This is a quick tutorial on how to configure OpenVPN clients to use specific DNS server. OpenVPN server can be configured to enable the clients to use specific DNS server for hostname resolution.
Table of Contents
Install and Configure OpenVPN Server
In our previous tutorials, we have covered how to install and configure OpenVPN server
To use specific DNS server with OpenVPN clients;
There are various ways in which you can push specific DNS servers for name resolution.
- Push DNS addresses to Clients from OpenVPN Server
- Define DNS addresses on OpenVPN Client config
Push DNS addresses to Clients from OpenVPN Server
To configure OpenVPN server to push DNS addresses to clients, edit the OpenVPN server configuration file and add the line;
push "dhcp-option DNS X.X.X.X"Where X.X.X.X is the DNS server IP address.
You can add multiple DNS server entries;
push "dhcp-option DNS 192.168.58.22"
push "dhcp-option DNS 8.8.8.8"To specify the DNS domain part;
push "dhcp-option DOMAIN DOMAIN-NAME"For example;
push "dhcp-option DOMAIN kifarunix-demo.com"Here is a sample of my OpenVPN server configuration file;
cat /etc/openvpn/server/server.conf
port 1194
proto udp
dev tun
ca ca.crt
cert issued/server.crt
key private/server.key # This file should be kept secret
dh dh.pem
topology subnet
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist /var/log/openvpn/ipp.txt
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 192.168.58.22"
push "dhcp-option DNS 8.8.8.8"
push "dhcp-option DOMAIN kifarunix-demo.com"
client-to-client
keepalive 10 120
tls-auth ta.key 0 # This file is secret
cipher AES-256-CBC
data-ciphers AES-256-CBC
comp-lzo no
persist-key
persist-tun
status /var/log/openvpn/openvpn-status.log
log-append /var/log/openvpn/openvpn.log
verb 3
explicit-exit-notify 1
auth SHA512
Restart DNS Server;
systemctl restart [email protected]Define DNS addresses on OpenVPN Client config
If you dont have access to the OpenVPN server to enforce the above configurations, then you can edit your OpenVPN client configuration file and add the lines;
dhcp-option DNS X.X.X.X
dhcp-option DNS DNS-IP-1
dhcp-option DNS DNS-IP-2
push "dhcp-option DOMAIN DOMAIN-NAME"Here is a sample OpenVPN client;
cat client-1.ovpn
client
tls-client
pull
dev tun
proto udp4
remote 192.168.58.22 1194
resolv-retry infinite
nobind
#user nobody
#group nogroup
persist-key
persist-tun
key-direction 1
remote-cert-tls server
auth-nocache
comp-lzo
verb 3
auth SHA512
cipher AES-256-CBC
data-ciphers AES-256-CBC
comp-lzo no
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
ec31b288a9a3865c4b5f3583b481ff5c
434e957be6569ed573a58a102ce53efc
b9528f15f5412046c5a603e6916b565b
fe2c6a0f955dcec2d3f7e6cec7e373bb
dff40b041f1488d4177c3de04bdff43b
e361eff6328c499621e0846ec72565ef
734fc02e51540d1c5c19102156a080f7
fde124822bf6fc802dff9facf24998de
6f91f081dafcdd28f4bca9223afe694d
12d57beb6aed96753d651a2ca4722214
5fa87829b9f53f2ccb89d9f15112c9cd
3594ead75bc1df737b50188c2829d724
3aff136577b3c79e6f863112aadf5aeb
8b6d53c607874c71104acfa22e587bd3
22b14a2c0a91e15569d99d5e35a52a8b
0aa4f24ccf10d8757dfd75da14fd21ac
-----END OpenVPN Static key V1-----
-----BEGIN CERTIFICATE-----
MIIDSzCCAjOgAwIBAgIUW5NhoHubpdB2QE1IdTqCZeD4CK4wDQYJKoZIhvcNAQEL
BQAwFjEUMBIGA1UEAwwLRWFzeS1SU0EgQ0EwHhcNMjExMTA1MTcxNDQ4WhcNMzEx
MTAzMTcxNDQ4WjAWMRQwEgYDVQQDDAtFYXN5LVJTQSBDQTCCASIwDQYJKoZIhvcN
AQEBBQADggEPADCCAQoCggEBALGvwj57vpugazdMtjIVngKybzapSfT7rm1Rv+d2
SssBwsTf4kDXqfwQiQLPEDo5mpxIO1XBEhsNS3CeBBSfGHgvT3EbiXKLS0mpMiIK
nayJJh2+v3xg+3EU5jemNJ8p3iqsWz566ds/C6haZsp9cM5oGBOOSbHOMJo4S6+6
XmZfi8sdCWlSxrntd74MmEPI7wvmClA5xaM3hfzpHXdhrcTr9JDVMf0sYSkXUbc5
nyDQrLtcZiVyoPCJxB41OoTYd1aLDV/7F+A6ShSQSw/04jQq3yoyQd9qMZUfPieE
edjBiVtaN/ecNGdJM7u7k2L3ADe+ObX9o3Dq6evmxWPUtSECAwEAAaOBkDCBjTAd
BgNVHQ4EFgQUvMfE2qXU2IZw4c5X+i48cGji1/owUQYDVR0jBEowSIAUvMfE2qXU
2IZw4c5X+i48cGji1/qhGqQYMBYxFDASBgNVBAMMC0Vhc3ktUlNBIENBghRbk2Gg
e5ul0HZATUh1OoJl4PgIrjAMBgNVHRMEBTADAQH/MAsGA1UdDwQEAwIBBjANBgkq
hkiG9w0BAQsFAAOCAQEAn5mckexf90rXn/xjzhKSbc2pNarQJ/YcmQ5xpRwv8D6x
GQieEk9BB8iWzaufH0cW+LI80zZYpjMg1qygKDoPIRryn0MVsr03XRCxnQRlkC7f
ow62PMXOp31ru1vq0ar/BjYE9EhQVEFdErhmc0FMmrkWP7H5rwRX7GO5T3wNfO3q
+rftpJiCVeY4lFWyNuHKZv3n8DtfwOoT5ybpJ31/mn6i/SWfaJa5gY9I8+jh6q7m
bRcTvNQk+G1ApgJZuoV5shAPZg6oJZVvU9q8FryMmcPxB4dTZwA3NIZfjQs8Q7lD
B0/XhJ+bjQvtC2YLfNLZgsEwOrUGs+ZCbL3T1FyLpg==
-----END CERTIFICATE-----
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
a8:92:f9:c5:d7:40:22:75:38:b8:b6:b6:1e:b1:8c:2c
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=Easy-RSA CA
Validity
Not Before: Nov 5 17:20:19 2021 GMT
Not After : Feb 8 17:20:19 2024 GMT
Subject: CN=koromicha
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:d1:f5:5f:c8:1e:6c:c5:35:fe:9a:68:d1:91:2d:
cb:11:b3:08:ed:47:3a:b8:32:74:df:f1:b7:78:be:
25:fc:95:73:be:6b:de:c8:89:1d:39:5e:72:4d:ea:
a3:13:2a:c9:29:44:2e:17:fc:48:d9:6c:8b:2f:ca:
a4:e5:90:43:a9:8b:a2:7a:bb:b5:c8:7a:6a:fe:9d:
4b:aa:67:78:e8:3f:53:9e:9d:b3:25:77:a1:22:f3:
b1:f0:82:97:9e:f5:14:b2:93:de:c5:20:84:05:54:
d5:70:ad:d5:4f:41:04:a6:56:04:08:e9:45:ea:eb:
c2:00:da:ee:1b:b4:30:74:c5:9e:76:6d:49:0c:8c:
7e:45:8a:e5:93:1a:d0:f6:70:1a:73:df:b2:eb:68:
2d:7a:1e:68:00:9e:b1:1f:1d:14:75:1b:89:56:b2:
e8:8e:84:e6:ea:39:50:93:0d:0e:30:6d:fc:97:3e:
6a:66:c3:cc:f3:93:12:5c:38:b4:62:ef:58:7f:a7:
70:05:2c:2d:f0:54:5e:7e:7a:98:ea:af:8d:6d:2e:
9c:47:80:1f:26:67:b4:2d:44:11:2f:6d:a5:9a:96:
7f:b5:ae:f8:48:61:ca:5c:f8:d5:1b:44:40:8b:fc:
97:01:5e:15:24:28:c6:24:81:39:d4:e0:3d:1f:81:
9a:11
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Subject Key Identifier:
B1:97:65:D8:90:01:7E:57:CA:11:73:4D:E2:E3:83:6F:71:B9:1B:6E
X509v3 Authority Key Identifier:
keyid:BC:C7:C4:DA:A5:D4:D8:86:70:E1:CE:57:FA:2E:3C:70:68:E2:D7:FA
DirName:/CN=Easy-RSA CA
serial:5B:93:61:A0:7B:9B:A5:D0:76:40:4D:48:75:3A:82:65:E0:F8:08:AE
X509v3 Extended Key Usage:
TLS Web Client Authentication
X509v3 Key Usage:
Digital Signature
Signature Algorithm: sha256WithRSAEncryption
57:ae:78:40:08:84:4f:4a:ec:53:b3:85:96:e8:c9:25:2b:3f:
