Ноя
15
2018
Данные методы шифрования являются устаревшими и уязвимыми ко взломам. Все чаще, в рамках требований политик безопасности и лучших практик, 3DES и RC4 рекомендуется отключить.
Отключение 3DES и RC4 в Windows Server 2016 (Powershell)
|
Disable-TlsCipherSuite -Name «TLS_RSA_WITH_3DES_EDE_CBC_SHA» #RC4 ([Microsoft.Win32.RegistryKey]::OpenRemoteBaseKey([Microsoft.Win32.RegistryHive]::LocalMachine,$env:COMPUTERNAME)).CreateSubKey(‘SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 128/128’) New-ItemProperty -path ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 128/128’ -name ‘Enabled’ -value ‘0’ -PropertyType ‘DWord’ -Force | Out-Null ([Microsoft.Win32.RegistryKey]::OpenRemoteBaseKey([Microsoft.Win32.RegistryHive]::LocalMachine,$env:COMPUTERNAME)).CreateSubKey(‘SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 40/128’) New-ItemProperty -path ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 40/128’ -name ‘Enabled’ -value ‘0’ -PropertyType ‘DWord’ -Force | Out-Null ([Microsoft.Win32.RegistryKey]::OpenRemoteBaseKey([Microsoft.Win32.RegistryHive]::LocalMachine,$env:COMPUTERNAME)).CreateSubKey(‘SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 56/128’) New-ItemProperty -path ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 56/128’ -name ‘Enabled’ -value ‘0’ -PropertyType ‘DWord’ -Force | Out-Null |
Отключение 3DES и RC4 в Windows Server 2012
Сохраните ключи реестра в файл с расширением .reg и примените его двойным щелчком мыши
Disable_3DES_RC4.reg
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers] [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 128/128] @=«» «Enabled»=dword:00000000 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 40/128] @=«» «Enabled»=dword:00000000 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 56/128] @=«» «Enabled»=dword:00000000 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168] @=«» «Enabled»=dword:00000000 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168/168] @=«» «Enabled»=dword:00000000 |
Hi,
a measure to protect your Windows System against Sweet32 attacks is to disable the DES and Triple DES.
To do this, add 2 Registry Keys to the SCHANNEL Section of the registry.
As registry file
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168] "Enabled"=dword:00000000 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168/168] "Enabled"=dword:00000000
or from command line
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168" /f reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168" /v Enabled /d 0 /t REG_DWORD /f reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168/168" /f reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168/168" /v Enabled /d 0 /t REG_DWORD /f
Michael
My Knowledgebase for things about Linux, Windows, VMware, Electronic and so on…
This website uses cookies to improve your experience and to serv personalized advertising by google adsense. By using this website, you consent to the use of cookies for personalized content and advertising. For more information about cookies, please see our Privacy Policy, but you can opt-out if you wish. Accept Reject Read More
RC4
To disable RC4 on your Windows server, set the following registry keys:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 128/128]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 40/128]
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 56/128]
"Enabled"=dword:00000000
3DES
To disable 3DES on your Windows server, set the following registry key:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168]
"Enabled"=dword:00000000
If your Windows version is anterior to Windows Vista (i.e. XP, 2003), you will need to set the following registry key:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168/168]
"Enabled"=dword:00000000
See also
- Configure an IIS8 server
- Configure an IIS7 server
- Configure an IIS6 server
- Sweet 32: attack targeting Triple DES (3DES)
- Enable/disable encryption algorithm in Windows
- RC4 vulnerability
- IIS Crypto: Tool developed by Nartac that allows you to customize protocol and cipher support on Windows.
Admins have become very aware of the need to adjust the Schannel protocol settings for TLS to enable TLS 1.2 and to disable older versions. However, the cipher suites do not always receive the same amount of attention and may be left at their default values.
If you are reading this post there is a good chance that your security auditors have flagged a weak cipher is enabled on your server, and they want it disabled.
This post is specific to the issues around 3DES and SWEET32 which is CVE-2016-2183.
This attack leverages birthday attack probability theory to abuse the higher number of collisions. As noted in the NVD:
The DES and Triple DES ciphers, as used in the TLS, SSH, and IPSec protocols and other protocols and products, have a birthday bound of approximately four billion blocks, which makes it easier for remote attackers to obtain cleartext data via a birthday attack against a long-duration encrypted session, as demonstrated by an HTTPS session using Triple DES in CBC mode
Windows will display this as the TLS_RSA_WITH_3DES_EDE_CBC_SHA cipher.
Security Audit Findings
The below are some examples of what may be provided by the security auditor. The exact text and description will depend on the security scan tool.
-
SSL Medium Strength Cipher Suites Supported (SWEET32)
-
Medium Strength Ciphers (> 64-bit and < 112-bit key, or 3DES)
-
Reconfigure the affected application if possible to avoid use of medium strength ciphers.
