Npcap
Npcap is a packet capture and injection library for
Windows by the Nmap Project. It is a complete update to
the unmaintained WinPcap project with improved
speed, reliability, and security.
Documentation
The complete documentation for Npcap is available in the Npcap
Guide on npcap.com. There you
will find information about
installation,
reporting
bugs,
developing software with
Npcap, and Npcap
internals.
Downloads
The latest installer, Software Development Kit (SDK), source, and debug symbols
can be downloaded from https://npcap.com/#download
Bug report
Please report any bugs or issues about Npcap at: Npcap issues on
GitHub. In your report, please provide
your
DiagReport
output, user software version (e.g. Nmap, Wireshark), reproduce steps and other
information you think necessary. Refer to the Npcap Guide section on reporting
bugs for more
complete directions.
License
The Npcap License allows
end users to download, install, and use Npcap from our site for free on up to 5
systems (including commercial usage). Software providers (open source or
otherwise) which want to use Npcap functionality are welcome to point their
users to npcap.com for those users to download and install.
We fund the Npcap project by selling Npcap OEM. This
special version of Npcap includes enterprise features such as the silent
installer and commercial support as well as special license rights.
Contact
dev@nmap.org(Nmap development list, for technical issues and discussion)sales@nmap.com(Sales address for commercial/licensing issues)- Npcap Issues Tracker
Imagine a river of data flowing beneath the surface of our digital world. Each ripple, each current, tells a story of communication, connection, and activity. Now, picture yourself as an artist, equipped with a special brush that allows you to dip into this river and paint a vivid picture of what’s happening beneath. This, in essence, is what packet capture is all about, and Npcap is one of the most powerful tools in your artistic arsenal. In today’s digital age, where every byte of data can be crucial, understanding and utilizing packet capture is more important than ever.
The Evolution of Packet Capture
Packet capture, at its core, is the process of intercepting and logging network traffic. The concept isn’t new; it has roots stretching back to the early days of networking. Think of the first network administrators, huddled around clunky machines, using rudimentary tools to sniff out anomalies and troubleshoot issues.
Early methods were often limited by hardware constraints and the sheer complexity of the task. Tools like tcpdump emerged as command-line stalwarts, offering a raw, unfiltered view of network packets. While incredibly powerful, they lacked the user-friendly interface and advanced features we expect today.
Over time, the aesthetic of network monitoring tools has evolved. Gone are the days of cryptic command lines and indecipherable output. Modern tools boast sleek user interfaces, intuitive dashboards, and visually appealing representations of network data. This evolution reflects a growing understanding of the importance of user experience in complex technical tasks.
Packet capture has become a critical component in network security and performance analysis. It’s the foundation upon which many security tools are built, enabling intrusion detection, malware analysis, and forensic investigations. In performance analysis, it helps identify bottlenecks, optimize network configurations, and ensure smooth data flow. Without packet capture, we’d be operating in the dark, blind to the intricate dance of data that powers our digital lives.
Introducing Npcap
So, what exactly is Npcap? Npcap is a modern, open-source packet capture library for Windows, designed to be a successor to the widely used WinPcap. Think of WinPcap as the reliable, slightly outdated workhorse, and Npcap as the sleek, high-performance sports car.
Npcap emerged to address some of the limitations of WinPcap, particularly in terms of security, performance, and compatibility with modern Windows operating systems. It was developed by Yang Luo and the Nmap Project team, the same folks behind the famous Nmap port scanner. They saw a need for a more robust and versatile packet capture solution on Windows, and Npcap was their answer.
Npcap’s purpose is simple: to provide a reliable and efficient way to capture network packets on Windows systems. It acts as a bridge between network interfaces and applications that need to analyze network traffic, such as Wireshark, Nmap, and intrusion detection systems.
But Npcap isn’t just a functional tool; it’s also aesthetically pleasing in its design and integration. Its seamless compatibility with Wireshark, for instance, creates a smooth and intuitive user experience. The clean, modern interface of Npcap, combined with the powerful analysis capabilities of Wireshark, makes network analysis a more enjoyable and accessible task.
Technical Features of Npcap
Let’s dive into the technical specifications that make Npcap stand out. Npcap boasts a range of features designed to enhance packet capture capabilities on Windows:
- Loopback Traffic Capture: One of Npcap’s key advantages is its ability to capture loopback traffic, which is traffic that stays within the local machine. WinPcap struggled with this, making Npcap essential for analyzing local network activity.
- Raw 802.11 Traffic Capture: Npcap supports capturing raw 802.11 traffic, allowing you to analyze wireless network packets directly. This is invaluable for wireless security assessments and troubleshooting.
- Npcap Driver: This is the core component that interacts directly with the network interface card (NIC) to capture packets. It operates at the kernel level, ensuring efficient and low-latency packet capture.
- Npcap Service: A Windows service that manages the Npcap driver and provides an interface for applications to access captured packets.
- Npcap API: A set of functions and libraries that applications can use to interact with Npcap and capture network traffic.
Npcap enhances packet capture in several ways:
- Improved Security: Npcap incorporates security enhancements to prevent malicious applications from abusing packet capture capabilities. It uses a whitelist approach, allowing only authorized applications to capture traffic.
- Enhanced Performance: Npcap is designed for high-performance packet capture, minimizing CPU usage and memory consumption.
- Compatibility: Npcap is compatible with a wide range of Windows operating systems, including the latest versions.
- NDIS 6 (Network Driver Interface Specification) Support: Npcap is built using NDIS 6, which allows for better integration with modern Windows network drivers. This results in improved performance and stability.
Here’s a simplified analogy: Imagine Npcap as a highly efficient postal service. The Npcap driver is the mail carrier, diligently collecting packets (letters) from the network interface (mailboxes). The Npcap service is the central distribution center, sorting and routing packets to the appropriate applications (recipients). The Npcap API is the set of rules and procedures that govern how applications can request and receive packets from the postal service.
Installation and Setup
Installing Npcap is a straightforward process. Here’s a step-by-step guide:
- Download Npcap: Visit the official Npcap website (https://npcap.com/) and download the latest version of the installer.
- Run the Installer: Double-click the downloaded installer to start the installation process.
- License Agreement: Accept the license agreement.
- Installation Options: Choose the installation options that best suit your needs. Key options include:
- Install Npcap in WinPcap API-compatible mode: This allows applications that rely on the WinPcap API to work with Npcap.
- Support loopback traffic: Enable this option to capture loopback traffic.
- Restrict Npcap access to Administrators only: This enhances security by limiting packet capture capabilities to administrator accounts.
- Install: Click the “Install” button to begin the installation.
- Reboot: After the installation is complete, reboot your computer to ensure that Npcap is properly initialized.
The installation interface is designed to be user-friendly, with clear instructions and visual cues. The aesthetic is clean and modern, reflecting the overall design philosophy of Npcap.
Using Npcap with Wireshark
Wireshark is a powerful and widely used network protocol analyzer. Integrating Npcap with Wireshark unlocks a world of possibilities for network analysis.
To use Npcap with Wireshark:
- Install Npcap: Follow the installation steps outlined above.
- Install Wireshark: Download and install Wireshark from its official website (https://www.wireshark.org/).
- Configure Wireshark: After installing both Npcap and Wireshark, launch Wireshark. It should automatically detect Npcap as the packet capture driver.
- Select Interface: In Wireshark, select the network interface you want to capture traffic from.
- Start Capture: Click the “Start Capture” button (the shark fin icon) to begin capturing packets.
The experience of using Npcap with Wireshark is seamless. Npcap provides the underlying packet capture engine, while Wireshark provides the interface for analyzing and interpreting the captured data. This combination allows you to:
- Capture Packets: Intercept and log network traffic in real-time.
- Analyze Data: Examine the contents of individual packets, including headers, protocols, and payloads.
- Interpret Results: Identify patterns, anomalies, and potential security threats.
Let’s consider a case study: Imagine you’re troubleshooting a slow network connection. Using Npcap and Wireshark, you can capture network traffic and analyze the packets to identify the source of the slowdown. You might discover that a particular application is consuming excessive bandwidth, or that there are a large number of retransmissions due to network congestion.
