2022-02-03
·
1 мин. для прочтения
При подключении по ssh получаю сообщение no matching host key type found. Their offer: ssh-rsa,ssh-dss.
Содержание
1 Описание ситуации
- После перехода на openssh-8.8 при подключении к серверам со старыми версиями системы появляется сообщение типа: no matching host key type found. Their offer: ssh-rsa,ssh-dss.
- Старый ssh поддерживал механизмы ssh-rsa и ssh-dss, а в новой версии их отключили.
2 Решение
- Будем считать, что мы подключаемся к хосту
192.168.0.10.
2.1 Однократное подключение
- Зададим алгоритм подключения как опции командной строки:
ssh -oHostKeyAlgorithms=+ssh-rsa root@192.168.0.10
2.2 Конфигурация для конкретного хоста
- Создайте файл конфигурации
~/.ssh/config: - Зададим конфигурацию конкретного хоста в файле
~/.ssh/config:Host 192.168.0.10 HostKeyAlgorithms=+ssh-rsa PubkeyAcceptedKeyTypes +ssh-rsaРаспечатка 1:
~/.ssh/config
2.3 Конфигурация для группы хостов
- Можно задать группу хостов в виде шаблонов командной строки (wildcards).
- Например, правило для сети:
Host 192.168.0.* HostKeyAlgorithms=+ssh-rsa PubkeyAcceptedKeyTypes +ssh-rsaРаспечатка 2:
~/.ssh/config - Можно задать привило для всех хостов:
Host * HostKeyAlgorithms=+ssh-rsa PubkeyAcceptedKeyTypes +ssh-rsaРаспечатка 3:
~/.ssh/config
- Например, правило для сети:
Эта ошибка возникает при подключении к серверу, который принимает для аутентификации RSA-ключи, но используемый тобой ключ сгенерирован алгоритмом, отличным от RSA.
Всё очень просто: достаточно в локальном файле ~/.ssh/config указать следующее:
Host *
# здесь могут быть и другие настройки, но важно добавить только эти:
PubkeyAcceptedAlgorithms +ssh-rsa
HostkeyAlgorithms +ssh-rsaПерезагружать ничего не надо. Можно сохранять файл и сразу стучаться на сервер и скорее всего он тебя пустит, если ранее ты к нему уже подключался и остальные настройки корректны.
Если у тебя нет RSA-ключа, то, помимо указанного выше, также необходимо его сгенерировать следующей командой:
ssh-keygen -t rsa -b 4096Программа будет просить у тебя дополнительные данные и парольную фразу. Они опциональны, всё можно протыкать Enter на каждый вопрос и оставить всё по дефолту (но это твоя совесть и ответственность).
После генерации ключа тебе необходимо его прописать на удалённой машине, к которой ты собрался подключаться. Для этого нужно скопировать содержимое файла ~/.ssh/id_rsa.pub (по умолчанию) в файл ~/.ssh/authorized_keys удалённой машины или использовать веб-интерфейс того сервиса, который позволяет тебе подключаться по SSH (например, GitHub).
А вообще, уже давно пора отказываться от RSA-ключей:
Unable to negotiate with 192.0.2.1 port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
Have you come across an error like this when trying to SSH into a switch or server? It happens when the SSH server and your SSH client disagree on what algorithms they support. By default, newer versions of OpenSSH don’t support older, less secure algorithms. This becomes a more prevalent problem as SSH clients update to newer versions and your switches and servers remain on older ones.
Don’t worry, though. You can enable support for these algorithms in your SSH client configuration for good!
Configuration Locations
First, lets locate where your SSH client configuration is. This is relatively the same between all operating systems.
- Windows:
C:\Users\<username>\.ssh\config - macOS:
/Users/<username>/.ssh/config - Linux:
/home/<username>/.ssh/config
If this folder and/or file doesn’t exist, you can create them.