37:16:37:53:e4:7b:eb:c5:0b:29:36:75:44:75:cc:47:a2:b1:
3a:fa:a1:07:88:89:99:b4:6e:21:82:1a:8e:42:1d:6c:b9:b5:
e2:21:85:55:a8:34:9e:80:52:27:81:c2:f7:af:e7:94:27:bf:
cb:7c:a2:cf:39:90:95:95:29:75:a1:c7:9c:68:5b:5e:5c:aa:
81:3d:c7:8a:79:54:9c:bc:9c:73:a2:76:02:56:42:56:4f:82:
80:23:0e:a3:8d:2f:86:0e:3e:08:7d:a8:b6:55:e7:2a:8f:6b:
4a:68:99:93:44:57:02:19:11:7d:cc:cf:05:a6:ce:4a:a0:41:
df:a1:88:8e:b3:0d:f3:67:cf:f9:82:27:41:bc:3b:4e:fb:7f:
60:e5:43:bb:7f:61:63:71:89:cf:55:fc:ce:82:bb:8c:2a:11:
9b:e7:e0:97:e3:ba:e0:cd:b0:12:35:56:41:58:62:0d:63:58:
ec:55:50:2b:82:5a:b5:4f:42:23:c7:e8:e6:8a:91:10:8b:a2:
40:47:85:ed:98:7f:e5:df:96:06:30:6b:ec:6f:9c:2d:5a:5a:
0a:71:fb:e2:1d:3e:f6:35:cd:ec:19:9b:67:c2:44:e3:b7:b6:
9f:81:51:c5
-----BEGIN CERTIFICATE-----
MIIDWDCCAkCgAwIBAgIRAKiS+cXXQCJ1OLi2th6xjCwwDQYJKoZIhvcNAQELBQAw
FjEUMBIGA1UEAwwLRWFzeS1SU0EgQ0EwHhcNMjExMTA1MTcyMDE5WhcNMjQwMjA4
MTcyMDE5WjAUMRIwEAYDVQQDDAlrb3JvbWljaGEwggEiMA0GCSqGSIb3DQEBAQUA
A4IBDwAwggEKAoIBAQDR9V/IHmzFNf6aaNGRLcsRswjtRzq4MnTf8bd4viX8lXO+
a97IiR05XnJN6qMTKskpRC4X/EjZbIsvyqTlkEOpi6J6u7XIemr+nUuqZ3joP1Oe
nbMld6Ei87Hwgpee9RSyk97FIIQFVNVwrdVPQQSmVgQI6UXq68IA2u4btDB0xZ52
bUkMjH5FiuWTGtD2cBpz37LraC16HmgAnrEfHRR1G4lWsuiOhObqOVCTDQ4wbfyX
Pmpmw8zzkxJcOLRi71h/p3AFLC3wVF5+epjqr41tLpxHgB8mZ7QtRBEvbaWaln+1
rvhIYcpc+NUbRECL/JcBXhUkKMYkgTnU4D0fgZoRAgMBAAGjgaIwgZ8wCQYDVR0T
BAIwADAdBgNVHQ4EFgQUsZdl2JABflfKEXNN4uODb3G5G24wUQYDVR0jBEowSIAU
vMfE2qXU2IZw4c5X+i48cGji1/qhGqQYMBYxFDASBgNVBAMMC0Vhc3ktUlNBIENB
ghRbk2Gge5ul0HZATUh1OoJl4PgIrjATBgNVHSUEDDAKBggrBgEFBQcDAjALBgNV
HQ8EBAMCB4AwDQYJKoZIhvcNAQELBQADggEBAFeueEAIhE9K7FOzhZboySUrPzcW
N1Pke+vFCyk2dUR1zEeisTr6oQeIiZm0biGCGo5CHWy5teIhhVWoNJ6AUieBwvev
55Qnv8t8os85kJWVKXWhx5xoW15cqoE9x4p5VJy8nHOidgJWQlZPgoAjDqONL4YO
Pgh9qLZV5yqPa0pomZNEVwIZEX3MzwWmzkqgQd+hiI6zDfNnz/mCJ0G8O077f2Dl
Q7t/YWNxic9V/M6Cu4wqEZvn4JfjuuDNsBI1VkFYYg1jWOxVUCuCWrVPQiPH6OaK
kRCLokBHhe2Yf+XflgYwa+xvnC1aWgpx++IdPvY1zewZm2fCROO3tp+BUcU=
-----END CERTIFICATE-----
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDR9V/IHmzFNf6a
aNGRLcsRswjtRzq4MnTf8bd4viX8lXO+a97IiR05XnJN6qMTKskpRC4X/EjZbIsv
yqTlkEOpi6J6u7XIemr+nUuqZ3joP1OenbMld6Ei87Hwgpee9RSyk97FIIQFVNVw
rdVPQQSmVgQI6UXq68IA2u4btDB0xZ52bUkMjH5FiuWTGtD2cBpz37LraC16HmgA
nrEfHRR1G4lWsuiOhObqOVCTDQ4wbfyXPmpmw8zzkxJcOLRi71h/p3AFLC3wVF5+
epjqr41tLpxHgB8mZ7QtRBEvbaWaln+1rvhIYcpc+NUbRECL/JcBXhUkKMYkgTnU
4D0fgZoRAgMBAAECggEBAMBTVd7Zx+dK06Ob+sRTP15CMx4vjmFmjtsI73jiLafX
O0QmSdhGiYegtXIcSi9nlQeBFfwQtKa+IC2yIiTLZr+rUjW9NwKi6Nm9Oq+owv9z
6uQ0LwNWNzvuIYRgDAWnGMOQYpMOewDrOe1Sv0AvHdREnMOQ8+QC/B6ObWjhQTXk
mqyvCY2IEg22upif5kDPLul6FtGuGwzUQwxYVfyOem0ECVJ4yotuS4ie8D36fxKD
utY18RJGhG9J1gRHJmQYcuB9jRkuVuno8pBdR3jabCE68DzpzOXvV4LHTIAxJtEz
NEZbzgwmf7TPg84pahaLYQOyxQpu8P6xm6QhBfTEPAECgYEA+UIKiGTlvy/EX8st
5I7PI8yhPJI8fbq/9oqjd5nwsUbzngdeuyy7HxruzAPQA/bFGSTikyf9jHPYAqZ0
7GGx9KCgbXyGNUk90ipHEqzXomrEjIh9y3qAQu+VLt4XILAfrDgV+QUITXIsRCnY
tOg4CdUJFJg5uQblR/AZCSx+9MECgYEA16M1SiSImoydUKvtl+4Jzqn4CSg3cKya
xWWtXYQLrh6PMOoKy/idGV6Xcl5H57xASqxjehyL5VzaBw6mSmcIuuovbuMWpI4Q
zVZQEgizsDtEFNr8tQ+qtlXR7DwEkUOLtfQaULDD9LR1OMM06x9Py9UxCbfi3/Dl
Kod8GFazaVECgYAleV1WBj1YUhknAcgDjcjsq+4tyhqYGISVz2AmMhmyvWURBDCk
2WPEmGsAdy5F+krFrfr2ftOq0xvNwjLf+wwjKCcWbttKlZlayIpo7114CK9GJZss
BV3VMmnuYut9OZ15afE7wBrwcdLf6J6xDByotcOouf4rqDK+bwWEkJEBwQKBgQDN
4OIhDq5puDT+b5fhhYBRkw/gVkhQSEtgigoyjb7FGCIoVlvGkHAVZ616oS9Pvfk4
EkzLqnOaocL8F+2GfcblBnARE7lrlMPP+EdsYGiGqp7+tnGtwO6BNYC+ZjMKKg46
w3tYbNw6RwzgC+f7UCLUfpBaMfnnS0zRBRfi+OxEcQKBgEMEes7DT5sqoQkam9lk
AmP8NK+eAoB7RWk8A1ADBlz48xmIH/lR99su9bWWd0xthYuBvx3ZpPRTqp0Z2ehm
7w3jnw+A7BZn1/gmcXLCXexQl+tn0nfm87xpwXCDmHjZzdldzLMpjOMHZDmOcufN
y30Rsmt3vdeo5Rv+whSSypnq
-----END PRIVATE KEY-----
Use specific DNS Server with OpenVPN Clients
So depending on the method you used above to define the DNS server address you can proceed as follows.
In this tutorial, we are using a Linux system, specifically, Debian 11/Rocky Linux 8 as our OpenVPN clients for demonstration purposes.
On Ubuntu/Debian Systems:
install openresol package.On Ubuntu/Debian systems;
apt install openresolvNext, edit the OpenVPN client configuration file;
vim client-1.ovpnand add the lines below;
script-security 2
up /etc/openvpn/update-resolv-conf
down /etc/openvpn/update-resolv-confSee my sample updated OpenVPN client configuration file;
cat client-1.ovpn
client
tls-client
pull
dev tun
proto udp4
remote 192.168.58.22 1194
resolv-retry infinite
nobind
persist-key
persist-tun
key-direction 1
remote-cert-tls server
auth-nocache
comp-lzo
verb 3
auth SHA512
cipher AES-256-CBC
data-ciphers AES-256-CBC
comp-lzo no
script-security 2
up /etc/openvpn/update-resolv-conf
down /etc/openvpn/update-resolv-conf
-----BEGIN OpenVPN Static key V1-----
ec31b288a9a3865c4b5f3583b481ff5c
434e957be6569ed573a58a102ce53efc
b9528f15f5412046c5a603e6916b565b
fe2c6a0f955dcec2d3f7e6cec7e373bb
dff40b041f1488d4177c3de04bdff43b
e361eff6328c499621e0846ec72565ef
734fc02e51540d1c5c19102156a080f7
fde124822bf6fc802dff9facf24998de
6f91f081dafcdd28f4bca9223afe694d
12d57beb6aed96753d651a2ca4722214
5fa87829b9f53f2ccb89d9f15112c9cd
3594ead75bc1df737b50188c2829d724
3aff136577b3c79e6f863112aadf5aeb
8b6d53c607874c71104acfa22e587bd3
22b14a2c0a91e15569d99d5e35a52a8b
0aa4f24ccf10d8757dfd75da14fd21ac
-----END OpenVPN Static key V1-----
-----BEGIN CERTIFICATE-----
MIIDSzCCAjOgAwIBAgIUW5NhoHubpdB2QE1IdTqCZeD4CK4wDQYJKoZIhvcNAQEL
BQAwFjEUMBIGA1UEAwwLRWFzeS1SU0EgQ0EwHhcNMjExMTA1MTcxNDQ4WhcNMzEx
MTAzMTcxNDQ4WjAWMRQwEgYDVQQDDAtFYXN5LVJTQSBDQTCCASIwDQYJKoZIhvcN
AQEBBQADggEPADCCAQoCggEBALGvwj57vpugazdMtjIVngKybzapSfT7rm1Rv+d2
SssBwsTf4kDXqfwQiQLPEDo5mpxIO1XBEhsNS3CeBBSfGHgvT3EbiXKLS0mpMiIK
nayJJh2+v3xg+3EU5jemNJ8p3iqsWz566ds/C6haZsp9cM5oGBOOSbHOMJo4S6+6
XmZfi8sdCWlSxrntd74MmEPI7wvmClA5xaM3hfzpHXdhrcTr9JDVMf0sYSkXUbc5
nyDQrLtcZiVyoPCJxB41OoTYd1aLDV/7F+A6ShSQSw/04jQq3yoyQd9qMZUfPieE
edjBiVtaN/ecNGdJM7u7k2L3ADe+ObX9o3Dq6evmxWPUtSECAwEAAaOBkDCBjTAd
BgNVHQ4EFgQUvMfE2qXU2IZw4c5X+i48cGji1/owUQYDVR0jBEowSIAUvMfE2qXU