Advanced Features and Use Cases
Npcap offers a range of advanced features that extend its capabilities beyond basic packet capture:
- Packet Filtering: Npcap allows you to filter packets based on various criteria, such as source and destination IP addresses, port numbers, and protocols. This helps you focus on the traffic that’s most relevant to your analysis.
- Capturing Specific Protocols: You can configure Npcap to capture only specific protocols, such as HTTP, DNS, or SMTP. This reduces the amount of data you need to analyze and simplifies the process of identifying protocol-specific issues.
- Analyzing Live Traffic: Npcap captures packets in real-time, allowing you to analyze live network traffic as it flows across the network. This is invaluable for detecting and responding to security threats in real-time.
Npcap has numerous use cases across various fields:
- Cybersecurity: Npcap is a critical tool for cybersecurity professionals, enabling them to:
- Detect and analyze malware.
- Identify and respond to network intrusions.
- Conduct forensic investigations.
- Network Troubleshooting: Npcap helps network administrators:
- Diagnose network performance issues.
- Identify bottlenecks.
- Optimize network configurations.
- Performance Monitoring: Npcap allows you to:
- Monitor network traffic patterns.
- Identify applications that are consuming excessive bandwidth.
- Optimize network performance.
Community and Support
The Npcap community is a vibrant and supportive ecosystem of users, developers, and experts. You can find help, resources, and inspiration from various sources:
- Npcap Website: The official Npcap website (https://npcap.com/) provides comprehensive documentation, tutorials, and FAQs.
- Nmap Mailing Lists: The Nmap Project maintains several mailing lists where you can ask questions, share your experiences, and connect with other Npcap users.
- Online Forums: Various online forums and communities, such as Stack Overflow and Reddit, have dedicated sections for Npcap-related questions and discussions.
- GitHub: The Npcap source code is hosted on GitHub (https://github.com/nmap/npcap), where you can contribute to the project, report bugs, and suggest new features.
The aesthetic of community engagement is one of collaboration, knowledge sharing, and mutual support. Users share their insights, experiences, and solutions in a visually appealing and accessible manner.
Conclusion
In conclusion, Npcap is a powerful and versatile packet capture library that unlocks the full potential of network analysis on Windows. Its advanced features, seamless integration with Wireshark, and vibrant community make it an indispensable tool for cybersecurity professionals, network administrators, and technology enthusiasts alike.
As we reflect on the aesthetic journey of packet capture, we see a transformation from cryptic command lines to intuitive interfaces, from raw data dumps to visually appealing representations of network activity. Npcap empowers users to paint a vivid picture of their network, revealing hidden patterns, identifying potential threats, and optimizing performance. It’s a testament to the power of technology to transform complex tasks into accessible and engaging experiences. So, grab your brush, dip into the river of data, and start painting your own network masterpiece with Npcap.
Learn more
Nmap Packet Capture is more critical than ever that one actually understands network traffic and is able to monitor it, be it a network administrator, a cybersecurity expert, or a developer building applications against network data. You need some solid tools to analyze and capture packets. One of the prominent tools which have been game-changers is npcap. What is actually this npcap, and why you should know? Read ahead to delve into Nmap Packet Capture features, benefits, use cases, everything one needs to know about this essential network capturing tool.
What Is npcap?How Does npcap Work?Features and Capabilities of npcapComparison With WinPcapBenefits of Using npcapFor Network AdministratorsFor DevelopersFor Cybersecurity ExpertsCommon Use Cases for npcapInstalling and Setting Up npcapSystem RequirementsInstallation ProcessTroubleshooting Common IssuesInstallation ProblemsPerformance IssuesCompatibility ChallengesAlternatives to npcapPopular AlternativesWhy Choose npcap?Advanced Network Traffic Filtering TechniquesUsing BPF for Custom FilteringMulti-Level Filtering StrategiesEnhancing Cybersecurity With Packet InjectionSimulating Threat ScenariosBuilding Active Defense MechanismsNpcap in Continuous Monitoring and SIEM IntegrationReal-Time Data IngestionCorrelation With Other Data SourcesBeyond Network Diagnostics: Npcap in Emerging FieldsDigital Twin NetworksSmart City NetworksLeveraging Npcap in 5G and IoT EnvironmentsHandling 5G TrafficSecuring IoT EcosystemsAdvanced Packet Replay for Forensics and TestingUse Cases for Packet ReplayAutomating Replay ScenariosHarnessing Machine Learning With Nmap Packet CaptureTraining AI ModelsReal-Time ML IntegrationUsing Nmap Packet Capture for Ethical Hacking and Red Team ExercisesScenarios Where Npcap ExcelsCombining With Other ToolsFuture of Nmap Packet Capture and Network Packet CapturingOngoing DevelopmentsTrends in Network AnalysisPotential Usde in AI-Driven AnalyticsThe Value of npcap in Modern NetworkingFAQsWhat is the difference between npcap and WinPcap?Is npcap free to use?Can Nmap Packet Capture capture encrypted traffic?Does npcap work with virtual machines?How do I contribute to npcap’s development?
Npcap is a library that captures packets and monitors networks at a very high speed on Windows platforms from the Nmap Project, thus being a more modern alternative to WinPcap. It not only provides the basic ability for applications to capture and send packets at the level of the network, but it goes way beyond that: it is simply very good and versatile so that it features real-value tools for networking diagnostics and cybersecurity.
How Does npcap Work?
Nmap Packet Capture acts as a Windows network driver and library, which devices tap into in order to communicate with applications for network-related purposes. It captures packets traversing the network interface and enables applications to analyze, log, or otherwise modify them in real-time. Some features comprise:
- Both inbound and outbound packets have been monitored.
- Compatibility with e.g. localhost loopback traffic.
- Advanced wireless packet capturing is done through Wi-Fi monitor mode.
Features and Capabilities of npcap
Npcap has very peculiar and advanced features that are not found in WinPcap:
| Feature | Description |
|---|---|
| High Performance | Optimized for speed and efficiency, with minimal impact on system resources. |
| Loopback Traffic Support | Unique capability to capture traffic on localhost. |
| Wi-Fi Monitor Mode | Enables packet capture on wireless networks in monitor mode. |
| Secure Driver | Digitally signed to ensure security and compatibility with Windows systems. |
Comparison With WinPcap
Npcap gives considerable enhancements in comparison with the legacy WinPcap library:
- Speed: Nmap Packet Capture boasts greater speed and efficiency arising from its very modern design.
- Dynamic Development: Rid of Peering, Nmap Packet Capture will be under continuous update unlike WinPcap.
- Superior Features: Loopback traffic and wireless monitoring mode are property of Nmap Packet Capture , lacking in WinPcap.
Benefits of Using npcap
For Network Administrators
With real-time packet intercepting and analysis capabilities, Nmap Packet Capture will make troubleshooting networks dead simple. Npcap will basically work together with popular network tools like Wireshark to enable the administrator to:
- Detect and fix issues with network latency.
- Find and mitigate packet loss.
- Have a better picture over his or her network’s traffic patterns to ensure the stability of the network.
For Developers
Developers can use the extensive API of Npcap to develop fully custom network tools and applications. The complete documentation and a responsive community offer developers:
- Develop network monitoring systems according to individual needs.
- Create standalone applications demanding lots of packet-level data.
For Cybersecurity Experts
Npcap gives a prominent weightage for cybersecurity via allowing exhaustive traffic analysis. Professionals get enabled to:
- Monitor traffic alarms generated by network intrusion detection systems.
- Examine network compromises as well as weaknesses.
