OpenVPN GUI
Installation Instructions for OpenVPN GUI for Windows
OpenVPN-GUI has been bundled with OpenVPN installers for a long time, so there
is rarely a need to install it separately. Bleeding-edge
versions of OpenVPN-GUI are available in OpenVPN snapshot
installers based on Git master
branch. OpenVPN-GUI gets installed by default in all OpenVPN installers.
Installation using the official OpenVPN installers
- Download an OpenVPN installer
- If you have a previous version of OpenVPN GUI running, shut it down.
Make sure it’s closed by ALL logged on users. - Run the OpenVPN installer
Manual installation of OpenVPN GUI
- First install OpenVPN using an official installer as described above.
- Build your own version of OpenVPN GUI from source. See BUILD.rst
for build instructions. From the build tree copy openvpn-gui.exe,
libopenvpn_plap.dll, openvpn-plap-install.reg and openvpn-plap-uninstall.reg
to OpenVPN’s bin folder.
Default is C:\Program Files\OpenVPN\bin\. You must put it in this folder
because OpenVPN GUI depends on the OpenSSL DLLs installed in this folder by
OpenVPN.
Configuring OpenVPN GUI to start on Windows logon
OpenVPN GUI can be configured to start automatically on logon to Windows from
its setting menu. This is default behavior for all users if OpenVPN GUI was
installed by an OpenVPN 2.4 installer using default installer options.
Adding an OpenVPN configuration file
To launch a VPN connections using OpenVPN GUI you need to add an OpenVPN
configuration file with .ovpn suffix. Any text editor (e.g. notepad.exe) can be
used to create a OpenVPN configuration files. Note that log and log-append
options are ignored as OpenVPN GUI redirects the normal output to a log file
itself. There are sample config files in the sample-config folder. Please
refer to the OpenVPN How To for more
information regarding creating the configuration file.
Once the configuration file is ready, you need to let OpenVPN GUI know about it.
There are three ways to do this:
- Place the file into the system-wide location, usually
C:\Program Files\OpenVPN\config\, or any of its immediate
subdirectories. This VPN connection will be visible for all users of the
system. - Place the file into C:\Users\username\OpenVPN\config\, or any of its
immediate subdirectories. The configuration file is only visible for the
user in question. If the user is not a member of the built-in «Administrators»
group or «OpenVPN Administrators» group and tries to launch such a connection,
OpenVPN GUI pops up a UAC, offering to create the latter group (if missing)
and to add the user to it. This will only work if admin-level credentials are
available. - Use the «Import file» function in OpenVPN GUI itself
- See the section on Persistent or Pre-started connections
for how to use OpenVPN GUI to conftrol configurations in
C:\Program Files\OpenVPN\config-auto\ that are started by the automatic service.
Using OpenVPN GUI
When OpenVPN GUI is started your OpenVPN config folders
(C:\Users\username\OpenVPN\config and
C:\Program Files\OpenVPN\config) will be scanned for .ovpn files and the
OpenVPN GUI icon will appear in the system tray. Each OpenVPN configuration
file shows up as a separate menu item in the OpenVPN GUI tray, allowing you to
selectively connect to and disconnect to your VPNs. The config dir will be
re-scanned for new config files every time you open the OpenVPN GUI menu by
right-clicking the icon.
When you choose to connect to a site OpenVPN GUI will launch openvpn with
the specified config file. If you use a passphrase protected key you will be
prompted for the passphrase.
If you want OpenVPN GUI to start a connection automatically when it’s started,
you can use the —connect cmd-line option. The extension of the config file
may be optionally included. Example:
openvpn-gui --connect office.ovpn OR openvpn-gui --connect office
Starting version 11.34, any connections active when OpenVPN GUI exits or the user
logs out are automatically reconnected when OpenVPN GUI is restarted.
To get help with OpenVPN GUI please use one of the official OpenVPN support
channels.
Running OpenVPN GUI
Run OpenVPN-GUI as normal user by double clicking on the icon. No
administrative privileges or runas-administrator options are required.
It just works as limited user with the help of Interactive Service which
is enabled by default.
Persistent or Pre-started connections
Starting release 2.5.8 (GUI version 11.30), OpenVPN GUI can
control connections started by the «automatic service»
(OpenVPNService) — also referred to as persistent connections.
OpenVPNService, if running, starts all connection profiles
listed in the config-auto directory in the installation path.
By default, such connections are scanned for, and attempt is
made to attach to their management interfaces if available.
User can then view the status of these connections, and disconnect,
reconnect, detach or re-attach them using the menu items.
It requires that such connections be started with
—management 127.0.0.1 port [pw-file] option in their config file.
pw-file containing a password is optional, but highly recommended.
The password should be a single line of text, preferably shorter than 128
characters of plain ascii.
Further, if —auth-user-pass or any such options requiring
interactive user input are present, the config file must also
contain —management-query-passwords.
This feature may be controlled by changing the Persistent Connections
setting in the General tab of the Settings menu: choose auto
for the default behaviour described above, manual to enumerate
and list such connections but not auto-attach, or disable to not scan
auto-started connection profiles.
Interactively starting connections before logon
Starting release 2.6 (GUI version 11.30), «Start Before Logon»
aka Pre-Logon Access Provider is supported. This feature is not
enabled by default. It may be enabled during installation or
through the General Settings menu of the GUI via the
Start Before Logon check mark.
Only persistent connection profiles described in the previous
section will be listed on the login screen. Ensure that
connections that may be interactively started from login
screen are setup in the config-auto folder, OpenVPNService
is running, and these connections are visible and controllable
from the GUI.
In addition to that, PLAP profiles must contain:
setenv IV_SSO webauth
to indicate that client supports web-based (as QR code for PLAP)
authentication method.
Once those pre-requisites are satisfied, the login screen will
display an icon for Pre-Logon Access Providers, clicking which
will bring up a list of OpenVPN connection profiles available, and
allow connecting or disconnecting them interactively.
Run Connect/Disconnect/Preconnect Scripts
There are three different scripts that OpenVPN GUI can execute to help
with different tasks like mapping network drives.
- Preconnect If a file named «xxx_pre.bat» exist in the config folder
- where xxx is the same as your OpenVPN config file name,
this will be executed BEFORE the OpenVPN tunnel is established. - Connect If a file named «xxx_up.bat» exist in the config folder
- where xxx is the same as your OpenVPN config file name,
this will be executed AFTER the OpenVPN tunnel is established. - Disconnect If a file named «xxx_down.bat» exist in the config folder
- where xxx is the same as your OpenVPN config file name,
this will be executed BEFORE the OpenVPN tunnel is closed.
The outputs of these scripts are redirected to «xxx_pre.log»,
«xxx_up.log» and «xxx_down.log» respectively. These log
files are created in the log_dir and over-written during
each evocation.
Send Commands to a Running Instance of OpenVPN GUI
When an instance of the GUI is running, certain commands may be sent to
it using the command line interface using the following syntax:
openvpn-gui.exe --command *cmd* [*args*]
Currently supported cmds are
- connect
config-name - Connect the configuration named config-name (excluding the
extension .ovpn). If already connected, show the status window. - disconnect
config-name - Disconnect the configuration named config-name if connected.
- reconnect
config-name - Disconnect and then reconnect the configuration named config-name
if connected. - disconnect_all
- Disconnect all active connections.
- silent_connection 0 | 1
- Set the silent connection flag on (1) or off (0)
- exit
- Disconnect all active connections and terminate the GUI process
- rescan
- Rescan the config folders for changes
- import
path - Import the config file pointed to by
path.
If no running instance of the GUI is found, these commands do nothing
except for —command connect config-name which gets interpreted
as —connect config-name
Registry Values affecting the OpenVPN GUI operation
Parameters taken from the global registry values in
HKEY_LOCAL_MACHINE\SOFTWARE\OpenVPN\ key
- (Default)
- The installation directory of openvpn (e.g., C:\Program Files\OpenVPN).
This value must be present. - config_dir
- The global configuration file directory. Defaults to
C:\Program Files\OpenVPN\config - exe_path
- path to openvpn.exe, defaults to C:\Program Files\OpenVPN\bin\openvpn.exe
- priority
-
the windows priority class for each instantiated OpenVPN process,
can be one of:- IDLE_PRIORITY_CLASS
- BELOW_NORMAL_PRIORITY_CLASS
- NORMAL_PRIORITY_CLASS (default)
- ABOVE_NORMAL_PRIORITY_CLASS
- HIGH_PRIORITY_CLASS
- ovpn_admin_group
- The windows group whose membership allows the user to start any configuration file
in their profile (not just those installed by the administrator in the global
config directory). Default: «OpenVPN Administrators». - disable_save_passwords
- Set to a nonzero value to disable the password save feature.
Default: 0 - auto_config_dir
- If persistent connection support is enabled and the so-called automatic
service (OpenVPNService) is running, any config files in this folder are
scanned and listed in the list of connection profiles.
User Preferences
All other OpenVPN GUI registry values are located below the
HKEY_CURRENT_USER\SOFTWARE\OpenVPN-GUI\ key. In a fresh
installation none of these values are present and are not
required for the operation of the program. These keys are only
used for persisting user’s preferences, and the key names
and their values are subject to change.
The user is not expected to edit any of these values directly.
Instead, edit all preferences using the settings menu.
- config_dir
- The user-specific configuration file directory: defaults to
C:\Users\username\OpenVPN\config.
The GUI parses this directory for configuration files before
parsing the global config_dir. - config_ext
- file extension on configuration files, defaults to ovpn
- connectscript_timeout
- Time in seconds to wait for the connect script to finish. If set to 0
the exitcode of the script is not checked. - disconnectscript_timeout
- Time in seconds to wait for the disconnect script to finish. Must be a
value between 1-99. - preconnectscript_timeout
- Time in seconds to wait for the preconnect script to finish. Must be a
value between 1-99. - log_dir
- log file directory, defaults to C:\Users\username\OpenVPN\log
- log_append
- if set to «0», the log file will be truncated every time you start a
connection. If set to «1», the log will be appended to the log file. - silent_connection
- If set to «1», the status window with the OpenVPN log output will
not be shown while connecting. Warnings such as interactive service
not started or multiple config files with same name are also suppressed. - show_balloon
-
0: Never show any connected balloon
1: Show balloon after initial connection is established
2: Show balloon even after re-connects
- config_menu_view
-
0: Use a hierarchical (nested) display of config menu reflecting the directory sturcture of config files if the number of configs exceed 25, else use a flat display
1: Force flat menu
2: Force nested menu
- disable_popup_messages
- If set to 1 echo messages are ignored
- popup_mute_interval
- Amount of time in hours for which repeated echo messages are not displayed.
Defaults to 24 hours. - management_port_offset
- The management interface port is chosen as this offset plus a connection specific index.
Allowed values: 1 to 61000, defaults to 25340.
All of these registry options are also available as cmd-line options.
Use «openvpn-gui —help» for more info about cmd-line options.
Building OpenVPN GUI from source
See BUILD.rst for build instructions.
1. Download OpenVPN
The first thing you need to do to connect to OVPN is to download the correct OpenVPN GUI for your computer.
We recommend to try the 64-bit version first if you are unsure which version you’re using.
If you’re running Windows on a 64-bit system, download this installer.
If you’re running Windows on a 32-bit system, download this installer instead.
If you’re running Windows on a ARM64 system, download this installer.
2. Install OVPN
To begin the installation, double-click the file you downloaded in the previous step. Go through the installation process.
Total infrastructure ownership
All the hardware used to operate OVPN is owned by us. All VPN servers operate without hard drives as the operating system only resides in RAM.
Learn more
3. Download the configuration you want
4. Import configuration file
OpenVPN’s icon should be in the activity tray in the right corner of your screen. You might need to click on the arrow in order to display the icon with the padlock. When you’ve found the icon, right click on it and choose Import file.
5. Connect to OVPN
Go ahead and right click on the OpenVPN icon again. This time, choose to Connect. When prompted, enter the username and password you used when creating your OVPN account.
6. Finished
You should now be connected to OVPN and be able to browse the internet safely. To make sure everything was set up correctly, please check the dashboard to verify that you are connected.
Пошаговая инструкция по настройке OpenVPN GUI в Windows 10. The OpenVPN GUI это бесплатная программа с открытым кодом, доступная для всех версий Windows.
Содержание
- Установка OpenVPN GUI
- Настройка OpenVPN GUI
- Подключение к VPN-серверу
Установка OpenVPN GUI
Зайдите на оффициальный сайт OpenVPN https://openvpn.net/index.php/open-source/downloads.html. Скачайте установочный файл .exe себе на компьютер.
Или скачайте установочный файл для вашей версии Windows по следующим ссылкам:
- Скачать для Windows 7, 8, 8.1
- Скачать для Windows 10

