From time to time, Windows checks for updates and automatically installs them. However, these updates may not always be compatible with your specific use case. Fortunately, it is possible to revert to a previous version of Windows that was functioning optimally. This guide will cover the steps to revert Windows updates on a Windows VPS.
When installing or uninstalling Windows updates we recommend taking a snapshot of the current state of the VPS. If you’d like to read more about taking snapshots of your Windows VPS, please check the guide here.
Windows Server 2016
1. To start, log in to your Windows Server 2016 and use the Windows search function to search and open Check for updates.
2. In the Windows Update window, click Update history to move on.
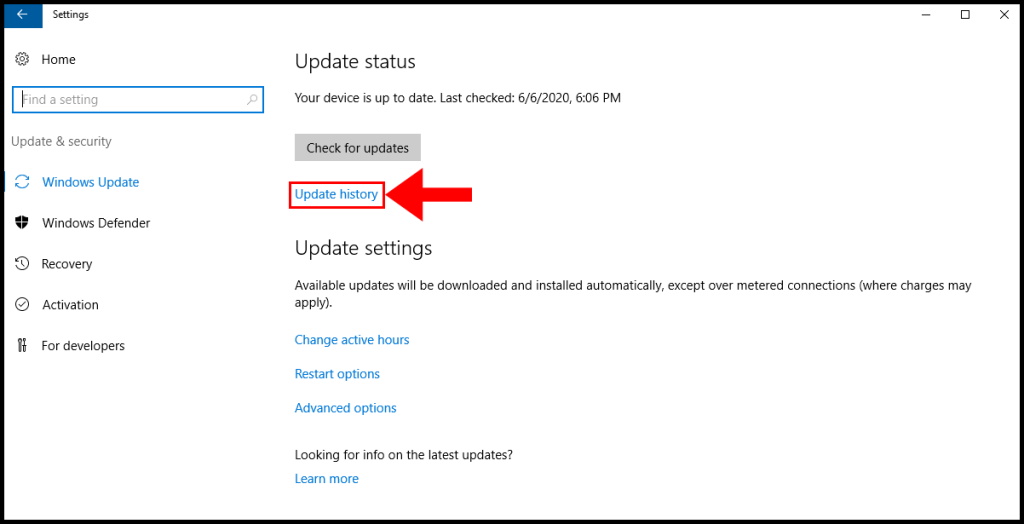
3. Now navigate to “Uninstall updates“.
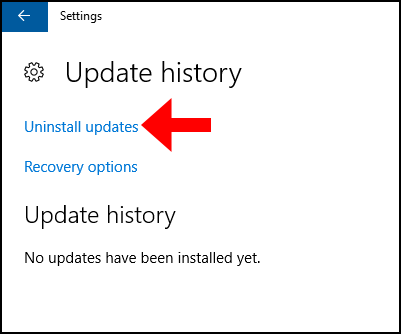
4. Then the Installed Updates window will appear with a list of updates, right-click the update you’d like to uninstall and click Uninstall.
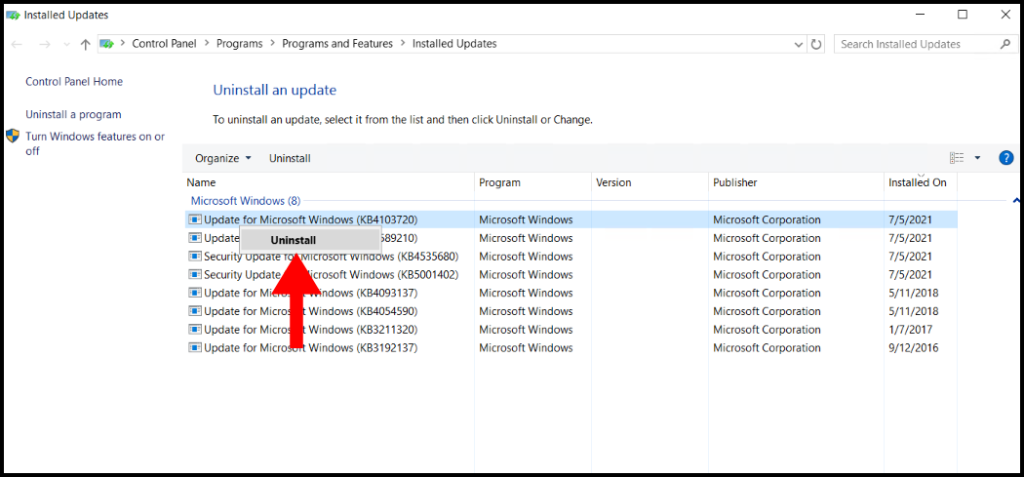
5. A pop-up will appear prompting you if you are sure you want to uninstall the update, click Yes to move forward with the uninstall.
6. Now the uninstall will begin, do not close out of this window. Once it is done, move on to the next step.
7. Once the uninstall is complete, it will prompt you to restart in order to for the changes to go into effect. Click Restart Now to restart the server. We have successfully gone over how to revert Windows updates on Windows VPS for Windows Server 2016.