2IZw4c5X+i48cGji1/qhGqQYMBYxFDASBgNVBAMMC0Vhc3ktUlNBIENBghRbk2Gg
e5ul0HZATUh1OoJl4PgIrjAMBgNVHRMEBTADAQH/MAsGA1UdDwQEAwIBBjANBgkq
hkiG9w0BAQsFAAOCAQEAn5mckexf90rXn/xjzhKSbc2pNarQJ/YcmQ5xpRwv8D6x
GQieEk9BB8iWzaufH0cW+LI80zZYpjMg1qygKDoPIRryn0MVsr03XRCxnQRlkC7f
ow62PMXOp31ru1vq0ar/BjYE9EhQVEFdErhmc0FMmrkWP7H5rwRX7GO5T3wNfO3q
+rftpJiCVeY4lFWyNuHKZv3n8DtfwOoT5ybpJ31/mn6i/SWfaJa5gY9I8+jh6q7m
bRcTvNQk+G1ApgJZuoV5shAPZg6oJZVvU9q8FryMmcPxB4dTZwA3NIZfjQs8Q7lD
B0/XhJ+bjQvtC2YLfNLZgsEwOrUGs+ZCbL3T1FyLpg==
-----END CERTIFICATE-----
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
a8:92:f9:c5:d7:40:22:75:38:b8:b6:b6:1e:b1:8c:2c
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=Easy-RSA CA
Validity
Not Before: Nov 5 17:20:19 2021 GMT
Not After : Feb 8 17:20:19 2024 GMT
Subject: CN=koromicha
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:d1:f5:5f:c8:1e:6c:c5:35:fe:9a:68:d1:91:2d:
cb:11:b3:08:ed:47:3a:b8:32:74:df:f1:b7:78:be:
25:fc:95:73:be:6b:de:c8:89:1d:39:5e:72:4d:ea:
a3:13:2a:c9:29:44:2e:17:fc:48:d9:6c:8b:2f:ca:
a4:e5:90:43:a9:8b:a2:7a:bb:b5:c8:7a:6a:fe:9d:
4b:aa:67:78:e8:3f:53:9e:9d:b3:25:77:a1:22:f3:
b1:f0:82:97:9e:f5:14:b2:93:de:c5:20:84:05:54:
d5:70:ad:d5:4f:41:04:a6:56:04:08:e9:45:ea:eb:
c2:00:da:ee:1b:b4:30:74:c5:9e:76:6d:49:0c:8c:
7e:45:8a:e5:93:1a:d0:f6:70:1a:73:df:b2:eb:68:
2d:7a:1e:68:00:9e:b1:1f:1d:14:75:1b:89:56:b2:
e8:8e:84:e6:ea:39:50:93:0d:0e:30:6d:fc:97:3e:
6a:66:c3:cc:f3:93:12:5c:38:b4:62:ef:58:7f:a7:
70:05:2c:2d:f0:54:5e:7e:7a:98:ea:af:8d:6d:2e:
9c:47:80:1f:26:67:b4:2d:44:11:2f:6d:a5:9a:96:
7f:b5:ae:f8:48:61:ca:5c:f8:d5:1b:44:40:8b:fc:
97:01:5e:15:24:28:c6:24:81:39:d4:e0:3d:1f:81:
9a:11
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Subject Key Identifier:
B1:97:65:D8:90:01:7E:57:CA:11:73:4D:E2:E3:83:6F:71:B9:1B:6E
X509v3 Authority Key Identifier:
keyid:BC:C7:C4:DA:A5:D4:D8:86:70:E1:CE:57:FA:2E:3C:70:68:E2:D7:FA
DirName:/CN=Easy-RSA CA
serial:5B:93:61:A0:7B:9B:A5:D0:76:40:4D:48:75:3A:82:65:E0:F8:08:AE
X509v3 Extended Key Usage:
TLS Web Client Authentication
X509v3 Key Usage:
Digital Signature
Signature Algorithm: sha256WithRSAEncryption
57:ae:78:40:08:84:4f:4a:ec:53:b3:85:96:e8:c9:25:2b:3f:
37:16:37:53:e4:7b:eb:c5:0b:29:36:75:44:75:cc:47:a2:b1:
3a:fa:a1:07:88:89:99:b4:6e:21:82:1a:8e:42:1d:6c:b9:b5:
e2:21:85:55:a8:34:9e:80:52:27:81:c2:f7:af:e7:94:27:bf:
cb:7c:a2:cf:39:90:95:95:29:75:a1:c7:9c:68:5b:5e:5c:aa:
81:3d:c7:8a:79:54:9c:bc:9c:73:a2:76:02:56:42:56:4f:82:
80:23:0e:a3:8d:2f:86:0e:3e:08:7d:a8:b6:55:e7:2a:8f:6b:
4a:68:99:93:44:57:02:19:11:7d:cc:cf:05:a6:ce:4a:a0:41:
df:a1:88:8e:b3:0d:f3:67:cf:f9:82:27:41:bc:3b:4e:fb:7f:
60:e5:43:bb:7f:61:63:71:89:cf:55:fc:ce:82:bb:8c:2a:11:
9b:e7:e0:97:e3:ba:e0:cd:b0:12:35:56:41:58:62:0d:63:58:
ec:55:50:2b:82:5a:b5:4f:42:23:c7:e8:e6:8a:91:10:8b:a2:
40:47:85:ed:98:7f:e5:df:96:06:30:6b:ec:6f:9c:2d:5a:5a:
0a:71:fb:e2:1d:3e:f6:35:cd:ec:19:9b:67:c2:44:e3:b7:b6:
9f:81:51:c5
-----BEGIN CERTIFICATE-----
MIIDWDCCAkCgAwIBAgIRAKiS+cXXQCJ1OLi2th6xjCwwDQYJKoZIhvcNAQELBQAw
FjEUMBIGA1UEAwwLRWFzeS1SU0EgQ0EwHhcNMjExMTA1MTcyMDE5WhcNMjQwMjA4
MTcyMDE5WjAUMRIwEAYDVQQDDAlrb3JvbWljaGEwggEiMA0GCSqGSIb3DQEBAQUA
A4IBDwAwggEKAoIBAQDR9V/IHmzFNf6aaNGRLcsRswjtRzq4MnTf8bd4viX8lXO+
a97IiR05XnJN6qMTKskpRC4X/EjZbIsvyqTlkEOpi6J6u7XIemr+nUuqZ3joP1Oe
nbMld6Ei87Hwgpee9RSyk97FIIQFVNVwrdVPQQSmVgQI6UXq68IA2u4btDB0xZ52
bUkMjH5FiuWTGtD2cBpz37LraC16HmgAnrEfHRR1G4lWsuiOhObqOVCTDQ4wbfyX
Pmpmw8zzkxJcOLRi71h/p3AFLC3wVF5+epjqr41tLpxHgB8mZ7QtRBEvbaWaln+1
rvhIYcpc+NUbRECL/JcBXhUkKMYkgTnU4D0fgZoRAgMBAAGjgaIwgZ8wCQYDVR0T
BAIwADAdBgNVHQ4EFgQUsZdl2JABflfKEXNN4uODb3G5G24wUQYDVR0jBEowSIAU
vMfE2qXU2IZw4c5X+i48cGji1/qhGqQYMBYxFDASBgNVBAMMC0Vhc3ktUlNBIENB
ghRbk2Gge5ul0HZATUh1OoJl4PgIrjATBgNVHSUEDDAKBggrBgEFBQcDAjALBgNV
HQ8EBAMCB4AwDQYJKoZIhvcNAQELBQADggEBAFeueEAIhE9K7FOzhZboySUrPzcW
N1Pke+vFCyk2dUR1zEeisTr6oQeIiZm0biGCGo5CHWy5teIhhVWoNJ6AUieBwvev
55Qnv8t8os85kJWVKXWhx5xoW15cqoE9x4p5VJy8nHOidgJWQlZPgoAjDqONL4YO
Pgh9qLZV5yqPa0pomZNEVwIZEX3MzwWmzkqgQd+hiI6zDfNnz/mCJ0G8O077f2Dl
Q7t/YWNxic9V/M6Cu4wqEZvn4JfjuuDNsBI1VkFYYg1jWOxVUCuCWrVPQiPH6OaK
kRCLokBHhe2Yf+XflgYwa+xvnC1aWgpx++IdPvY1zewZm2fCROO3tp+BUcU=
-----END CERTIFICATE-----
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDR9V/IHmzFNf6a
aNGRLcsRswjtRzq4MnTf8bd4viX8lXO+a97IiR05XnJN6qMTKskpRC4X/EjZbIsv
yqTlkEOpi6J6u7XIemr+nUuqZ3joP1OenbMld6Ei87Hwgpee9RSyk97FIIQFVNVw
rdVPQQSmVgQI6UXq68IA2u4btDB0xZ52bUkMjH5FiuWTGtD2cBpz37LraC16HmgA
nrEfHRR1G4lWsuiOhObqOVCTDQ4wbfyXPmpmw8zzkxJcOLRi71h/p3AFLC3wVF5+
epjqr41tLpxHgB8mZ7QtRBEvbaWaln+1rvhIYcpc+NUbRECL/JcBXhUkKMYkgTnU
4D0fgZoRAgMBAAECggEBAMBTVd7Zx+dK06Ob+sRTP15CMx4vjmFmjtsI73jiLafX
O0QmSdhGiYegtXIcSi9nlQeBFfwQtKa+IC2yIiTLZr+rUjW9NwKi6Nm9Oq+owv9z
6uQ0LwNWNzvuIYRgDAWnGMOQYpMOewDrOe1Sv0AvHdREnMOQ8+QC/B6ObWjhQTXk
mqyvCY2IEg22upif5kDPLul6FtGuGwzUQwxYVfyOem0ECVJ4yotuS4ie8D36fxKD
utY18RJGhG9J1gRHJmQYcuB9jRkuVuno8pBdR3jabCE68DzpzOXvV4LHTIAxJtEz
NEZbzgwmf7TPg84pahaLYQOyxQpu8P6xm6QhBfTEPAECgYEA+UIKiGTlvy/EX8st
5I7PI8yhPJI8fbq/9oqjd5nwsUbzngdeuyy7HxruzAPQA/bFGSTikyf9jHPYAqZ0
7GGx9KCgbXyGNUk90ipHEqzXomrEjIh9y3qAQu+VLt4XILAfrDgV+QUITXIsRCnY
tOg4CdUJFJg5uQblR/AZCSx+9MECgYEA16M1SiSImoydUKvtl+4Jzqn4CSg3cKya
xWWtXYQLrh6PMOoKy/idGV6Xcl5H57xASqxjehyL5VzaBw6mSmcIuuovbuMWpI4Q
zVZQEgizsDtEFNr8tQ+qtlXR7DwEkUOLtfQaULDD9LR1OMM06x9Py9UxCbfi3/Dl
Kod8GFazaVECgYAleV1WBj1YUhknAcgDjcjsq+4tyhqYGISVz2AmMhmyvWURBDCk
2WPEmGsAdy5F+krFrfr2ftOq0xvNwjLf+wwjKCcWbttKlZlayIpo7114CK9GJZss
BV3VMmnuYut9OZ15afE7wBrwcdLf6J6xDByotcOouf4rqDK+bwWEkJEBwQKBgQDN
4OIhDq5puDT+b5fhhYBRkw/gVkhQSEtgigoyjb7FGCIoVlvGkHAVZ616oS9Pvfk4
EkzLqnOaocL8F+2GfcblBnARE7lrlMPP+EdsYGiGqp7+tnGtwO6BNYC+ZjMKKg46
w3tYbNw6RwzgC+f7UCLUfpBaMfnnS0zRBRfi+OxEcQKBgEMEes7DT5sqoQkam9lk
AmP8NK+eAoB7RWk8A1ADBlz48xmIH/lR99su9bWWd0xthYuBvx3ZpPRTqp0Z2ehm
7w3jnw+A7BZn1/gmcXLCXexQl+tn0nfm87xpwXCDmHjZzdldzLMpjOMHZDmOcufN
y30Rsmt3vdeo5Rv+whSSypnq
-----END PRIVATE KEY-----
Connect client to VPN;
openvpn client-1.ovpn
2021-11-08 14:25:09 WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless "allow-compression yes" is also set.