Запустите скачанный установочный файл openvpn-install-2.4.8-I602-Win*.exe.
Windows спросит, «Do you want to allow the following program to make changes to this computer?» Нажмите Yes.
Установщик запущен. Нажмите Next для начала установки!

Далее вы увидите лицензионное солашение. Прочитайте его, если хотите, и нажмите I Agree.

На экране выбора компонентов нажмите Next.

На экране выбора места установки нажмите Install.

Windows спросит: «Would you like to install this device software?» Нажмите Install.
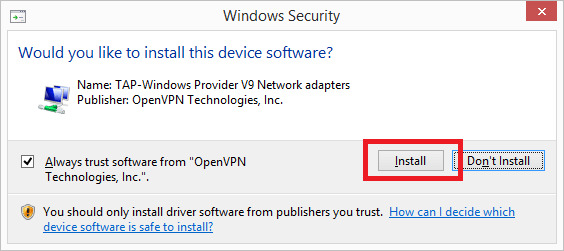
Когда появится экран завершения установки (Installation Complete) нажмите Next.

Далее вы увидите сообщение о том, что OpenVPN успешно установлен. Уберите галочку «Show Readme» и нажмите Finish.

Настройка OpenVPN GUI
В процессе установки, ярлык OpenVPN GUI будет добавлен на рабочий стол Windows. Нажмите правой кнопкой мыши по нему OpenVPN GUI и выберите в меню пункт «Открыть разположение файла».

Откроется папка C:\Program Files\OpenVPN\bin. Вам нужно перейти на уровень выше — C:\Program Files\OpenVPN.

Теперь нужно перейти в папку C:\Program Files\OpenVPN\config.

Теперь нужно перенасти конфигурационный файл OpenVPN в папку C:\Program Files\OpenVPN\config. Перетащите файл SnowdenVPN.ovpn из папки Загрузки, в папку, которая была открыта ранее.

После этого вы увидите предупреждение «Destination Folder Access Denied». Windows попросит вас предоставить права администратора для перемещения файла. Согласитесь.
Отлично! Ваш конфигурационный файл SnowdenVPN.ovpn находится в C:\Program Files\OpenVPN\config и теперь вы можете подключиться к серверу.
Подключение в VPN-серверу
Дважды нажмите мышью на ярлык OpenVPN GUI на рабочем столе.

Когда OpenVPN GUI запустится, на панеле уведомлений появится его значок.
Нажмите правой кнопкой мыши по значку OpenVPN GUI на панеле уведомлений.
В выпадающем меню выбирите пункт Подключиться.

После этого появится окно подключения.

Когда OpenVPN GUI подключится в серверу, значок станет зеленого цвета.

