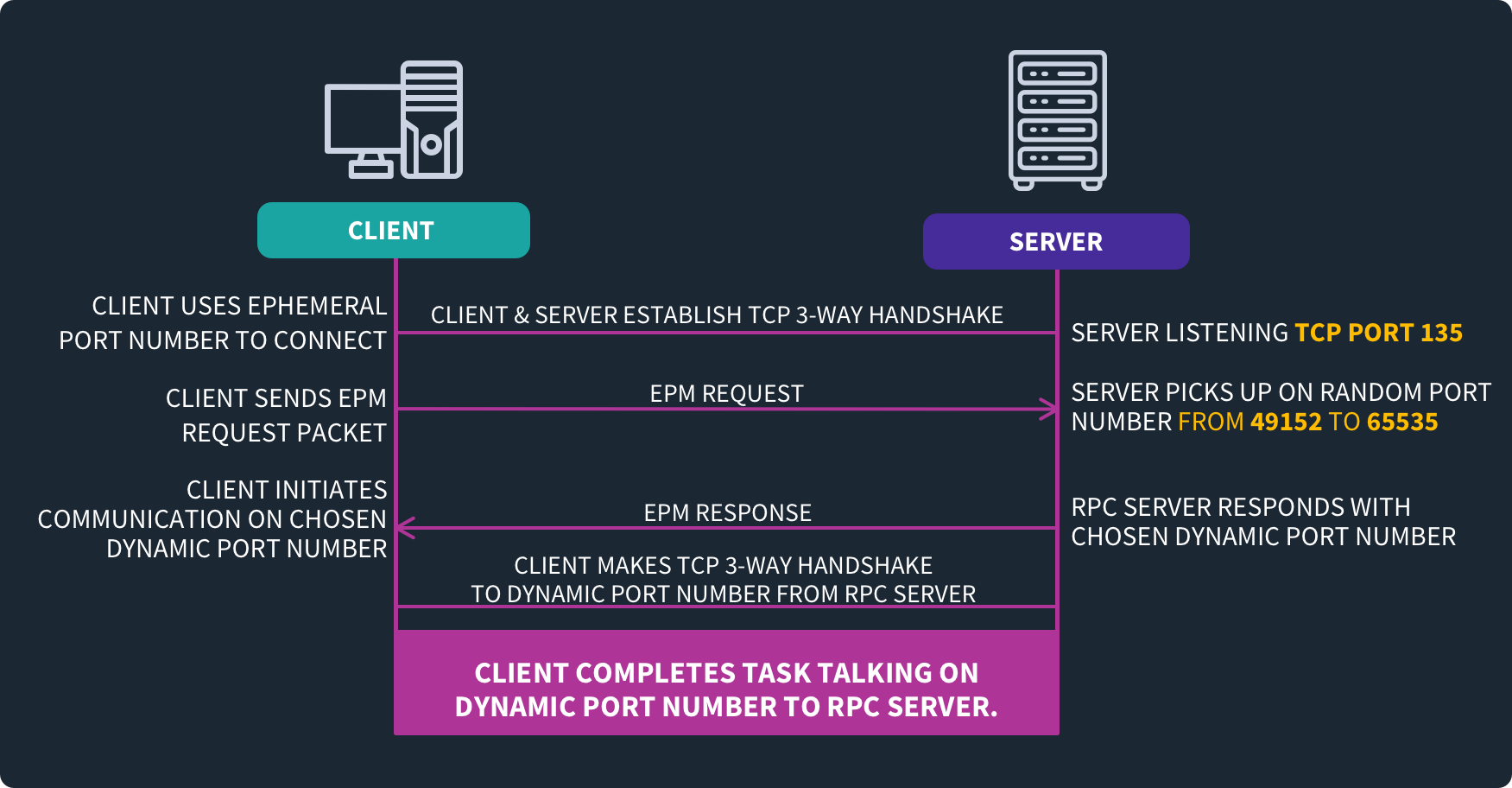
Primary Functions
The purpose of port 135 is to facilitate remote communication between clients and servers in a Windows environment. Without access to port 135 on devices, other devices would be unable to determine what services are available on them, nor would they be able to know on which ports these services are running.
