In today’s digital landscape, cybersecurity remains a priority for organizations of all sizes. With the increasing number of devices connecting to corporate networks, ensuring compliance with security policies becomes crucial. One solution that addresses these concerns is Network Access Protection (NAP) in Windows Server. In this article, we will explore the fundamentals of NAP, how it functions, its components, and how organizations can leverage it to enhance their network security.
Network Access Protection (NAP) is a Microsoft technology introduced to help organizations enforce health policies on devices connecting to their networks. It aims to ensure that only compliant devices—those meeting specific security requirements—can access network resources. By constantly monitoring and validating the health of devices, NAP not only helps protect the network from potential threats but also contributes to the overall security posture of the organization.
Key Components of NAP
NAP consists of several key components that work together to provide a cohesive and effective network access control solution:
-
Health Policy Server (HPS): The HPS is responsible for defining the health policies that must be met for devices to gain access to the network. It evaluates the compliance status of devices against these policies.
-
NAP Enforcement Clients: These clients are software components installed on devices (including Windows PCs, mobile devices, and other endpoints) to check the compliance status of the device in real-time.
-
NAP Servers: The NAP servers can be any of the following:
- Network Policy Server (NPS): Acts as a RADIUS server that authenticates and authorizes connection requests from clients.
- VPN Servers: Control access to the organization’s internal network via secure remote connections.
- Infrastructure Devices: Such as switches and wireless access points that support NAP enforcement.
-
Compliance Evaluation: This process involves the NAP clients evaluating the system health based on the criteria defined by the health policies. It checks for up-to-date antivirus software, security updates, and other required components.
- Remediation: If a device is found to be non-compliant, NAP facilitates remediation by directing the device to a restricted access network or providing resources for the user to resolve the issues.
How NAP Works
The operation of NAP can be broken into several key steps:
-
Device Connection: When a device attempts to connect to the network, it first communicates with the NAP component, usually the Network Policy Server (NPS).
-
Health Check: The NAP client on the device performs a health check to determine if it meets the organization’s health requirements.
-
Evaluation and Enforcement: The NPS evaluates the device’s health status based on the defined policies and determines the level of access granted:
- Full Access: Compliant devices are granted full access to the network.
- Limited Access: Non-compliant devices may be given limited access to specific resources, often involving a remediation process.
- No Access: Devices failing to comply will be denied access entirely until corrective actions are taken.
- User Notification: Users are notified of their compliance status, and if non-compliant, they may receive information on how to resolve their issues.
Benefits of Implementing NAP
Implementing NAP provides several key benefits:
-
Improved Security: By ensuring that only compliant devices can access the network, organizations can minimize the risk of security breaches.
-
Reduced Vulnerability: Continuous monitoring of endpoint devices for potential vulnerabilities helps maintain a healthy IT environment.
-
Automated Remediation: NAP can facilitate automated remediation, allowing users to quickly address compliance issues without manual intervention.
- Enhanced Regulatory Compliance: Many industries have specific compliance requirements regarding data security. NAP helps organizations meet these standards by enforcing health policies.
Conclusion
Network Access Protection (NAP) in Windows Server is a robust solution for organizations seeking to improve their network security and compliance posture. By enforcing health policies and controlling access to network resources, NAP mitigates the risks associated with non-compliant devices. Implementing NAP requires planning and consideration of your organization’s specific needs, but the benefits it offers in terms of security and operational efficiency can be significant.
As cyber threats continue to evolve, investing in effective network access solutions like NAP is essential for maintaining a secure and resilient IT infrastructure. To learn more about implementing NAP in your organization, consult Microsoft’s official documentation or engage with certified IT professionals who can guide your implementation strategy.
For more technology insights, tips, and tutorials, visit WafaTech Blogs. Stay secure, informed, and ahead in the rapidly evolving world of technology!
Компания Microsoft разработала технологию NAP (Network Access Protection), которая представлена в серверной операционной системе Windows Server 2008. Данная технология предназначена для блокирования/постановки в карантин компьютеров, не соответствующих политикам, принятым в локальной сети. Таким образом обеспечивается защита локальной сети.
Технология NAP предлагает различные варианты реализации: выдача IP-адресов из различных диапазонов для «хороших» и «плохих» компьютеров; установление соединения IPSec с «хорошими» компьютерами, в то время как «плохим» компьютерам в соединении будет отказано. И самый интересный и наиболее правильный для использования в локальной сети вариант — авторизация сетевых устройств по протоколу IEEE 802.1x на коммутаторах локальной сети. Далее я расскажу, как настроить роль Network Policy Server в Windows Server 2008, а также сетевые коммутаторы для реализации NAP в сети.