Windows Server 2012
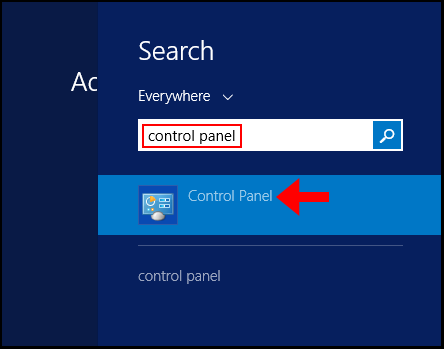
1. To start, log in to your Windows Server 2012 and use the Windows search function to search and open Control Panel.
2. Then, click the Category drop-down next to View by and select Small icons from the drop-down menu.
3. Next, locate and click Programs and Features to continue.
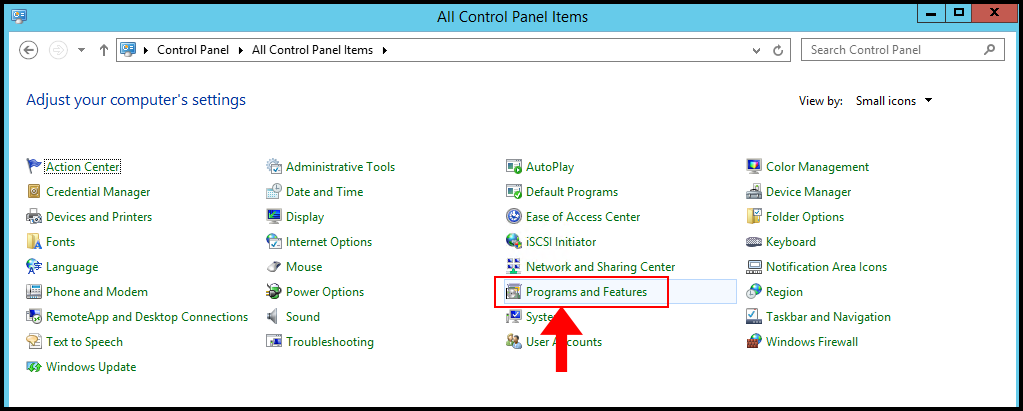
4. Then on the Programs and Features page, click View installed updates on the left-hand side.
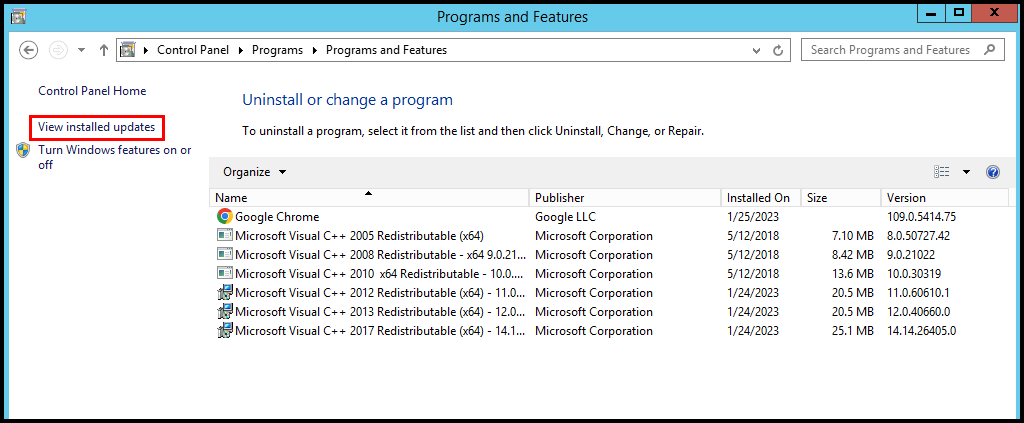
5. Right-click on the update which you want to remove and click Uninstall to revert the update. We have successfully gone over how to revert Windows updates on Windows VPS for Windows Server 2012.
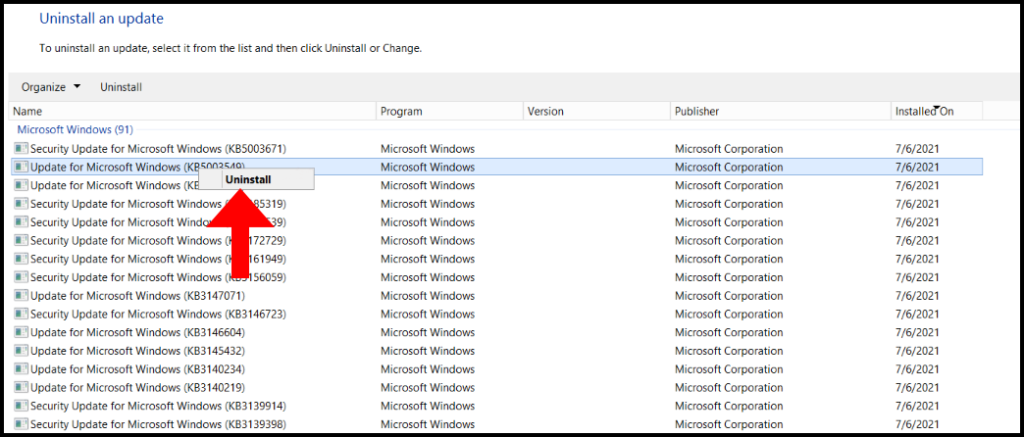
6. A pop-up will appear prompting you if you are sure you want to uninstall the update, click Yes to move forward with the uninstall.
7. Now the uninstall will begin, do not close out of this window. Once it is done, move on to the next step.
8. Once the uninstall is complete, it will prompt you to restart in order to for the changes to go into effect. Click Restart Now to restart the server. We have successfully gone over how to revert Windows updates on Windows VPS for Windows Server 2016.
В этой статье расскажем, как выполнить откат (даунгрейд) версии или редакции Windows Server, например, понизить версию Windows Server Datacenter до Standard без переустановки системы. Это может быть полезно, если на сервере используются ресурсы, для которых достаточно менее дорогой редакции.
Приобрести оригинальные ключи активации Windows Server можно у нас в каталоге от 1190 ₽
Как узнать редакцию Windows Server?
Проверить установленную редакцию Windows Server можно несколькими способами:
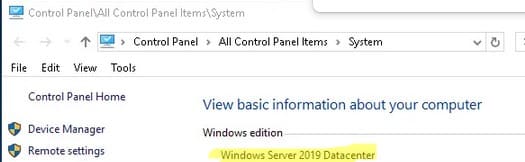
1. Через Панель управления:
— Перейдите в Control Panel > System and Security > System.
— В этом окне будет указана текущая версия и редакция Windows Server.
