Estimated reading: 3 minutes
1292 views
Using password policy can enhance password’s security. It requires users to set password length, password age, password history, etc. Via password policy, you can set a more complicated password that’s hard to be guessed or cracked.
In this article, we will guide you to Set Password Policy on Windows server 2019.
Step 1: Press “Win” + “R” key to open “Run” window. Type in: secpol.msc then click “OK”.

Step 2: After you open “Local Security Policy”, select them in order: “Security Settings” > “Account Policies” > “Password Policy”.

Step 3: In the right pane, double click any policy and change the setting according to your needs.

Explanation of Setting Each Password Policy
Password Must Meet Complexity Requirements
Requirements as below:
1. More than two contiguous characters from user name cannot be contained in password.
2. Be at least six characters in length and three of following four types of character need to be included in password.
• English uppercase characters (A through Z)
• English lowercase characters (a through z)
• Base 10 digits (0 through 9)
• Non-alphabetic characters (for example, !, $, #, %)
Minimum Password Length
The longer the password, the safer it will be. A password should at least contain the minimum number of characters for a user account.

Minimum Password Age
This security setting determines the period of time (in days) that a password must be used before the user can change it. For example, if you set 10 days, then your password can be changed after 10 days. Besides, password can be changed anytime if the minimum password age is set to be 0.
Maximum Password Age
This security setting determines the period of time (in days) that a password can be used before the system requires the user to change it. For example, if you set 90 days, your password will expire in 90 days then system will require you to change it. But the password will not expire if the maximum password age is set to 0.

Enforce Password History
This security setting determines the number of unique new passwords that have to be associated with a user account before an old password can be reused. It can ensure the old passwords are not reused continually. For example, if you keep 9 passwords remembered, then you need to change new passwords nine times before an old password can be reused.

Store Passwords Using Reversible Encryption
This security setting determines whether the operating system stores passwords using reversible encryption. If this policy is enabled, some bad guys may easily crack the password and access users’ PCs. It’s suggested to disable it unless application requirements are more important than the protection of password information.
Conclusion
So we have guided you through the steps set Password Policy on Windows server 2019 this will help increase security on your VPS.

Hello, how are you doing? In this opportunity, we will talk about password policies on Windows Server 2019. Once we have managed users through Active Directory, we need to set the valid date of the passwords. Indeed, sometimes we need to restrict access to certain users due to the security policies of the organization.
Please keep in mind that when working with servers, security is a fundamental aspect. For this reason, there are several reasons for modifying the duration of passwords. For this reason, there are several reasons for modifying the duration of passwords. According to the type of use, it is convenient to establish passwords with security time. For example, to temporary users, test users or those who are practicing in the company.
Now, we have two options for modifying password expiration policies on Windows Server 2019. Group Policy: Apply for when the computer is included in a corporate domain with Windows Server Domain Controller. Local Security Policy: Applies when our group is not in a domain, but is in a workgroup or is managed locally. Here’s how to change a password or change the expiration date of a password within Windows Server 2019 step by step.
Changing password expiration through Local Security Policy on Windows Server 2019
Below we will detail the process for entering the password policy configuration.
Step 1. Open Local Group Policy Editor
First, we need to enter Group Policy Management by clicking Windows+R and typing gpedit.msc

Once there, we must follow the next route: Local Computer Policy>Computer Configuration>Windows Settings>Security Settings>Password Policy

Step 2. Editing password policies
The editor allows you to configure different aspects of the password:
Enforce password history. This security setting determines the number of unique new passwords that have to be associated with a user account before an old password can be reused. The value must be between 0 and 24 passwords.
Maximum password age. This security setting determines the period of time (in days) that a password can be used before the system requires the user to change it. You can set passwords to expire after a number of days between 1 and 999, or you can specify that passwords never expire by setting the number of days to 0.
Minimum password age. This security setting determines the period of time (in days) that a password must be used before the user can change it. You can set a value between 1 and 998 days, or you can allow changes immediately by setting the number of days to 0.
Minimum password length. This security setting determines the least number of characters that a password for a user account may contain. It can set a value of between 1 and 20 characters, or you can establish that no password is required by setting the number of characters to 0.
Password must meet complexity requirements. This security setting determines whether passwords must meet complexity requirements.
Password Requirements
If it enabled, the password must meet the following minimum requirements:
Not contain the user’s account name or parts of the user’s full name that exceed two consecutive characters
Be at least six characters in length
Contain characters from three of the following four categories:
English uppercase characters (A through Z)
English lowercase characters (a through z)
Base 10 digits (0 through 9)
Non-alphabetic characters (for example, !, $, #, %)
Store passwords using reversible encryption. This security setting determines whether the operating system stores passwords using reversible encryption. This policy provides support for applications that use protocols that require knowledge of the user’s password for authentication purposes.
Changing password expiration through Local Active Directory on Windows Server 2019
To access the domain password policy editor, we need to open the Server Manager. Next, click on the Active Directory Administrative Center tool.