Common Use Cases for npcap
Nmap Packet Capture is really a powerful utility that used in many fields and has many use cases making it one of the irreplaceable tools for network experts as well as researchers. Nmap Packet Capture identifies if there are latency problems which become apparent through the process of capturing packets and measuring round-trip times and usually helps determine delays which negatively affect network performance during network diagnostics. Also, it shows real-time dropped packets for packet loss troubleshooting, identifying, and addressing packet loss to result in a smooth data stream. This is critical for security experts and agencies since it comes in handy during the monitoring of network traffic for tampering or threats. Npcap aids in intrusion detection, by capturing and analyzing suspicious packets that may give an indication of malicious activity taking place. Moreover, Nmap Packet Capture traffic analysis gives information of data which may subsequently show unusualness or breaches at times. For researchers and developers alike, Npcap also serves as a good platform for academic or industry studies.
Protocol analysis is another aspect that it facilitates to give researchers an opportunity to examine and understand how network protocols behave. It is also critical in application testing by emulating the real-world networking scenario within which new software will have to operate to really judge the performance and reliability of applications. With an increase in the number of Internet of things, Npcap has become necessary for ensuring the communication between smart devices and the verification of how well they function. The tool serves as a critical measuring instrument by taking the monitoring of traffic between devices for revealing possible weaknesses in IoT ecosystems. Therefore, with this, it had definitely become a strong tool for building security shields around each other in the interconnected networks.
You May Like: Is Disposable 10-Minute Mail Trackable? Exploring the Myths and Realities In 2025
Installing and Setting Up npcap
System Requirements
Before installing Nmap Packet Capture, ensure your system meets the following requirements:
- Operating System: Windows 7 or newer.
- Hardware: Minimum 1 GHz processor, 1 GB RAM, and a stable network adapter.
Installation Process
Installing npcap is straightforward. Follow these steps:
- Download the Installer: Visit the official npcap website and download the latest version.
- Run the Installer: Double-click the installer and follow the on-screen instructions.
2.1. Click I Agree If you Agree if upu accept the terms of the agreement
2.2. Check only Install Npcap in winPcap API
2.3. Click on Install, Wait Then Hit Finish. - Select Configuration Options:
- Enable loopback traffic capturing.
- Choose whether to install npcap in “WinPcap compatibility mode.”
Best Practices: Updates Nmap Packet Capture frequently to have the latest features and security patches, and during installation, see the configuration options to tailor them to your needs.
Troubleshooting Common Issues
Installation Problems
- Driver Conflicts: Uninstall any existing packet capture drivers (e.g., WinPcap) before installing Nmap Packet Capture.
- Error Messages: Check the installation logs for detailed error descriptions.
Performance Issues
- Optimize system resources by closing unnecessary applications during packet capture.
- Use a wired connection when capturing high volumes of data for better reliability.
Compatibility Challenges
- Ensure your network analysis tools support npcap’s API.
- Refer to the official documentation for troubleshooting specific compatibility issues.
Alternatives to npcap
Popular Alternatives
While npcap is highly recommended, other tools are available:
| Alternative | Platform | Key Features |
| Libpcap | Linux | Widely used, open-source library. |
| WinPcap | Windows | Legacy tool, now outdated. |
| Scapy | Cross-Platform | Python-based network analysis. |
Why Choose npcap?
Nmap Packet Capture stands out due to its modern features, active development, and superior performance. It is the preferred choice for professionals who require reliability and advanced capabilities.
You May Like: What Is Data Mining? Exploring How It Works, Its Benefits, Techniques, and Trends for 2025
Advanced Network Traffic Filtering Techniques
Nmap Packet Capture enables precise traffic filtering to enhance analysis and reduce noise. This is especially useful for handling high-traffic networks or isolating specific types of data.
Using BPF for Custom Filtering
Npcap supports Berkeley Packet Filter (BPF) syntax for efficient packet filtering:
- Capture Specific Protocols:
Example:udp port 53captures only DNS traffic. - Exclude Traffic:
Example:not tcp port 22filters out SSH packets.
Multi-Level Filtering Strategies
Layer-Specific Filters
- Layer 2: Focus on MAC addresses for device-specific monitoring.
- Layer 3: Filter based on IP addresses or subnets.
Application-Level Filters
Use filters to focus on high-level application data, e.g., HTTP, HTTPS, or custom protocols.
Enhancing Cybersecurity With Packet Injection
Npcap’s packet injection capabilities enable both testing and active defenses in network security scenarios.
Simulating Threat Scenarios
Security teams can use Nmap Packet Capture to:
- Replay Captured Packets: Test how devices or applications respond to specific traffic patterns.
- Inject Malicious Traffic: Evaluate firewall and IDS/IPS performance by simulating attacks like SYN floods or ARP spoofing.
Building Active Defense Mechanisms
Npcap helps organizations build tools that:
- Automatically inject reset (RST) packets to disrupt unauthorized connections.
- Send decoy traffic to confuse adversaries or mask legitimate communications.
Npcap in Continuous Monitoring and SIEM Integration
also plays a vital role in Security Information and Event Management (SIEM) workflows by feeding detailed packet data into analytics pipelines.
Real-Time Data Ingestion
Nmap Packet Capture allows continuous packet capture, offering raw data to SIEM tools like Splunk or ELK Stack for:
- Threat Hunting: Detect anomalies by analyzing packet trends.
- Compliance Monitoring: Ensure adherence to standards like PCI-DSS or GDPR through traffic auditing.
Correlation With Other Data Sources
It can work alongside logs from firewalls, routers, or endpoint devices to create a comprehensive view of network health.
Beyond Network Diagnostics: Npcap in Emerging Fields
Npcap’s utility goes beyond traditional network analysis, finding applications in cutting-edge domains.
Digital Twin Networks
Nmap Packet Capture supports the creation of digital replicas of network environments for:
- Predictive Analysis: Test potential failures in a virtualized network before deploying changes.
- Performance Optimization: Simulate upgrades or load changes to refine configurations.
Smart City Networks
Nmap Packet Capture aids in managing data flows in smart cities, including:
- Traffic Systems: Monitor communications between IoT sensors and centralized systems.
- Public Wi-Fi Security: Detect and mitigate unauthorized access in municipal Wi-Fi networks.
You May Like: Difference Between Aes, Des and Rsa Encryption
Leveraging Npcap in 5G and IoT Environments
Nmap Packet Capture is well-suited for analyzing modern, high-speed, and interconnected networks.
Handling 5G Traffic
With 5G, packet rates and data speeds challenge traditional capture tools. Nmap Packet Capture’s performance capabilities allow:
- Latency Analysis: Pinpoint delays in ultra-low-latency applications like AR/VR.
- Bandwidth Utilization: Monitor and optimize data distribution across multiple devices.
Securing IoT Ecosystems
Nmap Packet Capture helps identify vulnerabilities in IoT devices:
- Firmware Analysis: Capture firmware updates for reverse engineering or validation.
- Device Behavior Monitoring: Spot anomalies in device communication patterns that may indicate compromise.
Advanced Packet Replay for Forensics and Testing
Nmap Packet Capture is not just for packet capture—it’s also a powerful tool for replaying traffic for testing and forensic purposes.
Use Cases for Packet Replay
- Performance Testing:
- Replay traffic to measure how new infrastructure handles real-world loads.
- Application Debugging:
- Simulate user interactions with applications by replaying session traffic.
Automating Replay Scenarios
Combine Nmap Packet Capture with scripting tools like Python to automate complex replay scenarios for regression testing or forensic re-enactments.
Harnessing Machine Learning With Nmap Packet Capture
Nmap Packet Capture’s detailed data capture supports machine learning (ML) use cases in network analysis.
Training AI Models
- Traffic Classification: Use labeled packet data to train models for protocol identification.
- Anomaly Detection: Develop systems that identify abnormal patterns indicative of intrusions or malfunctions.
Real-Time ML Integration
Nmap Packet Capture data can feed into real-time ML pipelines for:
- Dynamic Filtering: Adjust capture settings based on evolving traffic patterns.
- Predictive Alerts: Identify potential issues before they escalate by correlating packet data with ML outputs.
Using Nmap Packet Capture for Ethical Hacking and Red Team Exercises
Nmap Packet Capture is a critical tool for ethical hackers and penetration testers conducting red team exercises.
Scenarios Where Npcap Excels
- Network Mapping:
- Capture and analyze ARP and ICMP traffic to map out devices and subnets.