2. Из командной строки:
systeminfo | findstr /B /C:"OS Name" /B /C:"OS Version"
или
wmic os get Caption, Version, BuildNumber, OSArchitecture
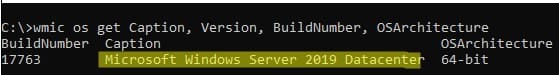
3. С помощью PowerShell:
Get-WindowsEdition –Online
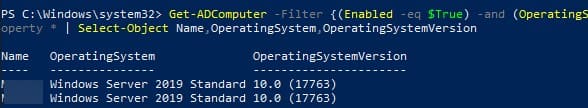
4. В доменных сетях можно использовать командлет для получения информации обо всех серверах в домене:
Get-ADComputer -Filter {(Enabled -eq $True) -and (OperatingSystem -Like '*Windows Server*')} -Property * | Select-Object Name,OperatingSystem,OperatingSystemVersion
Понижение редакции Windows Server с Datacenter до Standard
Microsoft официально не поддерживает понижение редакций (даунгрейд), поэтому рекомендуем перед выполнением даунгрейда создать полную резервную копию системы.
Шаги для понижения редакции:
1. Откройте реестр:
— Запустите regedit и перейдите в ветку HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion.
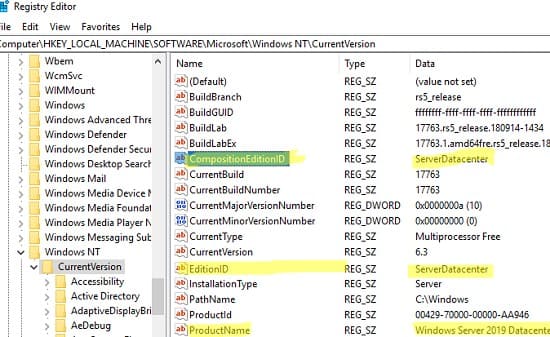
— Измените значения следующих параметров:
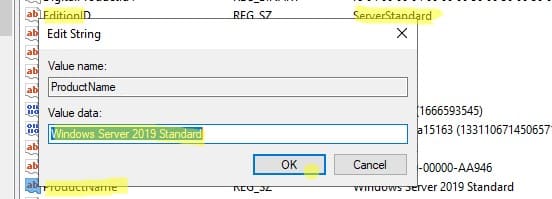
— EditionID = ServerStandard
— ProductName = Windows Server 2019 Standard
— CompositionEditionID = ServerStandard
Обратите внимание, что существует довольно редкая редакция Windows Server Essentials. Для нее нужно указывать EditionID = ServerSolution. Так же, не перезагружайте сервер после смены значений указанных ключей реестра, иначе они автоматически вернутся на предыдущие значения.
2. Запустите установку Windows Server 2019:
— Смонтируйте ISO образ с Windows Server 2019 и запустите установочный файл setup.exe.
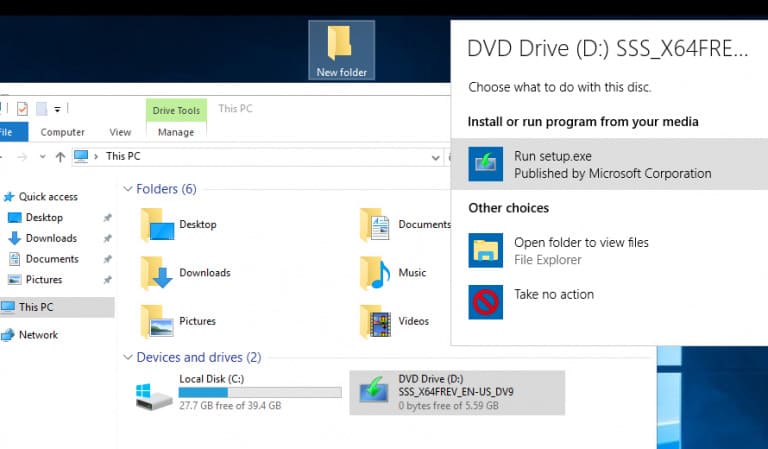
— Выберите Upgrade и укажите редакцию Windows Server 2019 Standard (Desktop Experience).
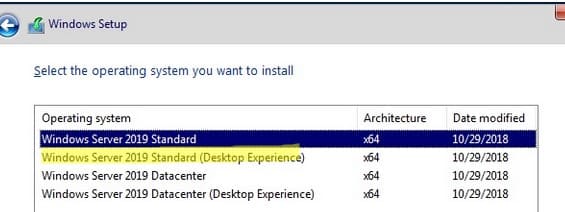
— Убедитесь, что выбрана опция Keep personal files and apps, чтобы сохранить установленные приложения и данные.
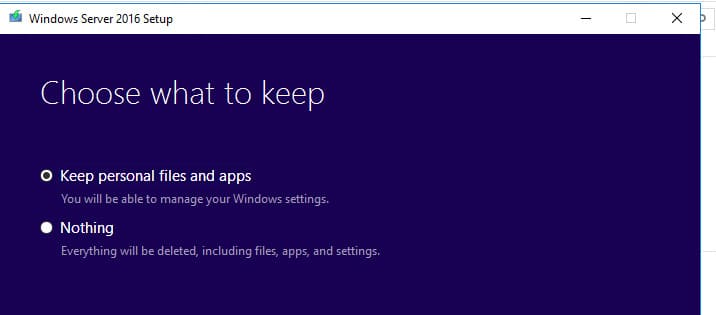
3. Подтвердите предупреждения:
— Если при установке возникают предупреждения, внимательно прочитайте их. Обычно рекомендуется выполнить чистую установку, но для даунгрейда можно продолжить процесс и нажать везде «Confirm».
4. Завершение процесса:
— После завершения установки и перезагрузок проверьте, что сервер теперь работает под редакцией Windows Server 2019 Standard.
Можно ли выполнить даунгрейд Windows Server 2022 до 2019/2016?
Правила лицензирования Microsoft разрешают использовать предыдущие версии Windows Server при наличии лицензии на более новую версию. Например, с лицензией на Windows Server 2022 можно запустить Windows Server 2019 или 2016.
Порядок действий:
1. Для активации предыдущей версии Windows Server получите ключ продукта через VLSC или обратитесь в службу поддержки Microsoft.
2. Установите сервер с использованием публичного GVLK ключа и активируйте через службу KMS.
