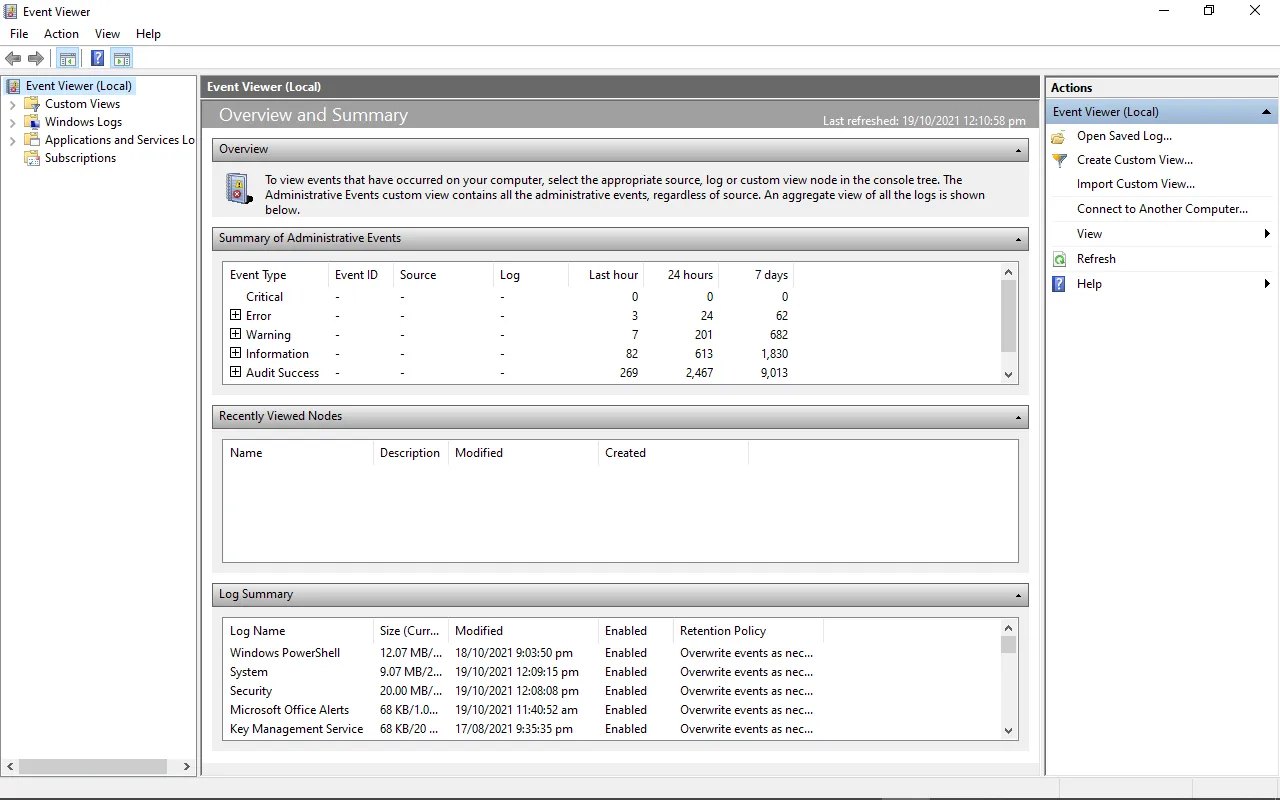
Troubleshooting a Windows server issue often comes down to checking the event logs—but finding the right information isn’t always straightforward. Windows event logs capture everything from system errors to security alerts, making them a crucial resource for diagnosing problems.
This guide focuses on what matters, helping you make sense of event logs without unnecessary complexity.
What Are Windows Event Logs?
Windows event logs are your system’s journal – they track pretty much everything that happens on your Windows servers and workstations. When an application crashes, a service stops, or someone tries to access something they shouldn’t, it all gets written here.
Think of event logs as your system’s receipts. They prove what happened, when it happened, and often why it happened.
The logging system in Windows organizes events by their source and type, making it (somewhat) easier to track down issues when things go sideways.
💡
If you’re running critical workloads on Windows Server, keeping an eye on performance metrics can save you from unexpected headaches—here’s a practical guide on Windows Server Monitoring.
Windows Event Logs Location: Where to Find Them
The actual log files live in C:\Windows\System32\winevt\Logs. But let’s be honest – nobody browses there directly.
Here’s how you access them:
Using Event Viewer
- Hit Win+R, type
eventvwr.msc, and press Enter - Or go through the longer route: Start → Administrative Tools → Event Viewer
The Event Viewer gives you a tree view of all logs, with the most common ones being:
- Application: Logs from installed software and applications
- Security: Anything security-related (login attempts, permission changes)
- System: OS and hardware events
- Setup: OS installation and updates
- Forwarded Events: Events collected from other machines (if configured)
Using PowerShell
# Get the latest 10 system events
Get-EventLog -LogName System -Newest 10
# Find all error events in the last 24 hours
Get-WinEvent -FilterHashtable @{LogName='Application'; Level=2; StartTime=(Get-Date).AddDays(-1)}
# Get events with a specific ID
Get-WinEvent -FilterHashtable @{LogName='Security'; ID=4624}PowerShell’s Get-WinEvent cmdlet is your best friend for scripting and automation. It’s faster than Get-EventLog and works with all event logs.
Log Types You Should Care About
Not all logs are created equal. Here’s what you should focus on:
Application Logs
These capture events from your apps. When your web server acts up or your database connection fails, this is your first stop.
System Logs
This is where Windows reports on itself – services starting or stopping, driver issues, and hardware problems.
Security Logs
Failed logins, permission changes, policy modifications – everything security-related lives here. If you’ve been hacked, the evidence is probably in this log.
Custom Application Logs
Many apps create their own event logs. SQL Server, IIS, and other major applications often create custom logs to avoid cluttering the main ones.
How to Read Windows Event Logs
Event logs can be overwhelming, so here’s how to cut through the noise:
Understanding Event Structure
Each event has these key parts:
| Component | What It Tells You |
|---|---|
| Level | Severity (Information, Warning, Error, Critical) |
| Date and Time | When it happened |
| Source | What generated the event |
| Event ID | Specific code for the event type |
| Task Category | Further classification by the source |
| Description | The human-readable details |
The Most Common Event IDs
Here’s a cheat sheet of event IDs you’ll see often:
| Event ID | What It Means |
|---|---|
| 4624 | Successful login |
| 4625 | Failed login attempt |
| 7036 | Service started or stopped |
| 1074 | System shutdown initiated |
| 6005/6006 | Event log service started/stopped |
| 41 | System rebooted without clean shutdown |
| 1001 | Windows Error Reporting |
Practical Tips for Log Management
Now for the real talk – how to use these logs in your DevOps workflow:
Filtering: Find the Signal in the Noise
The Event Viewer’s filter feature is good, but PowerShell is better:
# Find all errors from a specific application in the last hour
$oneHourAgo = (Get-Date).AddHours(-1)
Get-WinEvent -FilterHashtable @{
LogName='Application';
Level=2;
StartTime=$oneHourAgo;
ProviderName='Your Application Name'
}Creating Custom Views
For recurring investigations, create custom views in Event Viewer:
- In Event Viewer, click «Create Custom View»
- Set your filters (time range, event level, log, source, etc.)
- Name it something descriptive like «Failed Logins» or «Application Crashes»
Log Forwarding: Centralize Your Logs
For multi-server environments, set up log forwarding:
# On the collector server
wecutil qc /q
# On source servers
winrm quickconfigThis setup is for configuring Windows Event Forwarding (WEF), where logs from multiple source servers are sent to a central collector server.
wecutil qc /q(Run on the collector server)- Enables the Windows Event Collector service, allowing the server to receive logs from other machines.
- The
/qflag ensures it runs without prompting for confirmation.
winrm quickconfig(Run on source servers)- Configures Windows Remote Management (WinRM), which is required for event forwarding.
- Starts the WinRM service and sets it up for remote management.
With this setup, the collector can centralize logs from multiple machines, making monitoring and analysis easier.
💡
Managing log retention effectively ensures you have the right data when you need it—without unnecessary storage costs. Here’s a practical guide on Log Retention.
How to Integrate Event Logs With Your DevOps Workflow
Event logs aren’t useful if you’re only looking at them after something breaks. Here’s how to make them part of your workflow:
Monitoring & Alerting
To ensure system health and detect issues early, you need proper monitoring and alerting for Windows event logs. Here’s how different tools can help:
Windows Event Forwarding (WEF) – Native Centralized Logging
- A built-in Windows feature that forwards logs from multiple machines to a central event collector.
- Uses Windows Remote Management (WinRM) for secure log transmission.
- Works best for on-premises environments where logs need to be centralized without additional software.
- Requires setting up subscriptions to filter and collect only relevant event logs.
Azure Monitor – Cloud-Based Monitoring for Hybrid Environments
- Collects logs from on-premises Windows servers and Azure VMs using the Log Analytics Agent.
- Provides a query-based interface (Kusto Query Language — KQL) for analyzing event logs.
- Can trigger alerts based on specific event patterns or thresholds.
- Integrates with Azure Security Center for security event monitoring and compliance reporting.
Last9 – Observability Built for Reliability
- Purpose-built for reliability engineering, Last9 offers deep observability into logs, metrics, and traces.
- Helps teams understand infrastructure health by correlating logs with system performance.
- Otel-native makes it easy to ingest logs from various sources, including Windows Event Logs.
- Enables real-time alerting and anomaly detection with minimal operational overhead.
- Designed to handle large-scale distributed environments with efficient log aggregation and querying.
Automating Responses
# Example: Restart a service that keeps failing
$failEvents = Get-WinEvent -FilterHashtable @{
LogName='System';
ID=7031; # Service crashed unexpectedly
ProviderName='Service Control Manager'
} -MaxEvents 5
if ($failEvents.Count -ge 3) {
Restart-Service -Name "ProblemService" -Force
Send-MailMessage -To "you@company.com" -Subject "Service Restarted Automatically"
}This PowerShell script monitors Windows event logs for repeated service failures and automatically restarts the affected service if needed.
- It uses
Get-WinEventto filter logs in the System event log, specifically looking for Event ID 7031, which indicates a service crash, and filtering by the Service Control Manager provider. - It retrieves up to five recent events matching this criteria.
- If at least three failures are detected, the script forcefully restarts the service named
"ProblemService". - It then sends an email notification to alert the team that the service was restarted.
3 Common Log Location Issues & How to Fix Them
Sometimes your logs aren’t where you expect them to be:
«I Can’t Find My Logs»
If default logs are missing, check:
- If the Event Log service is running:
Get-Service EventLog - Disk space:
Get-Volume C - Log rotation settings:
Get-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Services\EventLog\Application
«My Logs Are Too Big/Small»
Adjust the maximum log size:
# Increase System log to 2GB
Limit-EventLog -LogName System -MaximumSize 2GB
# Check current settings
Get-EventLog -List«My Logs Aren’t Detailed Enough»
For more detailed logging:
# Enable debug logging for a service
wevtutil.exe sl Microsoft-Windows-YourService/Debug /e:true
# Enable analytical channels (super detailed)
wevtutil.exe set-log "Microsoft-Windows-YourService/Analytical" /enabled:true💡
Looking for a fast and efficient way to handle logs in Node.js? Check out this guide on NPM Pino Logger.
How Do You Retain Logs for Compliance Without Storage Issues?
Proper log retention is essential for meeting auditing, security, and compliance requirements. Logs serve as a historical record of system activity, helping organizations detect security incidents, meet regulatory requirements, and troubleshoot past issues.
Below is a structured approach to archiving Windows event logs effectively.
Backing Up and Clearing Event Logs
Before clearing logs, it’s critical to back them up to prevent data loss. Windows provides built-in utilities to handle this process:
# Back up the System log before clearing
wevtutil.exe epl System C:\Backups\System_$(Get-Date -Format "yyyyMMdd").evtx
# Clear the System log after backup
wevtutil.exe cl Systemwevtutil.exe eplexports the System log to a specified backup file, including a timestamp for easy identification.wevtutil.exe clclears the log after backup, ensuring that new logs can be captured without exceeding storage limits.
Long-Term Log Archiving Strategies
For long-term retention, consider structured approaches that align with compliance frameworks such as HIPAA, PCI-DSS, or SOC 2.
- Setting Up a SIEM System
- SIEM (Security Information and Event Management) tools like Splunk, QRadar, and Elastic Security aggregate, store, and analyze event logs.
- These tools allow for real-time threat detection and long-term forensic analysis.
- Logs are typically indexed for quick searching and reporting, meeting compliance requirements for log retention.
- Using Azure Log Analytics for Cloud-Based Archiving
- Windows event logs can be forwarded to Azure Monitor and Log Analytics for centralized storage.
- The logs are stored securely in the cloud, reducing the risk of local data loss.
- Supports Kusto Query Language (KQL) for advanced log querying and reporting.
- Automating log backups ensures consistency and compliance without manual intervention.
- A scheduled PowerShell task can back up logs periodically:
- This script can be scheduled via Task Scheduler to run daily or weekly, depending on retention needs.
Automating Log Archival with PowerShell
$logName = "System"
$backupPath = "C:\Backups\${logName}_$(Get-Date -Format 'yyyyMMdd').evtx"
wevtutil.exe epl $logName $backupPath
wevtutil.exe cl $logNameHow to Choose the Right Log Retention Policy
When designing a log retention strategy, consider:
- Regulatory Requirements: Ensure logs are retained as per legal and industry standards.
- Storage Costs: Optimize cloud storage plans or implement local compression strategies.
- Security Considerations: Encrypt archived logs and restrict access to authorized personnel only.
- Search and Retrieval Needs: Store logs in an indexed format for efficient query-based retrieval.
💡
Making sense of SIEM logs can be tricky, but the right approach helps turn data into actionable insights—here’s a practical guide on SIEM Logs.
Conclusion
Windows event logs might not be the most exciting part of your DevOps toolkit, but they’re often the difference between quick resolutions and late-night troubleshooting marathons.
The key is knowing not just where the logs are located, but how to extract the information you need when you need it.
FAQs
How far back do Windows event logs go?
By default, Windows keeps logs until they reach their maximum size (typically 20MB for System and Application logs). When logs fill up, Windows overwrites the oldest events. You can adjust this with PowerShell:
# See current retention settings
Get-EventLog -List
# Increase size to prevent early overwriting
Limit-EventLog -LogName Application -MaximumSize 4GBFor critical systems, consider setting up log forwarding or scheduled archiving to preserve logs indefinitely.
Can I read Windows event logs without admin rights?
For most logs, you’ll need administrative privileges. However, some applications write to logs that regular users can access. If you need to grant non-admin users access to specific logs:
# Grant read access to a user
wevtutil set-log Security /ca:'O:BAG:SYD:(A;;0x1;;;SY)(A;;0x1;;;BA)(A;;0x1;;;AU)(A;;0x1;;;YourDomain\YourUser)'But be careful – security logs contain sensitive information.
How do I correlate events across multiple servers?
Your options include:
- Set up Windows Event Forwarding to a central collector
- Use Azure Monitor to aggregate logs in the cloud
- Implement a third-party SIEM solution
- Use PowerShell to query multiple servers:
Invoke-Command -ComputerName Server1, Server2, Server3 -ScriptBlock {
Get-WinEvent -FilterHashtable @{LogName='System'; ID=1074} -MaxEvents 5
} | Select-Object PSComputerName, TimeCreated, ID, MessageTime synchronization is crucial here – make sure all servers use the same NTP source.
What’s the difference between .evt and .evtx file formats?
- .evt: Legacy format used in Windows XP/Server 2003
- .evtx: Modern XML-based format used since Windows Vista/Server 2008
The newer .evtx format offers better performance, more detailed information, and larger log sizes. If you’re dealing with older .evt files, use the Get-WinEvent cmdlet with the -Path parameter to read them.
Can I export logs for analysis in other tools?
Absolutely. Export options include:
# Export to XML
Get-WinEvent -LogName System -MaxEvents 100 | Export-Clixml -Path C:\Temp\events.xml
# Export to CSV
Get-WinEvent -LogName System -MaxEvents 100 | Select TimeCreated, ID, LevelDisplayName, Message | Export-Csv -Path C:\Temp\events.csv -NoTypeInformation
# Export raw EVTX
wevtutil epl System C:\Temp\system.evtxMany analysis tools like Last9, ELK Stack, and Graylog can ingest these formats.
Журнал событий Windows (Event Log) — это важный инструмент, который позволяет администратору отслеживать ошибки, предупреждения и другие информационные сообщения, которые регистрируются операционной системой, ее компонентами и различными программами. Для просмотра журнала событий Windows можно использовать графическую MMC оснастку Event Viewer (
eventvwr.msc
). В некоторых случаях для поиска информации в журналах событий и их анализа гораздо удобнее использовать PowerShell. В этой статье мы покажем, как получать информацию из журналов событий Windows с помощью командлета Get-WinEvent.