- Session Hijacking:
- Monitor unencrypted sessions for vulnerabilities in outdated protocols.
Combining With Other Tools
Nmap Packet Capture works seamlessly with hacking frameworks like Metasploit to:
- Launch Packet-Based Exploits: Test network resilience against advanced packet-based attacks.
- Analyze Attack Outcomes: Validate the success of simulated exploits by capturing post-attack traffic.
Future of Nmap Packet Capture and Network Packet Capturing
Ongoing Developments
The Nmap Project regularly updates Nmap Packet Capture in order to improve performance and new functions. Recent updates (e.g., December 2023 release) include:
- Improved Wi-Fi monitor mode.
- Enhanced security for driver installation.
Trends in Network Analysis
Npcap is poised to play a significant role in emerging technologies, such as:
- IoT: Monitoring data from connected devices.
- 5G Networks: Analyzing high-speed traffic.
Potential Usde in AI-Driven Analytics
Npcap may integrate with AI tools for:
- Real-time anomaly detection.
- Automated threat analysis in complex networks.
You May Like: How to Update and Enhance Internet Speed and Ping Using TCP Optimizer: A Step-by-Step Guide for a Faster Web Experience! 2025
The Value of npcap in Modern Networking
Npcap is a tool that is tough, reliable, and versatile when it comes to meeting the demands of network administrators, developers, and cybersecurity professionals. Advanced features and their development in progress make it still relevant with the need of contemporary systems: thus, it becomes a mandatory tool for someone engaged in network traffic analysis.
Want to elevate your network analysis capabilities? Download Nmap Packet Capture today and begin your experience with it. Share with the community, present your usage, and help with its development too. Nmap Packet Capture has what it takes to bring confidence into challenges presented by modern networking and how it deals with the current situation.
FAQs
What is the difference between npcap and WinPcap?
Npcap is faster, more secure, and actively maintained, unlike the discontinued WinPcap.
Is npcap free to use?
Yes, Nmap Packet Capture is free for non-commercial use. Commercial licenses are available for businesses.
Can Nmap Packet Capture capture encrypted traffic?
Nmap Packet Capture can capture encrypted packets, but decryption requires additional tools or keys.
Does npcap work with virtual machines?
Yes, Nmap Packet Capture supports virtual environments, but configuration may be required for optimal performance.
How do I contribute to npcap’s development?
Visit the official website for guidelines on contributing code, reporting bugs, or supporting the community.
WinPcap vs Npcap is an essential comparison for anyone involved in network analysis or cybersecurity. WinPcap provides stability and compatibility with legacy systems, while Npcap offers modern security features, performance enhancements, and support for advanced traffic capture. Both tools have strong community support and seamless integration with popular network tools like Wireshark and Nmap. Choosing the right tool depends on specific needs, system compatibility, and performance requirements, with WinPcap suitable for older setups and Npcap ideal for modern environments.
What is the Main Difference Between WinPcap and Npcap?
The main difference between WinPcap and Npcap is that while WinPcap is no longer actively maintained and lacks modern features and support for the latest Windows updates, Npcap is actively maintained, offering comprehensive support and enhanced performance for Windows 10 and beyond.
What is WinPcap and What is Npcap?
WinPcap is a widely-used packet capture library for Windows that allows applications to capture and transmit network packets. Originally developed in the late 1990s, WinPcap became a standard tool for diagnosing network traffic, performing network analysis, and building network monitoring tools. It was widely admired for its functionality and dependability. However, the maintenance ceased in 2013, making it outdated in terms of compatibility with modern Windows operating systems.
Npcap, on the other hand, is a newer and actively-maintained alternative to WinPcap. Developed by the same team that works on the popular network scanner Nmap, Npcap addresses many of the shortcomings of WinPcap. It offers better performance, enhanced support for modern Windows operating systems, and additional security features. Npcap is designed to be a drop-in replacement for WinPcap, providing compatibility with software that was initially built for WinPcap.
Key differences between WinPcap and Npcap
- Maintenance and Support: WinPcap has not been updated since 2013, leading to compatibility issues with newer Windows versions. Npcap receives regular updates and support, providing better reliability and performance.
- Compatibility with Modern Windows: WinPcap struggles with the latest Windows 10 updates. Npcap is optimized for the newest Windows Operating Systems, ensuring smooth functioning and enhanced capabilities.
- Performance: WinPcap has limitations in performance on Windows 10. Npcap operates at higher speeds and make better use of modern CPU architectures.
- Security Features: WinPcap lacks modern security enhancements. Npcap includes improved security measures, reducing vulnerabilities during packet capture.
- Loopback Traffic: WinPcap cannot capture loopback traffic (traffic sent from the device to itself). Npcap can capture loopback packets, a key feature for certain network analysis tasks.
- Power Efficiency: With WinPcap, power efficiency was not prioritized. Npcap is designed to use less power, making it ideal for use on laptops and other battery-powered devices.
- Capture Filter Language: WinPcap uses the BPF (Berkeley Packet Filter) for filtering packets. Npcap also uses BPF but with enhanced features and better implementation.
- Raw 802.11 Packet Capture: WinPcap does not support raw 802.11 packet capture, while Npcap has this capability, which is essential for wireless network analysis.
Key similarities between WinPcap and Npcap
- Purpose: Both WinPcap and Npcap are designed to capture and transmit network packets on Windows operating systems.
- Compatibility with Software: Software built for WinPcap is generally compatible with Npcap, thanks to Npcap’s design as a drop-in replacement.
- Packet Filtering: Both libraries use the Berkeley Packet Filter (BPF) to filter packets at the kernel level.
- Developer Base: Npcap was developed by the same team that created Nmap and maintained WinPcap, ensuring continuity in quality and expertise.
- Open Source: Both WinPcap and Npcap are open-source, which means their source codes are publicly available for examination and modification.
- Documentation: Comprehensive documentation is available for both libraries, aiding developers in robustly implementing network capture functionalities.
Benefits of Using WinPcap Over Npcap
- Stability Over Time: WinPcap has been around for many years, and its long history means it is well-tested and reliable for the systems it was designed for.
- Compatibility with Older Software: Some older software or legacy systems were explicitly built to work with WinPcap, making it the preferred choice for maintaining compatibility.
- Known Issues: Any bugs or issues within WinPcap are well-documented due to its long presence, which can make troubleshooting more straightforward.
- Lower Learning Curve: Developers familiar with WinPcap may find it easier to work with due to existing knowledge, reducing the learning time needed.
- Consistent Performance: On older Windows versions, WinPcap provides consistent performance, making it suitable for systems that haven’t upgraded.
- Community Support: Despite its age, WinPcap still has an active community of users providing support and solutions through forums and other resources.
- No Licensing Fees: WinPcap is completely free to use without any licensing fees, which can be a factor for budget-restricted projects.
Limitations of WinPcap Compared to Npcap
- Lack of Modern Support: WinPcap is not compatible with the latest versions of Windows, leading to significant compatibility issues.
- No New Features: The development and updates for WinPcap stopped in 2013, meaning no new features or improvements have been made since then.
- Security Vulnerabilities: As WinPcap lacks modern security features, it is more vulnerable to exploitation.
- Unavailable for Latest Windows: Users on Windows 10 or later may find WinPcap non-functional or unstable due to lack of updates.
- Limited Performance: WinPcap does not leverage the enhancements in newer CPU architectures and lacks performance optimizations.
- No Loopback Traffic Capture: WinPcap cannot capture loopback traffic, which can be crucial for advanced network troubleshooting.
- Power Consumption: It is less efficient in terms of power usage, making it unsuitable for laptops or battery-dependent devices.
Benefits of Choosing Npcap Over WinPcap
- Active Development: Npcap is under continuous development, receiving regular updates and improvements.
- Modern System Compatibility: Npcap works seamlessly with the latest Windows versions, including Windows 10.
- Better Performance: Npcap takes advantage of modern CPU architectures and offers higher performance levels.
- Enhanced Security: Npcap includes advanced security features, minimizing vulnerabilities during packet capture.