Industry Use Cases
A typical example of a service that relies on port 135 is Windows Management Instrumentation (WMI). It allows administrators to remotely administer client devices. If port 135 is not open on the remote computer, WMI will not function.
Another service that depends on port 135 is AD. This is a directory service that allows clients to remotely access important network resources.
How to Make Sure Port 135 is Secure
Port 135 is susceptible to several serious exploitations, so it is important for you to know how to secure it properly.
Exploitation Risks
If port 135 is left open on the public Internet, it can leave devices vulnerable to dangerous attacks such as remote command executions (RCEs), sensitive data exposure, and distributed denial-of-service (DDoS) attacks. Because of this, you must properly secure port 135 on your client and server devices that use the port.
Best Practices for Security
If you are not working in a Windows environment or don’t need remote access and management, you probably should close port 135 on your devices.
Otherwise, you should restrict access to port 135 in your firewall to local IP addresses only. You should also consider implementing authentication and encryption mechanisms on the port, such as SMB signing, IPsec, and Kerberos.
Disabling and Closing Port 135
To close port 135 in Windows, do the following:
-
Open the Firewall Control Panel by running firewall.cpl in a command prompt.
-
Select Advanced Settings and click Inbound Rules.
-
Click New Rule under Action.
-
Select TCP and Specific local ports, and enter 135.
-
Under Action, select Block the connection and click Next.
-
Under Profile, select Domain and Private and click Next.
-
Under Name, enter a name for the rule and click Finish.
-
Repeat steps 2 through 7 for Outbound Rules.
Monitoring and Troubleshooting Port 135
If your organization uses the RPC Mapper Service for remote access and management of your devices, you need to know whether port 135 is open on them. You also need to know how to troubleshoot conflicts on the port.
Detecting Port 135 Activity
To determine whether port 135 is open on a device, run the following command from a Windows command prompt:
Resolving Port 135 Conflicts
Only one service can listen to port 135 at a time. If you want to run the RPC Mapper Service on port 135 and discover through the netstat command that another service is listening on this port, you must disable this other service before you can start the RPC Mapper Service.
Frequently Asked Questions
The following FAQs answer questions typically asked relating to port 135. They provide a basic understanding of the port and its uses.
What is TCP port 135 used for?
You use TCP port 135 for remotely connecting clients and servers in a Windows environment through the RPC Mapper Service. It allows devices to see what services other devices provide and on which ports these services are available.
Can port 135 be exploited?
If you leave port 135 open on the public Internet, your devices can be susceptible to serious exploitations, such as RCE and DDoS attacks. So it’s important to implement security practices as described in the How To Make Sure Port 135 is Secure section.
Is it safe to block port 135?
If you don’t operate in a Windows environment or don’t need remote access and management, it is safe to block port 135 on your devices. But if you do need remote access and management in a Windows environment, you should leave the port open and instead implement security practices such as those described in the How To Make Sure Port 135 is Secure section.
How do I know if port 135 is listening?
You can check if a device is listening on port 135 by using the netstat command, as described in the Monitoring and Troubleshooting Port 135 section. Both clients and servers need to listen on this port to enable important Windows services such as WMI.
Conclusion
You use port 135 to implement the RPC Mapper Service in a Windows environment. It allows clients and servers to communicate for remote access and management. However, as port 135 is susceptible to various serious exploitations, you must know how to properly secure the port.
In this post, I will explore the TCP and UDP ports used by Active Directory from client to server.
I will use WireShark and a series of tests to determine what ports are used.
Tests I’ll be running:
- Ports Used When a User Logs into a Computer
- Ports used when running gpupdate
- Ports used when joining a computer to the domain
- Ports Used When Rebooting
Test Environment:
- Server 2022 with IP 192.168.100.10 (Active Directory Server)
- Windows 10 Pro with IP 192.168.100.20
- Wireshark is installed on the Active Directory server
- The Active Directory server is a default install
Here is a list of ports used by Active Directory by a default install. This is between the domain controller and a domain-joined computer.