2021-11-08 14:25:09 OpenVPN 2.5.1 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on May 14 2021
2021-11-08 14:25:09 library versions: OpenSSL 1.1.1k 25 Mar 2021, LZO 2.10
2021-11-08 14:25:09 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
2021-11-08 14:25:09 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
2021-11-08 14:25:09 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
2021-11-08 14:25:09 TCP/UDP: Preserving recently used remote address: [AF_INET]192.168.58.22:1194
2021-11-08 14:25:09 Socket Buffers: R=[212992->212992] S=[212992->212992]
2021-11-08 14:25:09 UDPv4 link local: (not bound)
2021-11-08 14:25:09 UDPv4 link remote: [AF_INET]192.168.58.22:1194
2021-11-08 14:25:09 TLS: Initial packet from [AF_INET]192.168.58.22:1194, sid=0a6596f7 2db76aa3
2021-11-08 14:25:09 VERIFY OK: depth=1, CN=Easy-RSA CA
2021-11-08 14:25:09 VERIFY KU OK
2021-11-08 14:25:09 Validating certificate extended key usage
2021-11-08 14:25:09 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
2021-11-08 14:25:09 VERIFY EKU OK
2021-11-08 14:25:09 VERIFY OK: depth=0, CN=server
2021-11-08 14:25:09 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 2048 bit RSA
2021-11-08 14:25:09 [server] Peer Connection Initiated with [AF_INET]192.168.58.22:1194
2021-11-08 14:25:09 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1 bypass-dhcp,dhcp-option DNS 192.168.58.22,dhcp-option DNS 8.8.8.8,dhcp-option DOMAIN kifarunix-demo.com,route-gateway 10.8.0.1,topology subnet,ping 10,ping-restart 120,ifconfig 10.8.0.2 255.255.255.0,peer-id 0,cipher AES-256-CBC'
2021-11-08 14:25:09 OPTIONS IMPORT: timers and/or timeouts modified
2021-11-08 14:25:09 OPTIONS IMPORT: --ifconfig/up options modified
2021-11-08 14:25:09 OPTIONS IMPORT: route options modified
2021-11-08 14:25:09 OPTIONS IMPORT: route-related options modified
2021-11-08 14:25:09 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
2021-11-08 14:25:09 OPTIONS IMPORT: peer-id set
2021-11-08 14:25:09 OPTIONS IMPORT: adjusting link_mtu to 1625
2021-11-08 14:25:09 OPTIONS IMPORT: data channel crypto options modified
2021-11-08 14:25:09 Outgoing Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key
2021-11-08 14:25:09 Outgoing Data Channel: Using 512 bit message hash 'SHA512' for HMAC authentication
2021-11-08 14:25:09 Incoming Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key
2021-11-08 14:25:09 Incoming Data Channel: Using 512 bit message hash 'SHA512' for HMAC authentication
2021-11-08 14:25:09 net_route_v4_best_gw query: dst 0.0.0.0
2021-11-08 14:25:09 net_route_v4_best_gw result: via 10.0.2.2 dev enp0s3
2021-11-08 14:25:09 ROUTE_GATEWAY 10.0.2.2/255.255.255.0 IFACE=enp0s3 HWADDR=08:00:27:36:23:40
2021-11-08 14:25:09 TUN/TAP device tun0 opened
2021-11-08 14:25:09 net_iface_mtu_set: mtu 1500 for tun0
2021-11-08 14:25:09 net_iface_up: set tun0 up
2021-11-08 14:25:09 net_addr_v4_add: 10.8.0.2/24 dev tun0
2021-11-08 14:25:09 /etc/openvpn/update-resolv-conf tun0 1500 1625 10.8.0.2 255.255.255.0 init
dhcp-option DNS 192.168.58.22
dhcp-option DNS 8.8.8.8
dhcp-option DOMAIN kifarunix-demo.com
2021-11-08 14:25:10 net_route_v4_add: 192.168.58.22/32 via 10.0.2.2 dev [NULL] table 0 metric -1
2021-11-08 14:25:10 net_route_v4_add: 0.0.0.0/1 via 10.8.0.1 dev [NULL] table 0 metric -1
2021-11-08 14:25:10 net_route_v4_add: 128.0.0.0/1 via 10.8.0.1 dev [NULL] table 0 metric -1
2021-11-08 14:25:10 Initialization Sequence Completed
This updates the /etc/resolv.conf file with your custom DNS entries;
cat /etc/resolv.conf# Generated by resolvconf
search kifarunix-demo.com
nameserver 192.168.58.22
nameserver 8.8.8.8My internal DNS resolution;
dig debian11.kifarunix-demo.com +short192.168.59.14Refer to our DNS guide;
Configure BIND DNS Server using Webmin on Debian 11
On CentOS/RHEL/Rocky Linux:
install update-systemd-resolved
git clone https://github.com/jonathanio/update-systemd-resolved.git
cd update-systemd-resolved
makeSample output;
Successfully installed update-systemd-resolved to /etc/openvpn/scripts/update-systemd-resolved.
Now would be a good time to update /etc/nsswitch.conf:
# Use systemd-resolved first, then fall back to /etc/resolv.conf
hosts: files resolve dns myhostname
# Use /etc/resolv.conf first, then fall back to systemd-resolved
hosts: files dns resolve myhostname
You should also update your OpenVPN configuration:
setenv PATH /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
script-security 2
up /etc/openvpn/scripts/update-systemd-resolved
up-restart
down /etc/openvpn/scripts/update-systemd-resolved
down-pre
or pass –config /etc/openvpn/scripts/update-systemd-resolved.conf
in addition to any other –config arguments to your openvpn command.
Next, enable systemd-resolved.service.
systemctl enable --now systemd-resolved.serviceUpdate the /etc/nsswitch.conf file to look up DNS via the resolve (systemd-resolved.service) service. (Use /etc/resolv.conf first, then fall back to systemd-resolved)
sed -i '/hosts:/s/dns/dns resolve/' /etc/nsswitch.confNext, update the client configuration file to include the lines;
setenv PATH /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
script-security 2
up /etc/openvpn/scripts/update-systemd-resolved
up-restart
down /etc/openvpn/scripts/update-systemd-resolved
down-preAnd this is how my sample config looks like;
cat client-1.ovpn
client
tls-client
pull
dev tun
proto udp4
remote 192.168.58.22 1194
resolv-retry infinite
nobind
persist-key
persist-tun
key-direction 1
remote-cert-tls server
auth-nocache
comp-lzo
verb 3
auth SHA512
cipher AES-256-CBC
comp-lzo no
setenv PATH /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
script-security 2
up /etc/openvpn/scripts/update-systemd-resolved
up-restart
down /etc/openvpn/scripts/update-systemd-resolved
down-pre
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
ec31b288a9a3865c4b5f3583b481ff5c
434e957be6569ed573a58a102ce53efc
b9528f15f5412046c5a603e6916b565b
fe2c6a0f955dcec2d3f7e6cec7e373bb
dff40b041f1488d4177c3de04bdff43b
e361eff6328c499621e0846ec72565ef
734fc02e51540d1c5c19102156a080f7
fde124822bf6fc802dff9facf24998de
6f91f081dafcdd28f4bca9223afe694d
12d57beb6aed96753d651a2ca4722214
5fa87829b9f53f2ccb89d9f15112c9cd
3594ead75bc1df737b50188c2829d724
3aff136577b3c79e6f863112aadf5aeb
8b6d53c607874c71104acfa22e587bd3
22b14a2c0a91e15569d99d5e35a52a8b
0aa4f24ccf10d8757dfd75da14fd21ac
-----END OpenVPN Static key V1-----
-----BEGIN CERTIFICATE-----
MIIDSzCCAjOgAwIBAgIUW5NhoHubpdB2QE1IdTqCZeD4CK4wDQYJKoZIhvcNAQEL
BQAwFjEUMBIGA1UEAwwLRWFzeS1SU0EgQ0EwHhcNMjExMTA1MTcxNDQ4WhcNMzEx
MTAzMTcxNDQ4WjAWMRQwEgYDVQQDDAtFYXN5LVJTQSBDQTCCASIwDQYJKoZIhvcN
AQEBBQADggEPADCCAQoCggEBALGvwj57vpugazdMtjIVngKybzapSfT7rm1Rv+d2
SssBwsTf4kDXqfwQiQLPEDo5mpxIO1XBEhsNS3CeBBSfGHgvT3EbiXKLS0mpMiIK
nayJJh2+v3xg+3EU5jemNJ8p3iqsWz566ds/C6haZsp9cM5oGBOOSbHOMJo4S6+6
XmZfi8sdCWlSxrntd74MmEPI7wvmClA5xaM3hfzpHXdhrcTr9JDVMf0sYSkXUbc5
nyDQrLtcZiVyoPCJxB41OoTYd1aLDV/7F+A6ShSQSw/04jQq3yoyQd9qMZUfPieE
edjBiVtaN/ecNGdJM7u7k2L3ADe+ObX9o3Dq6evmxWPUtSECAwEAAaOBkDCBjTAd
BgNVHQ4EFgQUvMfE2qXU2IZw4c5X+i48cGji1/owUQYDVR0jBEowSIAUvMfE2qXU