Содержание:
- Получение логов Windows с помощью Get-WinEvent
- Get-WinEvent: быстрый поиск в событиях Event Viewer с помощью FilterHashtable
- Расширенный фильтры событий Get-WinEvent с помощью FilterXml
- Получить логи Event Viewer с удаленных компьютеров
На данный момент в Windows доступны два командлета для доступа к событиям в Event Log: Get-EventLog и Get-WinEvent. В подавляющем большинстве случаев рекомендуем использовать именно Get-WinEvent, т.к. он более производителен, особенно в сценариях обработки большого количества событий с удаленных компьютеров. Командлет Get-EventLog является устаревшим и использовался для получения логов в более ранних версиях Windows. Кроме того, Get-EventLog не поддерживается в современных версиях PowerShell Core 7.x.
Получение логов Windows с помощью Get-WinEvent
Для использования команды Get-WinEvent нужно запустить PowerShell с правами администратора (при запуске Get-WinEvent от имени пользователя вы не сможете получить доступ к некоторым логам, например, к Security).
Для получения списка событий из определенного журнала, нужно указать его имя. В данном примере мы выведем последние 20 событий из журнала System:
Get-WinEvent -LogName Application -MaxEvents 20
Чаще всего вам нужно будет получать информацию из журналов System, Application, Security или Setup. Но вы можете указать и другие журналы. Полный список журналов событий в Windows можно получить с помощью команды:
Get-WinEvent -ListLog *
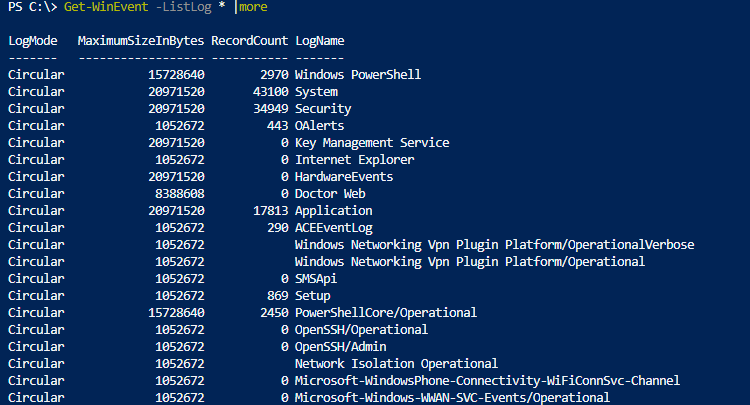
Например, чтобы вывести события RDP подключений к компьютеру, нужно указать лог Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational:
Get-WinEvent -LogName Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational
Или получить логи SSH подключений к Windows из журнала OpenSSH/Operational:
Get-WinEvent -LogName OpenSSH/Operational
Можно выбрать события сразу из нескольких журналов. Например, чтобы получить информацию о ошибках и предупреждениях из журналов System и Application за последние 24 часа (сутки), можно использовать такой код:
$StartDate = (Get-Date) - (New-TimeSpan -Day 1)
Get-WinEvent Application,System | Where-Object {($_.LevelDisplayName -eq "Error" -or $_.LevelDisplayName -eq "Warning") -and ($_.TimeCreated -ge $StartDate )}
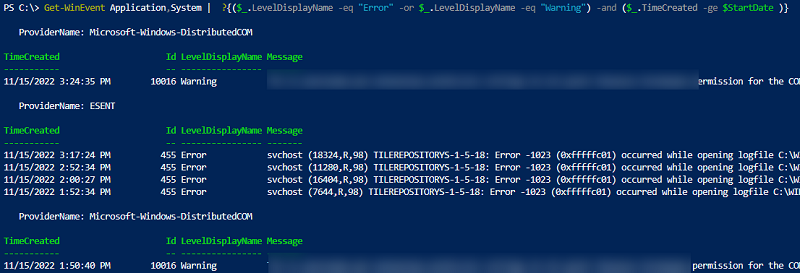
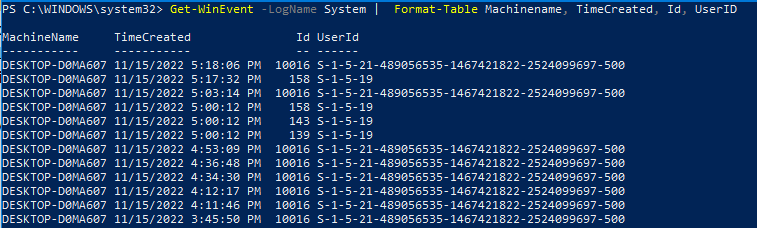
Чтобы вывести только определенные поля событий, можно использовать Select-Object или Format-Table:
Get-WinEvent -LogName System | Format-Table Machinename, TimeCreated, Id, UserID
Можно выполнить дополнительные преобразования с полученными данными. Например, в этом примере мы сразу преобразуем имя пользователя в SID:
Get-WinEvent -filterhash @{Logname = 'system'} |
Select-Object @{Name="Computername";Expression = {$_.machinename}},@{Name="UserName";Expression = {$_.UserId.translate([System.Security.Principal.NTAccount]).value}}, TimeCreated
Get-WinEvent: быстрый поиск в событиях Event Viewer с помощью FilterHashtable
Рассмотренный выше способ выбора определенных событий из журналов Event Viewer с помощью Select-Object прост для понимая, но выполняется крайне медленно. Это особенно заметно при выборке большого количества событий. В большинстве случаев для выборки событий нужно использовать фильтрацию на стороне службы Event Viewer с помощью параметра FilterHashtable.
Попробуем сформировать список ошибок и предупреждений за 30 дней с помощью Where-Object и FilterHashtable. Сравнима скорость выполнения этих двух команд PowerShell с помощью Measure-Command:
$StartDate = (Get-Date).AddDays(-30)
Проверим скорость выполнения команды с Where-Object:
(Measure-Command {Get-WinEvent Application,System | Where-Object {($_.LevelDisplayName -eq "Error" -or $_.LevelDisplayName -eq "Warning") -and ($_.TimeCreated -ge $StartDate )}}).TotalMilliseconds
Аналогичная команда с FilterHashtable:
(Measure-Command {Get-WinEvent -FilterHashtable @{LogName = 'System','Application'; Level =2,3; StartTime=$StartDate }})..TotalMilliseconds
В данном примере видно, что команда выборки событий через FilterHashtable выполняется в 30 раз быстрее, чем если бы обычный Where-Object (
2.5
сек vs
76
секунд).
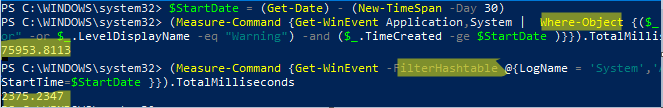
Если вам нужно найти события по EventID, используйте следующую команду с FilterHashtable:
Get-WinEvent -FilterHashtable @{logname='System';id=1074}|ft TimeCreated,Id,Message
В параметре FilterHashtable можно использовать фильтры по следующим атрибутам событий:
- LogName
- ProviderName
- Path
- Keywords (для поиска успешных событий нужно использовать значение 9007199254740992 или для неуспешных попыток 4503599627370496)
- ID
- Level (1=FATAL, 2=ERROR, 3=Warning, 4=Information, 5=DEBUG, 6=TRACE, 0=Info)
- StartTime
- EndTime
- UserID (SID пользователя)
- Data
Пример поиска события за определенный промежуток времени:
Get-WinEvent -FilterHashTable @{LogName='System'; StartTime=(get-date).AddDays(-7); EndTime=(get-date).AddHours(-1); ID=1234}
Если нужно найти определенный текст в описании события, можно использовать такую команду:
Get-WinEvent -FilterHashtable @{logname='System'}|Where {$_.Message -like "*USB*"}
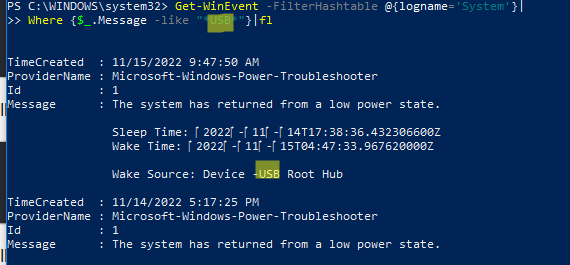
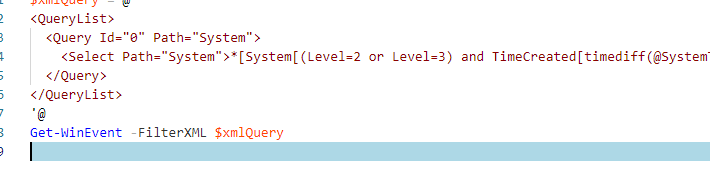
Расширенный фильтры событий Get-WinEvent с помощью FilterXml
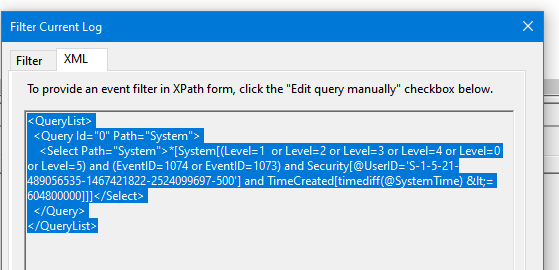
Фильтры Get-WinEvent с параметром FilterHashtable являются несколько ограниченными. Если вам нужно использовать для выборки событий сложные запросы с множеством условий, нужно использовать параметр FilterXml, который позволяет сформировать запрос на выбор событий в Event Viewer с помощью XML запроса. Как и FilterHashtable, фильтры FilterXml выполняется на стороне сервера, поэтому результат вы получите довольно быстро.
Например, аналогичный запрос для получения последних ошибок из журнала System за последние 30 дней может выглядеть так:
$xmlQuery = @'
<QueryList>
<Query Id="0" Path="System">
<Select Path="System">*[System[(Level=2 or Level=3) and TimeCreated[timediff(@SystemTime) <= 2592000000]]]</Select>
</Query>
</QueryList>
'@
Get-WinEvent -FilterXML $xmlQuery
Для построения кода сложных XML запросов можно использовать графическую консоль Event Viewer:
- Запустите
eventvwr.msc
; - Найдите журнал для которого вы хотите создать и выберите Filter Current Log;
- Выберите необходимые параметры запроса в форме. В этом примере я хочу найти события с определенными EventID за последние 7 дней от определенного пользователя;
- Чтобы получить код XML запроса для параметра FilterXML, перейдите на вкладку XML и скопируйте полученный код (CTRL+A, CTRL+C);
- Если нужно, вы можете вручную отредактировать данный запрос.
Для экспорта списка событий в CSV файл нужно использовать командлет Export-CSV:
$Events= Get-WinEvent -FilterXML $xmlQuery
$events| Export-CSV "C:\ps\FilterSYSEvents.csv" -NoTypeInformation -Encoding UTF8
Получить логи Event Viewer с удаленных компьютеров
Для получения события с удаленного компьютер достаточно указать его имя в параметре -ComputerName:
$computer='msk-dc01'
Get-WinEvent -ComputerName $computer -FilterHashtable @{LogName="System"; StartTime=(get-date).AddHours(-24)} | select Message,Id,TimeCreated
Можно опросить сразу несколько серверов/компьютеров и поискать на них определенные события. Список серверов можно получить из текстового файла:
$servers = Get-Content -Path C:\ps\servers.txt
Или из Active Directory:
$servers = (Get-ADComputer -Filter 'operatingsystem -like "*Windows server*" -and enabled -eq "true"').Name
foreach ($server in $servers) {
Get-WinEvent -ComputerName $server -MaxEvents 5 -FilterHashtable @{
LogName = 'System'; ID= 1234
} | Select-Object -Property ID, MachineName
}
Здесь есть другой пример для поиска событий блокировки учетной записи пользователя на всех контроллерах домена:
$Username = 'a.ivanov'
Get-ADDomainController -fi * | select -exp hostname | % {
$GweParams = @{
‘Computername’ = $_
‘LogName’ = ‘Security’
‘FilterXPath’ = "*[System[EventID=4740] and EventData[Data[@Name='TargetUserName']='$Username']]"
}
$Events = Get-WinEvent @GweParams
$Events | foreach {$_.Computer + " " +$_.Properties[1].value + ' ' + $_.TimeCreated}
}
If you’re using a Windows server and want to know what happened to your machine, Windows logs are an essential resource. Windows logs record various system activities, errors, and other significant events, providing valuable information for troubleshooting, auditing, and ensuring system integrity. Understanding how to access, interpret, and utilise these logs enables efficient, problem solving, enables security measures and ensures the smooth operation of your system.
In this guide, you will learn about Windows event logs, its different categories, how to filter and create Custom Views.
What is a Windows Event Log?
A Windows event log is a file that keeps track of system events and errors, application issues, and security events. Windows Event log can also provide insights into an application’s behavior by tracking its interactions with other processes and services. With the right knowledge of the information stored in these logs, you can easily diagnose and easily resolve issues within your system and applications.
You can access the windows events logs as follows:
Using the Start Menu:
- Click on the Start button or press the Windows key.
- Type
Event Viewerin the search box and select it from the search results.
Using the Run Dialog:
- Press
Windows + Rto open the Run dialog. - Type
eventvwrand press Enter.
Using the Control Panel:
- Open the Command Prompt and run as administrator.
- Type
eventvwrand press Enter.
You can see the detailed steps below. Now let’s discuss and understand windows events logs in detail.
Understanding Windows Event Logs categories & Types
There are different Windows logs, each serving a specific purpose in tracking and recording events related to your system, applications, and security. They include:
- System Events: System events log information is about the core operations of your Windows operating system. System events are essential for maintaining your system’s health and functionality because it records events related to the system’s hardware and software components. Some system events are as follows:
- Hardware Failures: Logs any issues related to hardware components, such as disc failures or memory errors.
- Driver Issues: Records events related to the loading, unloading, or malfunctioning of device drivers. This helps in identifying driver-related problems that could affect system stability.
- System Startups and Shutdowns: Tracks the times when the system starts up or shuts down. This can be useful for understanding system uptime and diagnosing issues related to improper shutdowns or startup failures.
- Application Events: Data related to software applications running on the system includes application errors, warnings, and informational messages. If you are using a Windows server to run your production-level application, you can use the application errors, warnings, and messages provided here to solve the issue. There are different types of Application events some are as follows:
- Application Errors: Application errors are events generated by software applications when they encounter issues that prevent them from functioning correctly.
- Warnings: Logs warnings from applications about potential issues that might not be critical but could lead to problems if not addressed.
- Informational Messages: Provides general information about application activities, such as successful operations or status updates, helping to understand the normal functioning of applications.
- Security Events: Security events are logs that capture all security-related activities on your Windows system. They are essential for monitoring, maintaining, and auditing the security of your system. These events help detect unauthorised access attempts, monitor access to sensitive resources, and track changes to system policies. Some security events are as follows:
- Successful and Failed Login Attempts: Successful and failed login attempts are critical events that are logged by a system to monitor access and ensure security. These logs provide valuable insights into user activity, helping to detect unauthorised access attempts and identify potential security threats.
- Resource Access: These events log attempts to access protected resources such as files, folders, or system settings. Monitoring these logs ensures that sensitive data is accessed appropriately and helps identify unauthorised access attempts.
- System Policy Changes: These logs record any changes to system policies, including modifications to user permissions or security settings. This is important for auditing purposes and ensuring compliance with security policies, helping to maintain the integrity and security of the system.
- Setup Events: Setup events are logs that contain detailed information about the installation and setup processes on your Windows system. These logs are valuable for diagnosing and resolving issues that occur during the installation or configuration of software and system components. Some Setup events are as follows:
- Installation Processes: Installation processes refer to the series of steps and operations carried out to install software, updates, or system components on a Windows system. It contains log details about software installation, updates, or system components. This helps in diagnosing issues related to incomplete or failed installations.
- Setup Configurations: Records information about system configurations during the setup process. This can be useful for understanding your system’s initial setup and configuration.
- Forwarded Events: Forwarded events are logs sent from other computers to a centralised logging server. This is particularly useful in larger environments where centralised log management is needed. They include:
- Logs from Remote Systems: Collects event logs from multiple systems, allowing for centralised monitoring and management.
- Centralised Logging Scenarios: Useful for organisations that need to aggregate logs from various systems to a single location for easier analysis and monitoring.
Accessing the Windows Event Viewer
Windows Event Viewer is a Windows application that lets you see your computer’s logs, warnings, and other events. Each application you open generates entries that are recorded in an activity log, which can be viewed from the Event Viewer.