Важно: Понизить уже установленную ОС с Windows Server 2022 до 2019 или 2016 нельзя. В этом случае потребуется выполнить чистую установку старой версии.
Также обратите внимание на необходимость обновления RDS CAL лицензий при даунгрейде, если у вас развернуты службы удаленных рабочих столов.
Понижение версии Windows Server может быть выполнено без переустановки, однако этот процесс не поддерживается официально Microsoft. Будьте внимательны при работе с важными серверами и всегда создавайте резервные копии перед началом операции.
Лицензионный ключ активации Windows Server от
При обновлении сервера один из апдейтов не смог установиться и сервер начал делать откат обновлений. Спустя какое-то время сервер перезагрузился, появилось черное окно с надписью «Обновление вашей системы» без какого-либо прогресса:
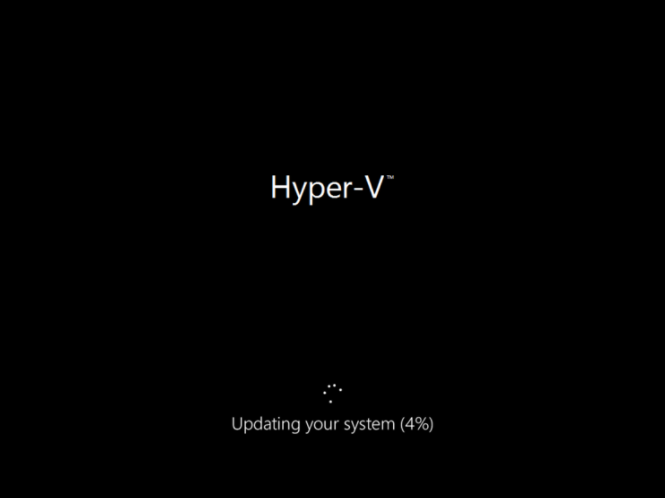
Очевидно, что это не дело и проблему нужно начинать решать самому. По скриншоту можно заметить, что это виртуальная машина на Hyper-V, исходя из этого мы можем сделать следующее:
1. Выключить виртуальную машину. В большинстве случаем безусловно нужно выключать через кнопку Завершение работы..., но в данном случае она не поможет и придется воспользоваться кнопкой Выключить...
2. Изменить настройки автозапуска (выставить задержку в несколько 5 секунд). Это надо понадобится, чтобы успеть зайти в safe mode
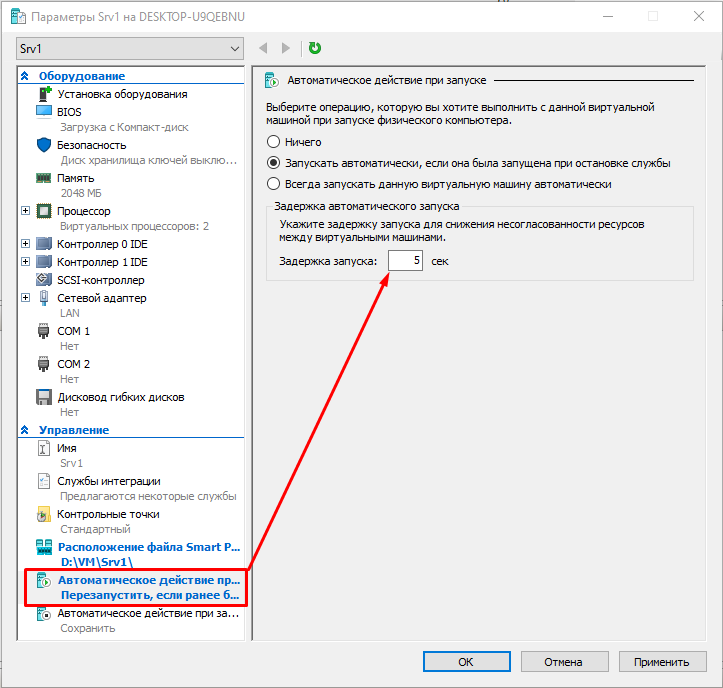
3. Запускаем виртуалку и не забываем кликать на F8. Появится знакомое меню
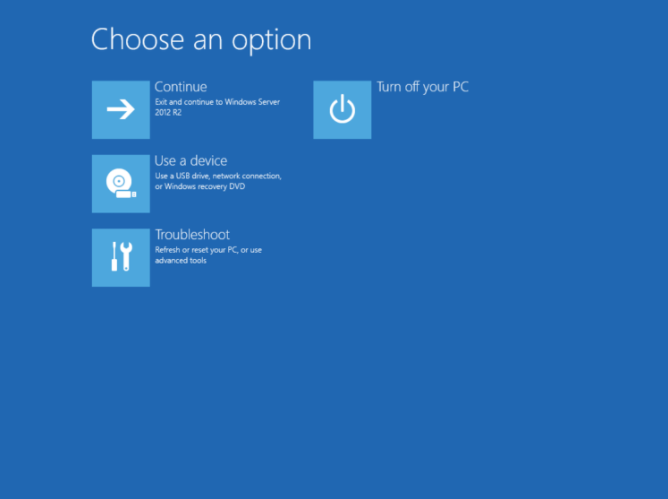
4. Итак, теперь мы можем попасть в командную строку. Кликаем на пункт Troubleshoot и затем на Command Line
5. Теперь запускаем команду, чтобы получить список доступных дисков:
wmic logicaldisk get name
6. Теперь нам нужно определить какой из этих дисков является диском C, т.к в режиме safe буква диска может отличаться от той, что мы видим в системе. Проще всего опознать нужную нам букву — это найти директорию Windows, используя команду dir
7. Итак, вы знаете букву нужного нам диска, я буду указывать букву C, вы же замените на ту, что у вас. Переходим в директорию C:\Windows\Winsxs:
cd C:\Windows\Winsxs
8. Теперь нам нужно вывести список всех файлов, начинающихся с Pending
dir pending*
9. Переименуем все эти файлы, добавив в конец их имени _old. Команда выглядит так:
ren Pending.xml Pending_old.xml
10. Создадим новый, пустой файл Pending.xml
echo > pending.xml
11. Перейдём на ветку наверх и создадим новую директорию:
cd..