Создать VPN-сервер бесплатно
The OpenVPN community project team is proud to release OpenVPN 2.6.14. This is a bugfix release containing one security fix.
For details see Changes.rst
Security fixes:
- CVE-2025-2704: fix possible
ASSERT()on OpenVPN servers using--tls-crypt-v2Security scope: OpenVPN servers between 2.6.1 and 2.6.13 using--tls-crypt-v2can be made to abort with anASSERT()message by sending a particular combination of authenticated and malformed packets. To trigger the bug, a valid tls-crypt-v2 client key is needed, or network observation of a handshake with a valid tls-crypt-v2 client key. No crypto integrity is violated, no data is leaked, and no remote code execution is possible. This bug does not affect OpenVPN clients. (Bug found by internal QA at OpenVPN Inc)
Windows MSI changes since 2.6.13:
- Built against OpenSSL 3.4.1
- Included openvpn-gui updated to 11.52.0.0
- Use correct
%TEMP%directory for debug log file. - Disable config in menu listing if its ovpn file becomes inaccessible (github openvpn-gui#729)
- Use correct
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.14-I001-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.14-I001-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.14-I001-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.14.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.13. This is a bugfix release.
For details see Changes.rst
Feature changes:
-
on non-windows clients (MacOS, Linux, Unix) send «release» string from
uname()call asIV_PLAT_VERto server — while highly OS specific this is still helpful to keep track of OS versions used on the client side (github #637) -
Windows: protect cached username, password, and token in client memory (using the
CryptProtectMemory()windows API) - Windows: use new API to get dco-win driver version from driver (newly introduced non-exclusive control device) (github ovpn-dco-win#76)
-
Linux: pass
--timeout=0 argumenttosystemd-ask-password, to avoid default timeout of 90 seconds («console prompting also has no timeout») (github #649)
Security fixes:
-
improve server-side handling of clients sending usernames or passwords longer than
USER_PASS_LEN— this would not result in a crash, buffer overflow or other security issues, but the server would then misparse incoming IV variables and produce misleading error messages.
Notable bug fixes:
- FreeBSD DCO: fix memory leaks in nvlist handling (github #636)
-
purge proxy authentication credentials from memory after use (if
--auth-nocacheis in use)
Windows MSI changes since 2.6.12:
- Built against OpenSSL 3.4.0
- Included openvpn-gui updated to 11.51.0.0
- Higher resolution eye icons (github openvpn-gui#697)
- Support for concatenating OTP with password
- Optionally always prompt for OTP
- Fix tooltip positioning when the taskbar is at top (github openvpn-gui#710)
- Debian/Ubuntu packages in OpenvpnSoftwareRepos are now available for Ubuntu 24.10 (oracular)
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.13-I002-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.13-I002-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.13-I002-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.13.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.12. This is a bugfix release.
For details see Changes.rst
Bug fixes:
- the fix for CVE-2024-5594 (refuse control channel messages with nonprintable characters) was too strict, breaking user configurations with AUTH_FAIL messages having trailing CR/NL characters. This often happens if the AUTH_FAIL reason is set by a script. Strip those before testing the command buffer (github #568). Also, add unit test.
- Http-proxy: fix bug preventing proxy credentials caching (trac #1187)
Windows MSI changes since 2.6.11:
- Built against OpenSSL 3.3.1
- Included openvpn-gui updated to 11.50.0.0
- Update Italian language (github #696)
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.12-I001-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.12-I001-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.12-I001-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.12.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.11. This is a bugfix release containing several security fixes.
For details see Changes.rst
Security fixes:
- CVE-2024-4877: Windows: harden interactive service pipe. Security scope: a malicious process with «some» elevated privileges (SeImpersonatePrivilege) could open the pipe a second time, tricking openvn GUI into providing user credentials (tokens), getting full access to the account openvpn-gui.exe runs as. (Zeze with TeamT5)
- CVE-2024-5594: control channel: refuse control channel messages with nonprintable characters in them. Security scope: a malicious openvpn peer can send garbage to openvpn log, or cause high CPU load. (Reynir Björnsson)
- CVE-2024-28882: only call schedule_exit() once (on a given peer). Security scope: an authenticated client can make the server «keep the session» even when the server has been told to disconnect this client (Reynir Björnsson)
New features:
- Windows Crypto-API: Implement Windows CA template match for searching certificates in windows crypto store.
- Support pre-created DCO interface on FreeBSD (OpenVPN would fail to set ifmode p2p/subnet otherwise)
Bug fixes:
- Fix connect timeout when using SOCKS proxies (trac #328, github #267)
- Work around LibreSSL crashing on OpenBSD 7.5 when enumerating ciphers (LibreSSL bug, already fixed upstream, but not backported to OpenBSD 7.5, see also LibreSSL/OpenBSD#150)
- Add bracket in fingerprint message and do not warn about missing verification (github #516)
Documentation:
- Remove «experimental» denotation for —fast-io
- Correctly document ifconfig_* variables passed to scripts
- Documentation: make section levels consistent
- Samples: Update sample configurations (remove compression & old cipher settings, add more informative comments)
Windows MSI changes since 2.6.10:
- For the Windows-specific security fixes see above
- Built against OpenSSL 3.3.1
- Included openvpn-gui updated to 11.49.0.0
- Contains part of the fix for CVE-2024-4877
Note: Windows MSI was updated to I002 on June 26th. Changes in I002:
- Group names are localized in some localizations, so we have to use SIDs. (Github: #671)
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.11-I002-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.11-I002-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.11-I002-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.11.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.10. This is a bugfix release containing several security fixes specific to the Windows platform.
For details see Changes.rst
Security fixes:
- CVE-2024-27459: Windows: fix a possible stack overflow in the interactive service component which might lead to a local privilege escalation. Reported-by: Vladimir Tokarev <vtokarev@microsoft.com>
- CVE-2024-24974: Windows: disallow access to the interactive service pipe from remote computers. Reported-by: Vladimir Tokarev <vtokarev@microsoft.com>
- CVE-2024-27903: Windows: disallow loading of plugins from untrusted installation paths, which could be used to attack
openvpn.exevia a malicious plugin. Plugins can now only be loaded from the OpenVPN install directory, the Windows system directory, and possibly from a directory specified byHKLM\SOFTWARE\OpenVPN\plugin_dir. Reported-by: Vladimir Tokarev <vtokarev@microsoft.com> - CVE-2024-1305: Windows TAP driver: Fix potential integer overflow in TapSharedSendPacket. Reported-by: Vladimir Tokarev <vtokarev@microsoft.com>
New features:
t_client.shcan now run pre-tests and skip a test block if needed (e.g. skip NTLM proxy tests if SSL library does not support MD4)
User visible changes:
- Update copyright notices to 2024
Bug fixes:
- Windows: if the win-dco driver is used (default) and the GUI requests use of a proxy server, the connection would fail. Disable DCO in this case. (Github: #522)
- Compression: minor bugfix in checking option consistency vs. compiled-in algorithm support
- systemd unit files: remove obsolete syslog.target
Documentation:
- remove license warnings about mbedTLS linking (README.mbedtls)
- update documentation references in systemd unit files
- sample config files: remove obsolete tls-*.conf files
- document that auth-user-pass may be inlined
Windows MSI changes since 2.6.9:
- For the Windows-specific security fixes see above
- Built against OpenSSL 3.2.1
- Included tap6-windows driver updated to 9.27.0
- Security fix, see above
- Included ovpn-dco-win driver updated to 1.0.1