There are several ways to access the Windows Event Viewer. Here are some of them:
-
Using the Start Menu:
- Click on the Start button or press the Windows key.
- Type
Event Viewerin the search box.
Using start menu to open Event viewer — Select Event Viewer from the search results which will popup something like this.
Event Viewer main page 2. Using the Run Dialog: — Press
Windows + Rto open the Run dialog. — Typeeventvwrand press Enter.Windows Run App to open Event Viewer Windows Event viewer landing page 3. Using Control Panel: — Open the Command Prompt and run as administrator
Open CMD as Administrator from start menu — Once open, type
eventvwrand press enter, and you will be redirected to Event Viewer page.CMD terminal
Windows Log Location
Windows event logs are stored in files located in the C:\\Windows\\System32\\winevt\\Logs directory. Each log file corresponds to a specific log category, such as System, Application, or Security. It may differ depending on which version of Windows you are using.
The main event log files are:
- Application.evtx: Logs events from applications and programs.
- Security.evtx: Logs security events like successful or failed logins.
- System.evtx: Logs events related to Windows system components and drivers
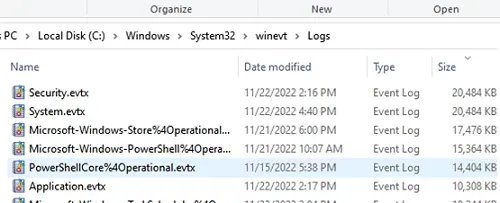
You can find many other log files which could be related to system operations & other processes that are happening inside the Windows System. Windows 11uses the .evtx format rather than using the classic EVT format.
Understanding Event Viewer Entries
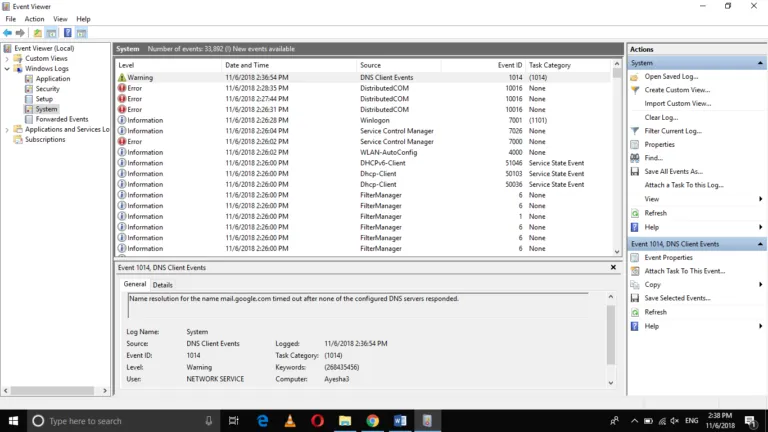
Event Viewer entries provide detailed information about each logged event. It is like a log book for your Windows system. They record important happenings within the system, including applications, systems, security, failed events, etc. Understanding these entries is key to effective log management.
The key components of an Event Viewer entry are:
- Date and Time: When the event occurred.
- Source: The application or system component that generated the event.
- Event ID: A unique identifier for the event type.
- Level: The severity of the event (Information, Warning, Error, Critical).
- User: The user account under which the event occurred.
- Computer: The name of the computer where the event was logged.
- Description: Detailed information about the event.
Each event in the Event Viewer has a severity level, indicating the importance and type of the event:
- Information (Green Light): These events resemble a green traffic light, signifying smooth sailing. They indicate successful operations or occurrences within your system.
- Warning (Yellow Light): Treat these entries with caution, like a yellow traffic light. They signal potential issues that warrant attention but might not cause immediate problems.
- Error (Orange Light): Think of error entries as an orange traffic light; proceed with care. They denote significant problems that could affect system functionality. Imagine an error message indicating a driver failure.
- Critical (Red Light): Critical entries are akin to a red traffic light; stop and address the situation immediately. They represent severe errors that have caused a major failure. A critical event might report a complete system shutdown or a critical service crashing.
Filtering and Custom Views
Event Viewer allows you to filter events using a variety of parameters, including date, event level, source, and more. Consider the following scenario: your system exhibits weird behaviour, but the Event Viewer is overflowing with hundreds, if not thousands, of entries. Filtering steps and generating custom views can significantly reduce the workload. You may also construct custom views to focus on specific kinds of events:
- In the Event Viewer, you’ll see Administrative Events, to create special logs right-click on «Custom Views» and select «Create Custom View.»
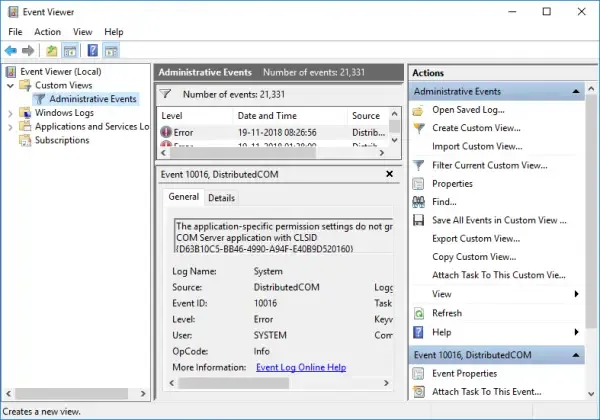
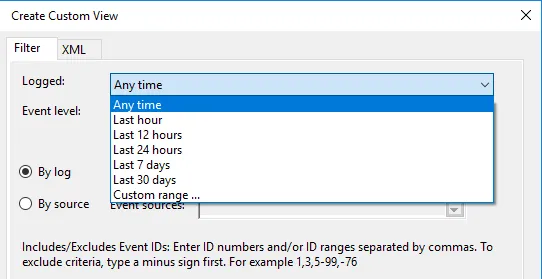
1. In the Custom View page, you can see logged drop down, choose a preferred time or it gives you an option to create a custom time to set. 2. On the Event Level choose an appropriate level for your custom view, You can choose among the 5 levels.
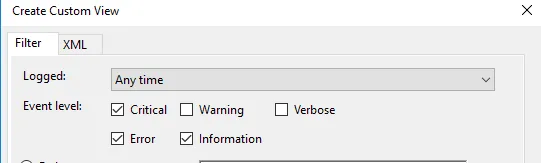
1. Once done, choose how you want the events to be filtered, By log or By source.
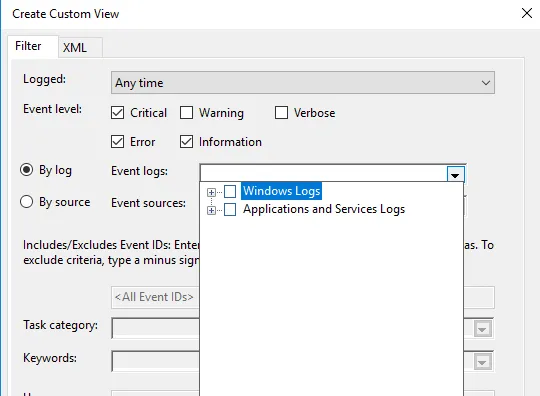
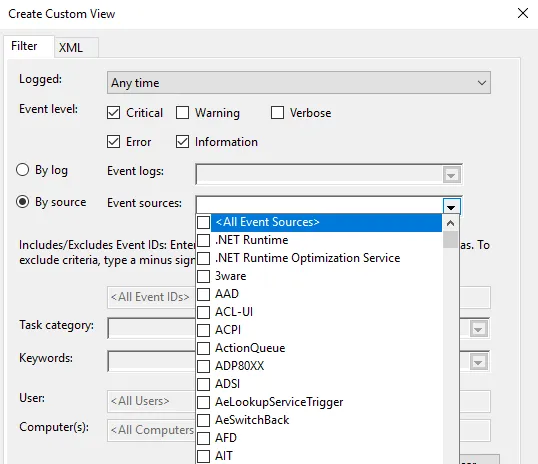
Once everything is set up according to your needs, save all events in Custom View as
from the drop-down menu and choose an appropriate location to save the logs. Click on the Save button. (A log file with the extension .evtx will be saved on your device).
Conclusion
This blog provides an understanding how you can use the Windows Event Viewer which is provided by the Windows in default and using it to monitor Windows logs.
- Main event log files are stored in
C:\\Windows\\System32\\winevt\\Logs. - Windows logs are crucial for understanding the activities, errors, and significant events on your machine. They provide valuable information for troubleshooting, auditing, and ensuring system integrity.
- They record a variety of system activities, errors, and other significant events, providing valuable information for troubleshooting, auditing, and ensuring system integrity.
- We learnt how to setup Filtering and Custom Views to optimise what we see and solve the problems and where it happened.
By grasping the significance of different event types such as System, Application, Security, Setup, and Forwarded Events, and knowing how to filter and export logs, you can effectively manage your Windows system.
FAQ’s
How to view Windows logs?
To view Windows logs, use the built-in Event Viewer:
- Press
Win + R, typeeventvwr, and press Enter. - Navigate through the console tree to find the log you want to view (e.g., Windows Logs > Application).
Where are Microsoft logs?
Microsoft logs, including Windows logs, can be found in the Event Viewer under sections like Application, Security, and System. Log files are also located in the C:\Windows\System32\winevt\Logs directory.
How do I audit Windows logs?
To audit Windows logs:
- Open Event Viewer.
- Navigate to Security logs under Windows Logs.
- Configure auditing policies via the Local Security Policy or Group Policy Management Console.
How do I check my Windows activity log
Check your Windows activity log by viewing the Security logs in Event Viewer. These logs record user logins, logoffs, and other security-related activities.
Which is Windows log key?
The Windows log key, often referred to as the Windows key, is the key on your keyboard with the Windows logo. It is used in various shortcuts to open system tools, including Event Viewer (Win + X > Event Viewer).
Where is the logs folder?
The logs folder is located at C:\Windows\System32\winevt\Logs. This folder contains all the event log files in .evtx format.
Why are Windows logs important?
Windows logs are important because they provide detailed information about system operations, security events, and application behavior, which is crucial for troubleshooting, auditing, and ensuring system integrity.
How to view log files?
View log files using Event Viewer:
- Open Event Viewer (
Win + R, typeeventvwr, press Enter). - Expand the Windows Logs section and select the log you want to view.
Where are login logs?
Login logs are located in the Security logs section of Event Viewer. They record all login attempts, both successful and failed.
What are system logs?
System logs contain information about the core operations of the Windows operating system, including hardware events, driver issues, and system startups and shutdowns. They are found under the System section in Event Viewer.
How do I find Windows log files?
Find Windows log files in the Event Viewer or directly in the C:\Windows\System32\winevt\Logs directory.
How do I view user logs in Windows 10?
View user logs in Windows 10 through the Event Viewer:
- Open Event Viewer.
- Go to Windows Logs > Security to see logs related to user activities, including logins and logoffs.
How do I view Windows setup logs?
To view Windows setup logs:
- Open Event Viewer.
- Navigate to Applications and Services Logs > Microsoft > Windows > Setup.
How do I view Windows app logs?
To view Windows application logs:
- Open Event Viewer.
- Navigate to Windows Logs > Application to see logs related to software applications running on your system.
Was this page helpful?
This article explores the exciting new features of Windows Server 2022 and emphasizes the critical role of analyzing Windows Server logs. You’ll also discover how EventLog Analyzer provides comprehensive, helps you achieve 360-degree protection against threats targeting these logs, ensuring robust security for your server environment.
Key Topics:
- The Importance of Proactive Log Management
- Windows Server 2022 and its Key Features
- Understanding Windows Server Logs
- The Importance of Analyzing Windows Server Logs
- Benefits of Using EventLog Analyzer for Windows Server Log Analysis
- Configuring EventLog Analyzer to Connect to Windows Server
- Summary
Related Articles:
- Event Log Monitoring System: Implementation, Challenges & Standards Compliance
- Detecting Windows Server Security Threats with Advanced Event Log Analyzers
The Importance of Proactive Log Management
Did you know that threats targeting Windows Server and its logs are becoming more significant? To protect your systems, you must monitor and analyze these logs effectively. Ensuring system security, compliance, and health requires effective log management.
Administrators can ensure optimal performance by promptly identifying and resolving issues through routine log review. Log analysis also protects sensitive data by assisting in the detection of any security breaches and unwanted access. Proactive log management ultimately improves the security and dependability of the IT infrastructure as a whole.
EventLog Analyzer monitors various Windows event logs, such as security audit, account management, system, and policy change event logs. The insights gleaned from these logs are displayed in the forms of comprehensive reports and user-friendly dashboards to facilitate the proactive resolution of security issues.
Windows Server 2022 and its Key Features
Windows Server 2022 is a server operating system developed by Microsoft as a part of the Windows New Technology family. It is the most recent version of the Windows Server operating system, having been released in August 2021. Large-scale IT infrastructures can benefit from the enterprise-level administration, storage, and security features offered by Windows Server 2022. Compared to its predecessors, it has various new and improved capabilities, with an emphasis on application platform advancements, security, and hybrid cloud integrations.
Let’s take a look at a few key features of Windows Server 2022:
- Cutting-edge security features, such as firmware protection, virtualization-based security, hardware roots of trust, and secured-core servers, that protect against complex attacks.
- Improved management and integrations with Azure services via Azure Arc’s support for hybrid cloud environments.
- New storage features, which include Storage Migration Service enhancements, support for larger clusters, and improvements to Storage Spaces Direct.
- Enhancements to Kubernetes, container performance, and Windows containers in Azure Kubernetes Service to improve support for containerized applications.
- Support for more powerful hardware configurations, including more memory and CPU capacity, with enhanced performance for virtualized workloads.
- File size reductions during transfers to increase efficiency and speed through the use of Server Message Block (SMB) compression.
- An integration with Azure Automanage for easier deployment, management, and monitoring of servers in hybrid and on-premises environments.
- Improved networking features, such as enhanced network security and performance as well as support for DNS over HTTPS.
- Enhanced VPN and hybrid connectivity options, such as an SMB over QUIC capability that permits safe, low-latency file sharing over the internet.
- Improvements to Windows Subsystem for Linux and tighter integration for cross-platform management, which provides better support for executing Linux workloads.
- A range of flexible deployment and licensing options, such as the usage of Azure’s subscription-based licensing.
- Support for modernizing existing .NET applications and developing new applications using the latest .NET 5.0 technologies.
- Enhanced automation capabilities with the latest version of PowerShell, PowerShell 7.
Understanding Windows Server Logs
Windows Server event logs are records of events that occur within the operating system or other software running on a Windows server. You can manage, observe, and troubleshoot the server environment with the help of these logs. The logs capture numerous pieces of information, such as application problems, security incidents, and system events. By examining and evaluating these logs, administrators can ensure the security, functionality, and health of the server.
Windows Server 2022 Event Viewer
Here are the different types of Windows Server logs:
- System logs: These logs document operating-system-related events, including hardware modifications, driver issues, and system startups and shutdowns.
- Application logs: These logs capture events generated by applications running on the server and include software errors, warnings, and informational messages.
- Security logs: Security logs keep track of events related to security, such as successful and unsuccessful login attempts, actions taken by users to manage their accounts (such as adding or removing accounts), and modifications made to security guidelines.
- Setup logs: Setup logs record activities about Windows Server and the installation and configuration of its components.
- Forwarded event logs: These logs gather events and are sent from one computer to another, enabling the centralized management of several workstations or servers.
The Importance of Analyzing Windows Server Logs
Windows Server log analysis is essential for several reasons, most of which have to do with security, system performance, and troubleshooting. Here are a few reasons:
- Logs help you identify any unauthorized access attempts, such as failed login attempts, which may point to possible security risks.
- For forensic investigations, logs offer a thorough audit record of user activities, which facilitates action tracing on the server.
- Administrators can identify unusual trends in logs, such as unexpected file changes or system modifications, which could indicate malware or other malicious activity.
- Logs can assist administrators in optimizing server performance and avoiding bottlenecks by revealing the resource utilization of the CPU, memory, and disk.
- Regular log analysis enables proactive maintenance and minimizes downtime by helping you discover any hardware or software issues before they become severe, aiding in system health monitoring.
- Windows Server event logs record errors and warnings that occur during the operation of the system, providing detailed information that is essential for troubleshooting and problem resolution.
- Logs provide information about the performance and stability of different services and applications that are operating on the server, assisting administrators in promptly finding and fixing problems.
- Many industries are subject to regulations that require detailed logging of server activities. Regular log analysis ensures that organizations meet these compliance requirements.
- Logs can be used to generate reports for management or auditors, providing evidence of security measures, performance metrics, and system usage.