- TCP 135 Microsoft RPC
- TCP/UDP 49152 – 65535 RPC Dynamic Ports
- TCP 88 Kerberos
- TCP 389 LDAP
- UDP 53 DNS
- TCP 445 SMB
TCP 135 Microsoft RPC Mapper
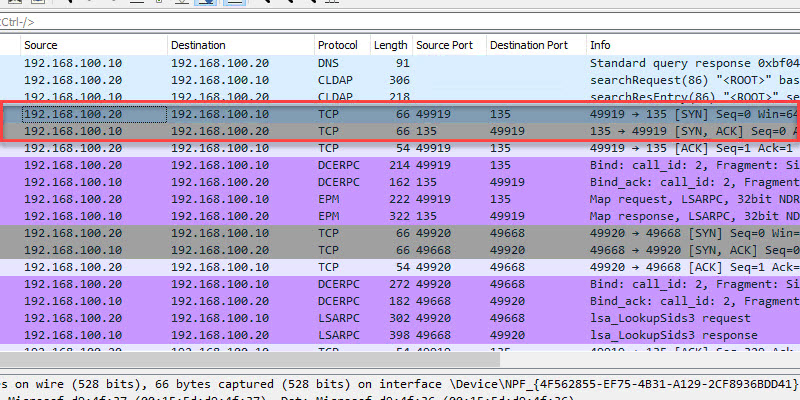
- Description: Port 135 is a critical client/server port. This port is used by many Microsoft services and should not be blocked by a firewall. First the client connects to the RPC mapper service (port 135) and asks the mapper what port a given service is listening on (which will be a dynamic port range… see below). The RPC mapper responds to the client with the port and then the client connects to that port. You can see this in the above screenshot.
- Firewall: Allow between client and server. Port 135 should not be exposed to the internet.
TCP/UDP 49152 – 65535 RPC Dynamic Ports
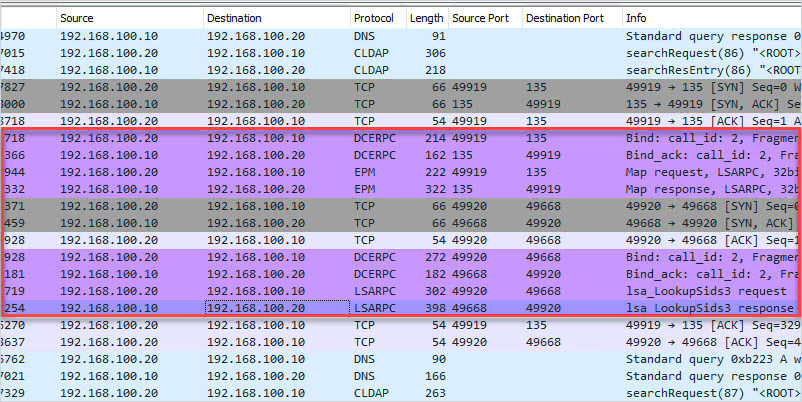
- Description: The dynamic port range is used by various server applications. RPC dynamic port allocation instructs the RPC program to use a particular random port in the range configured for TCP and UDP, based on the implementation of the operating system used. The RPC mapper (port 135) is used to connect clients to services running on these dynamic ports.
- Firewall: Allow between client and server. This port range should not be exposed to the internet.
we recommend that you reconfigure the firewalls to allow traffic between servers in the dynamic port range of 49152 through 65535. This range is in addition to well-known ports that are used by services and applications.
https://docs.microsoft.com/en-US/troubleshoot/windows-server/networking/default-dynamic-port-range-tcpip-chang
TCP 88 Kerberos
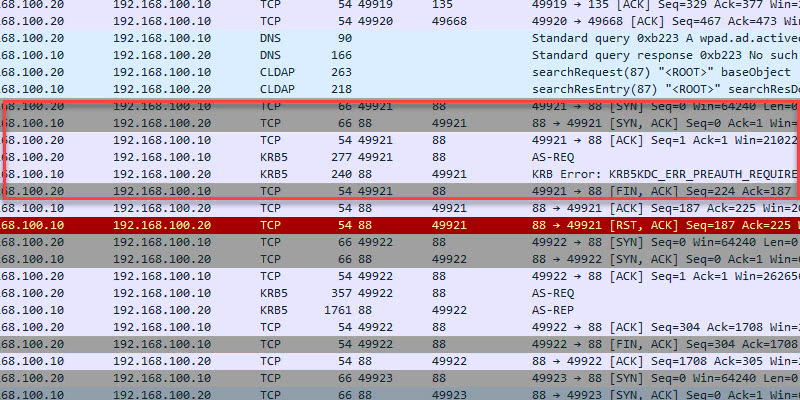
- Description: Kerberos is an authentication protocol that authenticates requests between a client and server in a secure manner. This is Microsoft Window’s default authentication method for domain-joined devices.