When reviewing the server in question, the below is an example of the registry which is missing the key and value to disable 3DES.
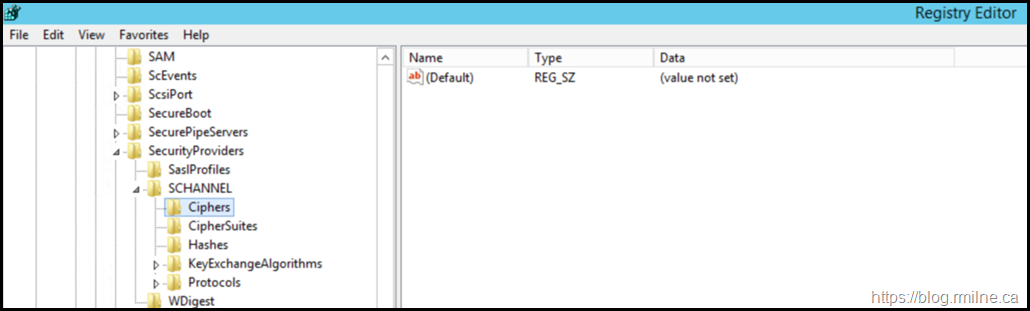
Windows Server 2012 R2 Remediation
Docs outlines all of the relevant information for Schannel protocols and algorithms.
The Ciphers registry key under the SCHANNEL key is used to control the use of symmetric algorithms such as DES and RC4. In this post we will disable the ciphers at this level. You could also edit the list of ciphers stored under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Cryptography\Configuration\Local\SSL\00010002 but that would require a little bit more work.
To disable 3DES at the Schannel level of the registry, create the below:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168
Type: DWORD
Name:Enabled
Value: 0
Note the value is zero or 0x0 in hex.
To create the required registry key and path, the below are two sample commands. The first creates the intermediate «Triple DES 168» registry key. This is required as PowerShell will error out if the “Triple DES 168” key does not exist.
New-Item -Path "HKLM:SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168" –Force
New-ItemProperty -Path "HKLM:SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168" -Name "Enabled" -PropertyType DWORD -Value "0x0" –Force
Note that Disable-TlsCipherSuite is not available for Windows Server 2012 R2. It is available for Windows Server 2016 onwards.
