Ниже приведена небольшая инструкция об изменении политики паролей в Microsoft Windows Server 2012 R2. По умолчанию политика паролей определена таким образом, что все пароли учетных записей пользователей должны удовлетворять следующим требованиям:
- Не содержать имени учетной записи пользователя или частей полного имени пользователя длиной более двух рядом стоящих знаков.
- Иметь длину не менее 6 знаков.
- Содержать знаки трех из четырех перечисленных ниже категорий:
- Латинские заглавные буквы (от A до Z)
- Латинские строчные буквы (от a до z)
- Цифры (от 0 до 9)
- Отличающиеся от букв и цифр знаки (например, !, $, #, %)
Все параметры политики паролей задаются в локальных групповых политиках. Для запуска Редактора Локальных Групповых Политик (Local Group Policy Editor) необходим выполнить команду gpedit.msc (для этого необходимо нажать комбинацию клавиш Win + R, в окне «Выполнить» (Run) в поле «Открыть:» (Open:) ввести имя команды и нажать «ОК» )
В запустившейся оснастке в дереве групповых политик последовательно раскрываем группы:
- «Конфигурация компьютера» (Computer Configuration)
- «Конфигурация Windows» (Windows Settings)
- «Параметры безопасности» (Security Settings)
- «Политики учетных записей» (Account Policies)
- «Политика паролей» (Password Policy)
- «Политики учетных записей» (Account Policies)
- «Параметры безопасности» (Security Settings)
- «Конфигурация Windows» (Windows Settings)
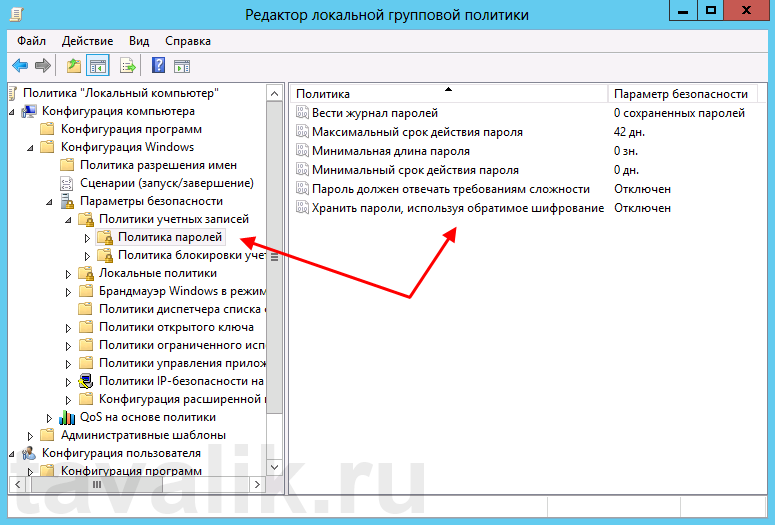
Здесь мы можем изменить необходимую нам политику. В частности, политику сложности паролей. Для этого два раза кликаем по строке «Пароль должен отвечать требованиям сложности» (Password must meet complexity requirements) и в окне свойства политики устанавливаем переключатель в «Отключен» (Disabled)
Для всех политик доступно довольно подробное описание, для доступа к которому необходимо перейти на вкладку «Объяснение» (Explain).
Изменив необходимые параметры, сохраняем настройки и закрываем окна, нажав «ОК» .
В этой же ветке можно изменить Политику блокировки учетных записей (Account Lockout Policy) в случае неверного ввода паролей. Все политики редактируются аналогичным образом.

Необходимо понимать, что изменение политики паролей может сильно снизить безопасность сервера. Лучше использователь специальные программы для генерации с хранения паролей.
In this second post dedicated to System Administrators who have to deal with a Risk Assessment, Security Assessment, Due Diligence or Compliance Questionnaire: if you lost the first one, you can read it here. This time we’ll talk about how to enforce a password policy by altering the default settings — in terms of password complexity and password minimum length — in Windows Server 2012.
This is a task that often needs to be done to comply with the security requirements asked by most modern regulations and standards — such as the ISO/IEC 27001:2013, ISO/IEC 27002:2013, ISO/IEC 20000:2011, NIST CyberSecurity Framework, SSAE/SOC2, ITIL, PCI-DSS and so on — but it can also be useful for those who just want to protect their system in a better way — or do the exact opposite by relaxing these controls (which is not something you should normally do — read here to understand why).