- Ensure we don’t pass too large key size to CryptoNG. We do not consider this a security issue since the CryptoNG API handles this gracefully either way.
- Included openvpn-gui updated to 11.48.0.0
- Position tray tooltip above the taskbar
- Combine title and message in tray icon tip text
- Use a custom tooltip window for the tray icon
Note: Windows MSI was updated to I002 on April 15th. Changes in I002:
- Update include ovpn-dco-win to v1.1.1
- Improves reconnect behavior after hibernate/standby. (Github: #64)
Note: Windows MSI was updated to I003 on May 23rd. Changes in I003:
- Update include ovpn-dco-win to v1.2.1
- Fix bug check in timer management routines. (Github: #70)
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.10-I003-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.10-I003-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.10-I003-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.10.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.9. This is a bugfix release containing one security fix for the Windows installer.
For details see Changes.rst
Security fixes:
- Windows Installer: fix CVE-2023-7235 where installing to a non-default directory could lead to a local privilege escalation. Reported by Will Dormann.
New features:
- Add support for building with mbedTLS 3.x.x
- New option
--force-tls-key-material-exportto only accept clients that can do TLS keying material export to generate session keys (mostly an internal option to better deal with TLS 1.0 PRF failures). - Windows: bump vcpkg-ports/pkcs11-helper to 1.30
- Log incoming SSL alerts in easier to understand form and move logging from
--verb 8to--verb 3. - protocol_dump(): add support for printing
--tls-cryptpackets
User visible changes:
- License change is now complete, and all code has been re-licensed under the new license (still GPLv2, but with new linking exception for Apache2 licensed code). See COPYING for details.
Code that could not be re-licensed has been removed or rewritten.
- The original code for the
--tls-export-certfeature has been removed (due to the re-licensing effort) and rewritten without looking at the original code. Feature-compatibility has been tested by other developers, looking at both old and new code and documentation, so there *should* not be a user-visible change here. - IPv6 route addition/deletion are now logged on the same level (3) as for IPv4. Previously IPv6 was always logged at
--verb 1. - Better handling of TLS 1.0 PRF failures in the underlying SSL library (e.g. on some FIPS builds) — this is now reported on startup, and clients before 2.6.0 that can not use TLS EKM to generate key material are rejected by the server. Also, error messages are improved to see what exactly failed.
Notable bug fixes:
- FreeBSD: for servers with multiple clients, reporting of peer traffic statistics would fail due to insufficient buffer space (Github: #487)
Windows MSI changes since 2.6.8:
- Security fix, see above
- Built against OpenSSL 3.2.0
- Included openvpn-gui updated to 11.47.0.0
- Windows GUI: always update tray icon on state change (Github: #669) (for persistent connection profiles, «connecting» state would not show)
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.9-I001-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.9-I001-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.9-I001-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.9.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.8. This is a small bugfix release fixing a few regressions in 2.6.7 release.
For details see Changes.rst
User visible changes:
- Windows: print warning if pushed options require DHCP (e.g. DOMAIN-SEARCH) and driver in use does not use DHCP (wintun, dco).
Bug fixes:
- SIGSEGV crash: Do not check key_state buffers that are in S_UNDEF state (Github #449) — the new sanity check function introduced in 2.6.7 sometimes tried to use a NULL pointer after an unsuccessful TLS handshake
- Windows:
--dnsoption did not work when tap-windows6 driver was used, because internal flag for «apply DNS option to DHCP server» wasn’t set (Github #447) - Windows: fix status/log file permissions, caused by regression after changing to CMake build system (Github: #454, Trac: #1430)
- Windows: fix
--chdirfailures, also caused by error in CMake build system (Github #448)
Windows MSI changes since 2.6.7:
- Included openvpn-gui updated to 11.46.0.0
For Community-maintained packages for Linux distributions see OpenvpnSoftwareRepos
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.8-I001-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.8-I001-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.8-I001-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.8.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.7. This is a bugfix release containing security fixes.
For details see Changes.rst
Security Fixes:
- CVE-2023-46850 OpenVPN versions between 2.6.0 and 2.6.6 incorrectly use a send buffer after it has been free()d in some circumstances, causing some free()d memory to be sent to the peer. All configurations using TLS (e.g. not using —secret) are affected by this issue. (found while tracking down CVE-2023-46849 / Github #400, #417)
- CVE-2023-46849 OpenVPN versions between 2.6.0 and 2.6.6 incorrectly restore
--fragmentconfiguration in some circumstances, leading to a division by zero when--fragmentis used. On platforms where division by zero is fatal, this will cause an OpenVPN crash. (Github #400, #417).
User visible changes:
- DCO: warn if DATA_V1 packets are sent by the other side — this a hard incompatibility between a 2.6.x client connecting to a 2.4.0-2.4.4 server, and the only fix is to use
--disable-dco. - Remove OpenSSL Engine method for loading a key. This had to be removed because the original author did not agree to relicensing the code with the new linking exception added. This was a somewhat obsolete feature anyway as it only worked with OpenSSL 1.x, which is end-of-support.
- add warning if p2p NCP client connects to a p2mp server — this is a combination that used to work without cipher negotiation (pre 2.6 on both ends), but would fail in non-obvious ways with 2.6 to 2.6.
- add warning to
--show-groupsthat not all supported groups are listed (this is due the internal enumeration in OpenSSL being a bit weird, omitting X448 and X25519 curves). --dns: remove support forexclude-domainsargument (this was a new 2.6 option, with no backend support implemented yet on any platform, and it turns out that no platform supported it at all — so remove option again)- warn user if INFO control message too long, do not forward to management client (safeguard against protocol-violating server implementations)
New features:
- DCO-WIN: get and log driver version (for easier debugging).
- print «peer temporary key details» in TLS handshake
- log OpenSSL errors on failure to set certificate, for example if the algorithms used are in acceptable to OpenSSL (misleading message would be printed in cryptoapi / pkcs11 scenarios)
- add CMake build system for MinGW and MSVC builds
- remove old MSVC build system
- improve cmocka unit test building for Windows
Windows MSI changes since 2.6.6:
- Included openvpn-gui updated to 11.45.0.0
- Add clarity for error on missing management parameter. See GH #657
- Improve «OpenVPN GUI» tooltip handling See GH #649
- MSIs now use OpenSSL 3.1.4
For Community-maintained packages for Linux distributions see OpenvpnSoftwareRepos
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.7-I001-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.7-I001-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.7-I001-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.7.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.6. This is a small bugfix release.
For details see Changes.rst
User visible changes:
- OCC exit messages are now logged more visibly See GH #391.
- OpenSSL error messages are now logged with more details (for example, when loading a provider fails, which .so was tried, and why did it fail) See GH #361.
- print a more user-friendly message when tls-crypt-v2 client auth fails
- packaging now includes all documentation in the source tarball
New features:
- set WINS server via interactive service — this adds support for «dhcp-option WINS 192.0.2.1» for DCO + wintun interfaces where no DHCP server is used. See GH #373.
Windows MSI changes since 2.6.5:
- Included openvpn-gui updated to 11.44.0.0
- MSIs now use OpenSSL 3.1.2
For Community-maintained packages for Linux distributions see OpenvpnSoftwareRepos