- Firewall: Allow between client and server. Port should not be exposed to the internet.
TCP 389 LDAP
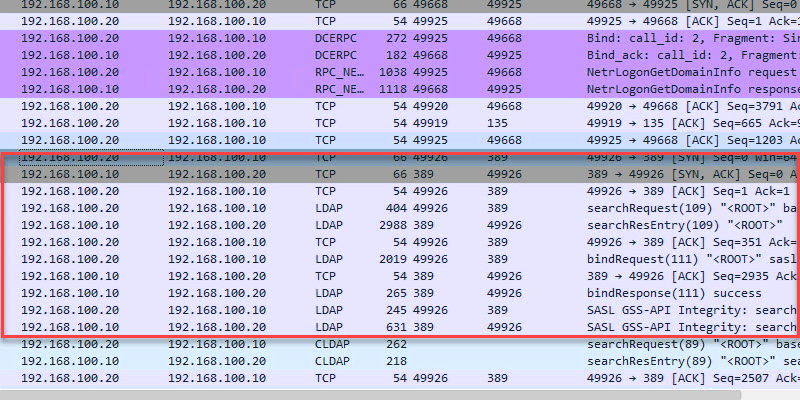
- Description: LDAP is a directory access protocol. This protocol is used to search, add/delete, authenticate and modify data in a Directory Server such as Active Directory.
- Firewall: Allow between client and server. Port should not be exposed to the internet.
UDP 53 DNS
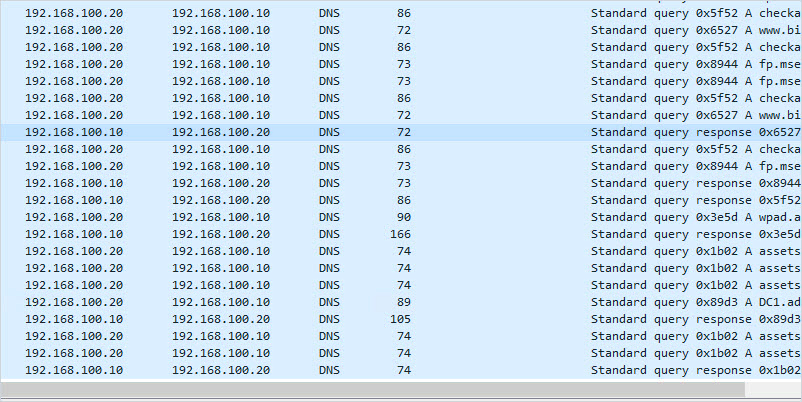
- Description: DNS is a critical service used to map IP addresses to host names. This is a critical service used by clients to locate resource records in the domain and lookup external domain names.
- Firewall: Allow between client and server. If DNS is running on your Active Directory server I do not recommend exposing it to the internet.
TCP 445 SMB
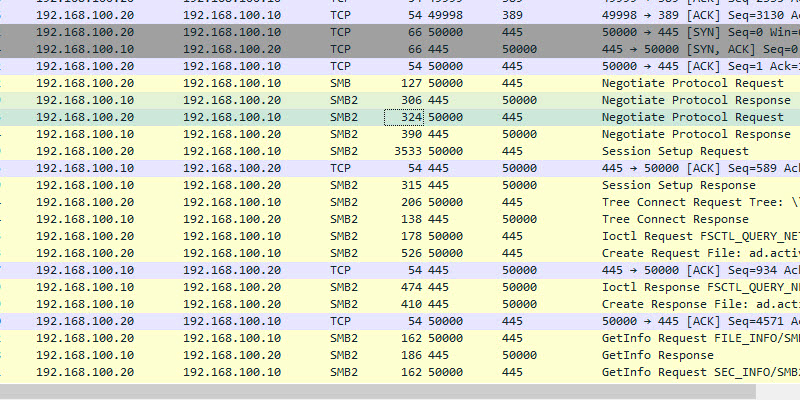
- Description: Server message blocks (SMB protocol) is a client-to-server communication protocol used for accessing files, printers, and data on a network. This port is used during startup to get GPO information, it is also used when running the gpupdate command.