mkdir scratch
12. Удалим\отменим все висящие действия из поврежденного образа с помощью DISM:
DISM /Image:C:\ /Cleanup-Image /RevertPendingActions /scratchdir:C:\Windows\Scratch
13. Переименуем папку SoftwareDistribution в SoftwareDistributionOld
ren C:\Windows\SoftwareDistribution C:\Windows\SoftwareDistributionOLD
14. Запустим проверку:
sfc /scannow
15. По завершении проверки перезагрузим виртуалку, это может занять немного больше времени, чем обычно. Но в итоге мы должны увидеть такую картину:
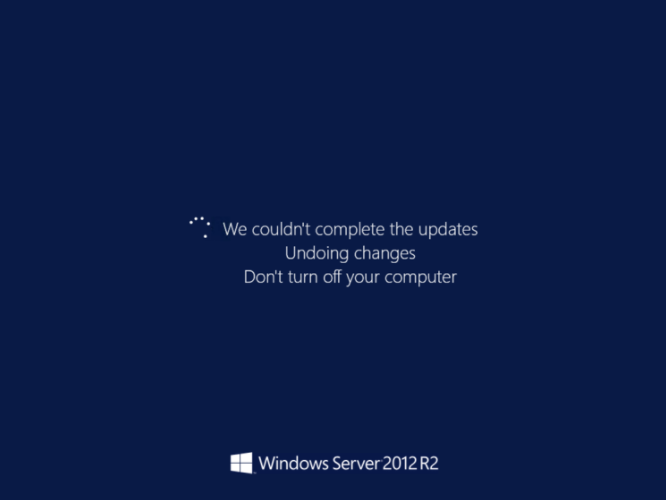
Когда процесс завершится, сервер должен вернуться в нормальное состояние!
12.01.2022, 10:12. Показов 2944. Ответов 4
Добрый день.
После установки обновлений, с последующей перезагрузкой происходит откат этих обновлений. Пробовал разные варианты решения проблемы: очистка кэша обновлений, sfc /scannow и др. Ничего не помогает.
Кликните здесь для просмотра всего текста
** END ** Service: Service exit [Exit code = 0x240001]
*************
=========== Logging initialized (build: 7.9.9600.19915, tz: +0500) ===========
= Process: C:\Windows\system32\svchost.exe
= Module: c:\windows\system32\wuaueng.dll
*************
** START ** Service: Service startup
*********
WARNING: Assert config failed, error = 80070002
WARNING: Failed to assert WU event log configuration: 0x80070002
Non-AoAc machine. Aoac operations will be ignored.
* WU client version 7.9.9600.19915
WARNING: SleepStudyTracker: Machine is non-AOAC. Sleep study tracker disabled.
* Base directory: C:\Windows\SoftwareDistribution
* Access type: No proxy
UpdateNetworkState Ipv6, cNetworkInterfaces = 1.
UpdateNetworkState Ipv4, cNetworkInterfaces = 1.
* Network state: Connected
UpdateNetworkState Ipv6, cNetworkInterfaces = 1.
UpdateNetworkState Ipv4, cNetworkInterfaces = 1.
*********** Agent: Initializing global settings cache ***********
* Endpoint Provider: 00000000-0000-0000-0000-000000000000
* WSUS server: http://10.101.44.73:8530
* WSUS status server: http://10.101.44.73:8530
* Target group: TERM
* Windows Update access disabled: No
WARNING: Network Cost is assumed to be not supported as something failed with trying to get handles to wcmapi.dll
WuTaskManager delay initialize completed successfully..
Timer: 13EB7139-5C9B-4817-98B7-A22174B1AA43, Expires 2022-01-12 09:58:50, not idle-only, not network-only
Timer: CF1ABEC6-7887-4964-BB93-B2E21B31CEC1, Expires 2022-01-10 12:17:15, not idle-only, not network-only
Timer: 29A863E7-8609-4D1E-B7CD-5668F857F1DB, Expires 2022-01-10 12:17:15, not idle-only, not network-only
WARNING: Failed to initialize event uploader for new server {7971F918-A847-4430-9279-4A52D1EFE18D} with hr = 80248014.
CWERReporter::Init succeeded
*********** Agent: Initializing Windows Update Agent ***********
Download manager restoring 0 downloads
Attempt 1 to obtain post-reboot results for event with cookie 30934536_2672482790.
FATAL: Got error querying the post-reboot status for session 30934536_2672482790: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934536_2873217950.
FATAL: Got error querying the post-reboot status for session 30934536_2873217950: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934536_3477082297.
FATAL: Got error querying the post-reboot status for session 30934536_3477082297: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934537_161064977.
FATAL: Got error querying the post-reboot status for session 30934537_161064977: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934537_1009678669.
FATAL: Got error querying the post-reboot status for session 30934537_1009678669: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934537_1575939883.
FATAL: Got error querying the post-reboot status for session 30934537_1575939883: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934537_1800614672.
FATAL: Got error querying the post-reboot status for session 30934537_1800614672: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934537_2368596576.
FATAL: Got error querying the post-reboot status for session 30934537_2368596576: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934537_2949541411.
FATAL: Got error querying the post-reboot status for session 30934537_2949541411: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934537_3543013971.
FATAL: Got error querying the post-reboot status for session 30934537_3543013971: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934537_3953811086.
FATAL: Got error querying the post-reboot status for session 30934537_3953811086: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934538_832031666.
FATAL: Got error querying the post-reboot status for session 30934538_832031666: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934538_1332732732.
FATAL: Got error querying the post-reboot status for session 30934538_1332732732: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934538_1800931067.
FATAL: Got error querying the post-reboot status for session 30934538_1800931067: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934538_2669225691.
FATAL: Got error querying the post-reboot status for session 30934538_2669225691: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934538_3314675701.