Windows (cmd.exe)
1 2 3 4 |
C:\Users\cne> mkdir %HOMEPATH\.ssh C:\Users\cne> cd %HOMEPATH%\.ssh C:\Users\cne\.ssh> copy NUL config C:\Users\cne\.ssh> notepad config |
Windows (Powershell)
1 2 3 4 |
PS C:\Users\cne> mkdir ~\.ssh PS C:\Users\cne> cd ~\.ssh PS C:\Users\cne> New-Item -Path config -ItemType File PS C:\Users\cne> notepad config |
macOS
1 2 3 4 |
cne@mcnc ~ % mkdir -m 700 ~/.ssh cne@mcnc ~ % cd ~/.ssh cne@mcnc .ssh % touch config cne@mcnc .ssh % open config |
Linux
1 2 3 4 |
cne@mcnc:~$ mkdir -m 700 ~/.ssh cne@mcnc:~$ cd ~/.ssh cne@mcnc:~/.ssh$ touch config cne@mcnc:~/.ssh$ nano config |
SSH Settings
There are several errors you may run across while connecting to older SSH servers. The most common settings related to these are KexAlgorithms (key exchange), HostKeyAlgorithms, Ciphers and MACs (message authentication codes).
KexAlgorithms
Key echange algorithms are used to exchange the secret key that the SSH server and client will use to encrypt the traffic between them. The error you’ll see is much like this:
Unable to negotiate with 192.0.2.1 port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
The key words here are no matching key exchange method found. The server supports the algorithms listed, which you must enable at least one of to communicate with it. You can do this by copying the offers and placing them in your config file with the configuration name KexAlgorithms and using the + to add them. Do NOT forget the +, or you’ll disable the defaults.
1 |
KexAlgorithms +diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
|
You can list all the key exchange algorithms your client supports with ssh -Q kex:
1 2 3 4 5 6 7 |
C:\Users\cne> ssh -Q kex diffie-hellman-group1-sha1 diffie-hellman-group14-sha1 diffie-hellman-group14-sha256 diffie-hellman-group16-sha512 diffie-hellman-group18-sha512 diffie-hellman-group... |
HostKeyAlgorithms
Host key algorithms specify which host key types that the server supports. The typical error looks something like this:
Unable to negotiate with 192.0.2.1 port 22: no matching host key type found. Their offer: ssh-rsa
The key words here are no matching host key type found. The server supports the algorithms listed, which you must enable at least one of to communicate with it. You can do this by copying the offers and placing them in your config file with the configuration name HostKeyAlgorithms and using the + to add them. Do NOT forget the +, or you’ll disable the defaults.
1 |
HostKeyAlgorithms +ssh-rsa
|
You can list all the host key algorithms your client supports with ssh -Q key:
1 2 3 4 5 6 7 8 9 |
C:\Users\cne> ssh -Q key ssh-ed25519 ssh-ed25519-cert-v01@openssh.com ssh-rsa ssh-dss ecdsa-sha2-nistp256 ecdsa-sha2-nistp384 ecdsa-sha2-nistp521 ssh-rsa-cert... |
Ciphers
Ciphers are used to actually do the encrypting of the traffic between client and server. An error you would see for ciphers is like this:
Unable to negotiate with 192.0.2.1 port 22: no matching cipher found. Their offer: aes256-cbc,aes192-cbc,aes128-cbc
The key words here are no matching cipher found. The server supports the ciphers listed, which you must enable at least one of to communicate with it. You can do this by copying the offers and placing them in your config file with the configuration name Ciphers and using the + to add them. Do NOT forget the +, or you’ll disable the defaults.
1 |
Ciphers +aes256-cbc,aes192-cbc,aes128-cbc
|
You can list all the ciphers that your client supports with ssh -Q cipher:
1 2 3 4 5 6 7 8 9 |
C:\Users\cne> ssh -Q cipher 3des-cbc aes128-cbc aes192-cbc aes256-cbc aes128-ctr aes192-ctr aes256-ctr aes128-gcm... |
MACs
MACs, or message authentication codes, are used to ensure that data hasn’t been tampered with before they reach their intended recipient. A MAC error looks like this:
Unable to negotiate with 192.0.2.1 port 22: no matching MAC found. Their offer: hmac-sha1
The key words here are no matching MAC found. The server supports the MACs listed, which you must enable at least one of to communicate with it. You can do this by copying the offers and placing them in your config file with the configuration name MACs and using the + to add them. Do NOT forget the +, or you’ll disable the defaults.