Для изучения и демонстрации технологии NAP у нас в компании был собран стенд «Поликом Про», состав оборудования которого был максимально приближен к реальным условиям. В нашей лабораторной сети установлен L3-коммутатор Cisco Catalyst 3550 и L2-коммутаторы Cisco Catalyst 2950. Данные модели наиболее распространены в сетях российских предприятий. Схема собранного стенда показана на рисунке.

Как мы видим, в качестве контроллера домена используется компьютер под управлением Windows Server 2003, центр сертификации также развернут на компьютере под управлением Windows Server 2003. На компьютере под Windows Server 2008 развернута только одна роль — Network Policy Server, которая необходима для реализации технологии NAP. Такая конфигурация стенда была выбрана специально, чтобы показать, что для использования технологии NAP администраторам не придется перестраивать всю существующую инфраструктуру, а при желании достаточно лишь добавить один сервер под управлением Windows Server 2008, и можно использовать новые технологии, реализованные в новой серверной операционной системе. В качестве клиентов использовались компьютеры под управлением Windows Vista и Windows XP SP2 плюс специальный программный модуль или Windows XP SP3.
Итак, я описал собранный стенд, теперь расскажу о том, как все это будет работать. Как сказано выше, у нас есть два коммутатора и клиентский компьютер под управлением Windows Vista. Сетевые политики нашей сети требуют, чтобы на клиентском компьютере на всех сетевых интерфейсах был включен брандмауэр Windows. Изначально на нашем компьютере-клиенте брандмауэр включен. Подключим наш компьютер по сети к коммутатору 2950, и, так как наш компьютер соответствует политикам сети (брандмауэр включен), получим полный доступ к ресурсам локальной сети. Если во время работы брандмауэр выключен, то доступ к сети будет немедленно заблокирован. Давайте теперь переключимся на коммутатор 3550. Пусть брандмауэр на нашем компьютере будет выключен. После подключения к сети мы получили доступ в сеть, однако коммутатор перенаправил порт, к которому мы подключились, в карантинную сеть, не имеющую доступа к основной сети. После того как мы включим брандмауэр и наш компьютер будет соответствовать политикам сети, коммутатор перенаправит нас в основную сеть. Данная несложная демонстрация показывает, как можно защитить локальную сеть на самом первом этапе подключения к сети.
Предварительная настройка Windows Server 2008
На рисунке мы видим, что у нас есть сервер с именем DC, который работает под управлением операционной системы Windows Server 2003. Данный сервер является контроллером домена nap.demo. Также на данном сервере развернут центр сертификации Microsoft Certification Authority. Никаких других настроек не производилось.
Второй сервер, NPS, работает под управлением операционной системы Windows Server 2008. Этот сервер входит в домен nap.demo, т. е. является членом домена. Первое, что необходимо сделать при его настройке, это запросить сертификат компьютера для данного сервера. Для этого открываем консоль mmc, в меню File выбираем Add/Remove Snap-in, в появившемся окне из списка предложенных оснасток выбираем оснастку Certificates, далее нажимаем кнопку Add, в следующем окне Certificates snap-in выбираем пункт Computer Account и нажимаем Next. В новом окне выбираем пункт Local computer (the computer this console is running on) и нажимаем кнопку Finish. В окне удаления/добавления оснасток нажимаем Ok.
В оснастке Certificates щелкаем правой кнопкой мыши на пункте Personal и из контекстного меню выбираем All Tasks, Request New Certificate, после чего появится мастер запроса сертификатов. В окне Before you begin нажимаем Next. Далее из списка предложенных шаблонов нужно выбрать шаблон Computer и Enroll. После получения сообщения об успешном завершении операции нажимаем Finish.
Чтобы удостовериться, что теперь на нашем компьютере есть сертификат, открываем Certificates(Local Computer), Personal, Certificates и видим в правой панели экрана выданный нам сертификат.
Следующим шагом будет установка роли Network Policy Server. Для этого необходимо открыть Server Manager, в разделе Roles Summary выбрать пункт Add Roles и далее в окне Before You Begin нажать Next. Из списка предложенных ролей выбираем роль Network Policy and Access Services и опять нажимаем Next. В окне Network Policy and Access Services нажимаем Next. Далее, в окне Role Services следует выбрать пункт Network Policy Server и щелкнуть Next. Для запуска установки роли нажимаем кнопку Install и после завершения установки — Close.
Настройка Network Policy Server
Все предварительные действия выполнены, теперь можно приступать к настройке самого Network Policy Server. Для этого открываем Start, Programs, Administrative Tools, Network Policy Server.