2IZw4c5X+i48cGji1/qhGqQYMBYxFDASBgNVBAMMC0Vhc3ktUlNBIENBghRbk2Gg
e5ul0HZATUh1OoJl4PgIrjAMBgNVHRMEBTADAQH/MAsGA1UdDwQEAwIBBjANBgkq
hkiG9w0BAQsFAAOCAQEAn5mckexf90rXn/xjzhKSbc2pNarQJ/YcmQ5xpRwv8D6x
GQieEk9BB8iWzaufH0cW+LI80zZYpjMg1qygKDoPIRryn0MVsr03XRCxnQRlkC7f
ow62PMXOp31ru1vq0ar/BjYE9EhQVEFdErhmc0FMmrkWP7H5rwRX7GO5T3wNfO3q
+rftpJiCVeY4lFWyNuHKZv3n8DtfwOoT5ybpJ31/mn6i/SWfaJa5gY9I8+jh6q7m
bRcTvNQk+G1ApgJZuoV5shAPZg6oJZVvU9q8FryMmcPxB4dTZwA3NIZfjQs8Q7lD
B0/XhJ+bjQvtC2YLfNLZgsEwOrUGs+ZCbL3T1FyLpg==
-----END CERTIFICATE-----
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
a8:92:f9:c5:d7:40:22:75:38:b8:b6:b6:1e:b1:8c:2c
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=Easy-RSA CA
Validity
Not Before: Nov 5 17:20:19 2021 GMT
Not After : Feb 8 17:20:19 2024 GMT
Subject: CN=koromicha
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:d1:f5:5f:c8:1e:6c:c5:35:fe:9a:68:d1:91:2d:
cb:11:b3:08:ed:47:3a:b8:32:74:df:f1:b7:78:be:
25:fc:95:73:be:6b:de:c8:89:1d:39:5e:72:4d:ea:
a3:13:2a:c9:29:44:2e:17:fc:48:d9:6c:8b:2f:ca:
a4:e5:90:43:a9:8b:a2:7a:bb:b5:c8:7a:6a:fe:9d:
4b:aa:67:78:e8:3f:53:9e:9d:b3:25:77:a1:22:f3:
b1:f0:82:97:9e:f5:14:b2:93:de:c5:20:84:05:54:
d5:70:ad:d5:4f:41:04:a6:56:04:08:e9:45:ea:eb:
c2:00:da:ee:1b:b4:30:74:c5:9e:76:6d:49:0c:8c:
7e:45:8a:e5:93:1a:d0:f6:70:1a:73:df:b2:eb:68:
2d:7a:1e:68:00:9e:b1:1f:1d:14:75:1b:89:56:b2:
e8:8e:84:e6:ea:39:50:93:0d:0e:30:6d:fc:97:3e:
6a:66:c3:cc:f3:93:12:5c:38:b4:62:ef:58:7f:a7:
70:05:2c:2d:f0:54:5e:7e:7a:98:ea:af:8d:6d:2e:
9c:47:80:1f:26:67:b4:2d:44:11:2f:6d:a5:9a:96:
7f:b5:ae:f8:48:61:ca:5c:f8:d5:1b:44:40:8b:fc:
97:01:5e:15:24:28:c6:24:81:39:d4:e0:3d:1f:81:
9a:11
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Subject Key Identifier:
B1:97:65:D8:90:01:7E:57:CA:11:73:4D:E2:E3:83:6F:71:B9:1B:6E
X509v3 Authority Key Identifier:
keyid:BC:C7:C4:DA:A5:D4:D8:86:70:E1:CE:57:FA:2E:3C:70:68:E2:D7:FA
DirName:/CN=Easy-RSA CA
serial:5B:93:61:A0:7B:9B:A5:D0:76:40:4D:48:75:3A:82:65:E0:F8:08:AE
X509v3 Extended Key Usage:
TLS Web Client Authentication
X509v3 Key Usage:
Digital Signature
Signature Algorithm: sha256WithRSAEncryption
57:ae:78:40:08:84:4f:4a:ec:53:b3:85:96:e8:c9:25:2b:3f:
37:16:37:53:e4:7b:eb:c5:0b:29:36:75:44:75:cc:47:a2:b1:
3a:fa:a1:07:88:89:99:b4:6e:21:82:1a:8e:42:1d:6c:b9:b5:
e2:21:85:55:a8:34:9e:80:52:27:81:c2:f7:af:e7:94:27:bf:
cb:7c:a2:cf:39:90:95:95:29:75:a1:c7:9c:68:5b:5e:5c:aa:
81:3d:c7:8a:79:54:9c:bc:9c:73:a2:76:02:56:42:56:4f:82:
80:23:0e:a3:8d:2f:86:0e:3e:08:7d:a8:b6:55:e7:2a:8f:6b:
4a:68:99:93:44:57:02:19:11:7d:cc:cf:05:a6:ce:4a:a0:41:
df:a1:88:8e:b3:0d:f3:67:cf:f9:82:27:41:bc:3b:4e:fb:7f:
60:e5:43:bb:7f:61:63:71:89:cf:55:fc:ce:82:bb:8c:2a:11:
9b:e7:e0:97:e3:ba:e0:cd:b0:12:35:56:41:58:62:0d:63:58:
ec:55:50:2b:82:5a:b5:4f:42:23:c7:e8:e6:8a:91:10:8b:a2:
40:47:85:ed:98:7f:e5:df:96:06:30:6b:ec:6f:9c:2d:5a:5a:
0a:71:fb:e2:1d:3e:f6:35:cd:ec:19:9b:67:c2:44:e3:b7:b6:
9f:81:51:c5
-----BEGIN CERTIFICATE-----
MIIDWDCCAkCgAwIBAgIRAKiS+cXXQCJ1OLi2th6xjCwwDQYJKoZIhvcNAQELBQAw
FjEUMBIGA1UEAwwLRWFzeS1SU0EgQ0EwHhcNMjExMTA1MTcyMDE5WhcNMjQwMjA4
MTcyMDE5WjAUMRIwEAYDVQQDDAlrb3JvbWljaGEwggEiMA0GCSqGSIb3DQEBAQUA
A4IBDwAwggEKAoIBAQDR9V/IHmzFNf6aaNGRLcsRswjtRzq4MnTf8bd4viX8lXO+
a97IiR05XnJN6qMTKskpRC4X/EjZbIsvyqTlkEOpi6J6u7XIemr+nUuqZ3joP1Oe
nbMld6Ei87Hwgpee9RSyk97FIIQFVNVwrdVPQQSmVgQI6UXq68IA2u4btDB0xZ52
bUkMjH5FiuWTGtD2cBpz37LraC16HmgAnrEfHRR1G4lWsuiOhObqOVCTDQ4wbfyX
Pmpmw8zzkxJcOLRi71h/p3AFLC3wVF5+epjqr41tLpxHgB8mZ7QtRBEvbaWaln+1
rvhIYcpc+NUbRECL/JcBXhUkKMYkgTnU4D0fgZoRAgMBAAGjgaIwgZ8wCQYDVR0T
BAIwADAdBgNVHQ4EFgQUsZdl2JABflfKEXNN4uODb3G5G24wUQYDVR0jBEowSIAU
vMfE2qXU2IZw4c5X+i48cGji1/qhGqQYMBYxFDASBgNVBAMMC0Vhc3ktUlNBIENB
ghRbk2Gge5ul0HZATUh1OoJl4PgIrjATBgNVHSUEDDAKBggrBgEFBQcDAjALBgNV
HQ8EBAMCB4AwDQYJKoZIhvcNAQELBQADggEBAFeueEAIhE9K7FOzhZboySUrPzcW
N1Pke+vFCyk2dUR1zEeisTr6oQeIiZm0biGCGo5CHWy5teIhhVWoNJ6AUieBwvev
55Qnv8t8os85kJWVKXWhx5xoW15cqoE9x4p5VJy8nHOidgJWQlZPgoAjDqONL4YO
Pgh9qLZV5yqPa0pomZNEVwIZEX3MzwWmzkqgQd+hiI6zDfNnz/mCJ0G8O077f2Dl
Q7t/YWNxic9V/M6Cu4wqEZvn4JfjuuDNsBI1VkFYYg1jWOxVUCuCWrVPQiPH6OaK
kRCLokBHhe2Yf+XflgYwa+xvnC1aWgpx++IdPvY1zewZm2fCROO3tp+BUcU=
-----END CERTIFICATE-----
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDR9V/IHmzFNf6a
aNGRLcsRswjtRzq4MnTf8bd4viX8lXO+a97IiR05XnJN6qMTKskpRC4X/EjZbIsv
yqTlkEOpi6J6u7XIemr+nUuqZ3joP1OenbMld6Ei87Hwgpee9RSyk97FIIQFVNVw
rdVPQQSmVgQI6UXq68IA2u4btDB0xZ52bUkMjH5FiuWTGtD2cBpz37LraC16HmgA
nrEfHRR1G4lWsuiOhObqOVCTDQ4wbfyXPmpmw8zzkxJcOLRi71h/p3AFLC3wVF5+
epjqr41tLpxHgB8mZ7QtRBEvbaWaln+1rvhIYcpc+NUbRECL/JcBXhUkKMYkgTnU
4D0fgZoRAgMBAAECggEBAMBTVd7Zx+dK06Ob+sRTP15CMx4vjmFmjtsI73jiLafX
O0QmSdhGiYegtXIcSi9nlQeBFfwQtKa+IC2yIiTLZr+rUjW9NwKi6Nm9Oq+owv9z
6uQ0LwNWNzvuIYRgDAWnGMOQYpMOewDrOe1Sv0AvHdREnMOQ8+QC/B6ObWjhQTXk
mqyvCY2IEg22upif5kDPLul6FtGuGwzUQwxYVfyOem0ECVJ4yotuS4ie8D36fxKD
utY18RJGhG9J1gRHJmQYcuB9jRkuVuno8pBdR3jabCE68DzpzOXvV4LHTIAxJtEz
NEZbzgwmf7TPg84pahaLYQOyxQpu8P6xm6QhBfTEPAECgYEA+UIKiGTlvy/EX8st
5I7PI8yhPJI8fbq/9oqjd5nwsUbzngdeuyy7HxruzAPQA/bFGSTikyf9jHPYAqZ0
7GGx9KCgbXyGNUk90ipHEqzXomrEjIh9y3qAQu+VLt4XILAfrDgV+QUITXIsRCnY
tOg4CdUJFJg5uQblR/AZCSx+9MECgYEA16M1SiSImoydUKvtl+4Jzqn4CSg3cKya
xWWtXYQLrh6PMOoKy/idGV6Xcl5H57xASqxjehyL5VzaBw6mSmcIuuovbuMWpI4Q
zVZQEgizsDtEFNr8tQ+qtlXR7DwEkUOLtfQaULDD9LR1OMM06x9Py9UxCbfi3/Dl
Kod8GFazaVECgYAleV1WBj1YUhknAcgDjcjsq+4tyhqYGISVz2AmMhmyvWURBDCk
2WPEmGsAdy5F+krFrfr2ftOq0xvNwjLf+wwjKCcWbttKlZlayIpo7114CK9GJZss
BV3VMmnuYut9OZ15afE7wBrwcdLf6J6xDByotcOouf4rqDK+bwWEkJEBwQKBgQDN
4OIhDq5puDT+b5fhhYBRkw/gVkhQSEtgigoyjb7FGCIoVlvGkHAVZ616oS9Pvfk4
EkzLqnOaocL8F+2GfcblBnARE7lrlMPP+EdsYGiGqp7+tnGtwO6BNYC+ZjMKKg46
w3tYbNw6RwzgC+f7UCLUfpBaMfnnS0zRBRfi+OxEcQKBgEMEes7DT5sqoQkam9lk
AmP8NK+eAoB7RWk8A1ADBlz48xmIH/lR99su9bWWd0xthYuBvx3ZpPRTqp0Z2ehm
7w3jnw+A7BZn1/gmcXLCXexQl+tn0nfm87xpwXCDmHjZzdldzLMpjOMHZDmOcufN
y30Rsmt3vdeo5Rv+whSSypnq
-----END PRIVATE KEY-----
Connecting to the VPN;
openvpn client-1.ovpn
Tue Nov 9 00:02:52 2021 OpenVPN 2.4.11 x86_64-redhat-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Apr 21 2021
Tue Nov 9 00:02:52 2021 library versions: OpenSSL 1.1.1g FIPS 21 Apr 2020, LZO 2.08
Tue Nov 9 00:02:52 2021 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Tue Nov 9 00:02:52 2021 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Tue Nov 9 00:02:52 2021 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Tue Nov 9 00:02:52 2021 TCP/UDP: Preserving recently used remote address: [AF_INET]192.168.58.22:1194
Tue Nov 9 00:02:52 2021 Socket Buffers: R=[212992->212992] S=[212992->212992]
Tue Nov 9 00:02:52 2021 UDPv4 link local: (not bound)
Tue Nov 9 00:02:52 2021 UDPv4 link remote: [AF_INET]192.168.58.22:1194
Tue Nov 9 00:02:52 2021 TLS: Initial packet from [AF_INET]192.168.58.22:1194, sid=f89234f0 4a96fc1e
Tue Nov 9 00:02:52 2021 VERIFY OK: depth=1, CN=Easy-RSA CA
Tue Nov 9 00:02:52 2021 VERIFY KU OK
Tue Nov 9 00:02:52 2021 Validating certificate extended key usage
Tue Nov 9 00:02:52 2021 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Tue Nov 9 00:02:52 2021 VERIFY EKU OK
Tue Nov 9 00:02:52 2021 VERIFY OK: depth=0, CN=server
Tue Nov 9 00:02:52 2021 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 2048 bit RSA