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.6-I001-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.6-I001-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.6-I001-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.6.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.4. This is a small bugfix release.
For details see Changes.rst
Note:
- License amendment: all new commits fall under a modified license that explicitly permits linking with Apache2 libraries (mbedTLS, OpenSSL) — see COPYING for details. Existing code will fall under the new license as soon as all contributors have agreed to the change — work ongoing.
Feature changes:
- DCO: support kernel-triggered key rotation (avoid IV reuse after 232 packets). This is the userland side, accepting a message from kernel, and initiating a TLS renegotiation. As of 2.6.4 release, only implemented in FreeBSD kernel.
Windows MSI changes since 2.6.3:
- Rebuilt included tap-windows driver with the correct version of the old Windows 7 driver, removing a warning about unsigned driver on Windows 7 installation. See GH openvpn-build#365.
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.4-I001-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.4-I001-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.4-I001-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.4.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.3. This is a small bugfix release.
For details see Changes.rst
Feature changes:
- Windows: support setting DNS domain in configurations without GUI and DHCP (typically wintun or windco drivers), see GH openvpn#306.
Windows MSI changes since 2.6.2:
- Several Windows-specific issues fixed:
- ensure interactive service stays enabled after silent reinstall, see GH openvpn-build#348, openvpn-build#349 and openvpn-build#351
- repair querying install path info for easyrsa-start.bat on some Windows language versions, see GH openvpn-build#352.
- MSIs are now built against OpenSSL 3.1.0.
- Update included openvpn-gui to 11.41.0.0
- This update removes the ability to change the password of a private key from the GUI. This was a niche feature which caused a direct dependency of GUI on OpenSSL. Use openssl.exe directly if you need to edit a private key.
Note: Windows MSI was updated to I003 on April 26th. Changes in I003:
- The GPG subkey for creating the .asc files for the downloads has been updated. You might need to re-download or update the GPG key if verifying the signatures.
- Fix the encoding of some documentation/sample files included in the installer. See GH openvpn-build#358
- Update include tap-windows6 driver to 9.25.0
- Fixes a problem with sending small non-IP packets (e.g. PPPoE) over the VPN connection. See GH tap-windows6#158
- Note: The new driver is only used on Windows 10 and newer. We can’t rebuild drivers for Windows 7/8 since Microsoft doesn’t support the signing mechanism anymore. We include the previous driver version to still allow installation on Windows 7/8.
- Update included openvpn-gui to 11.42.0.0
- Fixes a problem with passphrase prompt was sometimes not displayed. See GH openvpn-gui#619
- Adds «Password Reveal» feature which allows you to see passwords while entering them.
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.3-I003-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.3-I003-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.3-I003-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.3.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.2. This is mostly a bugfix release with some improvements.
For details see Changes.rst
Feature changes:
- implement byte counter statistics for DCO Linux (p2mp server and client)
- implement byte counter statistics for DCO Windows (client only)
--dns server <n> address ...now permits up to 8 v4 or v6 addresses
Important note for Linux DCO users:
- New control packets flow for data channel offloading on Linux: 2.6.2+ changes the way OpenVPN control packets are handled on Linux when DCO is active, fixing the lockups observed with 2.6.0/2.6.1 under high client connect/disconnect activity. This is an INCOMPATIBLE change and therefore an ovpn-dco kernel module older than v0.2.20230323 (commit ID 726fdfe0fa21) will not work anymore and must be upgraded. The kernel module was renamed to «ovpn-dco-v2.ko» in order to highlight this change and ensure that users and userspace software could easily understand which version is loaded. Attempting to use the old ovpn-dco with 2.6.2+ will lead to disabling DCO at runtime.
Windows MSI changes since 2.6.1:
- Update included openvpn-gui to 11.39.0.0
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.2-I001-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.2-I001-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.2-I001-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.2.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.1. This is mostly a bugfix release with some improvements.
For details see Changes.rst
Feature changes:
- Dynamic TLS Crypt: When both peers are OpenVPN 2.6.1+, OpenVPN will dynamically create a tls-crypt key that is used for renegotiation. This ensure that only the previously authenticated peer can do trigger renegotiation and complete renegotiations.
- CryptoAPI (Windows): support issuer name as a selector. Certificate selection string can now specify a partial issuer name string as
«—cryptoapicert ISSUER:<string>» where <string> is matched as a substring of the issuer (CA) name in the certificate.
Note: configure now enables DCO build by default on FreeBSD and Linux. On Linux this brings in a new default dependency for libnl-genl (for Linux distributions that are too old to have a suitable version of the library, use «configure —disable-dco»)
Windows MSI changes since 2.6.1:
- Update included ovpn-dco-win driver to 0.9.2
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.1-I001-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.1-I001-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.1-I001-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.1.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.6.0. This is a new stable release with some major new features.
For details see: Changes.rst
The Changes document also contains a section with workarounds for common problems encountered when using OpenVPN with OpenSSL 3.
New features and improvements in 2.6.0 compared to 2.5.8:
- Data Channel Offload (DCO) kernel acceleration support for Windows, Linux, and FreeBSD.
- OpenSSL 3 support.
- Improved handling of tunnel MTU, including support for pushable MTU.
- Outdated cryptographic algorithms disabled by default, but there are options to override if necessary.
- Reworked TLS handshake, making OpenVPN immune to replay-packet state exhaustion attacks.
- Added —peer-fingerprint mode for a more simplistic certificate setup and verification.
- Added Pre-Logon Access Provider support to OpenVPN GUI for Windows.
- Improved protocol negotiation, leading to faster connection setup.
- Included openvpn-gui updated to 11.37.0.0. See CHANGES.rst.
- Updated easy-rsa3 bundled with the installer on Windows.
- Various bug fixes.
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.0-I005-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.0-I005-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.0-I005-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.6.0.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.5.10. This is a bugfix release containing several security fixes specific to the Windows platform.
For details see Changes.rst
Note that OpenVPN 2.5.x is in «Old Stable Support» status (see SupportedVersions). This usually means that we do not provide updated Windows Installers anymore, even for security fixes. Since this release fixes several issues specific to the Windows platform we decided to provide installers anyway. This does not change the support status of 2.5.x branch. We might not provide security updates for issues found in the future. We recommend that everyone switch to the 2.6.x versions of installers as soon as possible.
Security fixes:
- CVE-2024-27459: Windows: fix a possible stack overflow in the interactive service component which might lead to a local privilege escalation. Reported-by: Vladimir Tokarev <vtokarev@microsoft.com>
- CVE-2024-24974: Windows: disallow access to the interactive service pipe from remote computers. Reported-by: Vladimir Tokarev <vtokarev@microsoft.com>
- CVE-2024-27903: Windows: disallow loading of plugins from untrusted installation paths, which could be used to attack