- Firewall: Allow between client and server. Do not expose this port to the internet.
Ports Used When a User Logs into a Domain-Joined Computer
In this example, I will log into computer PC1 (192.168.100.20) and capture the network packets from the domain controller.
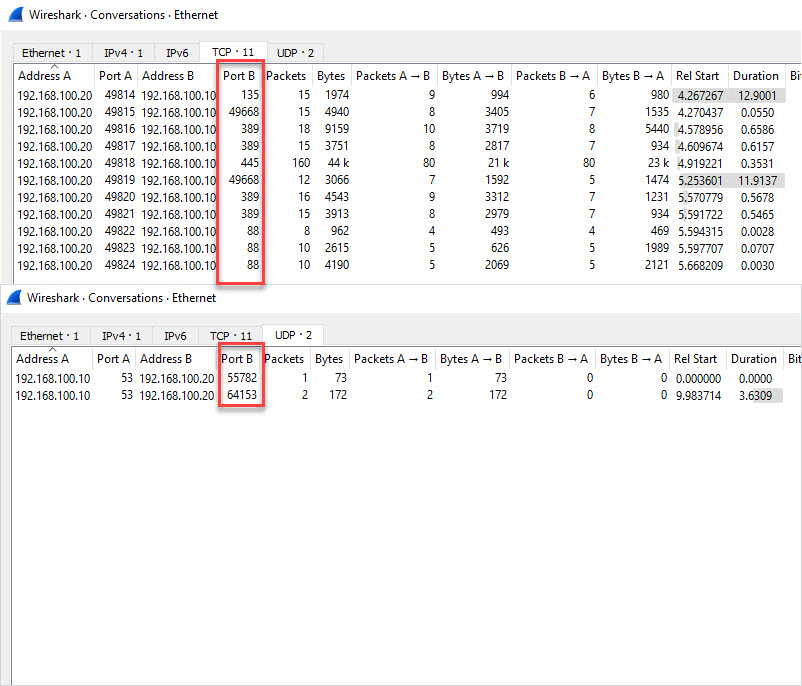
Here is a conversation view of the TCP/UDP ports used. This is traffic sent from the client to the domain controller and destination ports.
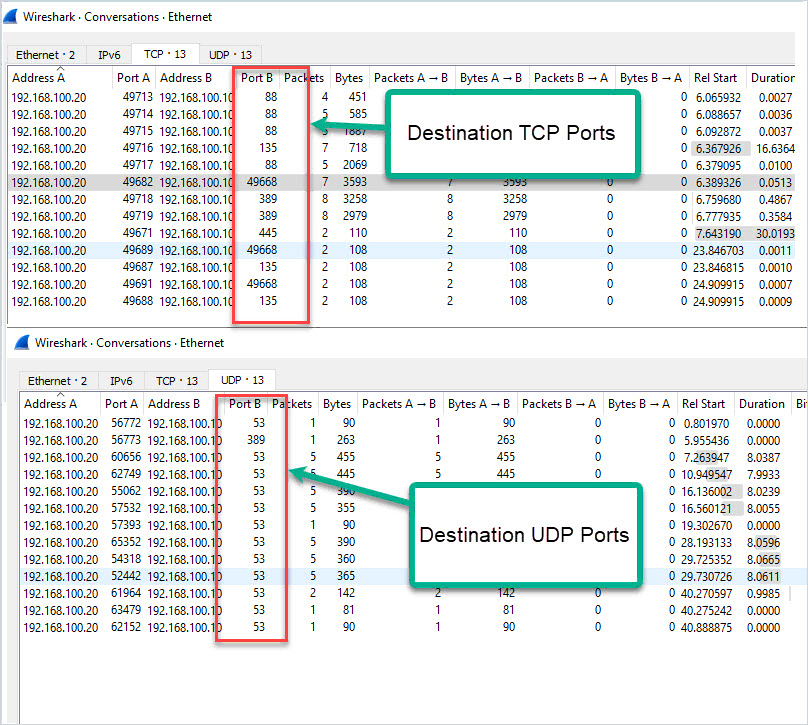
Here is a summary of the destination ports used by the client.