Tue Nov 9 00:02:52 2021 [server] Peer Connection Initiated with [AF_INET]192.168.58.22:1194
Tue Nov 9 00:02:53 2021 SENT CONTROL [server]: 'PUSH_REQUEST' (status=1)
Tue Nov 9 00:02:53 2021 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1 bypass-dhcp,dhcp-option DNS 192.168.58.22,dhcp-option DNS 8.8.8.8,dhcp-option DOMAIN kifarunix-demo.com,route-gateway 10.8.0.1,topology subnet,ping 10,ping-restart 120,ifconfig 10.8.0.2 255.255.255.0,peer-id 0,cipher AES-256-CBC'
Tue Nov 9 00:02:53 2021 OPTIONS IMPORT: timers and/or timeouts modified
Tue Nov 9 00:02:53 2021 OPTIONS IMPORT: --ifconfig/up options modified
Tue Nov 9 00:02:53 2021 OPTIONS IMPORT: route options modified
Tue Nov 9 00:02:53 2021 OPTIONS IMPORT: route-related options modified
Tue Nov 9 00:02:53 2021 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Tue Nov 9 00:02:53 2021 OPTIONS IMPORT: peer-id set
Tue Nov 9 00:02:53 2021 OPTIONS IMPORT: adjusting link_mtu to 1625
Tue Nov 9 00:02:53 2021 OPTIONS IMPORT: data channel crypto options modified
Tue Nov 9 00:02:53 2021 Outgoing Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key
Tue Nov 9 00:02:53 2021 Outgoing Data Channel: Using 512 bit message hash 'SHA512' for HMAC authentication
Tue Nov 9 00:02:53 2021 Incoming Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key
Tue Nov 9 00:02:53 2021 Incoming Data Channel: Using 512 bit message hash 'SHA512' for HMAC authentication
Tue Nov 9 00:02:53 2021 ROUTE_GATEWAY 10.0.2.2/255.255.255.0 IFACE=enp0s3 HWADDR=08:00:27:3e:fe:0e
Tue Nov 9 00:02:53 2021 TUN/TAP device tun0 opened
Tue Nov 9 00:02:53 2021 TUN/TAP TX queue length set to 100
Tue Nov 9 00:02:53 2021 /sbin/ip link set dev tun0 up mtu 1500
Tue Nov 9 00:02:53 2021 /sbin/ip addr add dev tun0 10.8.0.2/24 broadcast 10.8.0.255
Tue Nov 9 00:02:53 2021 /etc/openvpn/scripts/update-systemd-resolved tun0 1500 1605 10.8.0.2 255.255.255.0 init
<14>Nov 9 00:02:53 update-systemd-resolved: Link 'tun0' coming up
<14>Nov 9 00:02:53 update-systemd-resolved: Adding IPv4 DNS Server 192.168.58.22
<14>Nov 9 00:02:53 update-systemd-resolved: Adding IPv4 DNS Server 8.8.8.8
<14>Nov 9 00:02:53 update-systemd-resolved: Adding DNS Domain kifarunix-demo.com
<14>Nov 9 00:02:53 update-systemd-resolved: SetLinkDNS(22 2 2 4 192 168 58 22 2 4 8 8 8 8)
<14>Nov 9 00:02:53 update-systemd-resolved: SetLinkDomains(22 1 kifarunix-demo.com false)
Tue Nov 9 00:02:53 2021 /sbin/ip route add 192.168.58.22/32 via 10.0.2.2
Tue Nov 9 00:02:53 2021 /sbin/ip route add 0.0.0.0/1 via 10.8.0.1
Tue Nov 9 00:02:53 2021 /sbin/ip route add 128.0.0.0/1 via 10.8.0.1
Tue Nov 9 00:02:53 2021 Initialization Sequence Completed
Your local DNS should now be working when connected to VPN.
Read more about DNS leakage.
Other Tutorials
Make Permanent DNS Changes on resolv.conf in Linux
Easily Install and Setup PowerDNS Admin on Ubuntu 20.04
OpenVPN – это набор open source программ, который заслуженно является одним из самых популярных и легких решений для реализации защищенной VPN сети. OpenVPN позволяет объединить в единую сеть сервер и клиентов (даже находящиеся за NAT или файерволами), или объединить сети удаленных офисов. Серверную часть OpenVPN можно развернуть практически на всех доступных операционных системах (пример настройки OpenVPN на Linux). Вы можете установить OpenVPN сервер даже на обычный компьютер с десктопной редакцией Windows 10.
В этой статье, мы покажем, как установить OpenVPN сервер на компьютер с Windows 10, настроить OpenVPN клиент на другом Windows хосте и установить защищенное VPN подключение.
Содержание:
- Установка службы OpenVPN сервера в Windows
- Создаем ключи шифрования и сертификаты для OpenVPN
- Конфигурационный файл OpenVPN сервера в Windows
- Настройка OpenVPN клиента в Windows
Установка службы OpenVPN сервера в Windows
Скачайте MSI установщик OpenVPN для вашей версии Windows с официального сайта (https://openvpn.net/community-downloads/). В нашем случае это OpenVPN-2.5.5-I602-amd64.msi (https://swupdate.openvpn.org/community/releases/OpenVPN-2.5.5-I602-amd64.msi).
Запустите установку.
Если вы планируете, OpenVPN сервер работал в автоматическом режиме, можно не устанавливать OpenVPN GUI. Обязательно установите OpenVPN Services.
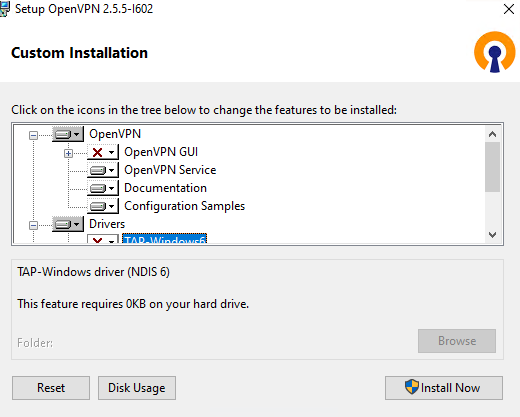
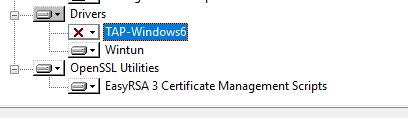
Начиная с версии OpenVPN 2.5, поддерживается драйвер WinTun от разработчиков WireGuard. Считается, что этот драйвер работает быстрее чем классический OpenVPN драйвер TAP. Установите драйвер Wintun, откажитесь от установки TAP-Windows6.
Установите OpenSSL утилиту EasyRSA Certificate Management Scripts.
Запустите установку.
По умолчанию OpenVPN устаналивается в каталог C:\Program Files\OpenVPN.
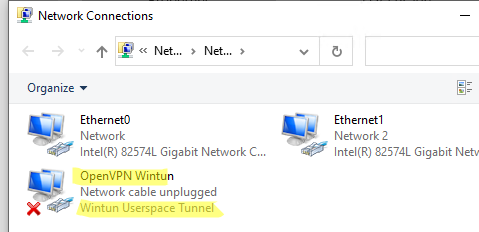
После окончания установки появится новый сетевой адаптер типа Wintun Userspace Tunnel. Этот адаптер отключен, если служба OpenVPN не запущена.
Создаем ключи шифрования и сертификаты для OpenVPN
OpenVPN основан на шифровании OpenSSL. Это означает, что для обмена трафиком между клиентом и серверов VPN нужно сгенерировать ключи и сертификаты с использованием RSA3.
Откройте командную строку и перейдите в каталог easy-rsa:
cd C:\Program Files\OpenVPN\easy-rsa
Создайте копию файла:
copy vars.example vars
Откройте файл vars с помощью любого текстового редактора. Проверьте пути к рабочим директориям.
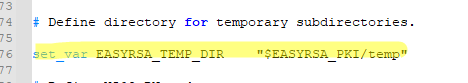
Обязательно поправьте переменную EASYRSA_TEMP_DIR следующим образом:
set_var EASYRSA_TEMP_DIR "$EASYRSA_PKI/temp"
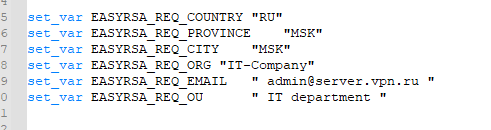
Можете заполнить поля для сертификатов (опционально)
set_var EASYRSA_REQ_COUNTRY "RU" set_var EASYRSA_REQ_PROVINCE "MSK" set_var EASYRSA_REQ_CITY "MSK" set_var EASYRSA_REQ_ORG "IT-Company" set_var EASYRSA_REQ_EMAIL " [email protected] " set_var EASYRSA_REQ_OU " IT department "
Срок действия сертификатов задается с помощью:
#set_var EASYRSA_CA_EXPIRE 3650 #set_var EASYRSA_CERT_EXPIRE 825
Сохраните файл и выполните команду:
EasyRSA-Start.bat
Следующие команды выполняются в среде EasyRSA Shell:
Инициализация PKI:
./easyrsa init-pki
Должна появится надпись:
init-pki complete; you may now create a CA or requests. Your newly created PKI dir is: C:/Program Files/OpenVPN/easy-rsa/pki
Теперь нужно сгенерировать корневой CA:
./easyrsa build-ca
Задайте дважды пароль для CA:
CA creation complete and you may now import and sign cert requests.
Данная команда сформировала:
- Корневой сертификат центра сертификации: «C:\Program Files\OpenVPN\easy-rsa\pki\ca.crt»
- Ключ центра сертификации «C:\Program Files\OpenVPN\easy-rsa\pki\private\ca.key»
Теперь нужно сгенерировать запрос сертификата и ключ для вашего сервера OpenVPN:
./easyrsa gen-req server nopass
Утилита сгенерирует два файла:
req: C:/Program Files/OpenVPN/easy-rsa/pki/reqs/server.req key: C:/Program Files/OpenVPN/easy-rsa/pki/private/server.key
Подпишем запрос на выпуск сертификата сервера с помощью нашего CA:
./easyrsa sign-req server server
Подтвердите правильность данных, набрав yes.
Затем введите пароль CA от корневого CA.