На первом этапе создадим в NPS записи для наших коммутаторов Cisco Catalyst 2950 и Cisco Catalyst 3550. Разворачиваем контейнер RADIUS Clients and Servers и щелкаем правой кнопкой мыши на RADIUS Clients. Из контекстного меню выбираем пункт New RADUIS Client и в появившемся окне указываем имя клиента — Cisco Catalyst 2950. Это имя будет отображаться в окне Network Policy Server. Указываем IP-адрес клиента — 192.168.200.10 — это IP-адрес коммутатора Cisco Catalyst 2950 (см. рисунок). Далее указываем ключ — выбираем Manual и в поле Shared Secret пишем cisco (данный пароль будет ниже использоваться при настройке коммутатора). Повторяем наш пароль в поле Confirm Shared Secret и последним шагом устанавливаем флажок у параметра Access-Request. Повторяем аналогичные действия для Cisco Catalyst 3550, только имя будет, соответственно, Cisco Catalyst 3550, а IP-адрес — 192.168.200.20. В качестве Shared Secret также указываем cisco. В результате этой процедуры у нас в Network Policy Server будут зарегистрированы оба коммутатора.
Подключение — по запросу
Теперь необходимо создать политики запроса подключения, для чего переходим в раздел Policies и, щелкнув правой кнопкой мыши на пункте Connection Request Policies, из контекстного меню выбираем New. В открывшемся окне вводим имя политики — Request Policy for 2950 и нажимаем Next. В окне Specify Conditions нажимаем кнопку Add, и в разделе RADIUS Client выбираем пункт Client IPv4 Address. Нажимаем Add и в появившемся окне вводим адрес коммутатора 192.168.200.10, после чего нажимаем Ok.
Далее нажимаем Next до тех пор, пока не появится окно Specify Authentication Methods. В этом окне устанавливаем флажок Override network policy authentication settings, нажимаем кнопку Add и из появившегося списка выбираем пункт Microsoft: Protected EAP (PEAP). В окне Specify Authentication Methods нужно указать только что добавленный метод аутентификации, нажать кнопку Edit и в окне Configure Protected EAP Properties убедиться, что в Certificate issued отображается сертификат нашего компьютера NPS.nap.demo. После этого нажимаем Ok, затем дважды Next, и в окне Completing Connection Request Policy Wizard нажимаем кнопку Finish (см. экран 1).
Создаем аналогичную политику для Cisco Catalyst 3550. При создании указываем имя политики Request Policy for 3550 и в окне Specify Conditions при указании IP-адреса клиента RADIUS вводим 192.168.200.20. Остальные действия аналогичны созданию политики для Cisco Catalyst 2950.
В итоге получаем две политики Connection Request Policies.
Проверка статуса
Следующий шаг — настройка проверки состояния компьютера для определения его статуса. Сначала укажем, какие параметры должны проверяться на компьютере, — открываем контейнер Network Access Protection и выбираем System Health Validators. В панели справа выбираем Windows Security Health Validator, щелкаем на нем правой кнопкой мыши и в контекстном меню выбираем пункт Properties. В открывшемся окне нажимаем кнопку Configure. Так как на нашем стенде клиентский компьютер работает под управлением операционной системы Windows Vista, на вкладке Windows Vista выбираем те параметры, которые нам необходимы. В нашем случае для стенда мы оставим включенной только проверку состояния брандмауэра. Проверку остальных параметров проводить не будем.
Теперь необходимо создать политики проверки состояния компьютеров, которые описывают, какой компьютер и с какими параметрами считать соответствующим политикам сети, а какой — нет. Для этого перейдем в контейнер Policies и, щелкнув правой кнопкой мыши на пункте Health Policies, из контекстного меню выберем пункт New.
В окне Create New Health Policy заполняем поле Policy Name — Compliant, убеждаемся, что в поле Client SHV Checks установлен переключатель Client passes all SHV checks, и ниже устанавливаем флажок напротив Windows Security Health Validator, после чего нажимаем Ok.
Аналогичным образом создаем политику для определения компьютеров, которые не соответствуют требованиям сети. Для Client SHV Checks выбираем значение Client fails one or more SHV checks.
Политики сети
Остался последний шаг — настройка сетевых политик. На пункте Network Policies щелкаем правой кнопкой мыши и из контекстного меню выбираем пункт New. В окне Specify Network Policy Name and Connection Type указываем имя политики Full Access for 2950 и нажимаем Next. В окне Specify Conditions нажимаем кнопку Add. Из открывшегося списка выбираем пункт Health Policies из раздела Network Access. Нажимаем кнопку Add, в появившемся окне выбираем из списка значение Compliant и нажимаем Ok.
В окне Specify Conditions опять нажимаем кнопку Add. Из появившегося списка следует выбрать пункт Client IPv4 Address из раздела RADIUS Client и нажать Add. В поле запроса IP-адреса вводим значение 192.168.200.10 и нажимаем Ok. Далее в окне Specify Conditions нажимаем Next. В следующем окне Specify Access Permission выбираем пункт Access granted и нажимаем Next до тех пор, пока не увидим окно Configure Settings (см. экран 2).