- TCP 88 (Kerberos)
- TCP 135 (Microsoft RPC)
- TCP 389 (LDAP)
- TCP 445 (Microsoft DS)
- TCP 49668 (RPC for LSA, SAM, NetLogon) – This starts with a request to port 135
- UDP 53 (DNS)
- UDP 389 (LDAP)
Ports Used When Running Gpupdate
While logged into the client PC I will run the gpupdate command to see what ports are used.
Results below. It Looks like TCP port 445 is used the most when running a gpupdate.
Ports Used When Joining a Computer to The Domain
This looked similar to the other packet captures.
TCP 88 (Kerberos)
TCP 135 (Microsoft RPC)
TCP 389 (LDAP)
TCP 445 (Microsoft DS)
TCP 49668 (RPC for LSA, SAM, NetLogon) – This starts with a request to port 135
UDP 53 (DNS)
Ports Used When Rebooting
Nothing new, I see the same ports used when compared to the other packet captures.
Hopefully, this guide helps you to understand the ports used between a client and an Active Directory server. Keep in mind this test was a default domain controller install with no additional services running, the more services you install the more ports that may be used.
Resources:
- Service overview and network port requirements for Windows
- Service Name and Transport Protocol Number Registry
Power Admin monitoring products contain a variety of modules that monitor different server resources. In general, the server resources are
accessed through one of three ways:
- Standard protocol ports
- Windows RPC
- Windows SMB/CIFS (file serving)
Do you need to monitor
servers in a DMZ?
Using the Satellite monitoring service that comes with the Ultra edition makes it much easer.
Distributed monitoring is easy. Check it out 
Standard Protocol Ports
Standard Protocol Ports would be those ports that are used by a protocol-specific monitor. For example, the Web Page monitor uses HTTP, and therefore (by default)
port 80 to access the remote server. The SMTP server monitor uses a default port of 25, POP3 is a default of port 110, etc. These standard protocol monitors therefore use
the port specified by the relevant standard.
Standard Ports:
FTP
Port 21
DNS
Port 53
Mail (POP3)
Port 110
Mail (IMAP)
Port 143
Mail (SMTP)
Port 25
SNMP
Ports 161 and 162
Web (HTTP)
Port 80
Web (HTTPS)
Port 443
Windows RPC
See below for Windows Firewall rules for Windows.
Windows-specific monitors (Event Log monitor, Service monitor, Performance monitor, etc) use standard Windows RPC to access the underlying resources. Windows RPC
uses TCP port 135 by default (although you can change this via tools on the Microsoft website). Because port 135 is targeted by much of the malware and worms on
the Internet, we do not recommend opening that port on an Internet-facing firewall.
Besides port 135, RPC also uses a dynamic port range that gets established between the endpoints. Microsoft has more information, including firewall considerations:
- How to configure RPC dynamic port allocation to work with firewalls
- Allowing in-bound traffic that uses dynamic RPC
Windows SMB / CIFS
Windows disk-based monitors (Disk Space monitor, File & Directory Change monitor, etc) use standard Windows SMB to access the underlying files and directories. Windows SMB
uses TCP port 445 by default (although you can change this via tools on the Microsoft website). Because port 445 is targeted by much of the malware and worms on
the Internet, we do not recommend opening that port on an Internet-facing firewall.
CIFS is another popular file sharing protocol that is basically the same as SMB.
It is supported by Linux via SAMBA, and many other operating systems and devices.
Additional Information
Windows
Windows comes with a very strict firewall which is enabled by default. Go to Control Panel > Windows Firewall with Advanced Security to the incoming rules,
and enable the Remote Administration rule to enable typical monitor access.
The Windows firewall is very strict and tightly locked down in its default configuration. For monitoring the server, consider enabling the following rules:
Disk Space
- File and Printer Sharing (SMB-In)
Event Log
- Remote Event Log Management (RPC)
- Remote Event Log Management (RPC-EPMAP)
- Also make sure the user account that is monitoring the server is a member of the target server’s «Event Log Readers» or the «Administrators» group.
Performance Counters
- File and Printer Sharing (SMB-In)
- Also make sure the user account that is monitoring the server is a member of the target server’s «Performance Monitor Users» or the «Administrators» group.