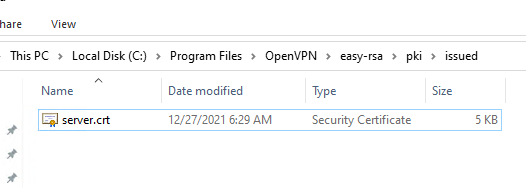
В каталоге issued появится сертификат сервера («C:\Program Files\OpenVPN\easy-rsa\pki\issued\server.crt»)
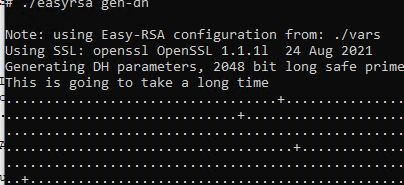
Теперь можно создать ключи Диффи-Хеллмана (займет длительное время):
./easyrsa gen-dh
Для дополнительной защиты VPN сервера желательно включить tls-auth. Данная технология позволяет использовать подписи HMAC к handshake-пакетам SSL/TLS, инициируя дополнительную проверку целостности. Пакеты без такой подписи будут отбрасываться VPN сервером. Это защитит вас от сканирования порта VPN сервера, DoS атак, переполнения буфера SSL/TLS.
Сгенерируйте ключ tls-auth:
cd C:\Program Files\OpenVPN\bin
openvpn --genkey secret ta.key
Должен появиться файл «C:\Program Files\OpenVPN\bin\ta.key». Переместите его в каталог C:\Program Files\OpenVPN\easy-rsa\pki
Теперь можно сформировать ключи для клиентов OpenVPN. Для каждого клиента, который будет подключаться к вашему серверу нужно создать собственные ключи.
Есть несколько способов генерации ключей и передачи их клиентам. В следующем примере, мы создадим на сервере ключ клиента и защитим его паролем:
./easyrsa gen-req kbuldogov
./easyrsa sign-req client kbuldogov
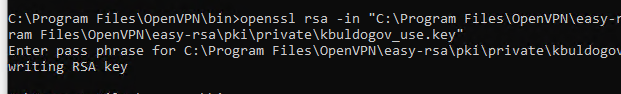
Данный ключ («C:\Program Files\OpenVPN\easy-rsa\pki\private\kbuldogov.key») нужно передать клиенту и сообщить пароль. Клиент может снять защиту паролем для ключа:
openssl rsa -in "C:\Program Files\OpenVPN\easy-rsa\pki\private\kbuldogov.key"-out "C:\Program Files\OpenVPN\easy-rsa\pki\private\kbuldogov_use.key"
Если вы хотите сгенерировать ключ, не защищенный паролем, нужно выполнить команду:
./easyrsa gen-req имяклиента nopass
На сервере с OpenVPN вы можете создать неограниченное количество ключей и сертификатов для пользователей. Аналогичным образом сформируйте ключи и сертфикаты для других клиентов.
Вы можете отохвать скомпрометированные сертификаты клиентов:
cd C:\Program Files\OpenVPN\easy-rsa
EasyRSA-Start.bat
./easyrsa revoke kbuldogov
Итак, мы сгенерировали набор ключей и сертификатов для OpenVPN сервера. Теперь можно настроить и запустить службу OpenVPN.
Конфигурационный файл OpenVPN сервера в Windows
Скопируйте типовой конфигурационный файл OpenVPN сервера:
copy "C:\Program Files\OpenVPN\sample-config\server.ovpn" "C:\Program Files\OpenVPN\config-auto\server.ovpn"
Откройте файл server.ovpn в любом текстовом редакторе и внесите свои настройки. Я использую следующий конфиг для OpenVPN:
# Указываем порт, протокол и устройство port 1194 proto udp dev tun # Указываем пути к сертификатам сервера ca "C:\\Program Files\\OpenVPN\\easy-rsa\\pki\\ca.crt" cert "C:\\Program Files\\OpenVPN\\easy-rsa\\pki\\issued\\server.crt" key "C:\\Program Files\\OpenVPN\\easy-rsa\\pki\\private\\server.key" dh "C:\\Program Files\\OpenVPN\\easy-rsa\\pki\\dh.pem" # Указываем настройки IP сети, адреса из которой будет будут получать VPN клиенты server 10.24.1.0 255.255.255.0 #если нужно разрешить клиентам подключаться под одним ключом, нужвно включить опцию duplicate-cn (не рекомендуется) #duplicate-cn # TLS защита tls-auth "C:\\Program Files\\OpenVPN\\easy-rsa\\pki\\ta.key" 0 cipher AES-256-GCM # Другая параметры keepalive 20 60 persist-key persist-tun status "C:\\Program Files\\OpenVPN\\log\\status.log" log "C:\\Program Files\\OpenVPN\\log\\openvpn.log" verb 3 mute 20 windows-driver wintun
Сохраните файл.
OpenVPN позволяет использовать как TCP, так и UDP для подключения. В этом примере я запустил OpenVPN на 1194 UDP. Рекомендуется использовать протокол UDP, это оптимально как с точки зрения производительности, так и безопасности.
Не забудьте открыть на файерволе порты для указанного вами порта OpenVPN на клиенте и на сервере. Можно открыть порты в Windows Defender с помощью PowerShell.
Правило для сервера:
New-NetFirewallRule -DisplayName "AllowOpenVPN-In" -Direction Inbound -Protocol UDP –LocalPort 1194 -Action Allow
Правило для клиента:
New-NetFirewallRule -DisplayName "AllowOpenVPN-Out" -Direction Outbound -Protocol UDP –LocalPort 1194 -Action Allow
Теперь нужно запустить службу OpenVPN и изменить тип ее запуска на автоматический. Воспользуйтесь таким командами PowerShell, чтобы включить службу:
Set-Service OpenVPNService –startuptype automatic –passthru
Get-Service OpenVPNService| Start-Service
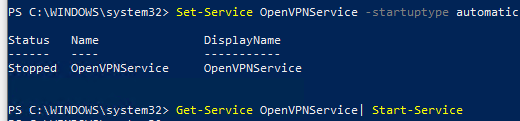
Откройте панель управления, и убедитесь, что виртуальный сетевой адаптер OpenVPN Wintun теперь активен. Если нет, смотрите лог «C:\Program Files\OpenVPN\log\server.log»
Если при запуске OpenVPN вы видите в логе ошибку:
Options error: In C:\Program Files\OpenVPN\config-auto\server.ovpn:1: Maximum option line length (256) exceeded, line starts with..
Смените в файле server.ovpn символы переноса строки на Windows CRLF (в notepad++ нужно выбрать Edit -> EOL Conversion -> Windows CR LF). Сохраните файл, перезапустите службу OpevVPNService.
Данный конфиг позволит удаленным клиентам получить доступ только к серверу, но другие компьютеры и сервисы в локальной сети сервера для них недоступны. Чтобы разрешить клиентам OpenVPN получить доступ к внутренней сети нужно:
Включить опцию IPEnableRouter в реестре (включает IP маршрутизацию в Windows, в том числе включает маршрутизацию меду сетями Hyper-V): reg add «HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters» /v IPEnableRouter /t REG_DWORD /d 1 /f
Добавьте в конфгурационный файл сервера OpenVPN маршруты до внутренней IP сети:
push "route 10.24.1.0 255.255.255.0" push "route 192.168.100.0 255.255.255.0"
Если нужно, назначьте клиенту адреса DNS серверов:
push "dhcp-option DNS 192.168.100.11" push "dhcp-option DNS 192.168.100.12"
Если нужно завернуть все запросы клиента (в том числе Интернет трафик) на ваш OpenVPN сервер, добавьте опцию:
push "redirect-gateway def1"
Настройка OpenVPN клиента в Windows
Создайте на сервере шаблонный конфигурационный файла для клиента VPN (на базе iшаблона client.ovpn) со следующими параметрами (имя файла kbuldovov.ovpn)
client dev tun proto udp remote your_vpn_server_address 1194 resolv-retry infinite nobind persist-key persist-tun ca ca.crt cert kbuldogov.crt key kbuldogov.key remote-cert-tls server tls-auth ta.key 1 cipher AES-256-GCM connect-retry-max 25 verb 3
В директиве remote указывается публичный IP адрес или DNS имя вашего сервера OpenVPN.
Скачайте и установите клиент OpenVPN Connect для Windows (https://openvpn.net/downloads/openvpn-connect-v3-windows.msi).
Теперь на компьютер с клиентом OpenVPN нужно с сервера скопировать файлы:
- ca.crt
- kbuldogov.crt
- kbuldogov.key
- dh.pem
- ta.key
- kbuldogov.ovpn
Теперь импортируйте файл с профилем *.ovpn и попробуйте подключиться к вашему VPN серверу.
Если все настроено правильно, появится такая картинка.
Проверьте теперь лог OpenVPN на клиенте «C:\Program Files\OpenVPN Connect\agent.log»
Mon Dec 27 08:09:30 2021 proxy_auto_config_url
Mon Dec 27 08:09:31 2021 TUN SETUP
TAP ADAPTERS:
guid='{25EE4A55-BE90-45A0-88A1-8FA8FEF24C42}' index=22 name='Local Area Connection'
Open TAP device "Local Area Connection" PATH="\\.\Global\{25EE4A55-BE90-45A0-88A1-8FA8FEF24C42}.tap" SUCCEEDED
TAP-Windows Driver Version 9.24
ActionDeleteAllRoutesOnInterface iface_index=22
netsh interface ip set interface 22 metric=1
Ok.
netsh interface ip set address 22 static 10.24.1.6 255.255.255.252 gateway=10.24.1.5 store=active
IPHelper: add route 10.24.1.1/32 22 10.24.1.5 metric=-1
Клиент успешно подключится к OpenVPN серверу и получил IP адрес 10.24.1.6.
Проверьте теперь лог на сервере («C:\Program Files\OpenVPN\log\openvpn.log»). Здесь также видно, что клиент с сертификатом kbuldogov успешно подключится к вашему серверу.