Here’s how we can take a look at the current system settings in terms of password strength and change them as we please:
Networks without Active Directory
In case you need to configure clients and/or servers not connected to an Active Directory Domain, use the following:
- Open the Control Panel.
- Navigate to Administrative Tools > Local Security Policy.
- In the modal window that will open, expand the Security Settings > Account Policies > Password Policy node.
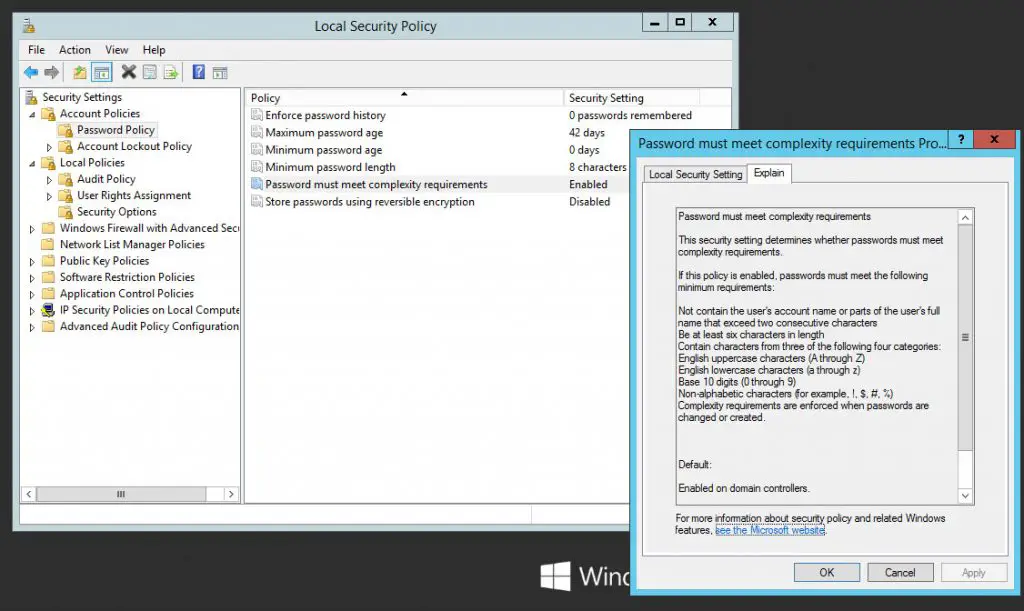
From there, you can view and/or edit the various options available in Windows Server 2012. For example, you can choose to enable or disable the password complexity requirements, which means the following:
If this policy is enabled, passwords must meet the following minimum requirements:
- Not contain the user’s account name or parts of the user’s full name that exceed two consecutive characters
- Be at least six characters in length
- Contain characters from three of the following four categories:
- English uppercase characters (A through Z)
- English lowercase characters (a through z)
- Base 10 digits (0 through 9)
- Non-alphabetic characters (for example, !, $, #, %)
- Complexity requirements are enforced when passwords are changed or created.
This standard complexity profile can be toggled altering the Password must meet complexity requirements policy.
These are quite good settings, except for the minimum password length: six characters would’ve been arguably viable for 2012, but are definitely not enough in 2017. Luckily enough, you can override that single option by altering the Minimum password length policy, which should be put to (at least) 8 to fend off most brute-force attacks.
Networks with Active Directory
If your client or server is part of an Active Directory domain, you won’t be able to use the Local Security Policy console: if that’s the case, use the Group Policy Management console from Control Panel > Administrative Settings of your AD domain controller and edit the GPO settings there.
Conclusion
That’s it: we hope that these hints will help other System Administrator to make their system compliant with the latest security standards.
If you’re looking for a way to set a idle timeout for Remote Desktop sessions, read this other post.
This post explains how to Disable Windows Server 2012 R2 password expiry. The reason that I discovered how to do this was that one of my server’s local Administrator password kept expiring every 45 days which was really annoying. If this was a production server then this is a good security feature but as the server is a demo server then it is really annoying.