Ping
- File and Printer Sharing (Echo Request — ICMPv4-In)
- File and Printer Sharing (Echo Request — ICMPv6-In)
Services
- Remote Service Management (RPC)
- Remote Service Management (RPC-EPMAP)
Inventory Collection
- Windows Management Instrumentation (DCOM-In)
- COM+ Network Access (DCOM-In)
- A good overview of Windows network port usage is available at: Service overview and network port requirements for the Windows Server system
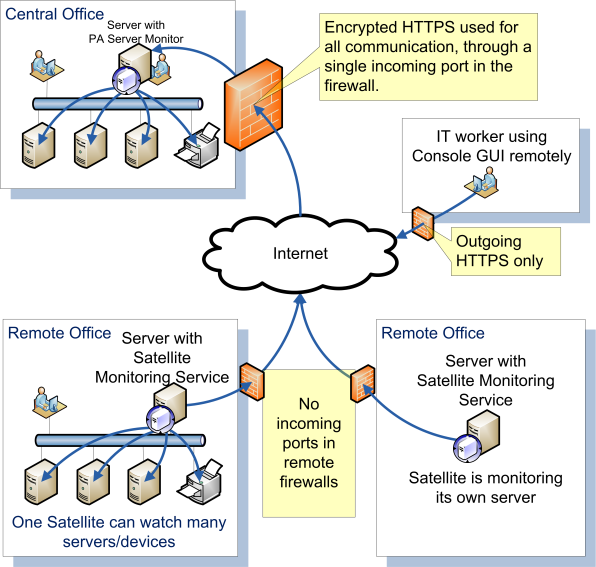
Alternative — Single HTTPS Port
If opening firewall ports is not desired, a good option is to use PA Server Monitor’s Satellite Monitoring Service. It is a small piece of software
installed on a single server on the other side of the firewall that will monitor other devices on that side, and then report back to your central service.
This works across firewalls as well as it does across the Internet at remote data centers.
Only a single incoming port for HTTPS traffic needs to be opened on the firewall.
View this page for more information.
Testing
To test if the ports are correctly opened, we recommend using a Windows app, like the Windows Event Log Viewer for example. Start eventvwr.msc and see if you can use
it to connect to and view the remote Event Log. If this works, any firewalls in between are letting the requests through. For advanced firewalls like the one in
Windows Server 2012, you should also try this with the Services applet (services.msc) and the Performance viewer (perfmon.msc) if you will be monitoring those
resources.
MSRPC
MSRPC usually uses ports 135, 593
What is MSRPC?
Microsoft Remote Procedure Call, also known as a function call or a subroutine call, is a protocol that uses the client-server model in order to allow one program to request service from a program on another computer without having to understand the details of that computer’s network. MSRPC was originally derived from open source software but has been developed further and copyrighted by Microsoft.
Depending on the host configuration, the RPC endpoint mapper can be accessed through TCP and UDP port 135, via SMB with a null or authenticated session (TCP 139 and 445), and as a web service listening on TCP port 593.
MSRPC working on only:
- Windows Server 2003
- Windows Server 2003 R2
- Windows Server 2003 with SP1
- Windows Server 2003 with SP2
1 2 |
PORT STATE SERVICE VERSION 135/tcp open msrpc Microsoft Windows RPC |
How does MSRPC work?
The MSRPC process begins on the client side, with the client application calling a local stub procedure instead of code implementing the procedure. The client stub code retrieves the required parameters from the client address space and delivers them to the client runtime library, which then translates the parameters into a standard Network Data Representation format to transmit to the server.
The client stub then calls functions in the RPC client runtime library to send the request and parameters to the server. If the server is located remotely, the runtime library specifies an appropriate transport protocol and engine and passes the RPC to the network stack for transport to the server. For more details, please check this link.