Windows Server 2012 R2 Verification
To verify if the server has the registry set to disable 3DES:
Get-ItemProperty -Path "HKLM:SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168" -Name Enabled | Select-Object Enabled | FT -Autosize
Once the registry value was added, you should then see the cipher has been removed from a SSL Labs scan.
Note that TLS_RSA_WITH_3DES_EDE_CBC_SHA is not visible is the SSL Labs output.
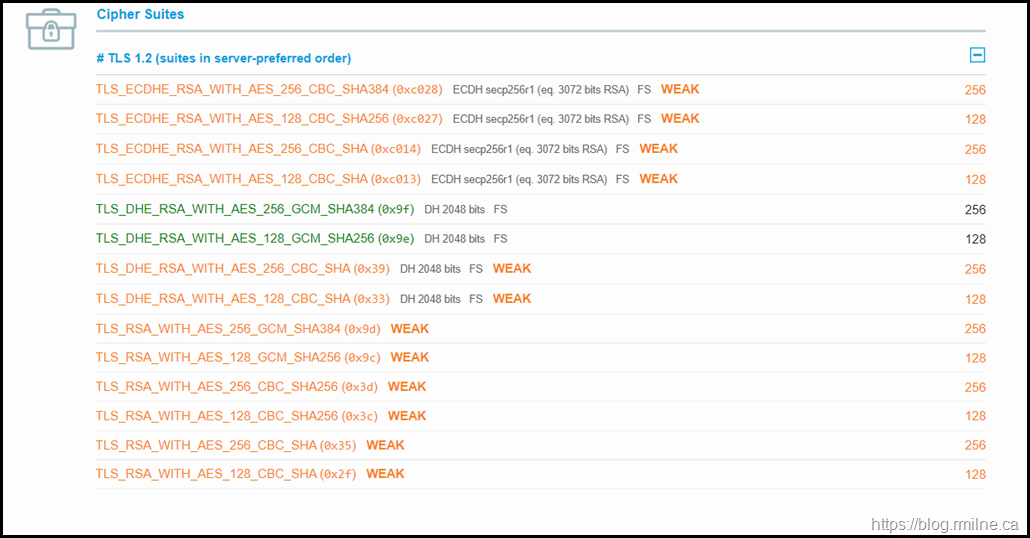
SSL Labs Reference
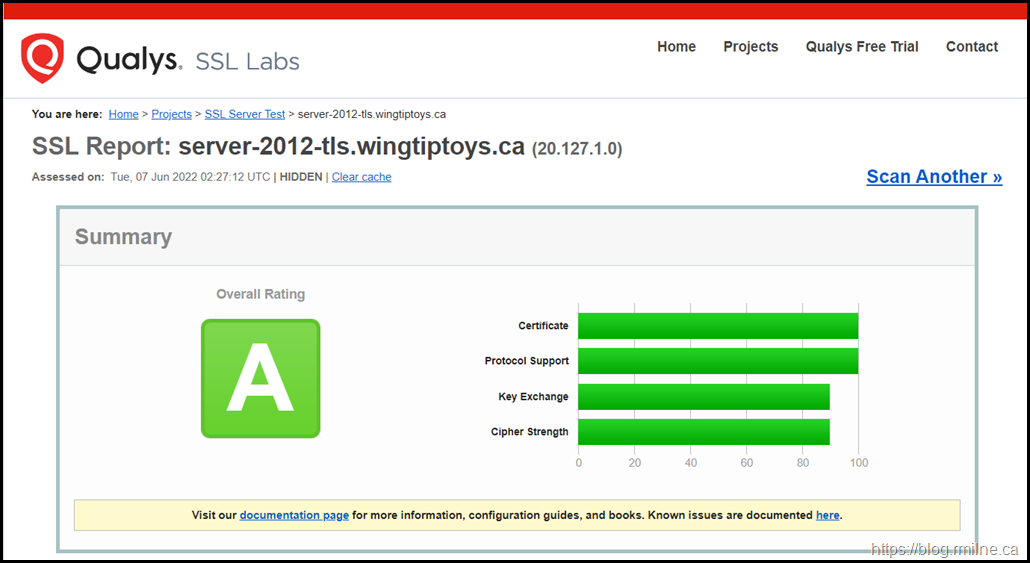
Note that just because you have a grade A rating on SSL Labs, that does not mean that all issues are resolved.
The below image is a Windows Server 2012 R2 test system with only TLS 1.2 enabled and weak DH disabled. The Certificate and Protocol Support sections are both 100%, the Key Exchange and Cipher Strength are not. You are encouraged to read the tool’s documentation to understand the scoring algorithm.
If we scroll down to the Cipher Suites section on the page, we can see why the Cipher Strength rating was not 100%
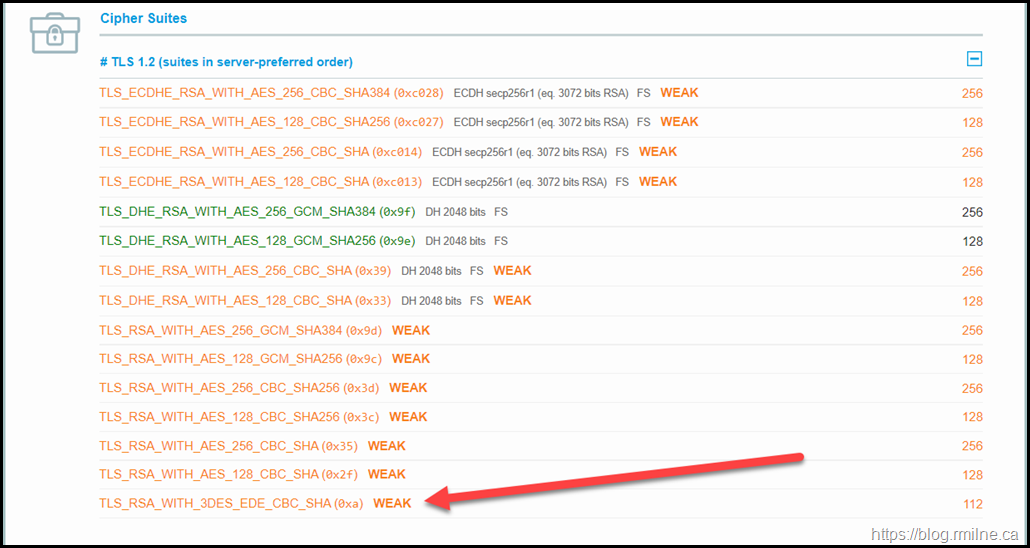
For the SWEET32 issue, the TLS_RSA_WITH_3DES_EDE_CBC_SHA cipher is highlighted.
Cheers,
Rhoderick
You are disabling some ciphers (e.g. DES 56/56, RC2 40/128, RC2 128/128, RC4 40/128, RC4 56/128, RC4 64/128, RC4 128/128) in order to harden your server OS. However you are unable to disable triple DES 168 and every vulnerability report still shows it as active.