Benefits of Using EventLog Analyzer for Windows Server Log Analysis
EventLog Analyzer provides valuable insights and better extractions from logs, making it a superior event logging tool compared to other tools. Here are a few key capabilities of EventLog Analyzer that help in Windows Server event log analysis:
- Automate log file management: With EventLog Analyzer’s auto-discover option (see below screenshot), you can quickly identify all Windows log sources inside your domain and begin collecting Windows event logs. This feature automatically detects Windows workstations, firewalls, IIS servers, and SQL servers. To strengthen your network security, you can just choose the important sources and automate log file management.
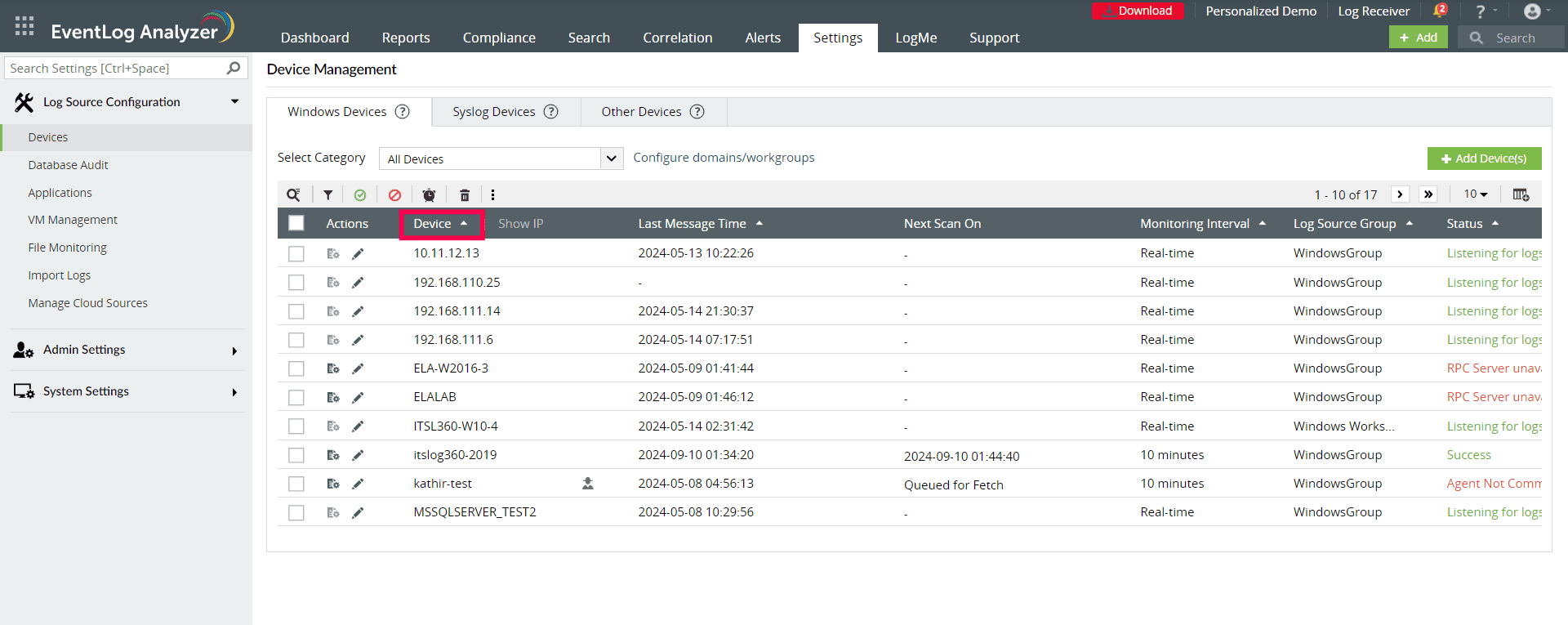
EventLog Analyzer’s auto-discover option (click to enlarge)
- Analyze logs comprehensively: With the help of EventLog Analyzer’s robust correlation engine, you can obtain thorough insights into log data from every log source in the network (see screenshot below). More than 40 prebuilt correlation rules are included in the Windows log monitoring application to identify common cyberattacks, including brute-force, ransomware, DoS, and SQL injection attacks. You also have the option to build custom rules to detect more complex attack patterns.
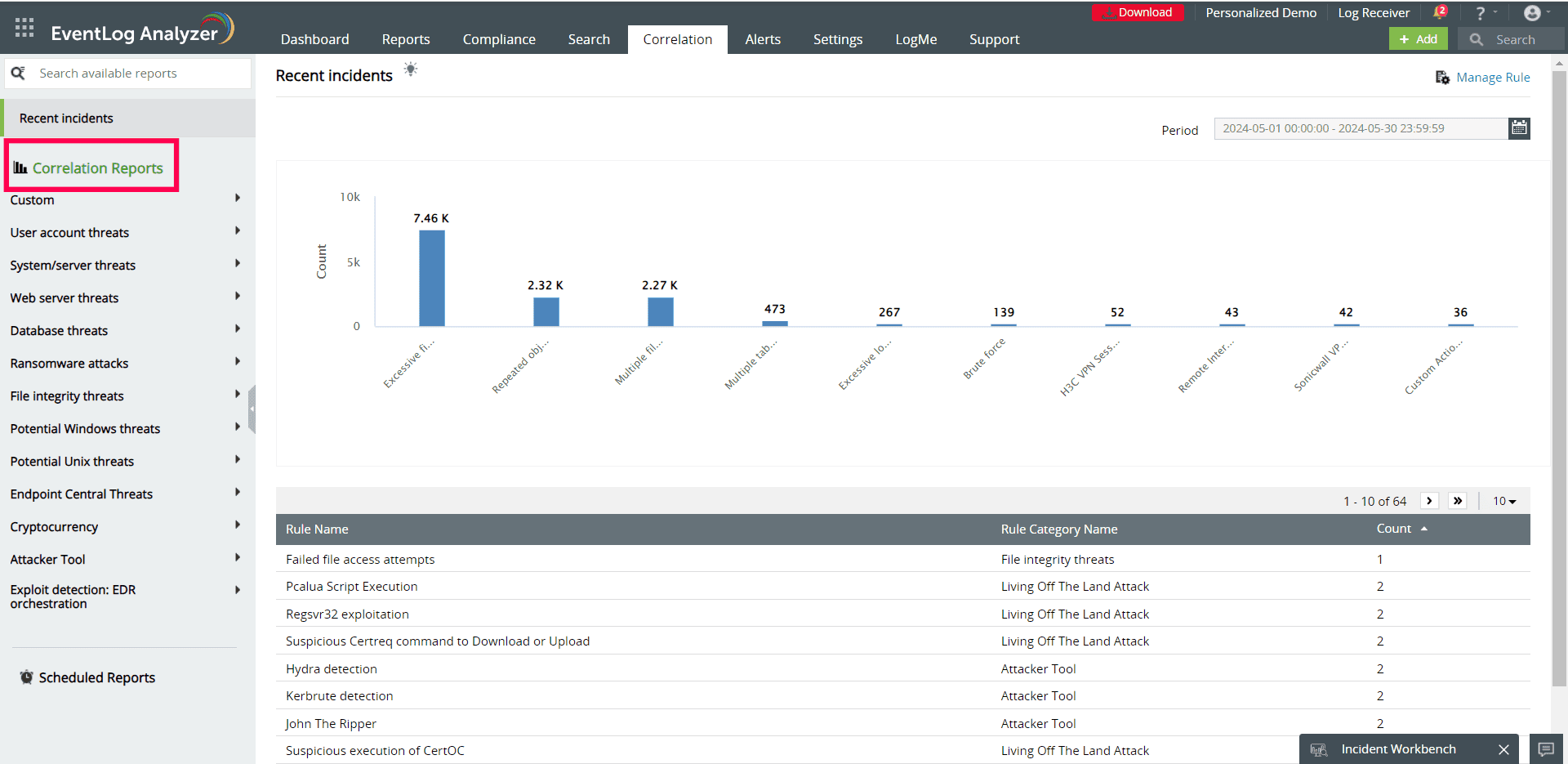
EventLog Analyzer correlation reports (click to enlarge)
- Conduct root cause analysis: EventLog Analyzer provides real-time Windows activity monitoring and lets you look through raw event logs to identify the precise log entry that resulted in a security issue (see screenshot below). So, in just a few minutes, you can determine the root cause of any security incident in your network.
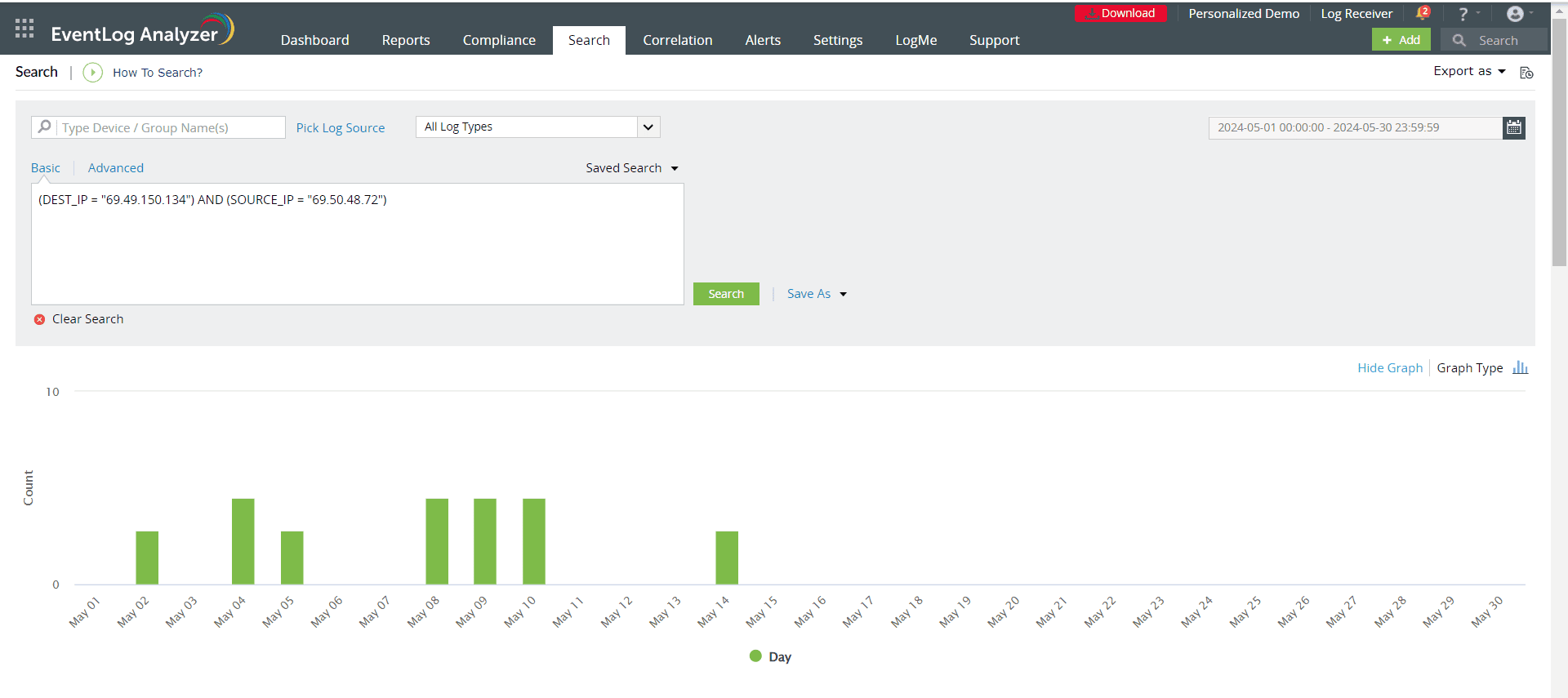
EventLog Analyzer’s log search feature (click to enlarge)
- Finding critical details about the identified incident, such as its severity, the time, the location, and the user involved, is made simple with the help of the log search feature (see screenshot below). This enables you to quickly take the necessary countermeasures to expedite the resolution of incidents.
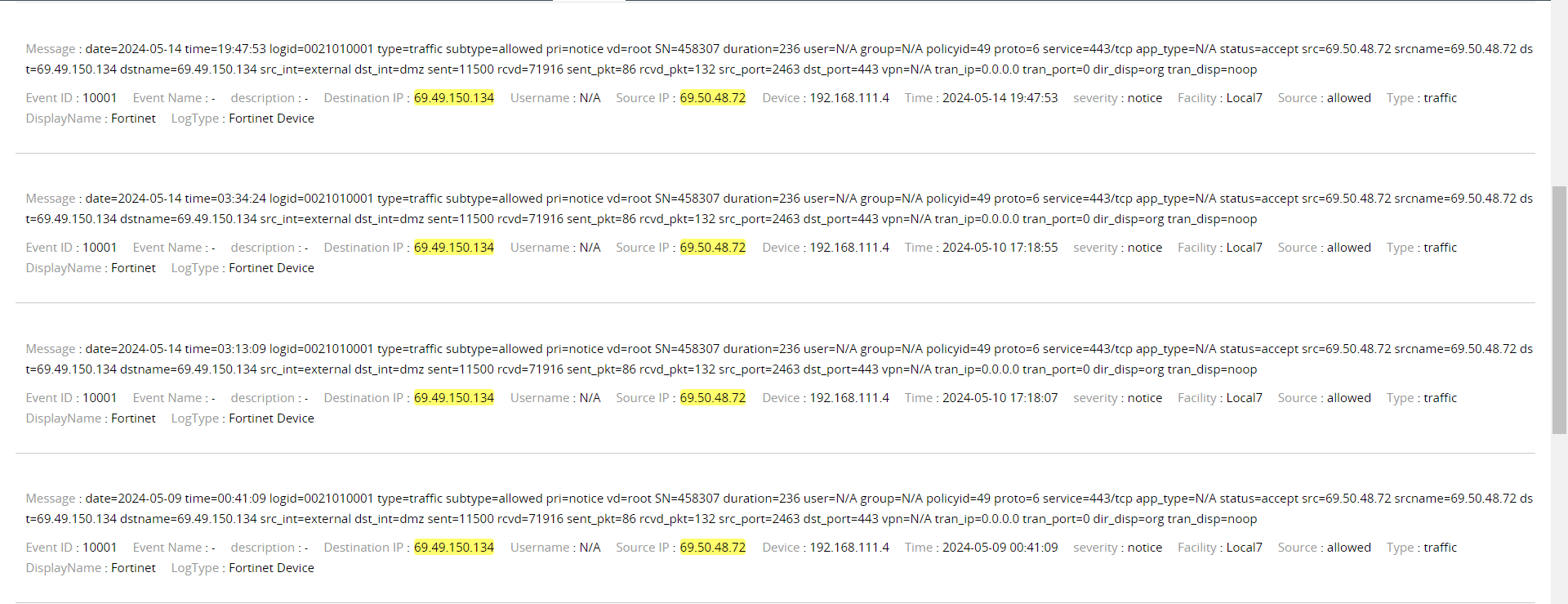
Precise details of a security incident shown by EventLog Analyzer (click to enlarge)
- Obtain detailed reports: For the Windows environment, EventLog Analyzer generates a number of reports that help with more detailed event auditing and monitoring. Reports on common attacks against Windows devices are also included (see screenshot below). EventLog Analyzer uses the event logs from Windows desktops and servers to provide comprehensive reports. It includes many Windows-specific report templates for security events such as failed logins, account lockouts, and security log manipulation. EventLog Analyzer also issues an email or SMS alert message as soon as it identifies a suspicious occurrence.