В левой части окна в разделе RADIUS Attributes выбираем пункт Standard, затем в рабочей области справа нажимаем кнопку Add и из списка параметров выбираем Termination-Action, после чего нажимаем кнопку Add. В окне Attribute Information в поле Attribute Value указываем значение RADIUS-Request и затем нажимаем Ok.
Таким же образом добавляем параметр Tunnel-Medium-Type со значением параметра 802 (includes all 802 media plus Ethernet canonical format). Затем закрываем окно Add Standard RADIUS Attribute.
В окне Configure Settings в левой части окна нужно выбрать пункт NAP Enforcement из раздела Network Access Protection. В правой части окна выбираем пункт Allow full network access и нажимаем Next.
В окне Completing New Network Policy нажимаем Finish. Все, сетевая политики для доступа «правильных» компьютеров создана.
Теперь создадим политику ограниченного доступа, для компьютеров, не соответствующих политикам сети. Для этого нужно щелкнуть правой кнопкой мыши на только что созданной политике и из контекстного меню выбрать пункт Duplicate Policy. На сдублированной политике Copy Of Full Access for 2950 щелкаем правой кнопкой мыши и из контекстного меню выбираем свойства. В открывшемся окне следует заменить значения полей Policy name на значение Limited Access for 2950, затем установить флажок Policy enabled, а в разделе Access Permission выбрать значение Deny Access. Переходим на вкладку Conditions. Выбираем пункт Health Policy и нажимаем кнопку Edit. В открывшемся окне меняем значение поля Health Policies на NonCompliant, нажимаем Ok и затем нажимаем кнопку Apply. Правила для Cisco Catalyst 2950 созданы: первое правило разрешает коммутатору открывать доступ компьютера в сеть, если у него включен брандмауэр. Второе правило предписывает коммутатору заблокировать порт, к которому подключен компьютер, если на нем брандмауэр выключен.
По аналогии создаем правила для Cisco Catalyst 3550. Для ускорения создания правил будем использовать правила, определенные на предыдущих этапах. Выбираем правило Full Access for 2950, щелкаем на нем правой кнопкой мыши и из контекстного меню выбираем Duplicate Policy. Открываем свойства вновь созданного правила и исправляем значения параметров следующим образом: в поле Policy name вводим Full Access for 3550, устанавливаем флажок Policy enabled. Переходим на вкладку Conditions, выбираем пункт Client IPv4 Address, нажимаем кнопку Edit и вводим IP-адрес 192.168.200.20. Переходим на вкладку Settings, в панели справа нажимаем кнопку Add и добавляем следующие параметры: Tunnel-Pvt-Group-ID со значением Healthy и Tunnel-Type со значением Viltual LANs (VLAN). Нажимаем Ok.
Повторяя шаги, необходимые для задания политик для 2950, создаем копию правила Full Access for 3550. Открываем свойства вновь созданного правила и редактируем следующим образом: в Policy name вводим Limited Access for 3550, устанавливаем флажок Policy enabled, переходим на вкладку Conditions, выбираем пункт Health Policy и изменяем значение этого параметра на NonCompliant. Далее переходим на вкладку Settings, в рабочей области экрана в разделе Attributes изменяем значение параметра Tunnel-Pvt-Group-ID на Quarantine и нажимаем Ok. Результат представлен на экране 3. На этом настройка Network Policy Server завершена.
Финал — настройка оборудования Cisco
Теперь приступим к настройке оборудования Cisco. Список необходимых команд приведен в листинге, я лишь вкратце поясню последовательность действий. Через терминальный кабель следует подключиться к Cisco Catalyst 2950 и для начала изменить имя коммутатора, чтобы потом не запутаться, поскольку предстоит повторить такую же последовательность для модели 3550. Далее настраиваем аутентификацию и авторизацию через службу RADIUS: прежде всего, задаем настройки сервера RADIUS; он должен быть доступен через первый порт коммутатора. Далее настраиваем параметры Default VLAN (Vlan 1). Следующий шаг — настроить порты коммутатора, к которым будут подключаться клиенты. Порт 9 в листинге выбран для примера, аналогичная настройка должна выполняться для всех портов, к которым будут подключаться клиенты. На последнем шаге останется только сохранить конфигурацию.
Настройки Cisco Catalyst 3550 аналогичны настройке Cisco Catalyst 2950, только в качестве клиентского порта на нашем стенде был настроен 13-й порт коммутатора.