You can list all the MACs that your client supports with ssh -Q mac:
1 2 3 4 5 6 7 8 9 10 |
C:\Users\cne> ssh -Q mac hmac-sha1 hmac-sha1-96 hmac-sha2-256 hmac-sha2-512 hmac-md5 hmac-md5-96 umac-64@openssh.com umac-128@openssh.com hmac-sha1-etm... |
Conclusion
Depending on how old the server is, you may not have to add each of the settings listed here, but they are the most common. The configuration I have to communicate with the server used in this example looks like this:
1 2 3 |
KexAlgorithms +diffie-hellman-group-exchange-sha1 HostKeyAlgorithms +ssh-rsa Ciphers +aes256-cbc |
If you’d like to use these less secure configurations only on certain servers, you can use Host to list the hosts and/or networks like this:
1 2 3 4 |
Host 192.0.2.1 192.168.* 172.16.0.* KexAlgorithms +diffie-hellman-group-exchange-sha1 HostKeyAlgorithms +ssh-rsa Ciphers +aes256-cbc |
To fix the “no matching host key type found” error in SSH, you need to modify your SSH client configuration to accept the host key types offered by the SSH server.
This error typically occurs when your SSH client does not support or is not configured to accept the host key types provided by the server.
Example error
Unable to negotiate with X.X.X.X port 22. no matching host key type found. Their offer: rsa-sha2-512,rsa-sha2-256,ecdsa-sha2-nistp256,ssh-ed25519.
Get Your Free Linux training!
Join our free Linux training and discover the power of open-source technology. Enhance your skills and boost your career!
Start Learning Linux today — Free!
Here’s a general approach to resolving this issue:
Table of Contents
Temporarily Allow Key Type in Command
Specify the host key algorithms directly in your SSH command:
ssh -o HostkeyAlgorithms=+ssh-rsa,ssh-dss user@hostname
Or you can add these options to the SSH client configuration file.
Modify SSH Client Configuration file
To resolve SSH host key type errors, modify the SSH client configuration:
- Edit the SSH client configuration file. Use ~/.ssh/config for a specific user or /etc/ssh/ssh_config for system-wide settings.
- Add or modify the line with HostkeyAlgorithms followed by the required host key type. For example, HostkeyAlgorithms ssh-rsa.
- Save the file and retry the SSH connection to implement the changes.
Troubleshooting Steps
Identify Supported Key Types
List the key types your client supports using ssh -Q key
You can do this by running the following command in your terminal:
ssh -Q key
This will display a list of supported key types, such as ssh-rsa, ecdsa-sha2-nistp256, ssh-ed25519, etc.
Identify Server-Offered Key Types
Look at the error message you received (e.g., “no matching host key type found. Their offer: ssh-rsa,ssh-dss”). It should list the key types the server is offering.
Compare the Lists
Compare the key types from your client’s list with those offered by the server. Identify any matching key types. If there’s a match, ensure your SSH configuration is set to use one of these common key types.
Following these steps can help you modify your SSH client to accommodate the server’s host key types, resolving the error while considering security implications.
SSH Host key and How to Fix Remote Host Key Has Changed Error
Obtaining SSH Host Key Fingerprint in Linux
2 ways to Automatically Accept an SSH Host Key Fingerprint in Linux
15 SSH Best Practices Every Linux Admin Should Know
Understanding SSH config file with Examples
3 ways to fix SSH Permission denied (publickey)
Are you experiencing trouble connecting to an SSH server and seeing an error message that says “no matching host key type found. their offer: ssh-rsa”? As someone who has encountered this error, I know how frustrating it can be.
SSH authentication is crucial for secure communication, and errors like this can prevent us from accessing remote resources or systems.
In this article, I’ll explain what this error message means, the different types of Host Key offered by SSH, and the importance of selecting the correct Host Key Type. I’ll also delve into the causes of the “No Matching Host Key Type Found” error and provide solutions to fix it.
By the end of this article, you’ll better understand SSH authentication and how to troubleshoot this particular error.
Understanding Host Key Types
To start, let’s discuss what Host Key Types are. When we connect to an SSH server, it generates a public-private key pair used for authentication. The public key is stored on the server, while the private key is stored on the client. These keys are used to verify the server’s identity and ensure that we communicate securely.