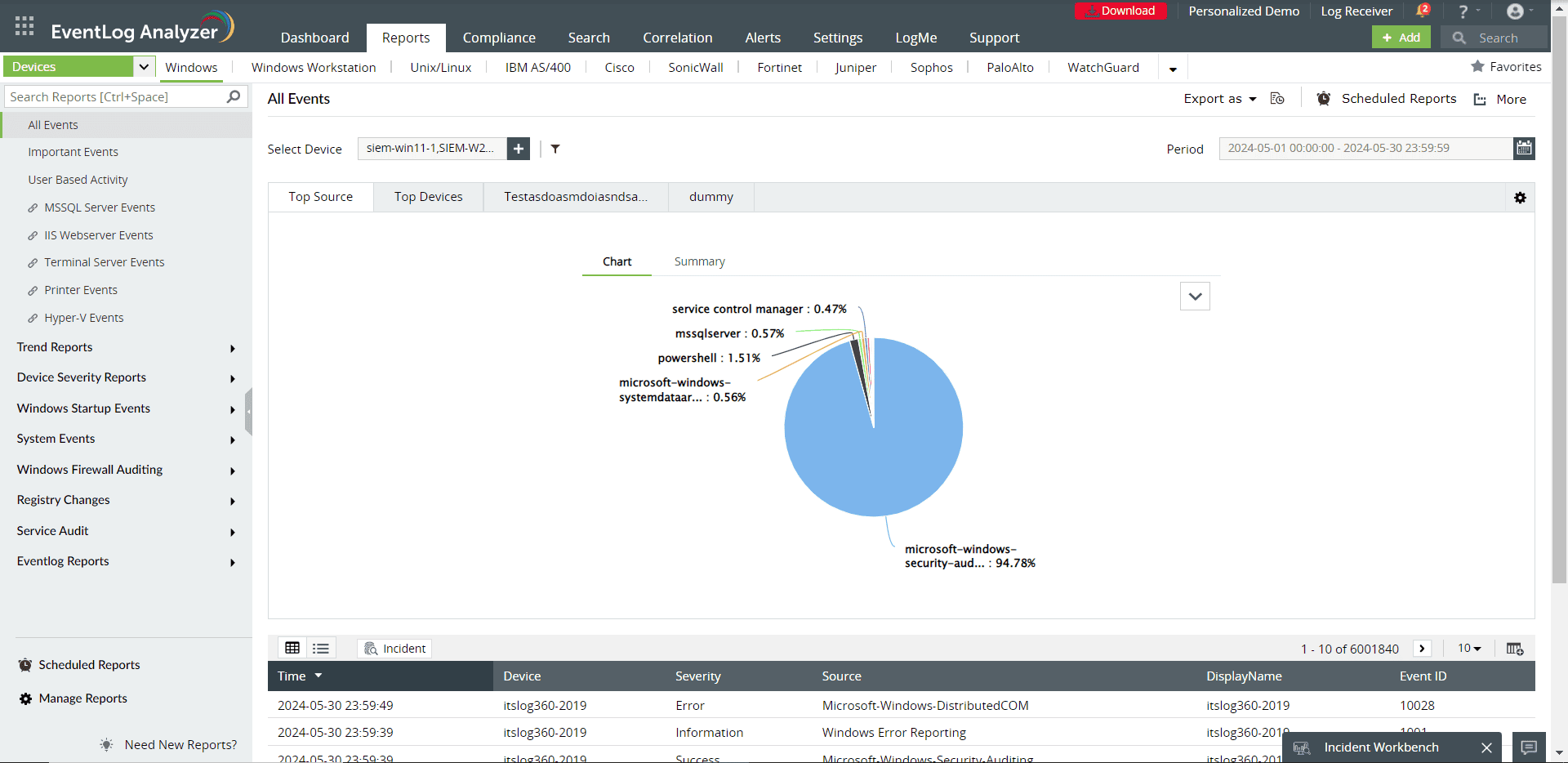
EventLog Analyzer’s reports related to Windows Server activities (click to enlarge)
Additionally, the solution includes report templates that help ensure compliance with regulations like the PCI DSS, SOX, HIPAA, the GDPR, and FISMA (see screenshot below). Custom reports can also be created to measure adherence to internal audit guidelines.
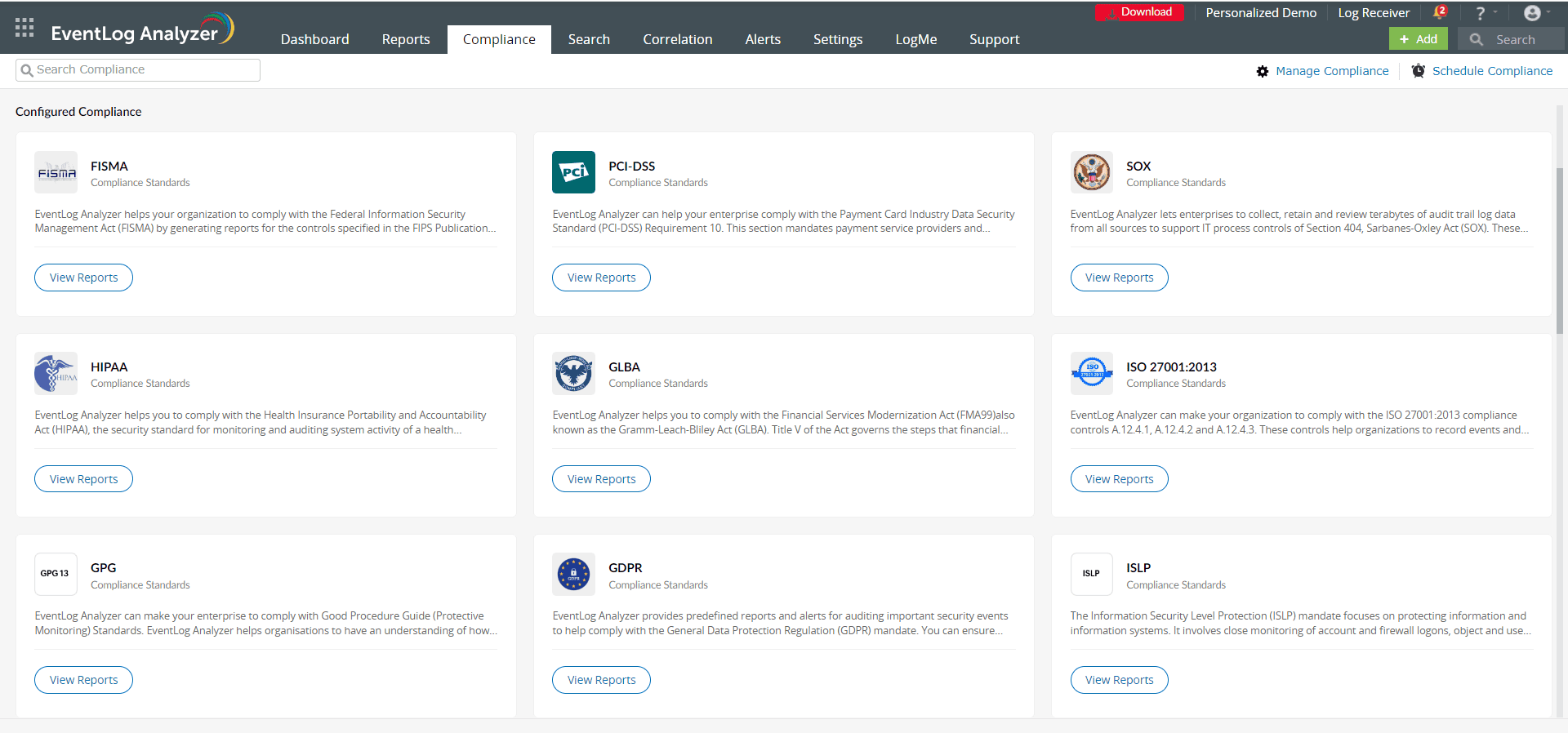
EventLog Analyzer’s compliance reports (click to enlarge)
- Receive instant alerts: Instantly identify security incidents occurring in your network and accelerate the troubleshooting process with EventLog Analyzer. You can use EventLog Analyzer to provide real-time alerts to manage incidents based on logs generated with a given log type, event ID, message, or severity (see screenshot below). The solution also supports integrations with help desks, so tickets can be raised automatically in your help desk software.
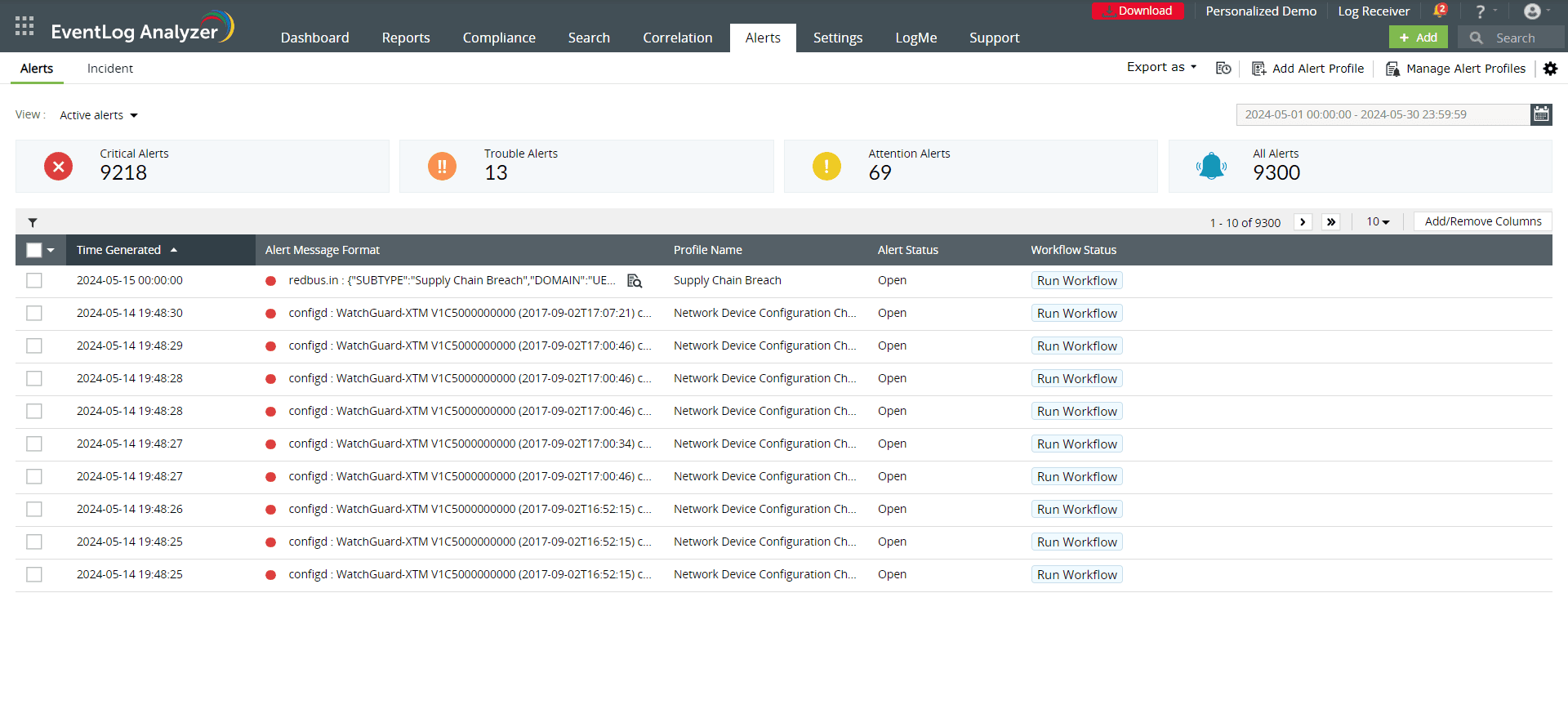
Real-time alerts generated in EventLog Analyzer (click to enlarge)
- Utilize advanced threat analytics: Through the use of reputation scores for potentially malicious URLs, domains, and IP addresses, the Advanced Threat Analytics add-on provides insightful information about the severity of threats (see screenshot below). By retrieving information about malicious IPs and domains with reputation scores, this feature alerts administrators about any suspicious IPs attempting to join your network.

EventLog Analyzer’s Advanced Threat Analytics feature (click to enlarge)
- Archive logs: EventLog Analyzer lets you specify the number of days after which event logs must be moved to the archive so you can automate the archiving of event logs (see screenshot below). After the archive period has been configured, EventLog Analyzer will organize event logs into folders on its own and compress those folders before encrypting them to ensure integrity and guard against tampering. Whenever they’re needed, the archived log files can be imported into EventLog Analyzer for forensics purposes.
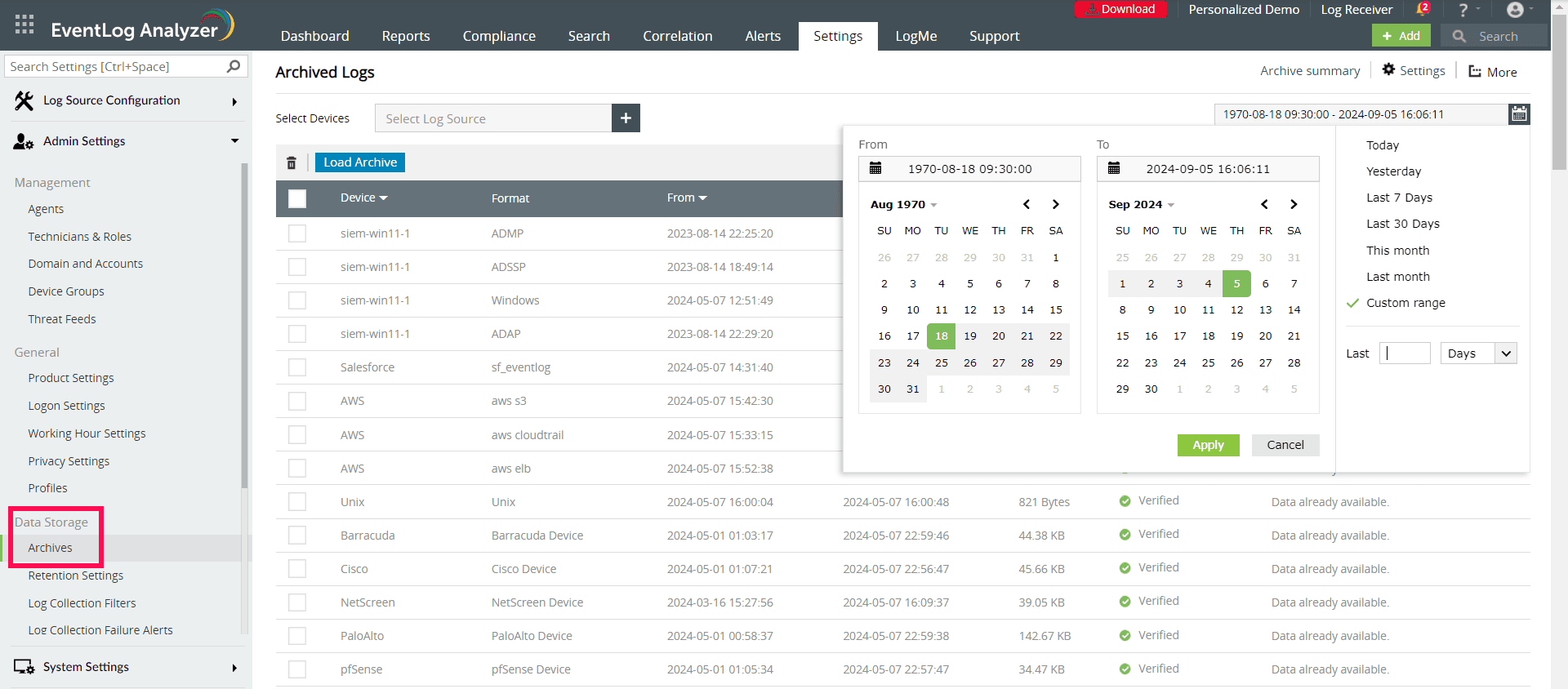
Event log archiving with EventLog Analyzer (click to enlarge)
Configuring EventLog Analyzer to Connect to Windows Server
Installing the Windows agent is mandatory for monitoring the files on Windows Server and collecting Windows event logs for EventLog Analyzer when it’s deployed on Linux operating systems.