You tried to disable triple DES 168 via the “SCHANNEL\Ciphers\Triple DES 168/168 subkey” which is mentioned via Microsoft KB 245030 (or set by Nartac IIS Crypto version 1.6). In more details you set the following:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168/168]
“Enabled”=dword:00000000
After you implemented the one above (and perform a full OS reboot) a nMap (on the RDP port) shows the following:
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-09-28 03:11 Pacific Daylight Time
Nmap scan report for 192.168.58.130
Host is up (0.00s latency).
PORT STATE SERVICE
3389/tcp open ms-wbt-server
| ssl-enum-ciphers:
| TLSv1.0:
| ciphers:
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (dh 256) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (dh 256) - A
| compressors:
| NULL
| cipher preference: server
| warnings:
| Weak certificate signature: SHA1
| TLSv1.1:
| ciphers:
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (dh 256) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (dh 256) - A
| compressors:
| NULL
| cipher preference: server
| warnings:
| Weak certificate signature: SHA1
| TLSv1.2:
| ciphers:
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (dh 256) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (dh 256) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (dh 256) - A
| compressors:
| NULL
| cipher preference: server
| warnings:
| Weak certificate signature: SHA1
|_ least strength: C
MAC Address: 00:0C:29:FB:83:9A (VMware)Nmap done: 1 IP address (1 host up) scanned in 14.91 seconds
If you perform the same on Windows 2012 R2 (RDP port) you see:
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-09-28 04:08 Pacific Daylight Time
Nmap scan report for 192.168.58.128
Host is up (0.00s latency).
PORT STATE SERVICE
3389/tcp open ms-wbt-server
| ssl-enum-ciphers:
| TLSv1.0:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (dh 256) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (dh 256) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C
| compressors:
| NULL
| cipher preference: server
| warnings:
| Weak certificate signature: SHA1
| TLSv1.1:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (dh 256) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (dh 256) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C
| compressors:
| NULL
| cipher preference: server
| warnings:
| Weak certificate signature: SHA1
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (dh 256) - A
| TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 (dh 128) - B
| TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 (dh 128) - C
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (dh 256) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (dh 256) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (dh 256) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C
| compressors:
| NULL
| cipher preference: server
| warnings:
| Key exchange parameters of lower strength than certificate key
| Weak certificate signature: SHA1
|_ least strength: C
MAC Address: 00:0C:29:36:42:27 (VMware)Nmap done: 1 IP address (1 host up) scanned in 14.91 seconds
If you delete the above reg key now and re-create the following now:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168]
“Enabled”=dword:00000000Reboot the computer and run a new nMap scan you see now the following:
Windows 2008 R2:
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-09-28 03:15 Pacific Daylight Time
Nmap scan report for 192.168.58.130
Host is up (0.014s latency).
PORT STATE SERVICE
3389/tcp open ms-wbt-server
| ssl-enum-ciphers:
| TLSv1.0:
| ciphers:
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (dh 256) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (dh 256) - A
| compressors:
| NULL
| cipher preference: server
| warnings:
| Weak certificate signature: SHA1
| TLSv1.1:
| ciphers:
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (dh 256) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (dh 256) - A
| compressors:
| NULL
| cipher preference: server
| warnings:
| Weak certificate signature: SHA1
| TLSv1.2:
| ciphers:
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (dh 256) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (dh 256) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (dh 256) - A
| compressors:
| NULL
| cipher preference: server
| warnings:
| Weak certificate signature: SHA1
|_ least strength: A
MAC Address: 00:0C:29:FB:83:9A (VMware)Nmap done: 1 IP address (1 host up) scanned in 14.91 seconds
Windows 2012 R2:
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-09-28 04:11 Pacific Daylight Time
Nmap scan report for 192.168.58.128
Host is up (0.013s latency).
PORT STATE SERVICE
3389/tcp open ms-wbt-server
| ssl-enum-ciphers:
| TLSv1.0:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (dh 256) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (dh 256) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| compressors:
| NULL
| cipher preference: server
| warnings:
| Weak certificate signature: SHA1
| TLSv1.1:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (dh 256) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (dh 256) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| compressors:
| NULL
| cipher preference: server
| warnings:
| Weak certificate signature: SHA1
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (dh 256) - A
| TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 (dh 128) - B
| TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 (dh 128) - C
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (dh 256) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (dh 256) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (dh 256) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| compressors:
| NULL
| cipher preference: server
| warnings:
| Key exchange parameters of lower strength than certificate key
| Weak certificate signature: SHA1
|_ least strength: C
MAC Address: 00:0C:29:36:42:27 (VMware)Nmap done: 1 IP address (1 host up) scanned in 14.99 seconds
Conclusion, it looks like there is a small bug in the Microsoft documentation and multiple other websites, documentations or blogs picked that up without checking that. So remove the “/168” part from your reg key, reboot the computer and triple DES is gone.