- Loopback Traffic Capture: It can capture loopback traffic, essential for testing and monitoring traffic sent internally within the host.
- Reduced Power Usage: Npcap is designed with power efficiency in mind, making it ideal for portable computers.
- Better Filtering: Npcap offers improved BPF (Berkeley Packet Filter) implementation, enhancing packet filtering capabilities.
Drawbacks of Npcap Compared to WinPcap
- Learning Curve: For developers accustomed to WinPcap, Npcap may introduce new elements, requiring additional time to understand.
- Compatibility Issues: While most software works with Npcap, some applications designed specifically for WinPcap might encounter issues.
- Licensing Costs: The professional version of Npcap may come with licensing fees, which can be a drawback for budget-conscious projects.
- Newer Software Bugs: As relatively newer software, Npcap might have undiscovered bugs or issues yet to be addressed.
- Community Support: While growing, the Npcap community is not as large as WinPcap’s, potentially leading to fewer user-contributed resources.
- Installation Overheads: Users might find Npcap’s installation process more complex, particularly when dealing with security features and compatibility settings.
When WinPcap is Preferable Over Npcap
- Use with Legacy Systems: WinPcap is a better fit for older systems or networks running legacy applications that were specifically designed to work with it.
- Existing Infrastructure: For environments where WinPcap has been long deployed and is deeply integrated, switching to Npcap might involve significant effort.
- Familiarity: Network administrators and developers who have long relied on WinPcap may prefer it due to familiarity and established workflows.
- Low or No Budget: Organizations with strict budget constraints might prefer WinPcap since it is completely free, without any licensing fees.
- Known Stability: If stability is more critical than new features, the tried-and-tested nature of WinPcap on older Windows systems can be a benefit.
- Community Solutions: The longstanding community around WinPcap might offer more extensive and time-tested solutions for certain specialized needs.
When Npcap is Preferable Over WinPcap
- Latest Windows Compatibility: Environments utilizing the latest Windows versions will find Npcap more stable and compatible.
- Performance Needs: For tasks requiring high performance and efficiency, Npcap offers better speed and use of modern CPU features.
- Enhanced Security: When security is a primary concern, Npcap’s modern security features can provide additional safety during network captures.
- Loopback Traffic: Scenarios requiring the capture of loopback traffic will benefit from Npcap’s ability to do so.
- Wireless Networks: For advanced wireless network analysis, Npcap’s ability to capture raw 802.11 traffic is invaluable.
- Power Efficiency: Npcap’s design makes it more power-efficient, making it suitable for portable devices like laptops.
- Active Development: Environments requiring regular updates and support will benefit from Npcap’s active development and maintenance.
Features of WinPcap vs Features of Npcap
- Packet Capturing:
WinPcap: Known for reliable packet capturing on supported Windows versions.
Npcap: Offers improved packet capturing performance and compatibility with modern systems. - Loopback Traffic:
WinPcap: Does not support loopback traffic capture.
Npcap: Can capture loopback traffic, useful for various diagnostic scenarios. - Security Enhancements:
WinPcap: Lacks modern security features.
Npcap: Incorporates advanced security measures to minimize risks. - Performance:
WinPcap: Sufficient for older systems, but lacks modern optimizations.
Npcap: Higher performance and better resource utilization on new hardware. - Wireless Packet Capture:
WinPcap: Limited to standard wired network captures.
Npcap: Supports raw 802.11 packet capture for wireless networks. - Power Efficiency:
WinPcap: Consumes more power, not ideal for battery-operated devices.
Npcap: Designed to be power-efficient, suitable for laptops and tablets. - Development and Support:
WinPcap: No longer maintained, with no new features or fixes.
Npcap: Actively developed and supported, ensuring regular enhancements.
Historical Context and Evolution before continuing
The Rise of WinPcap
WinPcap emerged during an era when comprehensive packet capture tools were scarce for the Windows platform. It filled a significant gap, becoming a staple in networking labs, research, and industry applications. The library allowed applications to capture and analyze network traffic efficiently, aiding in troubleshooting and network design. With its simple API and comprehensive documentation, developers quickly adopted WinPcap, cementing its place in the network toolkit arsenal.
Over time, WinPcap’s broad acceptance was due to its reliability and extensive community support. Even though the last update was released in 2013, many network administrators still use it for tasks suited to older systems. Its legacy continues to influence modern network capture tools, highlighting the technology’s long-lasting impact.
Birth and Growth of Npcap
Npcap was created to address the evolving needs of modern network analysis tools. Recognizing the limitations of WinPcap on newer Windows versions, the developers of Nmap took the initiative to build a fresher, more robust capture library. Introduced with a focus on performance and compatibility with modern operating systems, Npcap quickly gained traction.
Leveraging lessons learned from WinPcap’s development, Npcap incorporated newer security features and performance enhancements. It drew attention from both developers and network professionals, offering a sustainable solution with active maintenance. This ensured that the network tools stayed relevant to current and future technological advances.
Integration into Network Analysis Tools
WinPcap’s versatility allowed it to integrate seamlessly with many network analysis tools available at the time. Popular applications like Wireshark and Snort benefited greatly from its capabilities, offering users detailed packet data for network troubleshooting and security analysis. This ease of integration contributed to WinPcap’s wide usage and acceptance.
Npcap carried forward this legacy, quickly becoming compatible with the same tools. Its modern features and backward compatibility made it an attractive upgrade. Tools that previously relied on WinPcap could transition to Npcap without significant modifications, ensuring continuity in network analysis operations.
Practical Applications and Use Cases before continuing
Implementing WinPcap in Network Education
WinPcap has been extensively used in educational environments, teaching network concepts, protocols, and troubleshooting techniques. Its straightforward installation and operation made it ideal for classrooms and labs. Students could easily capture live traffic, analyze different protocol layers, and understand network behavior in real-world scenarios.
Educational institutions often chose WinPcap due to its stability on older systems used for teaching purposes. It helped bridge the gap between theoretical knowledge and practical skill by providing a hands-on learning experience. Many network professionals first encountered packet capture using WinPcap during their studies, forming a lasting impression.
Npcap in Cybersecurity Training
The rise of cybersecurity threats highlighted the need for modern tools like Npcap in training environments. Students and professionals studying cybersecurity could benefit from Npcap’s ability to capture and analyze current network traffic, even on the latest Windows systems. Its enhanced performance and security features made it a preferred choice for teaching advanced network defense and intrusion detection techniques.
Npcap’s compatibility with cybersecurity tools facilitated the development of comprehensive training programs. Instructors could demonstrate real-time threats, capture attack patterns, and develop strategies using cutting-edge technology. This practical knowledge equipped students with the skills needed to tackle contemporary security challenges.
Network Performance Monitoring
WinPcap has enabled network performance monitoring for businesses wanting to ensure optimal network operations. It allowed IT teams to capture data, analyze network performance, identify bottlenecks, and resolve issues efficiently. Reliable packet capture helped maintain smooth network operations and ensured high availability.
Npcap continues this role by offering enhanced capabilities, especially on newer systems. Its power efficiency and updated functionality mean that network performance monitoring can be more effective and less resource-intensive. Organizations benefit from real-time insights, leading to proactive network management and reduced downtime.
FAQs
Can Npcap be used as a drop-in replacement for WinPcap?
Yes, Npcap is designed to be a drop-in replacement for WinPcap. Most applications that work with WinPcap will also work seamlessly with Npcap without requiring any modifications. Npcap offers improved features and better support for modern systems, making it a suitable upgrade.
Is Npcap free for commercial use?
Npcap is free for personal and educational use but may require a commercial license for business or government use. The developers offer different licensing options depending on the scale and purpose of use. Always check the licensing terms before deploying Npcap in a commercial or organizational environment.
Does Npcap support Windows versions prior to Windows 10?
Npcap primarily supports Windows 10 and newer versions. While it may work on some older versions of Windows, it is optimized for modern systems. WinPcap, on the other hand, is more compatible with older Windows versions but lacks support for the latest updates.
Can WinPcap capture wireless traffic?