Now, different types of Host Keys can be used for SSH authentication. These include ssh-rsa, ssh-dss, ecdsa-sha2-nistp256, and more. The Host Key Types offered by an SSH server can depend on its configuration, security protocols, and software version.
Selecting the correct Host Key Type when connecting to an SSH server is important. Using the wrong Host Key can lead to security vulnerabilities and, in some cases, may prevent us from connecting to the server altogether. For example, if the SSH client only supports ssh-dss keys and the server only offers ssh-rsa keys, we may see the “No Matching Host Key Type Found” error.
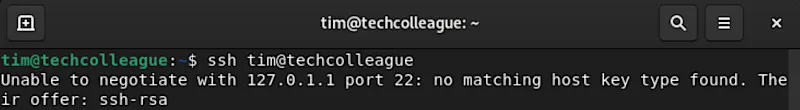
So, when connecting to an SSH server, we should always verify the Host Key Type being used and make sure it’s compatible with our SSH client. By doing so, we can ensure a secure and reliable connection.
Causes of “No Matching Host Key Type Found” Error
For several reasons, you might encounter the “No Matching Host Key Type Found” error when connecting to an SSH server. Here are some of the most common causes:
- Incompatibility between Host Key Types: The Host Key Types offered by the SSH client and server must be compatible. If the SSH client only supports one type of Host Key, and the server doesn’t offer that type, then you’ll see this error.
- Outdated or unsupported Host Key Types: Some older or less secure Host Key Types may no longer be supported by newer versions of SSH clients or servers. You may see this error if your SSH client uses an outdated or unsupported Host Key Type.
- Host Key Type mismatch in the SSH configuration: If the SSH client or server is configured to use a specific Host Key Type that doesn’t match the server’s offer, you’ll see this error.
To troubleshoot this error, you’ll need to identify which of these causes is the issue. Check your SSH client and server configurations to use compatible and up-to-date Host Key Types. You may also need to adjust your SSH configuration to match the server’s offer.
If you’re seeing the “No Matching Host Key Type Found” error when connecting to an SSH server, don’t worry! There are a few steps you can take to fix this issue:
1. Specify the Algorithm
If your SSH server is configured to use an older algorithm, you can specify it in the SSH command.
For example, to specify ssh-rsa when connecting to the SSH server, add the options -o HostKeyAlgorithms=+ssh-rsa -o PubkeyAcceptedKeyTypes=+ssh-rsa:
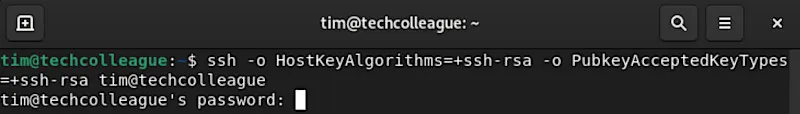
2. Change the Host Key Type in the SSH configuration
If the SSH client is configured to use a Host Key Type that doesn’t match the server’s offer, you can change it in the SSH configuration.
For example, to change the Host Key Type to ssh-rsa, you can add the following line to your SSH configuration file at ~/.ssh/config:
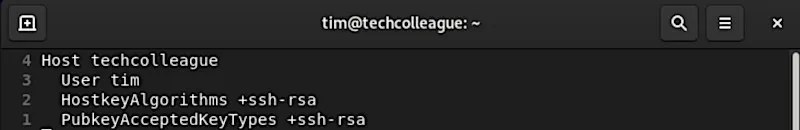
Please note that using ssh-rsa is not recommended as it is weak and deprecated. It is advisable to contact your IT department regarding the issue and switch to HTTPS until they resolve the problem or consider moving to a different platform.
Related: Fix: SSH could not resolve hostname
Conclusion
Encountering the “no matching host key type found. their offer: ssh-rsa” error when connecting to an SSH server can be frustrating, but it’s not an insurmountable problem. By understanding the Host Key Types used by your SSH client and server and the common causes of this error, you can troubleshoot and fix the issue with relative ease.
Whether it’s upgrading your SSH client or server, adding or enabling a missing Host Key Type, or changing the Host Key Type to match the server’s offer, there are several steps you can take to resolve this error and establish a secure connection to the SSH server.
By taking the time to understand and troubleshoot the “No Matching Host Key Type Found” error, you can ensure that your SSH connections are secure and reliable.