2021-12-27 08:09:35 192.168.13.202:55648 [kbuldogov] Peer Connection Initiated with [AF_INET6]::ffff:192.168.13.202:55648 2021-12-27 08:09:35 kbuldogov/192.168.13.202:55648 MULTI_sva: pool returned IPv4=10.24.1.6, IPv6=(Not enabled) 2021-12-27 08:09:35 kbuldogov/192.168.13.202:55648 MULTI: Learn: 10.24.1.6 -> kbuldogov/192.168.13.202:55648 2021-12-27 08:09:35 kbuldogov/192.168.13.202:55648 MULTI: primary virtual IP for kbuldogov/192.168.13.202:55648: 10.24.1.6
################################################
#### Dynamic DNS from website http://www.no-ip.com/
################################################
# First, create an account over at http://www.no-ip.com/ then goto
# https://www.no-ip.com/members/dns/ and click “add a host”.
# Then use this lazy command list for pi.
sudo bash
cd /usr/local/src/
wget http://www.no-ip.com/client/linux/noip-duc-linux.tar.gz
tar xf noip-duc-linux.tar.gz
cd noip-2.1.9-1/
make install
# Add a new text line /usr/local/bin/noip2 into file /etc/rc.local
# just before its last line “exit 0″ so no-ip starts automatically after reboot
nano /etc/rc.local
/usr/local/bin/noip2
#CTRL+o ENTER # write output, save in other words
#CTRL+x # exit nano editor
# start it with
sudo /usr/local/bin/noip2
# check status with
sudo /usr/local/bin/noip2 -S
# kill it
sudo /usr/local/bin/noip2 -K ‘pid’ (get pid from -S)
# If you need to recreate the default config file
sudo /usr/local/bin/noip2 -C
################################################
#### Openvpn server and client from website http://openvpn.net
################################################
# Openvpn Based upon these blogs
http://wingloon.com/2012/05/25/how-to-i … ntication/
http://www.serverubuntu.it/openvpn-bridge-configuration
# Using SD card with “2012-08-08-wheezy-armel”
# Remember you gotta do port forwarding, not covered in this post
# Lets get started, start with an updated installation
sudo apt-get update
# Now install openvpn
sudo apt-get install openvpn -y
sudo mkdir /etc/openvpn/easy-rsa/
sudo cp -r /usr/share/doc/openvpn/examples/easy-rsa/2.0/* /etc/openvpn/easy-rsa/
sudo chown -R $USER /etc/openvpn/easy-rsa/
# You can put whatever you like in the vars file, just don’t leave these data fields blank
# I left everything as it was default, even “changeme” data
nano /etc/openvpn/easy-rsa/vars
# Now build certs and keys for server and client
# TIP: answer yes to sign and commit, leave everything else default
cd /etc/openvpn/easy-rsa/
source vars
./clean-all
./build-ca
./build-key-server server
./build-dh
./build-key clientpi
cd /etc/openvpn/easy-rsa/keys
sudo cp ca.crt ca.key dh1024.pem server.crt server.key /etc/openvpn
sudo mkdir $HOME/openvpn-client-files
sudo cp ca.crt clientpi.crt clientpi.key $HOME/openvpn-client-files
sudo mv $HOME/openvpn-client-files/ca.crt $HOME/openvpn-client-files/capi.crt
sudo chmod +r $HOME/openvpn-client-files/clientpi.key
# Now, copy the $HOME/openvpn-client-files directory using WinSCP to client Windows system:
# tip, I had to copy directory to C:\
# then directory contents clientpi.key, capi.crt clientpi.crt to
# C:\Program Files (x86)\OpenVPN\config
# windows 32bit will have a different OpenVPN directory
# C:\Program Files\OpenVPN\config
# in Windows, create a new text file called
# C:\Program Files (x86)\OpenVPN\config\raspberry.ovpn
# this is the OpenVPN client configuration
- CODE: SELECT ALL
client
dev tun
proto tcp
remote change_this_to_your_to_own_address_from_no-ip.com 34567
resolv-retry infinite
nobind
persist-key
persist-tun
ca capi.crt
cert clientpi.crt
key clientpi.key
ns-cert-type server
cipher AES-256-CBC
comp-lzo
verb 3
# Back to the Raspberry Pi, create new file for server config
# Below is my OpenVPN server configuration saved as /etc/openvpn/server.conf
sudo nano /etc/openvpn/server.conf
- CODE: SELECT ALL
port 34567
proto tcp
dev tun
ca ca.crt
cert server.crt
key server.key
dh dh1024.pem
server 10.8.0.0 255.255.255.0
cipher AES-256-CBC
comp-lzo
persist-key
persist-tun
status openvpn-status.log
verb 3
tun-mtu 1500
tun-mtu-extra 32
mssfix 1450
push "redirect-gateway def1"
push "dhcp-option DNS 208.67.222.222"
push "dhcp-option DNS 208.67.220.220"
keepalive 5 30
# Nano editor TIP: CTRL+o writeout, in other words save the file
# CTRL+x exit
# uncomment to allow data redirect
sudo nano /etc/sysctl.conf
net.ipv4.ip_forward=1
# Make file for firewall setting
sudo nano /usr/local/bin/firewall.sh
- CODE: SELECT ALL
#!/bin/bash
iptables -t filter -F
iptables -t nat -F
iptables -A FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD -s "10.8.0.0/24" -j ACCEPT
iptables -A FORWARD -j REJECT
iptables -t nat -A POSTROUTING -s "10.8.0.0/24" -j MASQUERADE
sudo chmod +x /usr/local/bin/firewall.sh
# run firewall
sudo /usr/local/bin/firewall.sh
# TIP: I got an error here
# /bin/bash^M: bad interpreter: No such file or directory
# seems to copy from wordpress adds hidden DOS CTRL characters
# I had to do
sudo apt-get install dos2unix
# then
sudo dos2unix /usr/local/bin/firewall.sh
sudo /usr/local/bin/firewall.sh
# check firewall
- CODE: SELECT ALL
sudo iptables --list
# put a line /usr/local/bin/firewall.sh into /etc/rc.local
# before ‘exit 0′ to ensure the iptables rules is created every reboot or power up.
sudo nano /etc/rc.local
/usr/local/bin/firewall.sh
# reboot the pi
sudo reboot
# connect VPN client from remote location
# did not work for me when client and server where connected
# to same router
# check VPN is working by checking your IP address
# changes after you connect http://ipchicken.com/
OpenVPN is a great tool to allow remote access of your network and I’ve been using it on and off for years. For longer than I care to admit I’ve been trying to solve a particularly pesky problem by which I’ve been unable to access local resources (other computers on my LAN) by their hostname. I could always access these resources by their IP addresses but using this system was cumbersome as I’d have to remember their IP addresses (instead of their easier to recall hostnames) and services that were setup to access resources by hostname (such as mapped network drives) wouldn’t work. In this article I’ll describe the parts of my network setup that are relevant and the procedure I implemented to allow an OpenVPN client to be able to access machines on the LAN by their hostnames.
This solution applies to a Linux based OpenVPN server and Linux based client.
Contents
- 1 Straight to the Solution
- 1.1 Server Mod
- 1.2 Client Mod
- 2 More Detailed Explanation
- 2.1 Router Setup
- 2.2 OpenVPN Server Setup
- 2.3 OpenVPN Client Setup
- 3 References
Straight to the Solution
Here’s the solution up front. Check out the rest of the article for more details on my setup.
The problem boils down to the fact that, by default, the client’s resolv.conf file doesn’t contain a line to point the client to the VPN’s DNS server nor does it contain a line telling the client what your local domain name is. Getting these two lines added (and removed) from resolv.conf automatically is the goal.
Server Mod
- Ensure the following two lines are in your server.conf (typically at /etc/openvpn/server.conf). This tells the client that they should use 192.168.1.1 as the DNS server (typically your router’s IP) and mylocaldomain.lan as a domain to sort of «automatically» append to hostnames that are requested.
push "dhcp-option DNS 192.168.1.1" push "dhcp-option DOMAIN mylocaldomain.lan"
Client Mod
- Install the resolvconf package to give your OpenVPN client the ability to rebuild the resolv.conf file when you start and stop your VPN connection; backup/remove your existing resolv.conf file; and create a symlink to resolvconf’s resolv.conf file. This can all be done by running the following
sudo apt install resolvconf sudo mv /etc/resolv.conf /etc/resolv.conf.orig sudo ln -s /run/resolvconf/resolv.conf /etc/resolv.conf
- Add the following 2 lines to your client.ovpn file to run update-resolv-conf every time you connect to or disconnect from your VPN server
up /etc/openvpn/update-resolv-conf down /etc/openvpn/update-resolv-conf
- Run the openvpn command with —script-security 2 flag to allow update-resolv-conf to be run as in the following example
sudo openvpn --script-security 2 --config /path/to/client.ovpn
More Detailed Explanation
Router Setup
My TP-Link TL-WDR3600 router is setup as a DNS Server and DHCP Server.
- My router is loaded with DD-WRT Firmware v24-sp2 (03/25/13) std
- Setup -> Network Address Server Settings (DHCP) -> Use DNSMasq for DNS is checked
- Services -> Services -> LAN Domain is set to mylocaldomain.lan
- Static IP addresses for LAN resources (computers) are assigned at Services -> Services -> DHCP Server -> Static Leases
OpenVPN Server Setup
- My OpenVPN is running on an LXC Container hosted on a Proxmox server.
- I setup my OpenVPN server using a script from https://raw.githubusercontent.com/davejm/OpenVPN-install/tcp/openvpn-install.sh
- My server configuration file (/etc/openvpn/server.conf) looks like this
port 1194 proto tcp dev tun ca ca.crt cert server.crt key server.key dh dh.pem user nobody group nogroup topology subnet server 192.168.2.0 255.255.255.0 ifconfig-pool-persist ipp.txt cipher AES-256-CBC auth SHA512 tls-version-min 1.2 tls-cipher TLS-DHE-RSA-WITH-AES-256-GCM-SHA384 push "dhcp-option DNS 192.168.1.1" push "dhcp-option DOMAIN mylocaldomain.lan" push "route 192.168.0.0 255.255.0.0" keepalive 10 120 persist-key persist-tun crl-verify crl.pem tls-server tls-auth tls-auth.key 0 log /var/log/openvpn/openvpn.log status /var/log/openvpn/status.log 20
- Make sure that your OpenVPN IP pool (the server 192.168.2.0 255.255.255.0 line does not conflict with the addresses assigned by your router / DHCP server. In this example all local resources are at 192.168.1.XXX and all OpenVPN clients are at 192.168.2.XXX.
- The line push dhcp-option DNS 192.168.1.1 tells the server to send the address of the local networks DNS server (in this case your router) to the client
- The line push dhcp-option DOMAIN mylocaldomain.lan tells the server to send your local domain to the client as a place for it to search for hostnames that are used by not fully qualified.
OpenVPN Client Setup
As mentioned above, the crux of the problem is that the client’s resolve.conf files doesn’t contain everything it needs. We’ve already modified the server.conf file to tell the server to send the necessary options to the client, but we have to make some changes on the client to ensure these options actually get put where they need to go (in the resolve.conf file)
- resolve.conf is automatically generated, and updated, by the OS. Therefore we can’t really modify it directly or our changes will simply be lost. a package called resolveconf comes to the rescue. Once installed we replace the resolv.conf file (typically located at /etc/resolv.conf with a symlink to resolvconf’s version of the file. This file gets modified by resolvconf which we can take advantage of with OpenVPN. The procedure is to install resolveconf; then move/backup the original resolv.conf file; and create a symlink to resolvconf instance of the resolv.conf file.
sudo apt install resolvconf sudo mv /etc/resolv.conf /etc/resolv.conf.orig sudo ln -s /run/resolvconf/resolv.conf /etc/resolv.conf
- Now that we have setup resolvconf we can use it in the OpenVPN client configuration to take the DNS and DOMAIN information setup in the server’s server.conf and insert them into the client’s resolv.conf. Add the following 2 lines to your client.ovpn file which will run update-resolv-conf each time you start, and stop, OpenVPN.
up /etc/openvpn/update-resolv-conf down /etc/openvpn/update-resolv-conf
- Lastly, in order to allow the OpenVPN to actually call update-resolv-conf we have to tell openvpn that we want to ease off its default security posture a bit. The follow command will allow you to connect to your OpenVPN server in a way that allows update-resolv-conf to run at start & stop.
sudo openvpn --script-security 2 --config /path/to/client.ovpn
References
- http://www.softwarepassion.com/solving-dns-problems-with-openvpn-on-ubuntu-box/
- https://serverfault.com/questions/318563/how-to-push-my-own-dns-server-to-openvpn