FATAL: Got error querying the post-reboot status for session 30934538_3314675701: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934538_3914437868.
FATAL: Got error querying the post-reboot status for session 30934538_3914437868: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934539_194967818.
FATAL: Got error querying the post-reboot status for session 30934539_194967818: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934539_723928671.
FATAL: Got error querying the post-reboot status for session 30934539_723928671: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934539_1132285588.
FATAL: Got error querying the post-reboot status for session 30934539_1132285588: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934539_1648115097.
FATAL: Got error querying the post-reboot status for session 30934539_1648115097: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934539_2309343464.
FATAL: Got error querying the post-reboot status for session 30934539_2309343464: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934539_3326122709.
FATAL: Got error querying the post-reboot status for session 30934539_3326122709: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934539_3943650026.
FATAL: Got error querying the post-reboot status for session 30934539_3943650026: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934540_170567762.
FATAL: Got error querying the post-reboot status for session 30934540_170567762: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934540_3359941916.
FATAL: Got error querying the post-reboot status for session 30934540_3359941916: 0x8007045b.
Attempt 1 to obtain post-reboot results for event with cookie 30934540_4199911600.
FATAL: Got error querying the post-reboot status for session 30934540_4199911600: 0x8007045b.
########### AU: Initializing Automatic Updates ###########
AIR Mode is disabled
# Policy Driven Provider: http://10.101.44.73:8530
# Detection frequency: 22
# Target group: TERM
# Approval type: Scheduled (Policy)
# Auto-install minor updates: Yes (User preference)
# Will interact with non-admins (Non-admins are elevated (User preference))
WARNING: Failed to get Wu Exemption info from NLM, assuming not exempt, error = 0x80240037
WARNING: Failed to get Network Cost info from NLM, assuming network is NOT metered, error = 0x80240037
AU finished delayed initialization
Calculating current update level for this session
FATAL: UH: 0x8007045b: EnumeratePackages failed in CCbs::CalculateCUL
Done calculating current update level for this session
WARNING: Failed to get current update level, hr=8007045b.
Waiting for post reboot processing results, will not show low priority client UIs.
Currently AUX is enabled — so not show any WU Upgrade notifications.
WARNING: Failed to get Network Cost info from NLM, assuming network is NOT metered, error = 0x80240037
WARNING: Failed to get Network Cost info from NLM, assuming network is NOT metered, error = 0x80240037
Adding timer:
Timer: 31DA7559-FE27-4810-8FF6-987195B1FD98, Expires 2022-01-11 04:32:55, not idle-only, not network-only
Asking handlers to reconcile their sandboxes
########### AU: Uninitializing Automatic Updates ###########
Uninit WU Task Manager
WARNING: SessionConnectHandler, could not find Windows task folder, error = 0x80070003
WARNING: SessionConnectHandler, could not validate and register task, error = 0x80070003
WARNING: AUFirmwareInstallTaskHandler, ValidateTriggers, could not find Windows task folder, error = 0x80070003
WARNING: AUFirmwareInstallTaskHandler, could not find Windows task folder, error = 0x80070003
WARNING: AUFirmwareInstallTaskHandler, could not validate and register task, error = 0x80070003
REPORT EVENT: {D9E55691-A349-4943-8D47-E0D73A8BAFC4} 2022-01-10 15:35:48:572+0500 1 202 [AU_REBOOT_COMPLETED] 102
CWERReporter finished handling 1 events. (00000000)
Earliest future timer found:
Timer: CF1ABEC6-7887-4964-BB93-B2E21B31CEC1, Expires 2022-01-10 12:17:15, not idle-only, not network-only
WARNING: CPersistentTimeoutScheduler | SetScheduledTask(Network), could not find Windows task folder, error = 0x80070003
Earliest future timer found:
Timer: CF1ABEC6-7887-4964-BB93-B2E21B31CEC1, Expires 2022-01-10 12:17:15, not idle-only, not network-only
WARNING: CPersistentTimeoutScheduler | SetScheduledTask(No Network), could not find Windows task folder, error = 0x80070003
*********
** END ** Service: Service exit [Exit code = 0x240001]
*************
=========== Logging initialized (build: 7.9.9600.19915, tz: +0500) ===========
= Process: C:\Windows\system32\svchost.exe
= Module: c:\windows\system32\wuaueng.dll
*************
** START ** Service: Service startup
*********
WARNING: Assert config failed, error = 80070002
WARNING: Failed to assert WU event log configuration: 0x80070002
Non-AoAc machine. Aoac operations will be ignored.
* WU client version 7.9.9600.19915
WARNING: SleepStudyTracker: Machine is non-AOAC. Sleep study tracker disabled.
* Base directory: C:\Windows\SoftwareDistribution
* Access type: No proxy
UpdateNetworkState Ipv6, cNetworkInterfaces = 1.
UpdateNetworkState Ipv4, cNetworkInterfaces = 1.
* Network state: Connected
UpdateNetworkState Ipv6, cNetworkInterfaces = 1.
UpdateNetworkState Ipv4, cNetworkInterfaces = 1.
*********** Agent: Initializing global settings cache ***********
* Endpoint Provider: 00000000-0000-0000-0000-000000000000
* WSUS server: http://10.101.44.73:8530
* WSUS status server: http://10.101.44.73:8530
* Target group: TERM
* Windows Update access disabled: No
WARNING: Network Cost is assumed to be not supported as something failed with trying to get handles to wcmapi.dll
WuTaskManager delay initialize completed successfully..
Timer: 31DA7559-FE27-4810-8FF6-987195B1FD98, Expires 2022-01-11 04:32:55, not idle-only, not network-only
Timer: CF1ABEC6-7887-4964-BB93-B2E21B31CEC1, Expires 2022-01-10 12:17:15, not idle-only, not network-only
Timer: 29A863E7-8609-4D1E-B7CD-5668F857F1DB, Expires 2022-01-10 12:17:15, not idle-only, not network-only
WARNING: Failed to initialize event uploader for new server {7971F918-A847-4430-9279-4A52D1EFE18D} with hr = 80248014.