In the next window, select the forest and then follow the following path: Domains>nameofdomain>Default Domain Policy. Where nameofdomain is the name of our domain, in my case telematic.local. Next, double click on Default Domain Policy to edit the values.

Once the window opens, follow this path: Default Domain Policy>Compuer Configuration>Policies>Windows Settings>Security Settings>Password policy

As we see we have the same options as in the local directives, the only difference is that if we open the local policies with our computer in a domain we cannot make any change in the directives. On the other hand, from a computer in a domain using this option if we will be able to make adjustments in the policies.
Changing or unlocking administrator password on Windows Server 2019
Sometimes it happens that we want to change the administrator password, or the account has been blocked. Sometimes it happens that we want to change the administrator password, or the account has been blocked. To do this, we must enter the Server Manager and select Active Directory Administrative Center.

Once there, all you have to do is select Reset Password, and enter the new password or unblock the account if it is locked.

As has been noted, the process for changing password policies is not that complicated. However, we must be careful when modifying these values, as it will affect the entry of users. In conclusion, Windows Server 2019 is a very friendly system and has wizards that facilitate the changes desired by the server administrator.
Well, this is all for now, before saying goodbye I would like to invite you to review our tutorial on installing Apache on Windows Server 2019.
— Advertisement —
Everything Linux, A.I, IT News, DataOps, Open Source and more delivered right to you.
Subscribe
«The best Linux newsletter on the web»
If you’re an IT professional looking to maximize the security of your Windows Server 2019, a password policy is your best bet. Password policy Windows Server 2019 is an important aspect of ensuring your infrastructure is protected from malicious actors who may try to gain access. Implementing a password policy for Windows Server 2019 allows you to control the strength and complexity of passwords used on your systems. Establishing strong guidelines for setting passwords can help deter hackers from accessing your network and prevents the risk of data breaches. By utilizing password policy Windows Server 2019, you can rest easy knowing that your information is secure.
1. Securing Your Network with a Password Policy for Windows Server 2019
Keeping the network safe and secure is a major priority for organizations. Fortunately, there are ways you can keep your Windows Server 2019 secure with a password policy. Here are some of the steps you should take:
- Create a Strong password: Ensure each user has their own unique password that is difficult to guess. The password should be longer than eight characters and include both letters and numbers.
- Require periodic changes: Enforce users to change their passwords at regular intervals in order to keep the system secure.
- Restrict access to specific user accounts: Only grant access to user accounts on a need to know basis. By restricting access to specific user accounts, the security of the network is strengthened.
In addition to creating a strong password policy, it is important to regularly audit user accounts. This allows administrators to look for suspicious activity and revoke access for user accounts that are no longer needed. Organizations should also take steps to protect their network from external threats such as malware, viruses, and hackers. This can be done by deploying antivirus software and a firewall to the network.
2. Step-by-Step Guide to Setting Up Password Policies for Windows Server 2019
Step 1: Access Group Policy Settings
To get started with password policies, you will need to access the Group Policy Settings on Windows Server 2019. To do this, open your server and press the Windows key to navigate to the start menu. At the start menu, type in “Edit Group Policy” to show the app you need. Once you have launched the application, you will be able to configure password policies for your server.
Step 2: Setting Up Password Properties
Once you are in the Group Policy Settings, you can now setup the password policies. The following properties need to be setup:
- Enforce password history
- Minimum password length
- Password must meet complexity requirements
- Store password using reversible encryption for all users in the domain
Each property has a different set of instructions that need to be followed to ensure the password policies are configured correctly. Make sure to follow each set of instructions carefully and save your changes when you’re done.