As a side note I use really long passwords anyway (20+) characters so the password expiry is not really an issue as there is not technology available to crack the passwords at the moment!
After a bit of clicking through the server policies I found the setting that needed to be changed and was able to disable password expiry entirely on the server.
This is how I Disable Windows Server 2012 R2 users password expiry.
It is not a good idea on an enterprise system but as my server is a test server I wanted to stop the password from expiring every 45 days. Luckily this is a really easy process that takes a couple of minutes to do.
To disable password expiry do the following:
Click on the start bar and type “local security policy” and select Local Security Policy:
This opens the Local Security Policy Group Policy Snapin:
Open Account Policies and click on Password Policy:
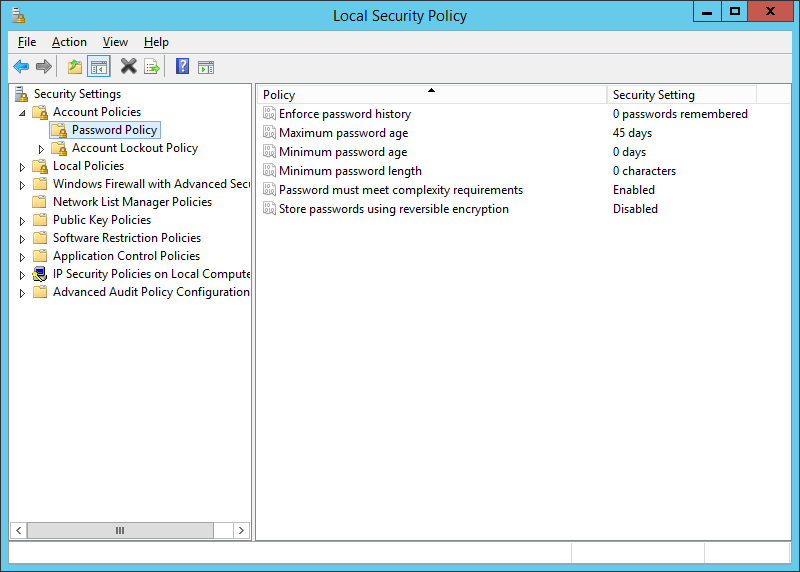
Double click on Maximum password age:
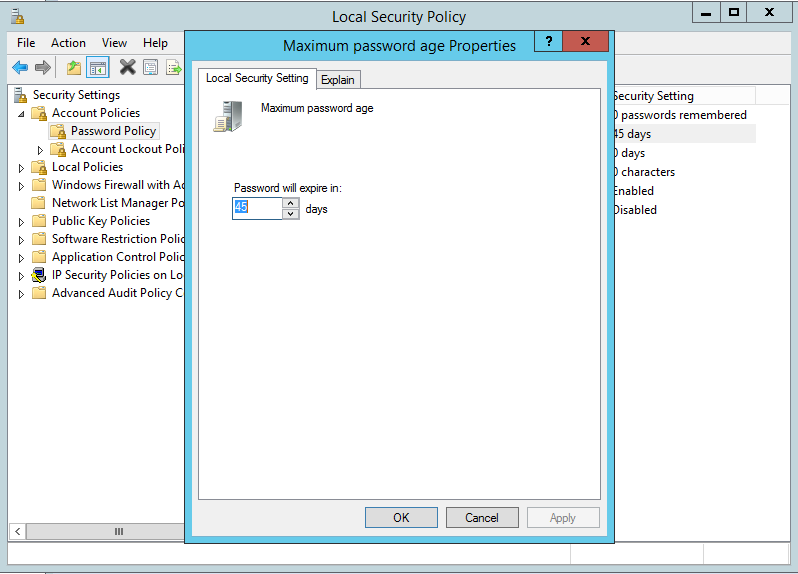
Change the default 45 days to a value in days that the password will be changed. In my case I set it to 0 as I don’t want it to ever expire. Click apply to save the changes:
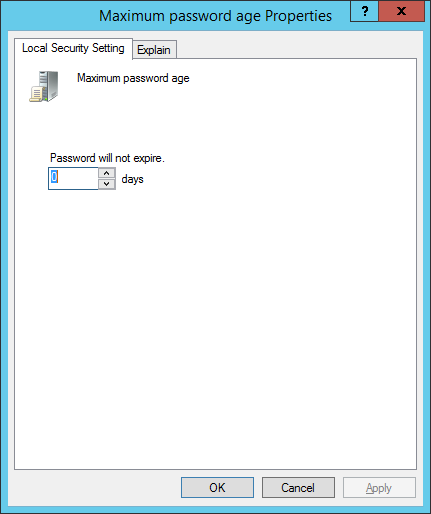
The password is now set to never expire. Click OK to close the wizard.:
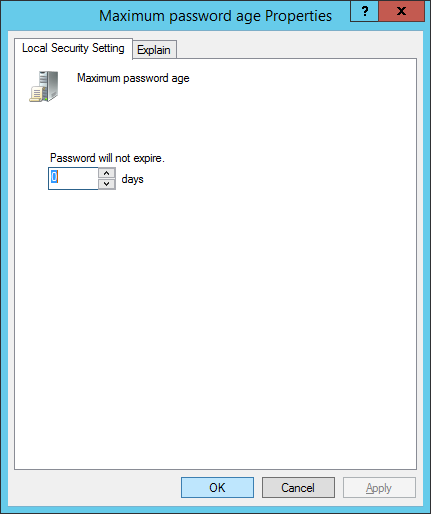
You will now see that the minimum password age is now set to 0:
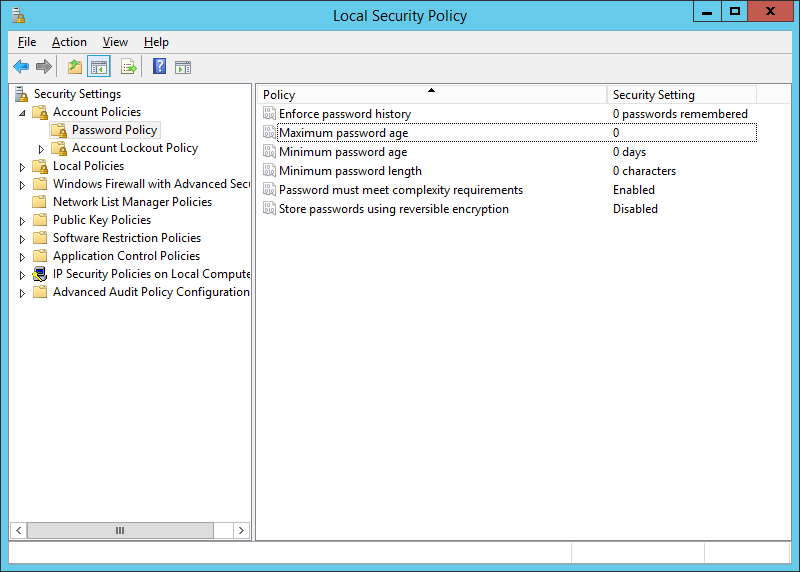