openvpn.exevia a malicious plugin. Plugins can now only be loaded from the OpenVPN install directory, the Windows system directory, and possibly from a directory specified byHKLM\SOFTWARE\OpenVPN\plugin_dir. Reported-by: Vladimir Tokarev <vtokarev@microsoft.com> - CVE-2024-1305: Windows TAP driver: Fix potential integer overflow in TapSharedSendPacket. Reported-by: Vladimir Tokarev <vtokarev@microsoft.com>
Windows MSI changes since 2.5.10:
- For the Windows-specific security fixes see above
- Built against OpenSSL 1.1.1w
- Note that OpenSSL 1.1.1 is not supported anymore, so this might not address all known issues in OpenSSL 1.1.1. If that concerns you, please switch to OpenVPN 2.6.x
- Included tap6-windows driver updated to 9.27.0
- Security fix, see above
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.10-I601-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.5.10-I601-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.10-I601-x86.msi |
Source archive file |
GnuPG Signature | openvpn-2.5.10.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.5.4. This release include a number of fixes and small improvements. One of the fixes is to password prompting on windows console when stderr redirection is in use — this breaks 2.5.x on Win11/ARM, and might also break on Win11/amd64. Windows executable and libraries are now built natively on Windows using MSVC, not cross-compiled on Linux as with earlier 2.5 releases. Windows installers include updated OpenSSL and new OpenVPN GUI. The latter includes several improvements, the most important of which is the ability to import profiles from URLs where available. Installer version I602 fixes loading of pkcs11 files on Windows. Installer version I603 fixes a bug in the version number as seen by Windows (was 2.5..4, not 2.5.4). Installer I604 fixes some small Windows issues.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.4.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.4.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.4.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.4-I604-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.4-I604-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.5.4-I604-arm64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.5.3. Besides a number of small improvements and bug fixes, this release fixes a possible security issue with OpenSSL config autoloading on Windows (CVE-2021-3606). Updated OpenVPN GUI is also included in Windows installers.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.3.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.3.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.3.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.3-I601-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.3-I601-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.5.3-I601-arm64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
- Connections setup is now much faster
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.5.2. It fixes two related security vulnerabilities (CVE-2020-15078) which under very specific circumstances allow tricking a server using delayed authentication (plugin or management) into returning a PUSH_REPLY before the AUTH_FAILED message, which can possibly be used to gather information about a VPN setup. In combination with «—auth-gen-token» or a user-specific token auth solution it can be possible to get access to a VPN with an otherwise-invalid account. OpenVPN 2.5.2 also includes other bug fixes and improvements. Updated OpenSSL and OpenVPN GUI are included in Windows installers.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.2.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.2.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.2.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.2-I601-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.2-I601-amd64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
- Connections setup is now much faster
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.5.1. It includes several bug fixes and improvements as well as updated OpenSSL and OpenVPN GUI for Windows.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.1.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.1.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.1.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.1-I601-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.1-I601-amd64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
- Connections setup is now much faster
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.5.0 which is a new major release with many new features.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.0.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.0.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.0.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.0-I601-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.0-I601-amd64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
- Connections setup is now much faster
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.4.11. It fixes two related security vulnerabilities (CVE-2020-15078) which under very specific circumstances allow tricking a server using delayed authentication (plugin or management) into returning a PUSH_REPLY before the AUTH_FAILED message, which can possibly be used to gather information about a VPN setup. This release also includes other bug fixes and improvements. The I602 Windows installers fix a possible security issue with OpenSSL config autoloading on Windows (CVE-2021-3606). Updated OpenSSL and OpenVPN GUI are included in Windows installers.
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.11.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.11.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.11.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.11-I602-Win7.exe |
Windows 10/Server 2016/Server 2019 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.11-I602-Win10.exe |
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer works on Windows 10 and Windows Server 2016/2019. The Windows 7 installer will work on Windows 7/8/8.1/Server 2012r2. This is because of Microsoft’s driver signing requirements are different for kernel-mode devices drivers, which in our case affects OpenVPN’s tap driver (tap-windows6).
This is primarily a maintenance release with bugfixes and small improvements. Windows installers include the latest OpenSSL version (1.1.1i) which includes security fixes.
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer works on Windows 10 and Windows Server 2016/2019. The Windows 7 installer will work on Windows 7/8/8.1/Server 2012r2. This is because of Microsoft’s driver signing requirements are different for kernel-mode devices drivers, which in our case affects OpenVPN’s tap driver (tap-windows6).
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.10.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.10.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.10.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.10-I601-Win7.exe |
Windows 10/Server 2016/Server 2019 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.10-I601-Win10.exe |
Instructions for verifying the signatures are available here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
This is primarily a maintenance release with bugfixes and improvements. This release also fixes a security issue (CVE-2020-11810, trac #1272) which allows disrupting service of a freshly connected client that has not yet not negotiated session keys. The vulnerability cannot be used to inject or steal VPN traffic.
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them. We are moving to MSI installers in OpenVPN 2.5, but OpenVPN 2.4.x will remain NSIS-only.
Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless connection migration when client’s IP address changes (Peer-ID). Also, the new —tls-crypt feature can be used to increase users’ connection privacy.
OpenVPN GUI bundled with the Windows installer has a large number of new features compared to the one bundled with OpenVPN 2.3. One of major features is the ability to run OpenVPN GUI without administrator privileges. For full details, see the changelog. The new OpenVPN GUI features are documented here.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer works on Windows 10 and Windows Server 2016/2019. The Windows 7 installer will work on Windows 7/8/8.1/Server 2012r2. This is because of Microsoft’s driver signing requirements are different for kernel-mode devices drivers, which in our case affects OpenVPN’s tap driver (tap-windows6).