3. The Benefits of Configuring a Password Policy for Windows Server 2019
Windows Server 2019 brings a comprehensive solution for setting up a secure password policy that offers amazing benefits. With this secure password policy, a Windows server admin can strengthen their system’s security with robust password requirements for keeping those with malicious intent away from harm.
- Protection from Brute Force Attacks: By implementing a strong password policy, a Windows server admin can protect their system from brute force attacks. These attacks involve repeated attempts at guessing passwords. A strong password policy requires passwords with complex characters and can significantly reduce the chances of such an attack.
- Enhanced Data Security: A secure password policy helps to prevent any sort of data theft or unauthorized access. Requiring complicated passwords that regularly need to be updated, ensures that the chances of data falling into the wrong hands are low.
Apart from protection against malicious activities, configuring a secure password policy for Windows Server 2019 also helps to limit user errors. As long as the passwords meet the criteria set out by the admin, users do not need to remember multiple usernames and passwords. This also eases the need for technicians to help users with resetting forgotten passwords.
4. Protect Your Assets with the Right Password Policy for Windows Server 2019
Protecting your Windows Server 2019 assets is essential for keeping your data safe and secure. To ensure maximum security, it’s imperative to employ a strong password policy that meets industry-standard requirements. Here’s what to consider when creating your Windows Server 2019 password policy:
- Establish requirements for a minimum of 8 characters for passwords.
- Set password complexity rules like requiring non-alphabetic characters, uppercase and lowercase letters, and numbers.
- Require users to change their passwords regularly – every 90 days is best practice.
- Don’t allow users to re-use recent passwords.
- Disallow passwords based on common dictionary words.
- Enforce a 15-minute lockout period on incorrect login attempts.
User access controls are also an important component of a secure password policy. Limit user access to only those resources necessary to carry out their assigned tasks, and require users to log off or lock their machines when they are away from their workstation. Establish a clear set of rules for user access that employees must adhere to, and ensure that all users’ roles are well-defined in the system.
The password policy in Windows Server 2019 is a critical component of ensuring the security and integrity of a domain environment. The policy includes a variety of settings such as password expiration policies, complexity requirements, and password length limits that help to prevent unauthorized access to sensitive information. The default domain policy sets the baseline for these settings, but administrators can customize them for specific organizational units or user groups. Strong passwords, including 14-character passwords with a mix of uppercase letters, lowercase letters, numbers, and special characters, are essential for protecting against common password attacks like brute force and dictionary attacks.
Additionally, implementing a custom password filter can further enhance security by enforcing specific password requirements. Enforcing password policy requirements, such as minimum password length and complexity rules, helps to minimize security incidents and protect against credential stuffing attacks. By regularly auditing and enforcing password policies, organizations can mitigate potential risks and maintain a secure password security infrastructure. Sources: docs.microsoft.com
In Windows Server 2019, the Password Policy plays a crucial role in ensuring the security of Domain Controllers and server core installations. The policy includes settings such as password length, complexity requirements, and password expiration period to enhance the strength of passwords used for authentication. By enforcing complex password strength rules, including the use of uppercase characters, consecutive characters, Unicode characters, and limiting password dictionaries, the policy reduces the risk of brute-force attacks and unauthorized access.
Additionally, the policy enforces password history policies, preventing users from reusing their favorite passwords or creating weak passwords. The configuration of password complexity and policy settings can be customized through the SecurityPolicy/CFG to meet specific corporate password requirements and security considerations.