Close the window and you have successfully disabled password expiry on your Windows 2012 R2 server.
As I stated earlier it is really not recommended to have the Local Administrator password set to never expire on a production server and this process should only be done on demo/ dev servers.
For more Windows Server posts click HERE.
How to disable (turn off) the default Administrator Complexity for an Active Directory Domain Controller — Windows Server 2012 R2
1) Открыть Server Manager, меню Tools, в раскрывшемся меню выбрать Group Policy Management.

2) Раскройте Forrest >> Domains >> Ваш контролер домена.
Правой кнопкой мыши кликнуть на Default Domain Policy и в контекстном меню выбрать Edit .

3) Раскройте Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Account Policies -> Password Policy
Двойной клик мышкой на Passwords Must Meet Complexity Requirements.

4) Выбрать Disabled в пункте Define this policy setting:. Кликнуть
OK и закрыть все окна.
5) Чтобы применить политики без перезагрузки выполните в командной строке (CMD) команду «gpupdate /force«.
-
Lucas
-
April 15, 2017
Windows Server 2012 and 2016 have password security policies, which increases the complexity of their composition.
To disable password complexity in Windows Server 2012 / 2016, follow the steps below:
- Go to Administrative Tools > Local Security Policies.
- Then click on Account Policies > Password Policies.
- Disable the option“Password must meet complexity requirements“, that’s it!