Роман Совалов (RSovalov@polikom.ru) — ведущий инженер компании «Поликом Про»
Introduction
Network Access Protection (NAP) is a security feature in Windows Server that allows you to control access to your network based on the health of the client computer. NAP can be used to help protect your network from viruses and other malware by ensuring that only healthy computers are allowed to access the network. In this article, we will show you how to set up NAP in Windows Server 2022.
Prerequisites
Before you begin, you will need to have the following:
- A Windows Server 2022 machine.
- An active Directory Domain.
Setting up Network Policy Server
The first thing you need to do is set up the Network Policy Server (NPS) role on your Windows Server machine. To do this, open the Server Manager and click on “Add roles and features”. On the “Before you begin” page, click “Next”. On the “Installation Type” page, select “Role-based or feature-based installation” and click “Next”. On the “Server Selection” page, select your server from the list and click “Next”. On the “Server Roles” page, select “Network Policy Server” and click “Next”. On the “Features” page, click “Next”. On the “Confirm installation selections” page, click “Install”. Once the installation is complete, click “Close”.
Configuring Network Policy Server
Now that you have the NPS role installed, you need to configure it. To do this, open the NPS console and click on “Network Policies”. On the “Network Policies” page, click “New”. On the “Create New Network Policy” page, enter a name for the policy and description (optional) and click “Next”. On the “Conditions” page, select the “Windows Groups” condition and click “Add”. On the “Select Groups” page, select the group that you want to allow access to the network and click “Add”. Once you have added the group, click “Next”. On the “Constraints” page, select the “EAP Types” constraint and click “Add”. On the “EAP Types” page, select the “Smart Card or other certificate” EAP type and click “OK”. Once you have added the EAP type, click “Next”. On the “Settings” page, select the “Grant access” radio button and click “Next”. On the “Summary” page, review the settings and click “Finish”.
Creating a Certificate Template
The next thing you need to do is create a certificate template. To do this, open the Certificate Templates console and click on “New”. On the “Welcome to the Certificate Template Wizard” page, click “Next”. On the “Select a Certificate Template” page, select the “User” template and click “Open”. On the “Specify Certificate Template Information” page, enter a name for the template and click “Next”. On the “Cryptography” page, select the “Minimum key size” and “Provider” options and click “Next”. On the “Security” page, add the “Authenticated Users” group and give it the “Read” permission. Click “Add” and then “Next”. On the “ Subject Name” page, select the “Supply in the request” option and click “Next”. On the “Extensions” page, select the “Application Policies” extension and click “Edit”. On the “Edit Application Policies” page, click “Add”. On the “Select Application Policy” page, select the “Client Auth” policy and click “OK”. Once you have added the policy, click “OK”. On the “Extensions” page, click “Next”. On the “Request Handling” page, select the “Allow private key to be exported” option and click “Next”. On the “Cryptography” page, select the “Minimum key size” and “Provider” options and click “Next”. On the “Summary” page, review the settings and click “Finish”.
Requesting a Certificate
Now that you have created the certificate template, you need to request a certificate. To do this, open the Certificate Authority console and click on “Request a Certificate”. On the “Request a Certificate” page, click “Advanced Certificate Request”. On the “Advanced Certificate Request” page, select the “Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file” option and click “Next”. On the “Certificate Template” page, select the template that you created and click “Submit”. On the “Certificate Issued” page, click “Download Certificate”. Save the certificate to your computer.
Installing the Certificate
Now that you have downloaded the certificate, you need to install it. To do this, open the Certificates console and click on “Import”. On the “Certificate Import Wizard” page, click “Next”. On the “File to Import” page, browse to the certificate that you downloaded and click “Open”. On the “Password” page, enter the password for the certificate and click “Next”. On the “Certificate Store” page, click “Next”. On the “Completion” page, click “Finish”.
Configuring NAP Client Settings
The next thing you need to do is configure the NAP client settings. To do this, open the NPS console and click on “NAP Client Configuration”. On the “NAP Client Configuration” page, select the “Windows 7 and later” option and click “Configure”. On the “Configure NAP Client Settings” page, select the “Smart card or other certificate” option and click “OK”. On the “NAP Client Configuration” page, click “OK”.
Testing NAP
To test NAP, you will need to have a client computer that is not compliant with the health policy. To do this, you can install a virus on the computer or disable the firewall. Once you have done this, try to access the network from the client computer. You should see that the client is not able to access the network. To fix this, you will need to fix the issues on the client computer and then try to access the network again. You should now be able to access the network.
Conclusion
In this article, we have shown you how to set up NAP in Windows Server 2022. We have also shown you how to create a certificate template and request a certificate. We have also shown you how to install the certificate and configure the NAP client settings. Finally, we have shown you how to test NAP.