Pentesting MSRPC
| Shodan search query : |
|---|
port:135,593,445 |
1 2 |
nmap -sV -p135 10.10.x.x nmap -p135 --script=msrpc-enum 10.10.x.x |

1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 |
########################################## enum4linux ########################################## # Verbose mode enum4linux -v 192.168.x.x # Do everything enum4linux -a 192.168.x.x # List users enum4linux -U 192.168.x.x # If you've managed to obtain credentials, you can pull a full list of users regardless of the RestrictAnonymous option enum4linux -u administrator -p password -U 192.168.x.x # Get username from the defaut RID range (500-550, 1000-1050) enum4linux -r 192.168.x.x # Get username using a custom RID range enum4linux -R 600-660 192.168.x.x # List groups enum4linux -G 192.168.x.x # List shares enum4linux -S 192.168.x.x # Perform a dictionary attack, if the server doesn't let you retrieve a share list enum4linux -s shares.txt 192.168.x.x # Pulls OS information using smbclient, this can pull the service pack version on some versions of Windows enum4linux -o target-ip # Pull information about printers known to the remove device. enum4linux -i target-ip # enum4linux-ng is a rewrite of the official tool (python3) # adding some features like colors and parsing https://github.com/cddmp/enum4linux-ng |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 |
########################################## rpcclient ########################################## # Anonymous connection (-N=no pass) rpcclient -U "" -N 192.168.x.x # Connection with user rpcclient -U "user" 192.168.x.x # Get information about the DC srvinfo # Get information about objects such as groups(enum*) enumdomains enumdomgroups enumalsgroups builtin # Try to get domain password policy getdompwinfo # Try to enumerate different truste domains dsr_enumtrustdom # Get username for a defined user ? getusername # Query user, group etc informations queryuser RID querygroupmem519 queryaliasmem builtin 0x220 # Query info policy lsaquery # Convert SID to names lookupsids SID #Different tool RPCinfo rpcinfo –p 192.168.x.x |


Identifying Exposed RPC Services
You can query the RPC locator service and individual RPC endpoints to catalog interesting services running over TCP, UDP, HTTP, and SMB (via named pipes). Each IFID value gathered through this process denotes an RPC service (e.g., 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc is the Messenger interface).
Todd Sabin’s rpcdump and ifids Windows utilities query both the RPC locator and specific RPC endpoints to list IFID values. The rpcdump syntax is as follows:
1 |
python3 /usr/share/doc/python3-impacket/examples/rpcdump.py 192.168.x.x |

You can access the RPC locator service by using four protocol sequences:
- ncacn_ip_tcp and ncadg_ip_udp (TCP and UDP port 135)
- ncacn_np (the \pipe\epmapper named pipe via SMB)
- ncacn_http (RPC over HTTP via TCP port 80, 593, and others)
1 2 3 4 |
msf6 > use auxiliary/scanner/dcerpc/endpoint_mapper msf6 > use auxiliary/scanner/dcerpc/hidden msf6 > use auxiliary/scanner/dcerpc/management msf6 > use auxiliary/scanner/dcerpc/tcp_dcerpc_auditor |


Note that from the mentioned options all except of
tcp_dcerpc_auditorcan only be executed against msrpc in port 135.
Notable RPC interfaces
| IFID value | Named pipe | Description |
|---|---|---|
| 12345778-1234-abcd-ef00-0123456789ab | \pipe\lsarpc | LSA interface, used to enumerate users |
| 3919286a-b10c-11d0-9ba8-00c04fd92ef5 | \pipe\lsarpc | LSA Directory Services (DS) interface, used to enumerate domains and trust relationships |
| 12345778-1234-abcd-ef00-0123456789ac | \pipe\samr | LSA SAMR interface, used to access public SAM database elements (e.g., usernames) and brute-force user passwords regardless of account lockout policy Oreilly library |
| 1ff70682-0a51-30e8-076d-740be8cee98b | \pipe\atsvc | Task scheduler, used to remotely execute commands |
| 338cd001-2244-31f1-aaaa-900038001003 | \pipe\winreg | Remote registry service, used to access the system registry |
| 367abb81-9844-35f1-ad32-98f038001003 | \pipe\svcctl | Service control manager and server services, used to remotely start and stop services and execute commands |
| 4b324fc8-1670-01d3-1278-5a47bf6ee188 | \pipe\srvsvc | Service control manager and server services, used to remotely start and stop services and execute commands |
| 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57 | \pipe\epmapper | DCOM interface, supporting WMI |
Identifying IP addresses
Using https://github.com/mubix/IOXIDResolver, comes from Airbus research is possible to abuse the ServerAlive2 method inside the IOXIDResolver interface.
This method has been used to get interface information as IPv6 address from the HTB box APT. See here for 0xdf APT writeup, it includes an alternative method using rpcmap.py from Impacket with stringbinding (see above).