To enhance security measures, the policy also includes auditing capabilities, such as password length audit warnings and reporting on security events related to password enforcement. Furthermore, the policy covers the management of administrator passwords, device account passwords, and Database User Strong Passwords to ensure strict adherence to security standards and limit security breaches.
The implementation of fine-grained password policies and granular password settings allows for a more tailored approach to password management, addressing issues with applications and ensuring the integrity of password storage across different versions of Domain Controllers. The enforcement of password policy mechanisms and frequent password resets contribute to reducing the attack surface and making password-based authentication more secure in a Windows Server environment. (Source: Microsoft Documentation – Password Policy for Windows Server 2019)
Benefits of Password Policy for Windows Server 2019
| Password Policy Benefit | Description |
|---|---|
| Protection from Brute Force Attacks | Reduce chances of unauthorized access through repeated password guessing. |
| Enhanced Data Security | Prevention of data theft and unauthorized access with strong password requirements. |
| Limit User Errors | Reduce password-related mistakes and simplify user authentication processes. |
| Secure Assets | Ensure maximum security by enforcing industry-standard password policies. |
| Access Control | Limit user access to necessary resources and enforce logoff procedures. |
Q&A
Q: What is a password policy?
A: A password policy is a set of rules and guidelines that help protect data by creating a secure password for a computer or server.
Q: What is the difference between a Local Password Policy and a Domain Password Policy?
A: A local password policy is used to set restrictions for users on a single computer or server. A domain password policy applies to all the computers within a domain.
Q: What are the requirements for a Windows Server 2019 password policy?
A: The requirements for a Windows Server 2019 password policy include having a minimum password length of 8 characters, text complexity requirements, use of encryption, age requirements, lockout settings and account expiration.
Q: What is the default password policy in Windows Server 2019?
A: The default domain password policy in Windows Server 2019 includes settings for Minimum password age, Maximum password age, Minimum password length, Password complexity requirements, and Account lockout policy.
Q: Can the default domain password policy be modified in Windows Server 2019?
A: Yes, the default domain password policy can be modified to suit the specific security requirements of an organization. Administrators can adjust settings such as password length, complexity requirements, and expiration policies.
Q: What are the password complexity requirements in Windows Server 2019?
A: The password complexity requirements in Windows Server 2019 typically include rules such as using a combination of uppercase letters, lowercase letters, numbers, and special characters in passwords to enhance security.
Q: How can the password policy be enforced in Windows Server 2019?
A: The password policy in Windows Server 2019 can be enforced through Group Policy settings in Active Directory. Administrators can configure password settings objects to enforce stringent password requirements for users.
Q: What is the significance of auditing password lengths in Windows Server 2019?
A: Auditing of password lengths in Windows Server 2019 helps organizations monitor and track password security practices. It allows for the detection of weak or easily guessable passwords that may pose security risks.
Q: How can organizations enhance password security in Windows Server 2019?
A: Organizations can enhance password security in Windows Server 2019 by implementing strong password schemes, enforcing password complexity policies, regularly updating passwords, and conducting security audits to identify vulnerabilities.
Sources: Microsoft TechNet: Password Policy in Windows Server 2019
Conclusion
Your organization’s network security is best protected with a Password Policy Windows Server 2019 and a secure password manager like LogMeOnce. With advanced features like multifactor authentication, secure password sharing and automated password changing, LogMeOnce is the perfect combination of enterprise-grade security and convenience. LogMeOnce is the right choice for those who prioritize their online security, as it ensures that no data is ever sent in plain text and logs all user activity, so that your password policy windows server 2019 is never compromised. With LogMeOnce’s reliable and free subscription, you can have the peace of mind you need to focus on maintaining your network security.