Here are the steps to install the EventLog Analyzer agent using the product console:
1. On the Settings tab, navigate to Admin Settings > Agents.
2. Click ‘+ Install Agent‘, then click the ‘+‘ icon next to Device(s):
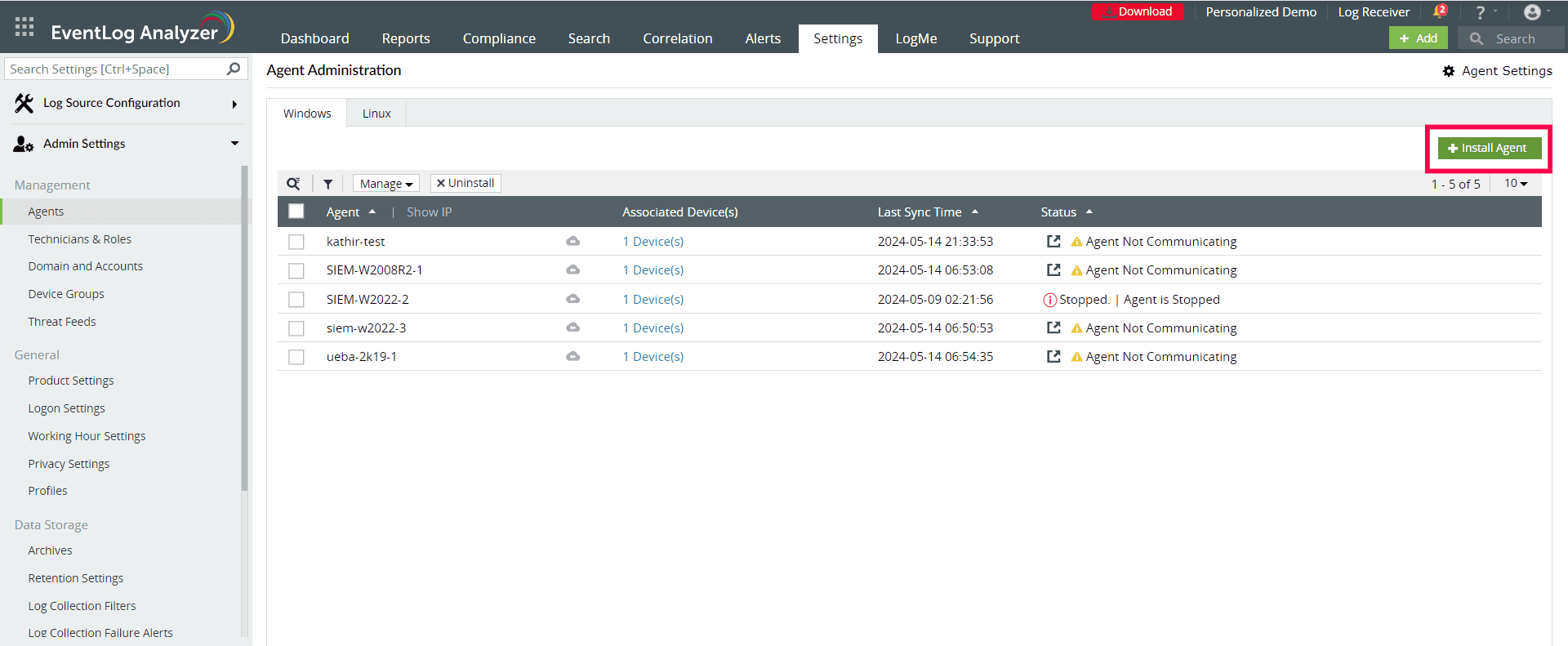
Installing the EventLog Analyzer agent (click to enlarge)
3. Select the devices on which you want to install the agent:
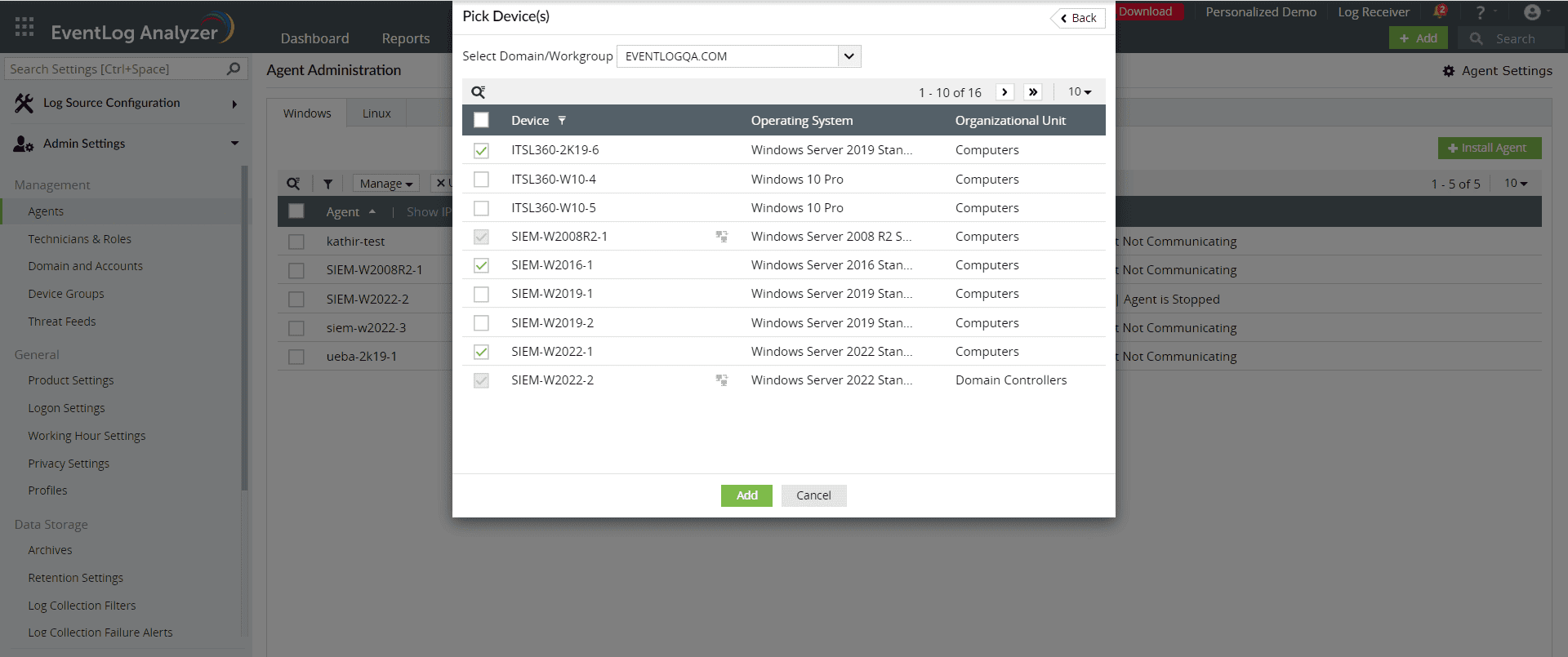
Selecting the devices on which to install the EventLog Analyzer agent (click to enlarge)
4. Enter the username and password to access the devices. This account should have admin privileges to install the agent successfully. Alternatively, you can select the Use Default Credentials option:
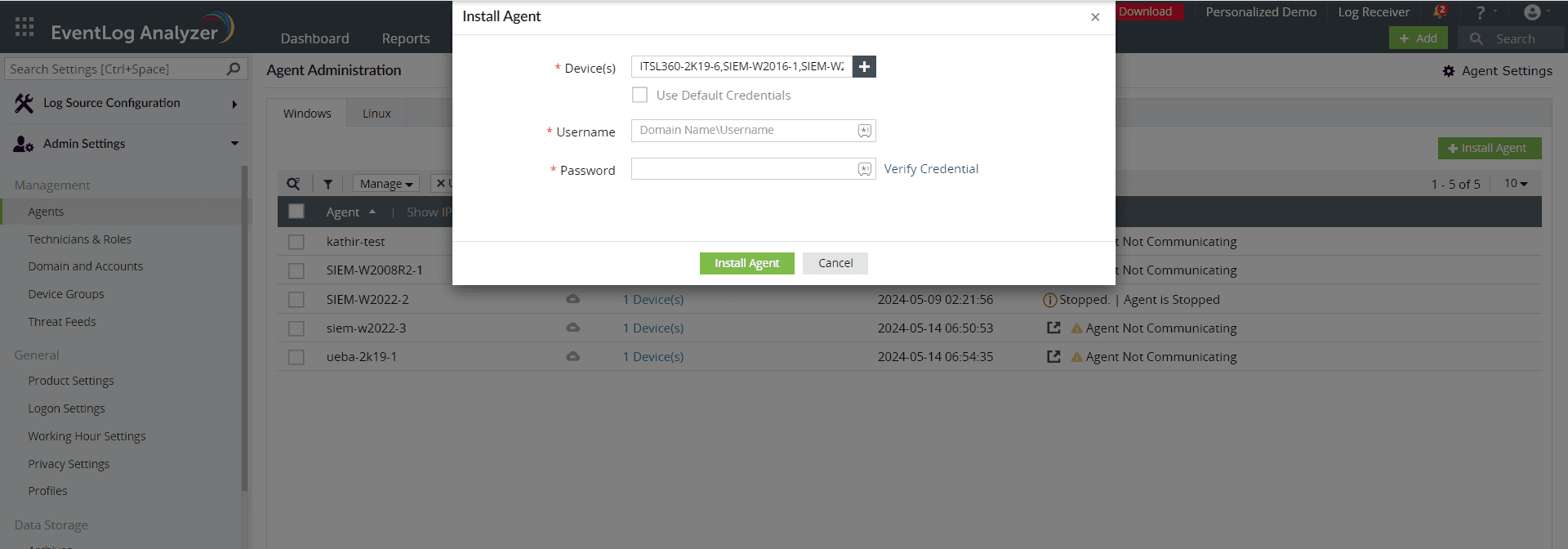
Accessing devices by entering the login details in EventLog Analyzer (click to enlarge)
Following this, in order to add the Windows devices, follow the steps given below:
- On the Settings tab, navigate to Log Source Configuration > Devices.
- Click ‘+ Add Device(s)‘ and select the domain from the Select Category drop-down menu. The Windows devices in the selected domain will be automatically discovered and listed:
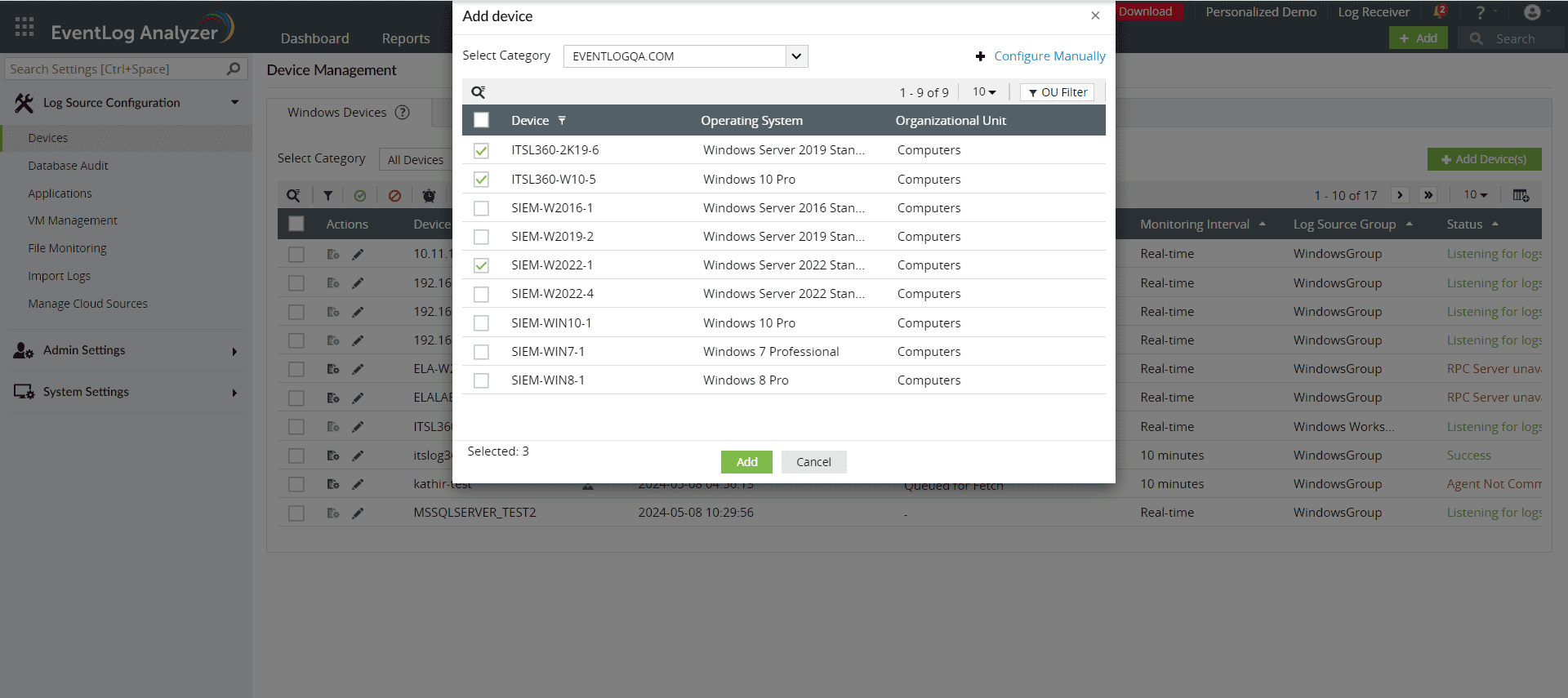
Automatically discovering devices in EventLog Analyzer (click to enlarge)
- Select the devices by clicking the respective check boxes. You can easily search for a device by using the search box or by filtering based on the OU with the OU Filter option:
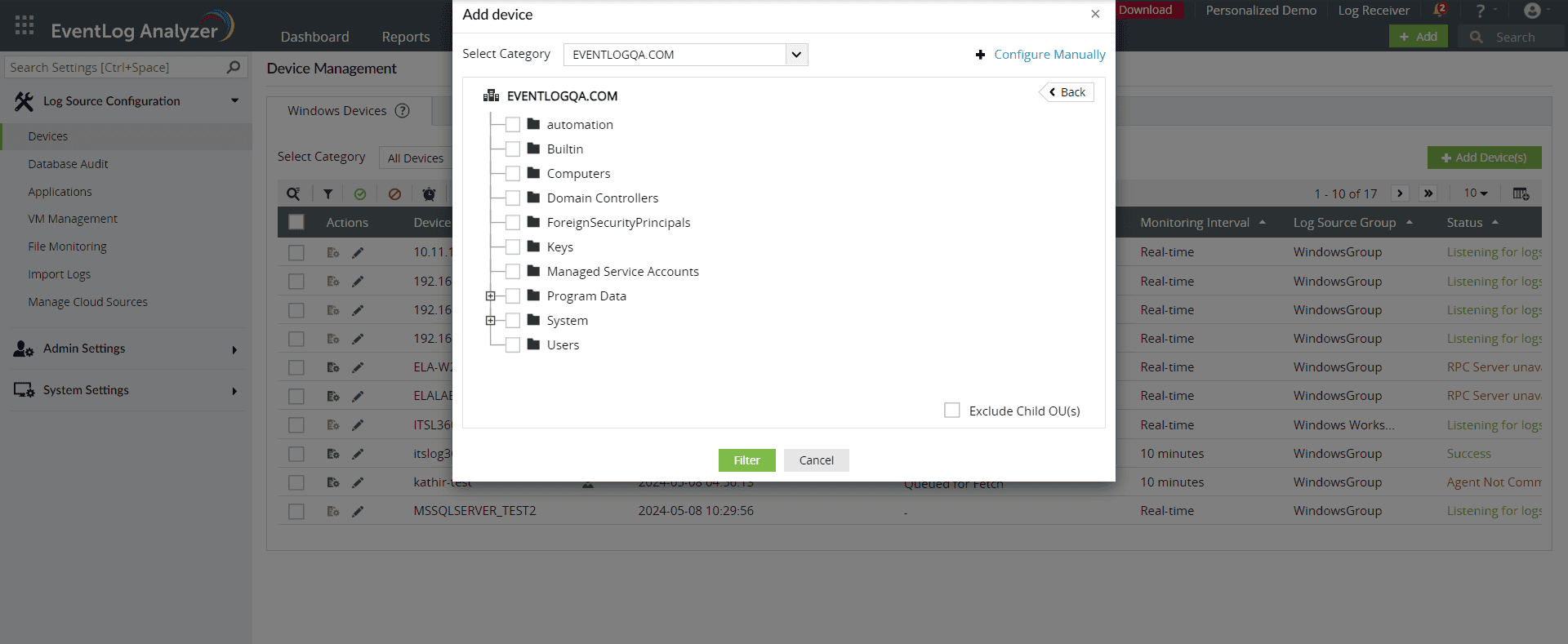
Using the OU Filter option in EventLog Analyzer to search for devices (click to enlarge)
- Click Add to add the devices for monitoring.
With EventLog Analyzer, you can customize log collection based on time. You have the option of collecting logs from the current time or from the past few hours, days, weeks, or even months.
To collect logs according to time:
- On the Settings tab, navigate to Log Source Configuration > Devices > + Add Device(s) > + Configure Manually.