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.9.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.9.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.9.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.9-I601-Win7.exe |
Windows 10/Server 2016/Server 2019 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.9-I601-Win10.exe |
NOTE: the GPG key used to sign the release files has been changed since OpenVPN 2.4.0. Instructions for verifying the signatures, as well as the new GPG public key are available here.
We also provide static URLs pointing to latest releases to ease automation. For a list of files look here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
You can use EasyRSA 2 or EasyRSA 3 for generating your own certificate authority. The former is bundled with Windows installers. The latter is a more modern alternative for UNIX-like operating systems.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
This is primarily a maintenance release with bugfixes and improvements. The Windows installers (I601) have several improvements compared to the previous release:
- New tap-windows6 driver (9.24.2) which fixes some suspend and resume issues
- Latest OpenVPN-GUI
- Considerable performance boost due to new compiler optimization flags
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them. We are moving to MSI installers in OpenVPN 2.5, but OpenVPN 2.4.x will remain NSIS-only.
Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless connection migration when client’s IP address changes (Peer-ID). Also, the new —tls-crypt feature can be used to increase users’ connection privacy.
OpenVPN GUI bundled with the Windows installer has a large number of new features compared to the one bundled with OpenVPN 2.3. One of major features is the ability to run OpenVPN GUI without administrator privileges. For full details, see the changelog. The new OpenVPN GUI features are documented here.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer works on Windows 10 and Windows Server 2016/2019. The Windows 7 installer will work on Windows 7/8/8.1/Server 2012r2. This is because of Microsoft’s driver signing requirements are different for kernel-mode devices drivers, which in our case affects OpenVPN’s tap driver (tap-windows6).
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.8.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.8.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.8.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.8-I602-Win7.exe |
Windows 10/Server 2016/Server 2019 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.8-I602-Win10.exe |
NOTE: the GPG key used to sign the release files has been changed since OpenVPN 2.4.0. Instructions for verifying the signatures, as well as the new GPG public key are available here.
We also provide static URLs pointing to latest releases to ease automation. For a list of files look here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
You can use EasyRSA 2 or EasyRSA 3 for generating your own certificate authority. The former is bundled with Windows installers. The latter is a more modern alternative for UNIX-like operating systems.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
This is primarily a maintenance release with bugfixes and improvements. One of the big things is enhanced TLS 1.3 support. A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them. We are moving to MSI installers in OpenVPN 2.5, but OpenVPN 2.4.x will remain NSIS-only.
Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless connection migration when client’s IP address changes (Peer-ID). Also, the new —tls-crypt feature can be used to increase users’ connection privacy.
OpenVPN GUI bundled with the Windows installer has a large number of new features compared to the one bundled with OpenVPN 2.3. One of major features is the ability to run OpenVPN GUI without administrator privileges. For full details, see the changelog. The new OpenVPN GUI features are documented here.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer will not work on Windows 7/8/8.1/Server 2012r2. This is because Microsoft’s driver signing requirements and tap-windows6. For the same reason you need to use an older installer with Windows Server 2016. This older installer has a local privilege escalation vulnerability issue which we cannot resolve for Windows Server 2016 until tap-windows6 passes the HLK test suite on that platform. In the meanwhile we recommend Windows Server 2016 users to avoid installing OpenVPN/tap-windows6 driver on hosts where all users can’t be trusted. Users of Windows 7-10 and Server 2012r2 are recommended to update to latest installers as soon as possible.
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.7.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.7.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.7.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.7-I607-Win7.exe |
Windows 10 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.7-I607-Win10.exe |
Windows Server 2016 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.7-I603.exe |
NOTE: the GPG key used to sign the release files has been changed since OpenVPN 2.4.0. Instructions for verifying the signatures, as well as the new GPG public key are available here.
We also provide static URLs pointing to latest releases to ease automation. For a list of files look here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
You can use EasyRSA 2 or EasyRSA 3 for generating your own certificate authority. The former is bundled with Windows installers. The latter is a more modern alternative for UNIX-like operating systems.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
This is primarily a maintenance release with minor bugfixes and improvements, and one security relevant fix for the Windows Interactive Service. Windows installer includes updated OpenVPN GUI and OpenSSL. Installer I601 included tap-windows6 driver 9.22.1 which had one security fix and dropped Windows Vista support. However, in installer I602 we had to revert back to tap-windows 9.21.2 due to driver getting reject on freshly installed Windows 10 rev 1607 and later when Secure Boot was enabled. The failure was due to the new, more strict driver signing requirements. The 9.22.1 version of the driver is in the process of getting approved and signed by Microsoft and will be bundled in an upcoming Windows installer.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them. Our long-term plan is to migrate to using MSI installers instead.
Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless connection migration when client’s IP address changes (Peer-ID). Also, the new —tls-crypt feature can be used to increase users’ connection privacy.
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
OpenVPN GUI bundled with the Windows installer has a large number of new features compared to the one bundled with OpenVPN 2.3. One of major features is the ability to run OpenVPN GUI without administrator privileges. For full details, see the changelog. The new OpenVPN GUI features are documented here.
Please note that OpenVPN 2.4 installers will not work on Windows XP.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developha er IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.6.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.6.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.6.zip |
Windows installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.6-I602.exe |
NOTE: the GPG key used to sign the release files has been changed since OpenVPN 2.4.0. Instructions for verifying the signatures, as well as the new GPG public key are available here.
We also provide static URLs pointing to latest releases to ease automation. For a list of files look here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
You can use EasyRSA 2 or EasyRSA 3 for generating your own certificate authority. The former is bundled with Windows installers. The latter is a more modern alternative for UNIX-like operating systems.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
You can download Windows developments snapshots (MSI installers) from here (Index of /downloads/snapshots/github-actions/openvpn2/ ). Those are automatically built from commits to OpenVPN master branch and include functionality which will be available in the next release. Development snapshots are less stable than releases, so use at your own risk.