WinPcap has limited capabilities when it comes to capturing wireless traffic. It is mainly designed for wired network traffic analysis. Npcap, on the other hand, supports capturing raw 802.11 wireless traffic, making it more versatile for wireless network analysis.
How is Npcap more secure than WinPcap?
Npcap incorporates several modern security features that reduce vulnerabilities during packet capture. It supports user-mode packet capture, which minimizes the risks associated with kernel-mode operations. These enhancements make Npcap a safer option for network monitoring and analysis.
Is there community support available for Npcap?
Yes, Npcap has a growing community of users and developers who contribute to forums, provide support, and share solutions. While it may not be as extensive as the WinPcap community, it is rapidly expanding and offers valuable resources for troubleshooting and development.
Can I install both WinPcap and Npcap on the same machine?
Installing both WinPcap and Npcap on the same machine is not recommended as it may cause conflicts. It is advisable to use one or the other, depending on your system requirements and compatibility needs. If you need to transition from WinPcap to Npcap, ensure that WinPcap is uninstalled first.
What tools are compatible with both WinPcap and Npcap?
Many popular network analysis tools like Wireshark, Nmap, and Snort are compatible with both WinPcap and Npcap. These tools benefit from Npcap’s modern features while retaining backward compatibility with WinPcap. This ensures seamless integration regardless of which packet capture library is in use.
WinPcap vs Npcap Summary
WinPcap and Npcap each offer valuable capabilities for network packet capture and monitoring. WinPcap is preferred for its stability and compatibility with older systems, while Npcap brings modern features, better performance, and enhanced security. Both libraries have strong community support and integration with popular network tools, making them essential for various network analysis and cybersecurity tasks. Choosing between them depends on specific needs, system compatibility, and performance requirements. Npcap is suitable for modern setups, while WinPcap remains relevant in legacy environments. Understanding their features helps in selecting the right tool for effective network analysis.
| Aspect | WinPcap | Npcap |
|---|---|---|
| Maintenance and Support | No longer updated since 2013 | Actively maintained and updated |
| Compatibility with Windows | Best for older versions, struggles with Windows 10 | Works seamlessly with Windows 10 and newer |
| Performance | Sufficient for older systems, lacks modern optimizations | Higher performance and better architecture use |
| Security | Lacks modern security measures | Enhanced security features |
| Community Support | Long-standing community | Growing and active community |
| Feature: Loopback Traffic Capture | Cannot capture loopback traffic | Captures loopback traffic |
| Cost | Free to use | Free for personal, licenses for commercial |
| Power Efficiency | Less efficient in power usage | Designed to be power-efficient |
| Raw 802.11 Packet Capture | Does not support | Supports raw 802.11 capture |
| Use in Education | Widely used in network courses and training | Used in modern cybersecurity training |
| Older Systems Compatibility | Suitable for legacy environments | Optimized for modern infrastructures |
Capturing Wireless on Windows was always problematic, because other than on Linux or Mac it wasn’t possible to activate Monitor mode on the WiFi cards to capture the radio layer. All you could do was capture packets on your WiFi card from the Ethernet layer and up. That’s unless you spent money on the now discontinued AirPCAP USB adapters. But now there is a silver lining on the horizon in the form of the npcap library.
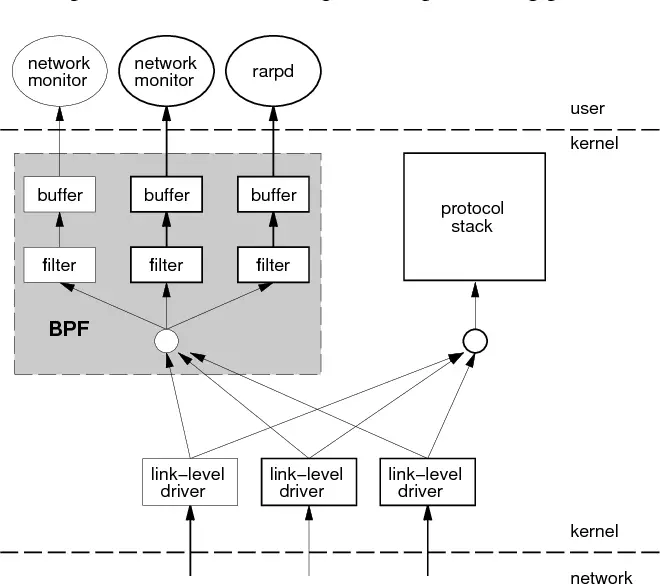
I have to admit that capturing wireless traffic isn’t my strong suit. Dealing with radio waves is a whole different topic than picking up packets from a cable, so there’s a different set of skills required to troubleshoot WiFi issues. But at least I know that there’s a difference between being able to use “Monitor Mode” and not being able to. Of course I can capture on a WiFi card, e.g. picking up packets like this on my “Wi-Fi 2” card:
Figure 1 – “Wireless” capture without monitor mode
As you can see, the capture looks just like a normal Ethernet capture would. There’s nothing related to the radio layer, so troubleshooting the wireless connectivity is not possible this way. To get the radio layer information, you need at least three things (other than Wireshark, of course):
- A WiFi card that supports monitor mode.
- The npcap capture libraries (instead of WinPCAP).
- A tool to enable monitor mode
Requirement 1 – a WiFi card with monitor mode
Unfortunately, not all WiFi cards support monitor mode on Windows. There’s a matrix available that you can use to check if your card is supported: https://secwiki.org/w/Npcap/WiFi_adapters.
I use either Alfa cards or, in this case, a NetGear A6210, which I bought at a local electronics store.
Requirement 2 – the npcap libraries
Since Wireshark 3.0 came out WinPCAP is no longer the default capture library installed. Instead, the npcap libraries are used, which replace the discontinued WinPCAP libraries. If you want to know more about the differences between the two, check this comparison. If you recently installed Wireshark 3.x (or later) you should automatically have replaced WinPCAP with npcap, unless you didn’t allow the installer to do that. Important: you need to make sure “Support raw 802.11 traffic (and monitor mode) for wireless adapters” is checked:
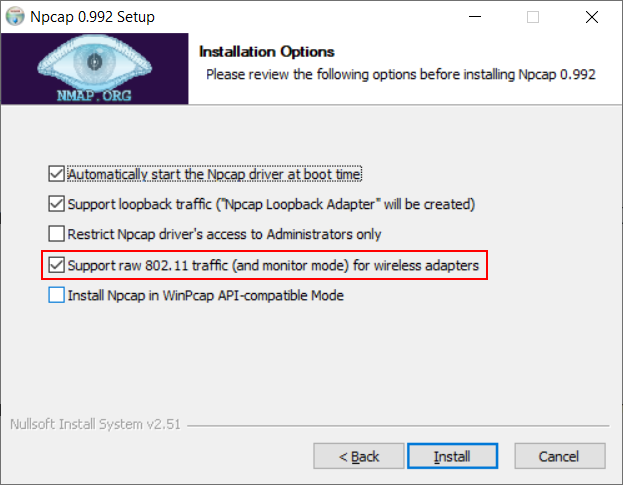
Figure 2 – npcap Installation Options
Requirement 3 – A tool to enable monitor mode
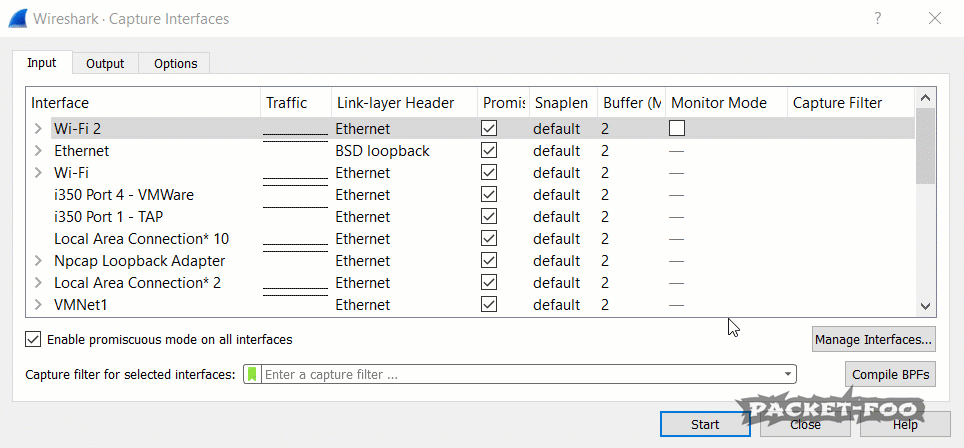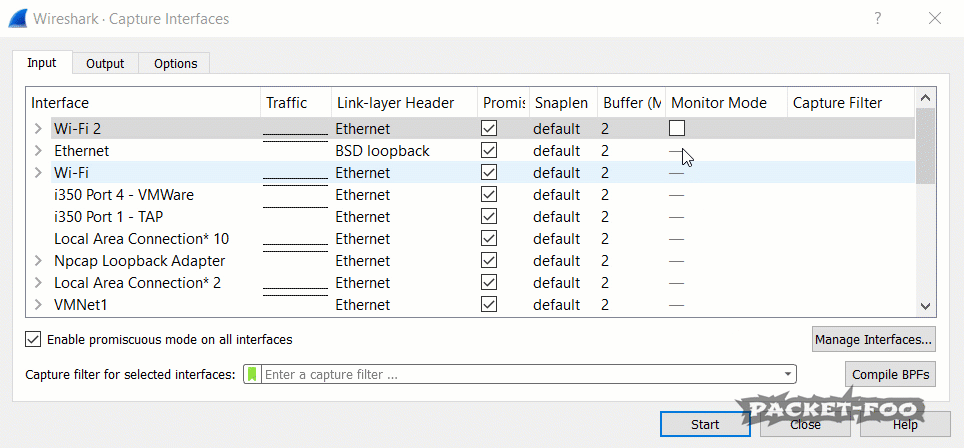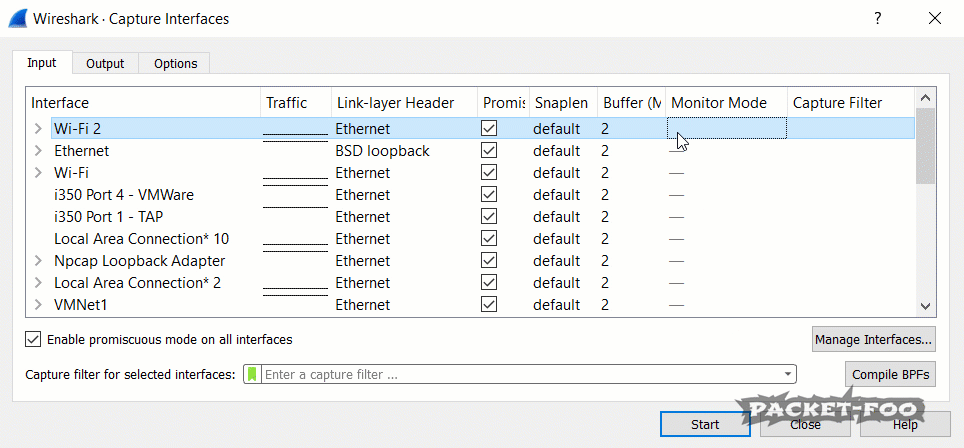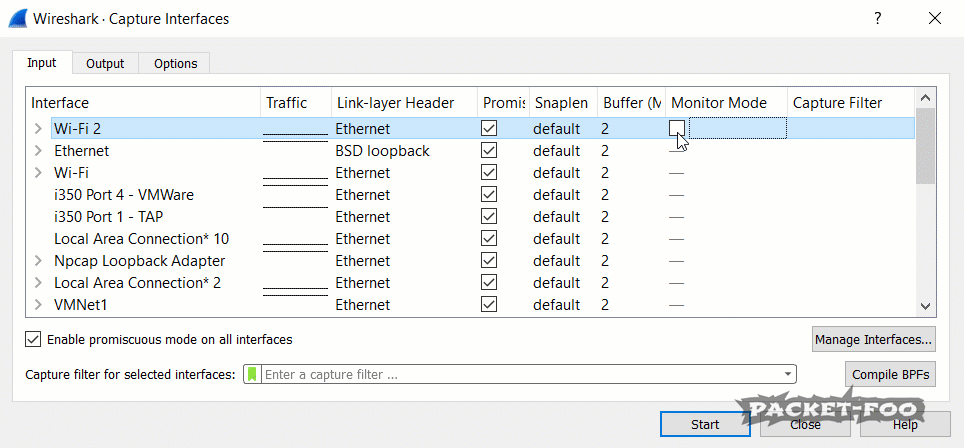
Figure 3 – enabling Monitor Mode fails
If you run Wireshark, you’ll notice that you have a “Monitor Mode” checkbox in the capture interface dialog for your WiFi cards. You can open that dialog from the main menu via “Capture” -> “Options” or by pressing CTRL-K. Unfortunately, even with npcap installed correctly it doesn’t seem to work if you click it (at least in my case), because the check mark disappears again after a short moment.
I’m not sure if that’s normal, but as far as I found out Wireshark can’t modify that setting because it doesn’t have the sufficient privileges to do that. You can either run Wireshark in administrative mode – which I strongly advise against, because it could allow malicious packets to compromise your system. Check out this blog post about “Attacking Wireshark” for details.
The much better plan is to use the wlanhelper utility in an elevated command prompt, which is why I added it specifically to the list of requirements. Fortunately, this comes as part of the npcap installation and is called wlanhelper.exe. You can find it in C:\Windows\System32\Npcap\
Check which mode your WiFi card is in using the “wlanhelper.exe” tool. You should run a command line prompt as administrator and change into the directory “C:\Windows\System32\npcap”. To check the current WiFi card mode, run this command (replace “Wi-Fi 2” with the name of your network card you want to manage):
C:\Windows\System32\Npcap>wlanhelper "Wi-Fi 2" mode managed
“Managed” is the default mode that your card should usually be in. It means that it is ready to be used for normal WiFi connectivity. To put it into monitor mode you use the following command:
C:\Windows\System32\Npcap>wlanhelper "Wi-Fi 2" mode monitor Success
But you may also see a result like this:
C:\Windows\System32\Npcap>WlanHelper.exe "Wi-Fi 2" mode monitor Error: SetWlanOperationMode::SetInterface error, error code = 5 (Access is denied) Failure
As you can see we got an error back, which is most likely caused by the fact that the command line prompt wasn’t started as administrator – so if you get this, close your command prompt and start it again, as administrator. If you’re not sure how to do that, follow these steps:
- Press CTRL & ESC to open the start menu
- type “cmd”, which should find the “Command Prompt” icon
- Click “Run as Administrator” or (if you want to impress people standing behind you) press CTRL & Shift & Enter to launch the icon in administrative mode.