- Click the historical log collection icon in the top-right corner as shown below:
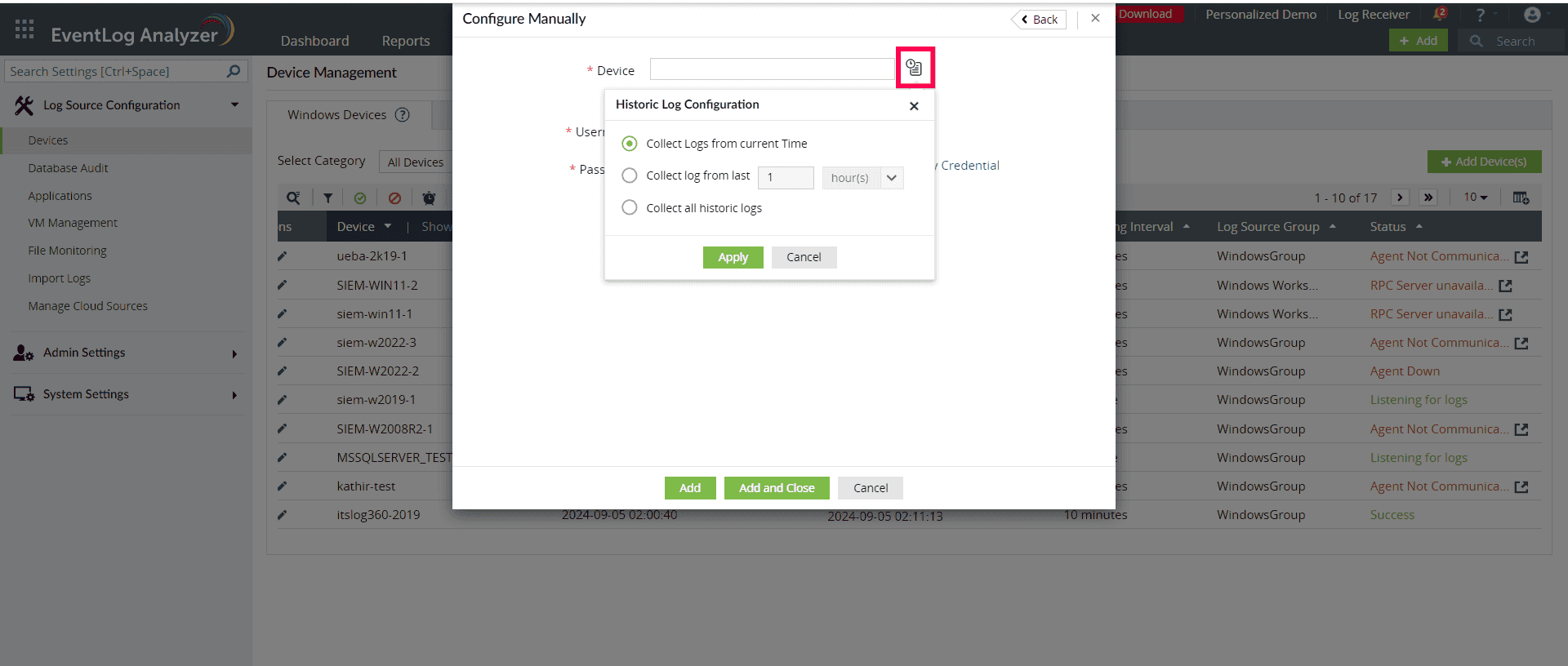
Historical log collection in EventLog Analyzer.
- For the Collect log from last option, select the number of hours, days, weeks, or months for which you would like to collect the historical logs.
- Click Apply.
Summary
Analyzing and monitoring Windows Server event logs involves checking for errors, security breaches, or malfunctions in system-generated logs in real time. This facilitates enhancing security, ensuring high system performance, and promptly resolving issues. It ensures proactive issue resolution and compliance with security policies.
EventLog Analyzer is a comprehensive log management tool that supports Windows event logs along with other log sources—all on a single console. It parses, analyzes, correlates, and archives log data to complete the log management process once the logs are collected on a central server.
Need more power and insights than Windows Event Viewer can deliver? We show you some of the best tools to manage the Windows event log across your network.
Network Security and Administration Expert
Updated: November 30, 2024

Windows event log data is a goldmine of information that you can use to monitor network infrastructure and manage security events
While you can use Windows Event Viewer, log management tools are a superior alternative and enable you to manage Windows event log data with enhanced GUIs and visualizations.
Here is our list of the best tools to manage Windows Event Log / Event Viewer:
- SolarWinds Log Analyzer EDITOR’S CHOICE This tool collects, centralizes, and analyzes log data from Windows systems. It provides real-time log monitoring, detailed event analysis, and manual and automated search capabilities, helping with troubleshooting, security monitoring, and compliance reporting. Runs on Windows Server. A 30-day free trial is available.
- ManageEngine EventLog Analyzer (FREE TRIAL) Log management software with custom reports, a correlation engine, and more. Download the 30-day free trial.
- Site24x7 Log Management (FREE TRIAL) A log server, consolidator, and processor that is available from several plans offered by a cloud-based system monitoring platform. 30-day free trial available.
- ManageEngine Log360 (FREE TRIAL) A SIEM that collects Windows Event logs plus Syslog messages and data from more than 700 applications. Runs on Windows Server. Start a 30-day free trial.
- Netwrix Event Log Manager Free event log management tool that centrally stores Windows event log data, and generates event alerts.
- LogRhythm SIEM platform with analytics, machine intelligence, workflow automation, alarms, and more.
- Sumo Logic Free log management software, available as a SaaS service with custom dashboards, real-time analytics, and machine learning.
- Datadog Cloud monitoring tool with log management capabilities, dashboards, alerts, search, filtering, and more.
- Syslog-NG Log management software with TLS encryption, log collection, storage, forwarding, and more.
The best tools to manage Windows Event Log / Event Viewer
The following reviews include some of the top log management tools, SIEM software, and other tools that provide network administrators with more visibility into logs.
Our methodology for selecting Windows Event log management tools
We reviewed the market for Windows Event log management software and assessed the options based on the following criteria:
- The ability to receive and file Windows Events messages
- A file management service that creates meaningful logfile names and a meaningfully named directory structure
- A logical logfile rotation strategy that prevents log files from becoming too large while maintaining a manageable file naming strategy
- Nice to have a log consolidator that can also receive Syslog messages and logs from applications
- A logfile metrics screen in the dashboard that shows the arrival rate of Windows Event messages and optionally displays those messages on the screen
- A free trial or a money-back guarantee that creates a no-risk assessment period
- A comprehensive tool that improves efficiency and is sold at a reasonable price
1. SolarWinds Log Analyzer (FREE TRIAL)
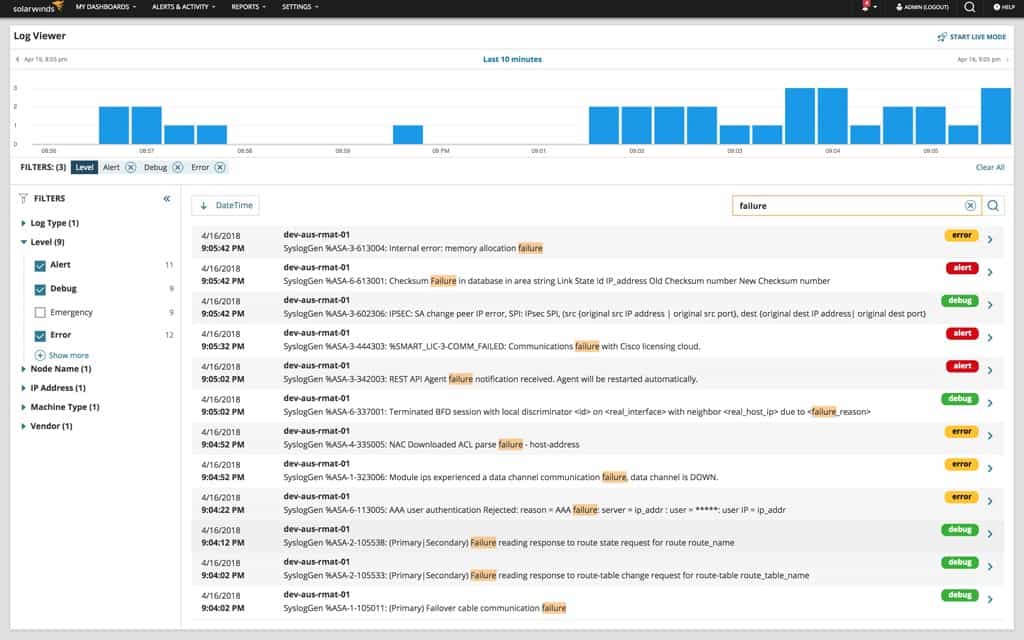
SolarWinds Log Analyzer is an event log monitoring tool for Windows that collects event log data. You can monitor event log data in real-time through syslog, SNMP traps, and system event logs. Data can be collected and monitored through one user interface.
Key Features:
- Real-Time Log Monitoring: Tracks log data as it occurs for immediate insights.
- Log Tagging and Filtering: Simplifies log navigation and categorization.
- Customizable Alerts: Sets alerts based on specific log criteria.
- Centralized Log Collection: Collects Windows Event Logs, Syslog, and custom log formats, for centralized storage and analysis.
- Security Event Correlation: Combines log data from multiple sources to identify and respond to security incidents.
Why do we recommend it?
SolarWinds Log Analyzer runs on Windows Server and it will collect log messages from all around your network, covering all endpoints and the software that runs on them. The tool will collect Windows Events, Syslog messages, and logs from applications. The service can file or forward consolidated logs.
The software is very easy to use. Tagging and filtering enable the user to navigate through log data efficiently. There is also a search bar, and event logs are tagged with icons including warning, alert, error, emergency, and debug so that the user understands what’s happening more clearly.
A customizable alert system enables the user to set trigger conditions for alerts. Users can set alerts according to severity, and configure reset conditions to minimize false positives. Alerts can be sent from email and trigger external scripts to ensure you respond to performance events as they unfold.

Who is it recommended for?
This log analyzer shows log messages as they arrive, provides statistics on arrival rates by source, type, and severity, and it includes a data viewer for analysis. You can set up your own custom queries to perform on messages and link them through to custom alerts. However, this is not a full SIEM system.
Pros:
- Versatile Log Collection: Gathers logs from Syslog, SNMP traps, and system event logs.
- User-Friendly Interface: Makes log management accessible and efficient.
- Event Log Mining: Supports thorough analysis and troubleshooting.
- Log Retention and Compliance: Implements regulatory compliance, and automatically archives older logs to reduce storage costs.
- Log Forwarding: Forward logs to other systems or external SIEM solutions.
Cons:
- Lacks SaaS Option: Only available as an on-premises solution.
- OS Compatibility: Requires Windows Server 2016 or 2019.
SolarWinds Log Analyzer is an excellent tool for managing Windows event log data through a single pane of glass. The platform provides extensive visibility through an intuitive platform that makes it easy to find the information you need to. Prices start at $1,495 (£1,210). You can download the 30-day free trial.
EDITOR’S CHOICE
SolarWinds Log Analyzer is our top pick for a Windows Event log management tool because it is a real-time log monitoring package that enables users to instantly identify and respond to critical events and security incidents as they happen. This is crucial for maintaining the health and security of Windows-based systems in dynamic, high-traffic environments. The tool implements centralized log collection, consolidating logs from various sources—including Windows Event Logs, Syslog, and custom log formats—into a single platform. This centralized approach streamlines troubleshooting and simplifies the monitoring of large, distributed networks. SolarWinds Log Analyzer also offers advanced search and filtering features, allowing users to drill down into specific events with ease, making it much faster to identify root causes of issues or detect patterns indicative of security threats. Customizable dashboards provide a user-friendly interface for visualizing system health, performance, and security events, giving administrators actionable insights at a glance. The tool’s alerting and notification system ensures that IT teams are instantly notified of critical events or suspicious activity, enabling swift remediation. SolarWinds Log Analyzer supports log forwarding and integration with other security tools, making it a flexible solution that can fit into an organization’s existing IT infrastructure. Its ability to balance simplicity with powerful functionality makes it an ideal choice for organizations looking to streamline log management while enhancing security and compliance efforts.
Download: Get 30-day FREE Trial
Official Site: https://www.solarwinds.com/log-analyzer/registration
OS: Windows Server 2016 or 2019
Related post: Best Log Analysis Tools
2. ManageEngine EventLog Analyzer (FREE TRIAL)

ManageEngine EventLog Analyzer is a log management tool for Windows and Linux that can manage event logs and syslogs. You can process logs at 25,000 logs per second, which enables you to detect cyberattacks in real-time. The software can pull log data from services like WindowsServer, Linux, Oracle, Amazon Web Service, Apache, Cisco, HP, IIS, and more.
Key Features:
- High-Performance Log Processing: Handles up to 25,000 logs per second.
- Customizable Dashboard: Tailors log monitoring to specific needs.
- Compliance Reporting: Supports HIPAA, PCI DSS, ISO 27001, and more.
Why do we recommend it?
ManageEngine EventLog Analyzer is a compliance manager. It requires log messages for source data, so the package also includes a log collector and consolidator that can receive Windows Events, Syslog messages, and logs from applications – 750 sources in total. The tool provides a facility for manual analysis and also generates log message throughput statistics.
The correlation engine automatically processes event logs and compares them with other logs to detect the signs of a cyber attack. The automatic processing enables you to monitor log data more efficiently and stay on top of threats. However, you can use the search module to search manually as well.
Compliance reports enable you to create log reports and comply with a range of regulatory frameworks. The EventLog Analyzer creates reports that comply with PCI DSS, ISO 27001, GLBA, SOX, FISMA, and HIPAA regulations. Reports can also be customized and scheduled according to the preferences of the user.

Who is it recommended for?
ManageEngine provides a lot of deployment options for the EventLog Analyzer. It is available as a SaaS package and it can also be installed on Windows Server or Linux. The package provides log management and provides opportunities for manual analysis. It also implements security scanning. The Free edition would interest very small businesses.
Pros:
- Extensive Log Source Compatibility: Integrates with a variety of services and platforms.
- Efficient Cyber Attack Detection: Identifies security issues in real-time.
- Flexible Log Analysis: Manual and automatic log processing options.
Cons:
- Additional Cost for Multi-Site Monitoring: Can increase the total investment for larger networks.
ManageEngine EventLog Analyzer is one of the top free event log management tools. The free edition supports up to five log sources. Paid versions start at $595 (£481.78) with features like compliance reporting and log forensics. You can download the 30-day free trial.
ManageEngine EventLog Analyzer
Download 30-day FREE Trial
3. Site24x7 Log Management (FREE TRIAL)

Site24x7 Log Management is a module in a suite of monitoring services delivered from the Cloud by Site24x7. This log management tool isn’t available as a standalone product. Instead, it is integrated into all of the packages that Site24x7 offers. These are:
- Website Monitoring
- Site24x7 Infrastructure
- Application Performance Monitor
- All-in-one
- MSP
The Site24x7 system is mainly resident in the Cloud but it does need a data collector to be installed on the monitored system. This agent is available for the Windows Server and Linux operating system and it can collect statistics over a network.
Key Features:
- Diverse Log Collection: Gathers Windows Events, Syslog, and application logs.
- Unified Log Format Consolidation: Streamlines log management across different sources.
- Comprehensive Data Analysis Tools: Enhances log data examination.
Why do we recommend it?
Site24x7 Log Management is a cloud-based log collector and consolidator. This system is able to gather log messages from multiple sites and file them. It also shows live messages as they arrive and can provide throughput statistics. The package can handle Windows Events and Syslog messages as well as application logs.
The data collector also catches log messages as they circulate around the server and network. It collects Windows Event messages and also Syslog and application log messages. These are sent to the Site24x7 server over a secure connection for processing. The server consolidates all of the log messages that it receives and converts them into a common format. This enables a unified treatment of log messages from all sources.
The Log Management system includes a data viewer, which can be accessed from the Site24x7 system dashboard. This includes data analysis features such as the ability to sort, filter, group, and summarize records.

Who is it recommended for?
The Site24x7 system is affordable for any size of enterprise. The service also provides a 30-day window for the storage of log files. You can set up the system to forward logs immediately to another system or accumulate them in files and move them to another storage location.
Pros:
- Cloud-Based Flexibility: Offers remote accessibility and management.
- Real-Time Log Viewing: Allows immediate log data analysis.
- Integrated with Site24x7 Services: Part of a comprehensive monitoring suite.
Cons:
- No Standalone Version: Must be used within the Site24x7 ecosystem.
All of the Site24x7 packages are subscription services and all are available on 30-day free trials. For example, you can get a free trial of the Site24x7 Infrastructure plan in order to try out the services’ Log Management tool.