The IT industry long ago saw the issue of
network vulnerability due to problematic computers connecting to the
network coming and has been furiously investigating solutions to enforce
company security policies physically. Network Access Control (NAC) was
created to combat this very issue. NAC provides a framework for vendors
to produce services and features that can interrogate a computer prior
to a connection to the secure, internal network and ensure a computer’s
compliance with stated health requirements and security settings.
Microsoft has introduced its version of
controlling network access with NAP, which provides an enforcement
service for health requirement policies prior to network access. NAP
offers services, components, and an application programming interface
(API) that provide an inherent solution for ensuring the health of
servers and networks running Windows Server 2008 as well as of computers
running Windows Vista and Windows XP Service Pack 3 as clients.
1. Network Access Protection Overview
Network Access Protection (NAP) provides a
platform for validating the health of computer systems prior to allowing
access to protected networks. In doing so, a level of assurance can be
attained that a computer has at least been “inspected” prior to
accessing the private network every time a new connection is made. The
validation a computer undergoes can now be logically enforced.
Prior to NAP, a typical connection from an
external computer would involve a client connecting across a public
network such as the Internet, using a VPN connection. The client
connection would initially pass through a firewall or be forwarded by a
proxy using the appropriate communication ports required by the chosen
security protocol. An authentication service would then examine the
credentials of the remote access client. If the credentials were
successfully authenticated, the client would be connected to whatever
portion of the protected network the connection was previously set up to
accomplish.
This
scenario has a major flaw. If the remote access client is exactly who
it purports to be, provides all the necessary credentials appropriately,
and performs only the tasks on the private network that the connection
was set up to do, would there still be a problem? Maybe. Suppose the
remote access client performs unintended service requests, discovery,
research, or—worse—invasive software installations without the knowledge
of the user of the computer making the remote access connection. This
has become one of the primary reasons for implementing a NAP solution.
Paul Mancuso
After spending a considerable amount of time,
effort, and money, you have deployed across an entire network the
following security services:
-
A top-of-the-line perimeter firewall device
-
An antivirus module inside the firewall device whose services you have configured to check for updates once every hour
-
An
automated update service for workstations and servers to call upon
periodically for updates to the operating system and installed
applications -
An enterprise anti-malware
service that installed anti-malware agents on all client workstations
and servers within the environment, with centralized management for
setting and configuring changes and updating installed software and
agents on deployed computers
Feeling that the enterprise has a reasonable
level of security, you go home and think that tomorrow should now be a
relatively peaceful day.
In the evening, a salesman visiting a branch
office connects his laptop to the protected network. The salesman’s
laptop is considered safe merely because it is corporate property. A
worm that was released into the wild that day had infected the corporate
offices of another corporation, where the salesman had plugged the
laptop in while delivering a presentation. The worm can now perform
functions inside the network from a device considered to be a secure
system. Tomorrow comes, and virus reports are coming out of the
woodwork.
Several factors could have caused the salesman’s
laptop to become infected. First, it is presumed that the salesman does
not alter the basic security settings of either the security software
or the operating system. Also, the laptop is part of the domain;
internal group policies were set to ensure the timely scheduling of
updates to either the operating system or the security software on all
computers, including those the salesman uses. This last presumption
leads to missed updates when the salesman is traveling and not connected
to the network.
These periodic lapses in acquiring updates
provide opportunities for infections when the salesman connects the
laptop to unknown environments. The salesman’s laptop can acquire all
kinds of Trojan horse programs, viruses, and worms. The salesman travels
back to the office, plugs the infected laptop into the protected
network, and unknowingly unleashes the malicious programming on the
laptop into the protected network. The salesman has bypassed all the
security precautions the enterprise administrator has painstakingly set
up in the network.
With a NAP solution, the possibilities of a
traveling employee or guest unleashing an infection into your secured
network are lessened. The standard communication flow from a computer
being introduced to a network for its initial connection to the network
would be altered to pass through a perimeter network as the components
of the NAP platform engage. The NAP platform would now involve an entire
NAP ecosystem with the connection request of an external client now
referred to as a NAP client. The perimeter network would still include
the same security services and devices as before, but now the NAP
client’s request for access takes a detour as the various components of
the NAP platform engage to determine the health status of the connecting
client. Figure 1 shows the difference between a traditional remote access connection and one involving a NAP platform.