CWERReporter::Init succeeded
*********** Agent: Initializing Windows Update Agent ***********
Download manager restoring 0 downloads
Attempt 2 to obtain post-reboot results for event with cookie 30934536_2672482790.
Attempt 2 to obtain post-reboot results for event with cookie 30934536_2873217950.
Post-reboot status for session 30934536_2873217950: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934536_3477082297.
Post-reboot status for session 30934536_3477082297: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934537_161064977.
Post-reboot status for session 30934537_161064977: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934537_1009678669.
Post-reboot status for session 30934537_1009678669: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934537_1575939883.
Post-reboot status for session 30934537_1575939883: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934537_1800614672.
Post-reboot status for session 30934537_1800614672: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934537_2368596576.
Post-reboot status for session 30934537_2368596576: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934537_2949541411.
Post-reboot status for session 30934537_2949541411: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934537_3543013971.
Post-reboot status for session 30934537_3543013971: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934537_3953811086.
Post-reboot status for session 30934537_3953811086: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934538_832031666.
Post-reboot status for session 30934538_832031666: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934538_1332732732.
Post-reboot status for session 30934538_1332732732: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934538_1800931067.
Post-reboot status for session 30934538_1800931067: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934538_2669225691.
Post-reboot status for session 30934538_2669225691: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934538_3314675701.
Post-reboot status for session 30934538_3314675701: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934538_3914437868.
Post-reboot status for session 30934538_3914437868: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934539_194967818.
Post-reboot status for session 30934539_194967818: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934539_723928671.
Post-reboot status for session 30934539_723928671: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934539_1132285588.
Post-reboot status for session 30934539_1132285588: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934539_1648115097.
Post-reboot status for session 30934539_1648115097: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934539_2309343464.
Post-reboot status for session 30934539_2309343464: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934539_3326122709.
Post-reboot status for session 30934539_3326122709: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934539_3943650026.
Post-reboot status for session 30934539_3943650026: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934540_170567762.
Post-reboot status for session 30934540_170567762: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934540_3359941916.
Post-reboot status for session 30934540_3359941916: 0x00000000.
Attempt 2 to obtain post-reboot results for event with cookie 30934540_4199911600.
Calculating current update level for this session
UH: Current cumulative update level calculated: package identity Package_for_KB3000850~31bf3856ad364e35~a md64~~6.3.1.8, display name KB3000850, support URL http://support.microsoft.com/?kbid=3000850, timestamp 01d7d552f31d4cac
Done calculating current update level for this session
########### AU: Initializing Automatic Updates ###########
AIR Mode is disabled
# Policy Driven Provider: http://10.101.44.73:8530
# Detection frequency: 22
# Target group: TERM
# Approval type: Scheduled (Policy)
# Auto-install minor updates: Yes (User preference)
# Will interact with non-admins (Non-admins are elevated (User preference))
WARNING: Failed to get Wu Exemption info from NLM, assuming not exempt, error = 0x80240037
WARNING: Failed to get Network Cost info from NLM, assuming network is NOT metered, error = 0x80240037
AU finished delayed initialization
Currently AUX is enabled — so not show any WU Upgrade notifications.
WARNING: Failed to get Network Cost info from NLM, assuming network is NOT metered, error = 0x80240037
WARNING: Failed to get Network Cost info from NLM, assuming network is NOT metered, error = 0x80240037
Asking handlers to reconcile their sandboxes
REPORT EVENT: {0CDD8AD5-6C5F-4886-8130-FA17DEF3F00F} 2022-01-10 15:42:21:427+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {E0510113-B313-4801-8B49-C4570A1C45B5} 2022-01-10 15:42:21:427+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {09183BF1-E82A-46D2-9180-73653F8AD9B7} 2022-01-10 15:42:21:427+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {78D384F0-C3D4-43A0-8C05-8D4F497FA7CE} 2022-01-10 15:42:21:443+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {24B82688-D58F-4033-AA3F-93159F5C1125} 2022-01-10 15:42:21:443+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
CWERReporter finished handling 10 events. (00000000)
REPORT EVENT: {71A65772-2FEA-4B15-8D03-A8257AA8913F} 2022-01-10 15:42:21:489+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {9E3951EC-D82D-4230-ACEA-06DDD154A213} 2022-01-10 15:42:21:489+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {3A57EB89-DF36-45FC-8B87-88C62A19BFB8} 2022-01-10 15:42:21:489+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {70FC1122-98A6-43AA-8CD5-1318CC9DD702} 2022-01-10 15:42:21:505+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {4F059F24-CB92-439E-907B-0343C30EEBE4} 2022-01-10 15:42:21:505+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
CWERReporter finished handling 10 events. (00000000)
REPORT EVENT: {99F4A5DD-D268-48FC-88BF-A0CF7C63EAEA} 2022-01-10 15:42:21:568+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {FF911440-1EF8-4CCD-AF7F-730B6BB80686} 2022-01-10 15:42:21:568+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {A4AE3837-04F9-484E-BC70-FAA97C3BEE9B} 2022-01-10 15:42:21:568+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {6D77FEAB-AC3C-4D40-AF74-2992B8248F9C} 2022-01-10 15:42:21:568+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {FCC2D07E-80F9-480B-A9A2-B672C3DC112E} 2022-01-10 15:42:21:568+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
CWERReporter finished handling 10 events. (00000000)
REPORT EVENT: {481AB035-A747-4349-B3EC-53C4A074FC73} 2022-01-10 15:42:21:568+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {EC688BE6-5AF8-42BF-8E50-81215A347C3C} 2022-01-10 15:42:21:568+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {8E66902F-AA2A-41BC-B9AC-856378BC3276} 2022-01-10 15:42:21:568+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {5BAC25DC-C452-4DE0-992D-4D80946FAE53} 2022-01-10 15:42:21:568+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {816275D1-5D0A-45F6-B235-56FD1097D057} 2022-01-10 15:42:21:568+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
CWERReporter finished handling 10 events. (00000000)
REPORT EVENT: {458FE0AE-CAC6-4D34-BB0D-A8D3477717C0} 2022-01-10 15:42:21:568+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {62846445-CD97-44BE-B375-F309E6387C23} 2022-01-10 15:42:21:583+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {3138A52E-6012-4975-B062-67C769026CD3} 2022-01-10 15:42:21:583+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {DD504A65-F5FA-4AA3-BABC-B0661536B915} 2022-01-10 15:42:21:583+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
REPORT EVENT: {D8F9F1BA-D1E9-4BD4-85C9-E7542AE9704D} 2022-01-10 15:42:21:583+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
CWERReporter finished handling 10 events. (00000000)
REPORT EVENT: {14C36849-ADA2-45CA-A95D-57E09F0DE372} 2022-01-10 15:42:21:583+0500 1 183 [AGENT_INSTALLING_SUCCEEDED] 101
CWERReporter finished handling 2 events. (00000000)
,
In a previous article I had described how you can automatically back up your Windows Server 2016/2012 or 2012R2 by using the Windows Server Backup feature, in order to protect your server from any problem that may occur and prevent it from functioning properly.