- Confirm the User Access Control prompt
Now, we we run Wireshark again, we can “turn on” monitor mode (which we already did; we’re just telling Wireshark to try it to make it realize it works now):
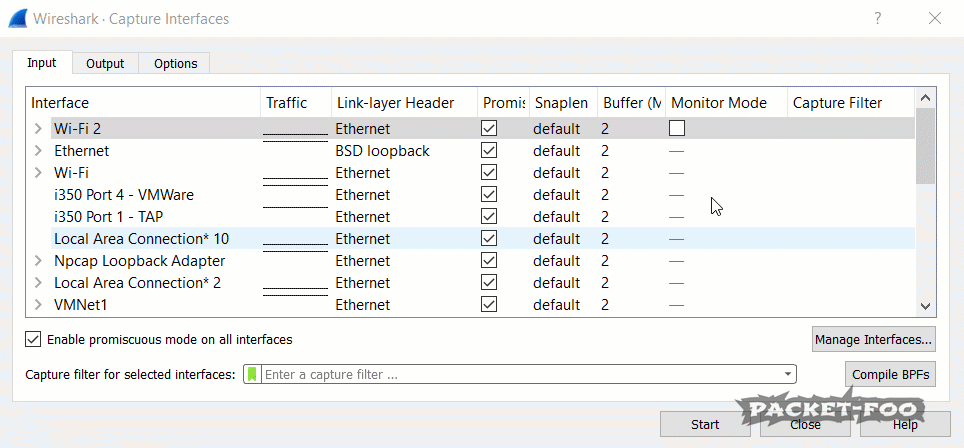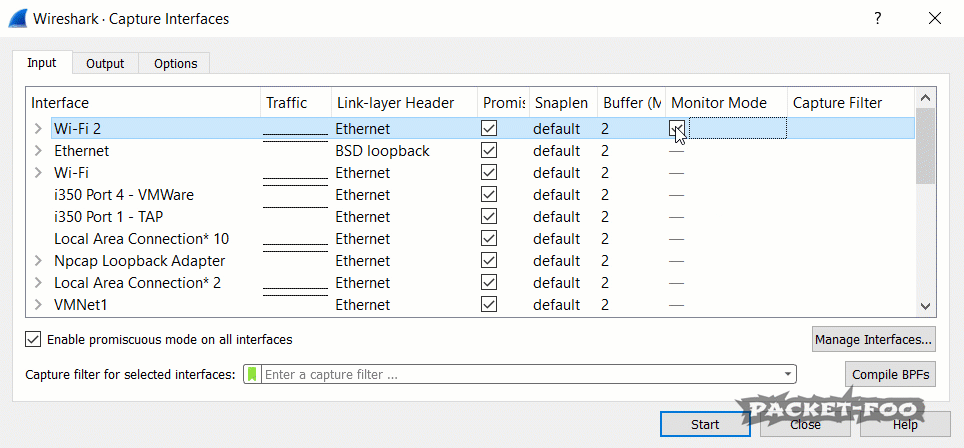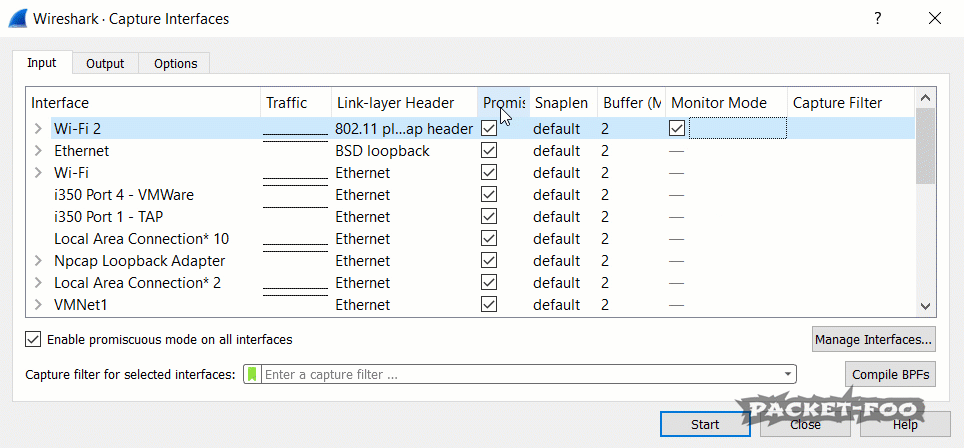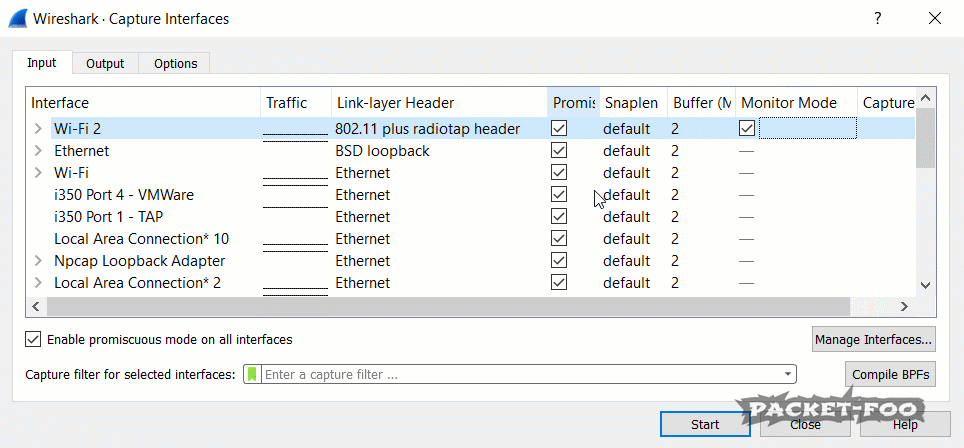
Figure 4 – enabling Monitor Mode works
As you can see, the “Link-layer Header” changes from “Ethernet” to “802.11 plus radio tap header”, which tells us that we’re now going to capture radio layer information as well. Now, when we start a capture on a card like that, we’ll see a different story:
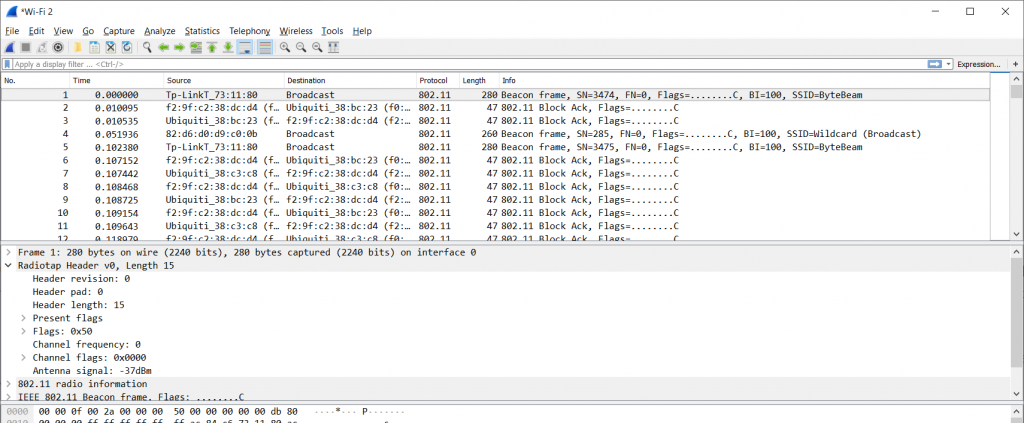
Figure 5 – Capturing with Monitor Mode enabled
We get a ton of management frames, and we also see the typical “Radiotap Header” that tells us about the radio layer. Exactly what we wanted.
Changing channels
One thing that will probably bug you is that Wireshark 3.x doesn’t yet come with a WiFi toolbar, which allows to change channels in a convenient way from the GUI. Unfortunately you’ll have to change channels manually until that problem is solved, and you can do that (again) with the help of the wlanhelper utility, using the according commands:
C:\Windows\System32\Npcap>wlanhelper
WlanHelper for Npcap 0.992 ( http://npcap.org )
Usage: WlanHelper [Commands]
or: WlanHelper {Interface Name or GUID} [Options]
OPTIONS:
mode : Get interface operation mode
mode <managed|monitor|master|..> : Set interface operation mode
modes : Get all operation modes supported by the interface, comma-separated
channel : Get interface channel
channel <1-14> : Set interface channel (only works in monitor mode)
freq : Get interface frequency
freq <VALUE> : Set interface frequency (only works in monitor mode)
modu : Get interface modulation
modu <dsss|fhss|irbaseband|ofdm|hrdsss|erp|ht|vht|ihv (VALUE)|..> : Set interface modulation
modus : Get all modulations supported by the interface, comma-separated
Final Words
Capturing Wireless on Windows got a lot easier now, and with npcap it’s also possible to capture on more recent cards than the old WinPCAP adapters which stopped at the 802.11n technology as far as I know. One thing to keep in mind: capturing in monitor mode means that the card becomes a “receive-only” card. So don’t be surprised when you lose connectivity if you have only one WiFi card in your system. If you need to stay connected to a wireless network while capturing it you need two cards – one in managed mode, one in monitor mode.