Figure 1. Remote access connection comparison with and without NAP
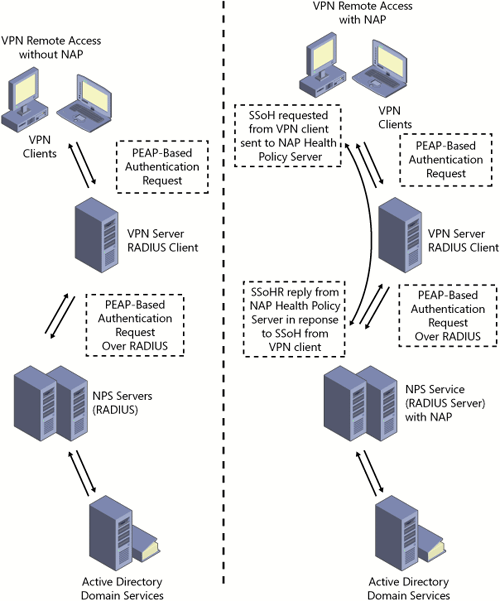
Figure 1
shows that not only are NAP components now involved in the
communication flow, but also that the NAP client might be restricted to
an external network referred to as the remediation network, where
additional servers using health resources update the client and bring it
into compliance.
A complete NAP solution involves three distinct features:
-
Health state validation
-
Health policy compliance
-
Limited access
Health state validation is the process of
validating a computer’s health and determining its compliance. If the
NAP platform is configured for a remediation network, a noncompliant
computer is restricted to only the remediation network’s subnet until it
meets compliance. If the NAP platform has been implemented initially
with logging only to quantify compliance issues, the health compliance
of a computer is logged, and it is allowed to proceed with the normal
connection routine.
To monitor and possibly enforce health policy
requirements, administrators create health policies. The health policy
component is the heart of a NAP solution. Health policies mandate the
level of software updates, operating system build, antivirus revision,
and firewall features implemented among many other possible health
compliance factors.
When computer systems do not meet the level of
health compliance necessary to connect to the private network, an
administrator can mandate one of two outcomes, either to allow the
connection and log the noncompliant issues or to shunt the connection to
a remediation network to configure and update any noncompliant aspect
of the computer. This is the limited-access feature of NAP.
Note: Network Access Quarantine
Limited access has some similarities to Network
Access Quarantine Control, but only in one principal feature: limiting
access for noncompliant computers when making dial-up and VPN
connections. Limited access when implemented with a NAP platform
provides much capability and a standardized structure. This structure
facilitates the addition of third-party enhancements and services. NAP
also extends beyond VPN and dial-up communication to include protection
when computer systems connect on the LAN. For more information, please
visit the Cable Guy article on Network Access Quarantine at http://technet.microsoft.com/en-us/library/bb877976.aspx.
Overview of NAP Infrastructure
The NAP infrastructure for all types of enforcement provides a similar architectural overview as displayed in Figure 2. Only the devices and regions of interest to a NAP solution are pictured.
Figure 2. Overview of the NAP architecture
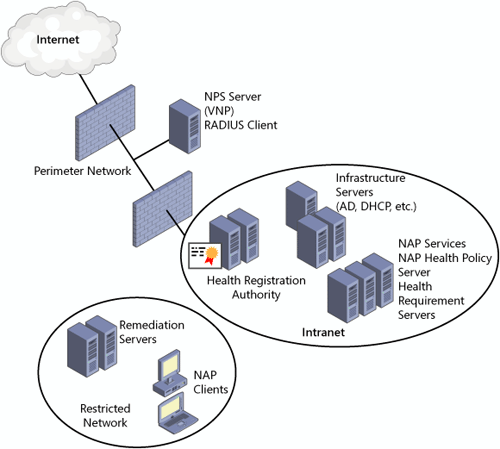
-
The
Internet lies outside the perimeter network and is separated by the
perimeter firewall. VPN clients access the internal network from this
region. -
The perimeter network is segregated by a perimeter and internal firewall.
VPN
servers reside here and provide the initial point of enforcement for a
NAP VPN enforcement point. For security purposes, no other NAP service
is needed in this location. -
The
restricted network is logically separated from the intranet for
computers that, although having passed authentication for the NAP
enforcement points that require authentication, have not yet acquired
the necessary authorization to access the secure intranet. Servers
deployed here can include quite a range of NAP support services:-
The
usual DNS, Windows Internet Name Service (WINS), Active Directory
domain controllers, and DHCP servers along with other supporting network
infrastructure devices can be deployed. -
Servers supporting software updates such as Windows Server Update Services (WSUS) can be deployed.
-
For wired switches employing 802.1x enforcement, any switch ports can be associated logically with the restricted network.
-
For
wireless access points employing 802.1x enforcement, the entire access
point might be logically associated with the restricted network because,
at any time, it can be servicing compliant and noncompliant computers.-
The
intranet is considered the secured network for most NAP enforcement
methods and contains the corporate environment. NAP IPsec enforcement
includes an additional logical boundary between two of its zones
necessary for IPsec enforcement operation.-
The
boundary network is where Health Registration Authority servers and,
possibly, NAP CAs, NPS servers, and IPsec remediation servers reside. -
The
secure network is where the remaining portion of all NAP enforcement
components resides. These components are the NAP health policy servers,
the health requirement servers, the RADIUS proxy servers, and the NPS
servers’ endpoints.