Neha Kapoor is a versatile professional with expertise in content writing, SEO, and web development. With a BA and MA in Economics from Bangalore University, she brings a diverse skill set to the table. Currently, Neha excels as an Author and Content Writer at LogMeOnce, crafting engaging narratives and optimizing online content. Her dynamic approach to problem-solving and passion for innovation make her a valuable asset in any professional setting. Whether it’s writing captivating stories or tackling technical projects, Neha consistently makes impact with her multifaceted background and resourceful mindset.
Windows Server
- 10.12.2014
- 57 152
- 9
- 05.07.2022
- 52
- 48
- 4
- Содержание статьи
- Отключаем требования сложности к паролю через редактор групповых политик
- Комментарии к статье ( 9 шт )
- Добавить комментарий
Начиная с Windows Server 2003, для всех пользователей операционной системы стали предъявляться повышенные требования к сложности пароля. Пароль пользователя должен соответствовать как минимум 3 условиям из списка перечисленного ниже:
- Наличие прописных букв английского алфавита от A до Z;
- Наличие строчных букв английского алфавита от a до z;
- Наличие десятичных цифр (от 0 до 9);
- Наличие неалфавитных символов (например, !, $, #, %)
Отключаем требования сложности к паролю через редактор групповых политик
Если же кто-то находит все эти сложности лишними, то это весьма легко отключается. Для этого нужно проделать действия описанные ниже.
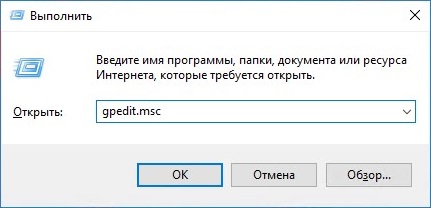
- Открываем «Выполнить» (Пуск — Выполнить или поочередно зажимаем клавиши Win+R), после чего набираем gpedit.msc и жмем ОК.
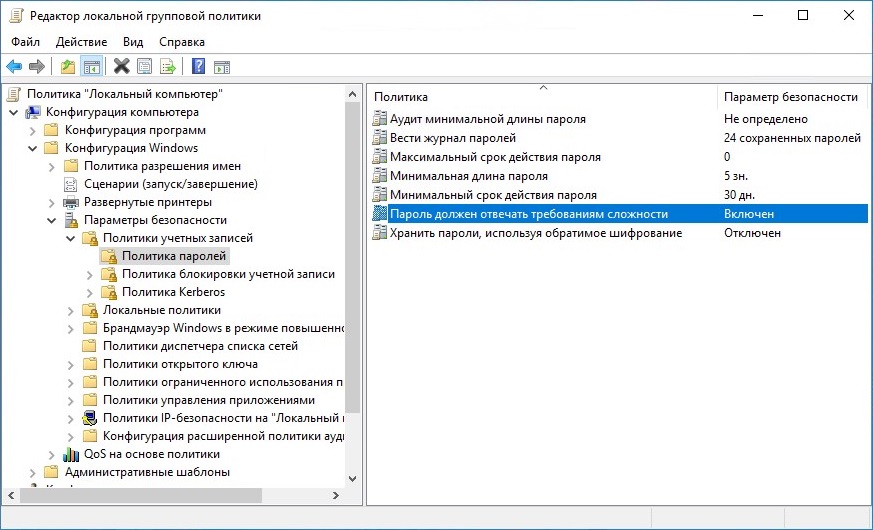
- В левой панели выбираем Конфигурация компьютера — Конфигурация windows — Параметры безопасности — Политики учетных записей — Политика паролей. Там выбираем пункт «Пароль должен отвечать требованиям сложности».
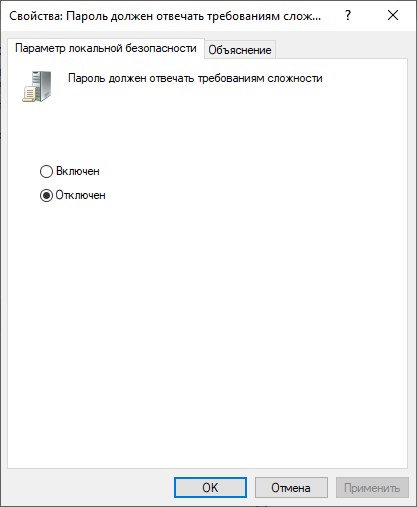
- Открываем настройки данного параметра, щелкнув по нему два раза. Выбираем «Отключен».
- Нажимаем на кнопку «ОК» для сохранения изменений.
In this post, we will see the steps for creating fine-grained password policies on Windows Server 2019 Active Directory Domain Environment.
Fine-grained password policies allow you to specify multiple password policies within a single domain so that you can apply different restrictions for password and account lockout policies to different sets of users in a domain.
For this post, I have created two users and one security group in Active Directory. Both users are members of that security group. Once we create a Fine-grained password policy, we would be applying it to a group named HRUsers.
Users: HR User1 and HR User2.
Group: HRUsers.
Create a new Fine-Grained Password Policy:
To create FGPP, login to the Windows server 2019 domain controller using a domain admin account and click on Server Manager.
To create a new Fine-Grained Password Policy, We need to open the Active Directory Administrative Center (ADAC).
On server manager console, click on Tools and select the Active Directory Administrative Center.
On the left side pane, click on the domain name(mylab.local).
Navigate to the System, Password Settings Container.
Right-click the Password Settings Container object and select New and click on Password Settings.
It will open the following Create Password Settings screen.
In the Name text box, type the name of the Password Settings Container (Ex. HRSecure_FGPP).
In the Precedence text box, type a Precedence number. Passwords with a lower precedence number overwrite Password Settings Containers with a higher precedence number.
Fill in or edit the appropriate fields for the settings that you want to use.
Now you need to apply this PSO (Password Settings Object) to a group called HRUsers.
(Note: A Password Settings Object (PSO) is an Active Directory object. This object contains all the settings that you can find in the Default Domain Policy GPO.)
Click on Add
Browse the security group, in our case it is HRUsers group. Select the group and click OK.
Click on OK.
Done! We have successfully applied the Fine-Grained Password Policy on members of HRUsers group but still we want to verify that.
To view the resultant PSO.
Locate the security group HRUsers. Right-click on the security group and select properties.
On the left side pane, click on Password Settings.
Here we can verify that HRSecure_FGPP PSO is applied to our security group.
Even as an administrator if we try to setup a simple password.
Definitely we will get the error because we did specify in the policy that the password must meet complexity requirements
Next, test account lockout policy as well. After three failed login attempts, user account is going to be lockout until administrator manually unlock it.
That’s it. I hope this article will help setting up Fine-grained Password Policies in Windows Server 2019 Active Directory Domain.
Post Views: 4,351