In this article I will explain how to restore Server 2016/2012/2012R2 to a previous system state, from a system image backup, which created with the Windows Server Backup application, if the system is online (Windows is able to start normally).
Related Articles:
- How to Create System Restore Points on Server 2016/2012 using Windows Server Backup.
- How to Restore Files from Windows Server Backup in Server 2016/2012/2012R2.
How to Restore Server 2016 in a Previous System State from a System Image Backup.
The only way to perform a system state recovery on Server 2016/2012, when your server is online, * is by using the WbAdmin command utility.
* Note: If your server cannot start normally, then read the instructions in this tutorial.
To Restore the System State on Server 2016/2012 with WbAdmin:
1. Open Command prompt as administrator. (type CMD on the search box, right-click at the ‘Command Prompt’ result and select Run as Administrator)
2. At command prompt, type the following command to view all the available backup versions:
- wbadmin get versions
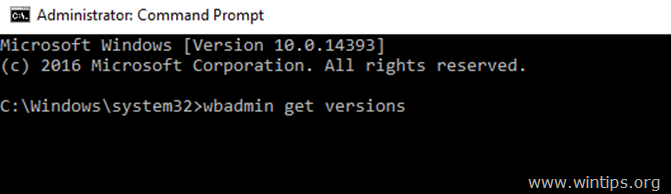
3. At the «wbadmin get versions» command output, note the version identifier of the backup that you want to restore and the backup location.
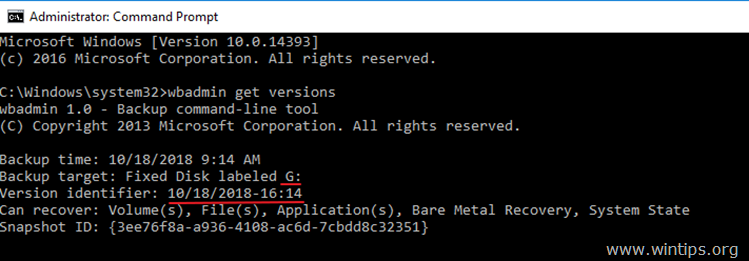
4. To perform a system state restore, use the wbadmin with the following syntax:
- wbadmin start systemstaterecovery -version:versionIdentifier -backupTarget:Backup Destination location -machine:MachineName -quiet
e.g. In this example, we want to restore the backup version: 10/18/2018-16:14 which is stored at drive G: on the local machine (server). So the command will be:
- wbadmin start systemstaterecovery -version:10/18/2018-16:14 -backupTarget:G:
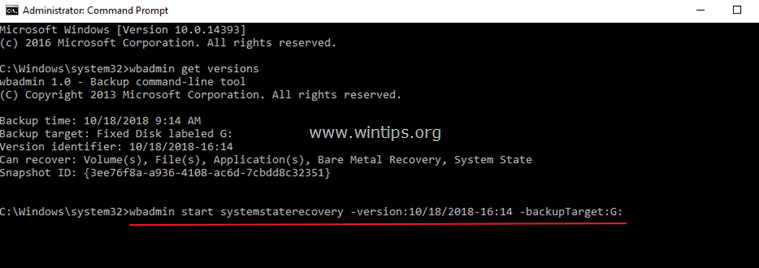
WbAdmin start systemstaterecovery (Explanation of the Base Parameters): *
* Note: Type «WbAdmin start systemstaterecovery» to view all available parameters.
-version Specifies the version identifier for the backup to recover in MM/DD/YYYY-HH:MM format. If you do not know the version identifier, type wbadmin get versions.
-backupTarget Specifies the storage location that contains the backup or backups you want to recover. This parameter is useful when the storage location is different from where the backups of this computer are usually stored.
e.g. If the backup is stored at the following network share folder \\192.168.1.200\Public\Backup, the command will be:
- wbadmin start systemstaterecovery -version:10/18/2018-16:14 -backupTarget:\\192.168.1.200\Public\Backup
-machine Specifies the name of the computer that you want to recover. This parameter is useful when multiple computers have been backed up to the same location. Should be used when the -backupTarget parameter is specified.
e.g. If you want to recover another machine (e.g. the «Server01»), from a backup which stored at the following network folder \\192.168.1.200\Public\Backup, the command will be:
- wbadmin start systemstaterecovery -version:10/18/2018-16:14 -backupTarget:\\192.168.1.200\Public\Backup -machine:server01
-quiet Runs the subcommand with no prompts to the user.
That’s it! Let me know if this guide has helped you by leaving your comment about your experience. Please like and share this guide to help others.
If this article was useful for you, please consider supporting us by making a donation. Even $1 can a make a huge difference for us in our effort to continue to help others while keeping this site free:
- Author
- Recent Posts
Konstantinos is the founder and administrator of Wintips.org. Since 1995 he works and provides IT support as a computer and network expert to individuals and large companies. He is specialized in solving problems related to Windows or other Microsoft products (Windows Server, Office, Microsoft 365, etc.).