-
-
-
Where NAP Works
NAP can be implemented in any scenario in which a
computer or network device has left a network and requires a new
connection when brought back to the network. Following are specific
scenarios of this type of event.
-
Desktop computers that have been dormant for periods of time
-
Laptops for roaming users
-
Personal desktops and laptops of corporate users when connecting to the network to retrieve e-mail and other data
-
Laptops of guests
-
Laptops and desktops from users of partner firms connected by an extranet
This list comprises the general
categories in which a NAP solution would provide a level of assurance of
the health of a connected computer. Due to the diversity of these
categories, the same level of enforcement of noncompliant computers
might not be possible in all situations. Computers that are unmanaged,
such as partner computers, home computers, laptops, and those of guests
would be sent to the restricted network and, might not be required to
undergo remediation, but also would not be allowed into the private
network. Managed computers provided by the corporation could institute
automatic remediation for any of its computers moved into the restricted
network. Options to remediate would vary, depending on the situation.
Network Access Protection (NAP) is a Microsoft technology for controlling network access of a computer host based on the system health of the host, first introduced in Windows Server 2008.
With Network Access Protection, system administrators of an organization’s computer network can define policies for system health requirements. Examples of system health requirements are whether the computer has the most recent operating system updates installed, whether the computer has the latest version of the anti-virus software signature, or whether the computer has a host-based firewall installed and enabled. Connecting or communicating computers have their health status evaluated. Computers that comply with system health requirements have full access to the network. Administrators can configure health policies that make it possible to ensure that computers not in compliance with system health requirements have restricted access to the network.
Overview[]
NAP clients are computers that report system health to a NAP enforcement point. A NAP enforcement point is a computer or network access device that can require the evaluation of a NAP client’s health state and optionally provide restricted network access or communication. NAP enforcement points can be IEEE 802.1X-capable switches or VPN servers, DHCP servers, or Health Registration Authorities (HRAs) that run Windows Server 2008 or Windows Server 2008 R2. The NAP health policy server is a computer running the Network Policy Server (NPS) service in Windows Server 2008 or Windows Server 2008 R2 that stores health requirement policies and provides health evaluation for NAP clients. Health requirement policies are configured by the administrator and can include settings that require that NAP client computers have the latest antivirus definitions and security updates installed, a personal firewall enabled, and other settings.
When a NAP-capable client computer contacts a NAP enforcement point, it submits its current health state. The NAP enforcement point sends the NAP client’s health state to the NAP health policy server for evaluation using the RADIUS protocol. The NAP health policy server can also act as a RADIUS-based authentication server for the NAP client.
The NAP health policy server can use a health requirement server to validate the health state of the NAP client or to determine the current version of software or updates that need to be installed on the NAP client. For example, a health requirement server might track the latest version of an antivirus signature file.
If the NAP enforcement point is an HRA, it obtains health certificates from a certification authority for NAP clients that are determined to be compliant with health requirements.
If the NAP client is determined to be noncompliant with health requirements, it can optionally be placed on a restricted network. The restricted network is a logical subset of the intranet and contains resources that allow a noncompliant NAP client to correct its system health. Servers that contain system health components or updates are known as remediation servers. A noncompliant NAP client on the restricted network can access remediation servers and install the necessary components and updates. After remediation is complete, the NAP client can perform a new health evaluation in conjunction with a new request for network access or communication.
NAP client support[]
A NAP client ships with Windows Vista and later Windows client operating systems. NAP client support is also included in Windows XP Service Pack 3 albeit with some limitations — no MMC snap-in (command line netsh only), no integration with Windows Security Center and no AuthIP-based IPsec enforcement (IKE-based only). Microsoft partners provide NAP clients for other operating systems such as Mac OS X and Linux. [1]
See also[]
- Access control
- Network Admission Control
- Network Access Control
- Network security
- Computer security
References[]
- ↑ XP NAP Rude Q and A: Network Access Protection team blog
External links[]
- Microsoft’s Network Access Protection Web page
- Microsoft’s Network Access Protection Web page on Microsoft Technet
- NAP Blog on Microsoft Technet
- Microsoft’s Network Access Protection Design Guide on Microsoft Technet
- Microsoft’s Network Access Protection Deployment Guide on Microsoft Technet
- Microsoft’s Network Access Protection Troubleshooting Guide on Microsoft Technet
| Microsoft Windows components | |
| Core |
|
| Management |
|
| Applications |
|
| Games |
|
| Kernel |
|
| Services |
|
| File Systems |
|
| Server |
|
| Architecture |
|
| Security |
|
| Compatibility |
|
| Edit — View |
nl:Network Access Protection
tr:Ağ Erişim Koruması