Site24x7 Log Management
Start 30-day FREE Trial
4. ManageEngine Log360 (FREE TRIAL)
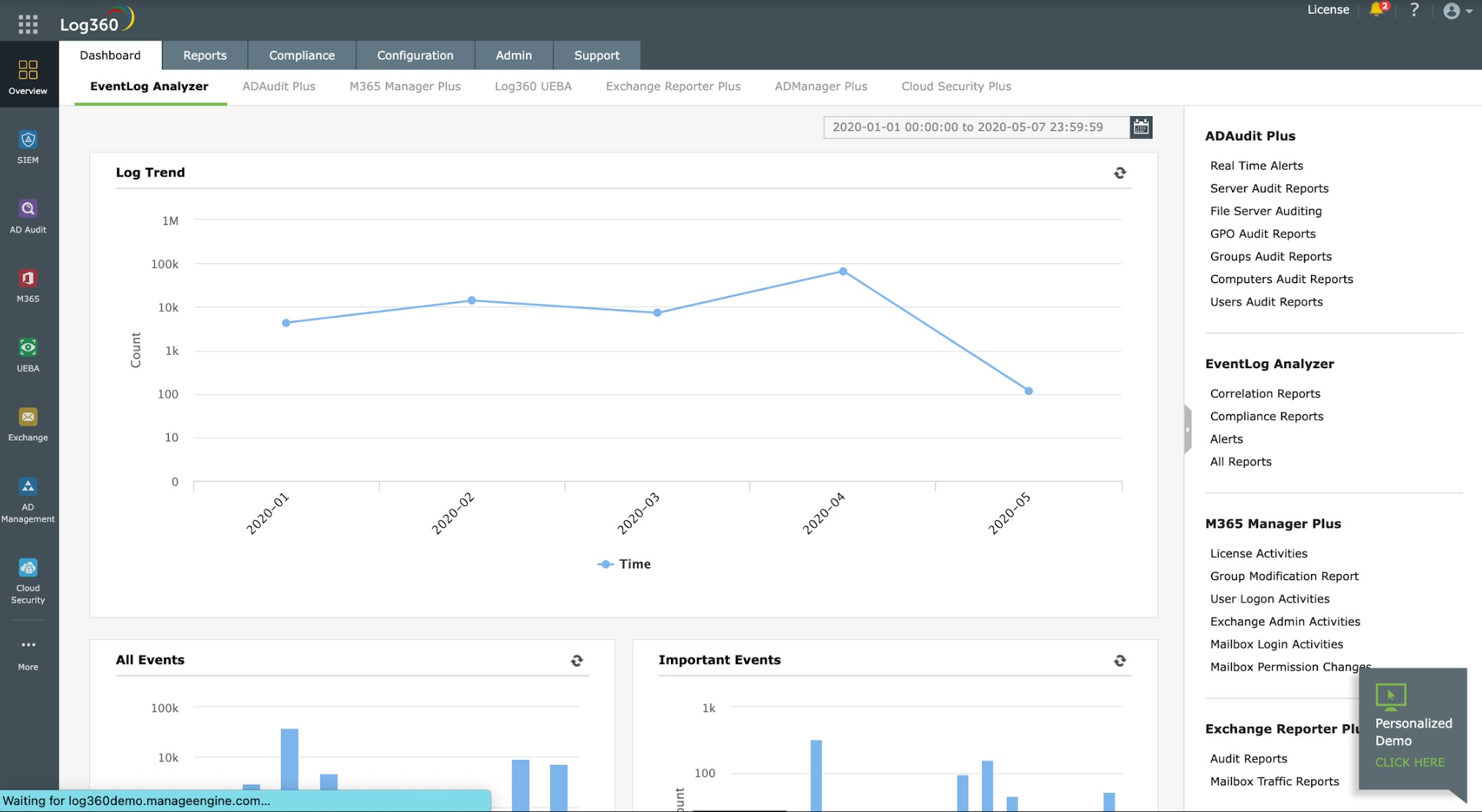
ManageEngine Log360 collects log messages and feeds them into a SIEM for threat detection. The collectors operating on Windows devices will pick up Windows Event logs and interact with software packages to extract operational data. The service can communicate with more than 700 applications. When operating on Linux, a Log360 agent will collect Syslog messages.
Key Features:
- Broad Application Integration: Works with over 700 applications for comprehensive coverage.
- Advanced Threat Intelligence Feed: Stays updated with current security threats.
- Regulatory Compliance Assistance: Meets HIPAA, PCI DSS, FISMA, SOX, GDPR, and GLBA standards.
Why do we recommend it?
ManageEngine Log360 is a megapack of log management and analysis systems and it provides a SIEM tool for security scanning. The EventLog Analyzer is included in the package along with five other log management tools for Windows Events, Syslog, application logs, and cloud platform reports. The system provides compliance reporting and data loss prevention.
The server component of Log360 installs on Windows Server but the collector system is available for a list of operating systems. The collectors send data to the log server, which converts their different formats into a common standard. The log server then files messages in a meaningful directory structure, rotating files daily or, for larger systems, more frequently. The log files need to be made available for investigation.
The dashboard for the system shows log throughput statistics and alerts. The console also includes a data viewer, which has manual analysis tools. Log messages are shown in the data viewer as they arrive and can also be loaded in from log files.

Who is it recommended for?
This is a very large package of system security tools and there is no Free edition, so it is unlikely to appeal to small businesses. As this tool is able to collect activity data from cloud platforms as well as on-premises assets, the system is ideal for use by businesses that operate a hybrid environment.
Pros:
- Extensive Log Management Tools: Offers a range of functionalities for different needs.
- Security-Oriented Features: Provides SIEM capabilities for enhanced protection.
Cons:
- Potentially Overwhelming Feature Set: Might be more than required for simple log management tasks.
The SIEM system has many features, which include a threat intelligence feed to speed up threat detection. The system produces alerts that can be channeled through service desk systems. You can assess ManageEngine Log360 with a 30-day free trial.
ManageEngine Log360
Download 30-day FREE Trial
5. Netwrix Event Log Manager
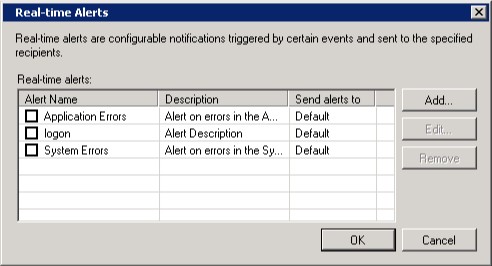
Netwrix Event Log Manager is a free event log management software that can collect Windows event logs. It collects event logs and centrally stores them for the user to analyze. The tool allows you to monitor the event log data of multiple Windows devices from one centralized location.
Key Features:
- Centralized Event Log Storage: Aggregates logs for easier access and analysis.
- Real-Time Alerts: Notifies about important events as they occur.
- Event Summaries: Provides quick insights into log data trends.
Why do we recommend it?
Netwrix Event Log Manager is a free tool that collects Windows Events messages and provides a range of useful services, such as statistical analysis on message throughput and log forwarding or filing. Although this tool centralizes the collection of Windows Events, it doesn’t provide handling for Syslog messages.
Managing and configuring the Event Log Manager is simple for new users. The platform runs as a service so you don’t need to have it open at all times for monitoring. To configure the tool, all the user needs to do is add target computers to monitor the network and enter alert parameters to determine when notifications are generated.
The alerts system sends you email notifications whenever an important event happens to a connected device. You can control what alerts you’re notified about through a dialog box. For example, you can set the system to notify you about Application Errors and Systems Errors.
Who is it recommended for?
This is a nice free tool for viewing Windows Events and it also provides analysis features such as searching and sorting. You can also set up alerts that you can have sent to you by email. This offers an administrator with no budget a way to assemble a customized monitoring system.
Pros:
- Streamlined Windows Event Management: Specifically tailored for Windows environments.
- Free Tool: Accessible to businesses of any size without budget constraints.
Cons:
- Limited to Windows Event Logs: Does not handle other log types like Syslog.
Netwrix Event Log Manager is a reliable tool for enterprises looking to manage Windows Event Log and event viewer data for free. It’s available for Windows XP SP3 and above, Windows Server 2008, 2012, and 2016. You can download the software for free.
6. LogRhythm
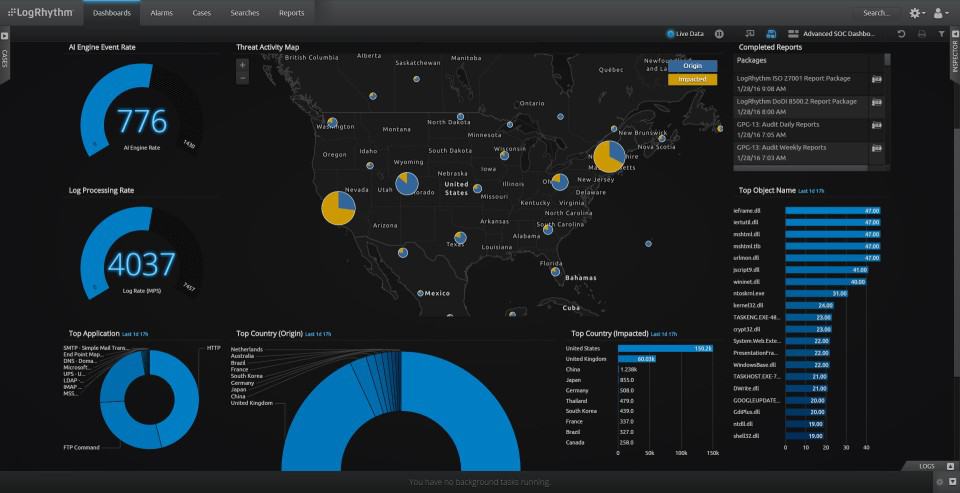
LogRhythm is a SIEM platform that can be deployed on-premises or in the cloud with high-performance and speed. It uses ElasticSearch to maintain performance for users during indexing and searching. Log data captured by the program is searchable so that you can locate event log data fast and easily.
Key Features:
- Advanced SIEM Capabilities: Provides high-end security incident and event management.
- ElasticSearch Integration: Ensures performance during data indexing and searching.
- Machine Intelligence: Employs AI for more accurate threat detection.
Why do we recommend it?
LogRhythm is a top-of-the-line cloud-based SIEM system that has an option user behavior analytics module. This tool collects and consolidates log messages from many sources, which include Windows Events and Syslog messages. It also consolidates different log formats into a common layout and files them.
Through a web-based user interface, users can monitor security incidents throughout their entire network. Security analytics and visualizations provide you with an engaging presentation of log data. Log data is processed by Machine Data Intelligence to classify and structure log messages to produce over 800 different data sources.

When it comes time to respond to an issue, LogRhythm has an alarms system that notifies the users about security events. To lower the time to resolve the user can use SmartResponse to create automated response workflows. The SmartResponse feature allows you to automatically complete tasks such as running a vulnerability scan or disabling a user account.
Who is it recommended for?
There is a log manager at the heart of the LogRhythm system because logs are the source data for the SIEM, which is the key feature of the platform. However, if you are just looking for a log manager, this option is way more than you need.
Pros:
- Scalable Architecture: Adapts to various organizational sizes and complexities.
- Comprehensive Security Monitoring: Offers a full suite of security-focused features.
Cons:
- Complex for Simple Log Management Needs: May offer more functionality than required for basic log management.
It’s is an excellent log management solution for scalability. LogRhythm offers a flexible pricing model that supports up to an unlimited number of log sources and users. However, you need to request a quote from the company directly. You can watch the demo.
7. Sumo Logic

Sumo Logic is a free SaaS-based log management tool that collects and analyzes windows event logs. You can create custom dashboards and use real-time analytics to monitor security events throughout your network. The analytics system can identify performance anomalies by analyzing log patterns, which helps the user to make sense of log data.
Key Features:
- Custom Dashboards: Personalizes log data visualization.
- Real-Time Analytics: Delivers immediate insights into log patterns.
- Machine Learning-Driven Alerts: Provides intelligent notifications of anomalies.
Why do we recommend it?
Sumo Logic is a SaaS platform that provides system monitoring and log management. The Free edition provides the base plan for the system. If you are just looking for a log manager, this is as far as you need to go because the higher plans add on a SIEM and other security monitoring tools.
One of its advantages is the ability to share dashboards and reports with other users. Dashboards include a range of displays such as charts to help the user make sense of log data. Users also have the option to adjust the time frame they’re looking at to change the data they view.

Who is it recommended for?
The Sumo Logic free package is limited to processing 1 GB of data per day. That’s great for small businesses but larger enterprises will have to upgrade to one of the paid plans. The higher plans provide security scanning, which you might not want if you are just looking for a log management package.
Pros:
- API Integration: Enhances functionality with third-party tools.
- Compliance Support: Meets PCI DSS, SOX, and HIPAA requirements.
Cons:
- Limited Free Plan Storage: 4 GB storage cap might be restrictive for larger enterprises.
Sumo Logic is a platform that’s recommended for those users who want a log management platform with top-notch analytics capabilities. The free version supports up to 4GB of log storage. Users that require more can purchase a paid version. Paid versions start at $90 (£72.97) per month per 1GB daily ingest. You can start the free trial.
8. Datadog

Datadog is a cloud monitoring tool that can monitor applications, services, and log data. You can take Windows Event Log data and use it to generate events in your Event Stream. The Event Stream displays a list of recent events that have occurred throughout your network.
Key Features:
- Integrated Log Management: Collects and analyzes logs within a unified platform.
- Advanced Filtering: Tailors log data analysis to specific needs.
- Machine Learning Alerts: Intelligent alerting based on log data trends.
Why do we recommend it?
Datadog Log Management is a cloud-based system that is able to collect and consolidate Windows Events, Syslog messages, and application logs. The tool calculates statistics on log message arrival and also displays messages in a data viewer. The data viewer can also load in messages from files.
The software enables you to search and filter log data in one place. All data can be archived centrally so that it’s accessible when you need it. Log data can be viewed through the dashboard, which is packed with visualization options like charts and diagrams to give you a more sophisticated perspective of what’s going on.
Machine learning-driven alerts notify you the moment there’s a problem. Alert notifications can be sent directly to external services like Slack, Hangouts Chat, and Microsoft Teams. You can also use Webhooks to follow up with custom code to deliver an automated response to the problem.

Who is it recommended for?
This tool is very affordable because all of its services are priced by data throughput. Another factor that enters into pricing is a data retention period for archiving. However, you could choose to file messages in this tool and then move those files elsewhere for archiving and save money.
Pros:
- Real-Time Log Collection: Gathers log data continuously for up-to-date insights.
- User-Friendly Dashboard: Simplifies monitoring and analysis of logs.
Cons:
- Complex Pricing Structure: Pricing based on data throughput and retention can be confusing.
There is a range of pricing options available for Datadog depending on your use case. For log management, prices start at $1.27 (£1.03) per million log events, per month with 7-day data retention or $0.10 (£0.081) per ingested or scanned GB, per month. You can start the 14-day free trial.
9. Syslog-NG

Syslog-NG is a log management solution that can collect and store Windows event logs. It can collect data from over 10,000 log sources and uses TLS encryption to protect important messages from unauthorized access. The platform offers users filtering to assist with navigation and store data in binary files.
Key Features:
- Log Data Storage: Safely archives log data for later analysis.
- Log Filtering and Forwarding: Organizes and redirects log data as needed.
- TLS Encryption: Secures log data during transmission and storage.
Why do we recommend it?
Syslog-NG is a free tool and it is able to process and forward Syslog messages, Windows Events, and many application log sources. It gives you the option of storing log messages to file or inserting them into a database. You can get the software and run it on your own server.
The software enables the user to forward log data to external tools. Users can send logs to SQL databases, MongoDB, and Hadoop Distributed File System nodes. The user can also send logs via SNMP or SMTP. Forwarding log data makes it easier for organizations to manage logs in the format that’s most convenient.
Who is it recommended for?
The free community edition is a good choice for those who just want to collect, consolidate, and file log messages. The paid options provide more options because they provide professional support, include a GUI interface, and can be run as software or bought as a network appliance.
Pros:
- Supports Over 10,000 Log Sources: Offers extensive log source compatibility.
- Flexible Log Management: Adapts to various organizational requirements.
Cons:
- Lacks Syslog Processing: Does not handle Syslog messages, limiting its scope.
Syslog-NG is recommended for enterprises that want a simple but comprehensive log management solution that supports a range of log sources. You can request a custom price quote from the sales team on the company website. Download the 30-day free trial.
Choosing the right tool for your organization
Managing Windows event logs is something that every enterprise should be doing. Having the visibility to detect failed services and availability issues early reduces the chance of the network is disrupted. The log management tools we’ve listed can all manage Windows event log data effectively, and give you the best chance of catching performance problems quickly.
Our editor’s choice for this article is SolarWinds Log Analyzer as it offers Windows users a comprehensive Windows event log monitoring experience for a competitive price tag. ManageEngine EventLog Analyzer also offers users a high-quality alternative and is recommended for companies looking for a free log management solution.
Windows Event Log Management FAQs
What is Event Log management?
Windows Events is Microsoft’s system for logging activity. These messages give status information from the operating system, Microsoft products, and third-party software packages. Managing these messages involves collecting them and storing them in files.
What are the five types of event logs?
Windows Event Log messages have five level codes: Information, Warning, Error, Success Audit, and Failure Audit. The message level makes it easy to filter incoming messages to focus on specific event severities.
What are event logs used for?
Event logs can be used for resource management, system maintenance, and security monitoring. Each message gives a little information about the operations of a resource. Putting those messages together can provide very useful information.