OpenVPN GUI представляет собой графический интерфейс, средство, с помощью которого можно работать с VPN-сервисом на компьютере. Утилита осуществляет защиту Wi-Fi соединения, а также выполняет ряд других полезных функций. Пользоваться программой довольно просто, что обеспечивается её дружелюбным и интуитивно понятным интерфейсом.
Возможности
Первым делом следует разобраться, что это за программа и какими функциями она может порадовать. К ним можно отнести:
- использование сторонних плагинов и скинов;
- OpenSSL-шифрование;
- использование собственных протоколов на базе TLS и SSL;
- поддержка работы с tls-auth для верификации подписи HMAC;
- отображение подробной информации о соединении.
Цифровой продукт отлично подходит для всех версий операционной системы Windows с архитектурой 32/64 Bit.
Плюсы и минусы
Дальше скажем несколько слов о преимуществах и недостатках софта.
Достоинства:
- легковесность;
- кроссплатформенность;
- простота в работе;
- бесплатное использование.
Недостатки:
- снижение скорости соединения.
Как скачать
Переходим по ссылке внизу и получаем желаемый контент на свое электронное устройство.
| Категория: | Сеть |
| Разработчик: | OpenVPN Technologies |
| Платформа: | Windows 7, 8, 10, 11 |
| Русский: | Да |
| Лицензия: | Бесплатно |
OpenVPN GUI
